GitBook: [master] 4 pages modified
This commit is contained in:
parent
d5c2278035
commit
10d93c8906
|
|
@ -142,6 +142,7 @@
|
|||
* [Frida Tutorial 3](mobile-apps-pentesting/android-app-pentesting/frida-tutorial/owaspuncrackable-1.md)
|
||||
* [Objection Tutorial](mobile-apps-pentesting/android-app-pentesting/frida-tutorial/objection-tutorial.md)
|
||||
* [Google CTF 2018 - Shall We Play a Game?](mobile-apps-pentesting/android-app-pentesting/google-ctf-2018-shall-we-play-a-game.md)
|
||||
* [Inspeckage Tutorial](mobile-apps-pentesting/android-app-pentesting/inspeckage-tutorial.md)
|
||||
* [Intent Injection](mobile-apps-pentesting/android-app-pentesting/intent-injection.md)
|
||||
* [Make APK Accept CA Certificate](mobile-apps-pentesting/android-app-pentesting/make-apk-accept-ca-certificate.md)
|
||||
* [Manual DeObfuscation](mobile-apps-pentesting/android-app-pentesting/manual-deobfuscation.md)
|
||||
|
|
|
|||
|
|
@ -435,7 +435,7 @@ Also, if you create a **ZIP** file with the source code if an **Android** or an
|
|||
|
||||
MobSF also allows you to **diff/Compare** analysis and to integrate **VirusTotal** \(you will need to set your API key in _MobSF/settings.py_ and enable it: `VT_ENABLED = TRUE` `VT_API_KEY = <Your API key>` `VT_UPLOAD = TRUE`\). You can also set `VT_UPLOAD` to `False`, then the **hash** will be **upload** instead of the file.
|
||||
|
||||
### Dynamic analysis with MobSF
|
||||
### Assisted Dynamic analysis with MobSF
|
||||
|
||||
**MobSF** can also be very helpful for **dynamic analysis** in **Android**, but in that case you will need to install MobSF and **genymotion** in your host \(a VM or Docker won't work\). _Note: You need to **start first a VM in genymotion** and **then MobSF.**_
|
||||
The **MobSF dynamic analyser** can:
|
||||
|
|
@ -495,6 +495,10 @@ adb shell settings put global http_proxy :0
|
|||
```
|
||||
{% endhint %}
|
||||
|
||||
### Assisted Dynamic Analysis with Inspeckage
|
||||
|
||||
You can get the tool from [**Inspeckage**](https://github.com/ac-pm/Inspeckage).
|
||||
|
||||
### [Yaazhini](https://www.vegabird.com/yaazhini/)
|
||||
|
||||
This is a **great tool to perform static analysis with a GUI**
|
||||
|
|
|
|||
|
|
@ -0,0 +1,61 @@
|
|||
# Inspeckage Tutorial
|
||||
|
||||
**Tutorial copied from** [**https://infosecwriteups.com/genymotion-xposed-inspeckage-89f0c8decba7**](https://infosecwriteups.com/genymotion-xposed-inspeckage-89f0c8decba7)\*\*\*\*
|
||||
|
||||
### Install Xposed Framework <a id="ef45"></a>
|
||||
|
||||
1. Download Xposed Installer APK from [here](https://forum.xda-developers.com/attachments/xposedinstaller_3-1-5-apk.4393082/)
|
||||
2. Download Xposed Framework zip from [here](https://dl-xda.xposed.info/framework/sdk25/x86/xposed-v89-sdk25-x86.zip)
|
||||
3. Download Inspeckage v2.4 APK from the github repo [here](https://github.com/ac-pm/Inspeckage/releases)
|
||||
|
||||
Start the Virtual Device from the menu
|
||||
|
||||

|
||||
|
||||
Make sure the device is online for adb
|
||||
|
||||
|
||||
|
||||
Drag and drop the Xposed framework zip file \(`xposed-vXX-sdkXX-x86.zip`\) to your virtual device display to flash the device.
|
||||
|
||||
Drag and drop Xposed Installer APK \(`XposedInstaller_*.apk`\). This should install and launch _Xposed Installer_ application. At this stage, it will display that the Xposed framework is installed but disabled:
|
||||
|
||||

|
||||
|
||||
Reboot the device with `adb reboot` command. **Do not reboot from** _**Xposed Installer**_ **as this will freeze the device.**
|
||||
|
||||

|
||||
|
||||
Launch _Xposed installer_. It should display “Xposed Framework version XX is active”
|
||||
|
||||

|
||||
|
||||
Drag and drop the Inspeackage APK \(app-release.apk\) to your virtual device display to install the app.
