10 KiB
Kubernetes Role-Based Access Control (RBAC)
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.
Role-Based Access Control (RBAC)
Kubernetes has an authorization module named Role-Based Access Control (RBAC) that helps to set utilization permissions to the API server.
RBAC’s permission model is built from three individual parts:
- Role\ClusterRole – The actual permission. It contains rules that represent a set of permissions. Each rule contains resources and verbs. The verb is the action that will apply on the resource.
- Subject (User, Group or ServiceAccount) – The object that will receive the permissions.
- RoleBinding\ClusterRoleBinding – The connection between Role\ClusterRole and the subject.
The difference between “Roles” and “ClusterRoles” is just where the role will be applied – a “Role” will grant access to only one specific namespace, while a “ClusterRole” can be used in all namespaces in the cluster. Moreover, ClusterRoles can also grant access to:
- cluster-scoped resources (like nodes).
- non-resource endpoints (like /healthz).
- namespaced resources (like Pods), across all namespaces.
From Kubernetes 1.6 onwards, RBAC policies are enabled by default. But to enable RBAC you can use something like:
kube-apiserver --authorization-mode=Example,RBAC --other-options --more-options
Templates
In the template of a Role or a ClusterRole you will need to indicate the name of the role, the namespace (in roles) and then the apiGroups, resources and verbs of the role:
- The apiGroups is an array that contains the different API namespaces that this rule applies to. For example, a Pod definition uses apiVersion: v1. It can has values such as rbac.authorization.k8s.io or [*].
- The resources is an array that defines which resources this rule applies to. You can find all the resources with:
kubectl api-resources --namespaced=true - The verbs is an array that contains the allowed verbs. The verb in Kubernetes defines the type of action you need to apply to the resource. For example, the list verb is used against collections while "get" is used against a single resource.
Rules Verbs
(This info was taken from here)
| HTTP verb | request verb |
|---|---|
| POST | create |
| GET, HEAD | get (for individual resources), list (for collections, including full object content), watch (for watching an individual resource or collection of resources) |
| PUT | update |
| PATCH | patch |
| DELETE | delete (for individual resources), deletecollection (for collections) |
Kubernetes sometimes checks authorization for additional permissions using specialized verbs. For example:
- PodSecurityPolicy
useverb onpodsecuritypoliciesresources in thepolicyAPI group.
- RBAC
bindandescalateverbs onrolesandclusterrolesresources in therbac.authorization.k8s.ioAPI group.
- Authentication
impersonateverb onusers,groups, andserviceaccountsin the core API group, and theuserextrasin theauthentication.k8s.ioAPI group.
{% hint style="warning" %}
You can find all the verbs that each resource support executing kubectl api-resources --sort-by name -o wide
{% endhint %}
Examples
{% code title="Role" %}
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: defaultGreen
name: pod-and-pod-logs-reader
rules:
- apiGroups: [""]
resources: ["pods", "pods/log"]
verbs: ["get", "list", "watch"]
{% endcode %}
{% code title="ClusterRole" %}
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
# "namespace" omitted since ClusterRoles are not namespaced
name: secret-reader
rules:
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get", "watch", "list"]
{% endcode %}
For example you can use a ClusterRole to allow a particular user to run:
kubectl get pods --all-namespaces
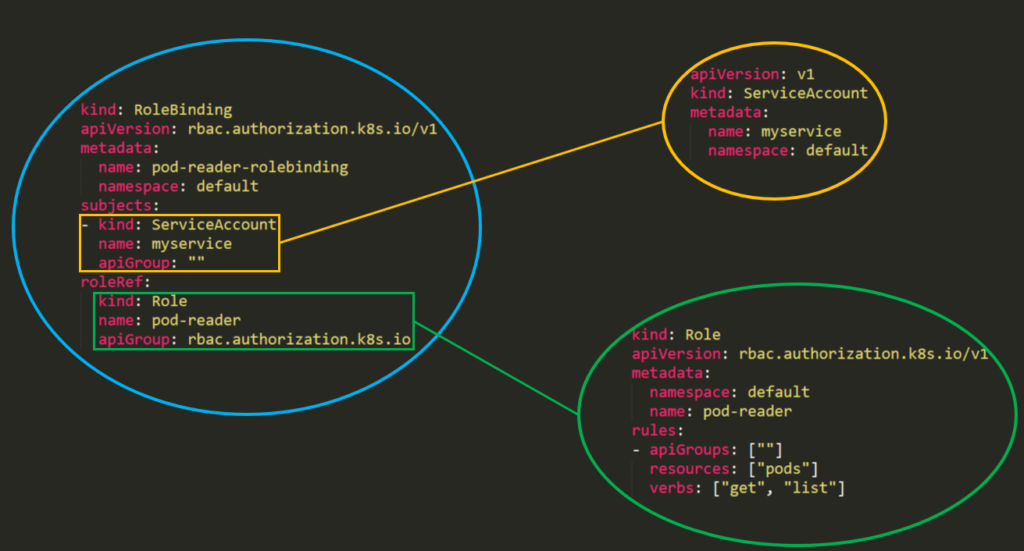
RoleBinding and ClusterRoleBinding
A role binding grants the permissions defined in a role to a user or set of users. It holds a list of subjects (users, groups, or service accounts), and a reference to the role being granted. A RoleBinding grants permissions within a specific namespace whereas a ClusterRoleBinding grants that access cluster-wide.
{% code title="" %}
piVersion: rbac.authorization.k8s.io/v1
# This role binding allows "jane" to read pods in the "default" namespace.
# You need to already have a Role named "pod-reader" in that namespace.
kind: RoleBinding
metadata:
name: read-pods
namespace: default
subjects:
# You can specify more than one "subject"
- kind: User
name: jane # "name" is case sensitive
apiGroup: rbac.authorization.k8s.io
roleRef:
# "roleRef" specifies the binding to a Role / ClusterRole
kind: Role #this must be Role or ClusterRole
name: pod-reader # this must match the name of the Role or ClusterRole you wish to bind to
apiGroup: rbac.authorization.k8s.io
{% endcode %}
{% code title="ClusterRoleBinding" %}
apiVersion: rbac.authorization.k8s.io/v1
# This cluster role binding allows anyone in the "manager" group to read secrets in any namespace.
kind: ClusterRoleBinding
metadata:
name: read-secrets-global
subjects:
- kind: Group
name: manager # Name is case sensitive
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: secret-reader
apiGroup: rbac.authorization.k8s.io
{% endcode %}
Permissions are additive so if you have a clusterRole with “list” and “delete” secrets you can add it with a Role with “get”. So be aware and test always your roles and permissions and specify what is ALLOWED, because everything is DENIED by default.
Enumerating RBAC
# Get current privileges
kubectl auth can-i --list
# use `--as=system:serviceaccount:<namespace>:<sa_name>` to impersonate a service account
# List Cluster Roles
kubectl get clusterroles
kubectl describe clusterroles
# List Cluster Roles Bindings
kubectl get clusterrolebindings
kubectl describe clusterrolebindings
# List Roles
kubectl get roles
kubectl describe roles
# List Roles Bindings
kubectl get rolebindings
kubectl describe rolebindings
Abuse Role/ClusterRoles for Privilege Escalation
{% content-ref url="../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/" %} abusing-roles-clusterroles-in-kubernetes {% endcontent-ref %}
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.