|
||||
|
||||
After installing, Go to Xposed Installer → Modules→ Activate the Module → reboot via adb
|
||||
|
||||

|
||||
|
||||
### Dynamic Analysis with Inspeckage <a id="7856"></a>
|
||||
|
||||
After, Successful installing of Inspeckage and Xposed Installer. Now we can hook any application with Inspeackage. To do this follow the below steps
|
||||
|
||||
1. Launch the Inspeckage Application from the application drawer
|
||||
2. Click on the “Choose target” text and select the target application
|
||||
|
||||

|
||||
|
||||
3. Then forward VD local-host port to main machine using adb
|
||||
|
||||
```text
|
||||
adb forward tcp:8008 tcp:8008
|
||||
```
|
||||
|
||||

|
||||
|
||||
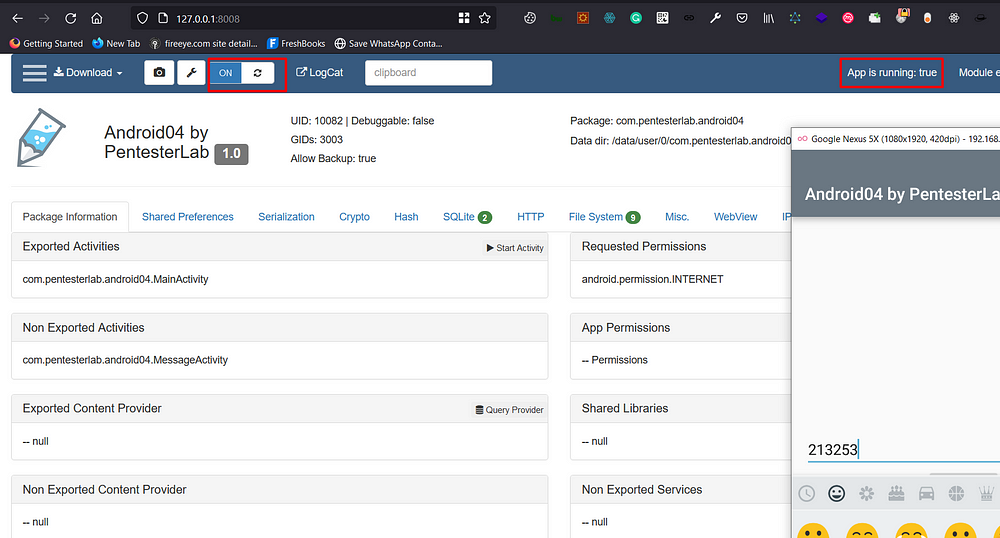
4. Now click on the “**LAUNCH APP**” Button and then visit [`http://127.0.0.1:8008`](http://127.0.0.1:8008/)
|
||||
|
||||
5. Now click Turn On the button to Inspect the app. \(make sure `App is running:` status should be **True** before you “Turn On”
|
||||
|
||||
|
||||
|
||||
|
|
@ -255,7 +255,7 @@ _Note that anytime a new directory is discovered during brute-forcing or spideri
|
|||
|
||||
* [**Broken link checker**](https://github.com/stevenvachon/broken-link-checker): Find broken links inside HTMLs that may be prone to takeovers
|
||||
* **File Backups**: Once you have found all the files, look for backups of all the executable files \("_.php_", "_.aspx_"...\). Common variations for naming a backup are: _file.ext~, \#file.ext\#, ~file.ext, file.ext.bak, file.ext.tmp, file.ext.old, file.bak, file.tmp and file.old._ You can also use the tool [**bfac**](https://github.com/mazen160/bfac).
|
||||
* **Discover new parameters**: You can use tools like [Arjun](https://github.com/s0md3v/Arjun) **and** [parameth](https://github.com/maK-/parameth) **to discover hidden parameters. If you can, you could try to search** hidden parameters on each executable web file.
|
||||
* **Discover new parameters**: You can use tools like [**Arjun**](https://github.com/s0md3v/Arjun)**,** [**parameth**](https://github.com/maK-/parameth)**,** [**x8**](https://github.com/sh1yo/x8) ****and ****[**Param Miner**](https://github.com/PortSwigger/param-miner) **to discover hidden parameters. If you can, you could try to search** hidden parameters on each executable web file.
|
||||
* **Comments:** Check the comments of all the files, you can find **credentials** or **hidden functionality**.
|
||||
* If you are playing **CTF**, a "common" trick is to **hide** **information** inside comments at the **right** of the **page** \(using **hundreds** of **spaces** so you don't see the data if you open the source code with the browser\). Other possibility is to use **several new lines** and **hide information** in a comment at the **bottom** of the web page.
|
||||
* **API keys**: If you **find any API key** there is guide that indicates how to use API keys of different platforms: [keyhacks](https://github.com/streaak/keyhacks), [**zile**](https://github.com/xyele/zile.git)**,** [truffleHog](https://github.com/dxa4481/truffleHog/), [SecretFinder](https://github.com/m4ll0k/SecretFinder), [RegHex](https://github.com/l4yton/RegHex%29\).
|
||||
|
|
|
|||
Loading…
Reference in New Issue